| File name: | AgentSetup_British+Business+Bank.exe |
| Full analysis: | https://app.any.run/tasks/85bad972-7707-4c37-9815-73501fea8616 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2024, 14:08:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | BC6461C94630D414E60340AD9ED8FF00 |
| SHA1: | 1E64C269DC7147C313A4E01C3B46DA82F0DB3C9B |
| SHA256: | F8D2BB2A7E4CAD97EDACE0AED665C4F948E721173BD92A0022FD81995DE1F693 |
| SSDEEP: | 98304:LAE6WTv7klWurdCLhMqhlNnxQPMtIwNpwlU/trYbvvGRC68a3pjyUkeqACWll+PC:fOBZLMjaj9Q/uYMg3sA |
MALICIOUS
Drops the executable file immediately after the start
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- RMM.WebRemote.exe (PID: 2848)
- AEMAgent.exe (PID: 1936)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
- CagService.exe (PID: 2036)
Changes the autorun value in the registry
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
Creates a writable file in the system directory
- CagService.exe (PID: 2036)
Registers / Runs the DLL via REGSVR32.EXE
- CagService.exe (PID: 2036)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
The process creates files with name similar to system file names
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- CagService.exe (PID: 2036)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
Executable content was dropped or overwritten
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- CagService.exe (PID: 2036)
- AEMAgent.exe (PID: 1936)
- RMM.WebRemote.exe (PID: 2848)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
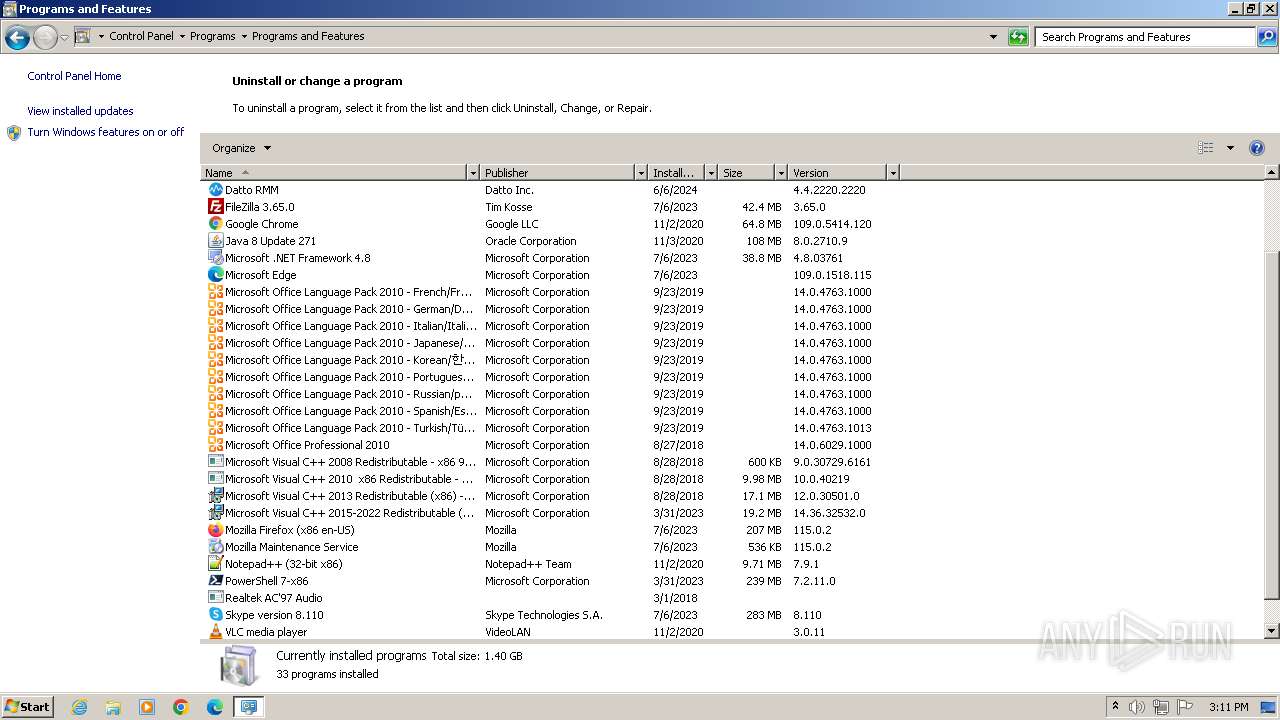
Process drops legitimate windows executable
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- CagService.exe (PID: 2036)
- AEMAgent.exe (PID: 1936)
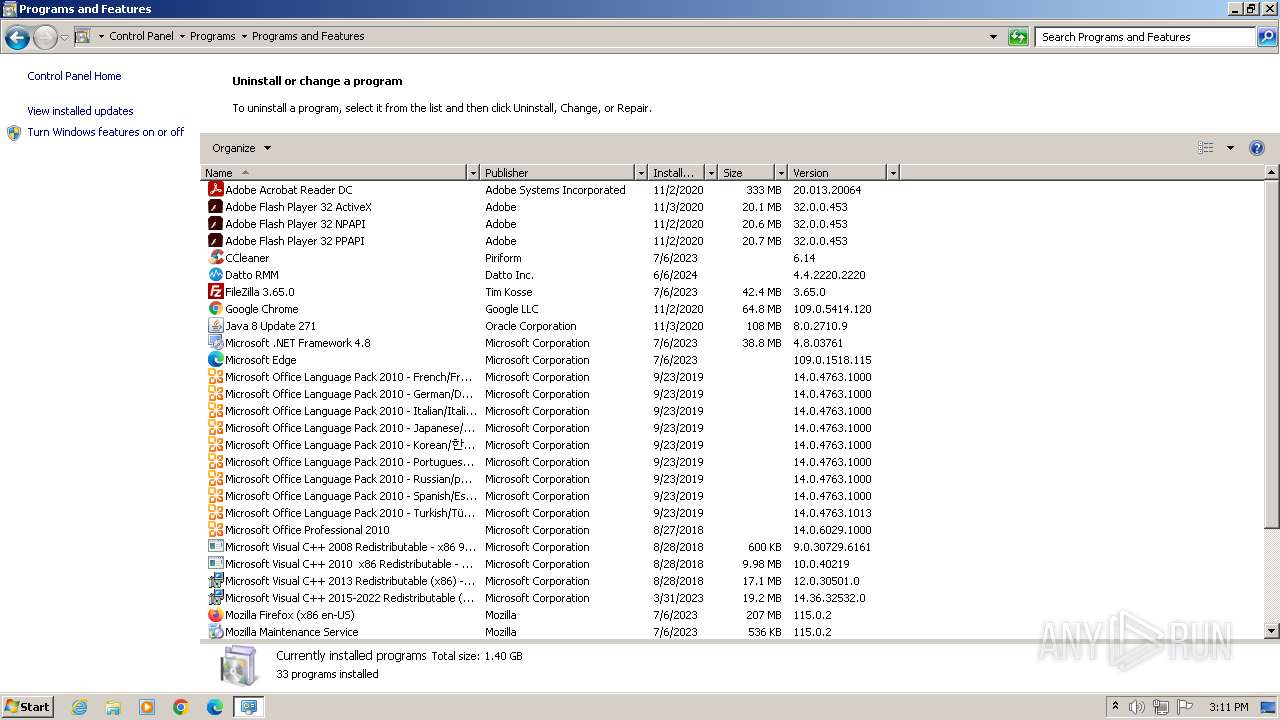
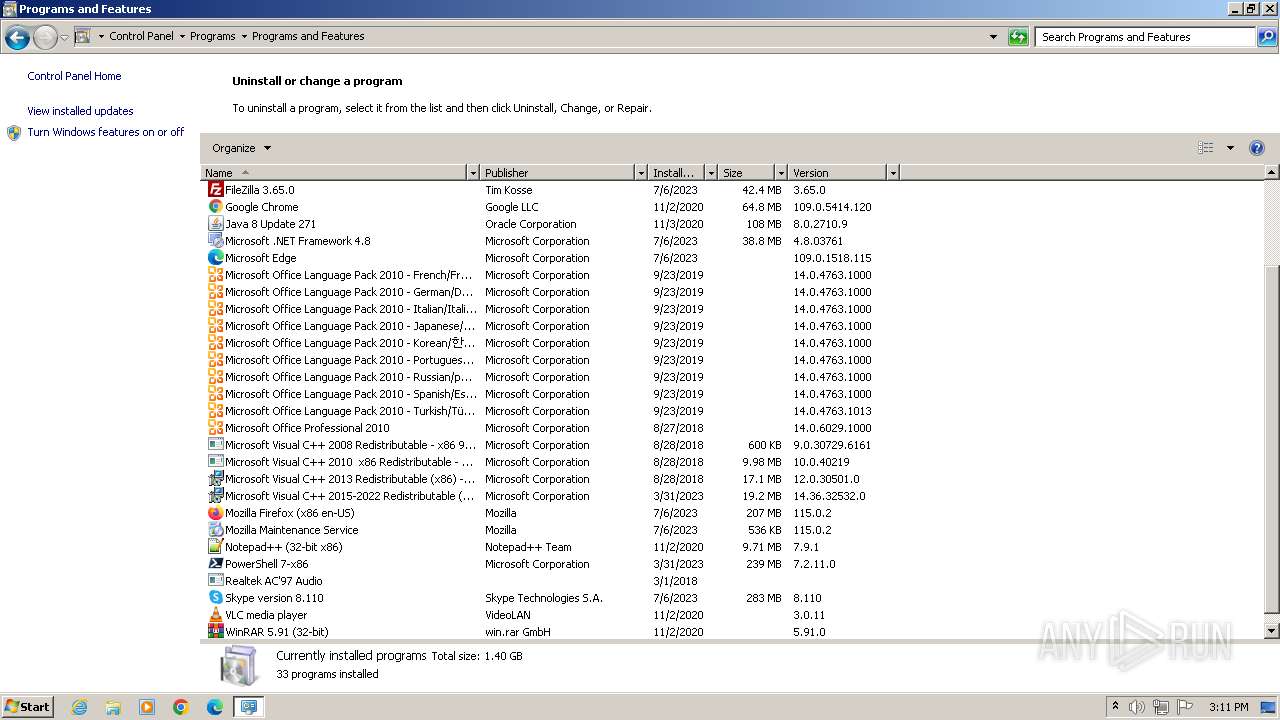
Creates a software uninstall entry
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- CagService.exe (PID: 2036)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
Executes as Windows Service
- CagService.exe (PID: 2036)
Reads the Internet Settings
- Gui.exe (PID: 1292)
Reads security settings of Internet Explorer
- Gui.exe (PID: 1292)
- CagService.exe (PID: 2036)
Checks Windows Trust Settings
- Gui.exe (PID: 1292)
Reads settings of System Certificates
- Gui.exe (PID: 1292)
Creates or modifies Windows services
- CagService.exe (PID: 2036)
Searches for installed software
- CagService.exe (PID: 2036)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1660)
The process drops C-runtime libraries
- CagService.exe (PID: 2036)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- AEMAgent.exe (PID: 1936)
- RMM.WebRemote.exe (PID: 2848)
Adds/modifies Windows certificates
- AEMAgent.exe (PID: 1936)
Uses NETSH.EXE to add a firewall rule or allowed programs
- AEMAgent.exe (PID: 1936)
- RMM.WebRemote.exe (PID: 2848)
Uses WMIC.EXE
- cmd.exe (PID: 3836)
- cmd.exe (PID: 3592)
- cmd.exe (PID: 3600)
- cmd.exe (PID: 3880)
- cmd.exe (PID: 3544)
- cmd.exe (PID: 4044)
- cmd.exe (PID: 4048)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 1848)
- cmd.exe (PID: 1964)
- cmd.exe (PID: 3712)
- cmd.exe (PID: 2484)
- cmd.exe (PID: 1996)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 1064)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 2436)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 2008)
- cmd.exe (PID: 1604)
- cmd.exe (PID: 3572)
- cmd.exe (PID: 1948)
- cmd.exe (PID: 2348)
- cmd.exe (PID: 1644)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 3040)
- cmd.exe (PID: 2416)
- cmd.exe (PID: 2456)
- cmd.exe (PID: 3108)
- cmd.exe (PID: 952)
Found strings related to reading or modifying Windows Defender settings
- AEMAgent.exe (PID: 1936)
Starts CMD.EXE for commands execution
- AEMAgent.exe (PID: 1936)
INFO
Checks supported languages
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- wmpnscfg.exe (PID: 1796)
- AEMAgent.exe (PID: 2124)
- AEMAgent.exe (PID: 1936)
- RMM.WebRemote.exe (PID: 2848)
- Gui.exe (PID: 2268)
- Gui.exe (PID: 1980)
- CagService.exe (PID: 2036)
- Gui.exe (PID: 1292)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
- Gui.exe (PID: 2356)
- AEMAgent.exe (PID: 1612)
Reads Environment values
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- CagService.exe (PID: 2036)
- AEMAgent.exe (PID: 1936)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
Reads the computer name
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- CagService.exe (PID: 2036)
- wmpnscfg.exe (PID: 1796)
- AEMAgent.exe (PID: 1936)
- RMM.WebRemote.exe (PID: 2848)
- Gui.exe (PID: 2268)
- Gui.exe (PID: 1980)
- Gui.exe (PID: 1292)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
- Gui.exe (PID: 2356)
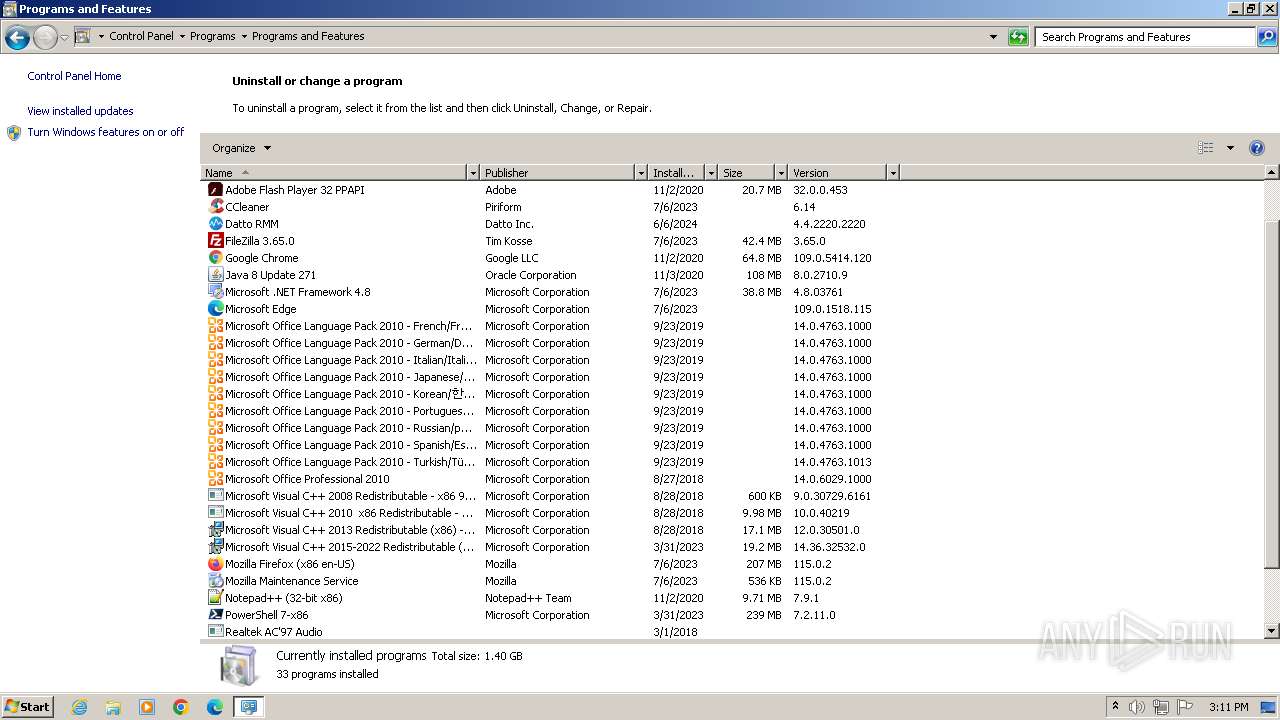
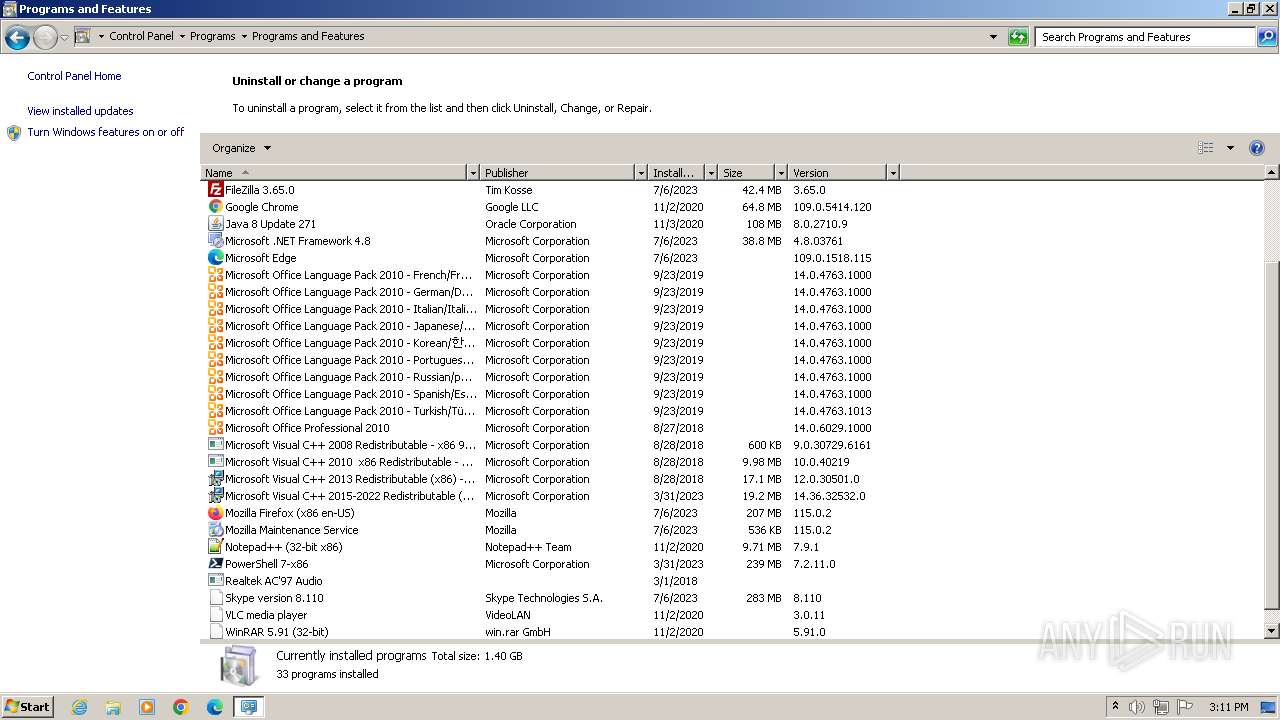
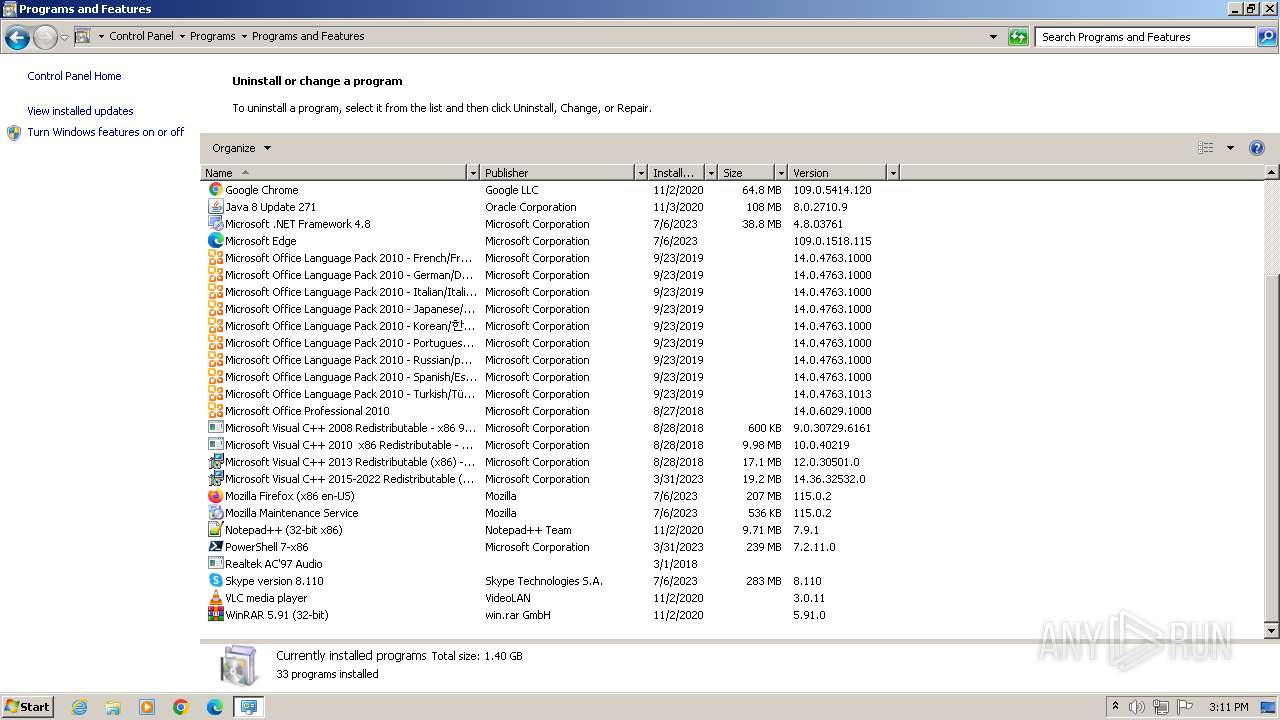
Creates files in the program directory
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- CagService.exe (PID: 2036)
- Gui.exe (PID: 1292)
- AEMAgent.exe (PID: 2124)
- AEMAgent.exe (PID: 1936)
- RMM.WebRemote.exe (PID: 2848)
Create files in a temporary directory
- AgentSetup_British+Business+Bank.exe (PID: 1120)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
Reads the machine GUID from the registry
- CagService.exe (PID: 2036)
- Gui.exe (PID: 1292)
- RMM.WebRemote.exe (PID: 2848)
- AEMAgent.exe (PID: 1936)
- Gui.exe (PID: 2268)
- Gui.exe (PID: 1980)
- Gui.exe (PID: 2356)
Creates files or folders in the user directory
- Gui.exe (PID: 1292)
Reads the software policy settings
- Gui.exe (PID: 1292)
- CagService.exe (PID: 2036)
- AEMAgent.exe (PID: 1936)
Disables trace logs
- CagService.exe (PID: 2036)
Checks proxy server information
- CagService.exe (PID: 2036)
Manual execution by a user
- wmpnscfg.exe (PID: 1796)
- Gui.exe (PID: 2268)
- Gui.exe (PID: 1980)
- AgentSetup_British+Business+Bank.exe (PID: 1280)
- AgentSetup_British+Business+Bank.exe (PID: 3800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:27 01:27:51+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.26 |
| CodeSize: | 35328 |
| InitializedDataSize: | 38912 |
| UninitializedDataSize: | 154112 |
| EntryPoint: | 0x4167 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
153
Monitored processes
93
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | wmic /namespace:\\root\Microsoft\Windows\Defender path MSFT_MpComputerStatus get /format:list | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 2147749902 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | wmic /namespace:\\root\Microsoft\Windows\Defender path MSFT_MpComputerStatus get /format:list | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 2147749902 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Windows\system32\cmd.exe" /c wmic /namespace:\\root\Microsoft\Windows\Defender path MSFT_MpComputerStatus get /format:list | C:\Windows\System32\cmd.exe | — | AEMAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 2147749902 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1028 | wmic /namespace:\\root\Microsoft\Windows\Defender path MSFT_MpComputerStatus get /format:list | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 2147749902 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1064 | "C:\Windows\system32\cmd.exe" /c wmic /namespace:\\root\Microsoft\Windows\Defender path MSFT_MpComputerStatus get /format:list | C:\Windows\System32\cmd.exe | — | AEMAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 2147749902 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1120 | "C:\Users\admin\Desktop\AgentSetup_British+Business+Bank.exe" | C:\Users\admin\Desktop\AgentSetup_British+Business+Bank.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1200 | wmic /namespace:\\root\Microsoft\Windows\Defender path MSFT_MpComputerStatus get /format:list | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 2147749902 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1280 | "C:\Users\admin\Desktop\AgentSetup_British+Business+Bank.exe" | C:\Users\admin\Desktop\AgentSetup_British+Business+Bank.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1292 | "C:\Program Files\CentraStage\Gui.exe" | C:\Program Files\CentraStage\Gui.exe | — | AgentSetup_British+Business+Bank.exe | |||||||||||
User: admin Company: CentraStage Integrity Level: HIGH Description: Agent Browser Version: 4.4.2220.2220 Modules
| |||||||||||||||
| 1296 | wmic /namespace:\\root\Microsoft\Windows\Defender path MSFT_MpComputerStatus get /format:list | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 2147749902 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
36 975
Read events
36 190
Write events
773
Delete events
12
Modification events
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CentraStage |
Value: C:\Program Files\CentraStage\Gui.exe | |||
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CentraStage |
| Operation: | write | Name: | DisplayName |
Value: CentraStage | |||
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CentraStage |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\CentraStage\uninst.exe" | |||
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CentraStage |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\CentraStage\CSIcon.ico | |||
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CentraStage |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.centrastage.com | |||
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CentraStage |
| Operation: | write | Name: | Publisher |
Value: CentraStage Limited | |||
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\CentraStage |
| Operation: | write | Name: | AgentFolderLocation |
Value: C:\ProgramData\CentraStage | |||
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\CentraStage |
| Operation: | write | Name: | AgentFolderStatus |
Value: 0 | |||
| (PID) Process: | (1120) AgentSetup_British+Business+Bank.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager |
| Operation: | write | Name: | PendingFileRenameOperations |
Value: \??\C:\Users\admin\AppData\Local\Temp\nse4123.tmp\nsProcess.dll | |||
| (PID) Process: | (2036) CagService.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
470
Suspicious files
44
Text files
98
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\Core.XmlSerializers.dll | executable | |
MD5:D19CC4F5AE445CA648C9020D9334C3F7 | SHA256:F572F258A83E4368680564B248CF006B9A38752386106C65C8B3CD93A2073AB9 | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\AxInterop.ViewerX.dll | executable | |
MD5:EDC5E696C4AD70F0BE6301F703AB3672 | SHA256:C6E5F17B2BC91202A1C6A9F3F0547CD7F208368B4CFEBB53F234A55F87C5ACD5 | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Users\admin\AppData\Local\Temp\nse4123.tmp\System.dll | executable | |
MD5:C17103AE9072A06DA581DEC998343FC1 | SHA256:DC58D8AD81CACB0C1ED72E33BFF8F23EA40B5252B5BB55D393A0903E6819AE2F | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\Common.dll | executable | |
MD5:5EB01EC12C1D6F8A93C77750C6ACFB75 | SHA256:627E4496060E075E3777CA77B22B93FF5011EE0607357AAC6DF1C4CB4C526F6B | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\Gui.exe | executable | |
MD5:85565EA373983DC1109C1A957D64638E | SHA256:2E7686E98CA5F3895855389B2825B48AF0EEF024AC485124055E4A3AEA9DA98D | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\FSharp.Core.dll | executable | |
MD5:99A817A04B25690B98EDF3370ED2EB83 | SHA256:9292EB06BF4CD100C94ABD2949A96351A0F3710008674993C7491DA578E1EDE1 | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\Microsoft.Threading.Tasks.dll | executable | |
MD5:D01819BFE03222DFA9E35A36555B6B6C | SHA256:5F29E16EDFF5379E93D5BE9BEE4CDDF98132B84326027688511AC0F3157AAF94 | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\ICSharpCode.SharpZipLib.dll | executable | |
MD5:C8164876B6F66616D68387443621510C | SHA256:40B3D590F95191F3E33E5D00E534FA40F823D9B1BB2A9AFE05F139C4E0A3AF8D | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\Gui.exe.config | xml | |
MD5:29D78BFD9A4C0D4F850250C25CA8112D | SHA256:71B4F6772FE48A80281E0D112DCB0A2FCAF99DA736A07FCA4CAA3E8107BF4AB0 | |||
| 1120 | AgentSetup_British+Business+Bank.exe | C:\Program Files\CentraStage\Microsoft.Threading.Tasks.Extensions.Desktop.dll | executable | |
MD5:E548A93D16964E52868C47CEF1C98F2E | SHA256:F71621C47C610E0886846CF53D955FD0E7448951F99ECC22FACD47493EF97A87 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
38
DNS requests
15
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
2036 | CagService.exe | 54.154.110.190:443 | 01cc.centrastage.net | AMAZON-02 | IE | unknown |
2036 | CagService.exe | 99.86.4.34:443 | update.centrastage.net | AMAZON-02 | US | unknown |
2036 | CagService.exe | 34.243.43.239:443 | features.pinotage.rmm.datto.com | AMAZON-02 | IE | unknown |
2036 | CagService.exe | 35.71.166.34:443 | pinotage-agent.centrastage.net | AMAZON-02 | US | unknown |
2036 | CagService.exe | 68.232.34.200:443 | download.visualstudio.microsoft.com | EDGECAST | US | whitelisted |
1936 | AEMAgent.exe | 99.86.4.34:443 | update.centrastage.net | AMAZON-02 | US | unknown |
1936 | AEMAgent.exe | 34.243.43.239:443 | features.pinotage.rmm.datto.com | AMAZON-02 | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
01cc.centrastage.net |
| unknown |
update.centrastage.net |
| whitelisted |
features.pinotage.rmm.datto.com |
| unknown |
pinotage-agent.centrastage.net |
| unknown |
download.visualstudio.microsoft.com |
| whitelisted |
agent-gateway.pinotage.rmm.datto.com |
| unknown |
pinotage-agent-notifications.centrastage.net |
| unknown |
pinotage-agent-comms.centrastage.net |
| unknown |
pinotage-monitoring.centrastage.net |
| unknown |
Threats
Process | Message |
|---|---|
AEMAgent.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 2124. Message ID: [0x2509].
|
AEMAgent.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 1936. Message ID: [0x2509].
|
RMM.WebRemote.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 2848. Message ID: [0x2509].
|
AEMAgent.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 1612. Message ID: [0x2509].
|