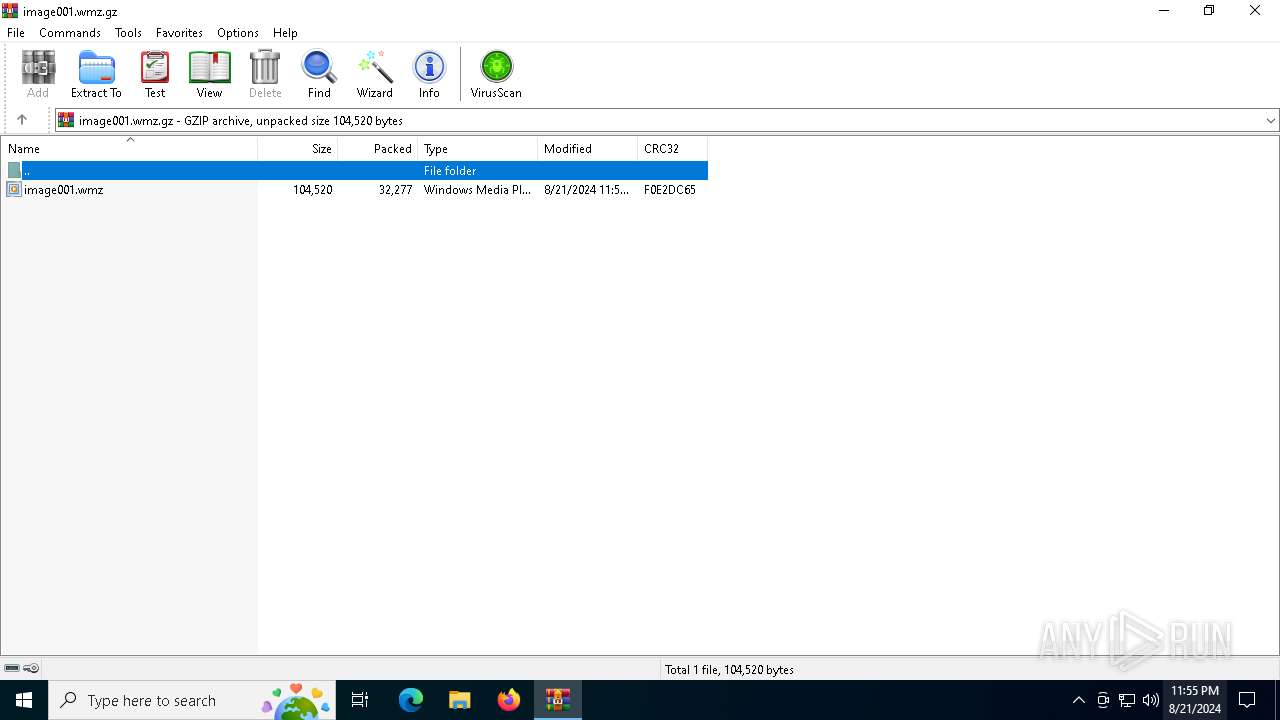
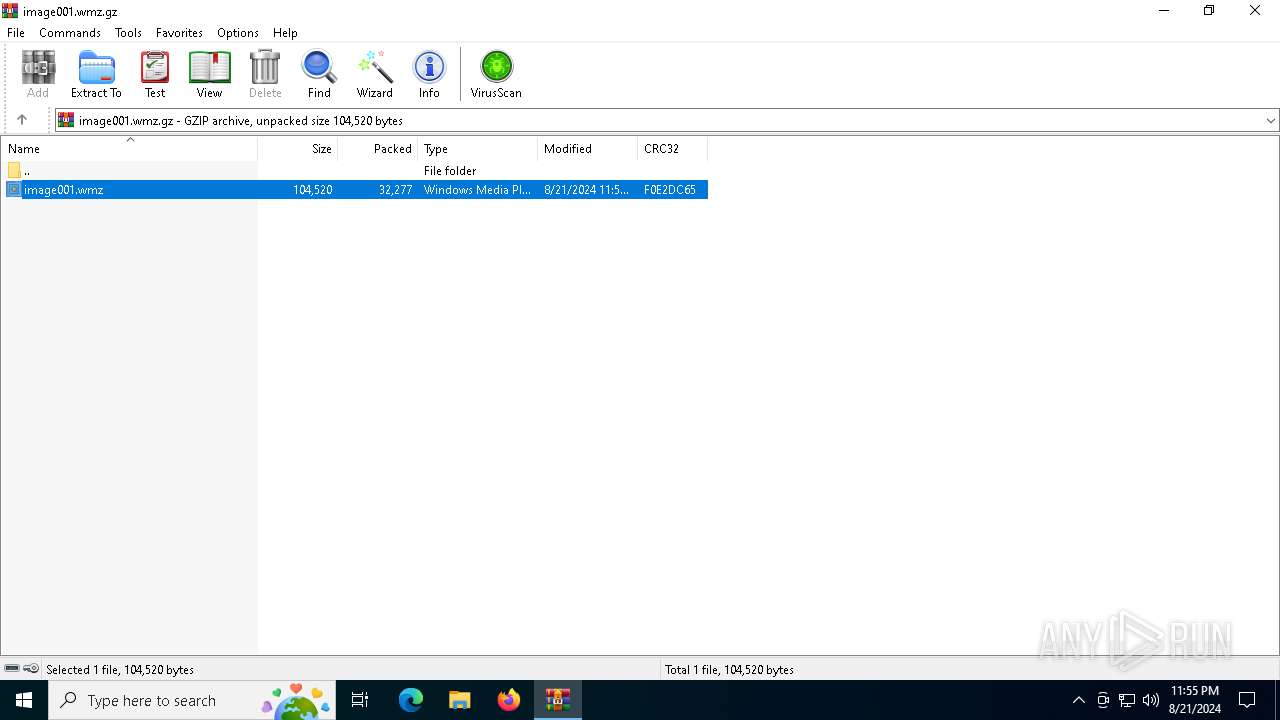
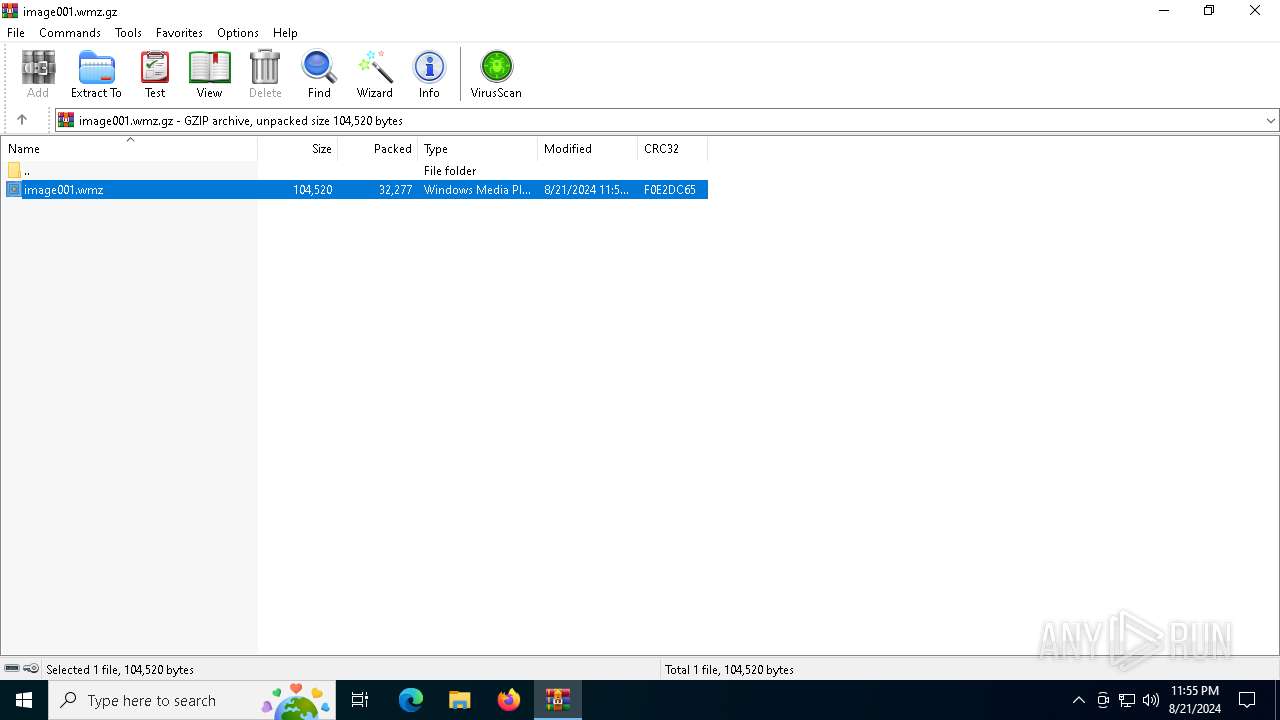
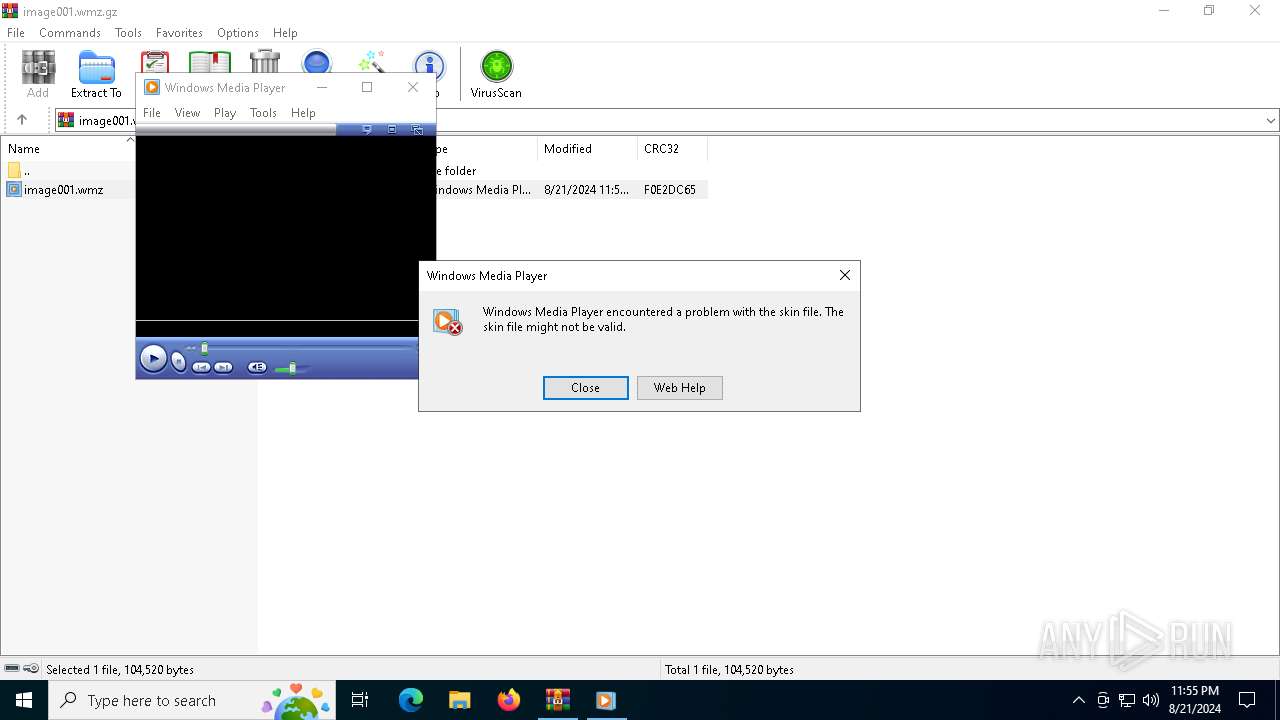
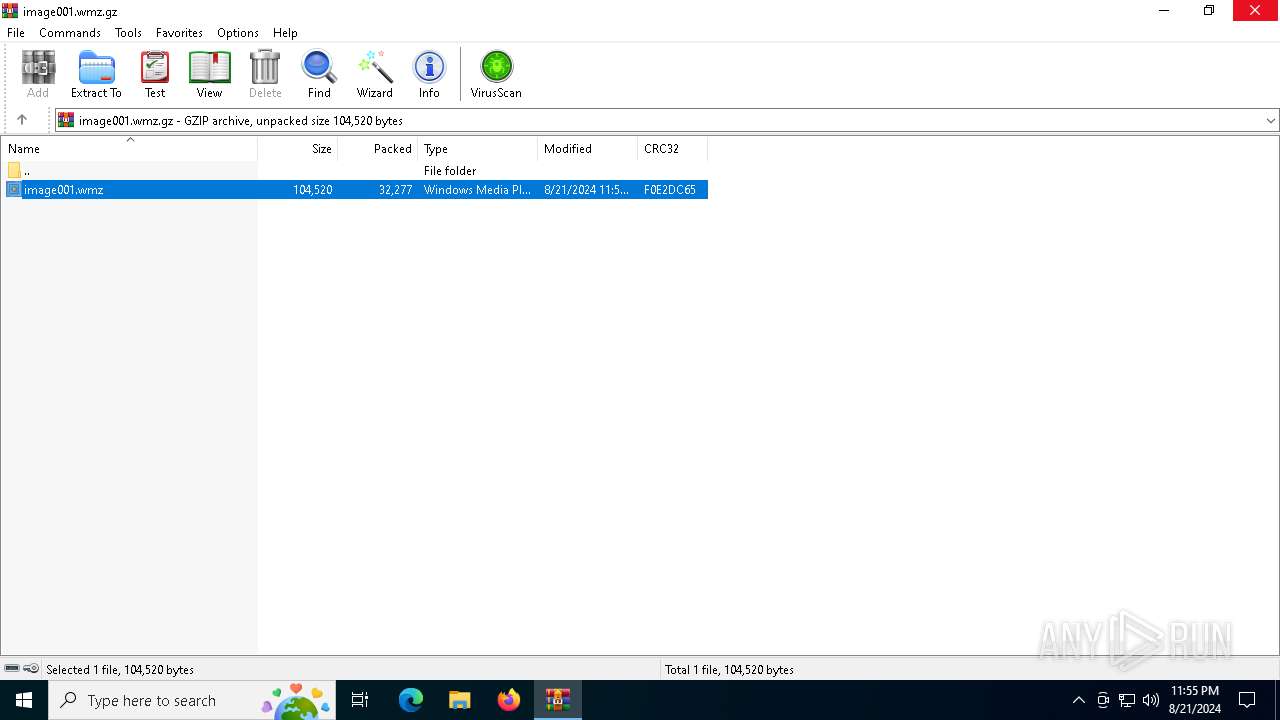
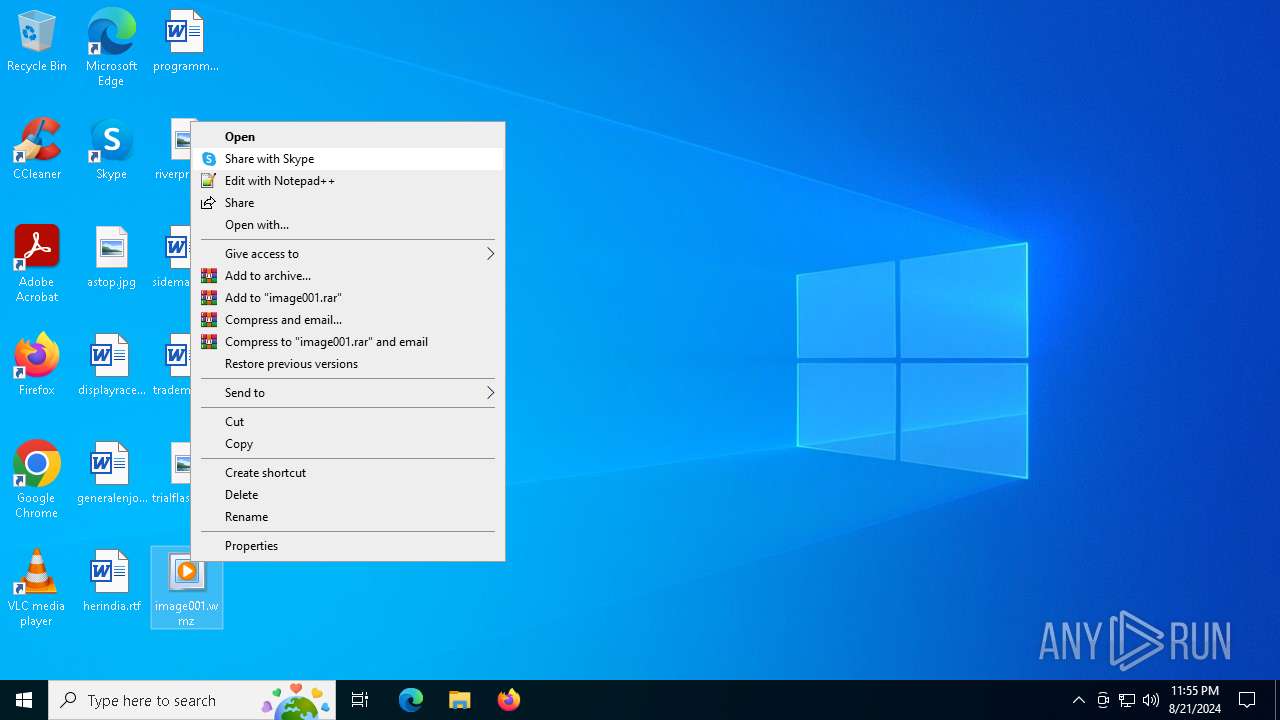
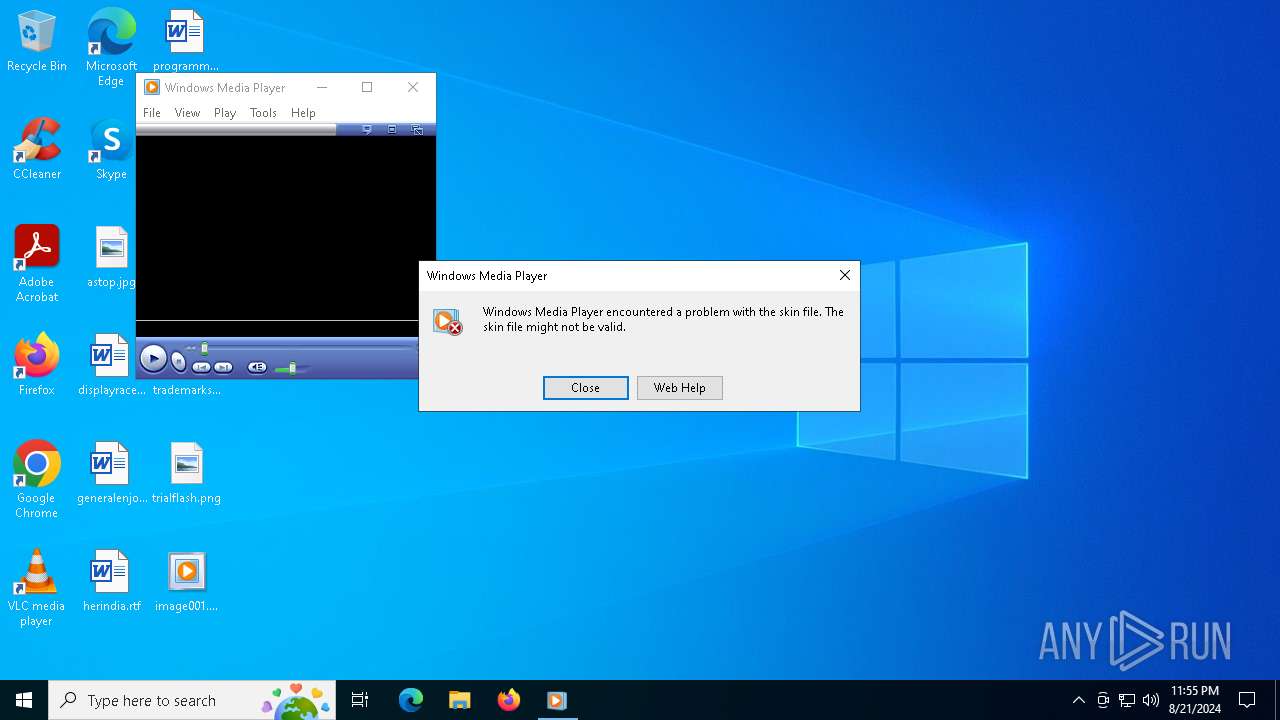
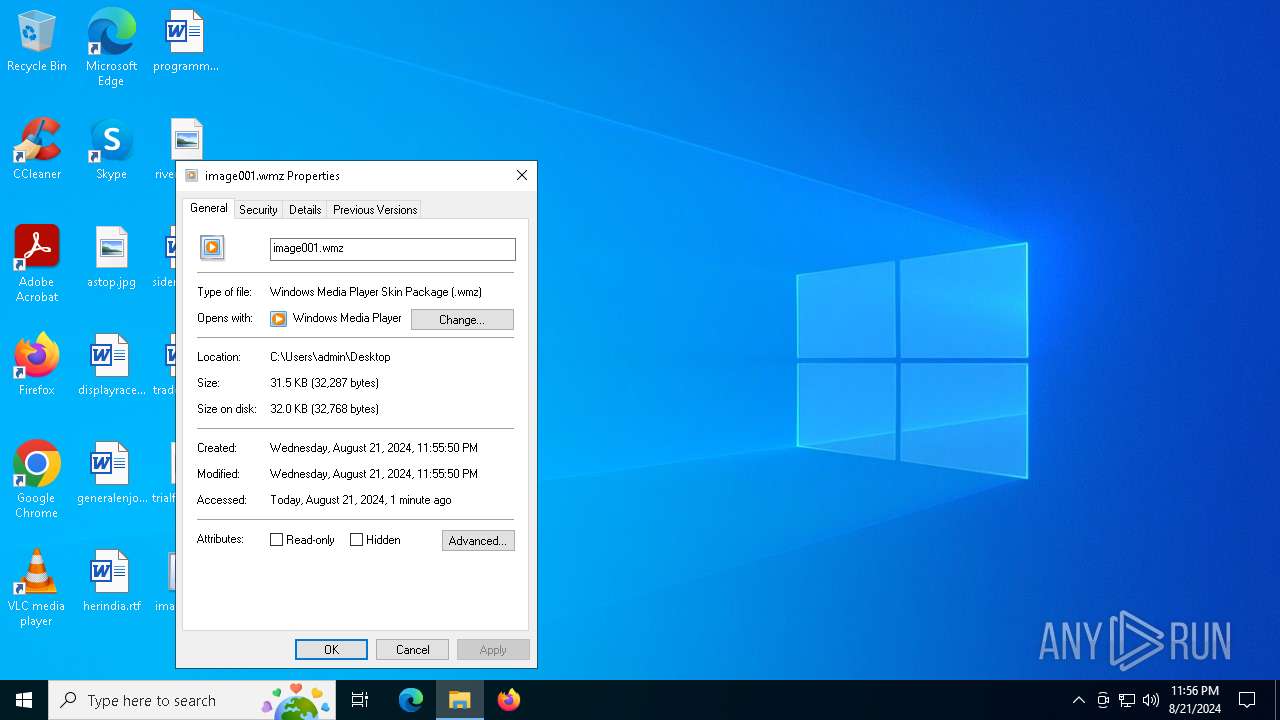
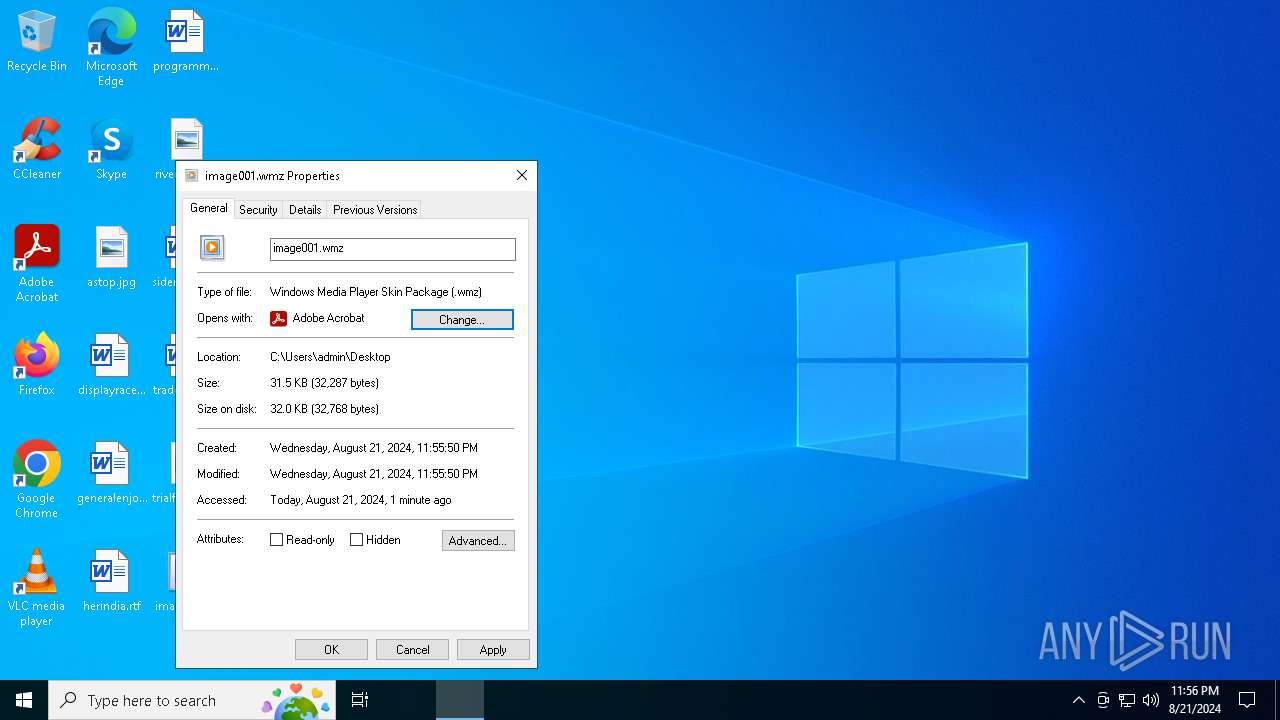
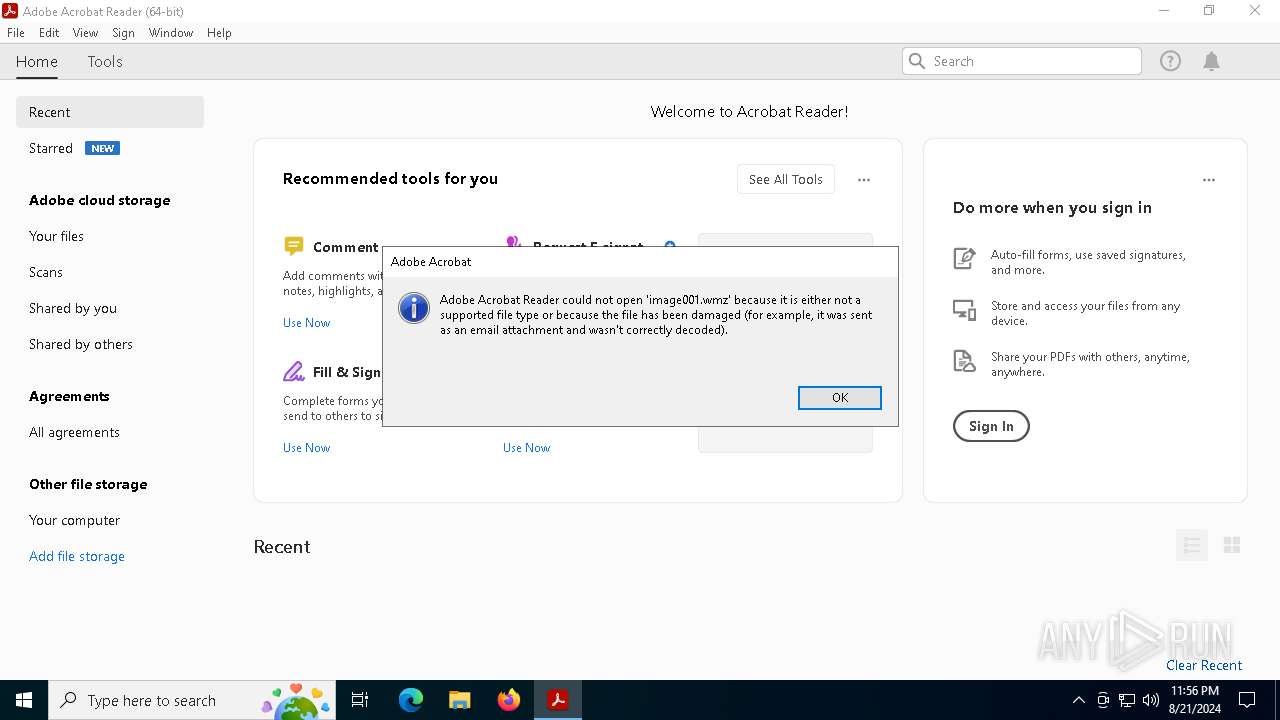
| File name: | image001.wmz |
| Full analysis: | https://app.any.run/tasks/549153ec-aac1-4704-b27f-dfdc1e11c43f |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2024, 23:55:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, max speed, from NTFS filesystem (NT), original size modulo 2^32 104520 |
| MD5: | 21EF923514E57C773CB3AE52C3108FA2 |
| SHA1: | 77F8846764EA8BFEDE12E2A9AF6D0A4790C391A2 |
| SHA256: | F91FD7AFE03E93D921EA6C2F7620514A749A297BE42CED1279F3ED571B33C890 |
| SSDEEP: | 768:ZjuFHAuO0HKP0pkH+BWOhLpp7ZcIl0+fqBsoD3hrY5bIsDIUEhXgsg:Cgt0qP+BWOdplcIaVrD3h5oIUcXgV |
MALICIOUS
Scans artifacts that could help determine the target
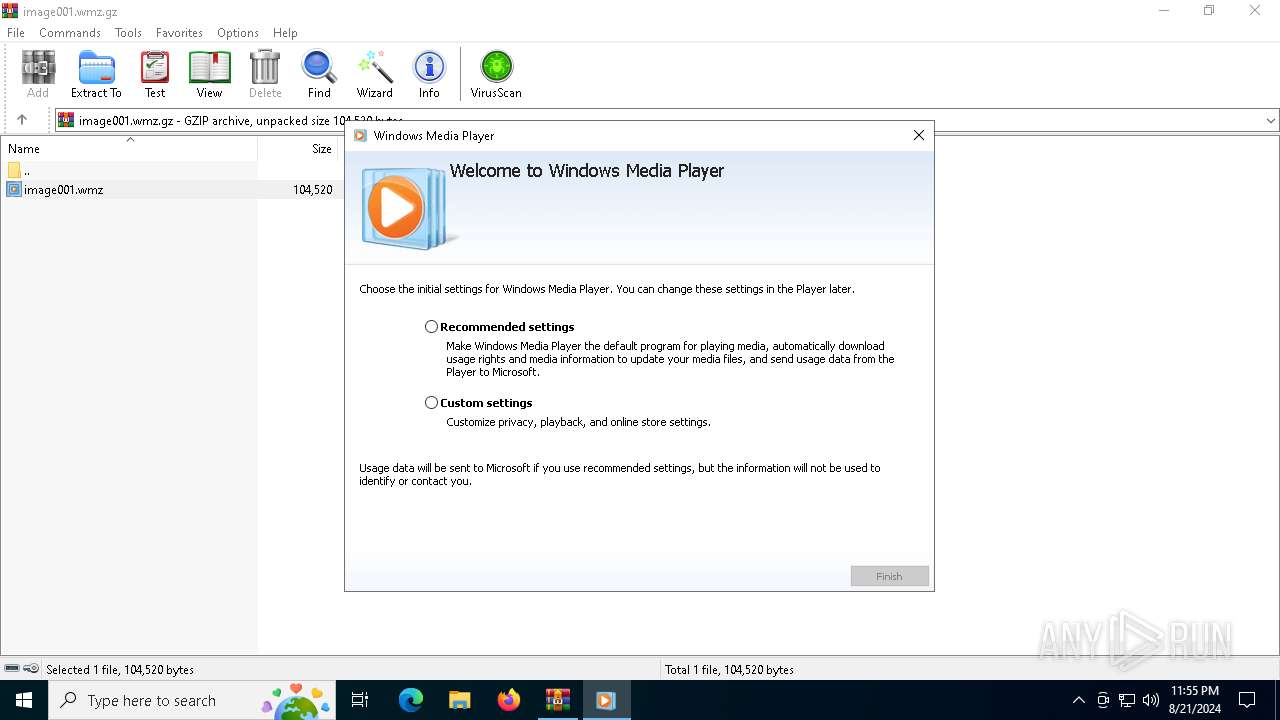
- wmplayer.exe (PID: 6236)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6540)
- wmplayer.exe (PID: 6680)
- setup_wm.exe (PID: 6720)
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Reads the date of Windows installation
- wmplayer.exe (PID: 6680)
- setup_wm.exe (PID: 6720)
Reads Microsoft Outlook installation path
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Reads Internet Explorer settings
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6540)
- OpenWith.exe (PID: 3540)
Checks supported languages
- wmplayer.exe (PID: 6680)
- setup_wm.exe (PID: 6720)
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
- acrobat_sl.exe (PID: 4880)
Reads security settings of Internet Explorer
- unregmp2.exe (PID: 6740)
- unregmp2.exe (PID: 6268)
Process checks computer location settings
- wmplayer.exe (PID: 6680)
- setup_wm.exe (PID: 6720)
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Create files in a temporary directory
- unregmp2.exe (PID: 6740)
Reads the computer name
- wmplayer.exe (PID: 6680)
- setup_wm.exe (PID: 6720)
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Reads Environment values
- setup_wm.exe (PID: 6720)
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Creates files or folders in the user directory
- unregmp2.exe (PID: 6792)
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Reads the machine GUID from the registry
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Process checks Internet Explorer phishing filters
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Checks proxy server information
- wmplayer.exe (PID: 6236)
- wmplayer.exe (PID: 5920)
Reads the software policy settings
- wmplayer.exe (PID: 6236)
Manual execution by a user
- wmplayer.exe (PID: 5920)
- Acrobat.exe (PID: 6676)
Application launched itself
- AcroCEF.exe (PID: 2368)
- AcroCEF.exe (PID: 5124)
- Acrobat.exe (PID: 6676)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 7112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | (none) |
| ModifyDate: | 0000:00:00 00:00:00 |
| ExtraFlags: | Fastest Algorithm |
| OperatingSystem: | NTFS filesystem (NT) |
Total processes
161
Monitored processes
27
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Desktop\image001.wmz" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2272 --field-trial-handle=1328,i,15927217461089853795,8376072212840413140,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2664 --field-trial-handle=1328,i,15927217461089853795,8376072212840413140,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3540 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4048 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2064 --field-trial-handle=1328,i,15927217461089853795,8376072212840413140,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4100 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1728 --field-trial-handle=1328,i,15927217461089853795,8376072212840413140,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4880 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat_sl.exe" | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrobat_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 22.3.20310.0 Modules
| |||||||||||||||
| 5064 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=2632 --field-trial-handle=1328,i,15927217461089853795,8376072212840413140,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5124 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
51 979
Read events
51 443
Write events
504
Delete events
32
Modification events
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\image001.wmz.gz | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\system32\unregmp2.exe,-9916 |
Value: Windows Media Player Skin Package | |||
| (PID) Process: | (6540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | WMP11.AssocFile.WMZ_.wmz |
Value: 0 | |||
Executable files
1
Suspicious files
100
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6792 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | text | |
MD5:5433EAB10C6B5C6D55B7CBD302426A39 | SHA256:23DBF7014E99E93AF5F2760F18EE1370274F06A453145C8D539B66D798DAD131 | |||
| 6792 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSD.XML | text | |
MD5:A9B5DA9AEC61657B32393D96217165F0 | SHA256:9F4611369CF65B33D886489B2486FCA7B1E83E0DC998D35B15B3AA4C8478A28D | |||
| 6792 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\CurrentDatabase_400.wmdb | binary | |
MD5:79AEACC048DB9CA31E1BAF148FFC66C6 | SHA256:9974FC100ABF3300E5EBCAB88D7BA8F66158429E8EBB155F7118AECCC062FFF7 | |||
| 6236 | wmplayer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UTTEYNENAIX5G7RMHMUM.temp | binary | |
MD5:3184F009F78E2BA14FCC9B1F599B3C68 | SHA256:8A1EEC2C08AF6DC66A300F5943CC115F893B745FCB28DFFB3BE0F1177EE068C1 | |||
| 6792 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | xml | |
MD5:90BE2701C8112BEBC6BD58A7DE19846E | SHA256:644FBCDC20086E16D57F31C5BAD98BE68D02B1C061938D2F5F91CBE88C871FBF | |||
| 6792 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\LocalMLS_3.wmdb | binary | |
MD5:21362316FAA6F9B3E30AC2823A6B0428 | SHA256:780704AB0182E023B5C5E8371F170D0F3A9C55BF6EE2957A77060C978F21E00D | |||
| 6236 | wmplayer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\74d7f43c1561fc1e.customDestinations-ms | binary | |
MD5:3184F009F78E2BA14FCC9B1F599B3C68 | SHA256:8A1EEC2C08AF6DC66A300F5943CC115F893B745FCB28DFFB3BE0F1177EE068C1 | |||
| 6236 | wmplayer.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\Sync Playlists\en-US\0000AEDD\02_Music_added_in_the_last_month.wpl | html | |
MD5:907BFC98CE854AE312127C952D8BE0F2 | SHA256:C475DC7423C2AD60F25ADAAC754CD8B68B57FF04F26ECEF78F3E5961B986A324 | |||
| 6236 | wmplayer.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\Sync Playlists\en-US\0000AEDD\04_Music_played_in_the_last_month.wpl | html | |
MD5:F8D3A4CACF055F5EC5C62218EA50D290 | SHA256:201F2170812CF8041964C4D3C5EF539D96ADEBA6A68B69ECAED0AFFE3AE8E25F | |||
| 6740 | unregmp2.exe | C:\Users\admin\AppData\Local\Temp\wmsetup.log | text | |
MD5:2BC477D260709D5B09A688DEC250FC29 | SHA256:4418BB7EBC5BAA169EC6F8569C2E1DC2F071FD19B7B981A84CD0FADAF48FE478 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
39
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2324 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7144 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6676 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
7092 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2992 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2456 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2992 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2324 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2324 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6236 | wmplayer.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |