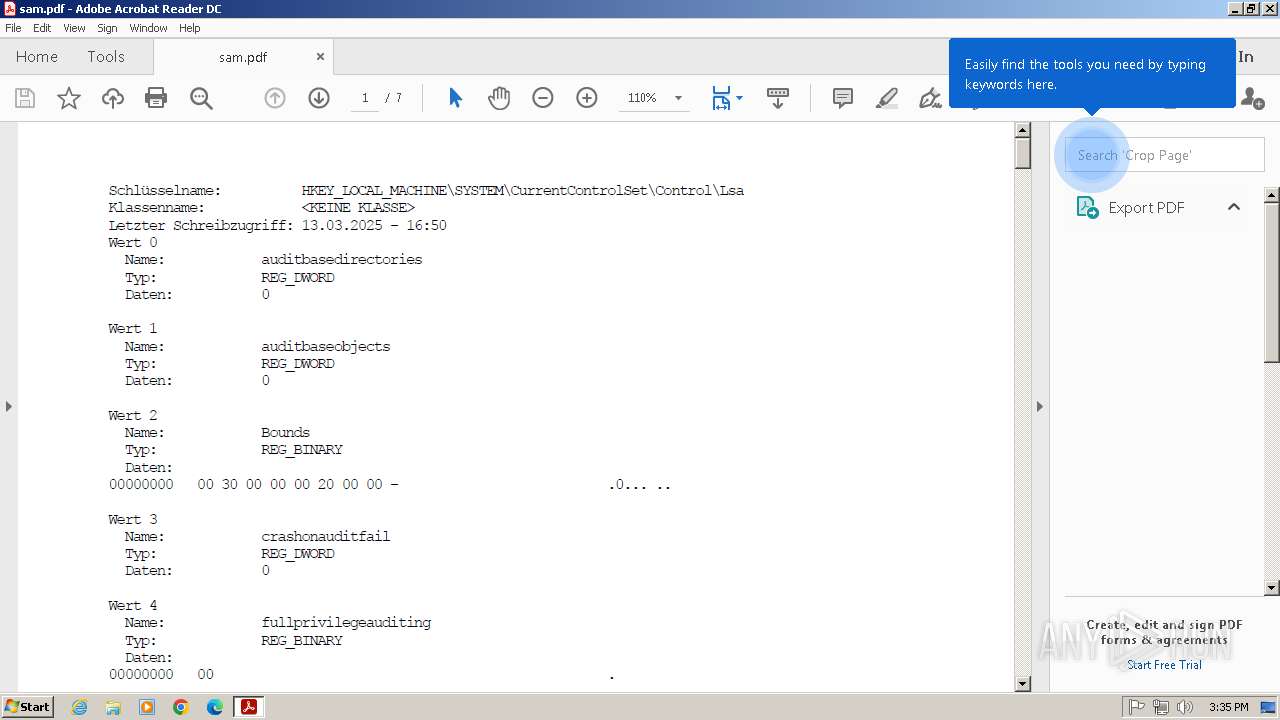
| File name: | sam.pdf |
| Full analysis: | https://app.any.run/tasks/055d4a10-4188-4b00-a48d-3090cd167a6a |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 14:35:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.7, 7 page(s) |
| MD5: | AD252DB34249D87B4AFA70D03512C211 |
| SHA1: | 9E59391D6C905EF4F0FE2D34EF5C2E30C859B360 |
| SHA256: | F8DDF0FBE9795B0F8ECE4CD30D747936FE05E0A52864B8522304CBA34E43FA74 |
| SSDEEP: | 3072:7R4deiNFuM8ZQ227gs4RQrIP8VO0pRll3Qo7x3WJ3oL2jbo:CnNr8ORgs4RwIP8VO0pRl1fNvH |
MALICIOUS
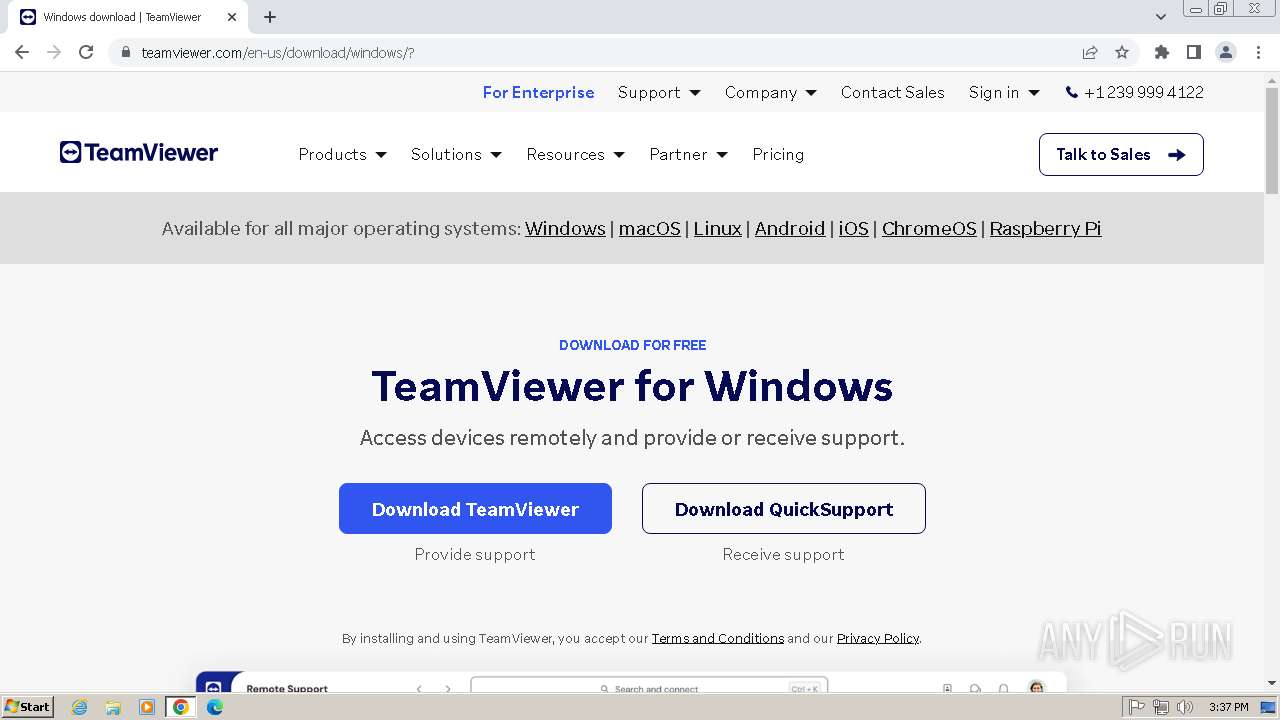
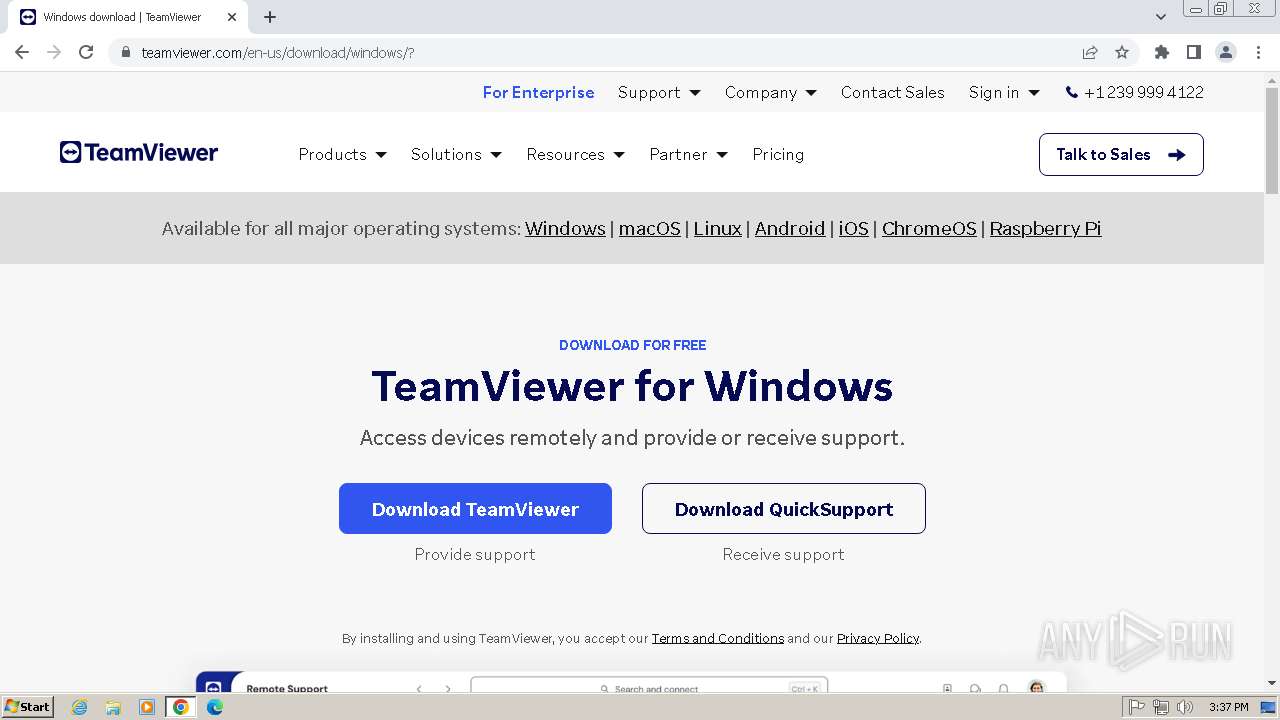
TEAMVIEWER has been detected (SURICATA)
- chrome.exe (PID: 3092)
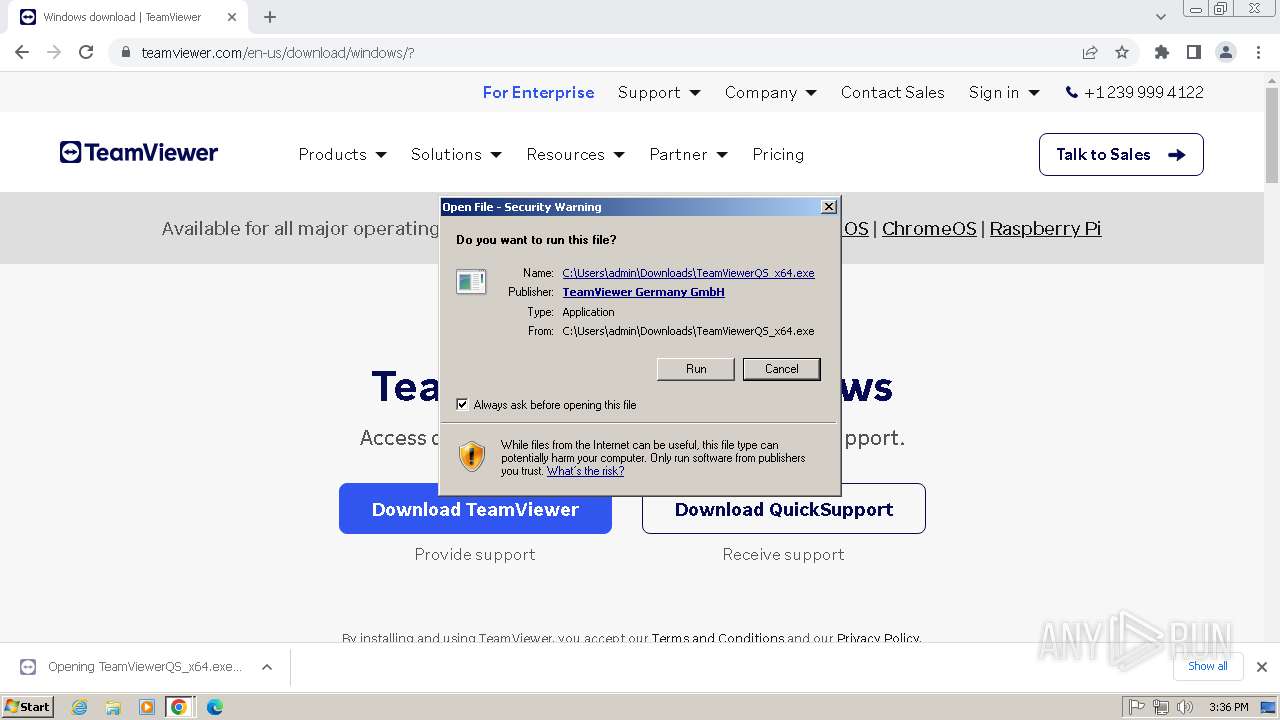
Executing a file with an untrusted certificate
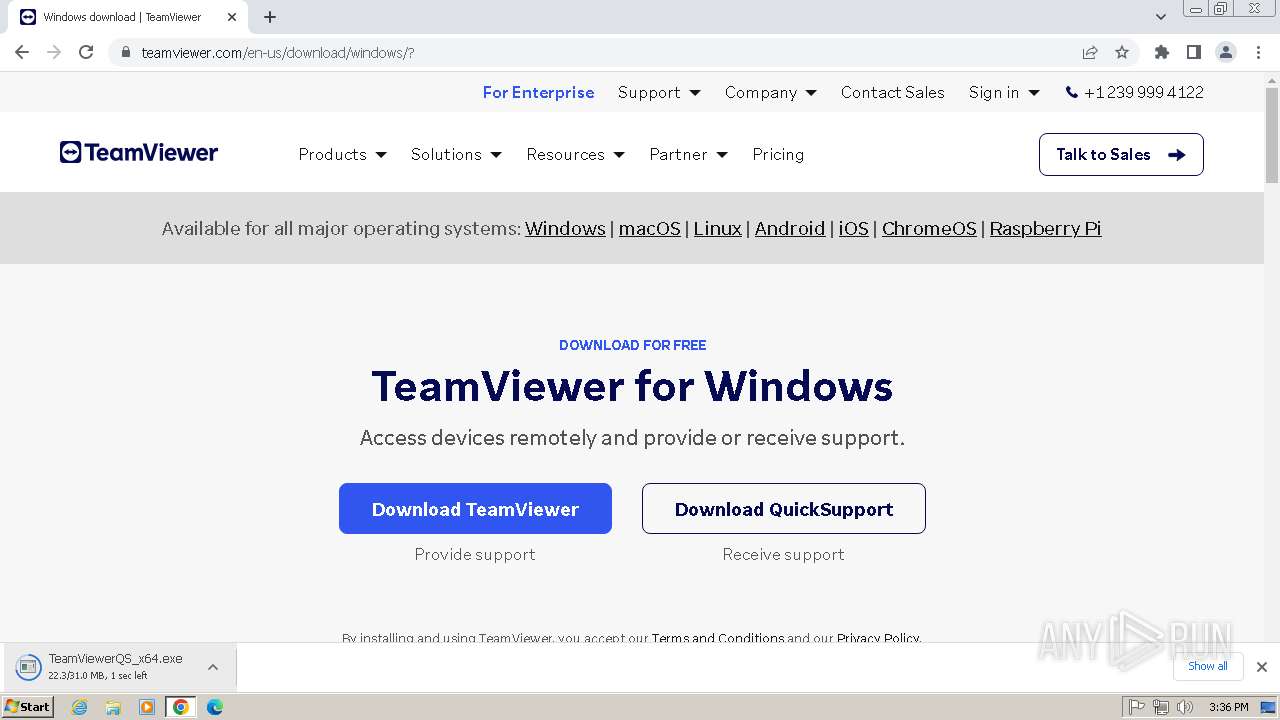
- TeamViewerQS_x64.exe (PID: 3976)
SUSPICIOUS
Creates file in the systems drive root
- AcroRd32.exe (PID: 1744)
There is functionality for taking screenshot (YARA)
- AcroRd32.exe (PID: 1744)
- RdrCEF.exe (PID: 1784)
- TeamViewerQS_x64.exe (PID: 3976)
The process creates files with name similar to system file names
- TeamViewerQS_x64.exe (PID: 3976)
Drops 7-zip archiver for unpacking
- TeamViewerQS_x64.exe (PID: 3976)
Malware-specific behavior (creating "System.dll" in Temp)
- TeamViewerQS_x64.exe (PID: 3976)
Reads security settings of Internet Explorer
- TeamViewerQS_x64.exe (PID: 3976)
Executable content was dropped or overwritten
- TeamViewerQS_x64.exe (PID: 3976)
Reads the Internet Settings
- TeamViewerQS_x64.exe (PID: 3976)
INFO
An automatically generated document
- AcroRd32.exe (PID: 2840)
Application launched itself
- AcroRd32.exe (PID: 2840)
- RdrCEF.exe (PID: 1784)
- chrome.exe (PID: 3272)
Reads Microsoft Office registry keys
- AcroRd32.exe (PID: 1744)
Executable content was dropped or overwritten
- chrome.exe (PID: 3272)
- chrome.exe (PID: 3092)
- chrome.exe (PID: 3952)
Manual execution by a user
- chrome.exe (PID: 3272)
The sample compiled with english language support
- chrome.exe (PID: 3272)
- chrome.exe (PID: 3092)
- TeamViewerQS_x64.exe (PID: 3976)
- chrome.exe (PID: 3952)
TeamViewer related mutex has been found
- TeamViewerQS_x64.exe (PID: 3976)
TEAMVIEWER has been detected
- TeamViewerQS_x64.exe (PID: 3976)
Checks supported languages
- TeamViewerQS_x64.exe (PID: 3976)
Reads the computer name
- TeamViewerQS_x64.exe (PID: 3976)
Create files in a temporary directory
- TeamViewerQS_x64.exe (PID: 3976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.7 |
|---|---|
| Linearized: | No |
| Author: | Sigma Skibidi Alpha |
| CreateDate: | 2025:03:13 16:55:43+01:00 |
| ModifyDate: | 2025:03:13 16:55:43+01:00 |
| Producer: | Microsoft: Print To PDF |
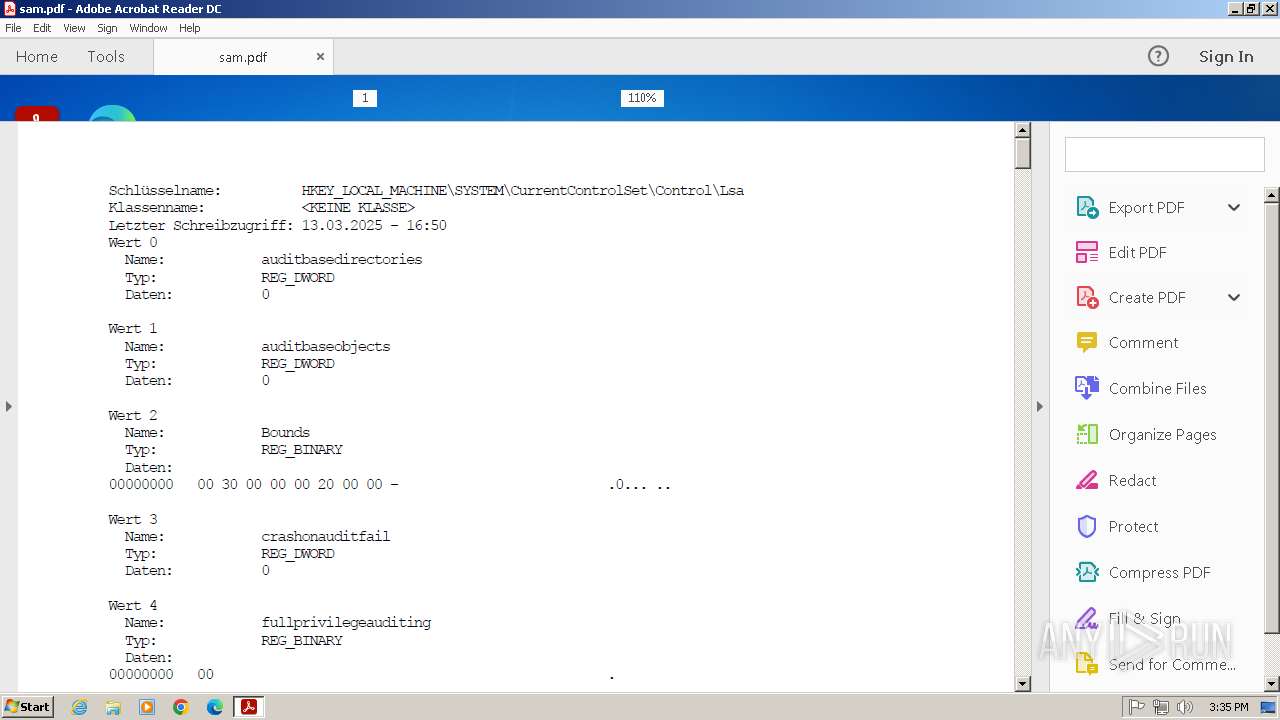
| Title: | Registrierungs-Editor |
| PageCount: | 7 |
Total processes
80
Monitored processes
42
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=1032 --field-trial-handle=1216,i,6808676742862373878,17225747423876220213,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3700 --field-trial-handle=1216,i,6808676742862373878,17225747423876220213,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4596 --field-trial-handle=1216,i,6808676742862373878,17225747423876220213,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2124 --field-trial-handle=1216,i,6808676742862373878,17225747423876220213,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=1984 --field-trial-handle=1216,i,6808676742862373878,17225747423876220213,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1416 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1168,17619609545423237218,15589055435602250076,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=14291837068444250226 --mojo-platform-channel-handle=1280 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1500 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1168,17619609545423237218,15589055435602250076,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=11792298926512151365 --mojo-platform-channel-handle=1280 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1648 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1168,17619609545423237218,15589055435602250076,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15046127602450747766 --renderer-client-id=6 --mojo-platform-channel-handle=1480 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\Desktop\sam.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1784 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
26 229
Read events
25 956
Write events
245
Delete events
28
Modification events
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | aDefaultRHPViewModeL |
Value: Expanded | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | iNumReaderLaunches |
Value: 6 | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FillSign |
| Operation: | write | Name: | uFillSignVariantTrackingTime |
Value: | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ToolsSearch |
| Operation: | write | Name: | iSearchHintIndex |
Value: 0 | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement\cWindowsCurrent |
| Operation: | write | Name: | iWinCount |
Value: 1 | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement |
| Operation: | write | Name: | bNormalExit |
Value: 0 | |||
| (PID) Process: | (1744) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement\cWindowsCurrent\cWin0\cTab0\cPathInfo |
| Operation: | write | Name: | sDI |
Value: 2F432F55736572732F61646D696E2F4465736B746F702F73616D2E70646600 | |||
Executable files
60
Suspicious files
330
Text files
46
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1784 | RdrCEF.exe | — | ||
MD5:— | SHA256:— | |||
| 1784 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8e417e79df3bf0e9_0 | binary | |
MD5:40A18DCD8DD06D946896C316AFDDAE36 | SHA256:F2E303421E01BEC70EEBDDE8477D8105F40D74FEC619857E3A00278442B6970E | |||
| 1744 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ConnectorIcons\icon-250419143512Z-190.bmp | image | |
MD5:A8595C11B03528253DAF0A43386B26F4 | SHA256:3AE53149DF3EE1AE2EDF031205F4DF8177C8B957865F1AA9683E8D6F2F3C4F4F | |||
| 1784 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old | text | |
MD5:5705BEF2F423E8D5EF921B2CBEE16FB9 | SHA256:154DF2B4012DEAA86794EF8A0C44FB435615A3143AA3336EA79D2A9544C14900 | |||
| 1784 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:F8D8A987C4E8E6AD2936357C0B392EA7 | SHA256:E76B27C2D372AC4BD12F70D0F6760C7DDC9B6ABE73104BCD53E8AAF9EAE0C940 | |||
| 1744 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 1784 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:627546620709E2A43C796B157A91CC80 | SHA256:B6A8EB54D60F8303DD5D6269BCE24470FDBAF6EB6D11657CF5DD472D0FDF0E04 | |||
| 1784 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\92c56fa2a6c4d5ba_0 | binary | |
MD5:94703E63C31D61D8C6283CF5FE3B9A6E | SHA256:8868A87A6F7ABD93D5794A0EEE2F9163ADD628316DF09D8F5D4A857F60737D93 | |||
| 1784 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:B45CA906ECE3BAACD2A17DC8C2245AD2 | SHA256:098AB4482EB1EB173995A1DBF1BC298715D500EA80B2A80CA216166701C4BE39 | |||
| 1784 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8c84d92a9dbce3e0_0 | binary | |
MD5:19A8B00D40331388F70CA524AE466F44 | SHA256:3DDD705D0AC9103186A44153357E007736F0808F01717421B92D113D1B1918AA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
143
DNS requests
192
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2840 | AcroRd32.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?62ef0279b4e2d3c9 | unknown | — | — | whitelisted |
2840 | AcroRd32.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f7549212f22f59d2 | unknown | — | — | whitelisted |
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acvebl5hyowh6yyy3wmoaw5wbfpa_4.10.2830.100/oimompecagnajdejgnnjijobebaeigek_4.10.2830.100_win32_acmfn7n2mz6vs4wnlypsmq4uakaq.crx3 | unknown | — | — | whitelisted |
2840 | AcroRd32.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acvebl5hyowh6yyy3wmoaw5wbfpa_4.10.2830.100/oimompecagnajdejgnnjijobebaeigek_4.10.2830.100_win32_acmfn7n2mz6vs4wnlypsmq4uakaq.crx3 | unknown | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acvebl5hyowh6yyy3wmoaw5wbfpa_4.10.2830.100/oimompecagnajdejgnnjijobebaeigek_4.10.2830.100_win32_acmfn7n2mz6vs4wnlypsmq4uakaq.crx3 | unknown | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acvebl5hyowh6yyy3wmoaw5wbfpa_4.10.2830.100/oimompecagnajdejgnnjijobebaeigek_4.10.2830.100_win32_acmfn7n2mz6vs4wnlypsmq4uakaq.crx3 | unknown | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acvebl5hyowh6yyy3wmoaw5wbfpa_4.10.2830.100/oimompecagnajdejgnnjijobebaeigek_4.10.2830.100_win32_acmfn7n2mz6vs4wnlypsmq4uakaq.crx3 | unknown | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acvebl5hyowh6yyy3wmoaw5wbfpa_4.10.2830.100/oimompecagnajdejgnnjijobebaeigek_4.10.2830.100_win32_acmfn7n2mz6vs4wnlypsmq4uakaq.crx3 | unknown | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acvebl5hyowh6yyy3wmoaw5wbfpa_4.10.2830.100/oimompecagnajdejgnnjijobebaeigek_4.10.2830.100_win32_acmfn7n2mz6vs4wnlypsmq4uakaq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2840 | AcroRd32.exe | 2.16.168.103:443 | acroipm2.adobe.com | Akamai International B.V. | RU | whitelisted |
1784 | RdrCEF.exe | 95.101.148.135:443 | armmf.adobe.com | Akamai International B.V. | NL | whitelisted |
1784 | RdrCEF.exe | 2.19.104.203:443 | geo2.adobe.com | AKAMAI-AS | DE | whitelisted |
2840 | AcroRd32.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2840 | AcroRd32.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1784 | RdrCEF.exe | 52.22.41.97:443 | p13n.adobe.io | AMAZON-AES | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3092 | chrome.exe | Misc activity | ET REMOTE_ACCESS TeamViewer RMM Domain (teamviewer .com) in DNS Lookup |