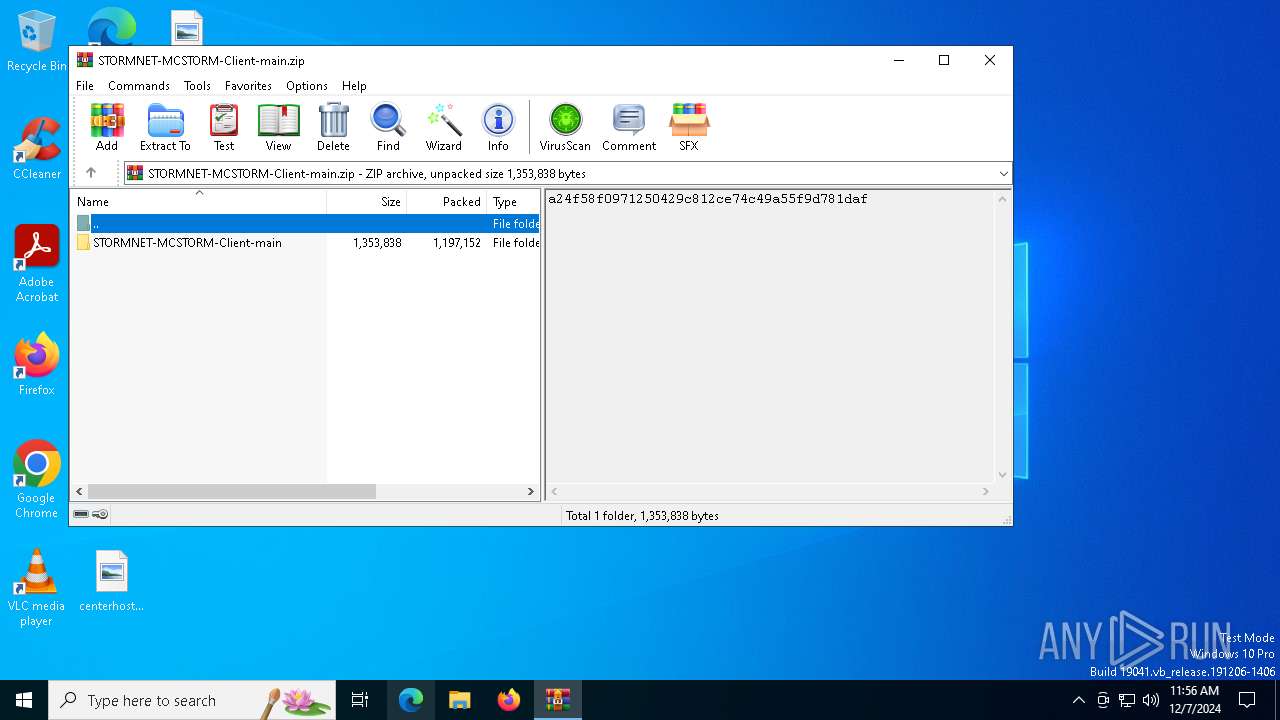
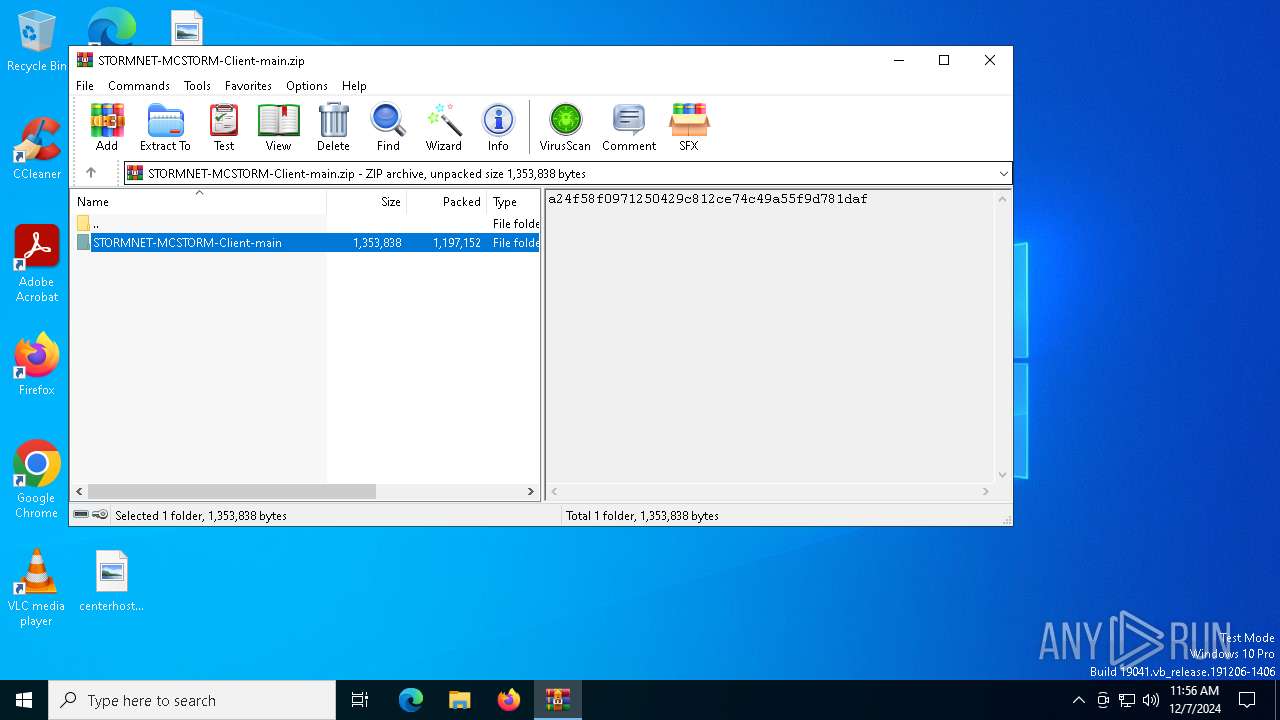
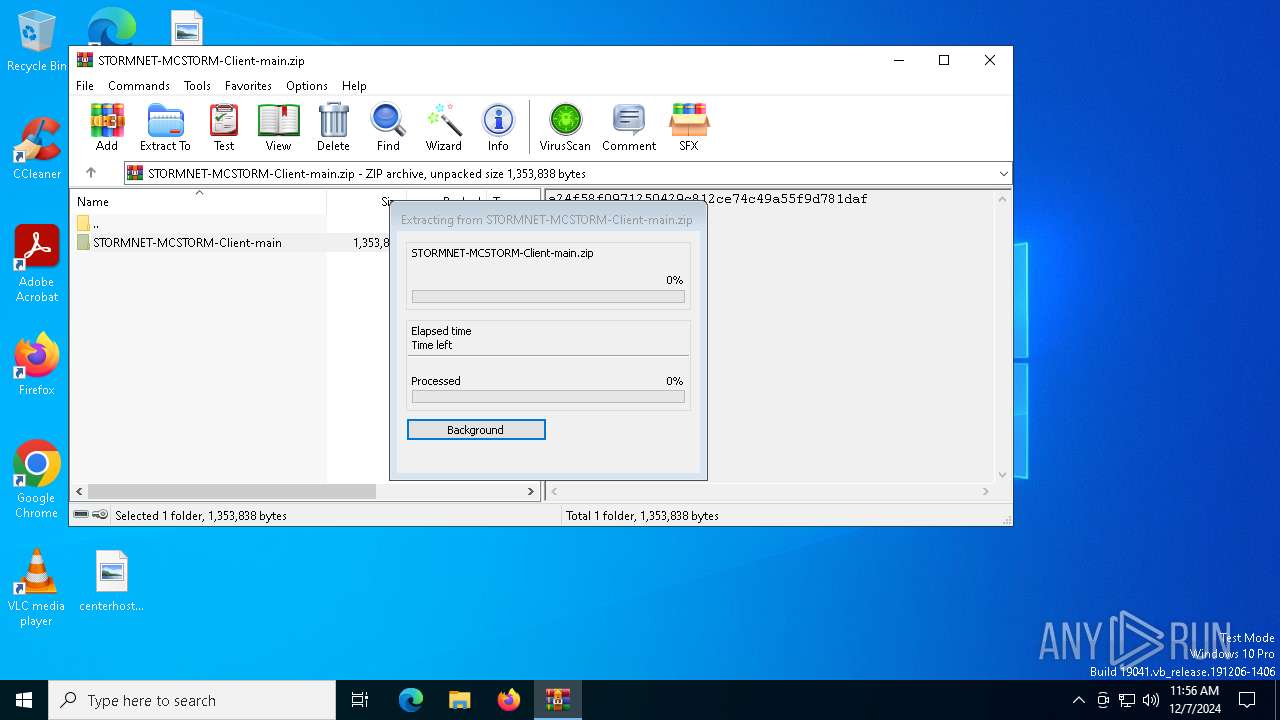
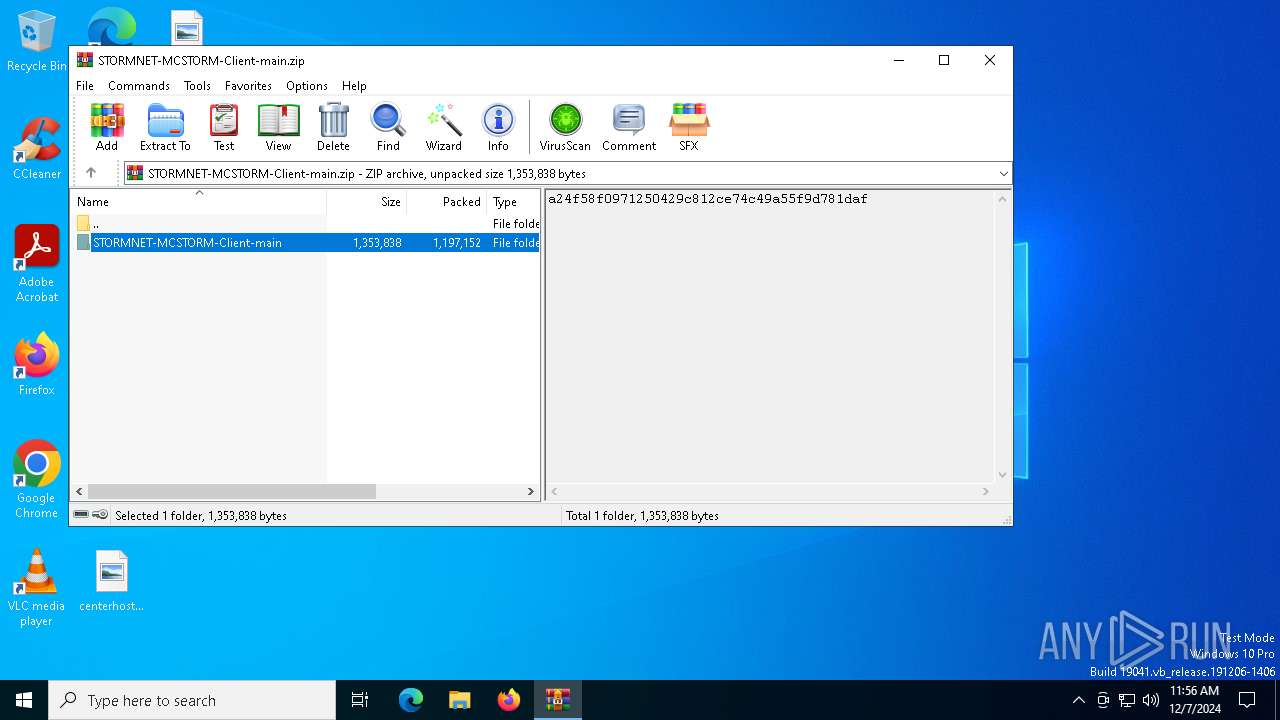
| File name: | STORMNET-MCSTORM-Client-main.zip |
| Full analysis: | https://app.any.run/tasks/3cb67439-f509-4052-8b75-7944e7614a9d |
| Verdict: | Malicious activity |
| Analysis date: | December 07, 2024, 11:56:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 02BA3395352F77293C9573B43092A046 |
| SHA1: | 38D59C8DAF26DA89C1A751C7F0B650CA421D0EE0 |
| SHA256: | F75D58BF8DC036849AD1DD9523877C883E6CD2EF621ABB848E10FB904DDFDF94 |
| SSDEEP: | 49152:5L41NAL2lezVpJgBVZLCIvln2cuXb4AYTOvppzonx3l+HtwxSnCB1KMzKFB1KMzK:5+NxeDQpE9Xb4kpl4l+HyqCnKMzKFnK7 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1228)
SUSPICIOUS
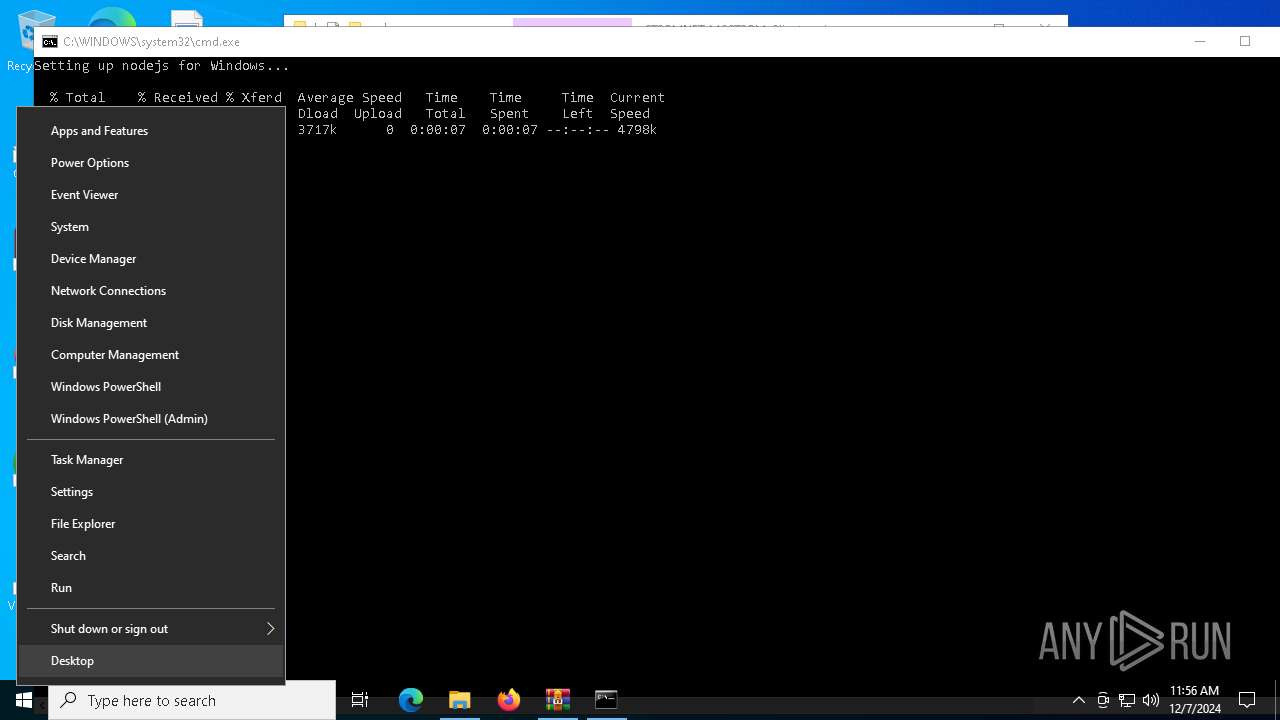
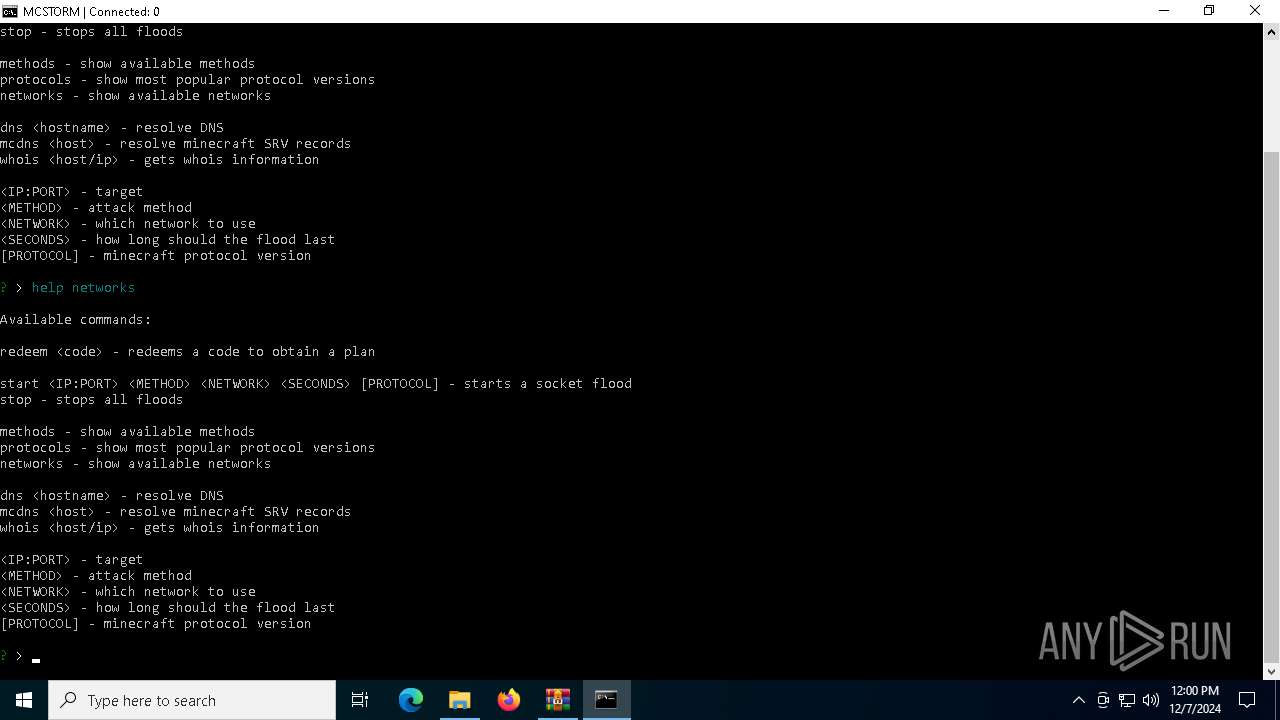
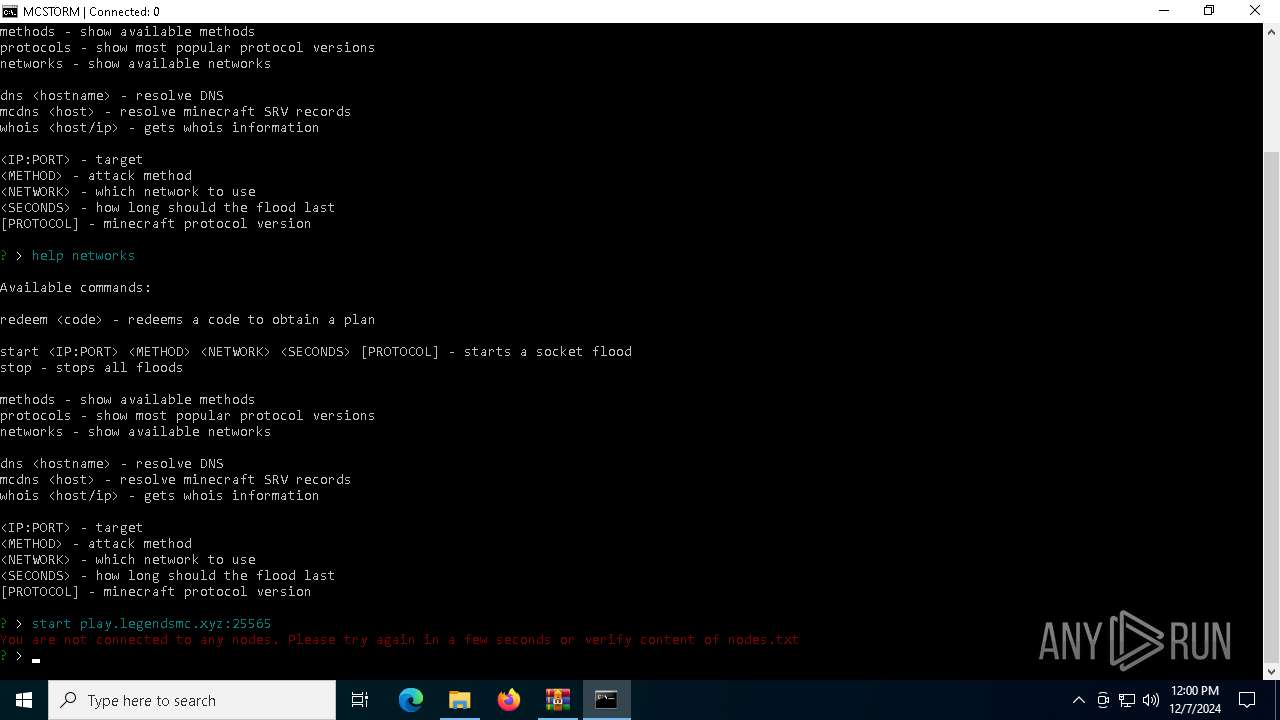
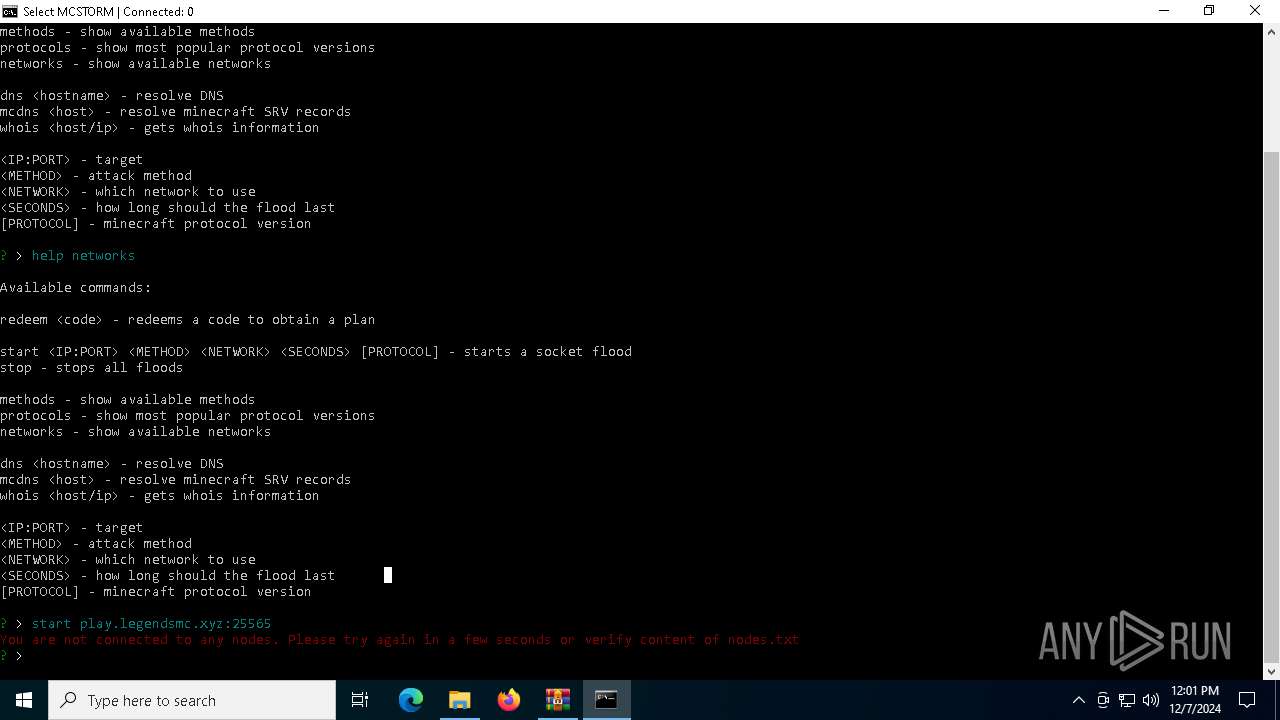
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6964)
Executes script using NodeJS
- node.exe (PID: 6880)
- node.exe (PID: 1920)
- node.exe (PID: 7072)
The executable file from the user directory is run by the CMD process
- node.exe (PID: 6880)
Application launched itself
- cmd.exe (PID: 6964)
Found regular expressions for crypto-addresses (YARA)
- node.exe (PID: 7072)
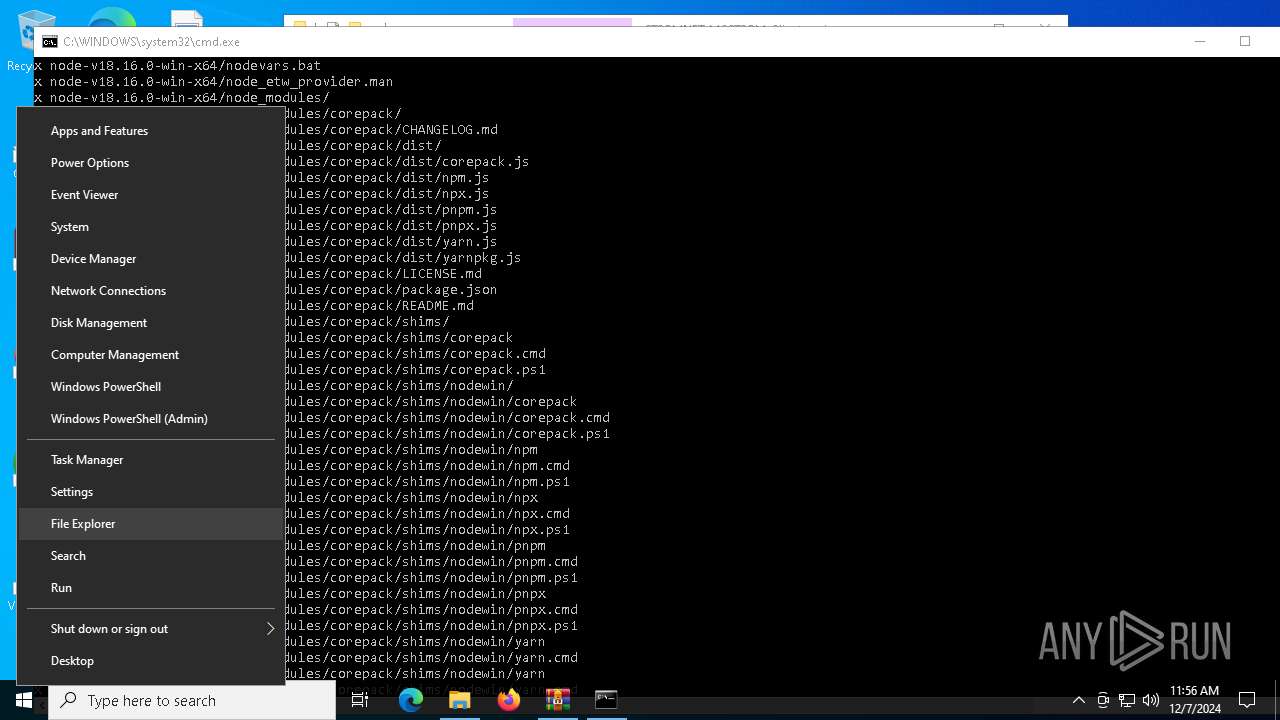
Executable content was dropped or overwritten
- node.exe (PID: 7072)
Connects to unusual port
- node.exe (PID: 1920)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 1228)
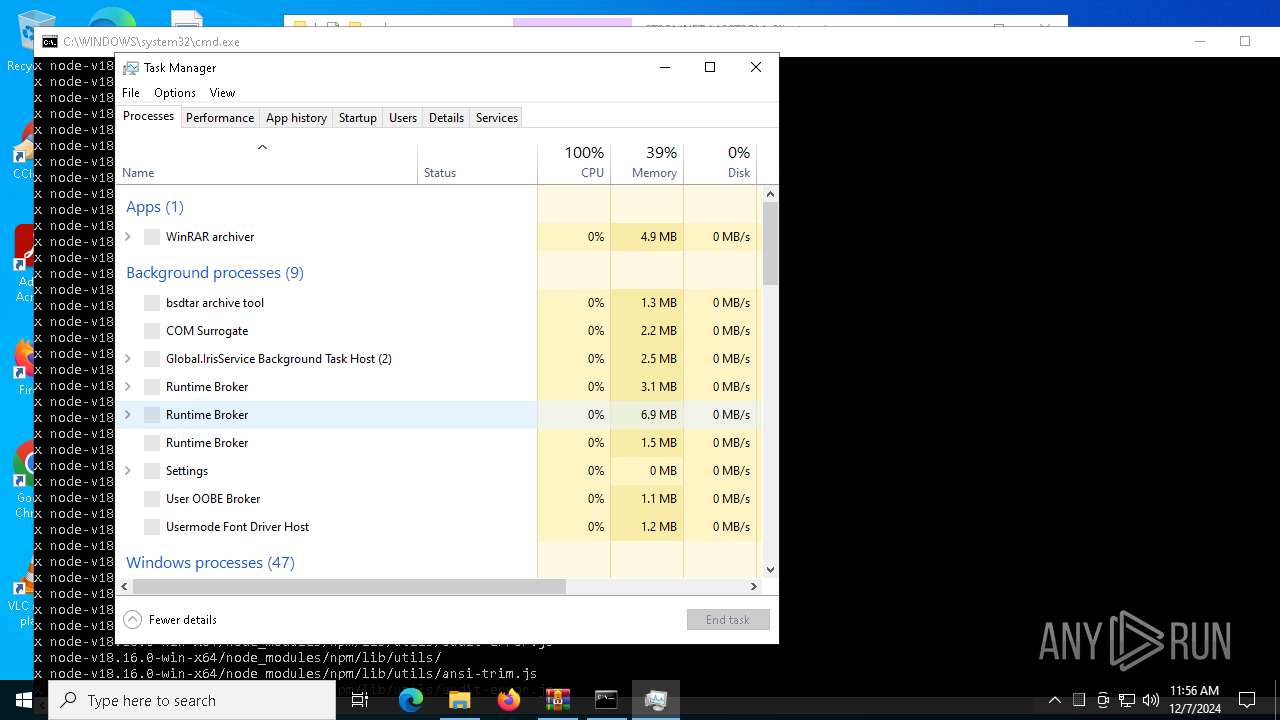
Manual execution by a user
- cmd.exe (PID: 6964)
- Taskmgr.exe (PID: 4244)
- Taskmgr.exe (PID: 5572)
- notepad.exe (PID: 6736)
- notepad.exe (PID: 6760)
Checks supported languages
- curl.exe (PID: 7076)
- mode.com (PID: 7032)
- tar.exe (PID: 3420)
- node.exe (PID: 6880)
- node.exe (PID: 1920)
- node.exe (PID: 7072)
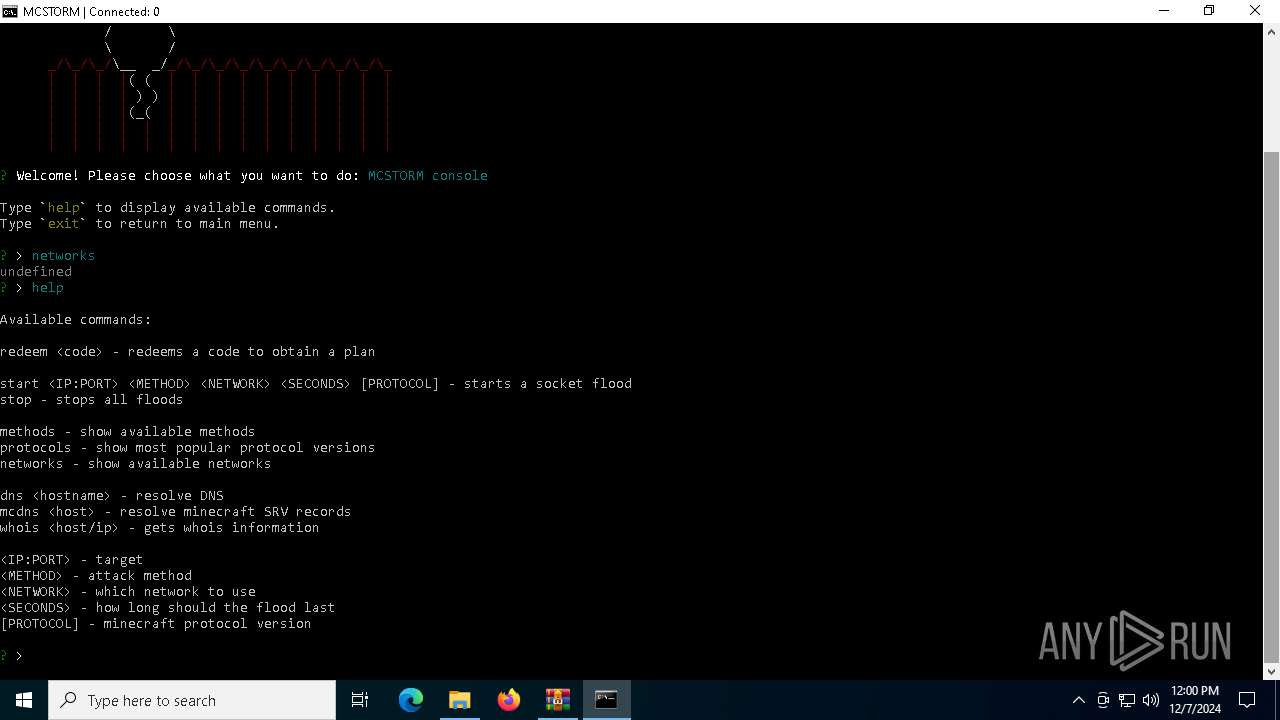
Execution of CURL command
- cmd.exe (PID: 6964)
Reads Environment values
- node.exe (PID: 6880)
- node.exe (PID: 7072)
- node.exe (PID: 1920)
Reads the computer name
- node.exe (PID: 6880)
- curl.exe (PID: 7076)
- node.exe (PID: 7072)
- node.exe (PID: 1920)
Drops encrypted JS script (Microsoft Script Encoder)
- node.exe (PID: 6880)
- node.exe (PID: 7072)
Drops encrypted VBS script (Microsoft Script Encoder)
- node.exe (PID: 6880)
- node.exe (PID: 7072)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6760)
- Taskmgr.exe (PID: 5572)
- notepad.exe (PID: 6736)
Starts MODE.COM to configure console settings
- mode.com (PID: 7032)
Reads product name
- node.exe (PID: 6880)
- node.exe (PID: 1920)
- node.exe (PID: 7072)
Reads CPU info
- node.exe (PID: 7072)
- node.exe (PID: 6880)
Creates files or folders in the user directory
- node.exe (PID: 7072)
- node.exe (PID: 6880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:04:29 13:25:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | STORMNET-MCSTORM-Client-main/ |
Total processes
146
Monitored processes
16
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1920 | "node-v18.16.0-win-x64/node" --no-deprecation --no-warnings index.js | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\node-v18.16.0-win-x64\node.exe | cmd.exe | ||||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Node.js JavaScript Runtime Version: 18.16.0 Modules
| |||||||||||||||
| 3420 | tar -xvf nodejs.zip | C:\Windows\System32\tar.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: bsdtar archive tool Exit code: 0 Version: 3.5.2 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5572 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
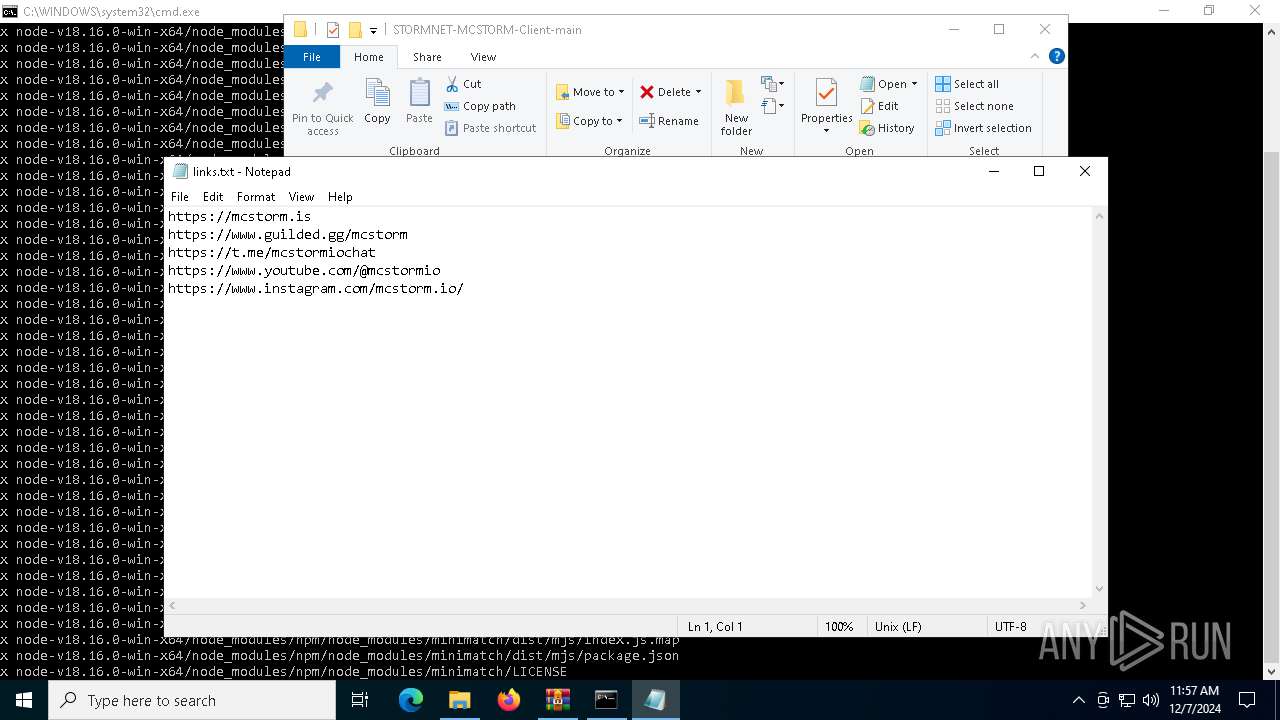
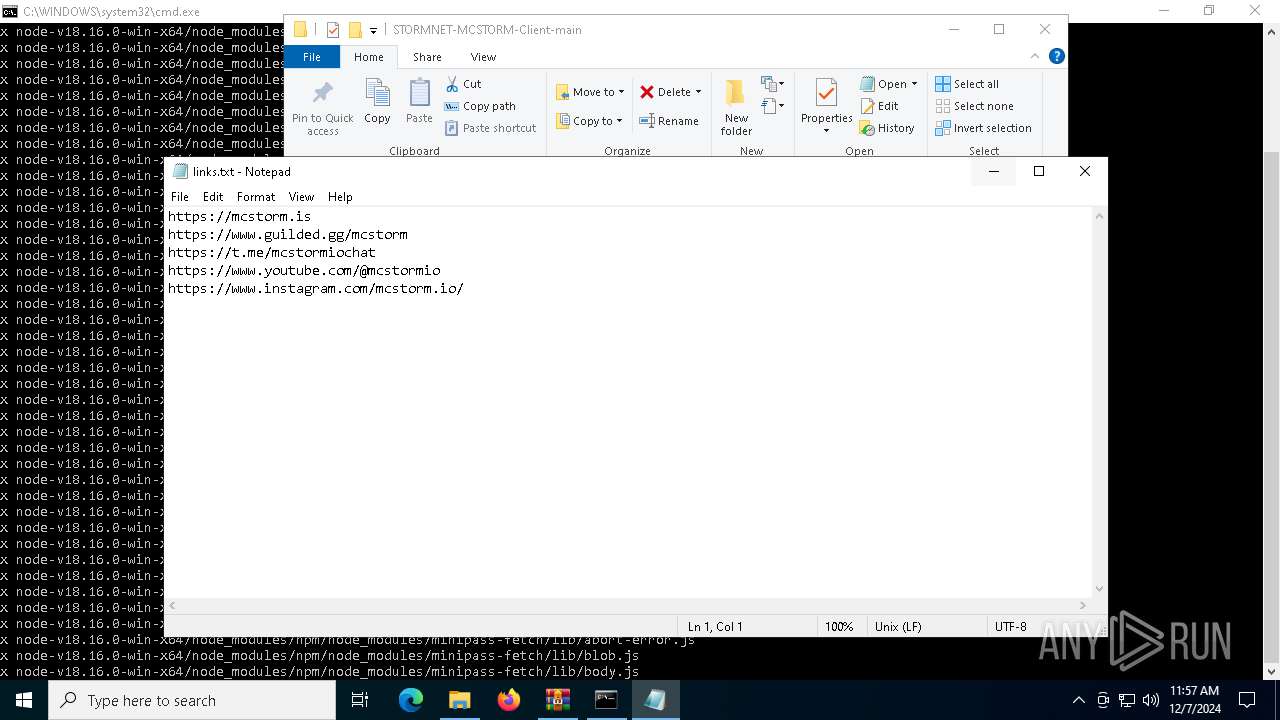
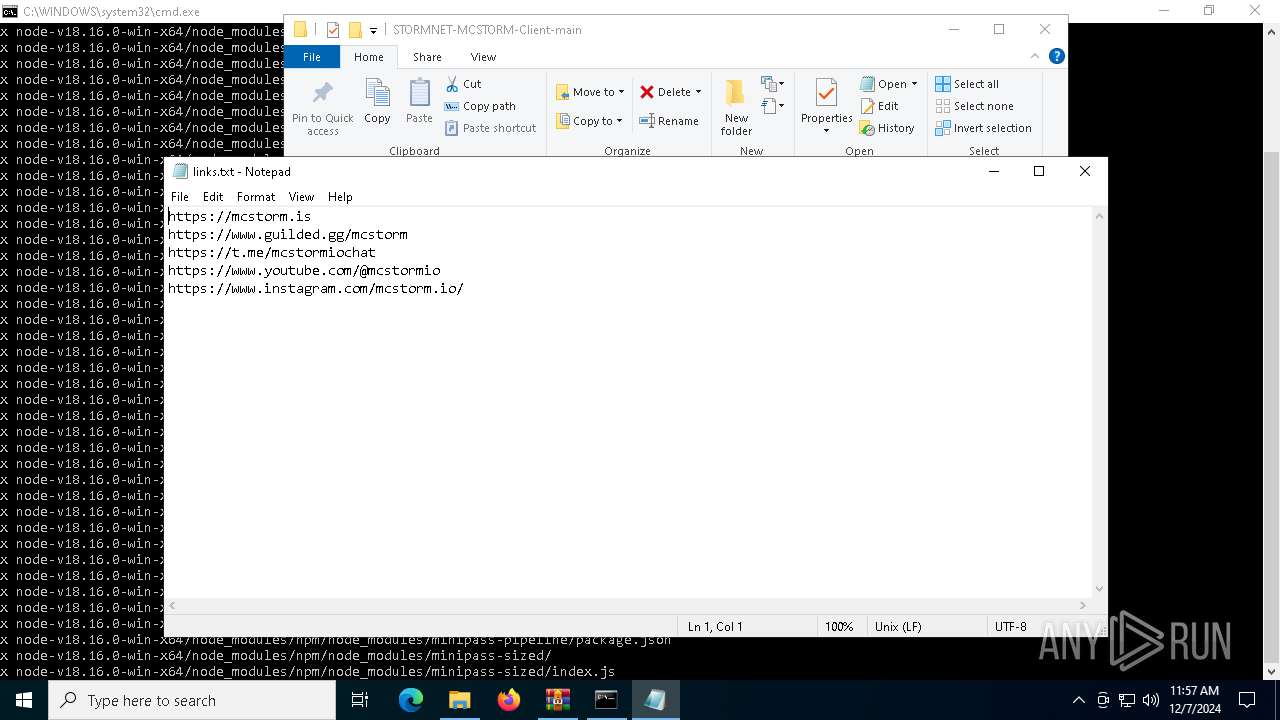
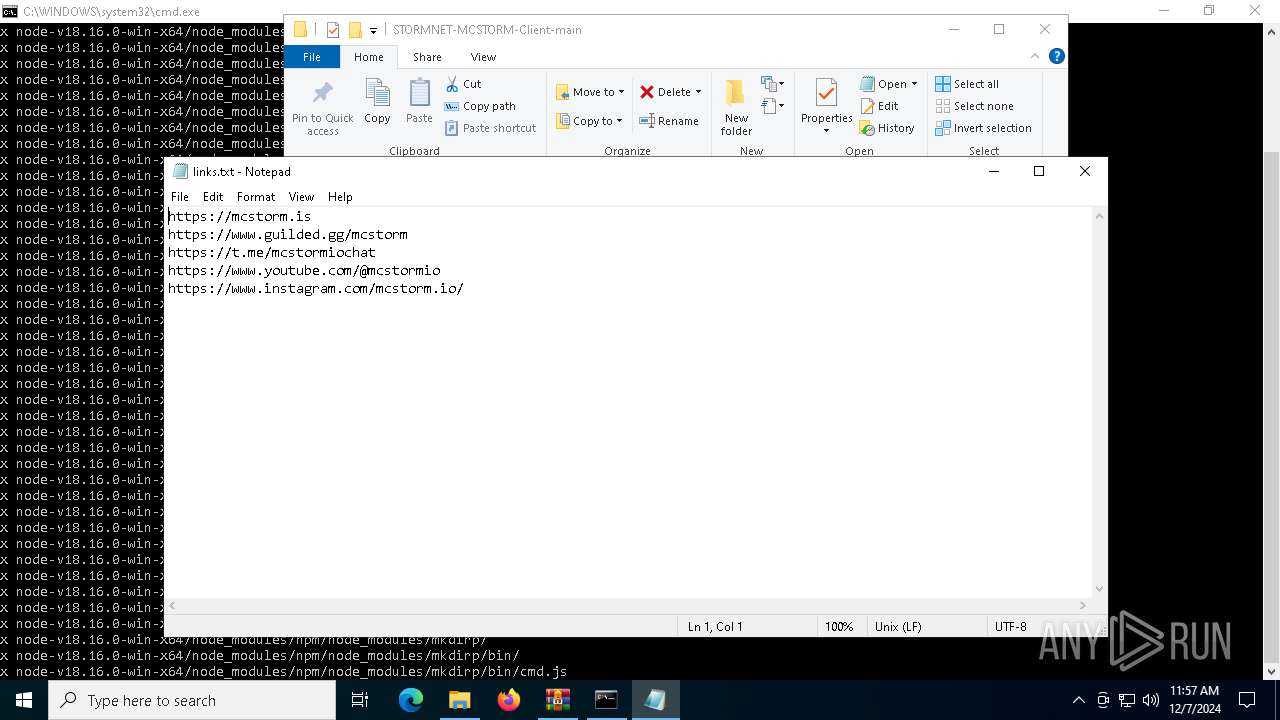
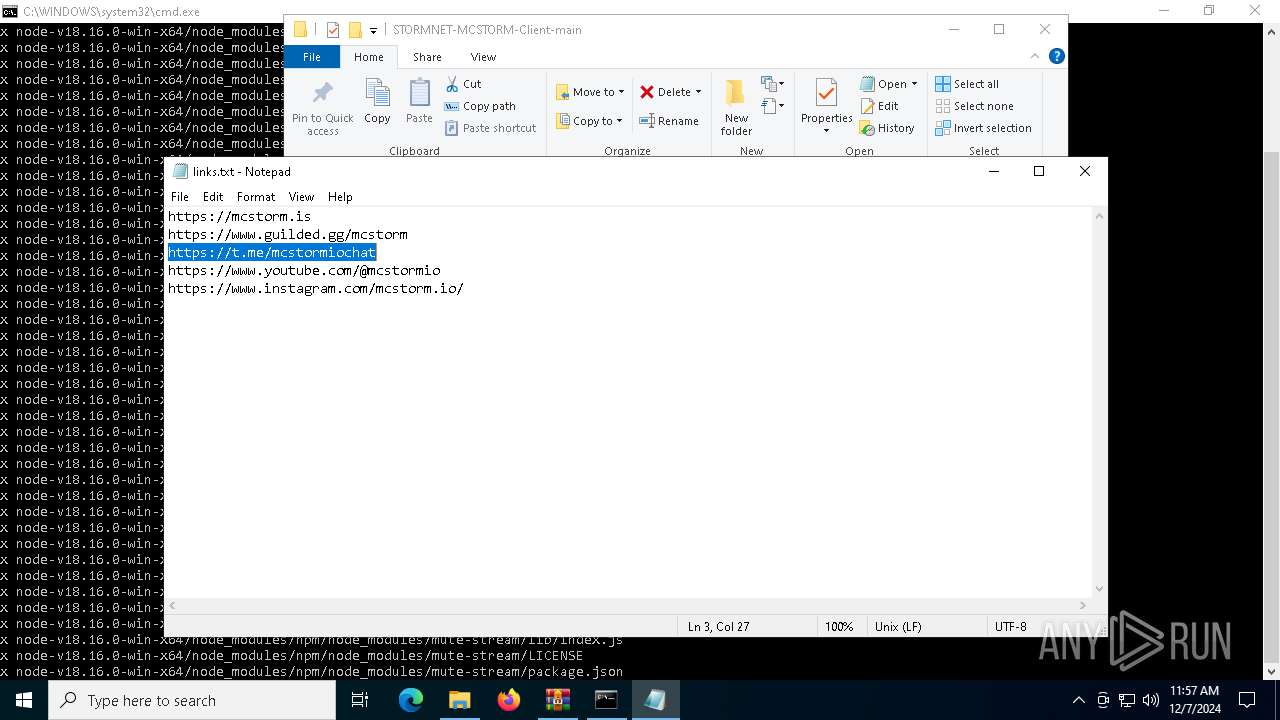
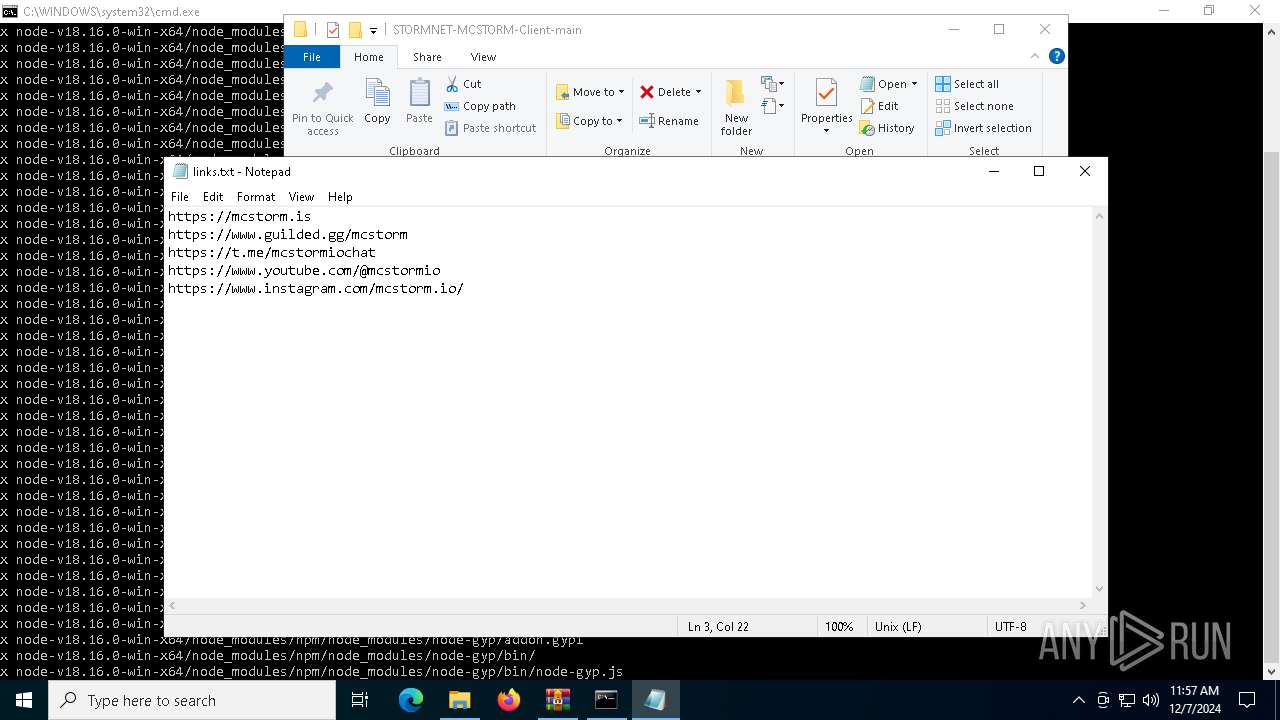
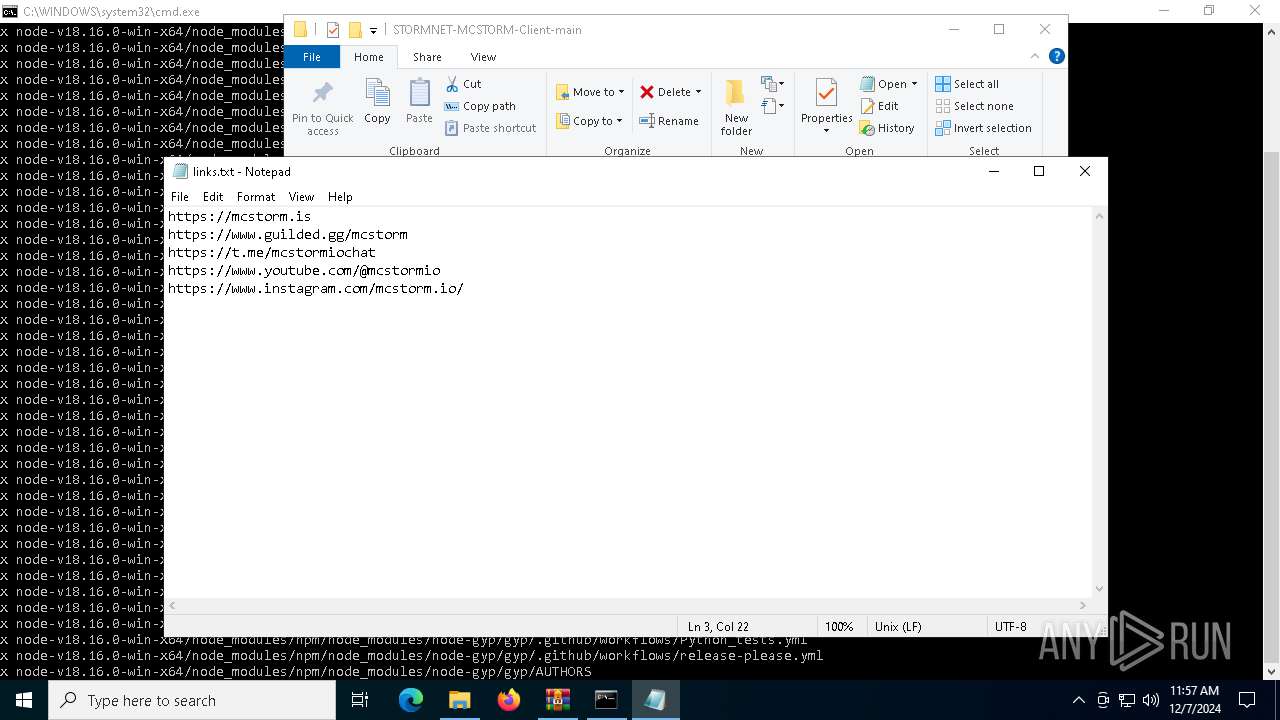
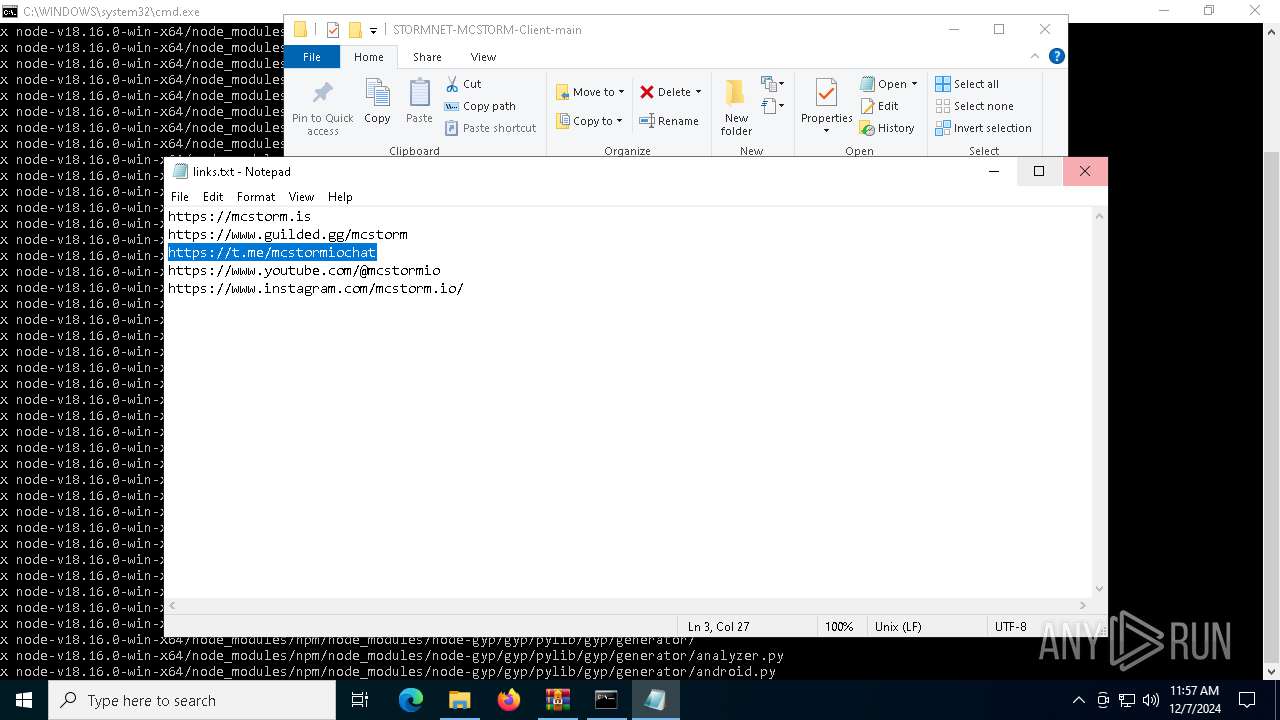
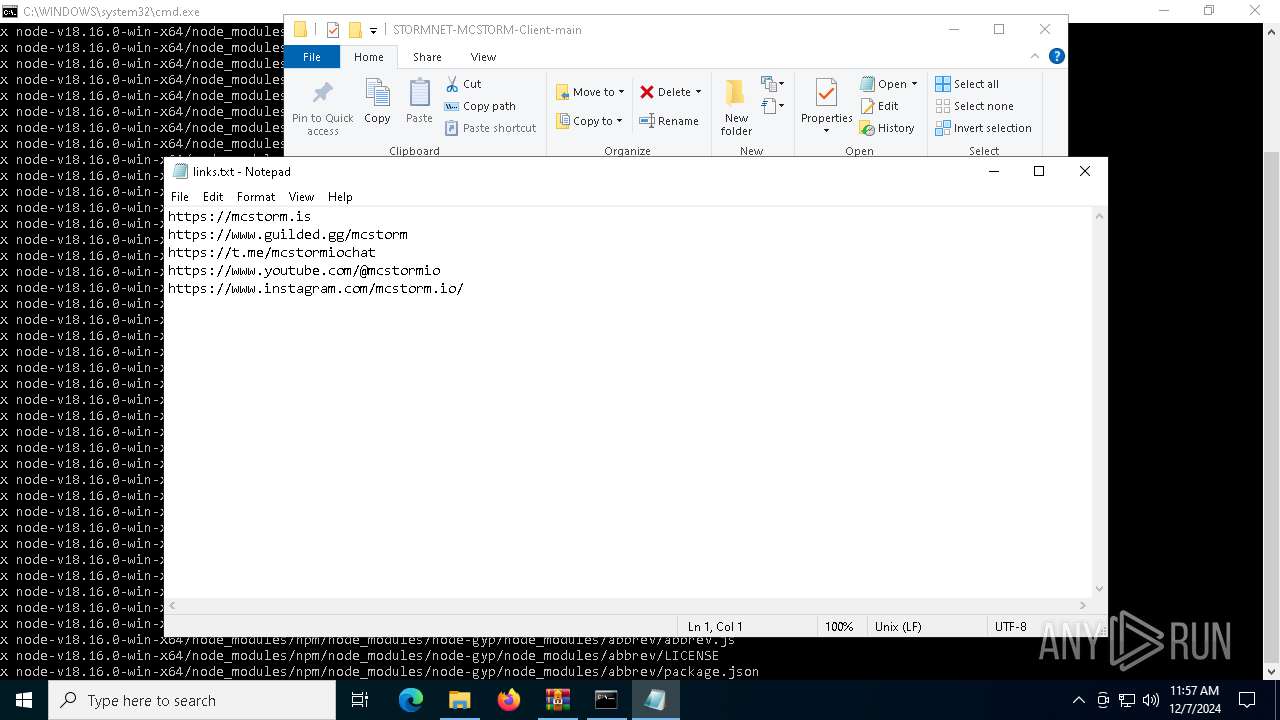
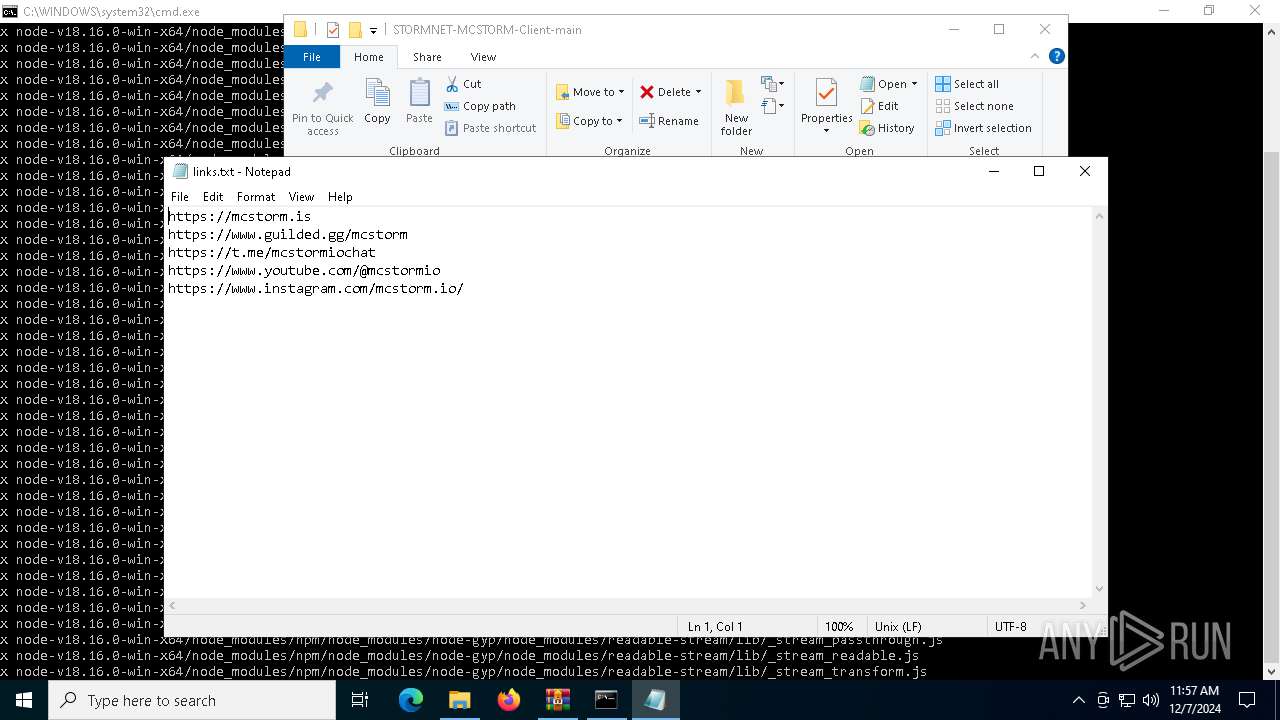
| 6736 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\links.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6760 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\links.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6828 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6880 | "C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\node-v18.16.0-win-x64\\node.exe" "C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\node-v18.16.0-win-x64\\node_modules\npm\bin\npm-cli.js" prefix -g | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\node-v18.16.0-win-x64\node.exe | — | cmd.exe | |||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Node.js JavaScript Runtime Exit code: 0 Version: 18.16.0 Modules
| |||||||||||||||
| 6888 | C:\WINDOWS\system32\cmd.exe /c CALL "C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\node-v18.16.0-win-x64\\node.exe" "C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\node-v18.16.0-win-x64\\node_modules\npm\bin\npm-cli.js" prefix -g | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 857
Read events
5 830
Write events
13
Delete events
14
Modification events
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main.zip | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
16
Suspicious files
1 793
Text files
1 049
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\README.md | text | |
MD5:05273554B70692DAA6EE5113849308E8 | SHA256:AD897CBC509CE88EE28BE5ADC299DEBF7D2A5700A5CA48DAA7F431E27F3AD41E | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\image\cloudflare-flexible.png | image | |
MD5:F2BBF6D56EEAA5B3EEAD7218C4A88592 | SHA256:E78E2BB3E8092C572834E406E544B0B90712FBFA9378A7BBB1D82BCD94BF0F6B | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\help.txt | text | |
MD5:4F0DB8159D2433187A73ED40834FB355 | SHA256:44A69C59FC4B03605E1012D76551853EE35EA569CA96ED0E155A0418CE5F2A65 | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\image\legend.png | image | |
MD5:4932C37D2116E89BDCD4843F1E329D40 | SHA256:8BC1FD968070EECCC55AB5E4A1D7F6FF8B99E0D0E196839C7074DBCF00964052 | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\image\stresser-cloudflare.png | image | |
MD5:C285CA8FF9C49870E733FAA967F95813 | SHA256:0FD669CDE12604DCD1AEB3CFA0D152162CF33352BC5E62828BAA350E8A197C0D | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\image\cloudflare-full.png | image | |
MD5:4E841B8F169994017C52DA40C100B488 | SHA256:4A51DCFBF0D48C59FC853F7977EA2064ADC66467C7F485446190B4DF79FE8EBC | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\image\STORMNET-mcstorm.png | image | |
MD5:0D46C0110DAC25A661D344A1E9FF6979 | SHA256:898E9D6B058C1374A913128C3334A7CF9348757FB5C6AA7F0A9F278A4E6CDCE7 | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\image\logo.png | image | |
MD5:470ED9CB0CB18DC657440CD4CE9F3BD3 | SHA256:F9E2B81D5581B8B548FA97DEC4E76B698398026317A66D68B5CC24C124745805 | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\image\screenshot2.png | image | |
MD5:446C8ABE4ABF098D430CBC4E3ECD7D30 | SHA256:49A8D0A585C919E46E17249DD243A4990DD9747B26FFAE4F0ABFC6F8DDB884B0 | |||
| 1228 | WinRAR.exe | C:\Users\admin\Downloads\STORMNET-MCSTORM-Client-main\STORMNET-MCSTORM-Client-main\image\screenshot.png | image | |
MD5:446C8ABE4ABF098D430CBC4E3ECD7D30 | SHA256:49A8D0A585C919E46E17249DD243A4990DD9747B26FFAE4F0ABFC6F8DDB884B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
57
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
1616 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6284 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEHtre38rtwB7v4VMLyrxkVE%3D | unknown | — | — | whitelisted |
1616 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2992 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nodejs.org |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |