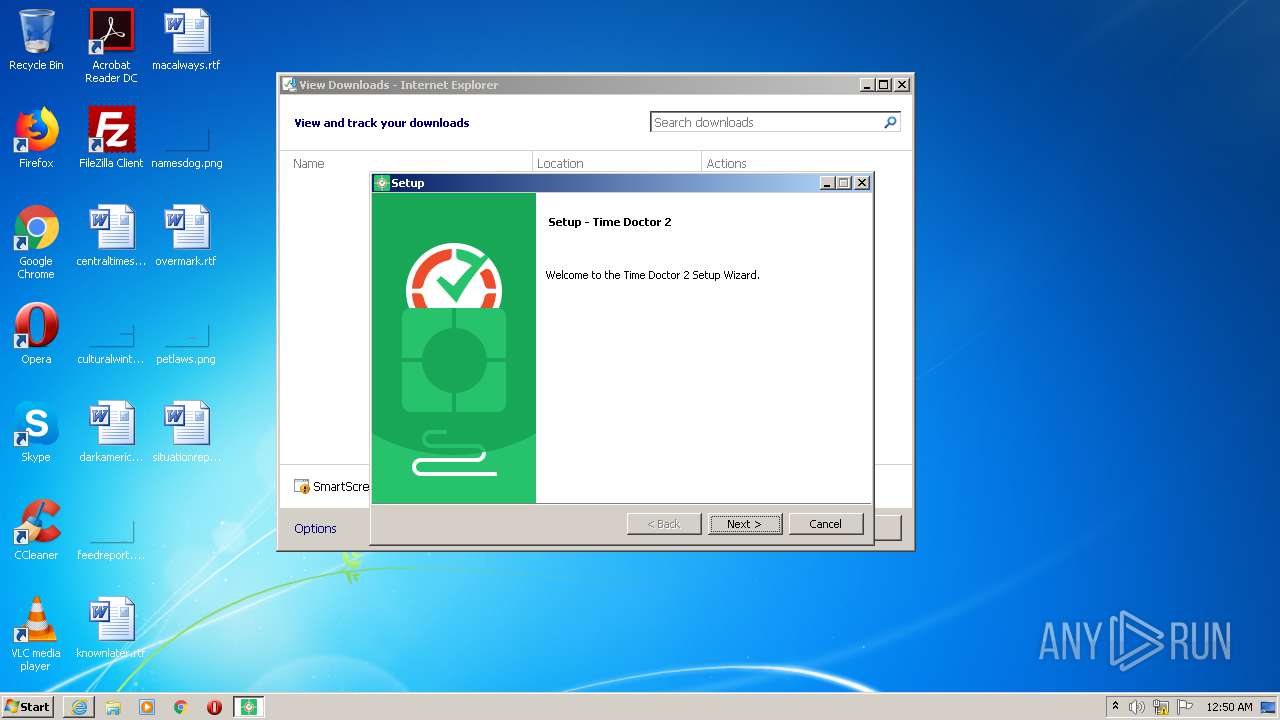
| URL: | https://s3.amazonaws.com/sfproc-downloads/3.2.12/windows/bitrock/timedoctor2-setup-3.2.12-windows.exe |
| Full analysis: | https://app.any.run/tasks/a15cf9a9-566f-450b-8322-6f311fff54a4 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2021, 00:49:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6E6EBDB096D8D905A9B0A12BD0159700 |
| SHA1: | 77B9B81764CA25931C3B80C44F15DE24E440BE21 |
| SHA256: | F7A4E0CB401F26A77766B93AF135769F00BB044BA2EA8523B1A5A70624194D62 |
| SSDEEP: | 3:N8H7WtWD9dIBJ94KWLXLObSILJa0p1jLUXvM3rA:2H9DbOWLXCnSkrA |
MALICIOUS
Application was dropped or rewritten from another process
- timedoctor2-setup-3.2.12-windows.exe (PID: 3824)
- timedoctor2-setup-3.2.12-windows.exe (PID: 2364)
- timedoctor2.exe (PID: 2396)
- timedoctor2.exe (PID: 3144)
- QtWebEngineProcess.exe (PID: 2248)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1456)
- timedoctor2.exe (PID: 2396)
- QtWebEngineProcess.exe (PID: 2248)
- timedoctor2.exe (PID: 3144)
Changes the autorun value in the registry
- timedoctor2.exe (PID: 3144)
Changes settings of System certificates
- timedoctor2.exe (PID: 3144)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 1384)
- timedoctor2-setup-3.2.12-windows.exe (PID: 3824)
- timedoctor2.exe (PID: 3144)
Application launched itself
- timedoctor2.exe (PID: 2396)
Drops a file with too old compile date
- timedoctor2-setup-3.2.12-windows.exe (PID: 3824)
Creates files in the user directory
- timedoctor2-setup-3.2.12-windows.exe (PID: 3824)
Drops a file that was compiled in debug mode
- timedoctor2-setup-3.2.12-windows.exe (PID: 3824)
Reads the time zone
- timedoctor2.exe (PID: 3144)
Creates files in the program directory
- timedoctor2.exe (PID: 3144)
Adds / modifies Windows certificates
- timedoctor2.exe (PID: 3144)
Starts Internet Explorer
- timedoctor2.exe (PID: 3144)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3792)
- iexplore.exe (PID: 2972)
Reads settings of System Certificates
- iexplore.exe (PID: 1384)
- iexplore.exe (PID: 3792)
- iexplore.exe (PID: 2704)
Changes settings of System certificates
- iexplore.exe (PID: 3792)
- iexplore.exe (PID: 2704)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3792)
- iexplore.exe (PID: 2704)
Dropped object may contain Bitcoin addresses
- timedoctor2-setup-3.2.12-windows.exe (PID: 3824)
- timedoctor2.exe (PID: 3144)
Application launched itself
- iexplore.exe (PID: 3792)
- iexplore.exe (PID: 2972)
Creates files in the user directory
- iexplore.exe (PID: 3792)
- iexplore.exe (PID: 2704)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3792)
Reads the hosts file
- timedoctor2.exe (PID: 3144)
Reads internet explorer settings
- iexplore.exe (PID: 2704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
10
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1384 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3792 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1456 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2248 | "C:\Users\admin\Time Doctor 2\QtWebEngineProcess.exe" --type=renderer --disable-accelerated-video-decode --disable-gpu-memory-buffer-video-frames --disable-logging --disable-shared-workers --enable-threaded-compositing --no-sandbox --disable-webrtc-hw-encoding --primordial-pipe-token=06C216723B6C1B93AF5C94F9DF4C3B6A --lang=en-US --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553 --disable-gpu-compositing --service-request-channel-token=06C216723B6C1B93AF5C94F9DF4C3B6A --renderer-client-id=2 --mojo-platform-channel-handle=1700 /prefetch:1 | C:\Users\admin\Time Doctor 2\QtWebEngineProcess.exe | — | timedoctor2.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: HIGH Description: Qt Qtwebengineprocess Exit code: 0 Version: 5.9.8.0 Modules
| |||||||||||||||
| 2364 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\timedoctor2-setup-3.2.12-windows.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\timedoctor2-setup-3.2.12-windows.exe | — | iexplore.exe | |||||||||||
User: admin Company: Time Doctor 2 Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2396 | "C:\Users\admin\Time Doctor 2\timedoctor2.exe" --detached | C:\Users\admin\Time Doctor 2\timedoctor2.exe | — | timedoctor2-setup-3.2.12-windows.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2704 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2972 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2972 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.timedoctor.com/?noQuestion=yes | C:\Program Files\Internet Explorer\iexplore.exe | timedoctor2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3144 | "C:\Users\admin\Time Doctor 2\timedoctor2.exe" | C:\Users\admin\Time Doctor 2\timedoctor2.exe | timedoctor2.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3792 | "C:\Program Files\Internet Explorer\iexplore.exe" https://s3.amazonaws.com/sfproc-downloads/3.2.12/windows/bitrock/timedoctor2-setup-3.2.12-windows.exe | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3824 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\timedoctor2-setup-3.2.12-windows.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\timedoctor2-setup-3.2.12-windows.exe | iexplore.exe | ||||||||||||
User: admin Company: Time Doctor 2 Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 360
Read events
2 127
Write events
229
Delete events
4
Modification events
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 39983888 | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30876122 | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
79
Suspicious files
217
Text files
155
Unknown types
67
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1384 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab2696.tmp | — | |
MD5:— | SHA256:— | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar2697.tmp | — | |
MD5:— | SHA256:— | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\timedoctor2-setup-3.2.12-windows[1].exe | — | |
MD5:— | SHA256:— | |||
| 3792 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF347B091FD05E788A.TMP | — | |
MD5:— | SHA256:— | |||
| 3792 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\timedoctor2-setup-3.2.12-windows.exe.upivx6b.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 3792 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\timedoctor2-setup-3.2.12-windows.exe | — | |
MD5:— | SHA256:— | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1E698CCB2C296D265AC1A253974E09FD_F5B19EEC46B3A283B42FC10E36B8EC76 | binary | |
MD5:— | SHA256:— | |||
| 3792 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{2E21182B-8DCD-11EB-A322-1203334A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_EE9DB89C3D6A328B5FEAFF0ED3C77874 | der | |
MD5:— | SHA256:— | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_EE9DB89C3D6A328B5FEAFF0ED3C77874 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
81
DNS requests
44
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3792 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2704 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRyyuDOSqb8BtprWZSAvBT9kFoYdwQU%2BftQxItnu2dk%2FoMhpqnOP1WEk5kCEQCveM83ew6Lpe8TG9brjMAy | US | der | 472 b | whitelisted |
3792 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2704 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDfIM2%2Bx2X%2BsgUAAAAAh5ww | US | der | 472 b | whitelisted |
3792 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1384 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuqL92L3tjkN67RNFF%2FEdvT6NEzAQUwBKyKHRoRmfpcCV0GgBFWwZ9XEQCEA1kUGtF8wzjWmwt3ywYtDc%3D | US | der | 471 b | whitelisted |
2704 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRyyuDOSqb8BtprWZSAvBT9kFoYdwQU%2BftQxItnu2dk%2FoMhpqnOP1WEk5kCEQCveM83ew6Lpe8TG9brjMAy | US | der | 472 b | whitelisted |
2704 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
3792 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3792 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1384 | iexplore.exe | 52.217.105.214:443 | s3.amazonaws.com | Amazon.com, Inc. | US | unknown |
3792 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3792 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3792 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | Microsoft Corporation | US | whitelisted |
— | — | 216.239.35.4:123 | time.google.com | Google Inc. | US | unknown |
3824 | timedoctor2-setup-3.2.12-windows.exe | 52.205.218.116:443 | td2-desktop-helpers.timedoctor.com | Amazon.com, Inc. | US | unknown |
1384 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3144 | timedoctor2.exe | 34.196.154.11:443 | api2.timedoctor.com | Amazon.com, Inc. | US | suspicious |
3144 | timedoctor2.exe | 17.253.34.251:123 | time.apple.com | Apple Inc. | GB | unknown |
3144 | timedoctor2.exe | 34.195.37.70:443 | api.staff.com | Amazon.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s3.amazonaws.com |
| shared |
ocsp.digicert.com |
| whitelisted |
td2-desktop-helpers.timedoctor.com |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
time.google.com |
| whitelisted |
desktop-v3.staff.com |
| suspicious |
fonts.gstatic.com |
| whitelisted |
o481059.ingest.sentry.io |
| suspicious |