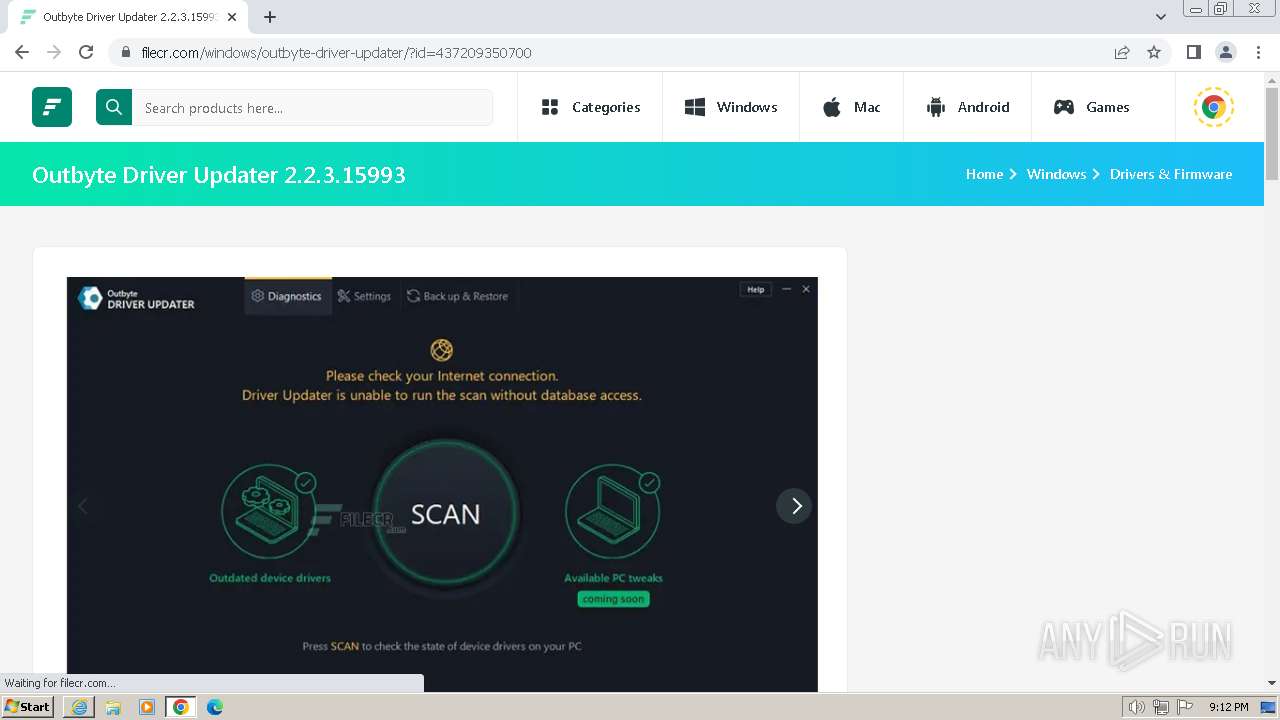
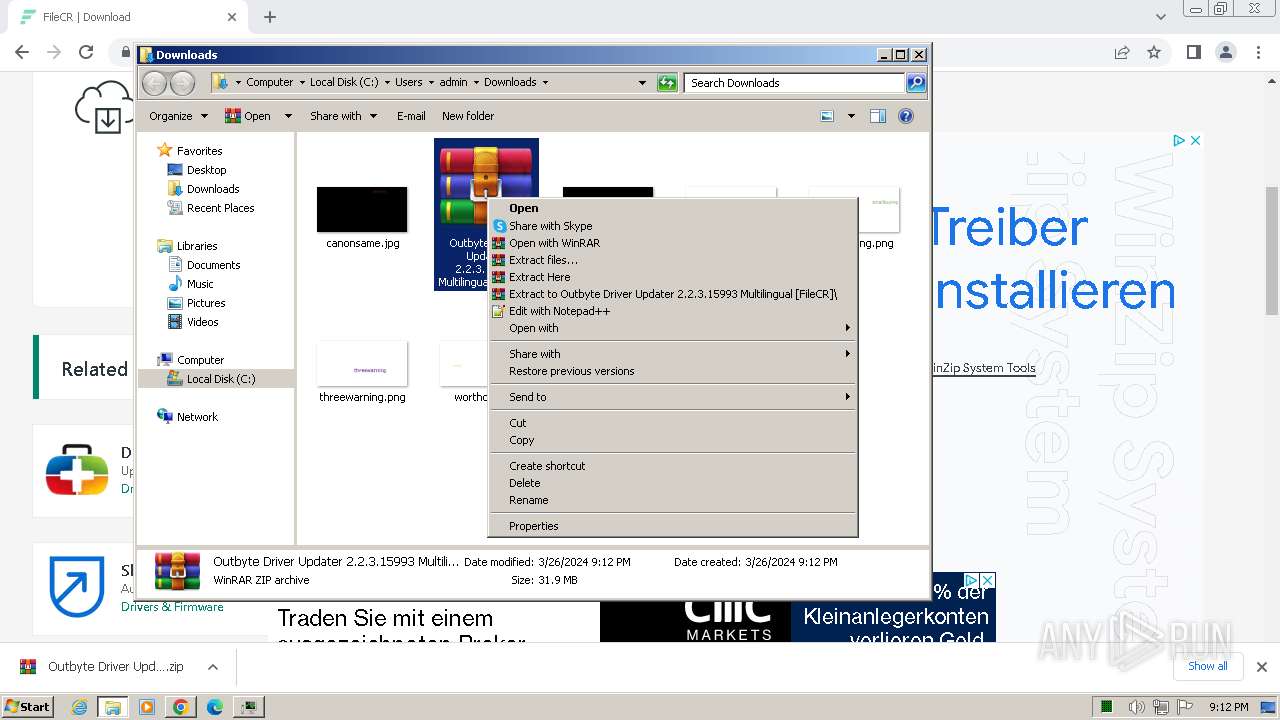
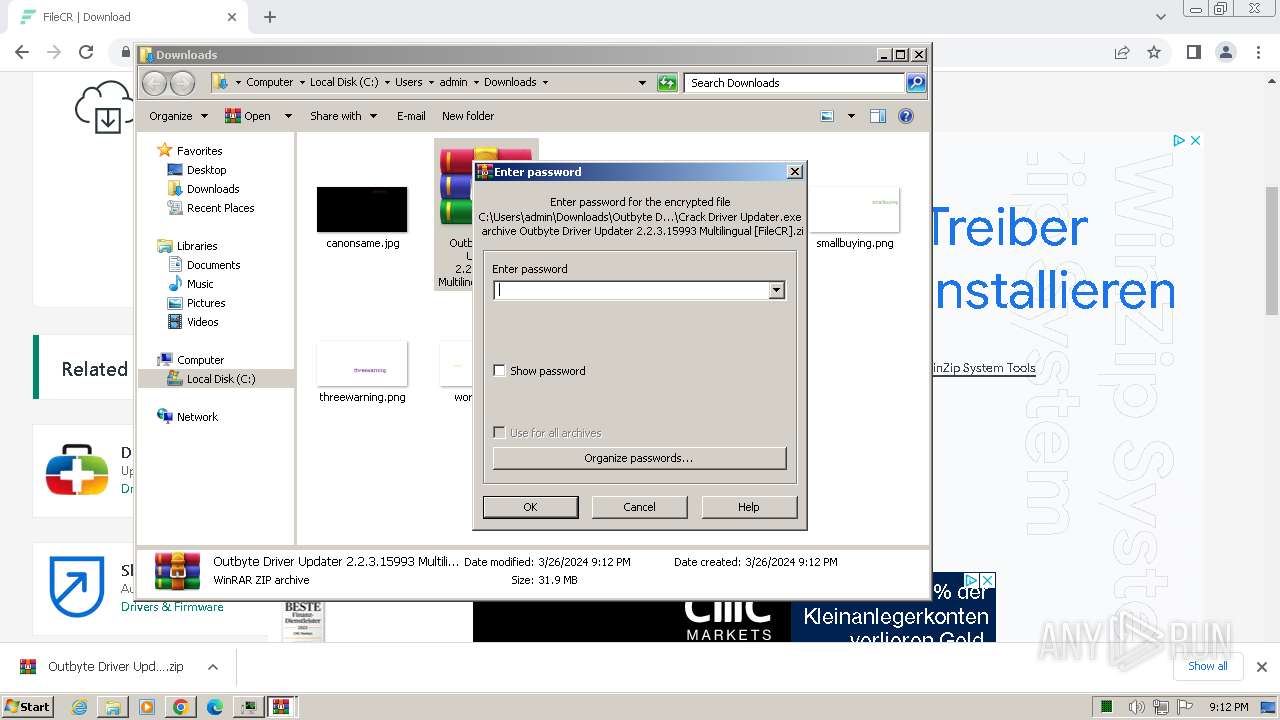
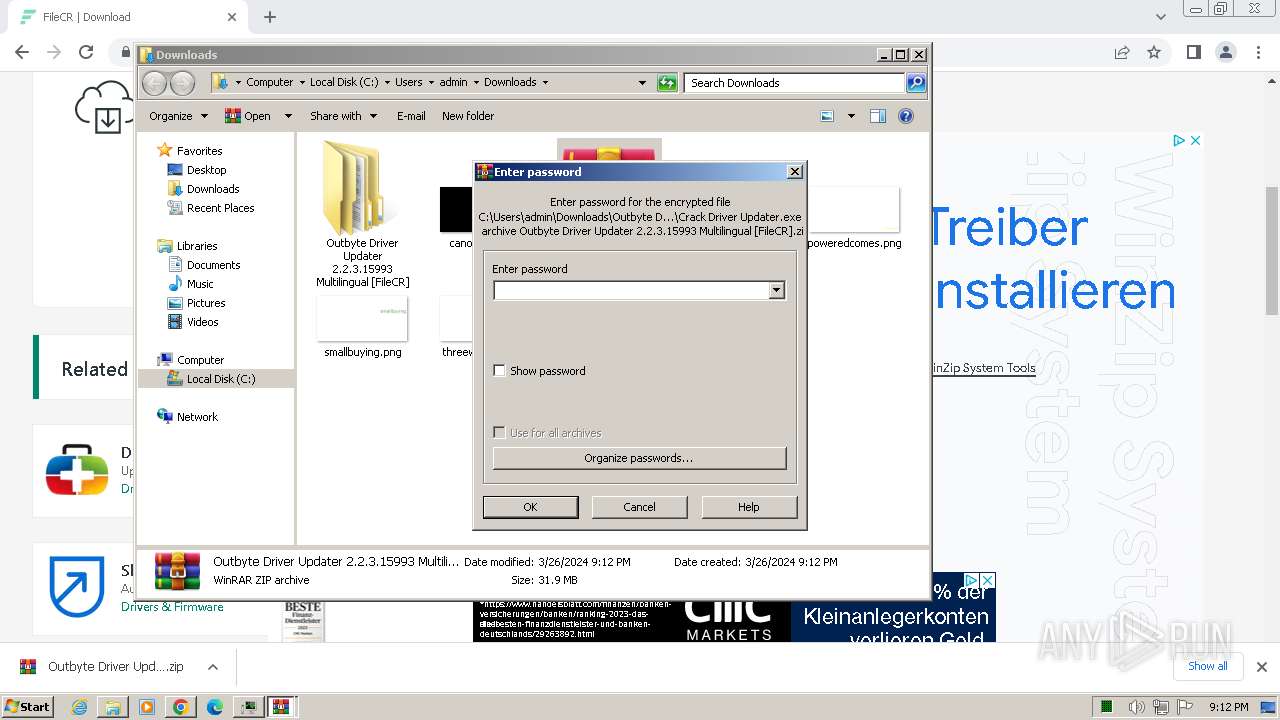
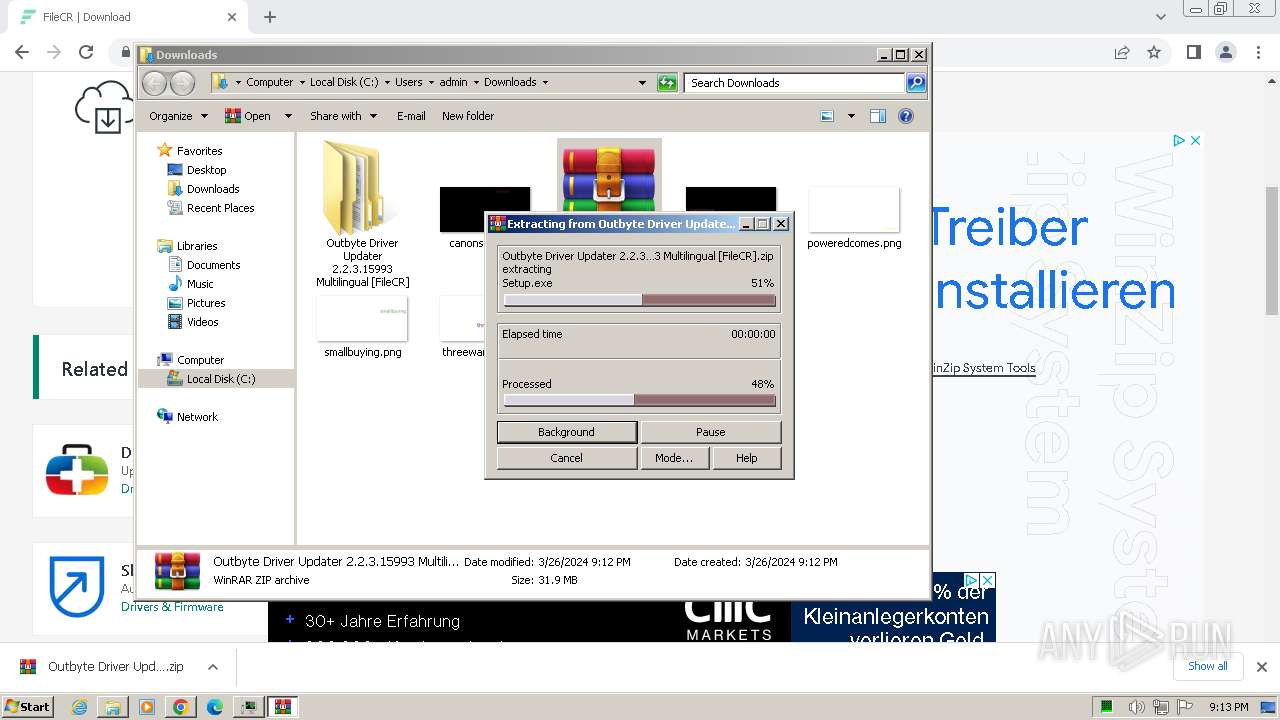
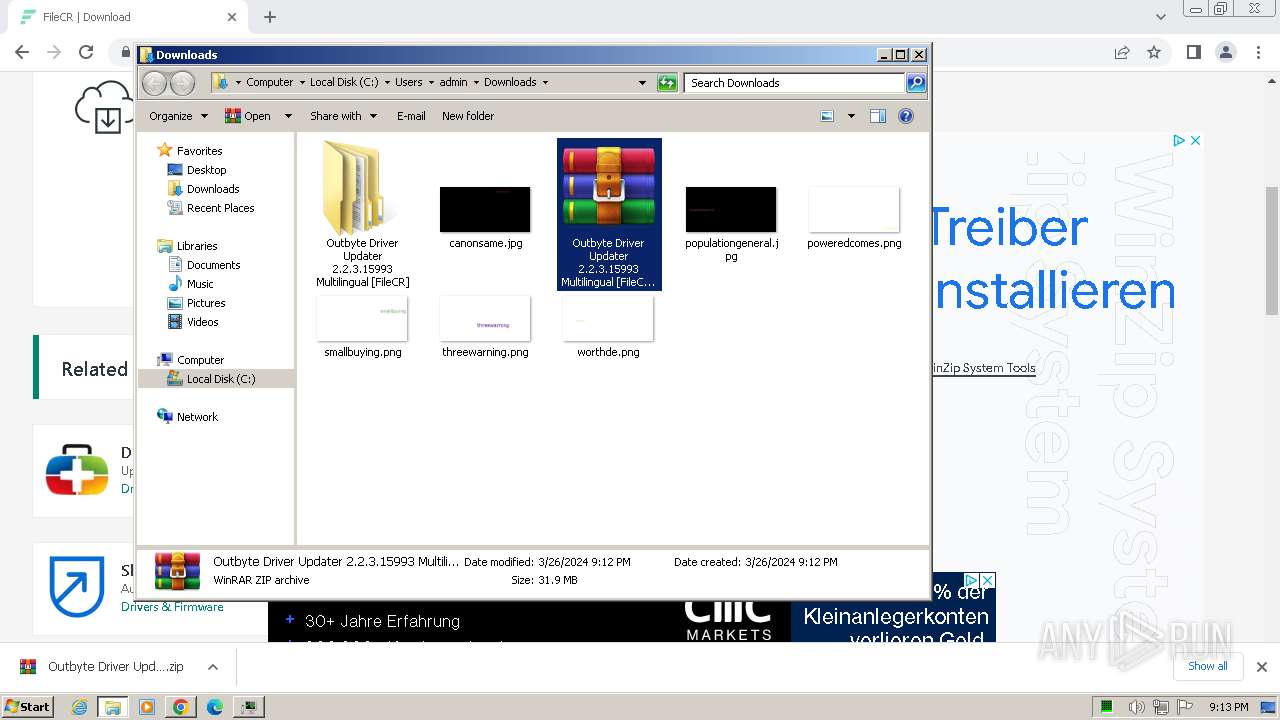
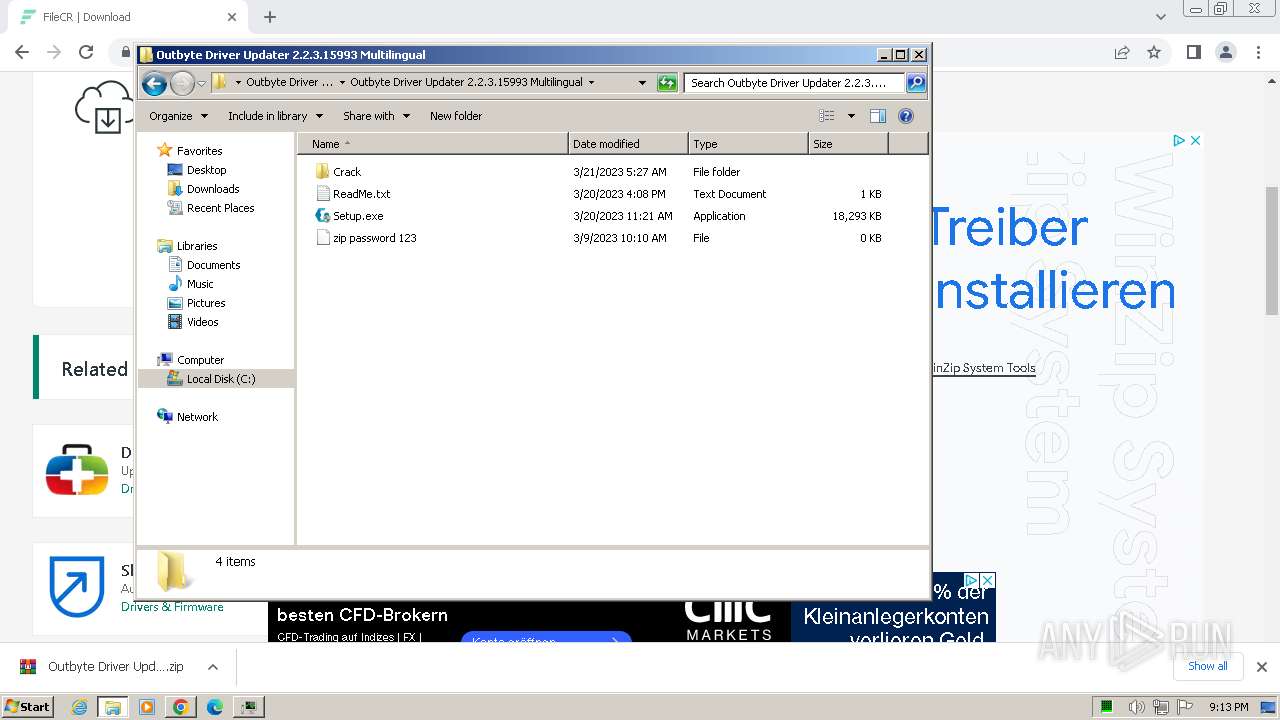
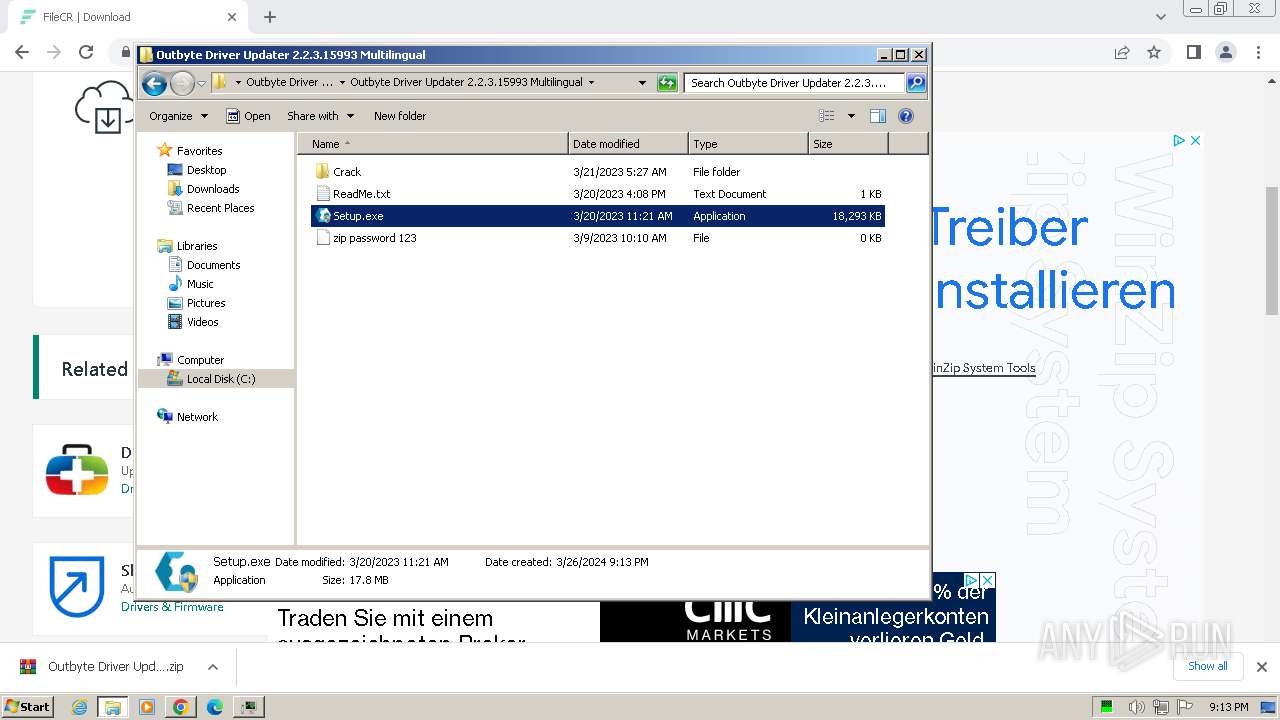
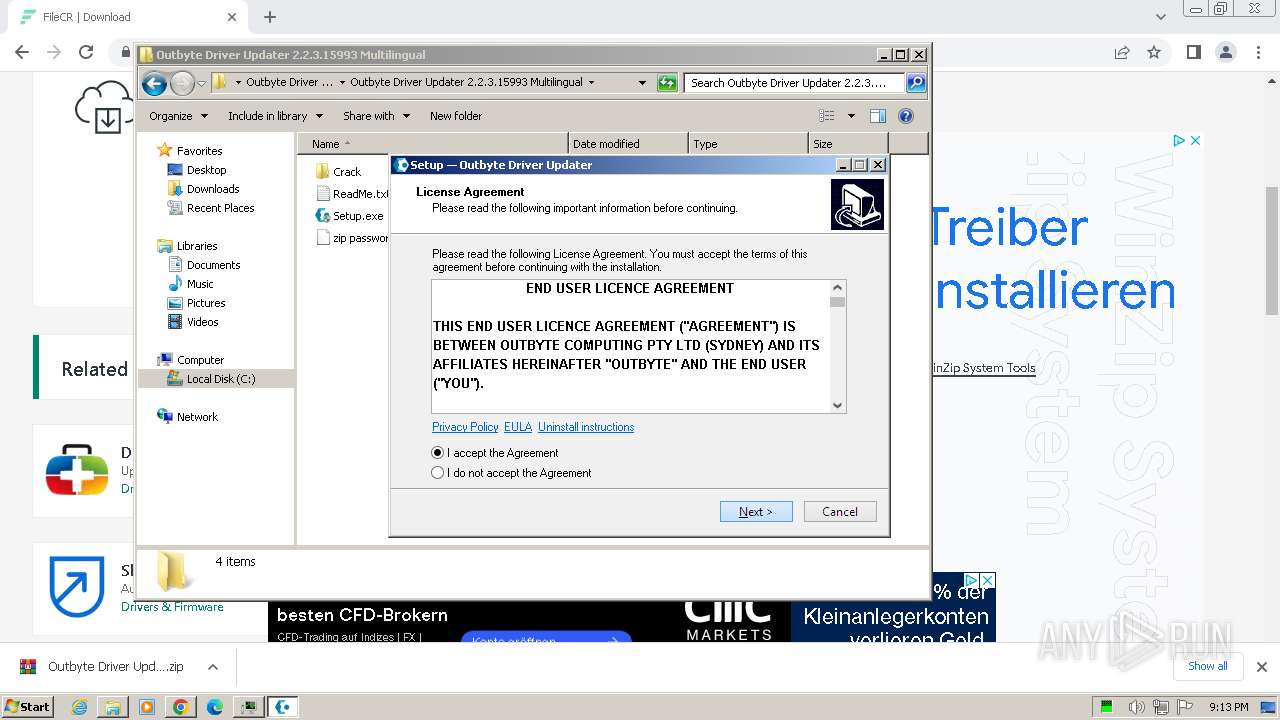
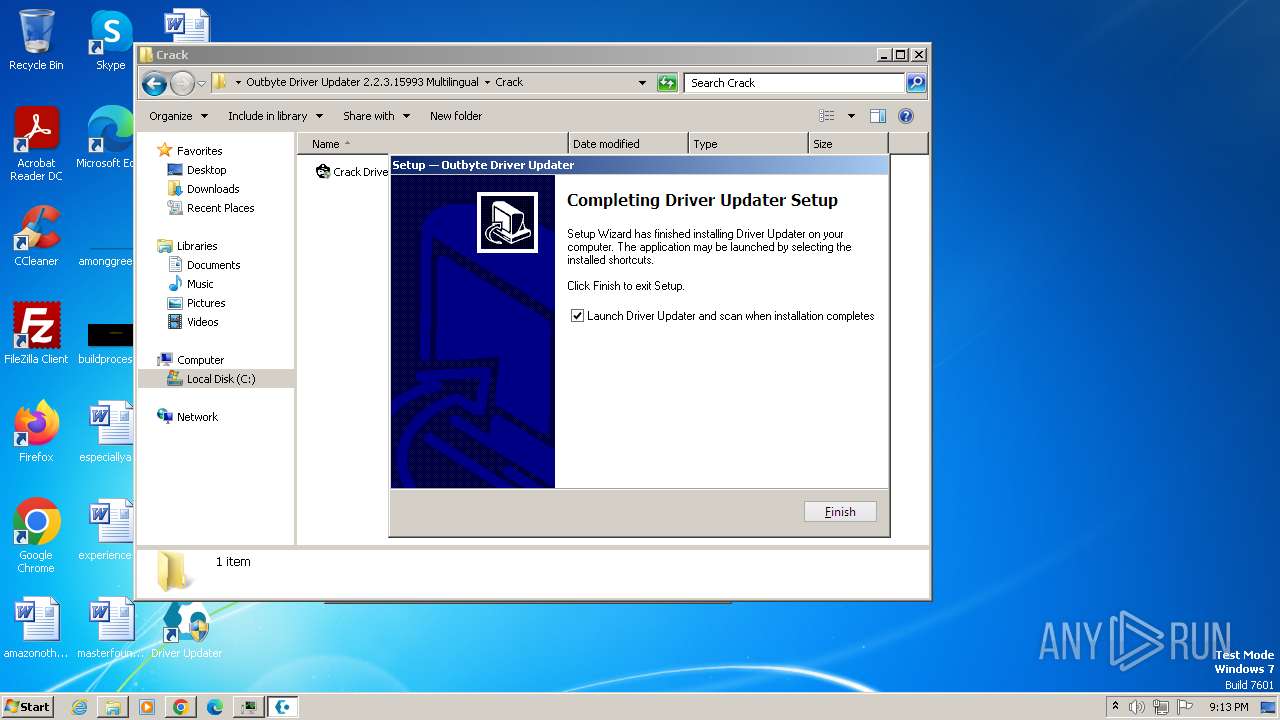
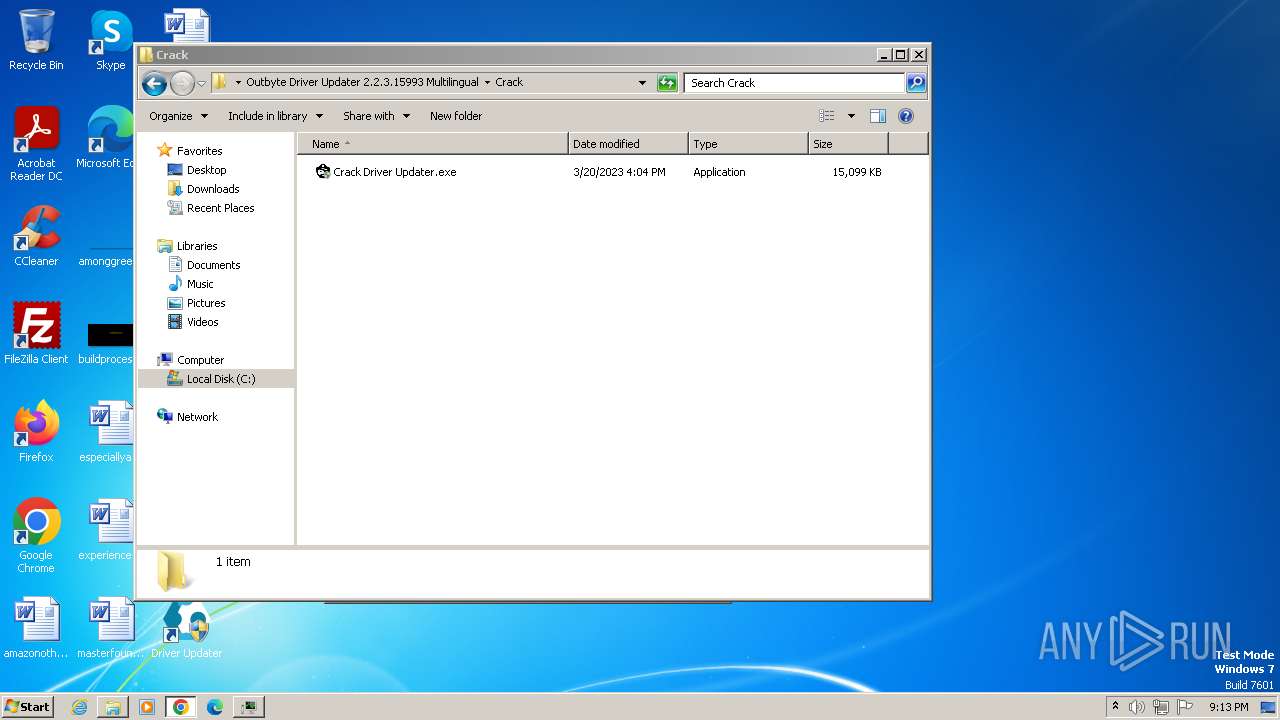
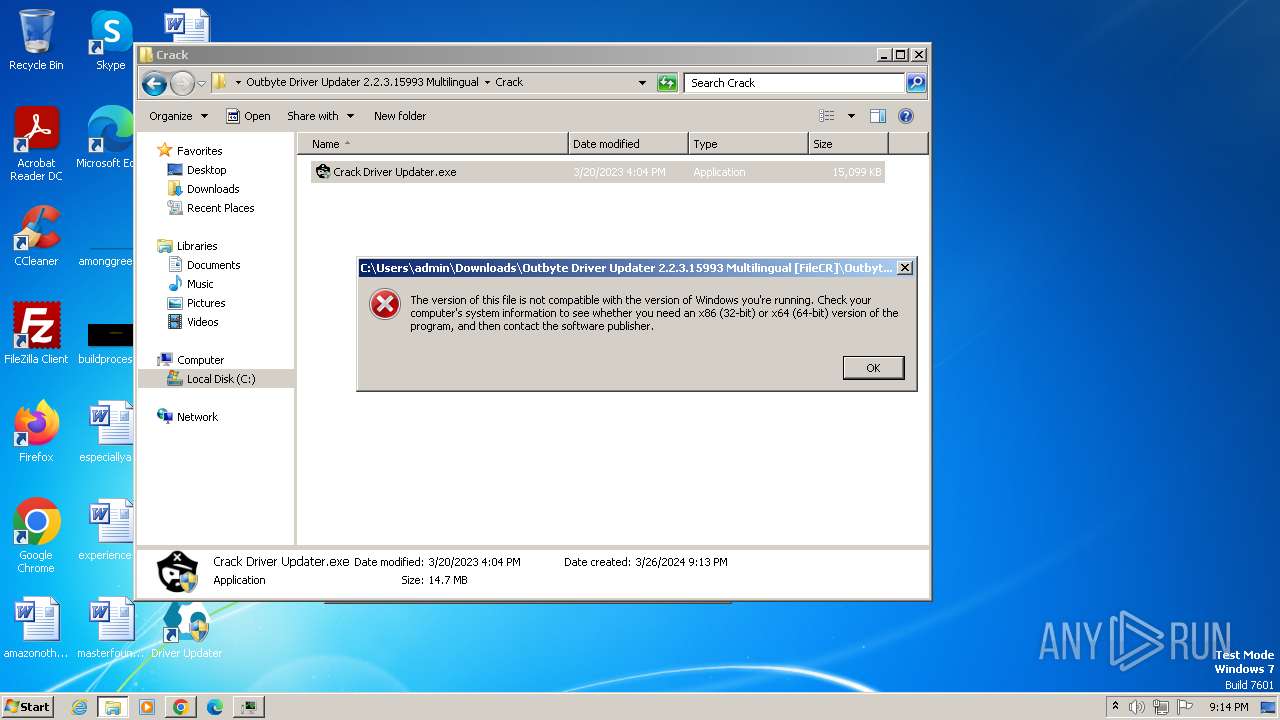
| URL: | https://filecr.com/windows/outbyte-driver-updater/?id=437209350700 |
| Full analysis: | https://app.any.run/tasks/32cb9971-e764-46b0-9f0f-aef5b75edde4 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2024, 21:11:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E4FAAA84E4A4A6A88A83B1E5D61E83B4 |
| SHA1: | 76EE99E6275902FC2CE3947013FD482A918CF3D0 |
| SHA256: | F7F5737CAFFB1BF6E90A0E74864E3B8C4AC3FA506EC5FE6C44D8651C22E5515E |
| SSDEEP: | 3:N8JTCoQRlbcxPn:2hLESxPn |
MALICIOUS
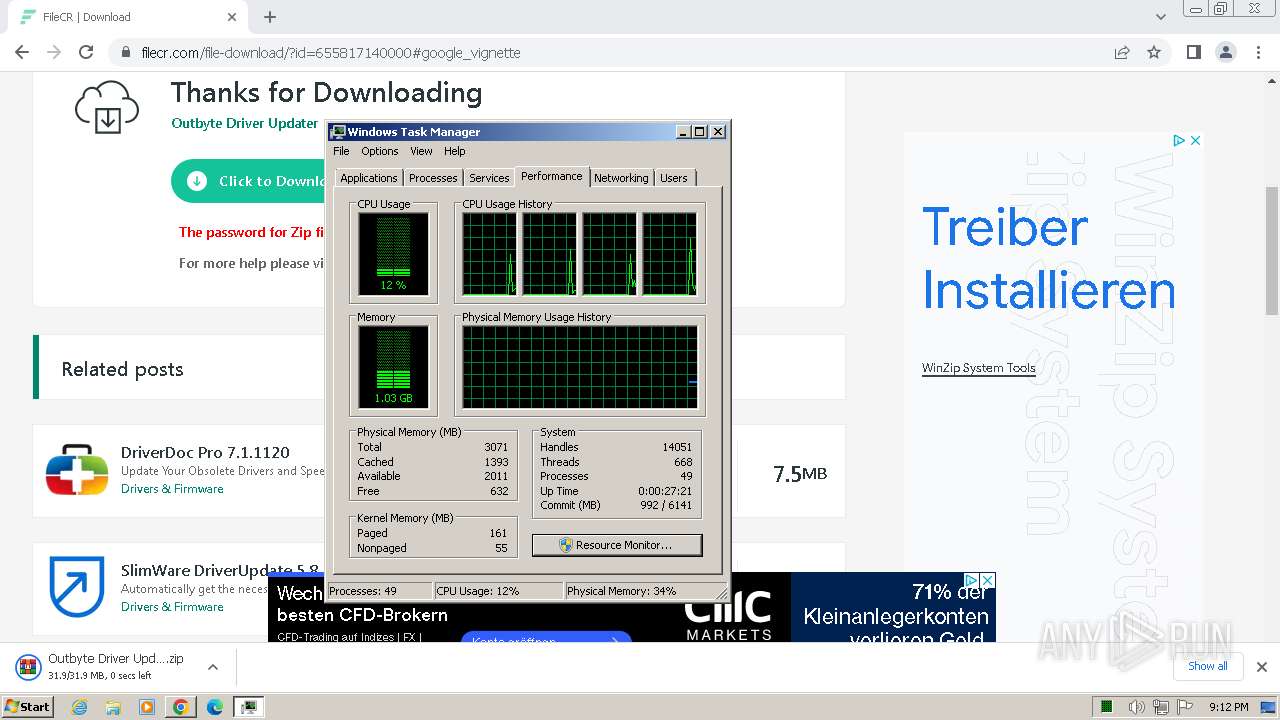
Drops the executable file immediately after the start
- Setup.exe (PID: 2508)
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 2768)
Steals credentials from Web Browsers
- Installer.exe (PID: 4000)
Actions looks like stealing of personal data
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- CustomDllSurrogate.x32.exe (PID: 2300)
- DriverUpdater.exe (PID: 2768)
Registers / Runs the DLL via REGSVR32.EXE
- DriverUpdater.exe (PID: 2768)
SUSPICIOUS
Reads the Internet Settings
- Setup.exe (PID: 2508)
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Checks Windows Trust Settings
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Reads the BIOS version
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- DriverUpdater.exe (PID: 2768)
Reads the Windows owner or organization settings
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 2768)
Reads security settings of Internet Explorer
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Process drops legitimate windows executable
- Installer.exe (PID: 4000)
Adds/modifies Windows certificates
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- CustomDllSurrogate.x32.exe (PID: 2300)
Process drops SQLite DLL files
- Installer.exe (PID: 4000)
Creates a software uninstall entry
- Installer.exe (PID: 4000)
Searches for installed software
- DriverUpdater.exe (PID: 1636)
- dllhost.exe (PID: 480)
- DriverUpdater.exe (PID: 2768)
Reads settings of System Certificates
- DriverUpdater.exe (PID: 1636)
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Non-standard symbols in registry
- DriverUpdater.exe (PID: 1636)
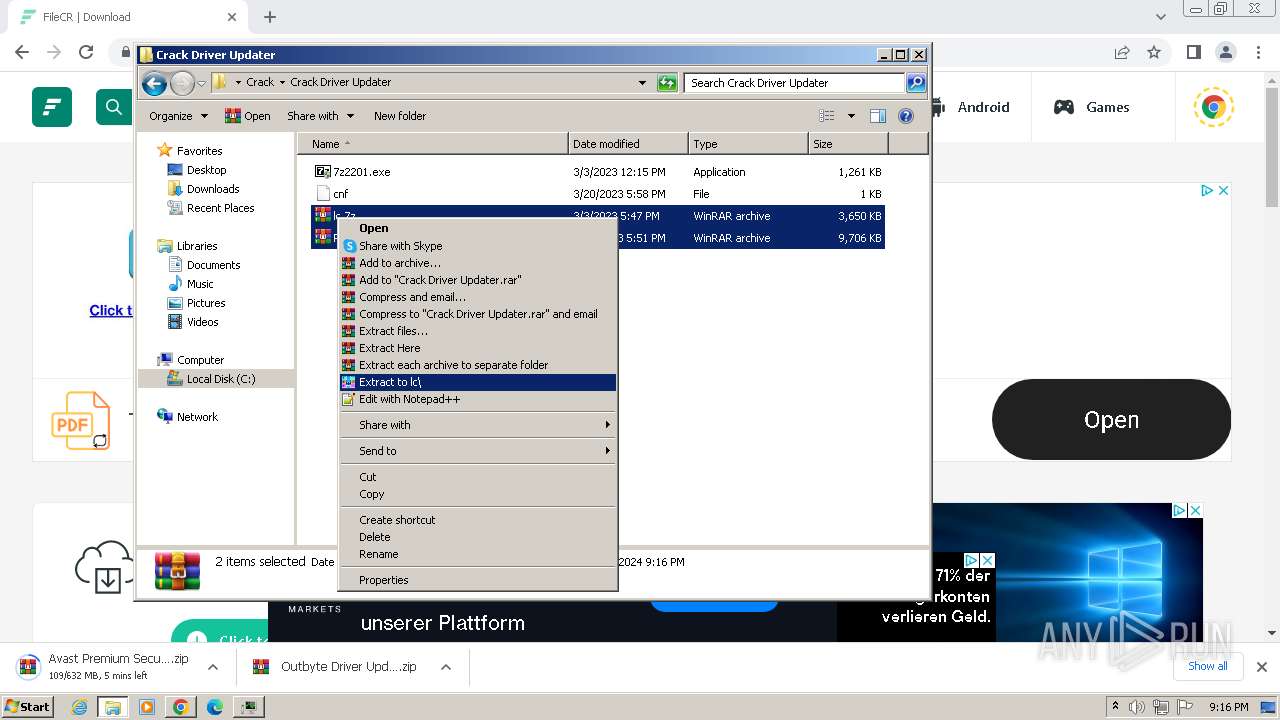
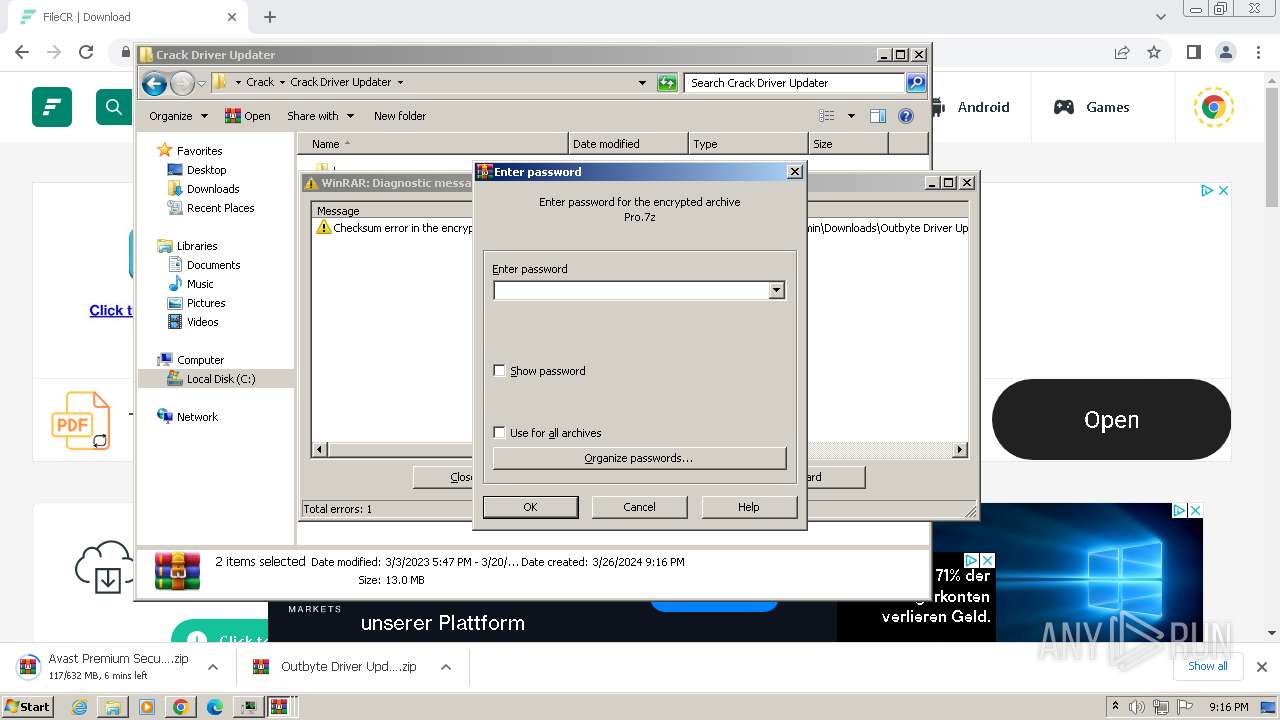
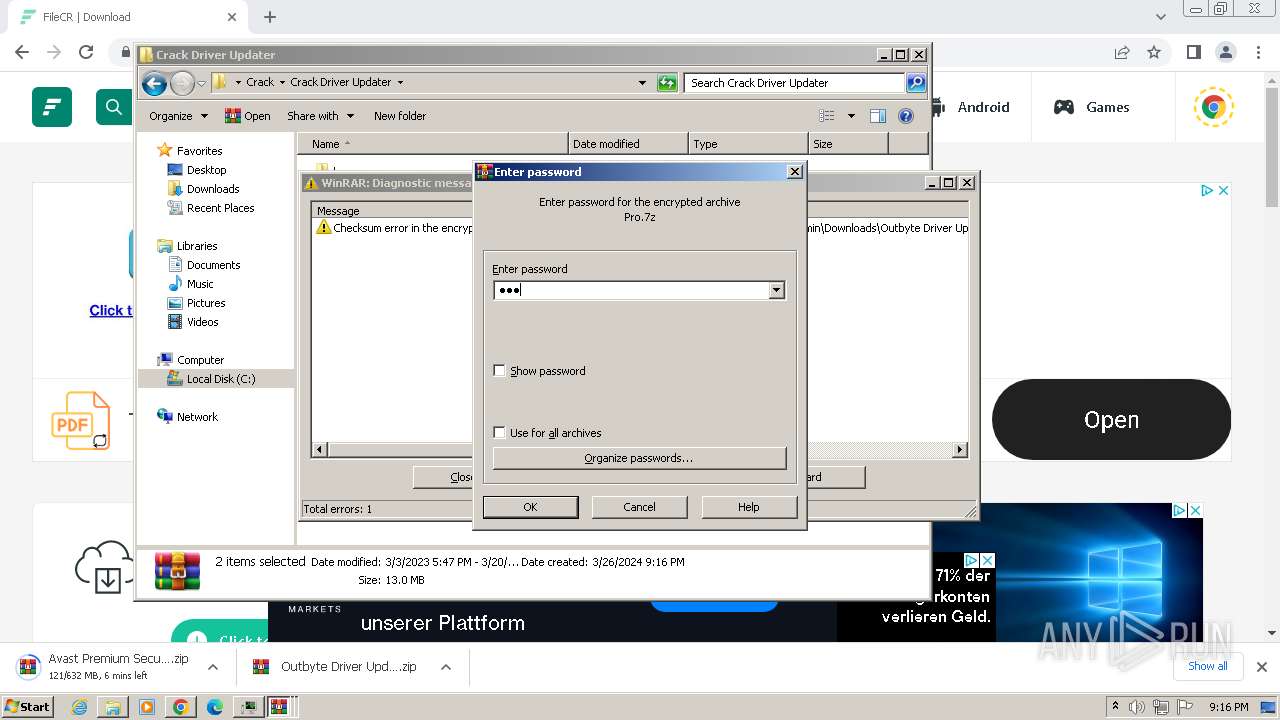
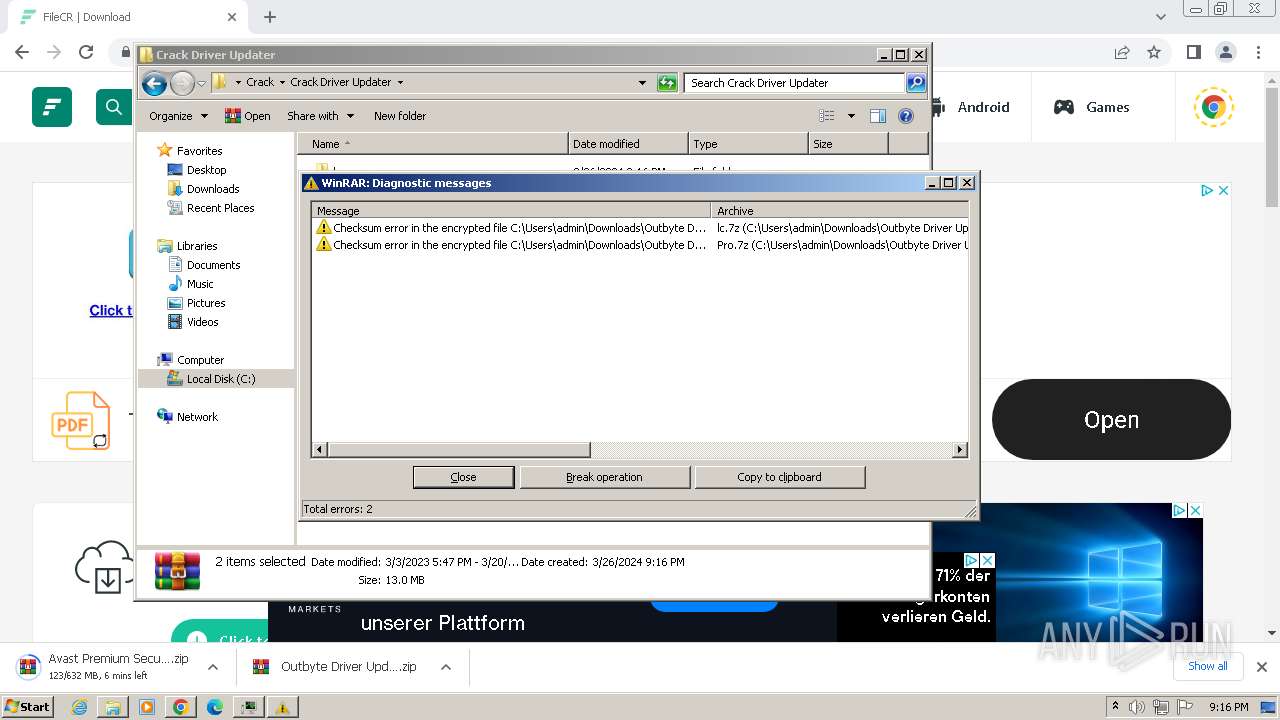
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 1636)
Executes as Windows Service
- VSSVC.exe (PID: 2556)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 4072)
INFO
Manual execution by a user
- chrome.exe (PID: 1352)
- taskmgr.exe (PID: 2092)
- WinRAR.exe (PID: 2020)
- Setup.exe (PID: 1196)
- Setup.exe (PID: 2508)
- 7z2201.exe (PID: 1192)
- WinRAR.exe (PID: 696)
- DriverUpdater.exe (PID: 2768)
- 7z2201.exe (PID: 4000)
- DriverUpdater.exe (PID: 920)
- WinRAR.exe (PID: 1636)
Application launched itself
- iexplore.exe (PID: 2120)
- chrome.exe (PID: 1352)
The process uses the downloaded file
- chrome.exe (PID: 2016)
- WinRAR.exe (PID: 2020)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2020)
- chrome.exe (PID: 2588)
- WinRAR.exe (PID: 1636)
Create files in a temporary directory
- Setup.exe (PID: 2508)
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 2768)
Checks supported languages
- Installer.exe (PID: 4000)
- Setup.exe (PID: 2508)
- DriverUpdater.exe (PID: 1636)
- DriverUpdater.exe (PID: 2768)
- 7z2201.exe (PID: 1192)
- CustomDllSurrogate.x32.exe (PID: 2300)
Reads the computer name
- Installer.exe (PID: 4000)
- Setup.exe (PID: 2508)
- DriverUpdater.exe (PID: 1636)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Checks proxy server information
- Setup.exe (PID: 2508)
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Reads the machine GUID from the registry
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Creates files in the program directory
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- regsvr32.exe (PID: 4072)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Process checks computer location settings
- Installer.exe (PID: 4000)
- Setup.exe (PID: 2508)
- DriverUpdater.exe (PID: 2768)
Reads the software policy settings
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Reads Windows Product ID
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 1636)
- DriverUpdater.exe (PID: 2768)
Creates files or folders in the user directory
- Installer.exe (PID: 4000)
- DriverUpdater.exe (PID: 2768)
- CustomDllSurrogate.x32.exe (PID: 2300)
Reads Microsoft Office registry keys
- DriverUpdater.exe (PID: 2768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
108
Monitored processes
47
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2152 --field-trial-handle=1156,i,7376541474876779725,7006639136730019034,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 480 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 696 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver "-an=C:\Users\admin\Downloads\Outbyte Driver Updater 2.2.3.15993 Multilingual [FileCR]\Outbyte Driver Updater 2.2.3.15993 Multilingual\Crack\Crack Driver Updater\lc.7z" -ad1 -- "C:\Users\admin\Downloads\Outbyte Driver Updater 2.2.3.15993 Multilingual [FileCR]\Outbyte Driver Updater 2.2.3.15993 Multilingual\Crack\Crack Driver Updater\Pro.7z" "C:\Users\admin\Downloads\Outbyte Driver Updater 2.2.3.15993 Multilingual [FileCR]\Outbyte Driver Updater 2.2.3.15993 Multilingual\Crack\Crack Driver Updater\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
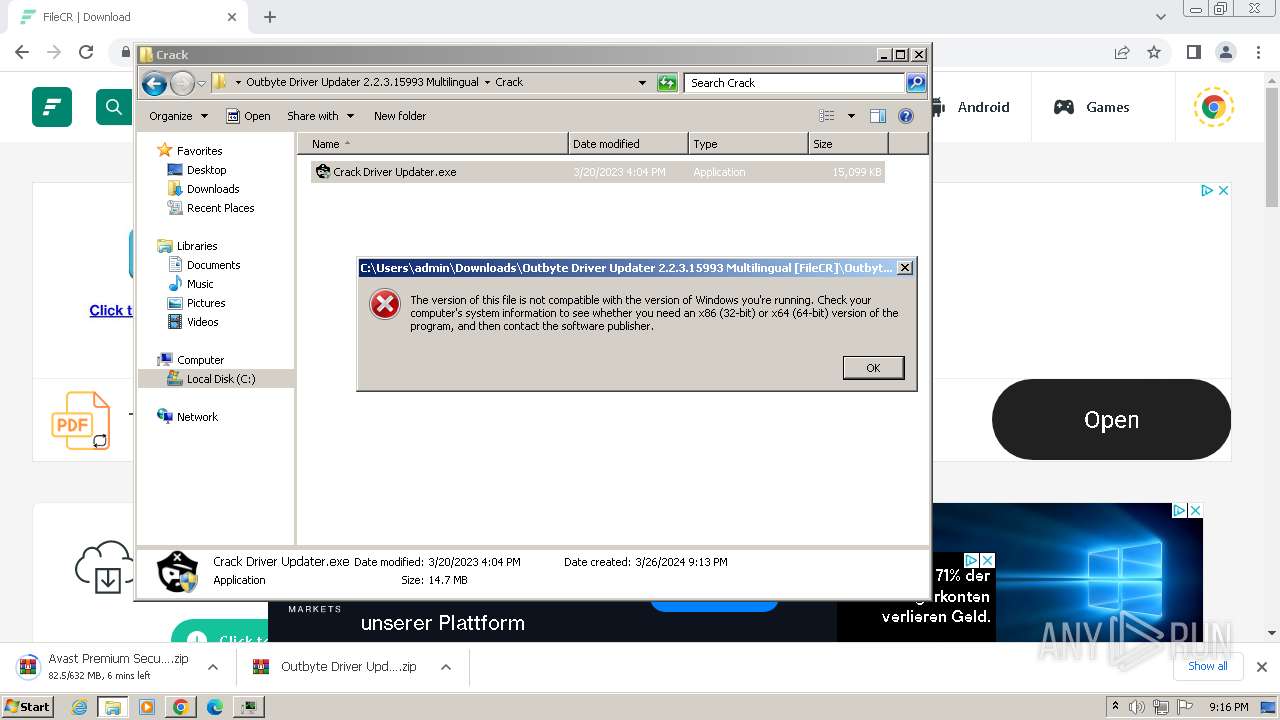
| 920 | "C:\Program Files\Outbyte\Driver Updater\DriverUpdater.exe" | C:\Program Files\Outbyte\Driver Updater\DriverUpdater.exe | — | explorer.exe | |||||||||||
User: admin Company: Outbyte Integrity Level: MEDIUM Description: Driver Updater Exit code: 3221226540 Version: 2.2.3.15993 Modules
| |||||||||||||||
| 1192 | "C:\Users\admin\Downloads\Outbyte Driver Updater 2.2.3.15993 Multilingual [FileCR]\Outbyte Driver Updater 2.2.3.15993 Multilingual\Crack\Crack Driver Updater\7z2201.exe" | C:\Users\admin\Downloads\Outbyte Driver Updater 2.2.3.15993 Multilingual [FileCR]\Outbyte Driver Updater 2.2.3.15993 Multilingual\Crack\Crack Driver Updater\7z2201.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 1 Version: 22.01 Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\Downloads\Outbyte Driver Updater 2.2.3.15993 Multilingual [FileCR]\Outbyte Driver Updater 2.2.3.15993 Multilingual\Setup.exe" | C:\Users\admin\Downloads\Outbyte Driver Updater 2.2.3.15993 Multilingual [FileCR]\Outbyte Driver Updater 2.2.3.15993 Multilingual\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Outbyte Integrity Level: MEDIUM Description: Outbyte Driver Updater Installation File Exit code: 3221226540 Version: 2.2.3.15993 Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=4380 --field-trial-handle=1156,i,7376541474876779725,7006639136730019034,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=4428 --field-trial-handle=1156,i,7376541474876779725,7006639136730019034,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2108 --field-trial-handle=1156,i,7376541474876779725,7006639136730019034,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
88 018
Read events
87 274
Write events
643
Delete events
101
Modification events
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 939896080 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31096770 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31096770 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
95
Suspicious files
63
Text files
86
Unknown types
359
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab2219.tmp | compressed | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab222B.tmp | compressed | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar222C.tmp | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar221A.tmp | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
68
TCP/UDP connections
113
DNS requests
125
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3092 | iexplore.exe | GET | 304 | 184.24.77.203:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f78d505714a595e3 | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 184.24.77.173:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1092bf53f2b6a28c | unknown | — | — | unknown |
2120 | iexplore.exe | GET | 304 | 184.24.77.203:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4dd617501e33218a | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 304 | 184.24.77.173:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x2.c.lencr.org/ | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 184.24.77.203:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1c38e09e3428bf6c | unknown | — | — | unknown |
2120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
4000 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAsllCLO2YEqFaBOmVKKDvo%3D | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3092 | iexplore.exe | 188.114.96.3:443 | filecr.com | CLOUDFLARENET | NL | unknown |
3092 | iexplore.exe | 184.24.77.173:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3092 | iexplore.exe | 184.24.77.203:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3092 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
2120 | iexplore.exe | 188.114.96.3:443 | filecr.com | CLOUDFLARENET | NL | unknown |
2120 | iexplore.exe | 184.24.77.203:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2120 | iexplore.exe | 104.126.37.161:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
filecr.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Installer.exe | Thread Exiting: 2976 |
DriverUpdater.exe | Begin logger initialization...
|
DriverUpdater.exe | Initializing thread ID = 0xACC - Context: DriverHiveEngine - entry point
|
DriverUpdater.exe | Executable: C:\Program Files\Outbyte\Driver Updater\DriverUpdater.exe
|
DriverUpdater.exe | Version: 1.0.20.23
|
DriverUpdater.exe | EL not enabled
|
DriverUpdater.exe | Maximum filesize set to 4194304 bytes
|
DriverUpdater.exe | ME not enabled
|
DriverUpdater.exe | End logger initialization
|
DriverUpdater.exe | [2024-03-26 21:16:41:351] [dhEngineInit] Default Locale ID: 1033
|