| File name: | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop |
| Full analysis: | https://app.any.run/tasks/0b2fc90c-f31d-44c9-b04a-d5fd9bbe3ef5 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 14:03:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 96689127593B2EBF0CB989536450EB62 |
| SHA1: | 3D110E6016D2B8A0CE7995DB759296465752F9B7 |
| SHA256: | F8FEA07E8F22B2E5957BDE396B0262353C8378A9EA651E91CB086573D0CB4062 |
| SSDEEP: | 98304:32Pl64jk9xadwIb1aN19xadwO+eobwEfUbkE4o9zSl3Ci:CK/ |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 252.#.exe (PID: 3788)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
Changes the autorun value in the registry
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
SUSPICIOUS
Creates file in the systems drive root
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
Executable content was dropped or overwritten
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
Detected use of alternative data streams (AltDS)
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
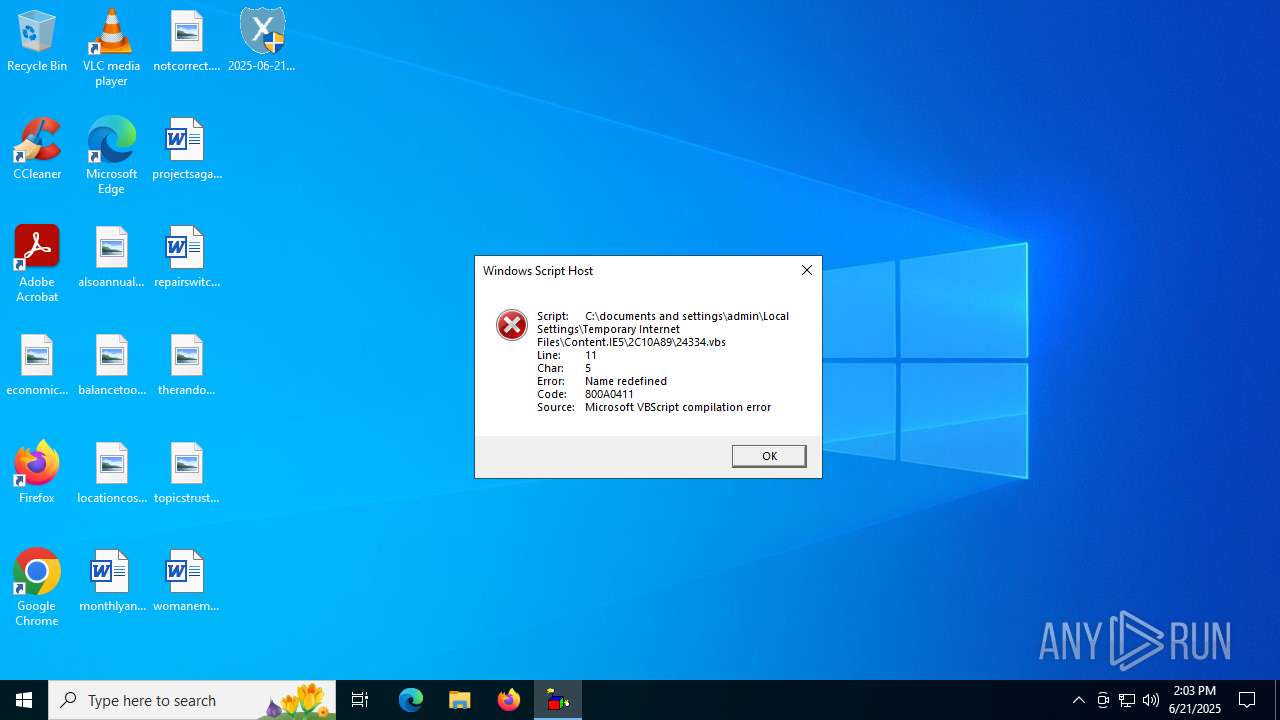
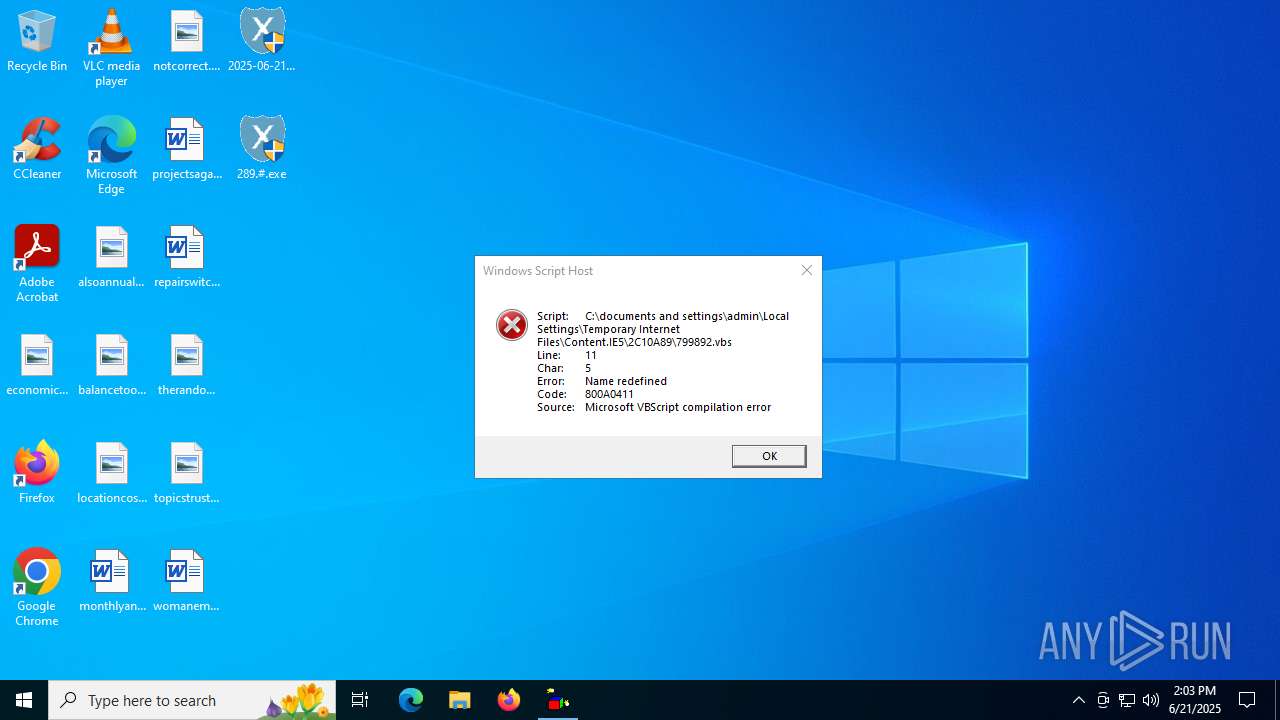
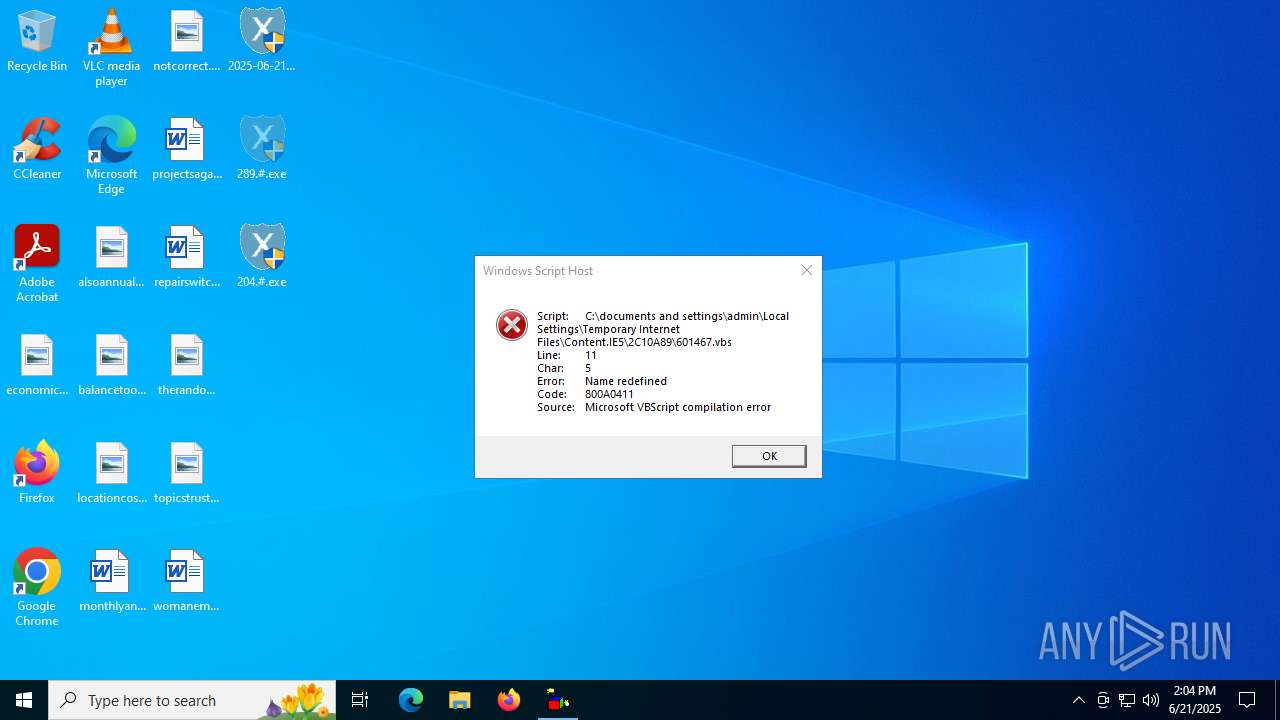
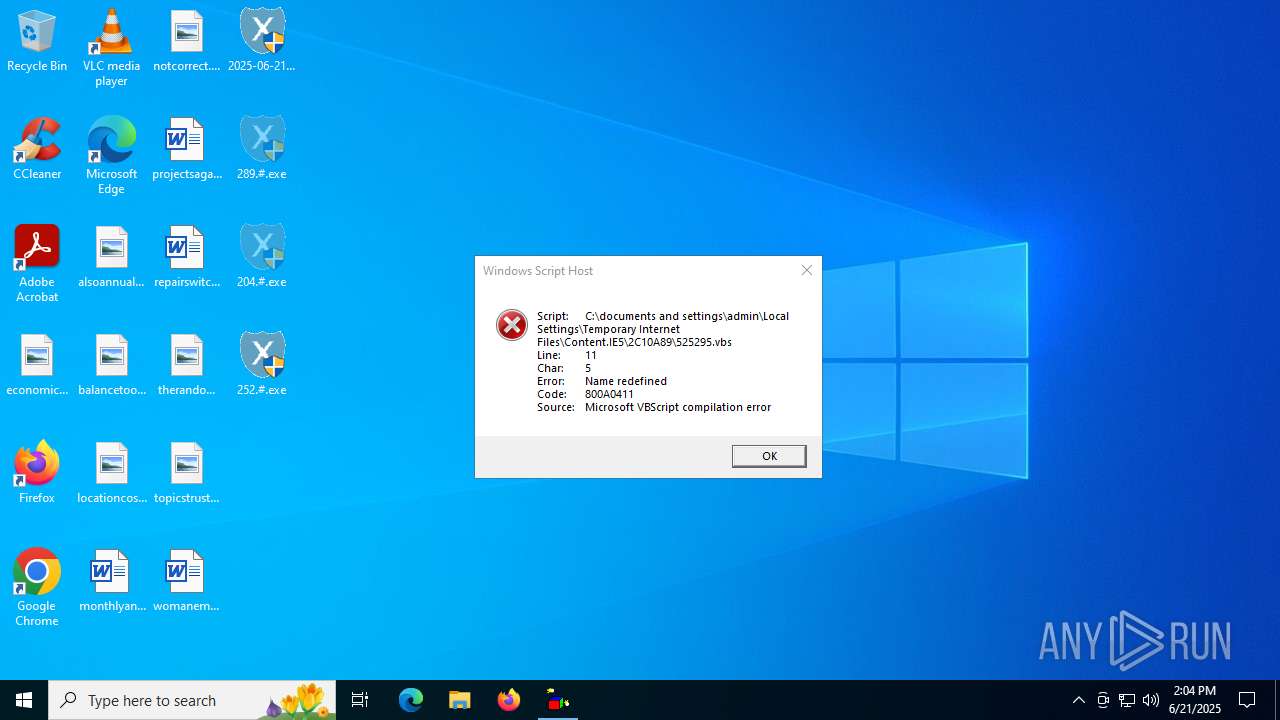
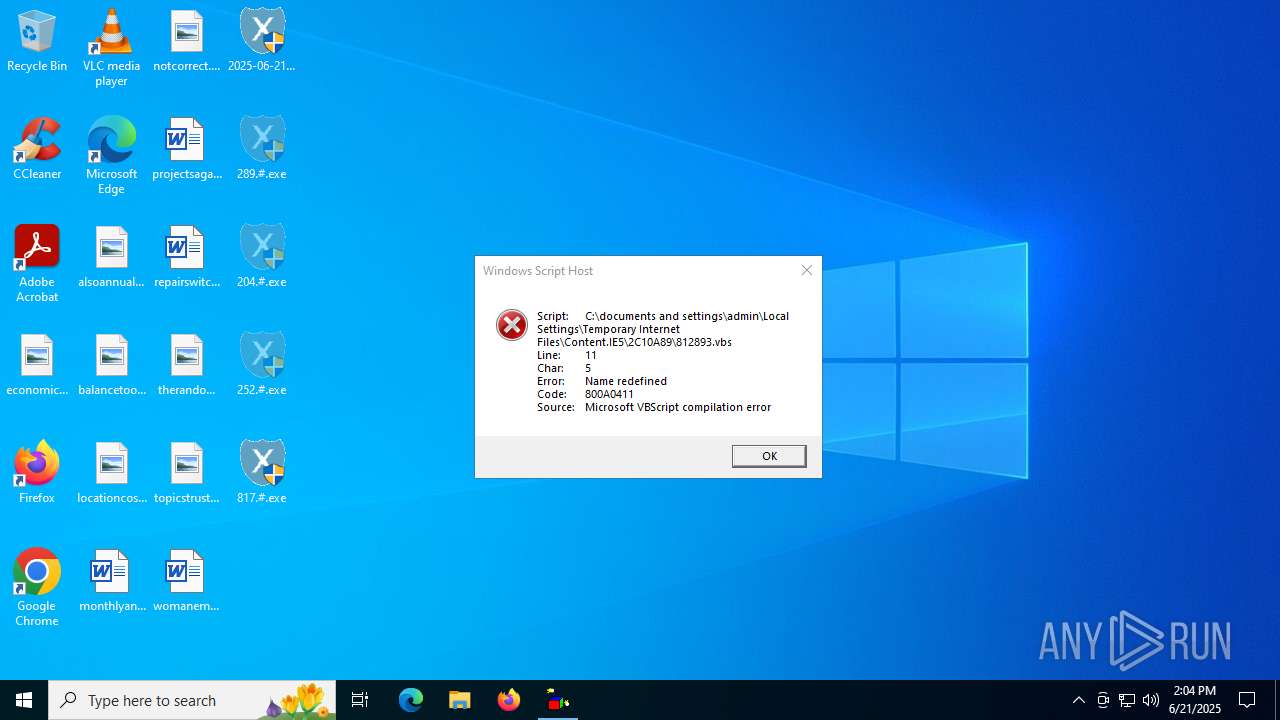
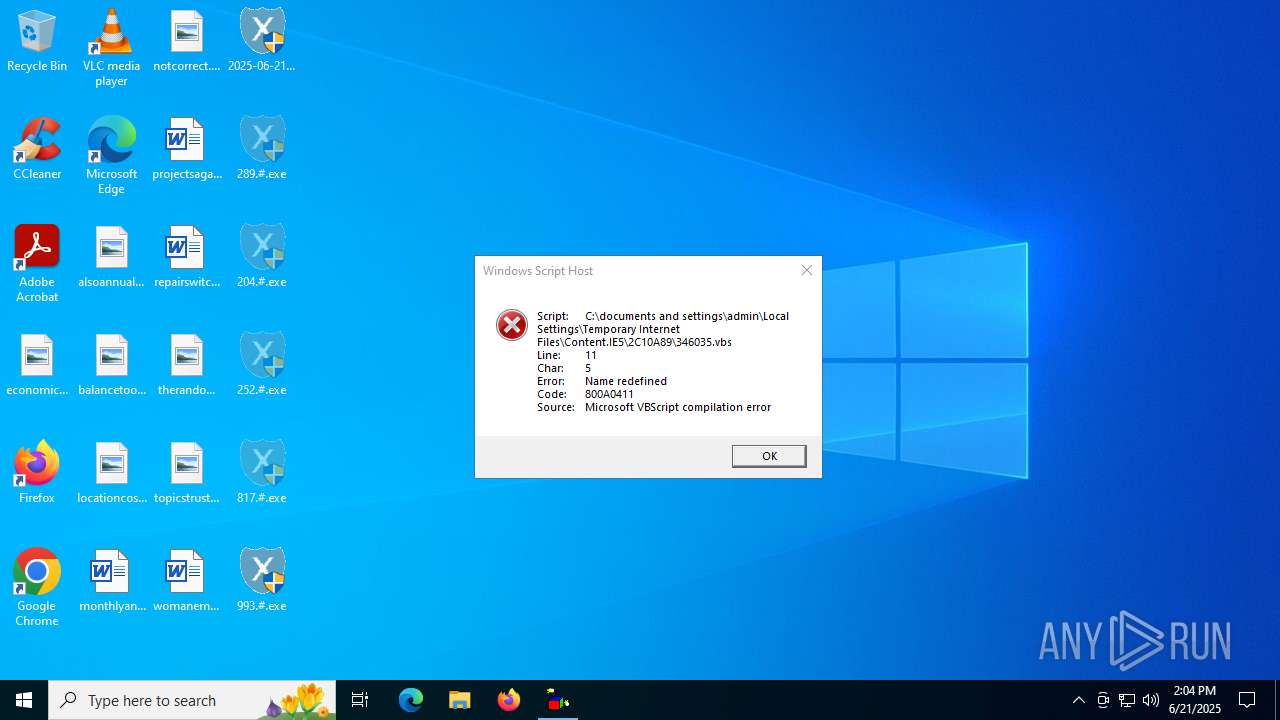
The process executes VB scripts
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 252.#.exe (PID: 3788)
- 204.#.exe (PID: 6268)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
Starts itself from another location
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
The process creates files with name similar to system file names
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 252.#.exe (PID: 3788)
- 204.#.exe (PID: 6268)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
INFO
Create files in a temporary directory
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
Checks supported languages
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
The sample compiled with chinese language support
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
Creates files or folders in the user directory
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 204.#.exe (PID: 6268)
- 289.#.exe (PID: 3048)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
Reads the computer name
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
Launching a file from a Registry key
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 289.#.exe (PID: 3048)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
- 314.#.exe (PID: 4196)
Manual execution by a user
- spfirewall.exe (PID: 1132)
- regsvr32.exe (PID: 6304)
Creates files in the program directory
- 289.#.exe (PID: 3048)
- 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe (PID: 6472)
- 204.#.exe (PID: 6268)
- 252.#.exe (PID: 3788)
- 817.#.exe (PID: 3732)
- 993.#.exe (PID: 5244)
- 192.#.exe (PID: 2524)
Checks proxy server information
- slui.exe (PID: 3724)
Reads the software policy settings
- slui.exe (PID: 3724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (42.1) |
|---|---|---|
| .exe | | | InstallShield setup (22.1) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (16) |
| .exe | | | Win64 Executable (generic) (14.1) |
| .exe | | | Win32 Executable (generic) (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:09:07 11:28:55+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 40960 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x173c |
| OSVersion: | 4 |
| ImageVersion: | 1.1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.0.13 |
| ProductVersionNumber: | 1.1.0.13 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| Comments: | Microsoft Firewall Installer 12th Edition |
| CompanyName: | XC Microsoft |
| FileDescription: | Microsoft Firewall Installer - Protect all of your files |
| LegalCopyright: | Microsoft (C) 2007 , All rights reserved. |
| LegalTrademarks: | Microsoft Firewall Installer |
| ProductName: | Microsoft Firewall Installer |
| FileVersion: | 1.01.0013 |
| ProductVersion: | 1.01.0013 |
| InternalName: | Firewall |
| OriginalFileName: | Firewall.exe |
Total processes
162
Monitored processes
28
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
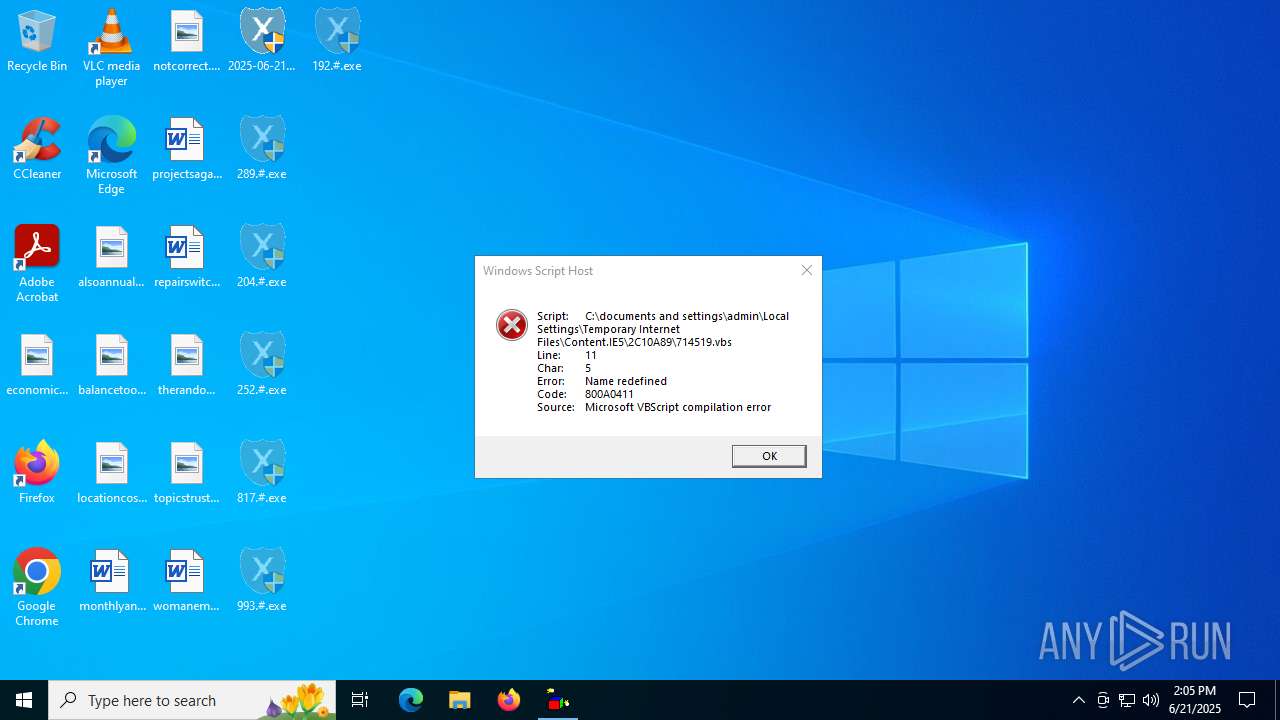
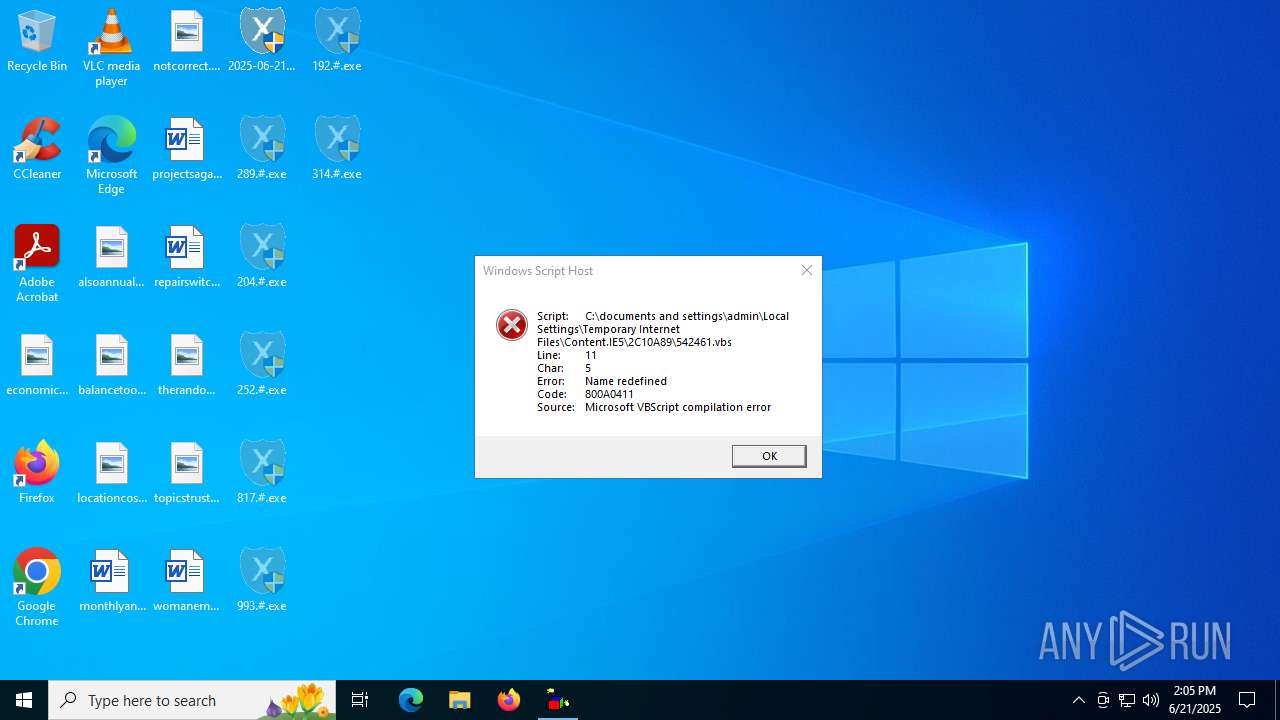
| 316 | wscript.exe "C:\documents and settings\admin\Local Settings\Temporary Internet Files\Content.IE5\2C10A89\542461.vbs" | C:\Windows\SysWOW64\wscript.exe | — | 314.#.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1036 | wscript.exe "C:\documents and settings\admin\Local Settings\Temporary Internet Files\Content.IE5\2C10A89\714519.vbs" | C:\Windows\SysWOW64\wscript.exe | — | 192.#.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1132 | C:\10a0699fa37928d39c\spfirewall.exe | C:\10a0699fa37928d39c\spfirewall.exe | — | explorer.exe | |||||||||||
User: admin Company: XC Microsoft Integrity Level: MEDIUM Description: Microsoft Firewall Installer - Protect all of your files Exit code: 3221226540 Version: 1.01.0013 Modules
| |||||||||||||||
| 1472 | regsvr32.exe /s scrrun.dll | C:\Windows\SysWOW64\regsvr32.exe | — | 204.#.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2220 | regsvr32.exe /s scrrun.dll | C:\Windows\SysWOW64\regsvr32.exe | — | 314.#.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2524 | C:\Users\admin\Desktop\192.#.exe | C:\Users\admin\Desktop\192.#.exe | 993.#.exe | ||||||||||||
User: admin Company: XC Microsoft Integrity Level: HIGH Description: Microsoft Firewall Installer - Protect all of your files Version: 1.01.0013 Modules
| |||||||||||||||
| 3048 | C:\Users\admin\Desktop\289.#.exe | C:\Users\admin\Desktop\289.#.exe | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | ||||||||||||
User: admin Company: XC Microsoft Integrity Level: HIGH Description: Microsoft Firewall Installer - Protect all of your files Version: 1.01.0013 Modules
| |||||||||||||||
| 3112 | wscript.exe "C:\documents and settings\admin\Local Settings\Temporary Internet Files\Content.IE5\2C10A89\346035.vbs" | C:\Windows\SysWOW64\wscript.exe | — | 993.#.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3724 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | C:\Users\admin\Desktop\817.#.exe | C:\Users\admin\Desktop\817.#.exe | 252.#.exe | ||||||||||||
User: admin Company: XC Microsoft Integrity Level: HIGH Description: Microsoft Firewall Installer - Protect all of your files Version: 1.01.0013 Modules
| |||||||||||||||
Total events
5 299
Read events
5 187
Write events
16
Delete events
96
Modification events
| (PID) Process: | (6472) 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | FileProtector |
Value: C:\10a0699fa37928d39c\spfirewall.exe | |||
| (PID) Process: | (6472) 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | RegSCRLib |
Value: regsvr32.exe /s scrrun.dll | |||
| (PID) Process: | (6772) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Scripting.Dictionary |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6772) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Scripting.FileSystemObject |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6772) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Scripting.Encoder |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6772) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\HTML.HostEncode |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6772) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\ASP.HostEncode |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6772) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\JSFile.HostEncode |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6772) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBSFile.HostEncode |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6772) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\htmlfile\ScriptHostEncode |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
414
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6472 | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | C:\10a0699fa37928d39c\spfirewall.exe | executable | |
MD5:96689127593B2EBF0CB989536450EB62 | SHA256:F8FEA07E8F22B2E5957BDE396B0262353C8378A9EA651E91CB086573D0CB4062 | |||
| 3048 | 289.#.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\2C10A89\799892.vbs | text | |
MD5:65D2A4211DB5B12673D7BD69A3DE8712 | SHA256:8F489BDE1B497F3E9DC14588E46A61D533C4962351B42765504ED6FA4BBC1D1F | |||
| 6472 | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\2C10A89\24334.vbs | text | |
MD5:65D2A4211DB5B12673D7BD69A3DE8712 | SHA256:8F489BDE1B497F3E9DC14588E46A61D533C4962351B42765504ED6FA4BBC1D1F | |||
| 6472 | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\SingleClientServicesUpdater.exe$ | executable | |
MD5:96689127593B2EBF0CB989536450EB62 | SHA256:F8FEA07E8F22B2E5957BDE396B0262353C8378A9EA651E91CB086573D0CB4062 | |||
| 6268 | 204.#.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\2C10A89\601467.vbs | text | |
MD5:65D2A4211DB5B12673D7BD69A3DE8712 | SHA256:8F489BDE1B497F3E9DC14588E46A61D533C4962351B42765504ED6FA4BBC1D1F | |||
| 6472 | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\SingleClientServicesUpdater.exe | executable | |
MD5:96689127593B2EBF0CB989536450EB62 | SHA256:F8FEA07E8F22B2E5957BDE396B0262353C8378A9EA651E91CB086573D0CB4062 | |||
| 6472 | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\SingleClientServicesUpdater.exe$ | executable | |
MD5:96689127593B2EBF0CB989536450EB62 | SHA256:F8FEA07E8F22B2E5957BDE396B0262353C8378A9EA651E91CB086573D0CB4062 | |||
| 6472 | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe$ | executable | |
MD5:96689127593B2EBF0CB989536450EB62 | SHA256:F8FEA07E8F22B2E5957BDE396B0262353C8378A9EA651E91CB086573D0CB4062 | |||
| 6472 | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\SingleClientServicesUpdater.exe | executable | |
MD5:96689127593B2EBF0CB989536450EB62 | SHA256:F8FEA07E8F22B2E5957BDE396B0262353C8378A9EA651E91CB086573D0CB4062 | |||
| 6472 | 2025-06-21_96689127593b2ebf0cb989536450eb62_amadey_elex_hijackloader_smoke-loader_stop.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\Browser\WCChromeExtn\WCChromeNativeMessagingHost.exe | executable | |
MD5:D20AA01E291BC360B2D6991CB133A07F | SHA256:8226141290870755BDA7CAA6C5A1481DB2D065A529E10AA5E48F86A9A0182233 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
42
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4868 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.65:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.76:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 400 | 20.190.160.65:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 200 | 20.190.160.130:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4868 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4868 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |