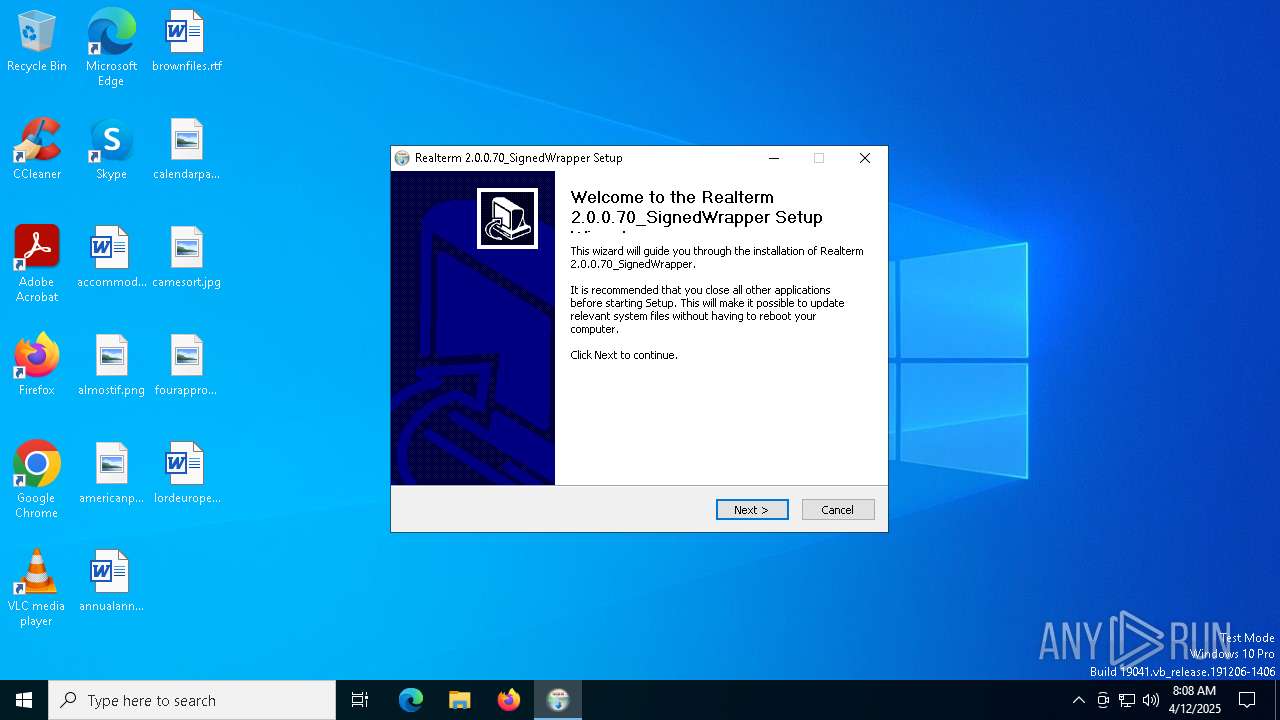
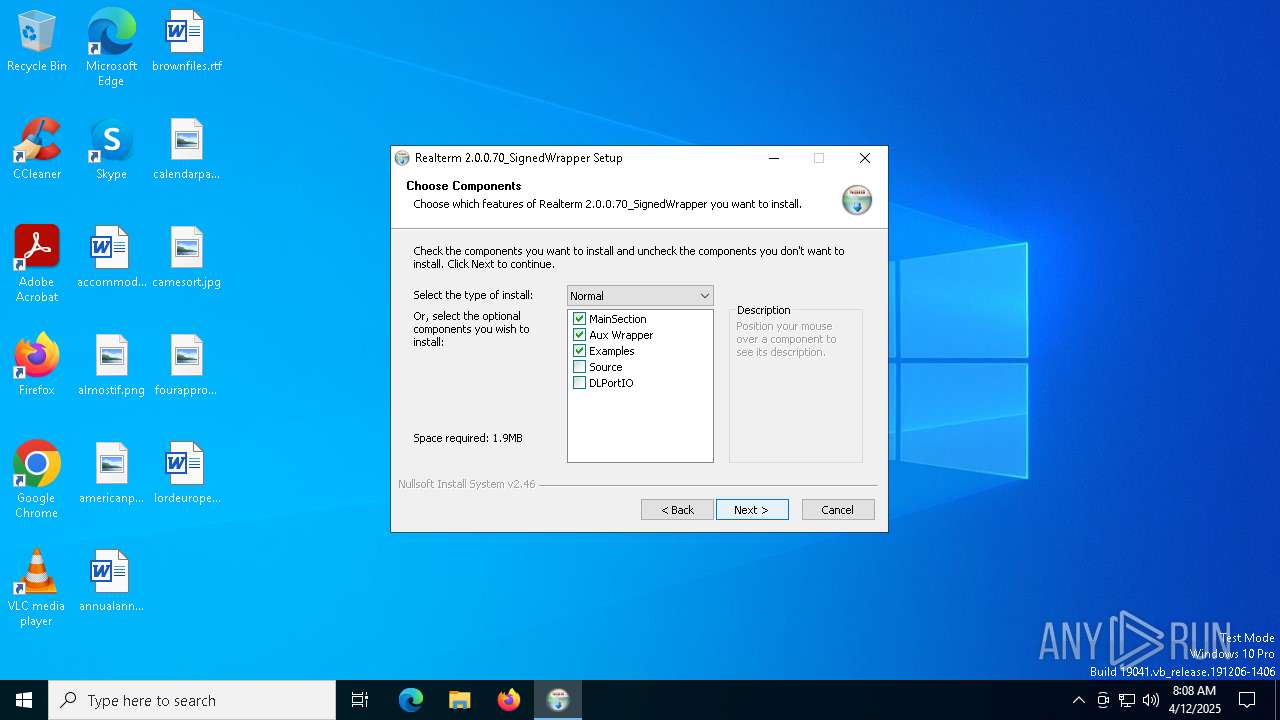
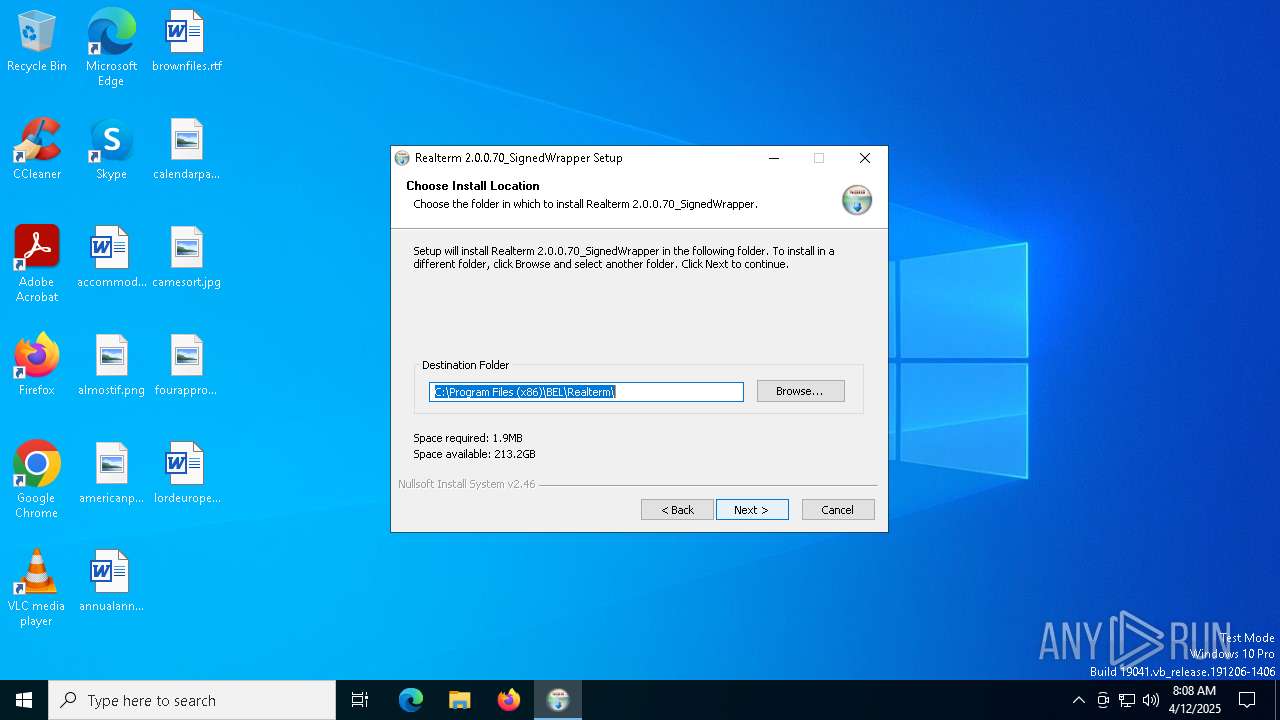
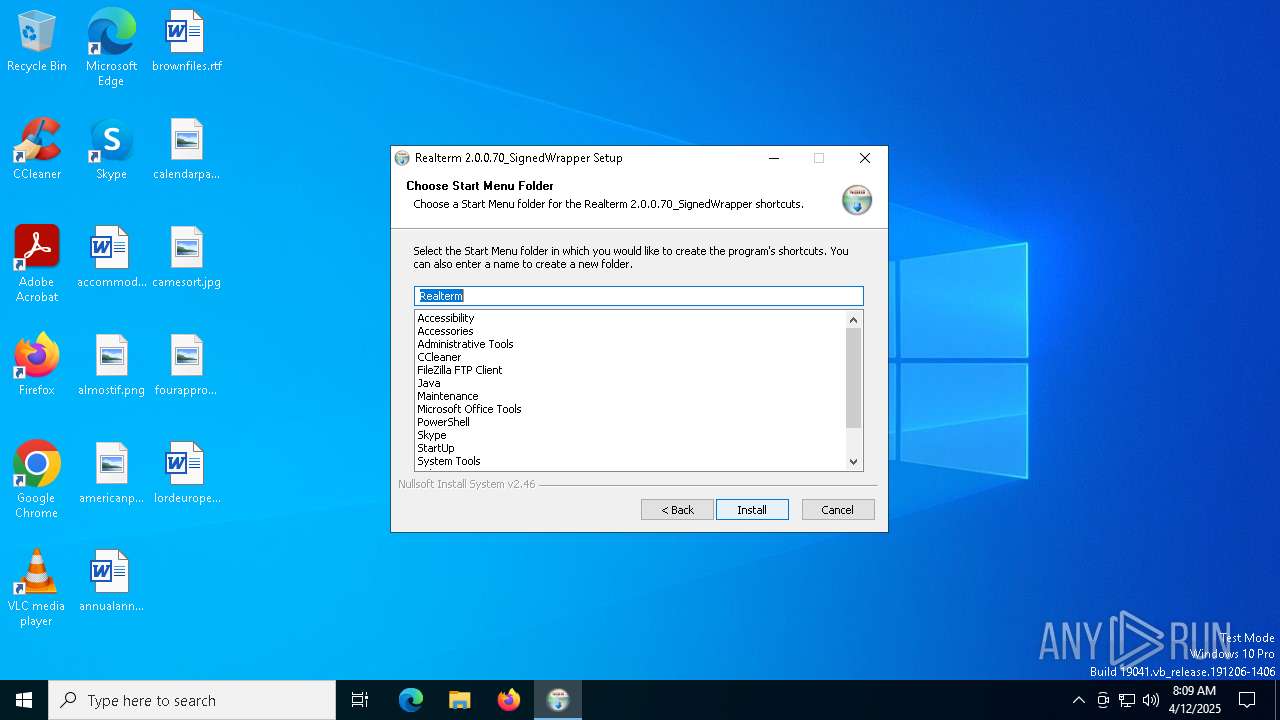
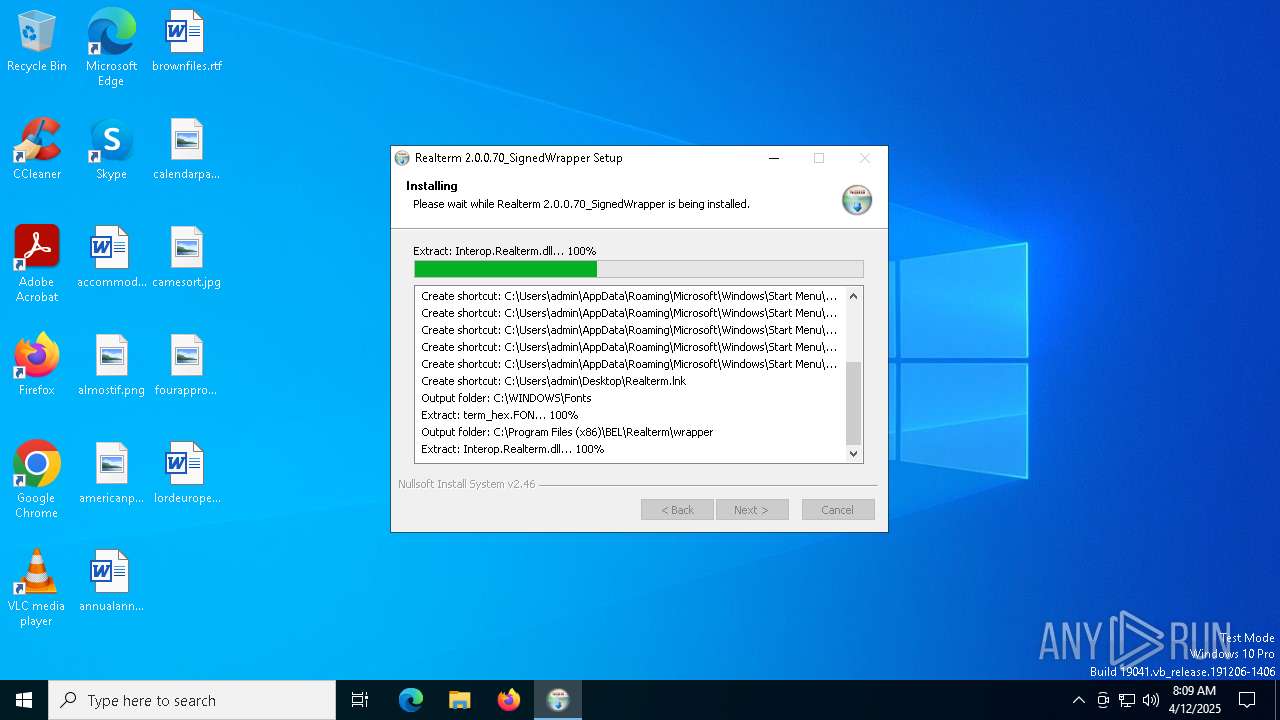
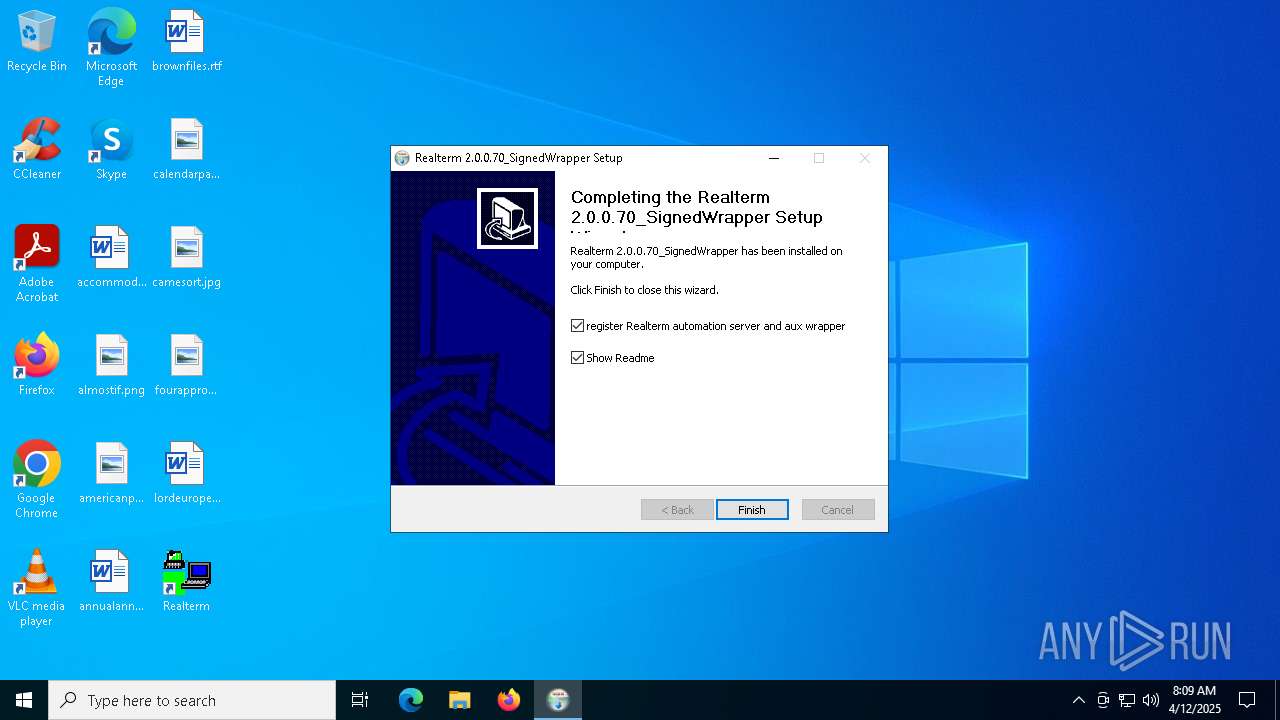
| File name: | Realterm_2.0.0.70_Signed_Wrapper_setup.exe |
| Full analysis: | https://app.any.run/tasks/ddb7f359-488e-4064-9827-46e2206667c2 |
| Verdict: | Malicious activity |
| Analysis date: | April 12, 2025, 08:08:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | BB396F3A9A59C871831C15E4F8B98D94 |
| SHA1: | 1523509458297C8507BB9F738D9D471A120AA2DE |
| SHA256: | F75B79C1E7FD34B0B33C848C6DF0BBE9AE48E981CB56002B42D63BB4B60E53B0 |
| SSDEEP: | 24576:fMZIH7o+OydDaYhe30JLla24MUW+9PLxcrlxRUwGTS:ED+xdULTH9PLxiSS |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
Creates a software uninstall entry
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
There is functionality for taking screenshot (YARA)
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
Executable content was dropped or overwritten
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
Malware-specific behavior (creating "System.dll" in Temp)
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
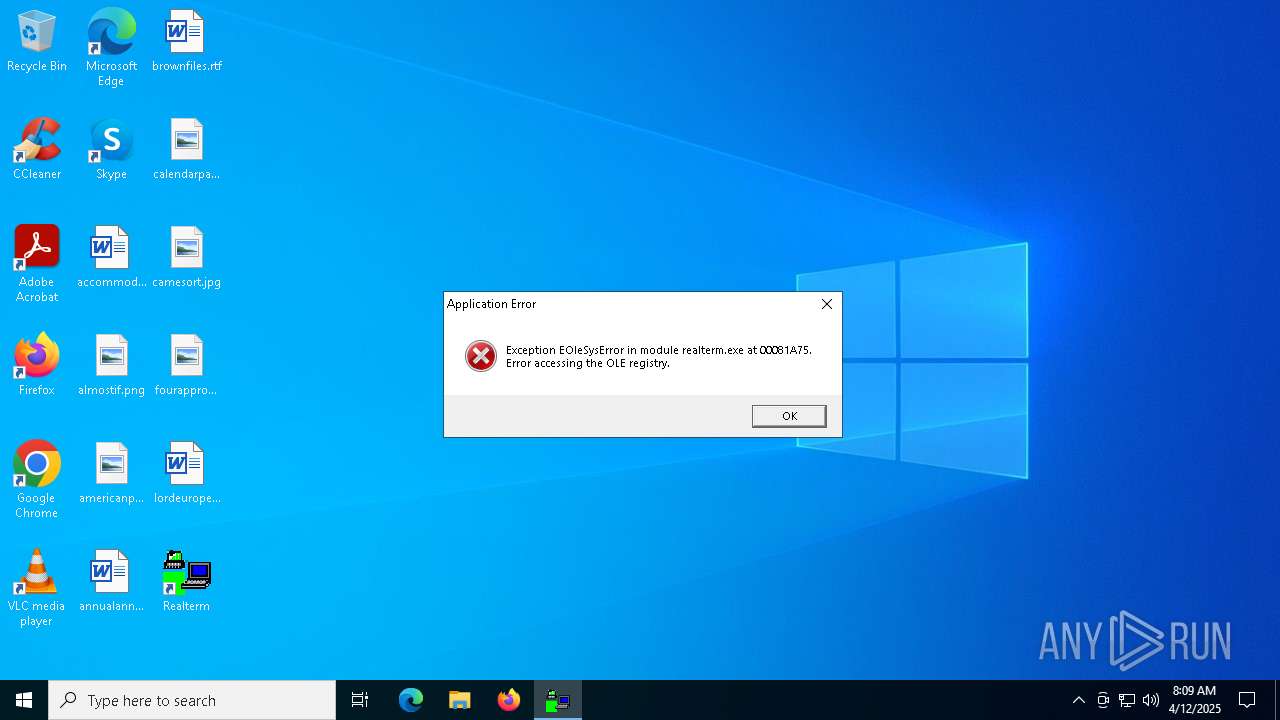
Executes application which crashes
- realterm.exe (PID: 1812)
Reads security settings of Internet Explorer
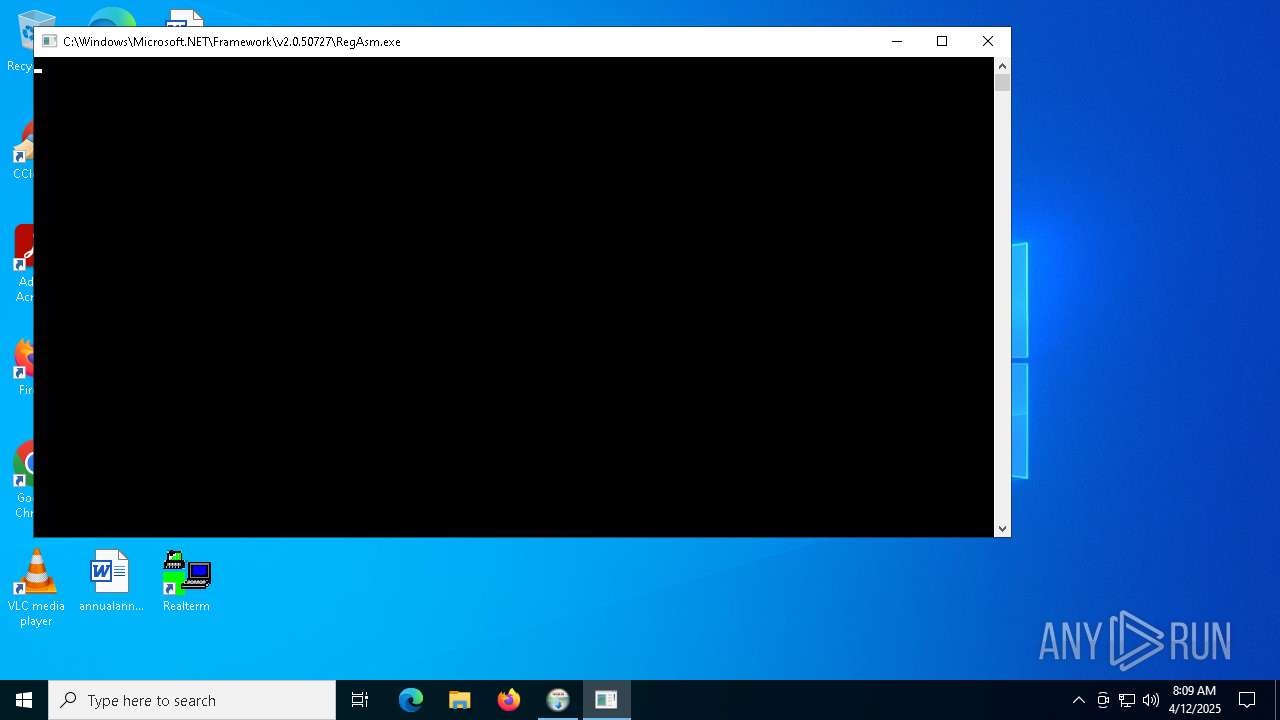
- RegAsm.exe (PID: 7588)
Creates/Modifies COM task schedule object
- RegAsm.exe (PID: 7588)
INFO
Create files in a temporary directory
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
Manual execution by a user
- realterm.exe (PID: 1812)
Creates files or folders in the user directory
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
- RegAsm.exe (PID: 7588)
- WerFault.exe (PID: 6240)
Checks supported languages
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
- RegAsm.exe (PID: 7588)
- realterm.exe (PID: 1812)
Reads the computer name
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
- realterm.exe (PID: 1812)
- RegAsm.exe (PID: 7588)
Creates files in the program directory
- Realterm_2.0.0.70_Signed_Wrapper_setup.exe (PID: 7180)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 7588)
Checks proxy server information
- RegAsm.exe (PID: 7588)
Reads the software policy settings
- RegAsm.exe (PID: 7588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23040 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30cb |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
141
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1812 | "C:\Program Files (x86)\BEL\Realterm\realterm.exe" | C:\Program Files (x86)\BEL\Realterm\realterm.exe | explorer.exe | ||||||||||||
User: admin Company: Broadcast Equipment Ltd Integrity Level: MEDIUM Exit code: 1 Version: 2.0.0.70 Modules
| |||||||||||||||
| 5244 | "C:\Users\admin\AppData\Local\Temp\Realterm_2.0.0.70_Signed_Wrapper_setup.exe" | C:\Users\admin\AppData\Local\Temp\Realterm_2.0.0.70_Signed_Wrapper_setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6240 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1812 -s 780 | C:\Windows\SysWOW64\WerFault.exe | — | realterm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7180 | "C:\Users\admin\AppData\Local\Temp\Realterm_2.0.0.70_Signed_Wrapper_setup.exe" | C:\Users\admin\AppData\Local\Temp\Realterm_2.0.0.70_Signed_Wrapper_setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7264 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7296 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7588 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" "C:\Program Files (x86)\BEL\Realterm\wrapper\RealtermWrapper.dll" /codebase | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 7596 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 743
Read events
5 723
Write events
20
Delete events
0
Modification events
| (PID) Process: | (7180) Realterm_2.0.0.70_Signed_Wrapper_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Terminal_Hex 9 |
Value: term_hex.FON | |||
| (PID) Process: | (7180) Realterm_2.0.0.70_Signed_Wrapper_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Realterm |
| Operation: | write | Name: | NSIS:StartMenuDir |
Value: Realterm | |||
| (PID) Process: | (7588) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{FA5F171A-61D3-4631-9100-84C500453D4F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (7588) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{FA5F171A-61D3-4631-9100-84C500453D4F}\InprocServer32 |
| Operation: | write | Name: | Class |
Value: RealTermWrapper.ClassRealTermWrapper | |||
| (PID) Process: | (7588) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{FA5F171A-61D3-4631-9100-84C500453D4F}\InprocServer32 |
| Operation: | write | Name: | Assembly |
Value: RealTermWrapper, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null | |||
| (PID) Process: | (7588) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{FA5F171A-61D3-4631-9100-84C500453D4F}\InprocServer32 |
| Operation: | write | Name: | RuntimeVersion |
Value: v2.0.50727 | |||
| (PID) Process: | (7588) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{FA5F171A-61D3-4631-9100-84C500453D4F}\InprocServer32 |
| Operation: | write | Name: | CodeBase |
Value: file:///C:/Program Files (x86)/BEL/Realterm/wrapper/RealTermWrapper.DLL | |||
| (PID) Process: | (7588) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{FA5F171A-61D3-4631-9100-84C500453D4F}\InprocServer32\1.0.0.0 |
| Operation: | write | Name: | Class |
Value: RealTermWrapper.ClassRealTermWrapper | |||
| (PID) Process: | (7588) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{FA5F171A-61D3-4631-9100-84C500453D4F}\InprocServer32\1.0.0.0 |
| Operation: | write | Name: | Assembly |
Value: RealTermWrapper, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null | |||
| (PID) Process: | (7588) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{FA5F171A-61D3-4631-9100-84C500453D4F}\InprocServer32\1.0.0.0 |
| Operation: | write | Name: | RuntimeVersion |
Value: v2.0.50727 | |||
Executable files
11
Suspicious files
26
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Users\admin\AppData\Local\Temp\nspB578.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Users\admin\AppData\Local\Temp\nspB578.tmp\StartMenu.dll | executable | |
MD5:A4173B381625F9F12AADB4E1CDAEFDB8 | SHA256:7755FF2707CA19344D489A5ACEC02D9E310425FA6E100D2F13025761676B875B | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Realterm\Realterm.lnk | binary | |
MD5:BC4A66188AAC9F9A6C7293D893C20933 | SHA256:9B1D2742AB1F9C9766211EABD653CBC0E73F69F6A73E6F09508D69A65F8043C4 | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Program Files (x86)\BEL\Realterm\realterm.exe | executable | |
MD5:6AC553C5D688F93890BEBE9D0B856576 | SHA256:175616843D3B087EF402AEAA63248CC92DC6E8B9C6BE07033AB812E27F7F1F5B | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Users\admin\AppData\Local\Temp\nspB578.tmp\InstallOptions.dll | executable | |
MD5:325B008AEC81E5AAA57096F05D4212B5 | SHA256:C9CD5C9609E70005926AE5171726A4142FFBCCCC771D307EFCD195DAFC1E6B4B | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Users\admin\AppData\Local\Temp\nspB578.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Program Files (x86)\BEL\Realterm\Readme.txt | text | |
MD5:7E44FE1443B9F09A46C4ADDFC92FE7F3 | SHA256:AE15794F6CE16079248AEE747660C557129F9C51AA689520D511FDD45783DE35 | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Realterm\Realterm I2C.lnk | binary | |
MD5:D685958AEEEE1C384076E0AF634D5833 | SHA256:D98CED7DB58FE1E9E621F96FDFBA3C1A032E16EB0D47C606B106CAB4389D8889 | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Realterm\Realterm I2C via USB.lnk | binary | |
MD5:BD8E9F745C0040B2877DD7149F6A4936 | SHA256:7D74EA2D67C020D8C499521D5E4FD58ECE8C1F99BFDFF9A97F032C315B032809 | |||
| 7180 | Realterm_2.0.0.70_Signed_Wrapper_setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Realterm\Realterm HalfDuplex RTSCTS.lnk | binary | |
MD5:8D7605E9AE550CBCFA14918C610A9041 | SHA256:0CD041984D1B23E20A0FCBAB87441827DC4CD968FB966349D32B3927120B2541 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
21
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.18.121.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7588 | RegAsm.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRm%2FrYSaqNr0YBIv29H4pMHhv2XmQQUl0gD6xUIa7myWCPMlC7xxmXSZI4CEARKoa%2F8q9sh21pD8bZmTow%3D | unknown | — | — | whitelisted |
7588 | RegAsm.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEALE0eWKSmgMVo2jBH5%2BTV8%3D | unknown | — | — | whitelisted |
7588 | RegAsm.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRm%2FrYSaqNr0YBIv29H4pMHhv2XmQQUl0gD6xUIa7myWCPMlC7xxmXSZI4CEARKoa%2F8q9sh21pD8bZmTow%3D | unknown | — | — | whitelisted |
7588 | RegAsm.exe | GET | 200 | 2.17.190.73:80 | http://crl3.digicert.com/ha-cs-2011a.crl | unknown | — | — | whitelisted |
8180 | SIHClient.exe | GET | 200 | 104.123.41.162:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8180 | SIHClient.exe | GET | 200 | 104.123.41.162:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.18.121.139:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7588 | RegAsm.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |