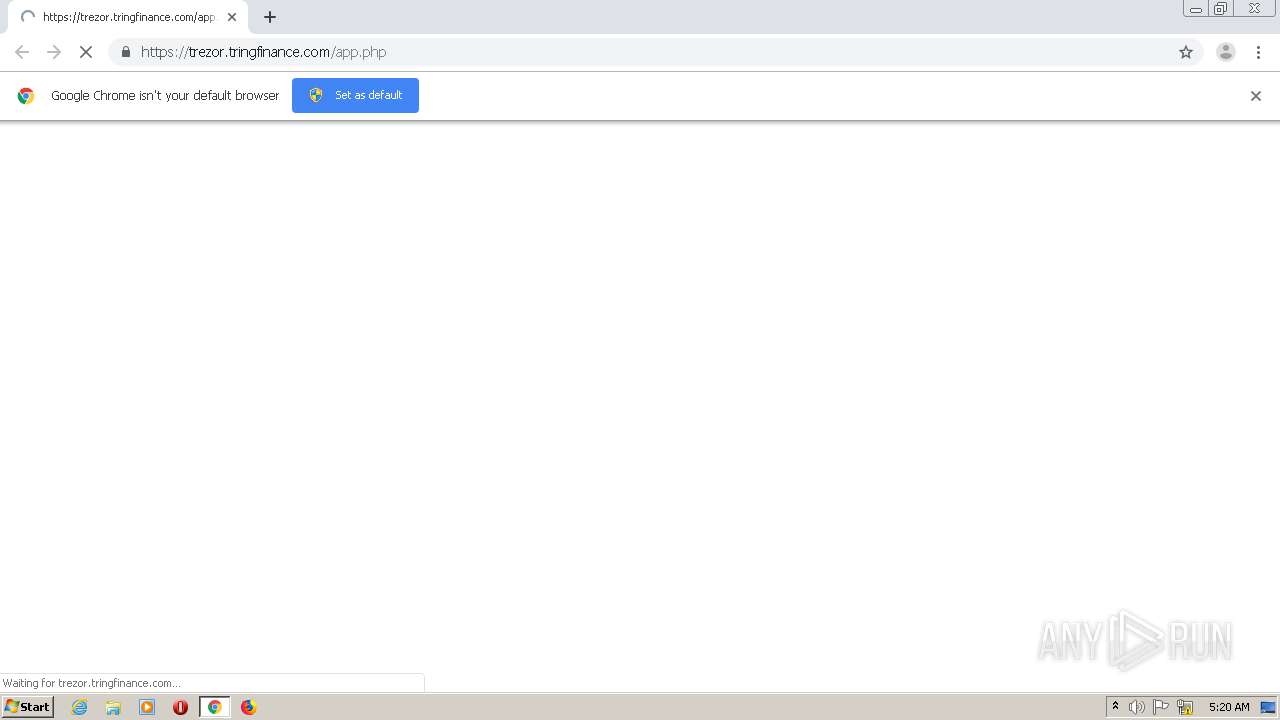
| URL: | https://trezor.tringfinance.com/app.php |
| Full analysis: | https://app.any.run/tasks/cc518729-6264-4892-ac6f-96f5ee78d99a |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 05:20:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 209051B10E8B0B84A1AAD39D18A8D740 |
| SHA1: | CE1EB79E4E7A1BB798350EEABDE432C77B66796B |
| SHA256: | F80A5479CBE42CD6AFCC0B36E22FE30E469746C4CEC2B7C4172738F0643CA3B1 |
| SSDEEP: | 3:N8f6KXuLimJNVn:2KLimJNV |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for external IP
- chrome.exe (PID: 2844)
INFO
Application launched itself
- chrome.exe (PID: 2588)
Reads the machine GUID from the registry
- chrome.exe (PID: 2588)
- chrome.exe (PID: 2844)
Reads settings of System Certificates
- chrome.exe (PID: 2844)
Reads the hosts file
- chrome.exe (PID: 2844)
- chrome.exe (PID: 2588)
Changes settings of System certificates
- chrome.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
19
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1684 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,7092414927107402800,18333681510727845117,131072 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3618602005274500408 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2320 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1772 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x84,0x88,0x8c,0x80,0x90,0x7fef3fe3ef8,0x7fef3fe3f08,0x7fef3fe3f18 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2104 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,7092414927107402800,18333681510727845117,131072 --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6231574977480607744 --mojo-platform-channel-handle=3540 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2352 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2228 --on-initialized-event-handle=328 --parent-handle=332 /prefetch:6 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2536 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,7092414927107402800,18333681510727845117,131072 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7386938094439955574 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2640 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2552 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1032,7092414927107402800,18333681510727845117,131072 --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=13897068416246363554 --mojo-platform-channel-handle=992 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2588 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" "https://trezor.tringfinance.com/app.php" | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2844 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,7092414927107402800,18333681510727845117,131072 --lang=en-US --service-sandbox-type=network --service-request-channel-token=15858543243040829282 --mojo-platform-channel-handle=1668 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2864 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,7092414927107402800,18333681510727845117,131072 --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11562698655536046461 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3356 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3000 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,7092414927107402800,18333681510727845117,131072 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13517333717233154835 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2332 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
346
Read events
291
Write events
52
Delete events
3
Modification events
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2324-13239293534024414 |
Value: 0 | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2588) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2588-13245916829272750 |
Value: 259 | |||
Executable files
0
Suspicious files
26
Text files
201
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F74159E-A1C.pma | — | |
MD5:— | SHA256:— | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000024.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\4a45d638-f2ce-441e-b58f-ee332f600042.tmp | — | |
MD5:— | SHA256:— | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C7925A6B262C5676D1C36638981A6EA | SHA256:07F6FB1E9CBCE4D15C00A9FBF9A95C1F31DE20C4C48B433198862E8759CD128D | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:963ED646A41C3DCEF8B1A846A70B0E99 | SHA256:FA6FBCDCFD899A377DDDD9B259AD140EDEEDC7AD90DD49EE22EDD3E1F66F2D7F | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:1A89A1BEBE6C843C4FF582E7ED33CA1F | SHA256:65099CA087B66AA8CA420AB121DAAD713E1DB5A61C5A574D9B1C0DF24F012520 | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:352F40AD53AB7F1152CAD77C58A149A5 | SHA256:BC7A7A8B6D0E52C14FB25C6715E244A2F0127F2FBFB5F2BA78E9DF663605B55E | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF1816bf.TMP | text | |
MD5:56052C3CBA145D49130B2518F4724E40 | SHA256:E267F083AEB0C0DE2B4EC93D65A3BC13D5EE6E06F61C4D07D049BC1F1AF5A343 | |||
| 2588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1816af.TMP | text | |
MD5:352F40AD53AB7F1152CAD77C58A149A5 | SHA256:BC7A7A8B6D0E52C14FB25C6715E244A2F0127F2FBFB5F2BA78E9DF663605B55E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
30
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
892 | svchost.exe | GET | 200 | 172.217.16.163:443 | https://clientservices.googleapis.com/chrome-variations/seed?osname=win&channel=stable&milestone=75 | US | compressed | 75.3 Kb | whitelisted |
2844 | chrome.exe | GET | 200 | 74.125.99.108:80 | http://r6---sn-hpa7kn7z.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWFjQUFXV2lsMkZVdjR5Vk5VZHJTM3E1dw/7919.1028.0.0_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=sX&mip=37.120.135.135&mm=28&mn=sn-hpa7kn7z&ms=nvh&mt=1601443156&mv=m&mvi=6&pl=24&shardbypass=yes | US | crx | 834 Kb | whitelisted |
2844 | chrome.exe | GET | 200 | 163.171.128.148:443 | https://www.solvay.com/sites/g/files/srpend221/files/css/css_1u2FJ4MAOx-uhxNbR_OGtWF9HX0JWxGU65BBL_r2E78.css | US | text | 30.1 Kb | suspicious |
2844 | chrome.exe | GET | 200 | 216.58.207.78:443 | https://clients2.google.com/service/update2/crx?os=win&arch=x64&os_arch=x86_64&nacl_arch=x86-64&prod=chromecrx&prodchannel=&prodversion=75.0.3770.100&lang=en-US&acceptformat=crx2,crx3&x=id%3Dapdfllckaahabafndbhieahigkjlhalf%26v%3D14.1%26installedby%3Dinternal%26uc%26brand%3DGCEA%26ping%3Dr%253D76%2526e%253D1&x=id%3Dblpcfgokakmgnkcojhhkbfbldkacnbeo%26v%3D4.2.8%26installedby%3Dinternal%26uc%26brand%3DGCEA%26ping%3Dr%253D76%2526e%253D1&x=id%3Dnmmhkkegccagdldgiimedpiccmgmieda%26v%3D1.0.0.5%26installedby%3Dother%26uc%26brand%3DGCEA%26ping%3Dr%253D76%2526e%253D1&x=id%3Dpjkljhegncpnkpknbcohdijeoejaedia%26v%3D8.2%26installedby%3Dinternal%26uc%26brand%3DGCEA%26ping%3Dr%253D76%2526e%253D1&x=id%3Dpkedcjkdefgpdelpbcmbmeomcjbeemfm%26v%3D7819.902.0.1%26installedby%3Dother%26uc%26brand%3DGCEA%26ping%3Dr%253D76%2526e%253D1&x=id%3Daohghmighlieiainnegkcijnfilokake%26v%3D0.10%26installedby%3Dinternal%26uc%26brand%3DGCEA%26ping%3Dr%253D76%2526e%253D0%2526dr%253D1&x=id%3Dghbmnnjooekpmoecnnnilnnbdlolhkhi%26v%3D1.11.0%26installedby%3Dexternal%26uc%26brand%3DGCEA%26ping%3Dr%253D76%2526e%253D0%2526dr%253D1 | US | xml | 1.95 Kb | whitelisted |
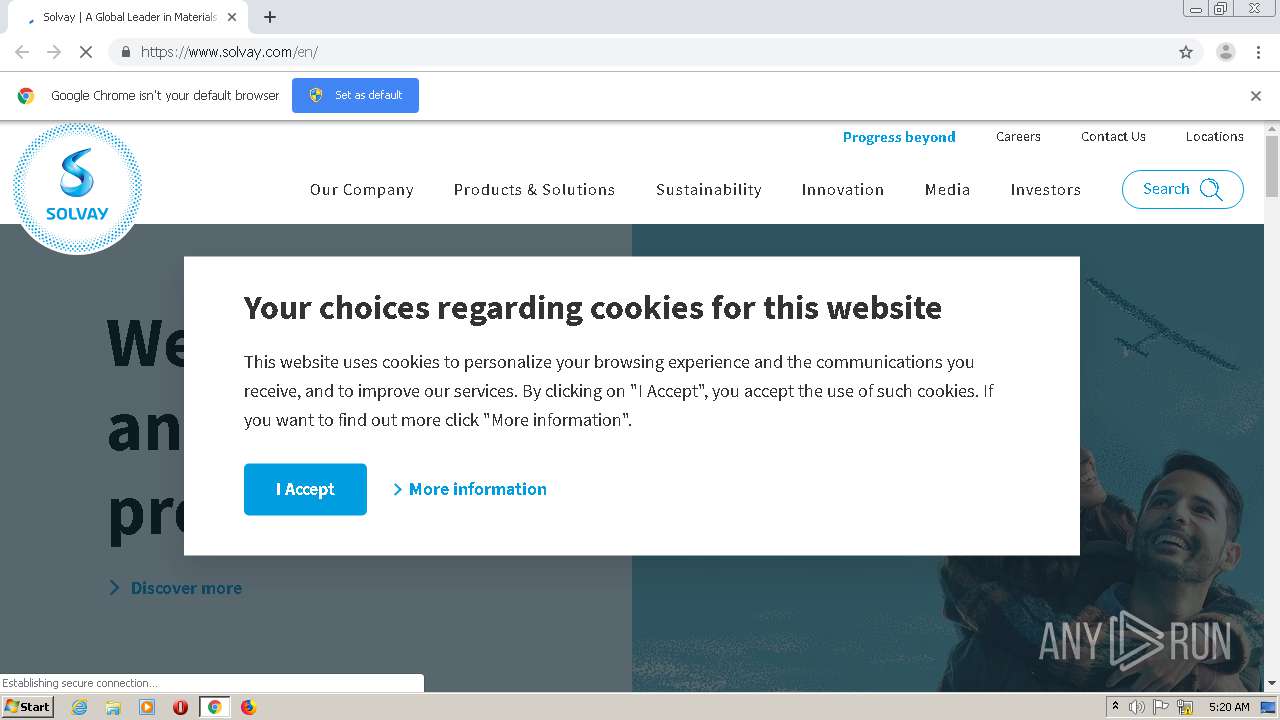
2844 | chrome.exe | GET | 301 | 163.171.128.148:443 | https://www.solvay.com/ | US | html | 27.0 Kb | suspicious |
2844 | chrome.exe | GET | 500 | 103.53.42.51:443 | https://trezor.tringfinance.com/favicon.ico | IN | html | 677 b | malicious |
2844 | chrome.exe | GET | 302 | 216.58.206.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWFjQUFXV2lsMkZVdjR5Vk5VZHJTM3E1dw/7919.1028.0.0_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 526 b | whitelisted |
2844 | chrome.exe | GET | 200 | 142.250.74.193:443 | https://clients2.googleusercontent.com/crx/blobs/QgAAAC6zw0qH2DJtnXe8Z7rUJP3tRdAiUfY8X7XWscfpoTq6M5HhT4jLZHyiQs-UvGU8fDSQ-r4dzf1ohyFtp8nsqIgyabZkFlwinLEYEbVHnuQRAMZSmuVmzLKbrxCMLR7rEO19BjK_OGg7qQ/extension_1_14_0_0.crx | US | crx | 76.1 Kb | whitelisted |
892 | svchost.exe | GET | 200 | 103.53.42.51:443 | https://trezor.tringfinance.com/app.php | IN | html | 754 b | malicious |
2844 | chrome.exe | GET | 200 | 163.171.128.148:443 | https://www.solvay.com/en/ | US | html | 140 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2844 | chrome.exe | 172.217.16.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 103.53.42.51:443 | trezor.tringfinance.com | PDR | IN | malicious |
2844 | chrome.exe | 172.217.23.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
— | — | 104.26.10.203:443 | npmcdn.com | Cloudflare Inc | US | unknown |
2844 | chrome.exe | 212.47.209.154:443 | tools.eurolandir.com | Linx Telecommunications B.V. | EE | unknown |
2844 | chrome.exe | 143.204.94.76:443 | lift3assets.lift.acquia.com | — | US | unknown |
2844 | chrome.exe | 74.125.99.108:80 | r6---sn-hpa7kn7z.gvt1.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 216.58.206.14:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 172.217.23.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 216.58.205.228:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
trezor.tringfinance.com |
| malicious |
clients2.google.com |
| whitelisted |
www.solvay.com |
| suspicious |
clients2.googleusercontent.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
r6---sn-hpa7kn7z.gvt1.com |
| whitelisted |
lift3assets.lift.acquia.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |