| File name: | Valorant.exe |
| Full analysis: | https://app.any.run/tasks/1d0642bd-a900-4833-a9ce-85b1f14384ce |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2025, 11:55:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 5DAFB369BD87C4D1627D4FB45A7C02E5 |
| SHA1: | BD9CC4D55F25B3684188FB284888655102751D52 |
| SHA256: | F7C5B4AA656892A9FCF825F27F83B43BBC67EDD013F138CB9A5483B6BA2D52FA |
| SSDEEP: | 98304:rC3CpA2vGuddqF3kTWSZhPLTLaMvZA4OF6ZEWU0tTqlqJ3k3czL36BeA9T9iplO5:+51UnUPbyhG+65 |
MALICIOUS
Changes the autorun value in the registry
- Valorant.exe (PID: 6668)
SUSPICIOUS
Process drops python dynamic module
- Valorant.exe (PID: 2116)
Executable content was dropped or overwritten
- Valorant.exe (PID: 2116)
Process drops legitimate windows executable
- Valorant.exe (PID: 2116)
The process drops C-runtime libraries
- Valorant.exe (PID: 2116)
Application launched itself
- Valorant.exe (PID: 2116)
Loads Python modules
- Valorant.exe (PID: 6668)
Reads security settings of Internet Explorer
- Valorant.exe (PID: 6668)
Reads the date of Windows installation
- Valorant.exe (PID: 6668)
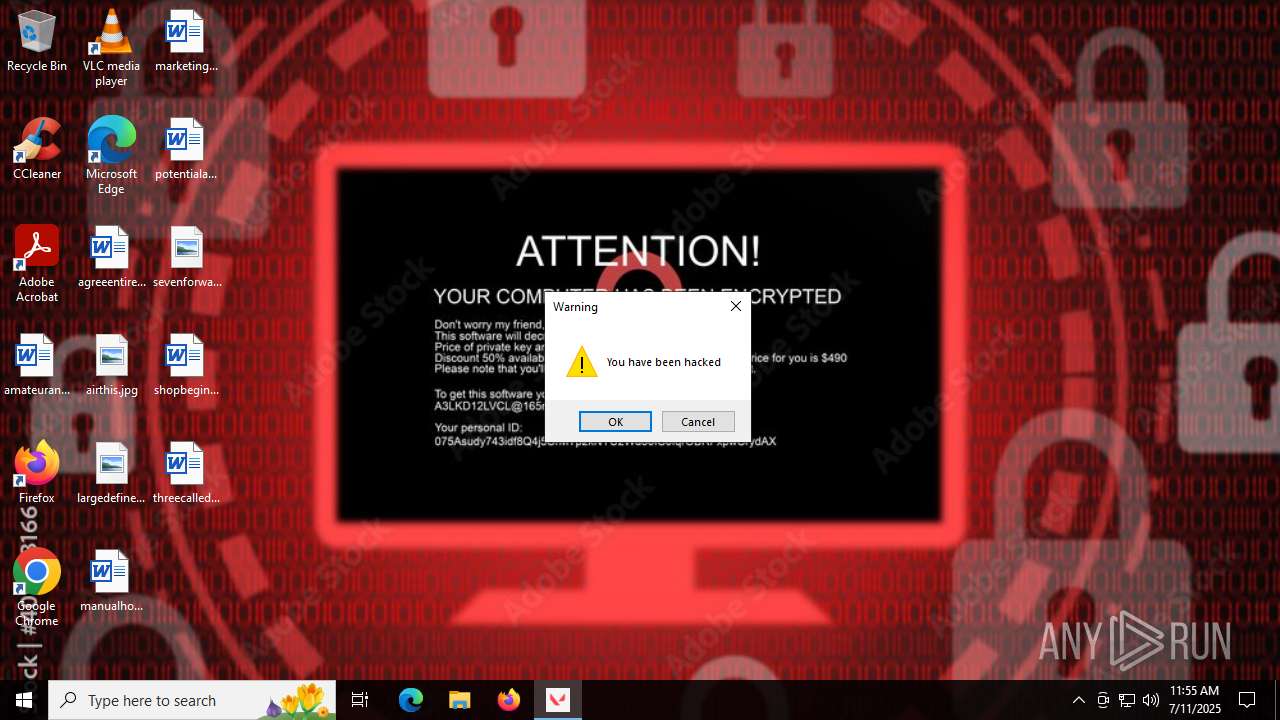
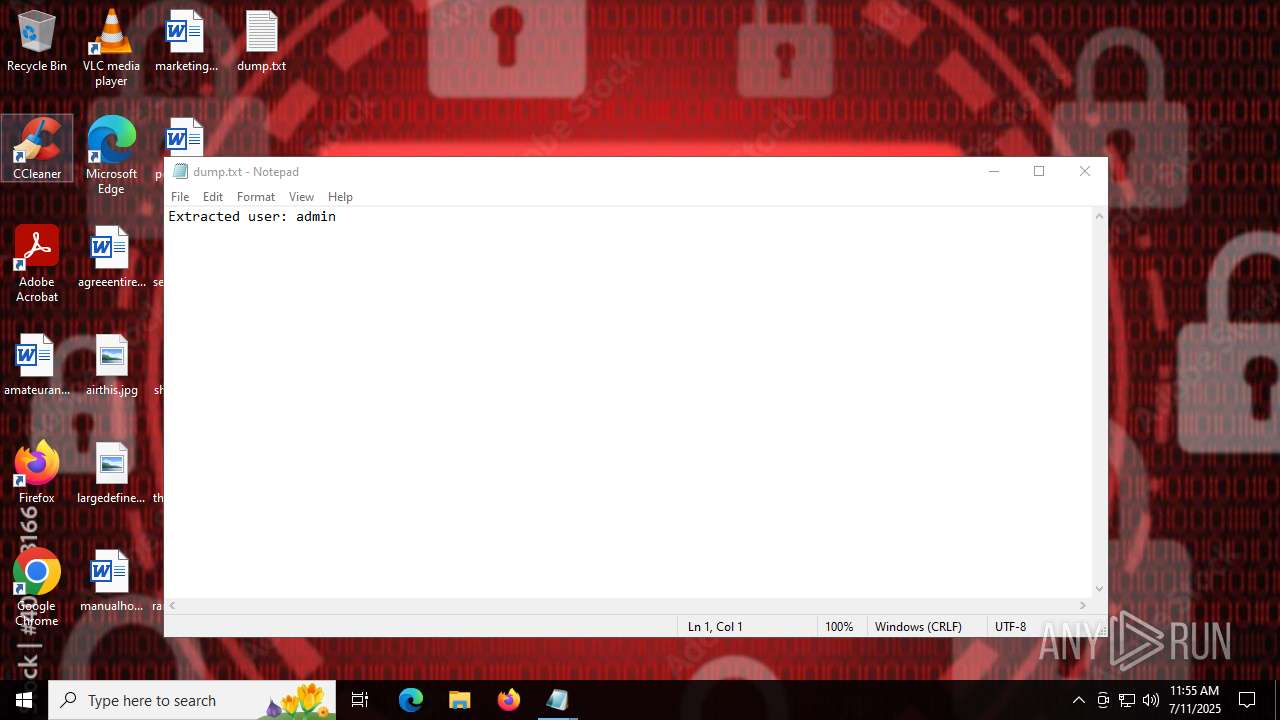
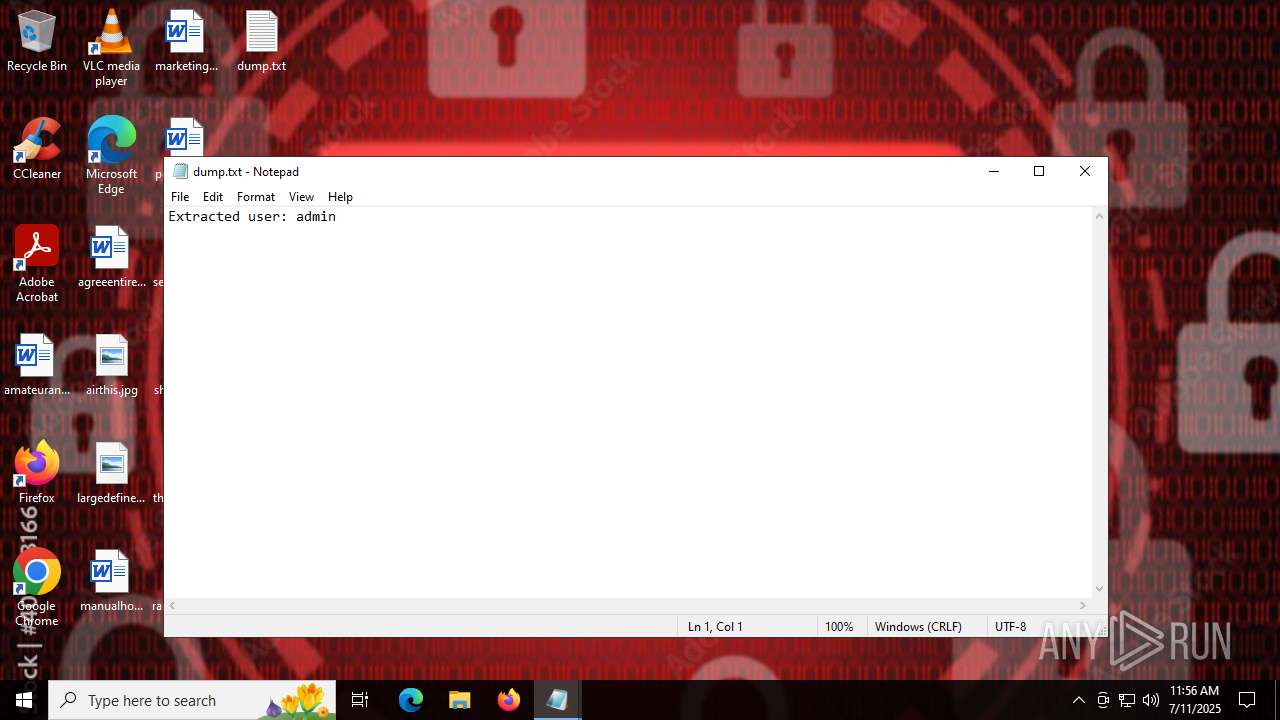
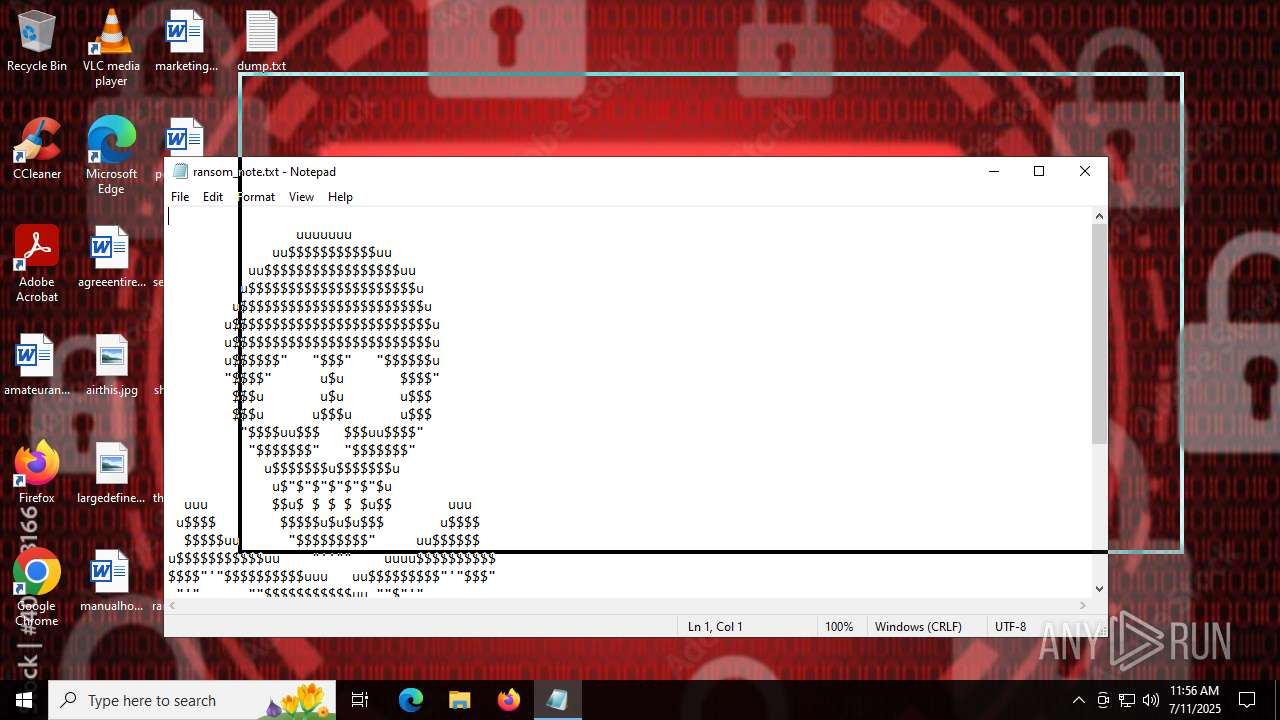
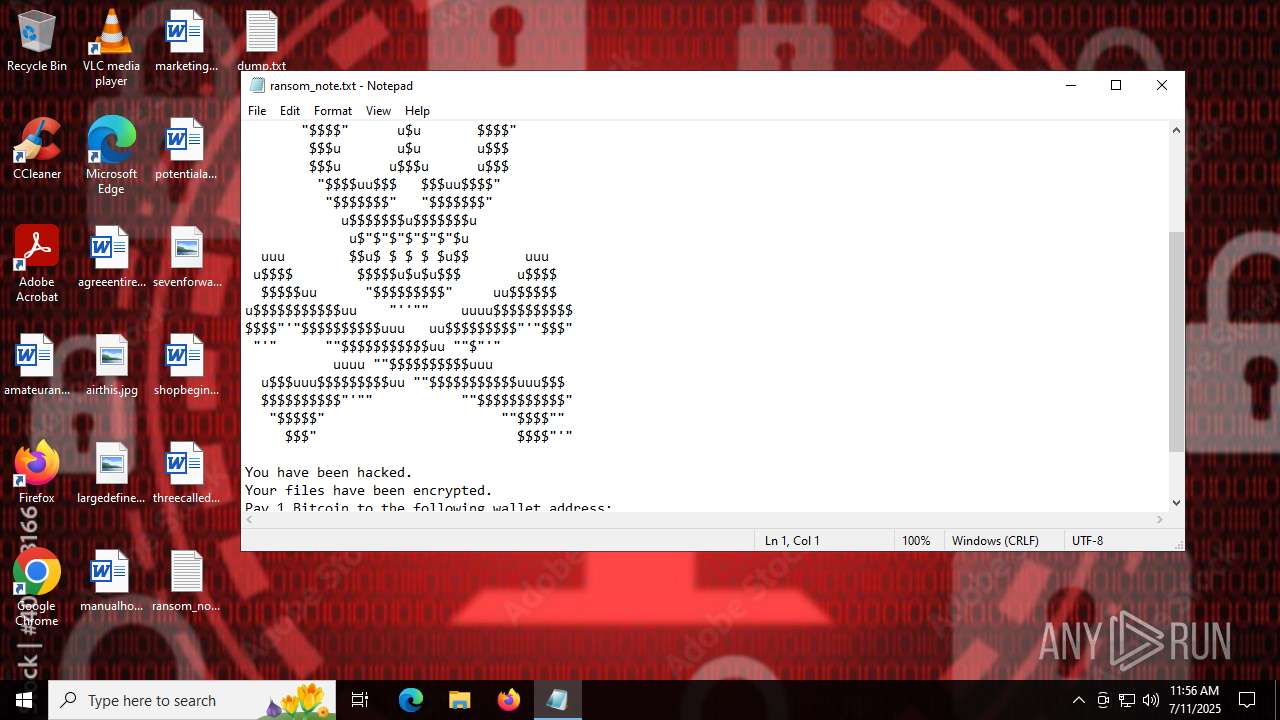
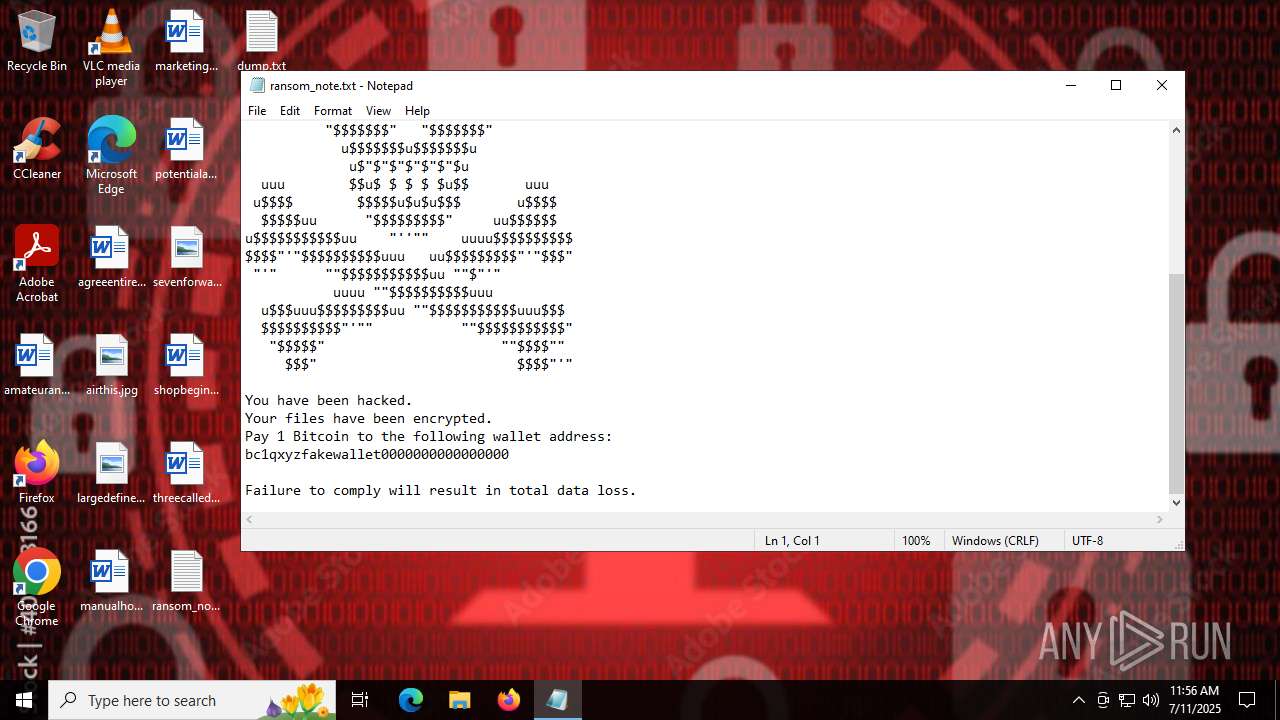
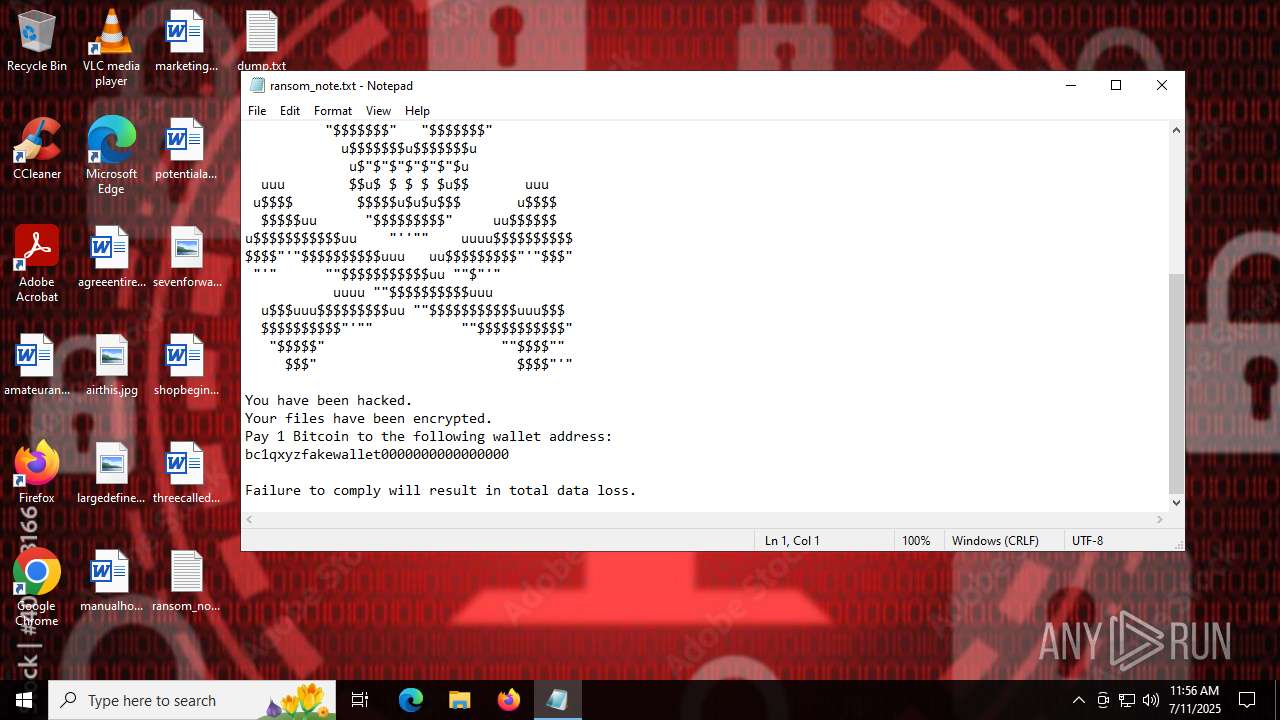
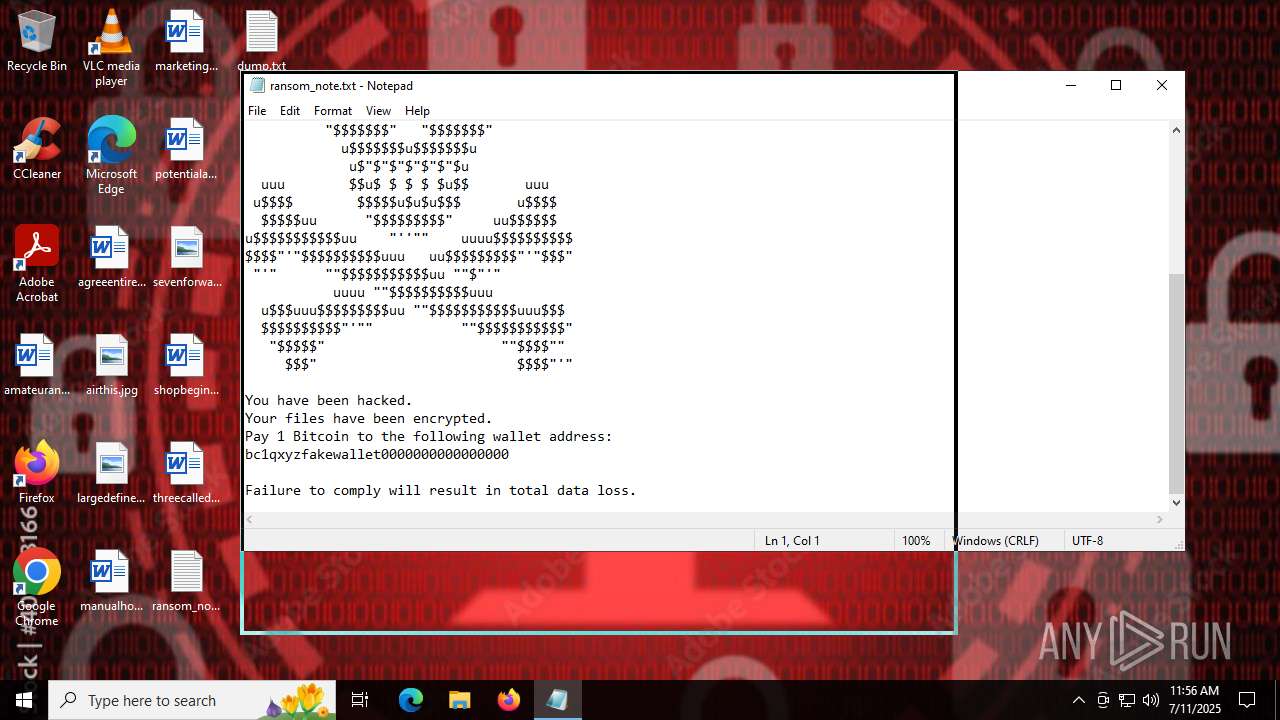
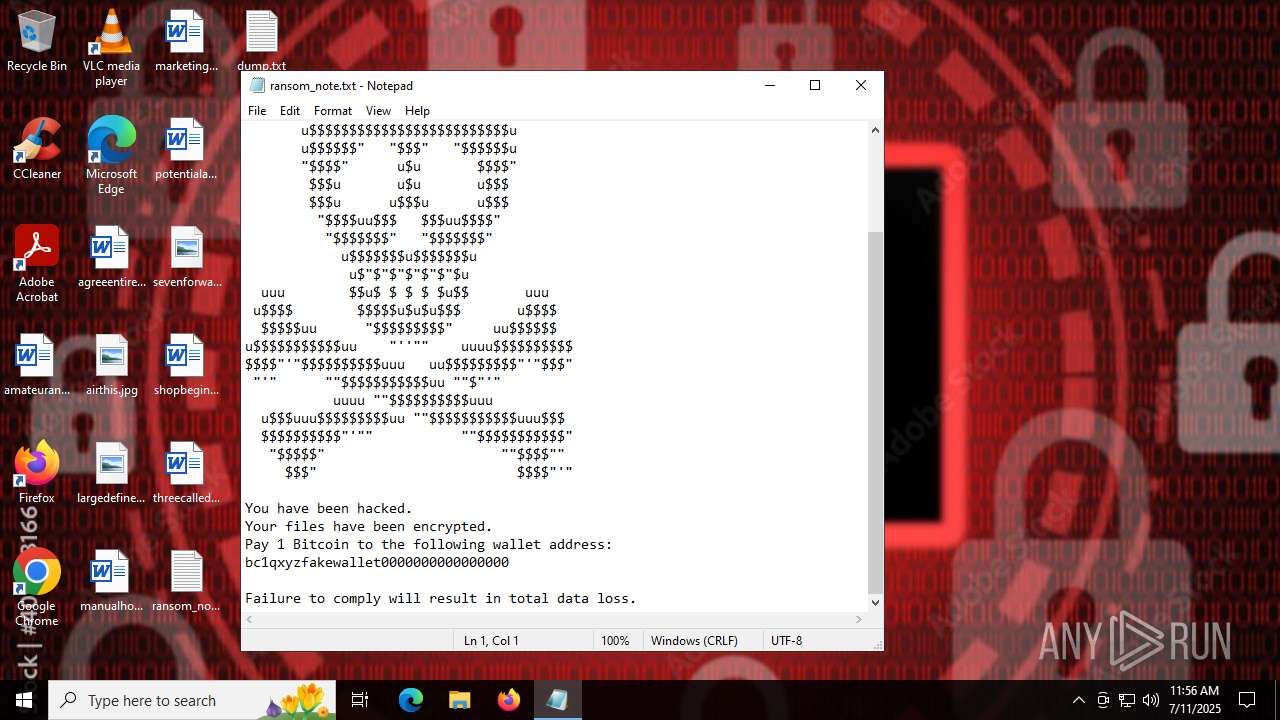
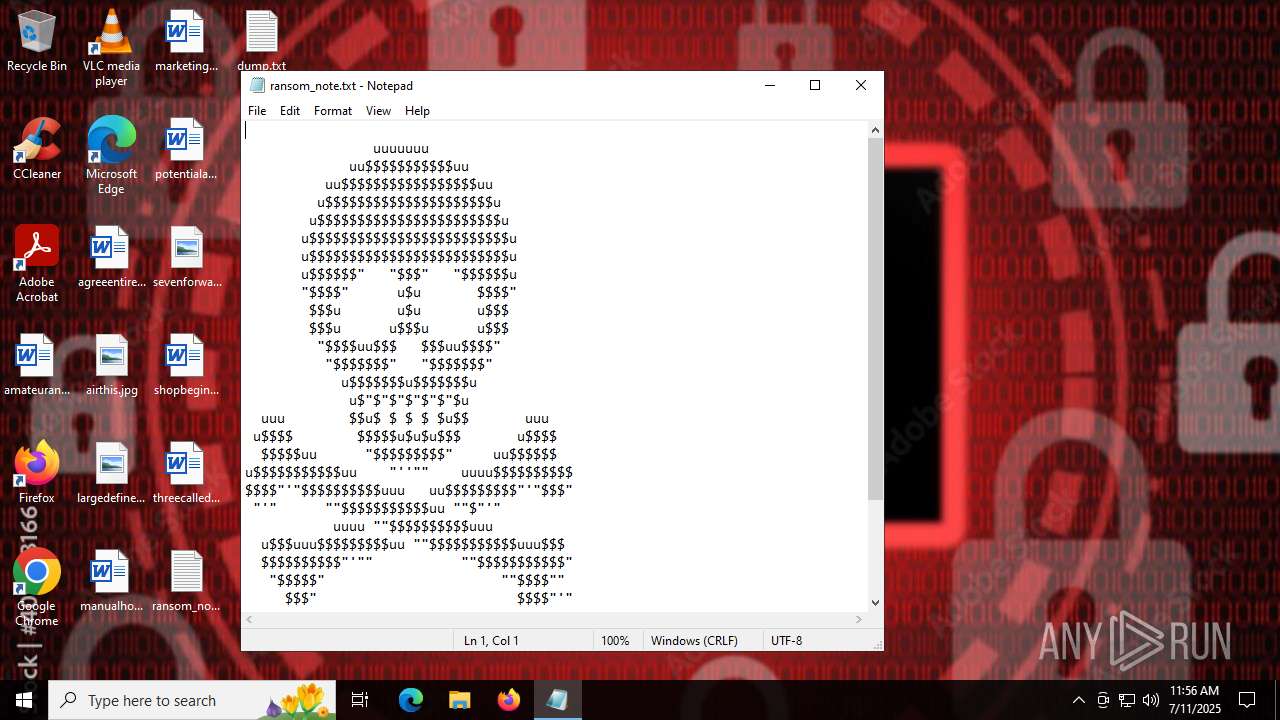
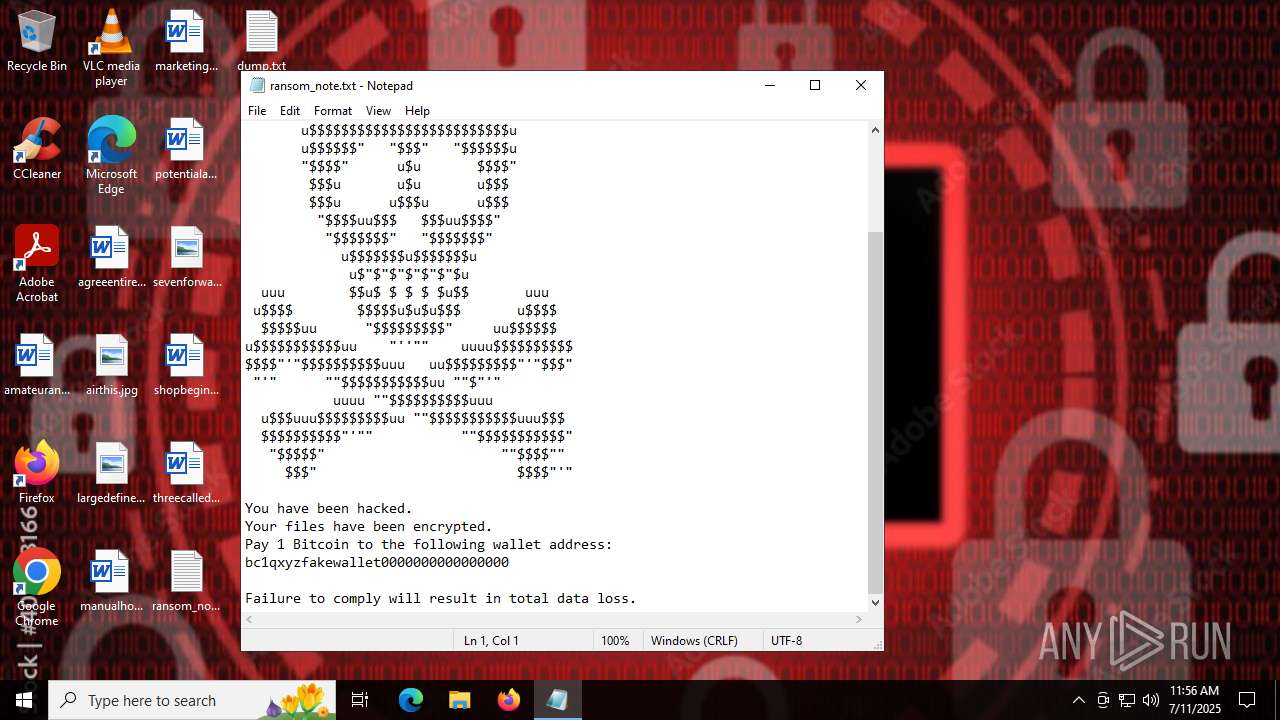
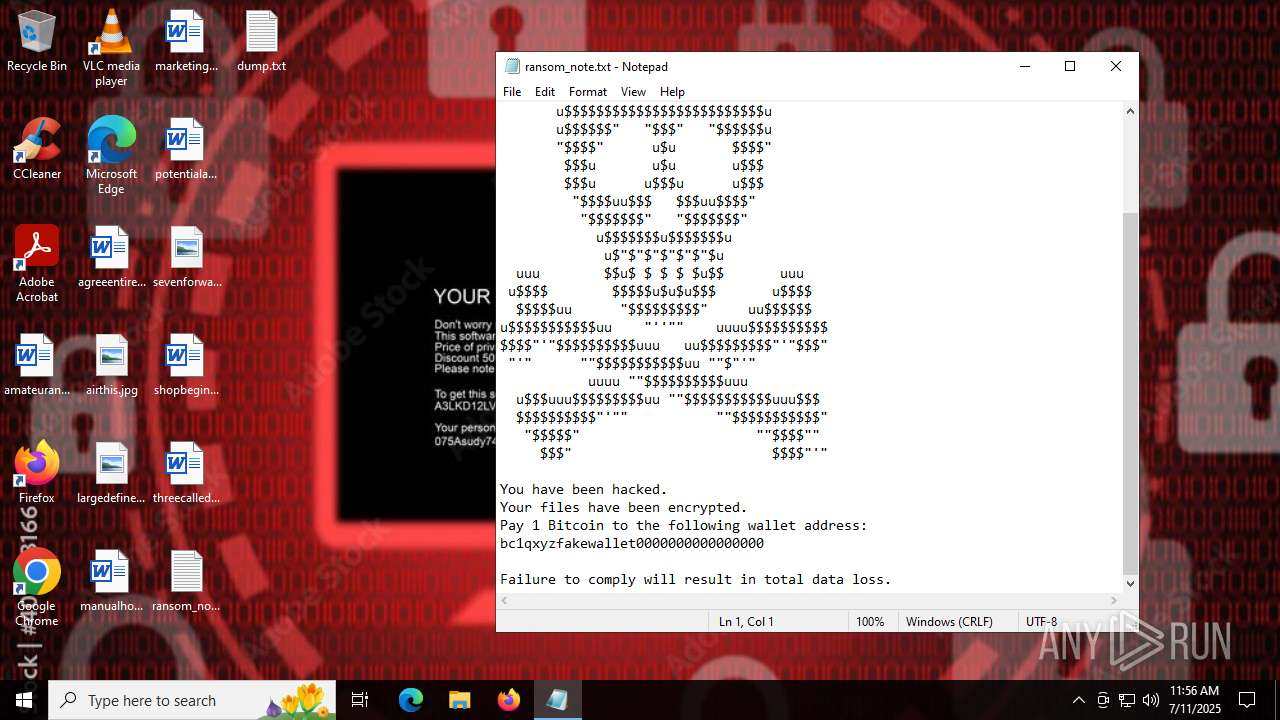
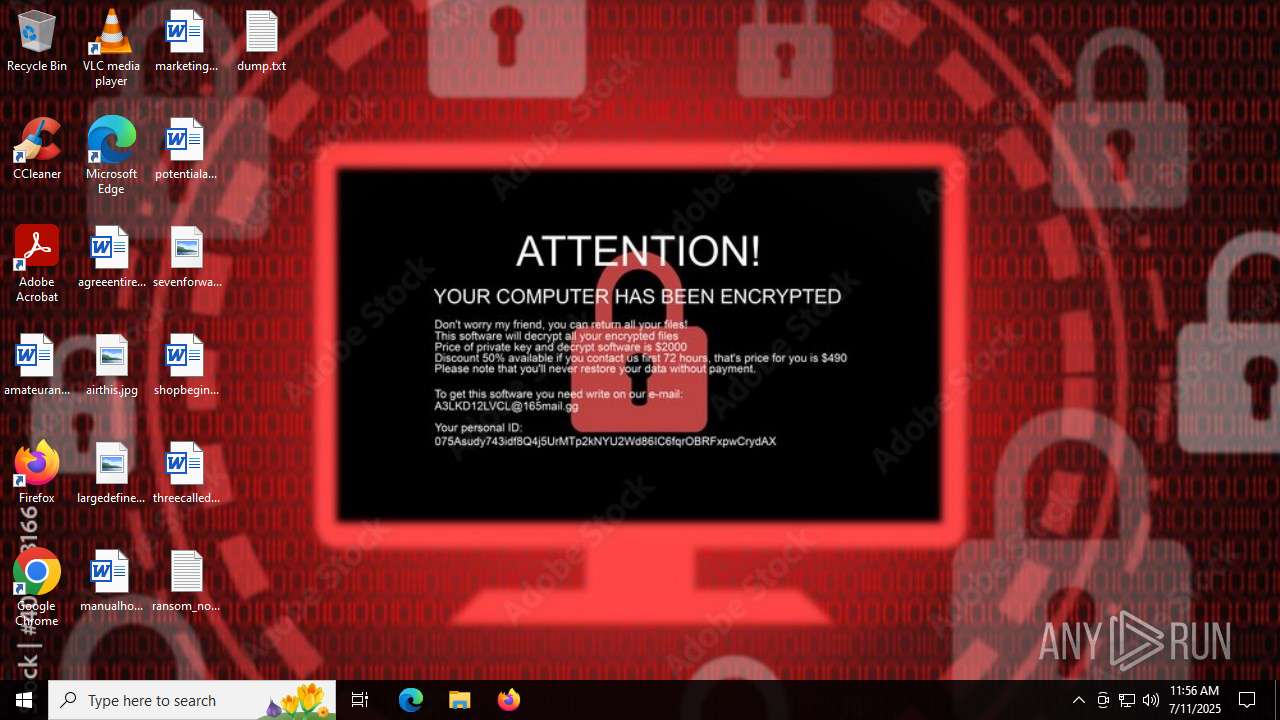
Start notepad (likely ransomware note)
- Valorant.exe (PID: 6668)
INFO
Create files in a temporary directory
- Valorant.exe (PID: 2116)
- Valorant.exe (PID: 6668)
Checks supported languages
- Valorant.exe (PID: 2116)
- Valorant.exe (PID: 6668)
The sample compiled with english language support
- Valorant.exe (PID: 2116)
Reads the computer name
- Valorant.exe (PID: 2116)
- Valorant.exe (PID: 6668)
Checks proxy server information
- Valorant.exe (PID: 6668)
PyInstaller has been detected (YARA)
- Valorant.exe (PID: 2116)
Reads Microsoft Office registry keys
- Valorant.exe (PID: 6668)
Launching a file from a Registry key
- Valorant.exe (PID: 6668)
Process checks computer location settings
- Valorant.exe (PID: 6668)
Creates files or folders in the user directory
- Valorant.exe (PID: 6668)
Reads security settings of Internet Explorer
- notepad.exe (PID: 316)
- notepad.exe (PID: 5504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:07:11 11:54:52+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 174592 |
| InitializedDataSize: | 270848 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd0d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Adobe Systems Incorporated |
| FileDescription: | Adobe Updater Utility |
| FileVersion: | 1.0.0.0 |
| InternalName: | AdobeUpdater.exe |
| LegalCopyright: | © Adobe Systems. All rights reserved. |
| OriginalFileName: | AdobeUpdater.exe |
| ProductName: | Adobe Updater |
| ProductVersion: | 1.0.0.0 |
Total processes
140
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\dump.txt | C:\Windows\System32\notepad.exe | — | Valorant.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2116 | "C:\Users\admin\AppData\Local\Temp\Valorant.exe" | C:\Users\admin\AppData\Local\Temp\Valorant.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Updater Utility Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3624 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
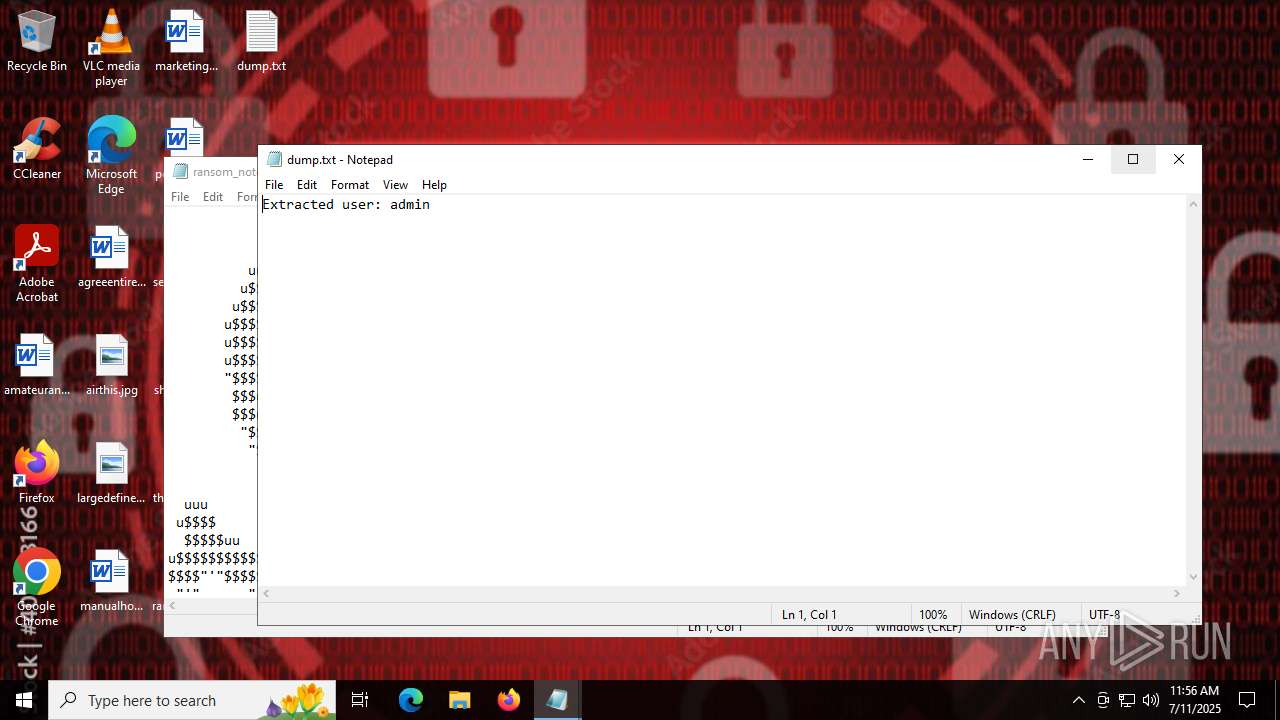
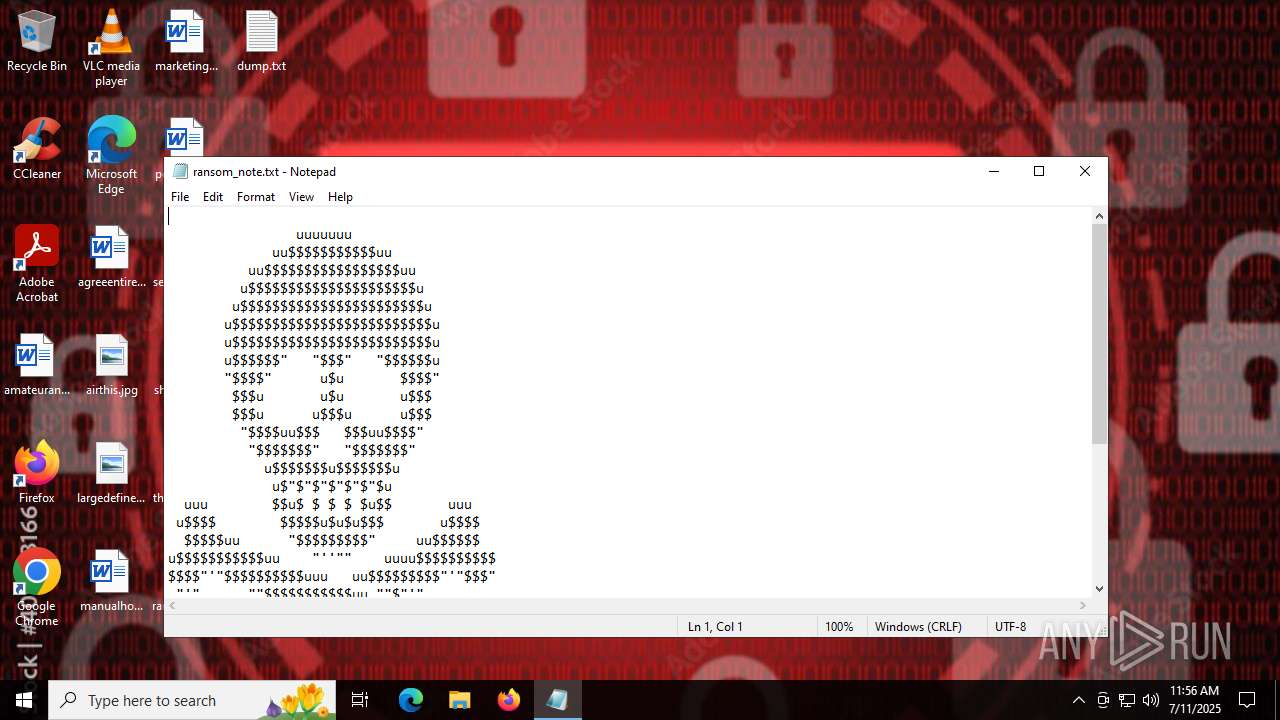
| 5504 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\ransom_note.txt | C:\Windows\System32\notepad.exe | — | Valorant.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6668 | "C:\Users\admin\AppData\Local\Temp\Valorant.exe" | C:\Users\admin\AppData\Local\Temp\Valorant.exe | Valorant.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Updater Utility Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
4 460
Read events
4 449
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6668) Valorant.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (6668) Valorant.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | FakeUpdater |
Value: C:\Users\admin\Desktop\ransom_note.txt | |||
| (PID) Process: | (316) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 250 | |||
| (PID) Process: | (316) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 144 | |||
| (PID) Process: | (316) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (316) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 489 | |||
| (PID) Process: | (5504) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 488 | |||
| (PID) Process: | (5504) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 51 | |||
| (PID) Process: | (5504) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 659 | |||
| (PID) Process: | (5504) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 589 | |||
Executable files
53
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\_decimal.pyd | executable | |
MD5:F78F9855D2A7CA940B6BE51D68B80BF2 | SHA256:D4AE192BBD4627FC9487A2C1CD9869D1B461C20CFD338194E87F5CF882BBED12 | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:C5E3E5DF803C9A6D906F3859355298E1 | SHA256:956773A969A6213F4685C21702B9ED5BD984E063CF8188ACBB6D55B1D6CCBD4E | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:EA00855213F278D9804105E5045E2882 | SHA256:F2F74A801F05AB014D514F0F1D0B3DA50396E6506196D8BECCC484CD969621A6 | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:40BA4A99BF4911A3BCA41F5E3412291F | SHA256:AF0E561BB3B2A13AA5CA9DFC9BC53C852BAD85075261AF6EF6825E19E71483A6 | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:F1534C43C775D2CCEB86F03DF4A5657D | SHA256:6E6BFDC656F0CF22FABBA1A25A42B46120B1833D846F2008952FE39FE4E57AB2 | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\api-ms-win-core-heap-l1-1-0.dll | executable | |
MD5:6168023BDB7A9DDC69042BEECADBE811 | SHA256:4EA8399DEBE9D3AE00559D82BC99E4E26F310934D3FD1D1F61177342CF526062 | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:BCB8B9F6606D4094270B6D9B2ED92139 | SHA256:FA18D63A117153E2ACE5400ED89B0806E96F0627D9DB935906BE9294A3038118 | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:BFFFA7117FD9B1622C66D949BAC3F1D7 | SHA256:1EA267A2E6284F17DD548C6F2285E19F7EDB15D6E737A55391140CE5CB95225E | |||
| 2116 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\_MEI21162\_socket.pyd | executable | |
MD5:439B3AD279BEFA65BB40ECEBDDD6228B | SHA256:24017D664AF20EE3B89514539345CAAC83ECA34825FCF066A23E8A4C99F73E6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6664 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6664 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1636 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2512 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6668 | Valorant.exe | 151.101.65.91:443 | as2.ftcdn.net | FASTLY | US | whitelisted |
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1636 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1636 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
as2.ftcdn.net |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |