| File name: | 43eecf22e8f914d44df3da16c23dcc2e076a8753.zip |
| Full analysis: | https://app.any.run/tasks/c01ce828-e738-4df2-a3cb-05dd11f2f8a6 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 12:06:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A8E41B10354D07800FA16FFB8247D4AA |
| SHA1: | 4CF5BBB099F33F30A5A95520B3184E3C9D9870A5 |
| SHA256: | F8BD28F38B64BD952D05F83069328FD7F38E7DA2B4E59F787CE27DB467D180B3 |
| SSDEEP: | 192:tU+GRY6E1fjWDOvZ/FQfTS1/CCVGDhwUJm7Yhbe0EKtXvWIg2bkALm/6ceEbbsX2:RL6sfjN/wTSdVGDhrJmSb7pWnRh/UEUm |
MALICIOUS
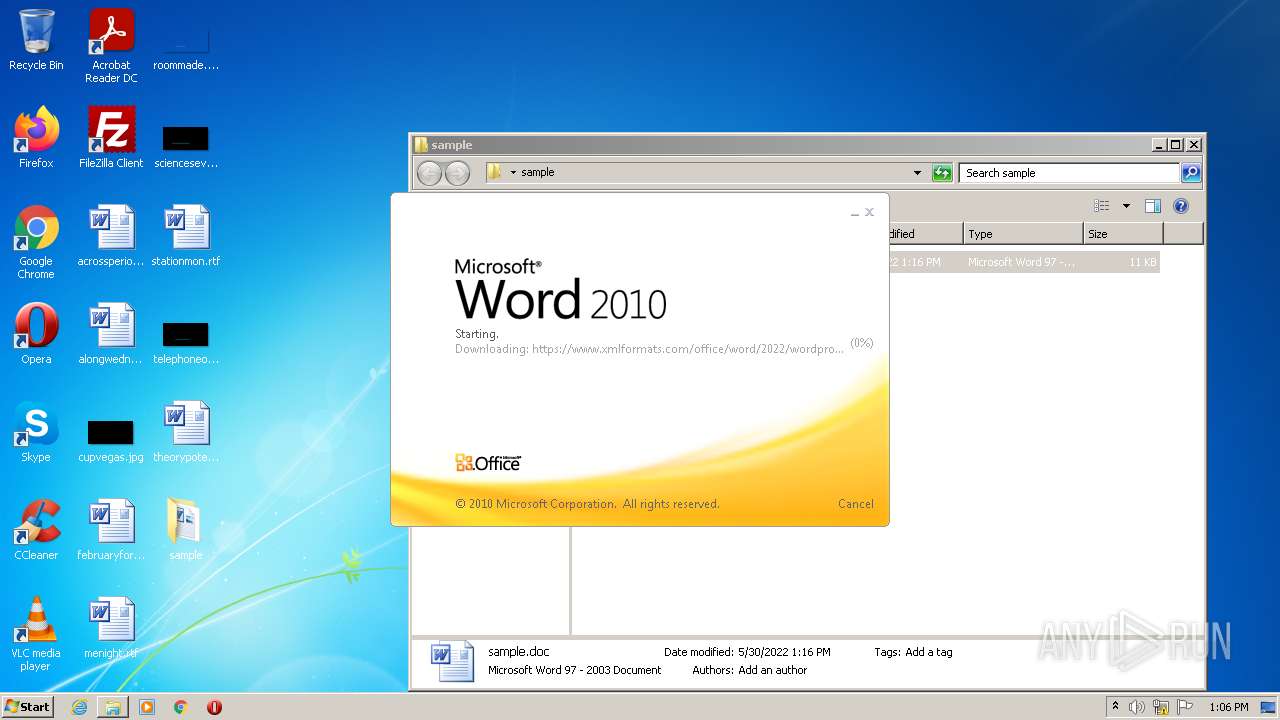
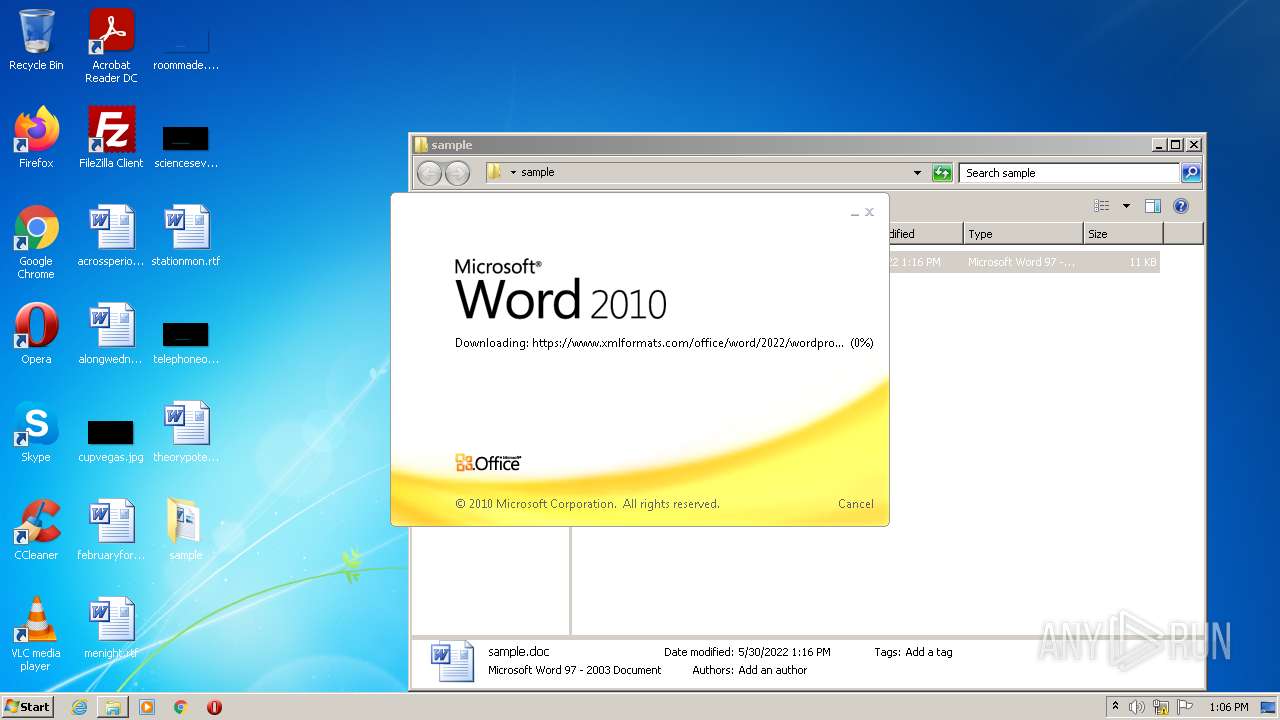
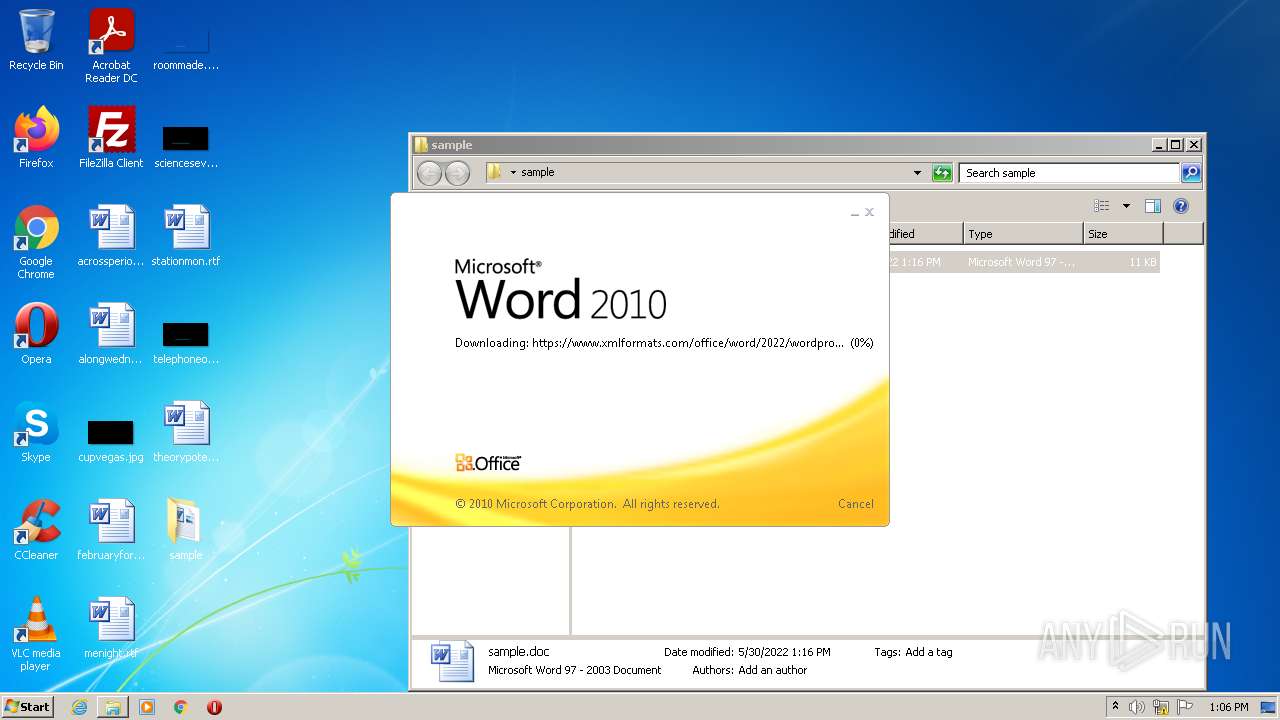
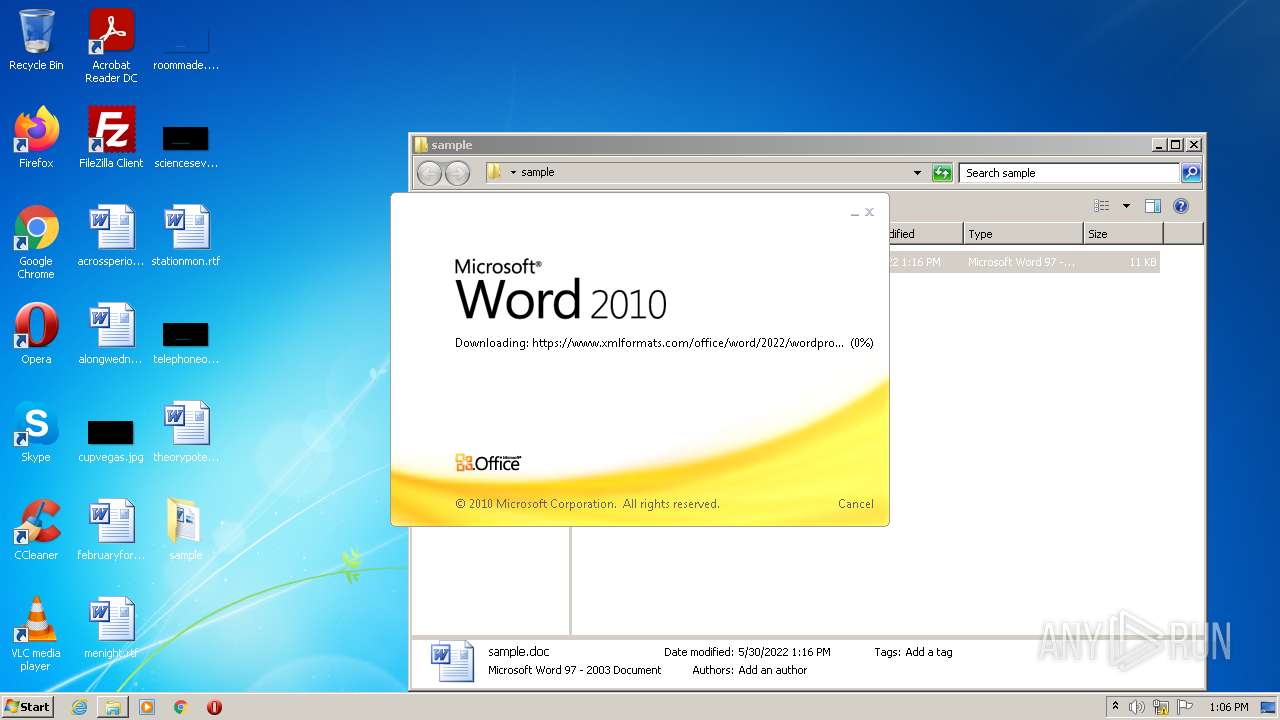
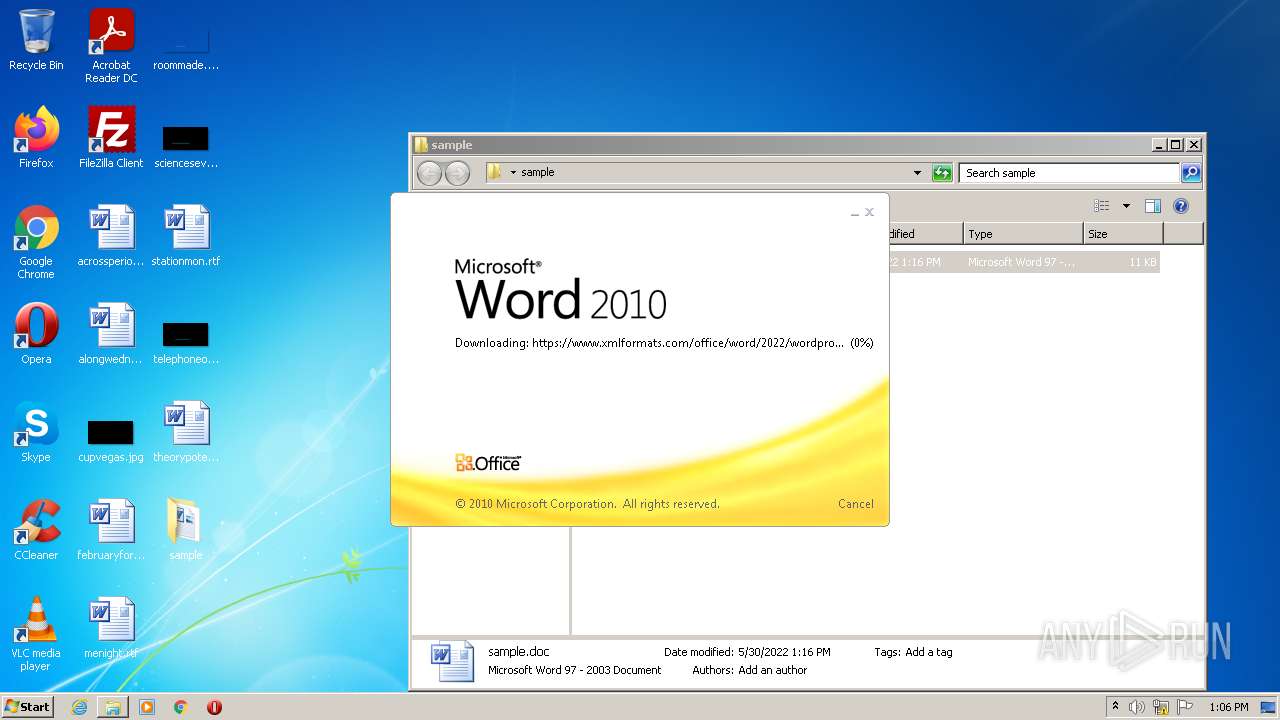
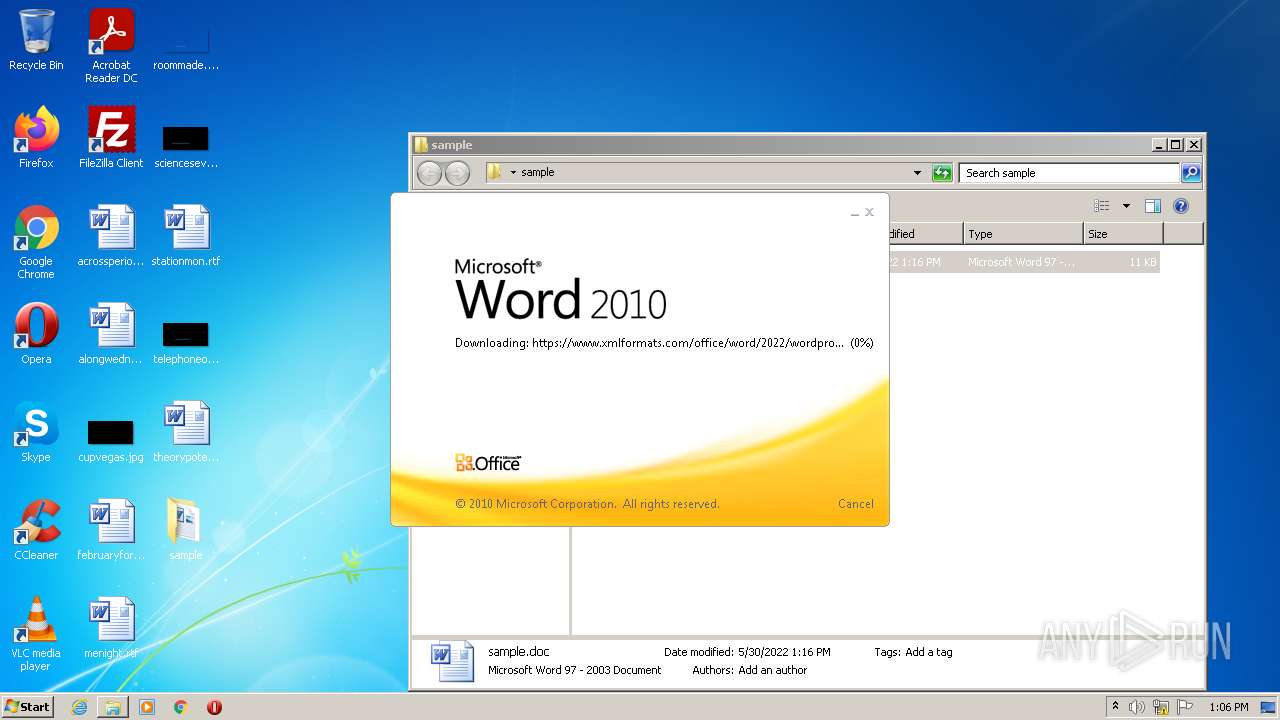
CVE-2022-30190 detected
- WINWORD.EXE (PID: 2620)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 1780)
Checks supported languages
- WinRAR.exe (PID: 1780)
Reads default file associations for system extensions
- WINWORD.EXE (PID: 2620)
INFO
Manual execution by user
- WINWORD.EXE (PID: 2620)
Creates files in the user directory
- WINWORD.EXE (PID: 2620)
Reads the computer name
- WINWORD.EXE (PID: 2620)
Checks supported languages
- WINWORD.EXE (PID: 2620)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | sample/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:06:01 17:02:16 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
43
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1780 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\43eecf22e8f914d44df3da16c23dcc2e076a8753.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2620 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\sample\sample.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
6 554
Read events
5 572
Write events
710
Delete events
272
Modification events
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\43eecf22e8f914d44df3da16c23dcc2e076a8753.zip | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
11
Text files
1
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7C75.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\Desktop\sample\~$sample.doc | pgc | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{1E4E1D5E-A8AE-4729-8156-03B1586F6EDF}.FSD | binary | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{B6BCD6CE-3A8F-4959-90AB-686126EF6C34} | binary | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{0E9594CE-29C3-4F8F-A424-0CB4A9FD5AF3} | binary | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\sample.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-{DFA86829-012F-4087-8202-658143BBEEE4}.FSD | binary | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.xmlformats.com |
| malicious |