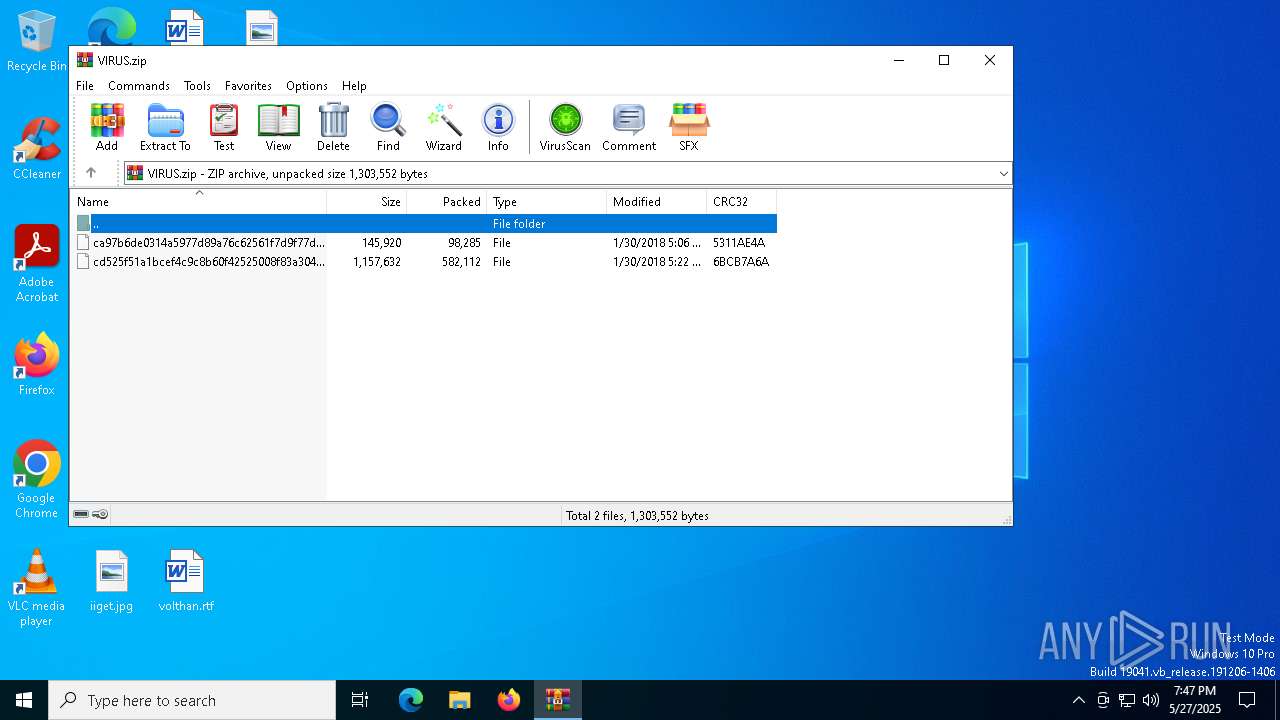
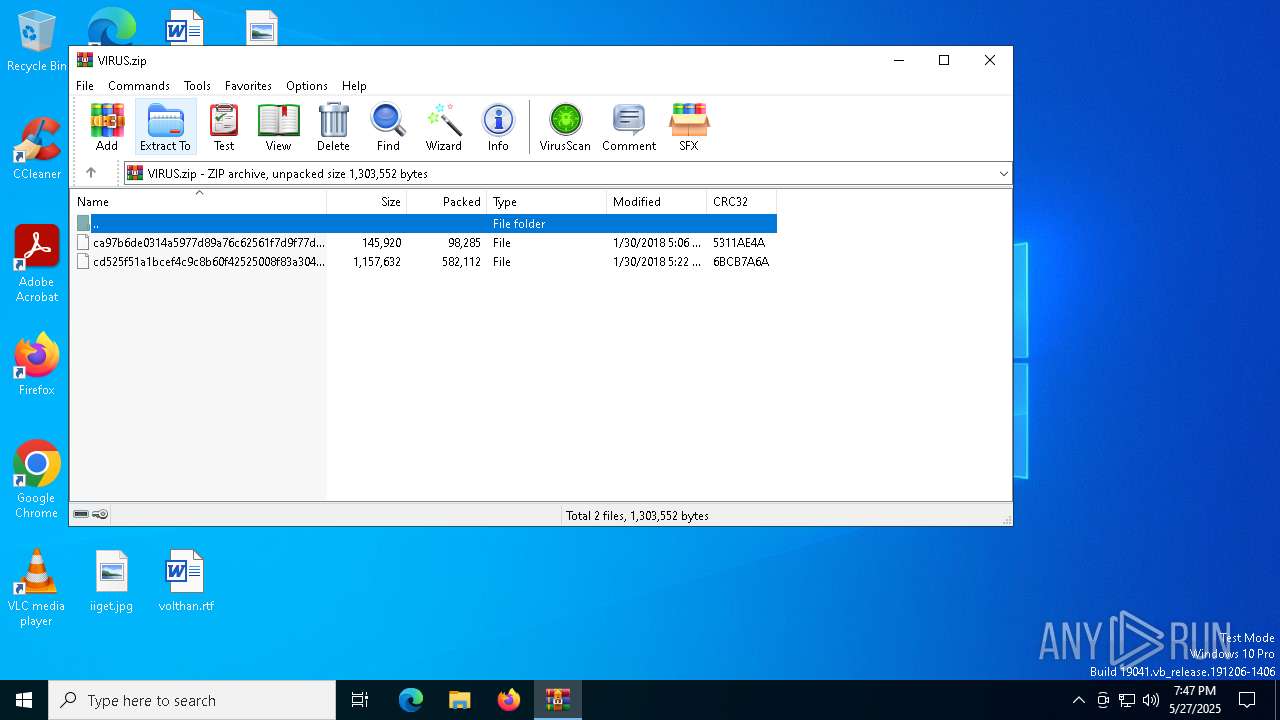
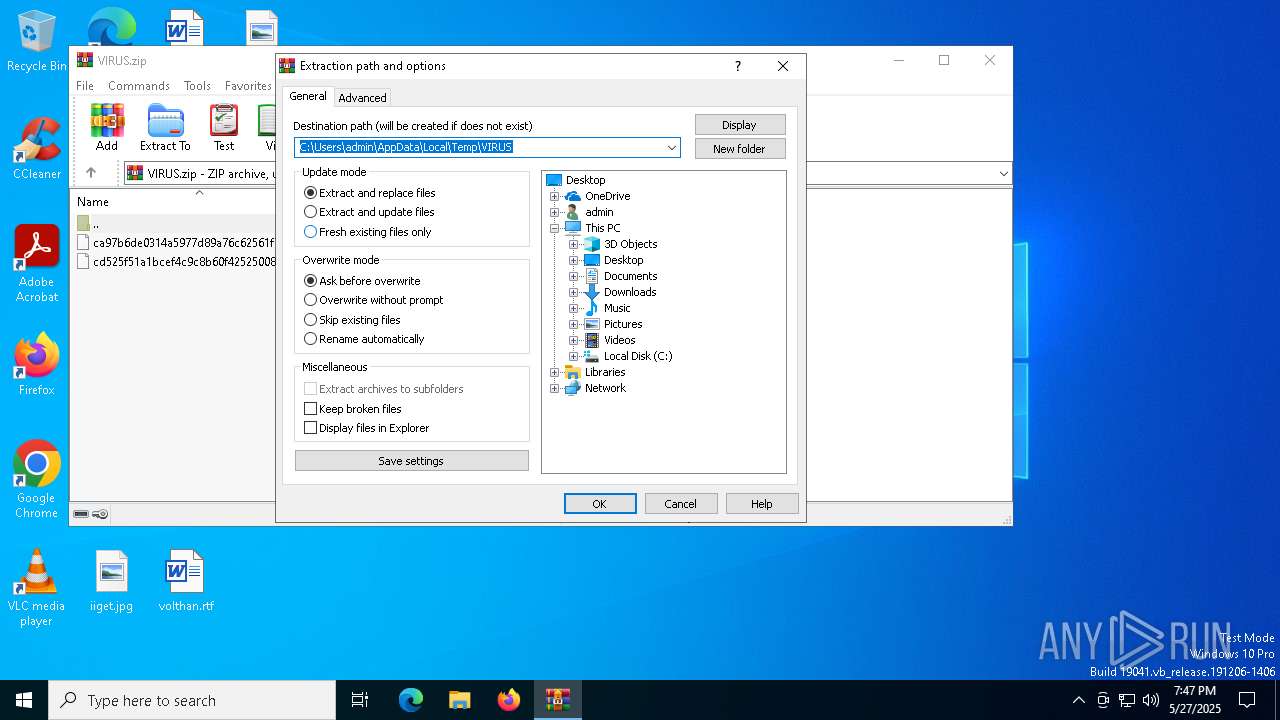
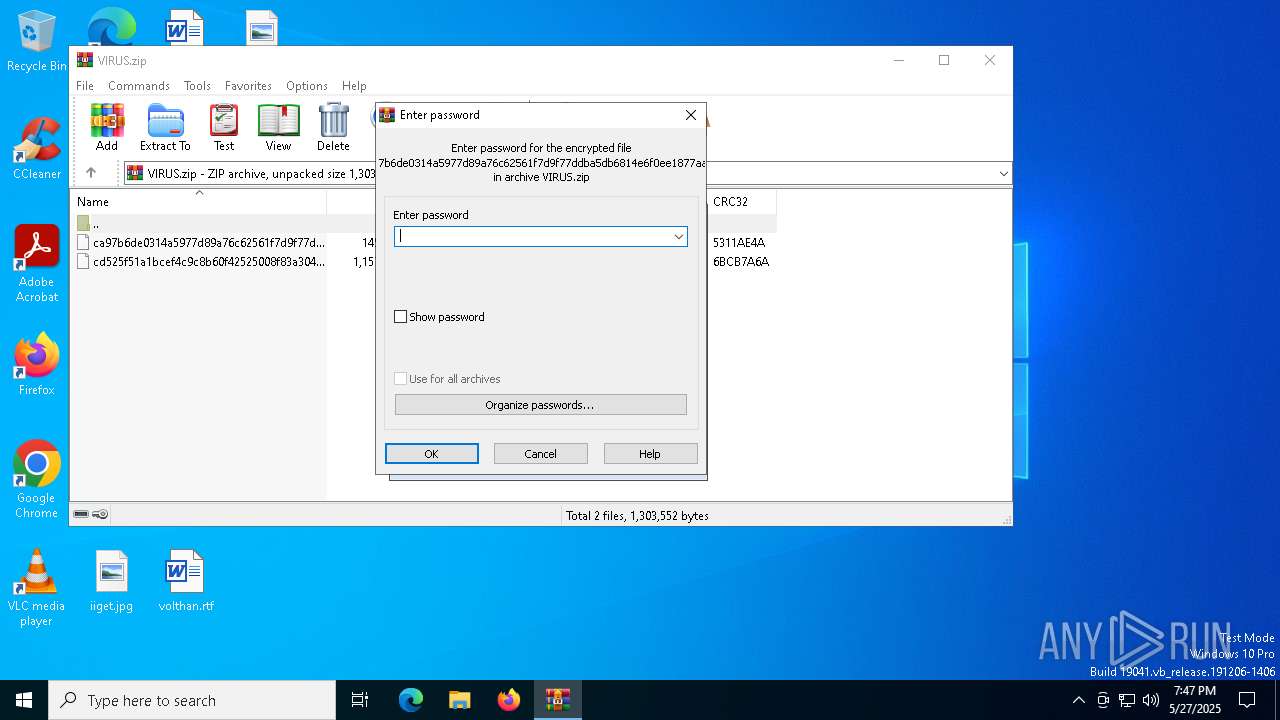
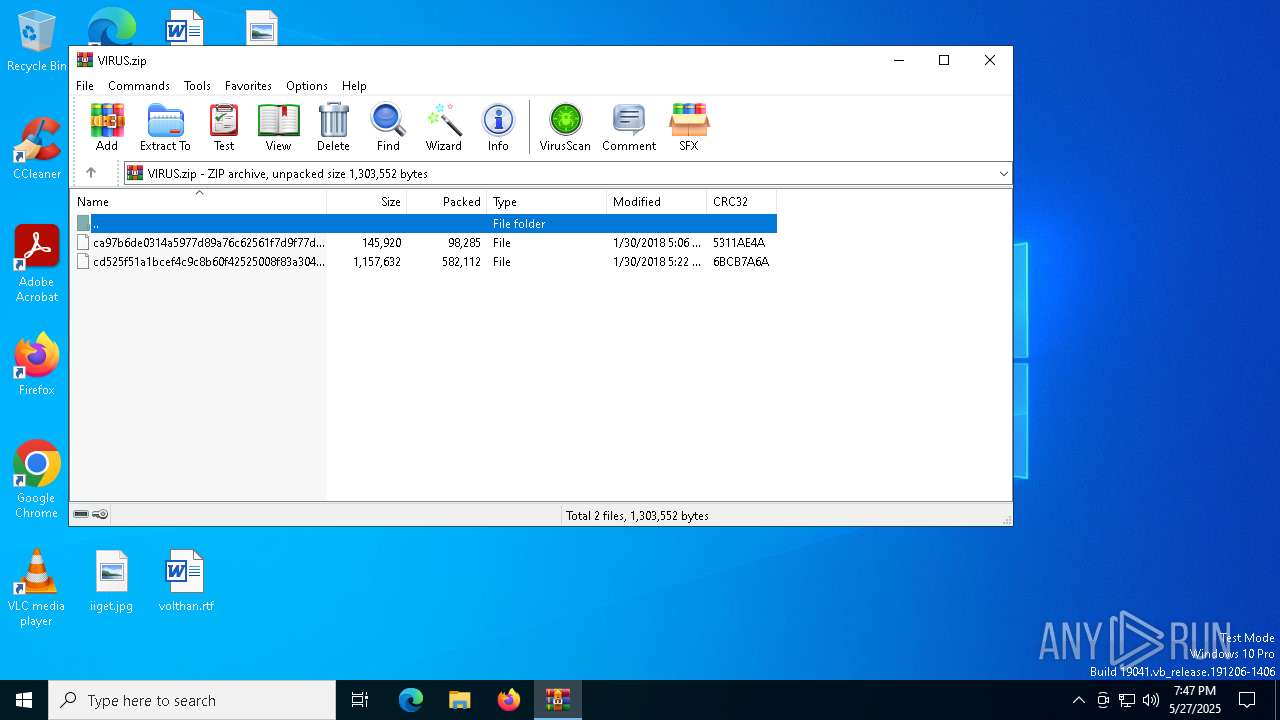
| File name: | VIRUS.zip |
| Full analysis: | https://app.any.run/tasks/6ae53d41-078a-4f13-98d6-296f6ca7ff1c |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 19:47:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E83FFB89CE3EF6682A0B97B5E6036A8F |
| SHA1: | 4468C49570B7BCF3636407772ED346667468A4F4 |
| SHA256: | F79CFB7975EA7DD18731F84A4940D20F743EA1A27DDA1ED9DC9126F694B5EF09 |
| SSDEEP: | 24576:U30raY1cGGMkQwVIAtkM8jLm4GVbDLtoHPXQK36oRozZ7HLnlZ4rlt4/8PK:U30raYaGGCwV3tkM8jLm4GVbDLtoHPXe |
MALICIOUS
Changes the autorun value in the registry
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
XMRIG has been detected (YARA)
- taskhost.exe (PID: 6808)
TOFSEE has been detected (YARA)
- svchost.exe (PID: 2892)
SUSPICIOUS
Executable content was dropped or overwritten
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
Reads security settings of Internet Explorer
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
Connects to SMTP port
- svchost.exe (PID: 2892)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 2892)
The process creates files with name similar to system file names
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
Starts itself from another location
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
Executes application which crashes
- taskhost.exe (PID: 6808)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 7756)
INFO
Checks supported languages
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
- rvcmmakg.exe (PID: 7200)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
- taskhost.exe (PID: 6808)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 7756)
The sample compiled with english language support
- WinRAR.exe (PID: 7400)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7400)
Manual execution by a user
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 7756)
Create files in a temporary directory
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
Reads the computer name
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
- rvcmmakg.exe (PID: 7200)
- taskhost.exe (PID: 6808)
Process checks computer location settings
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
Launch of the file from Registry key
- ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe (PID: 8152)
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
Creates files or folders in the user directory
- cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe (PID: 5964)
- WerFault.exe (PID: 5400)
- WerFault.exe (PID: 7260)
- WerFault.exe (PID: 6708)
Reads the software policy settings
- slui.exe (PID: 7568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:01:30 05:06:36 |
| ZipCRC: | 0x5311ae4a |
| ZipCompressedSize: | 98285 |
| ZipUncompressedSize: | 145920 |
| ZipFileName: | ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d |
Total processes
167
Monitored processes
24
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6808 -s 600 | C:\Windows\SysWOW64\WerFault.exe | — | taskhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1312 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6808 -s 464 | C:\Windows\SysWOW64\WerFault.exe | — | taskhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2064 | "C:\WINDOWS\SysWOW64\wusa.exe" | C:\Windows\SysWOW64\wusa.exe | ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Standalone Installer Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\Windows\System32\wusa.exe" | C:\Windows\SysWOW64\wusa.exe | — | ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Update Standalone Installer Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2892 | svchost.exe | C:\Windows\SysWOW64\svchost.exe | rvcmmakg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3768 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6808 -s 616 | C:\Windows\SysWOW64\WerFault.exe | — | taskhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6808 -s 584 | C:\Windows\SysWOW64\WerFault.exe | — | taskhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6808 -s 624 | C:\Windows\SysWOW64\WerFault.exe | — | taskhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6808 -s 392 | C:\Windows\SysWOW64\WerFault.exe | — | taskhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5964 | "C:\Users\admin\Desktop\ext\cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe" | C:\Users\admin\Desktop\ext\cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
10 891
Read events
10 879
Write events
12
Delete events
0
Modification events
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\VIRUS.zip | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ext | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
5
Suspicious files
0
Text files
6
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7260 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cd525f51a1bcef4c_9c1c36b4a8d3afa83ded6675d61d0f45343c05d_fc956c9e_049d5885-2e5a-4648-8f3d-a214c8d475cd\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5400 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_taskhost.exe_dad9597beee63a1ebc378ff8fb790d0a27943e5_3ecdd982_0da41820-a259-4a51-9692-182a78349b8a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6708 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cd525f51a1bcef4c_9c1c36b4a8d3afa83ded6675d61d0f45343c05d_fc956c9e_07c60be2-73b9-43df-bfa5-6d091ad52b44\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7400 | WinRAR.exe | C:\Users\admin\Desktop\ext\ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d | executable | |
MD5:A118AEB7A4E96BB3E89F32CBB03A9A61 | SHA256:CA97B6DE0314A5977D89A76C62561F7D9F77DDBA5DB6814E6F0EE1877AA6152D | |||
| 8152 | ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe | C:\Users\admin\AppData\Local\Temp\wteqklp.exe | executable | |
MD5:1D1609641A6A0B6D755595009F9E152D | SHA256:D63E486B06DD8451D222DFB5F1228FEA1E5C07759AA7D455A5DEECAE4A707D28 | |||
| 5964 | cd525f51a1bcef4c9c8b60f42525008f83a3042a2e218c487ea8b0c6b7e651cc.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\CPU\taskhost.exe | executable | |
MD5:D7EE3402B3E0C614E2210C55B1CFDD96 | SHA256:CD525F51A1BCEF4C9C8B60F42525008F83A3042A2E218C487EA8B0C6B7E651CC | |||
| 8152 | ca97b6de0314a5977d89a76c62561f7d9f77ddba5db6814e6f0ee1877aa6152d.exe | C:\Users\admin\rvcmmakg.exe | executable | |
MD5:1B9B6D1393FA5A77946F378BBDA295BC | SHA256:906CA872C9F0EB4B9FBCA8450978FB965D3C61DEBF6039D49055808C058DC5FA | |||
| 7260 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER4488.tmp.dmp | dmp | |
MD5:2C51ACCD3A254DD87832ACD3F79C8FD3 | SHA256:60F3556C27A17399F05246612FAC9860AD7440CD0811D075A92A1A849A1E4BAF | |||
| 7260 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER44C7.tmp.WERInternalMetadata.xml | xml | |
MD5:26D8E8ED0C69ABBC3DFE86855621DE26 | SHA256:344C3CE67C65CDE066A4E55C7A7B5F85C48E360B56DC18D35AC0C12C368BA458 | |||
| 7260 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER44F7.tmp.xml | xml | |
MD5:96C2767877ECA43FFFDB2E743A4F0C20 | SHA256:3F9D7F108C726AEC3DC90521B45A9D4FA9F571641DC96D6342C95D49BC0B3C87 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7964 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7964 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3284 | svchost.exe | GET | 200 | 23.48.23.154:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3284 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6592 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5796 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
microsoft.com |
| whitelisted |