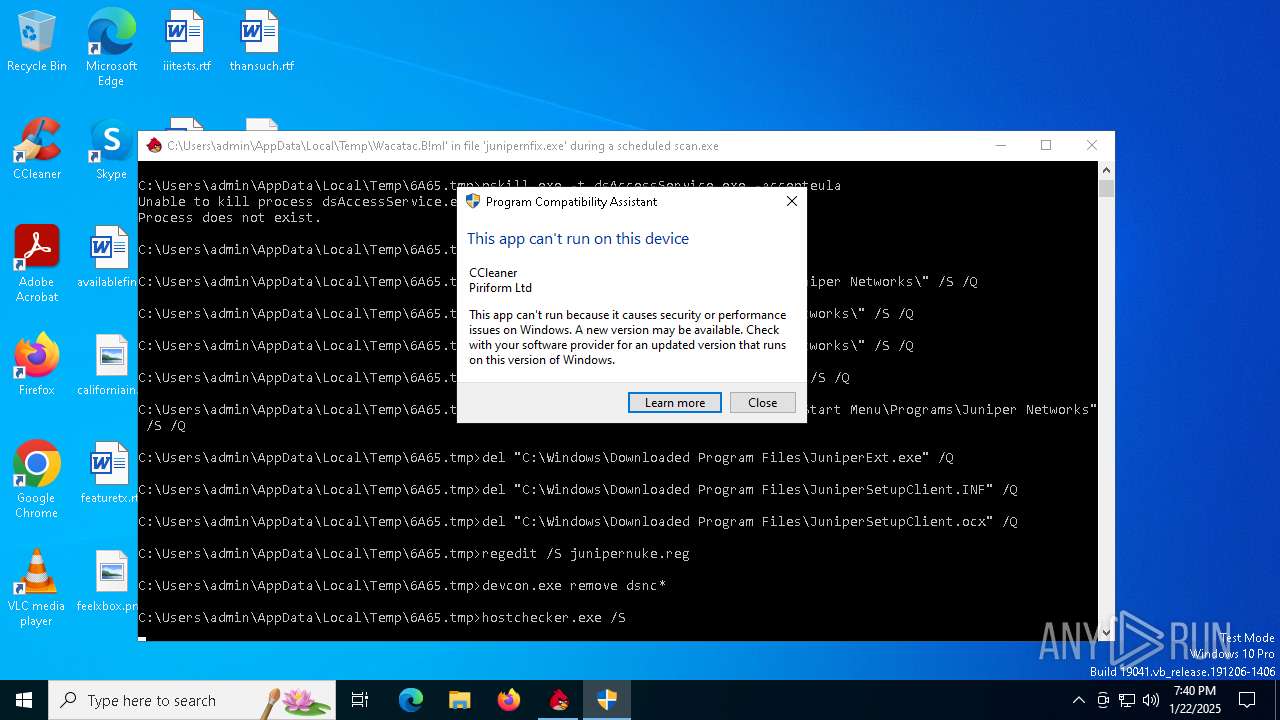
| File name: | Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan |
| Full analysis: | https://app.any.run/tasks/32ad70e0-8529-45bd-ae77-730432d2e1ff |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2025, 19:40:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | AC120137D7317DB137C91EA11AD3AF90 |
| SHA1: | CD82C2DAEB59F1DDCB88513D73FCB7EFF1239749 |
| SHA256: | F88DF0EBE5E2935450897750DC727D3A711D4829F0085D52CBAA3C62106C8511 |
| SSDEEP: | 98304:F3gYMReFcnGeg0ELiO2Vidq+yy9nn6WZuKv+aArH/JQv7VYWuJ66M7GC2OeiokmY:lTc1u |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe (PID: 1760)
- HostChecker.exe (PID: 6508)
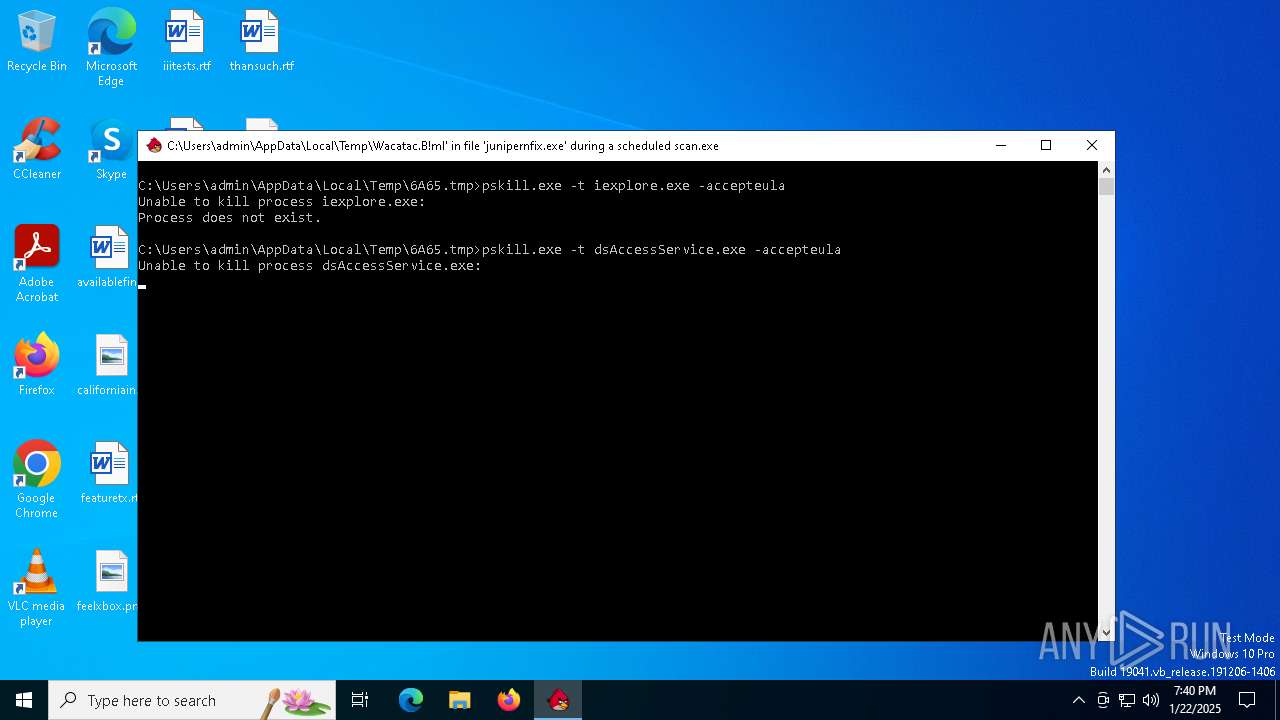
The executable file from the user directory is run by the CMD process
- pskill.exe (PID: 5920)
- pskill.exe (PID: 1448)
- pskill.exe (PID: 5872)
- pskill.exe (PID: 3952)
- pskill.exe (PID: 5340)
- pskill.exe (PID: 3612)
- pskill.exe (PID: 3364)
- pskill.exe (PID: 6136)
- pskill.exe (PID: 1944)
- pskill.exe (PID: 3732)
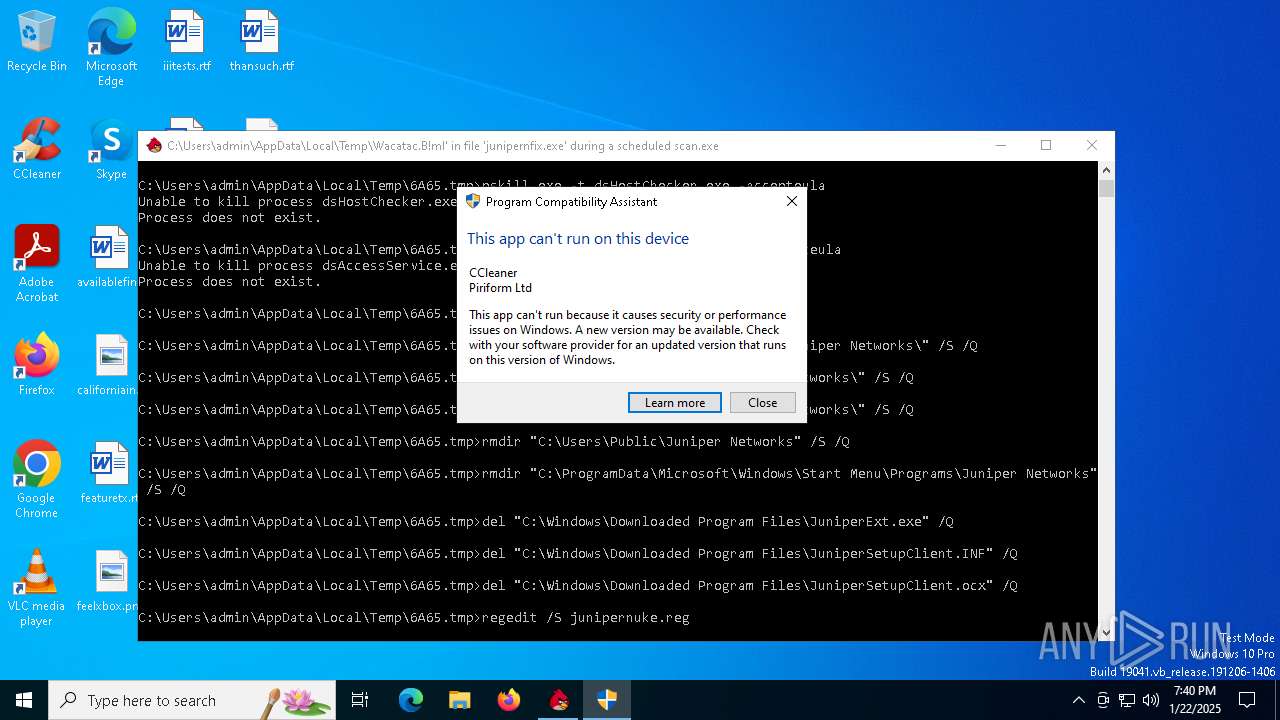
- CCleaner.exe (PID: 5720)
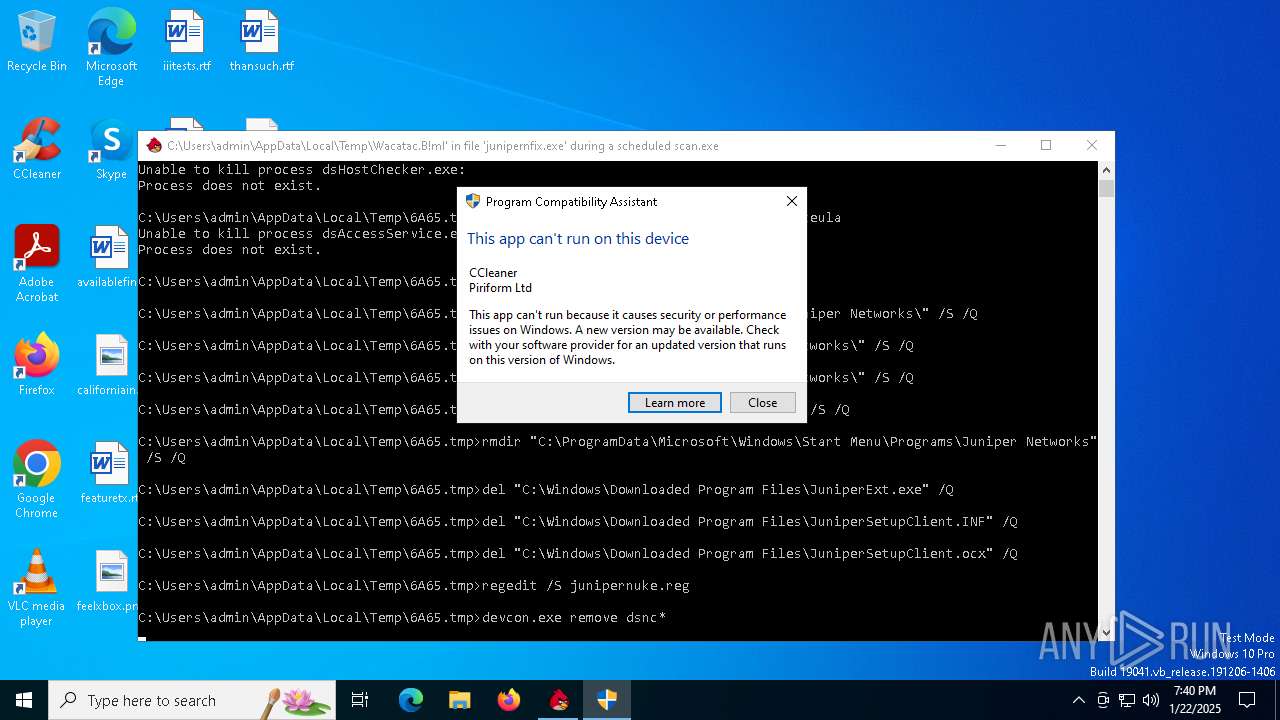
- devcon.exe (PID: 6344)
- devcon.exe (PID: 6364)
- devcon.exe (PID: 6412)
- HostChecker.exe (PID: 6508)
- pskill.exe (PID: 1228)
Executing commands from a ".bat" file
- Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe (PID: 1760)
Process drops legitimate windows executable
- Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe (PID: 1760)
- HostChecker.exe (PID: 6508)
Starts CMD.EXE for commands execution
- Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe (PID: 1760)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5488)
Starts a Microsoft application from unusual location
- devcon.exe (PID: 6344)
- devcon.exe (PID: 6364)
- devcon.exe (PID: 6412)
The process creates files with name similar to system file names
- HostChecker.exe (PID: 6508)
Creates a software uninstall entry
- HostChecker.exe (PID: 6508)
The process drops C-runtime libraries
- HostChecker.exe (PID: 6508)
Malware-specific behavior (creating "System.dll" in Temp)
- HostChecker.exe (PID: 6508)
INFO
Checks supported languages
- pskill.exe (PID: 1448)
- pskill.exe (PID: 5872)
- pskill.exe (PID: 3952)
- pskill.exe (PID: 3732)
- Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe (PID: 1760)
- pskill.exe (PID: 5920)
- pskill.exe (PID: 3612)
- pskill.exe (PID: 3364)
- pskill.exe (PID: 6136)
- pskill.exe (PID: 5340)
- pskill.exe (PID: 1944)
- pskill.exe (PID: 1228)
- devcon.exe (PID: 6412)
- HostChecker.exe (PID: 6508)
Reads the computer name
- pskill.exe (PID: 5872)
- pskill.exe (PID: 1448)
- pskill.exe (PID: 3952)
- pskill.exe (PID: 3732)
- pskill.exe (PID: 5920)
- pskill.exe (PID: 3364)
- pskill.exe (PID: 3612)
- pskill.exe (PID: 6136)
- pskill.exe (PID: 5340)
- pskill.exe (PID: 1944)
- pskill.exe (PID: 1228)
- HostChecker.exe (PID: 6508)
Create files in a temporary directory
- Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe (PID: 1760)
- HostChecker.exe (PID: 6508)
The sample compiled with english language support
- Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe (PID: 1760)
- HostChecker.exe (PID: 6508)
The process uses the downloaded file
- cmd.exe (PID: 5488)
Creates files or folders in the user directory
- HostChecker.exe (PID: 6508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 3260416 |
| InitializedDataSize: | 372736 |
| UninitializedDataSize: | 2670592 |
| EntryPoint: | 0x5a7750 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
149
Monitored processes
25
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | pskill.exe -t dsAccessService.exe -accepteula | C:\Users\admin\AppData\Local\Temp\6A65.tmp\pskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Terminates processes on local or remote systems Exit code: 4294967295 Version: 1.13 | |||||||||||||||
| 1412 | "C:\WINDOWS\system32\pcaui.exe" -g {11111111-1111-1111-1111-111111111111} -x {22bfeed6-cb41-4fe3-9e7b-fab443ef9e19} -a "CCleaner" -v "Piriform Ltd" -s "This app can't run because it causes security or performance issues on Windows. A new version may be available. Check with your software provider for an updated version that runs on this version of Windows." -n 2 -f 2021048 -k 0 -e "C:\Users\admin\AppData\Local\Temp\6A65.tmp\CCleaner.exe" | C:\Windows\System32\pcaui.exe | — | CCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Program Compatibility Assistant User Interface Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1448 | pskill.exe -t JuniperSetupClient.exe -accepteula | C:\Users\admin\AppData\Local\Temp\6A65.tmp\pskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Terminates processes on local or remote systems Exit code: 4294967295 Version: 1.13 | |||||||||||||||
| 1760 | "C:\Users\admin\AppData\Local\Temp\Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe" | C:\Users\admin\AppData\Local\Temp\Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1944 | pskill.exe -t dsHostChecker.exe -accepteula | C:\Users\admin\AppData\Local\Temp\6A65.tmp\pskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Terminates processes on local or remote systems Exit code: 4294967295 Version: 1.13 | |||||||||||||||
| 3364 | pskill.exe -t dsNcService.exe -accepteula | C:\Users\admin\AppData\Local\Temp\6A65.tmp\pskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Terminates processes on local or remote systems Exit code: 4294967295 Version: 1.13 | |||||||||||||||
| 3612 | pskill.exe -t dsHostChecker.exe -accepteula | C:\Users\admin\AppData\Local\Temp\6A65.tmp\pskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Terminates processes on local or remote systems Exit code: 4294967295 Version: 1.13 | |||||||||||||||
| 3688 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | pskill.exe -t dsNcService.exe -accepteula | C:\Users\admin\AppData\Local\Temp\6A65.tmp\pskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Terminates processes on local or remote systems Exit code: 4294967295 Version: 1.13 | |||||||||||||||
| 3952 | pskill.exe -t iexplore.exe -accepteula | C:\Users\admin\AppData\Local\Temp\6A65.tmp\pskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Terminates processes on local or remote systems Exit code: 4294967295 Version: 1.13 Modules
| |||||||||||||||
Total events
810
Read events
786
Write events
24
Delete events
0
Modification events
| (PID) Process: | (3952) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (3732) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (3612) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (6136) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (1944) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (5872) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (1448) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (5920) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (3364) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (5340) pskill.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsKill |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
Executable files
39
Suspicious files
1
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1760 | Wacatac.B!ml' in file 'junipernfix.exe' during a scheduled scan.exe | C:\Users\admin\AppData\Local\Temp\6A65.tmp\pskill.exe | executable | |
MD5:6F2F60AF33A5CAF03E1D0AC81A2DE892 | SHA256:ED8F3C368BA229043C8ACEF7AE4F4A0FDE62BF39FCE51522916B7DCE1E837F71 | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Roaming\Juniper Networks\Host Checker\dsWinClientResource_EN.dll | executable | |
MD5:A878377E2F591ACC3C51A9DD8F0E2B58 | SHA256:6F02C6038F12297550042FB3FEBF2A45D3EA36759059055D6F8EE26E45E29B4A | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Roaming\Juniper Networks\Host Checker\dsWinClientResource_DE.dll | executable | |
MD5:82048D12E59C31A6CA9ECA26691021ED | SHA256:7E707673F002B081C25DEDE6A734E723ED0E62B2F6446A121A3D750D26CAC2A2 | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Roaming\Juniper Networks\Host Checker\dsWinClientResource_ZH.dll | executable | |
MD5:49F714250B14FB0DEAA84B198807FF94 | SHA256:EA36D56FC988D776DE557D98C6213CCFA4AAF671087643817993F65B0009D6DF | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Roaming\Juniper Networks\Host Checker\dsWinClientResource_ES.dll | executable | |
MD5:4BCEBF4F3F97FA172F15E166B9D487C4 | SHA256:DC3BAE94D8DDD9DE63E167B73938784EB2C0A2151302291825A8FA2E472A7BCD | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Roaming\Juniper Networks\Host Checker\dsHostCheckerResource_en.dll | executable | |
MD5:0473281CDEDFF16D7ACD4B2C732DFB74 | SHA256:1A23E5A1410CA0BAC08ABC70E3A00D9A702ECB9C81B497F1C365B9DB41D67A38 | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Roaming\Juniper Networks\Host Checker\dsWinClientResource_JA.dll | executable | |
MD5:074021C7CE96BDEE46225A36A8FD5198 | SHA256:5804A03122537D48F75EDD8DA6E47101BC8797CC9B4C138FEECE800F3C5801FA | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Roaming\Juniper Networks\Host Checker\dsWinClient.dll | executable | |
MD5:C7AAAD2608903FD9F9CD08E3F31970DD | SHA256:A3DE427F632254B7F63803A93FD76ED79F9489B18C09E9F98AF577EF1A31EE8D | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Roaming\Juniper Networks\Host Checker\dsHostCheckerResource_de.dll | executable | |
MD5:A39DF902743572465156493119DD42DA | SHA256:860D8CABB7FFF5EFDB7AD4A8C2C6F18EF0B2FB089A7B50B49764E205322565E8 | |||
| 6508 | HostChecker.exe | C:\Users\admin\AppData\Local\Temp\nss7709.tmp\System.dll | executable | |
MD5:D6A1DC60C505105DC5D3812694B06539 | SHA256:F5E7A6981A1CDBE0B8E451088EA89012FCABDC1D0DF3F7C65A54CF73A62AE462 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
116
DNS requests
133
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.21.65.154:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
5564 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
— | — | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|