analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
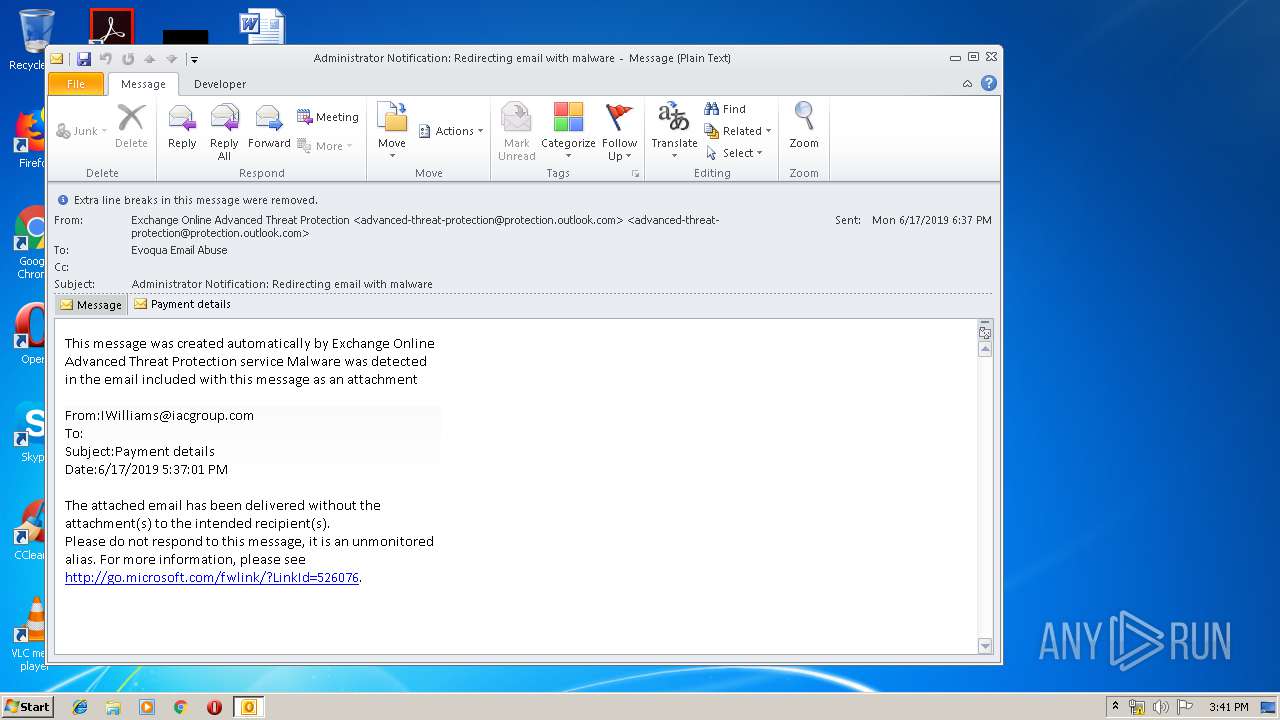
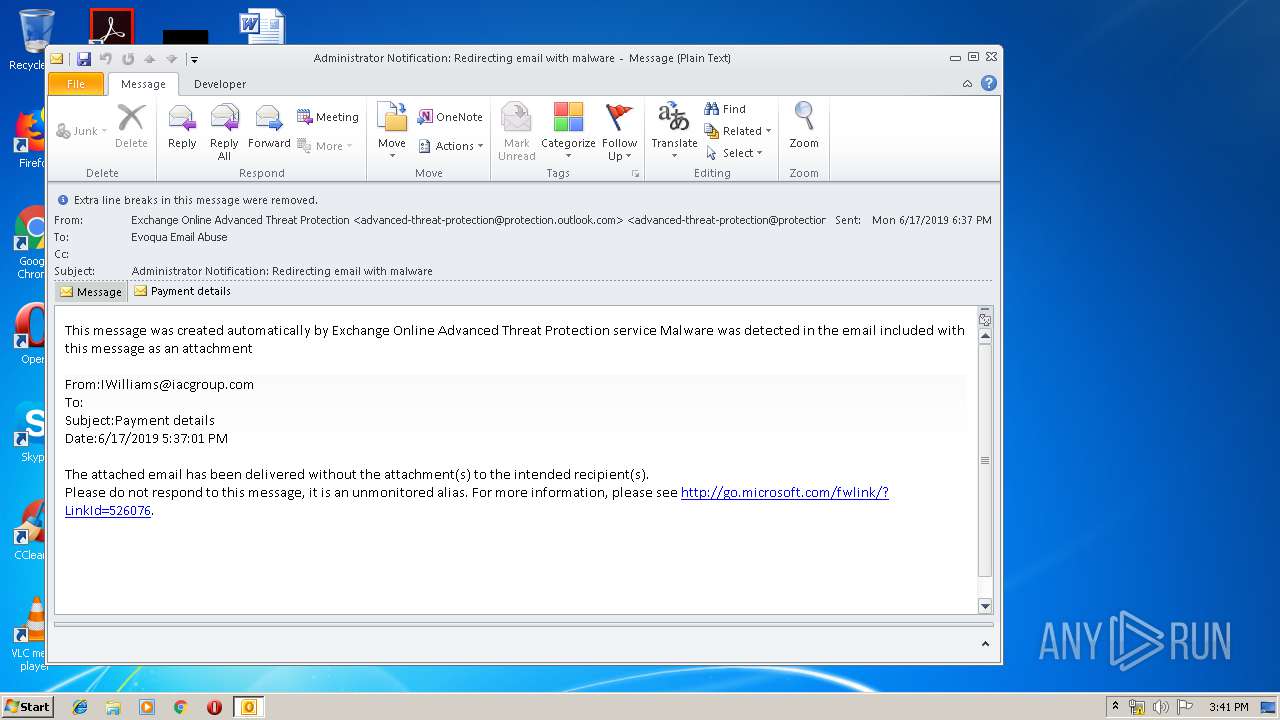
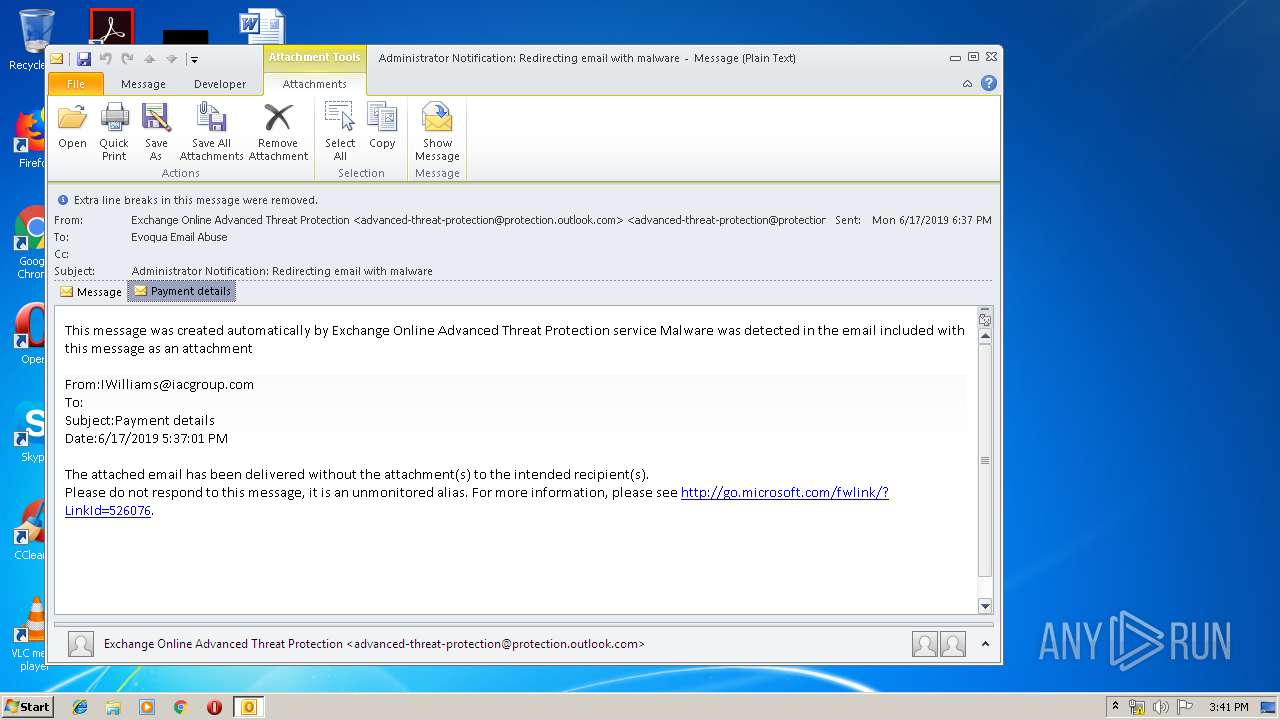
| File name: | Administrator Notification_ Redirecting email with malware.msg |
| Full analysis: | https://app.any.run/tasks/405ed262-2492-487a-88ba-c8bcb257ed7d |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 14:40:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | C0BC673C18176961D74D3C1D1AB3DD62 |
| SHA1: | 56FD4B7F860089DECDE34E7F9C4D3F49EDC627CE |
| SHA256: | F7D296CA2106CEDCE388A6266620823FB2E2026AF25F2D212E4BE569A6581CBC |
| SSDEEP: | 6144:lIEZd5jYsNll7TfXWdMOQRqQppNc3k/TrGyGuUC:lZZdlTPfWdBQp4kPGyG |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3144)
SUSPICIOUS
Starts Internet Explorer
- xpsrchvw.exe (PID: 2920)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3144)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3144)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2632)
Changes internet zones settings
- iexplore.exe (PID: 1856)
Creates files in the user directory
- iexplore.exe (PID: 2632)
Reads internet explorer settings
- iexplore.exe (PID: 2632)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
38
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3144 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Administrator Notification_ Redirecting email with malware.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 14.0.6025.1000 | ||||
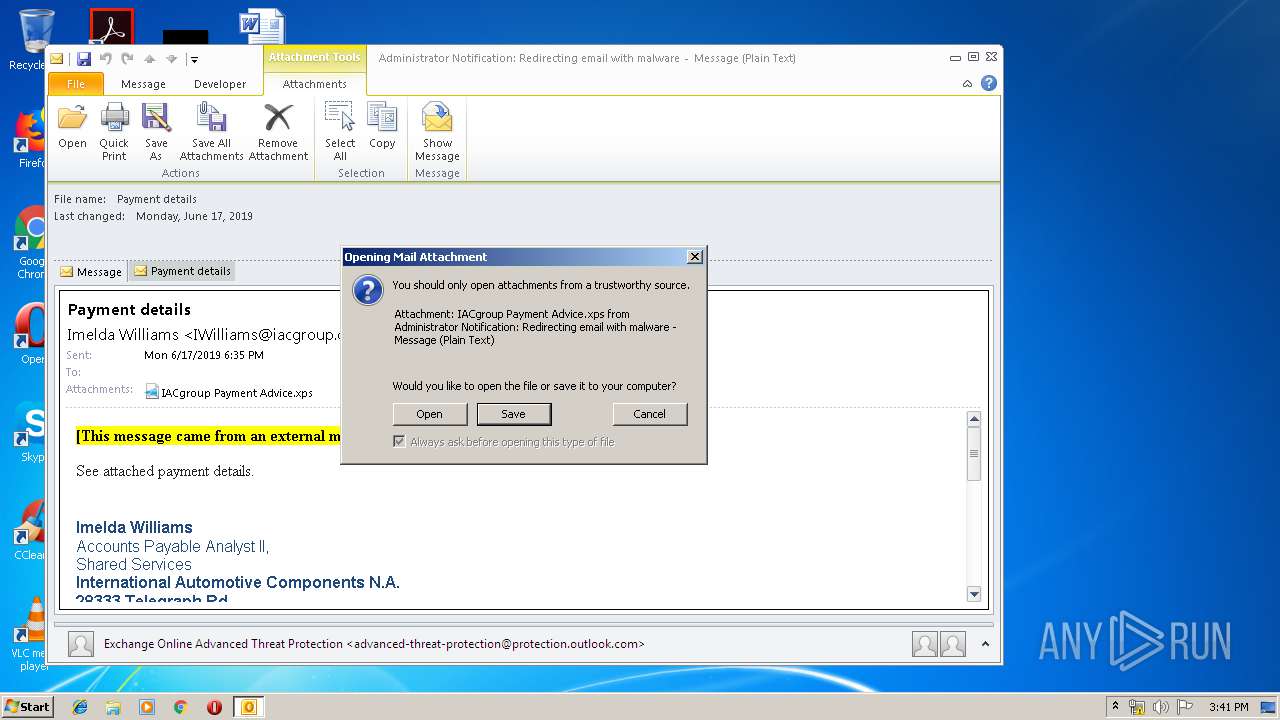
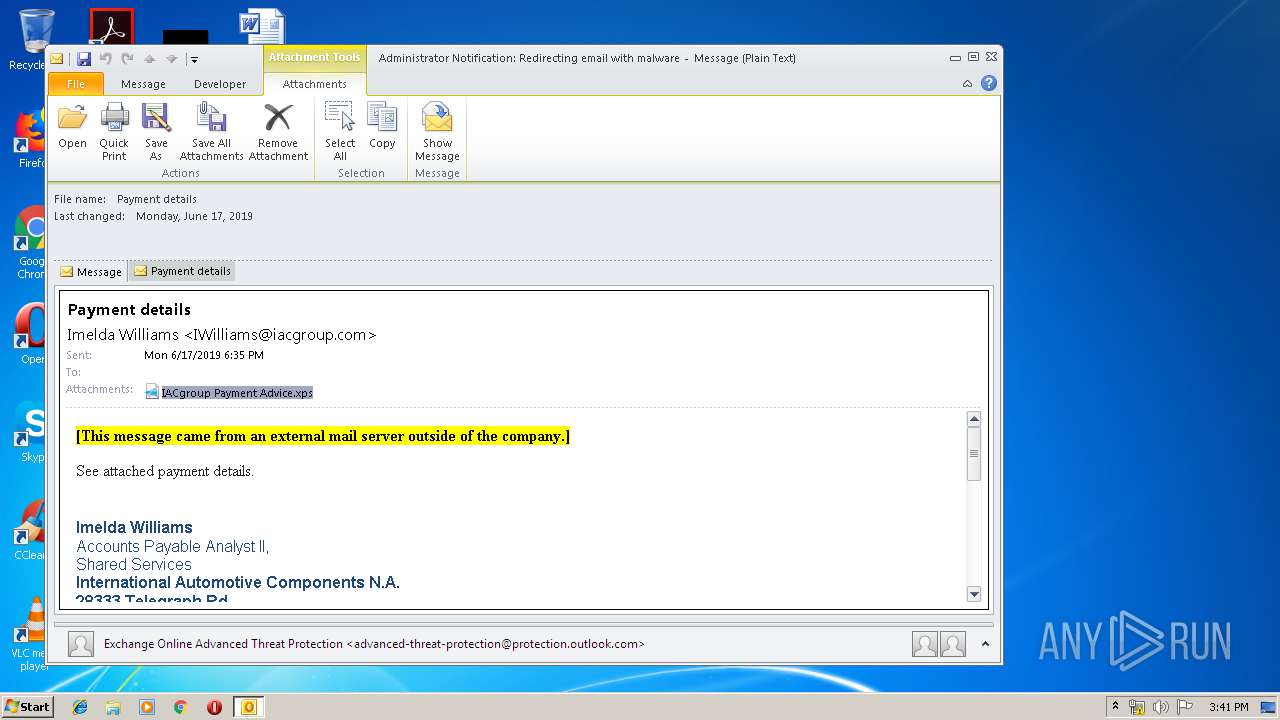
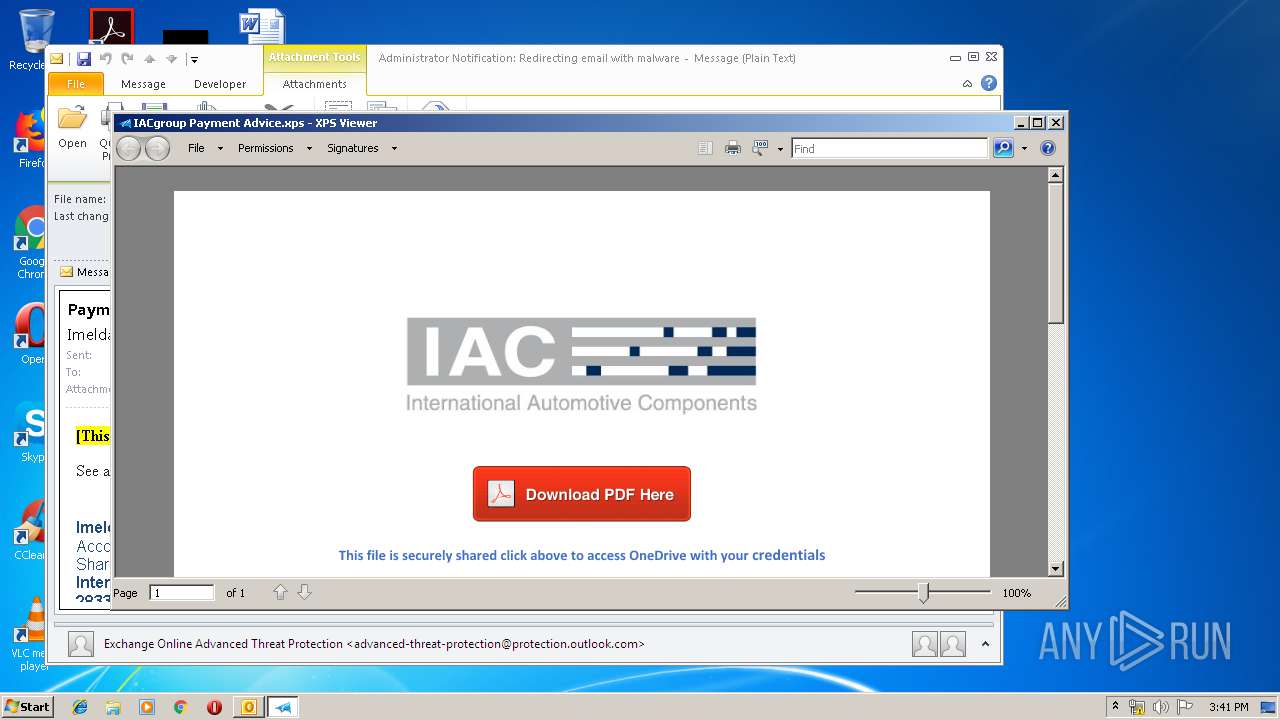
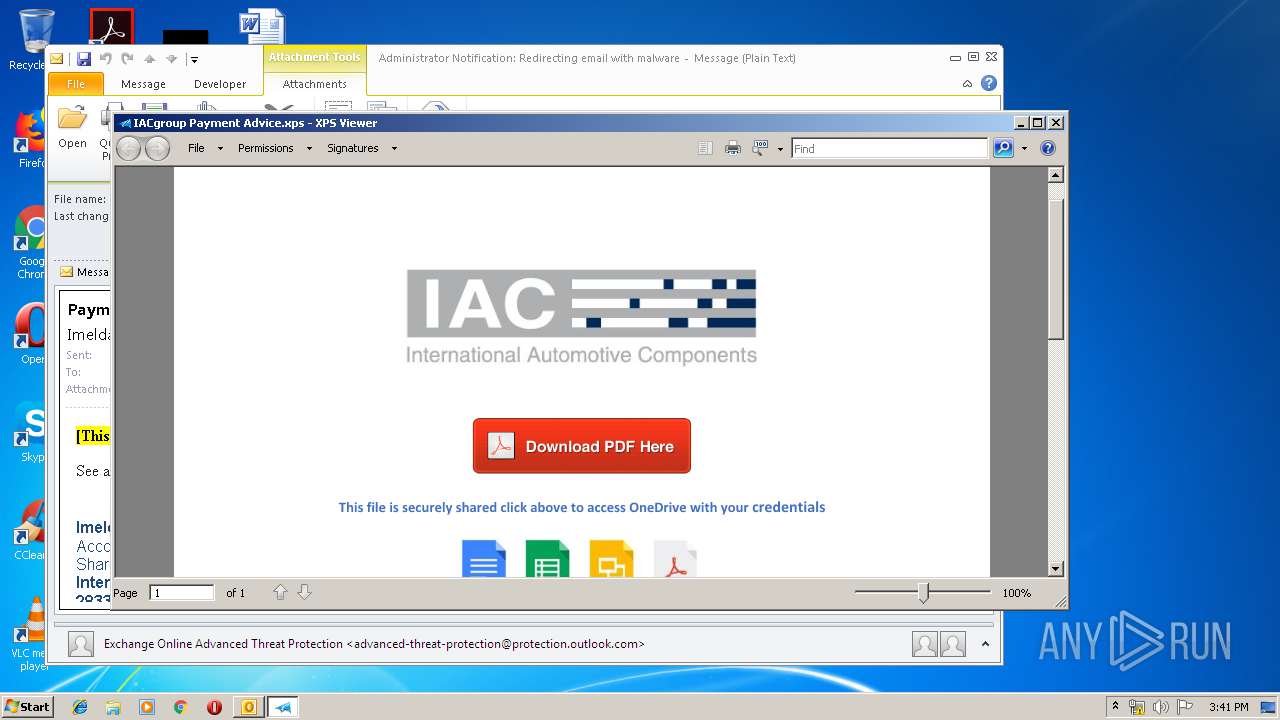
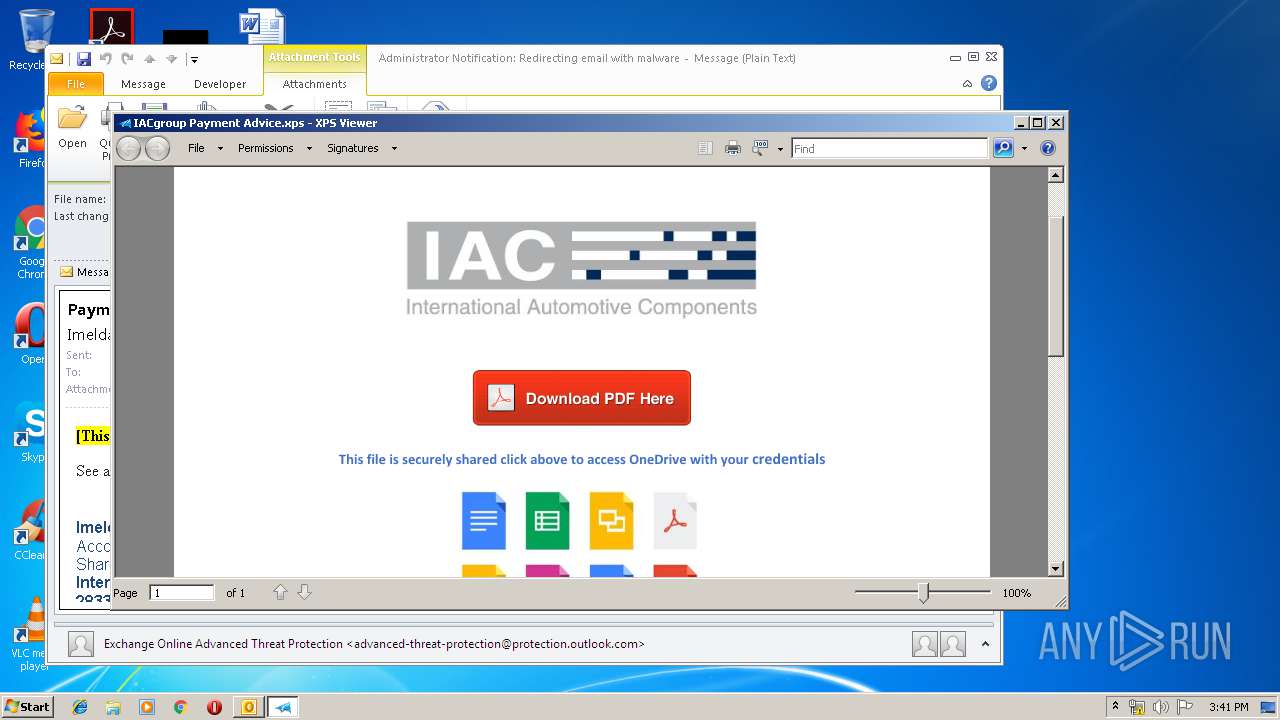
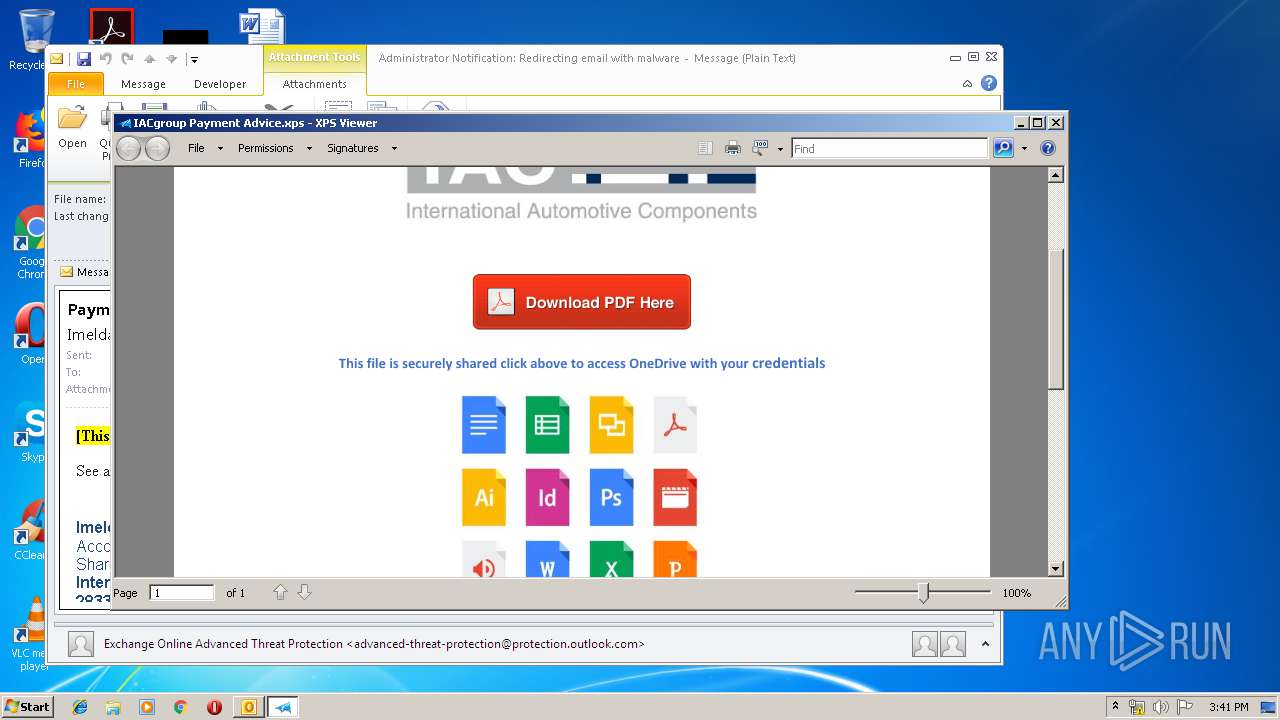
| 2920 | "C:\Windows\System32\xpsrchvw.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\FT0SYOAQ\IACgroup Payment Advice.xps" | C:\Windows\System32\xpsrchvw.exe | — | OUTLOOK.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: XPS Viewer Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1856 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | xpsrchvw.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 2632 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1856 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
1 944
Read events
1 460
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
40
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVREF10.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF137432B4FD44D9BD.TMP | — | |
MD5:— | SHA256:— | |||
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\FT0SYOAQ\IACgroup Payment Advice (2).xps\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:3E531B4A4CC2682C75E0C80FC790FCB7 | SHA256:9AF2D1B9C671AED76EFBF5E1EFB3364830BDBAE211EFD5A5B7E9EC5A16BDD29F | |||
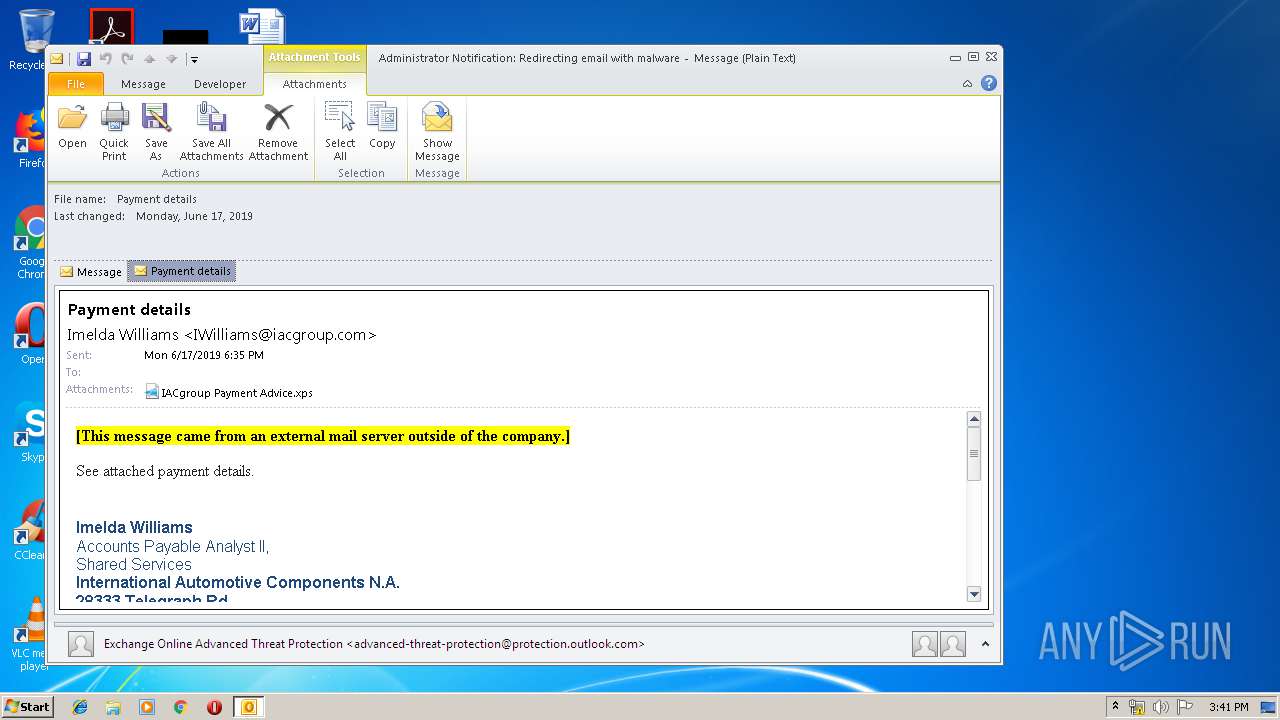
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\FT0SYOAQ\Payment details.msg | msg | |
MD5:41B063D31859093D12F690C63A0D59BB | SHA256:6C48C74DBBACFC176FDBC3F7FA1371642DC18B81EC5428205AD10165CB1CF04E | |||
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\FT0SYOAQ\IACgroup Payment Advice (2).xps | oxps | |
MD5:2E337E8CF75225CECA2197F2B0561A63 | SHA256:A5818ED8DD2BB0EF1BB5209A5382C3F14EF66D07275FC8419A6E0DF1671A8DD2 | |||
| 2920 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.ailh7a76vwgaw574kgr67eozf.tmp | text | |
MD5:456C25473B72C162508A8FC9A8BD5442 | SHA256:A833264F463468C1ABC906FB3215B6FCEC0D3CDD651AF1ECB86C493BA7789808 | |||
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_C671A99D9190F047964F125367F45A06.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 2920 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.20ip6ldoz404v5k_ir746tbtf.tmp | ttf | |
MD5:3040C485CFE4C419E2CAA648A30C6DA2 | SHA256:8DF3A80A8D9E6DD7D59DEF02929E9AAC0F58AE5BB3F3C2350793FAE902412537 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3144 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
1856 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3144 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
— | — | 172.217.16.206:80 | — | Google Inc. | US | whitelisted |
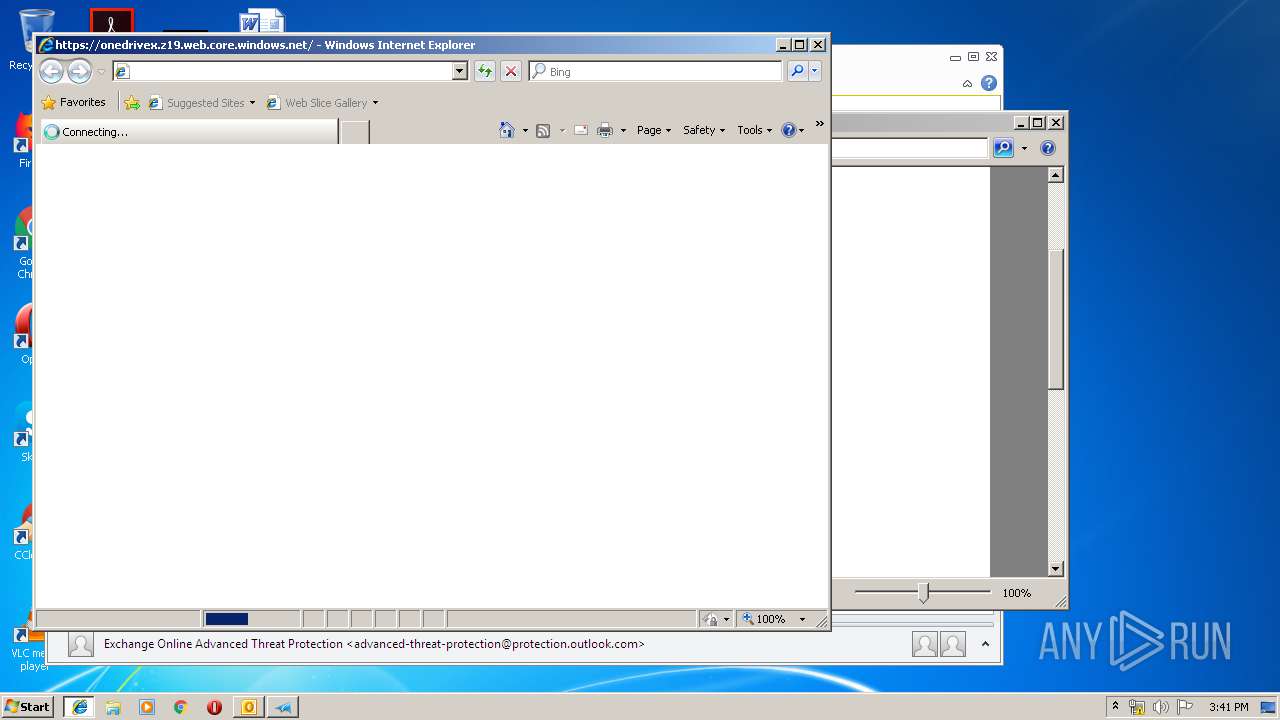
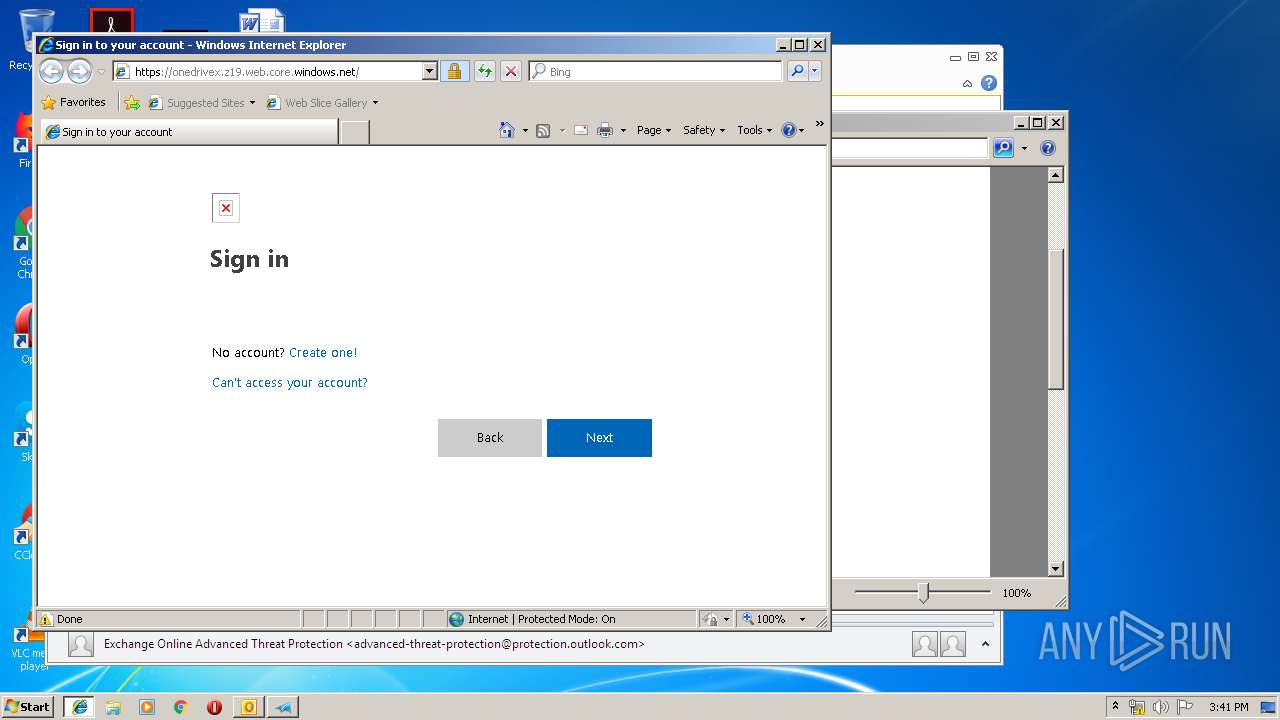
2632 | iexplore.exe | 52.239.177.65:443 | onedrivex.z19.web.core.windows.net | Microsoft Corporation | US | suspicious |
— | — | 52.239.177.65:443 | onedrivex.z19.web.core.windows.net | Microsoft Corporation | US | suspicious |
2632 | iexplore.exe | 205.185.208.52:443 | code.jquery.com | Highwinds Network Group, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
onedrivex.z19.web.core.windows.net |
| unknown |
code.jquery.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Lookup for Possible Common Brand Phishing Hosted on Legitimate Windows Service |
2632 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Request for Possible Common Brand Phishing Hosted on Legitimate Windows Service |