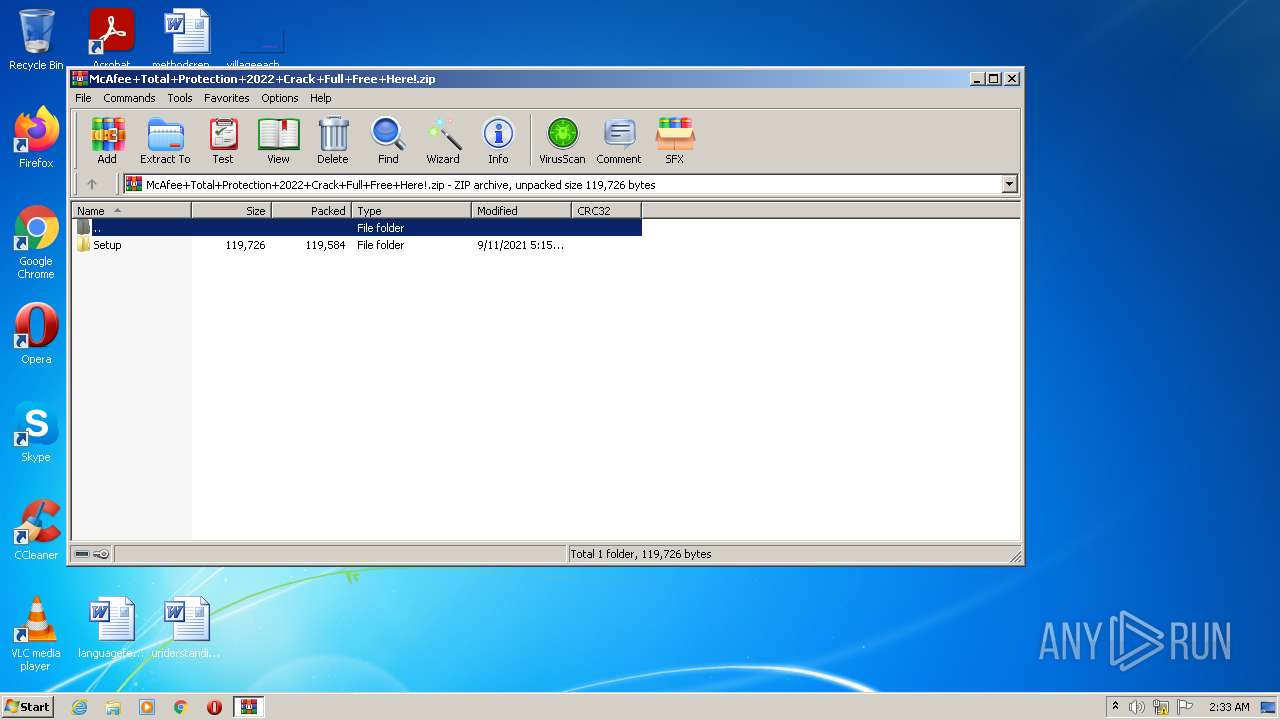
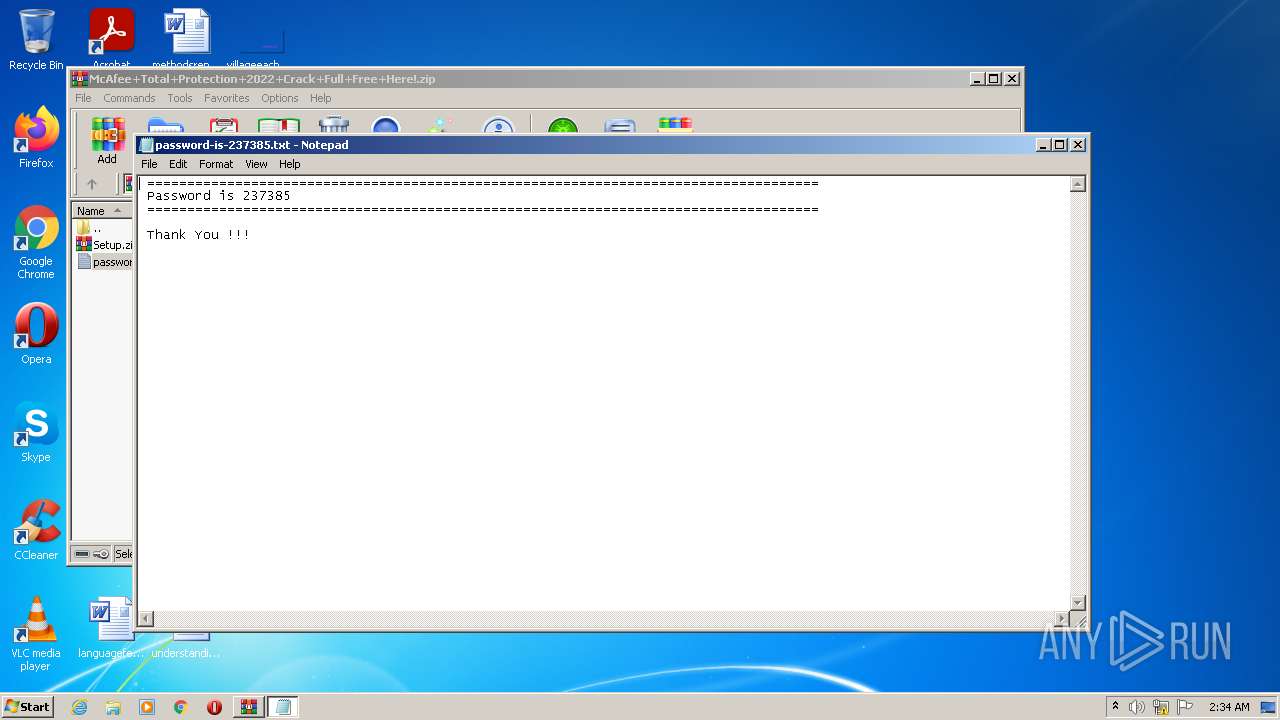
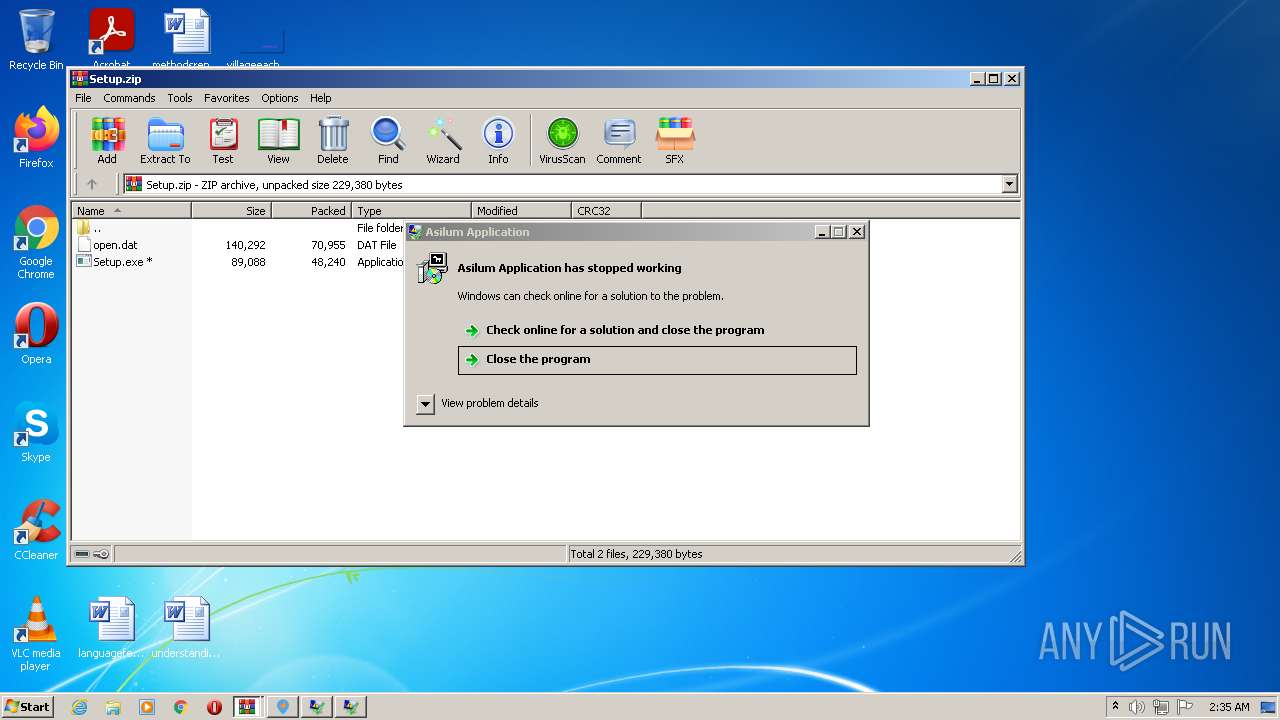
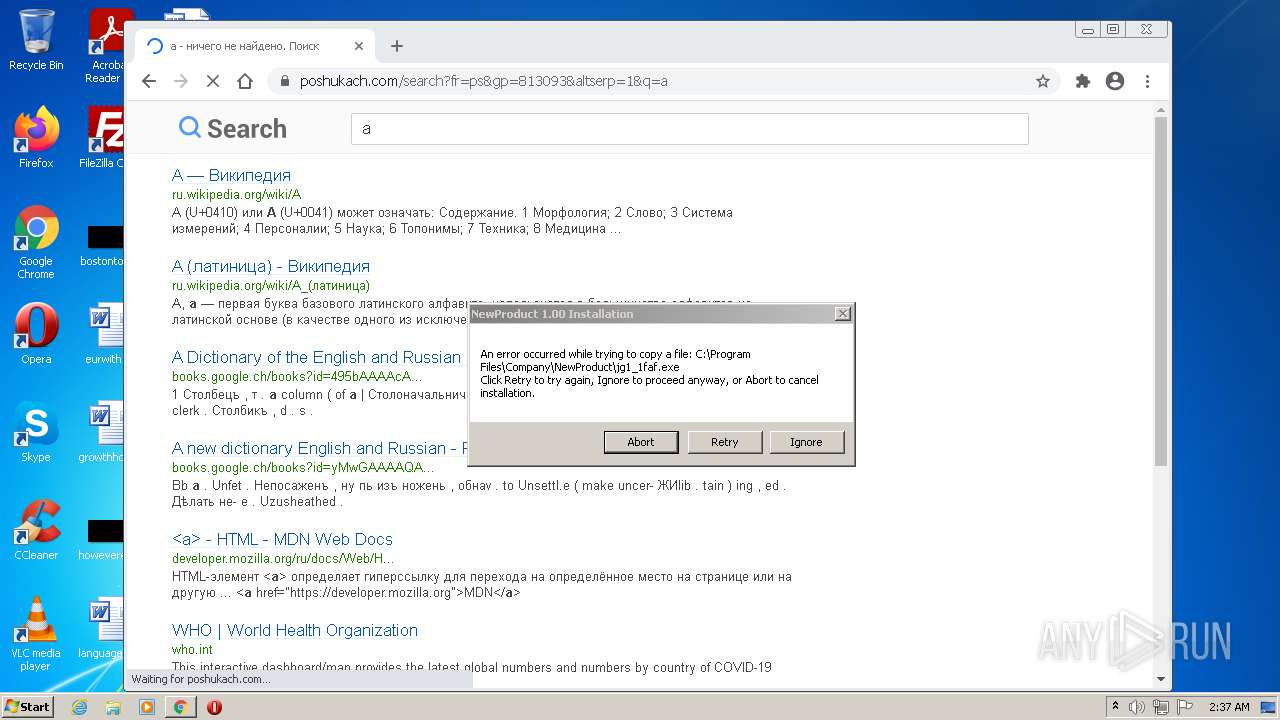
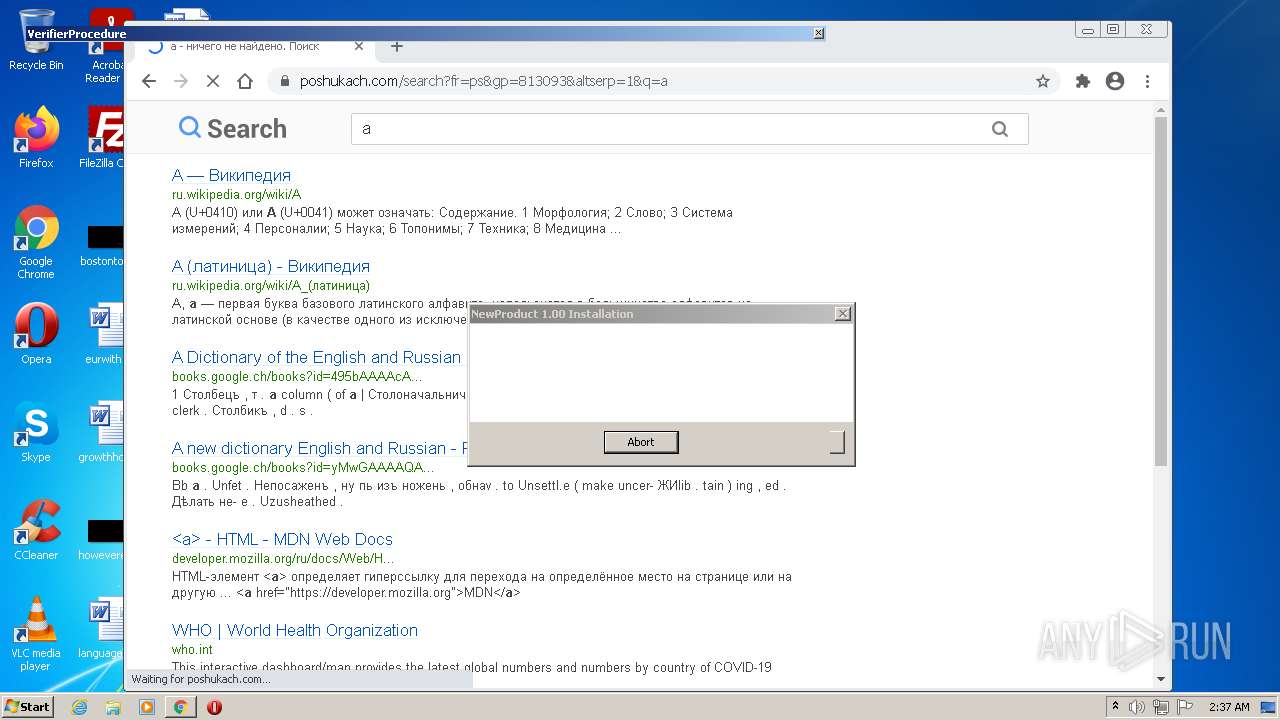
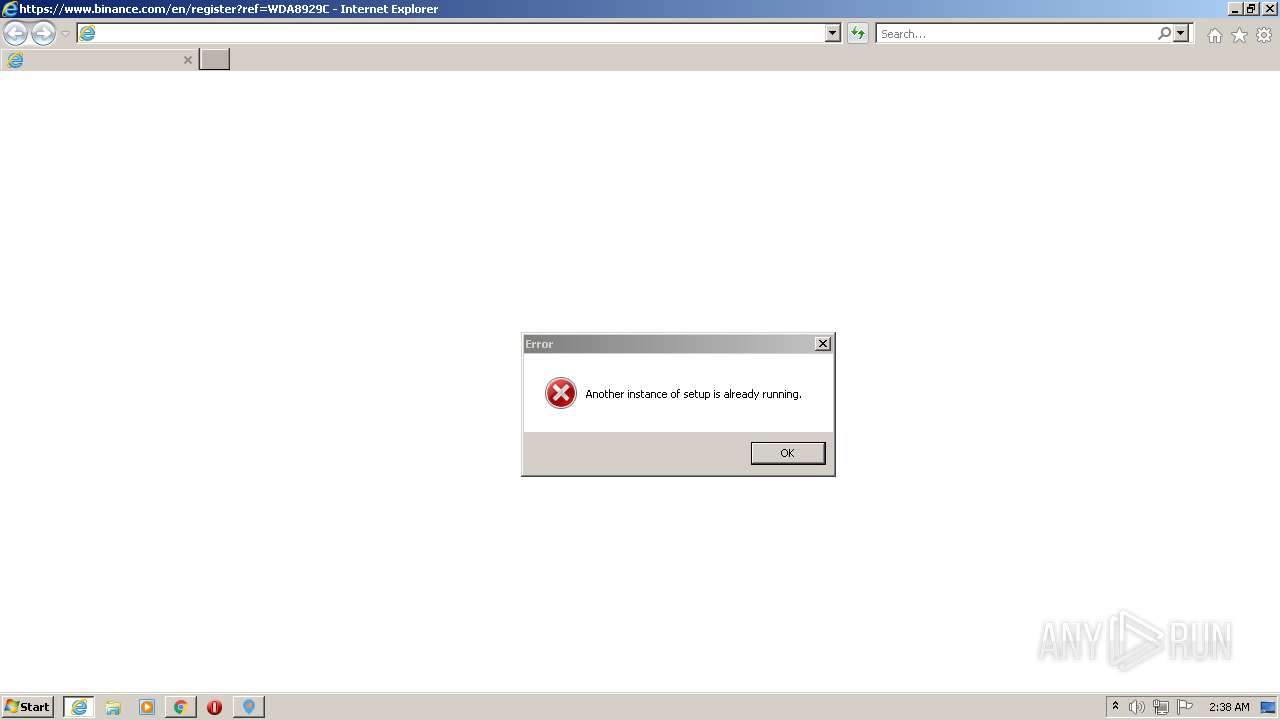
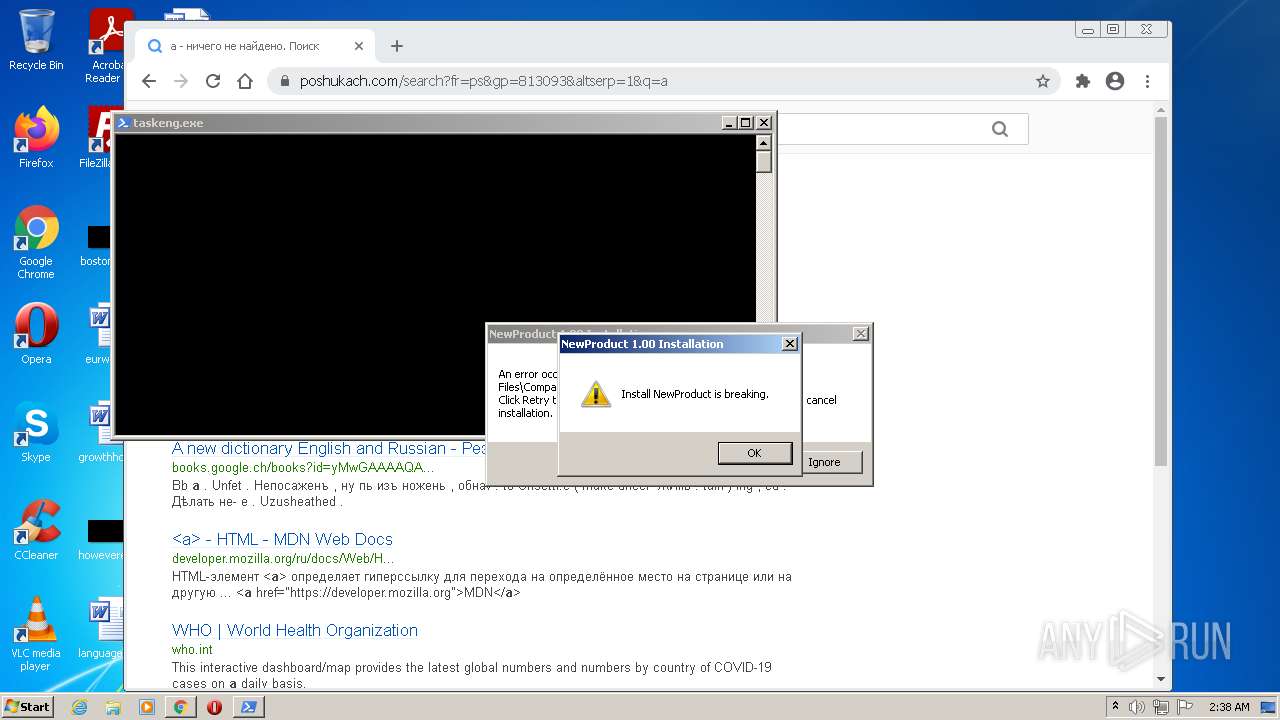
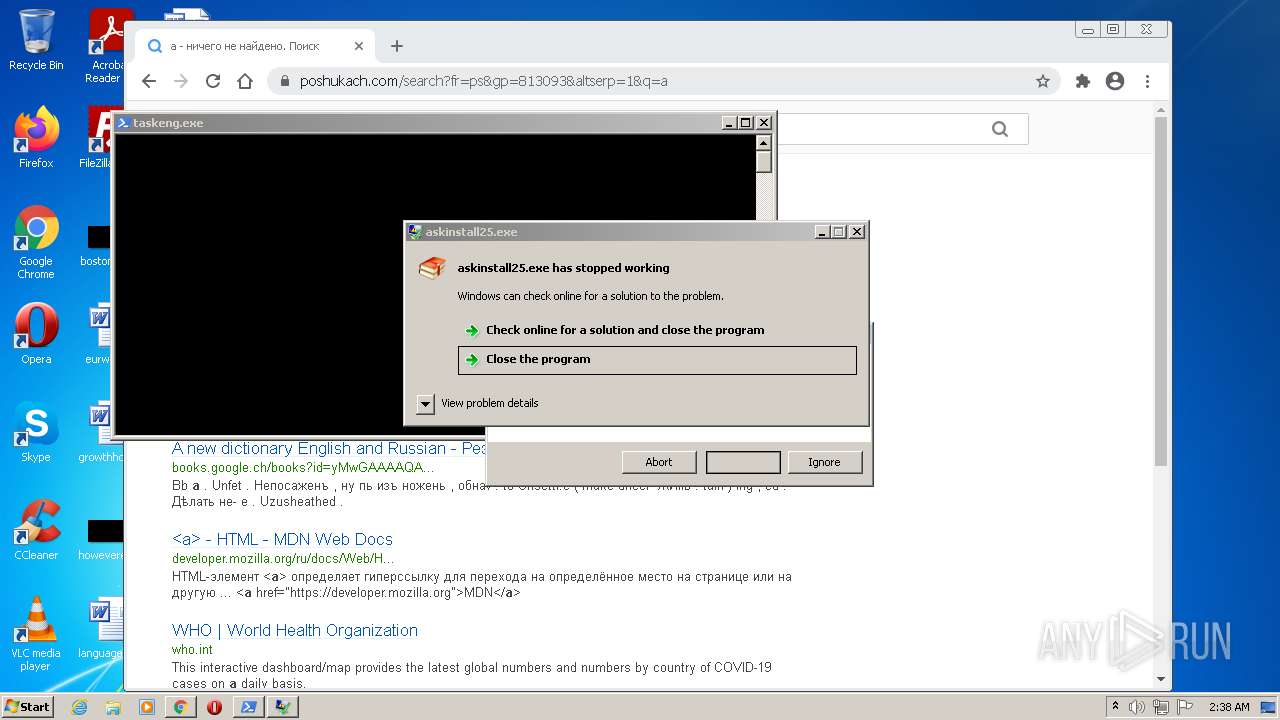
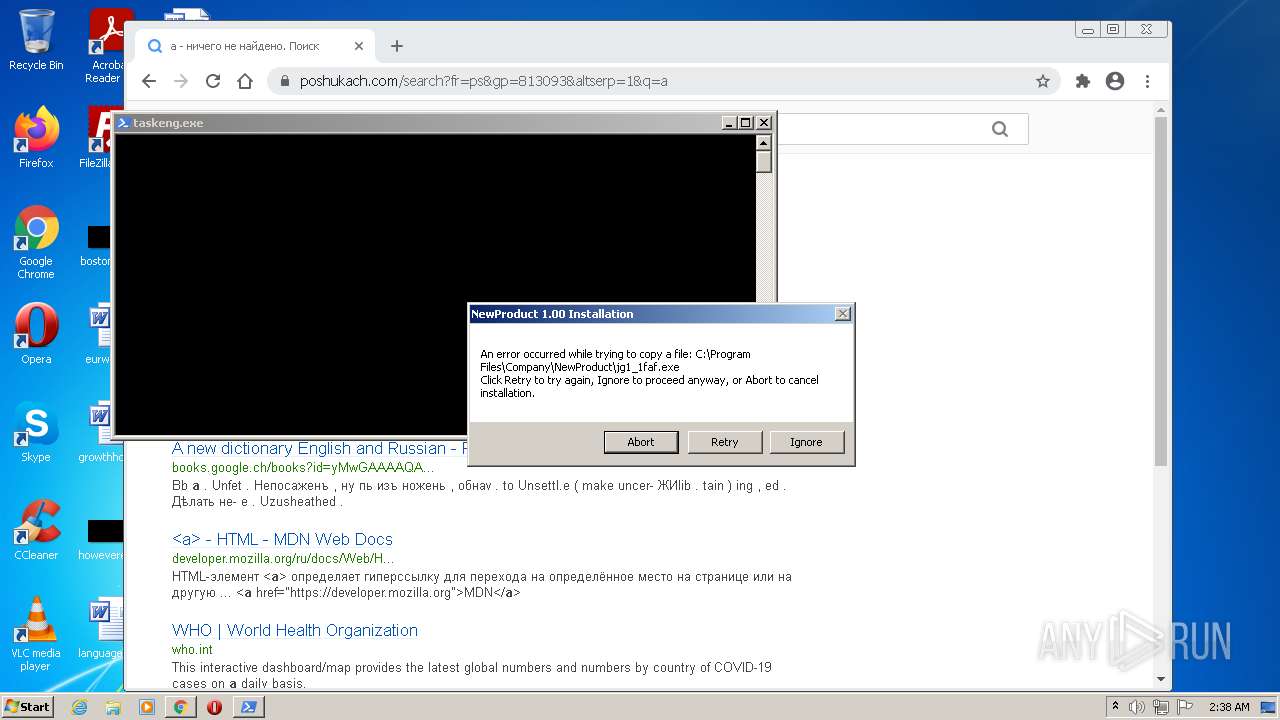
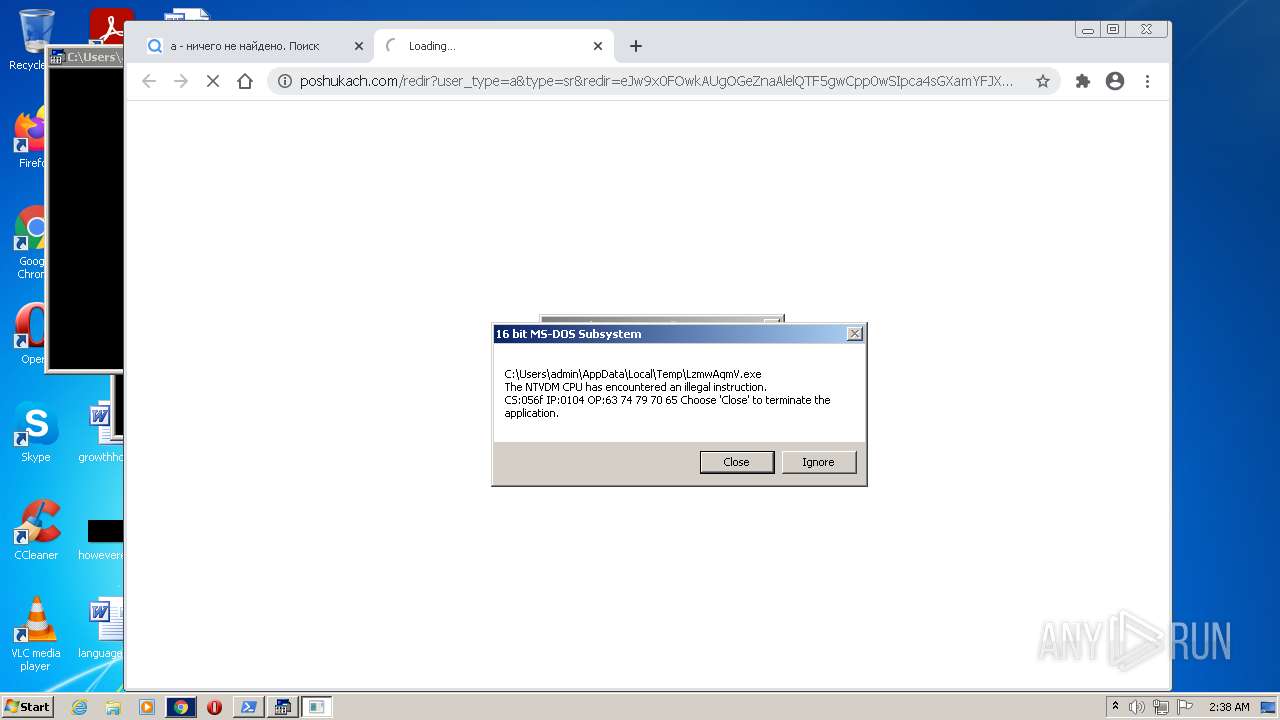
| File name: | McAfee+Total+Protection+2022+Crack+Full+Free+Here!.zip |
| Full analysis: | https://app.any.run/tasks/b2854e12-e4cb-419e-be39-96554a57c762 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 08, 2022, 02:33:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 68A2064FB56DBAC10768D9BDEB4D6AD6 |
| SHA1: | ADDA84425955F5E89F34DC66F068B9244DBDA2A0 |
| SHA256: | F75676A3C35E7918A80BBFE01E0BFA7B7561C57CD23EC26EA32A1DB37B5F65A3 |
| SSDEEP: | 3072:gydZCbGomfVVyrF+wqjXKdrELDZBE1Ez66lMB4sZscal/iBx:g8CKoaVVVwqjUrELD/WyjMewscaA |
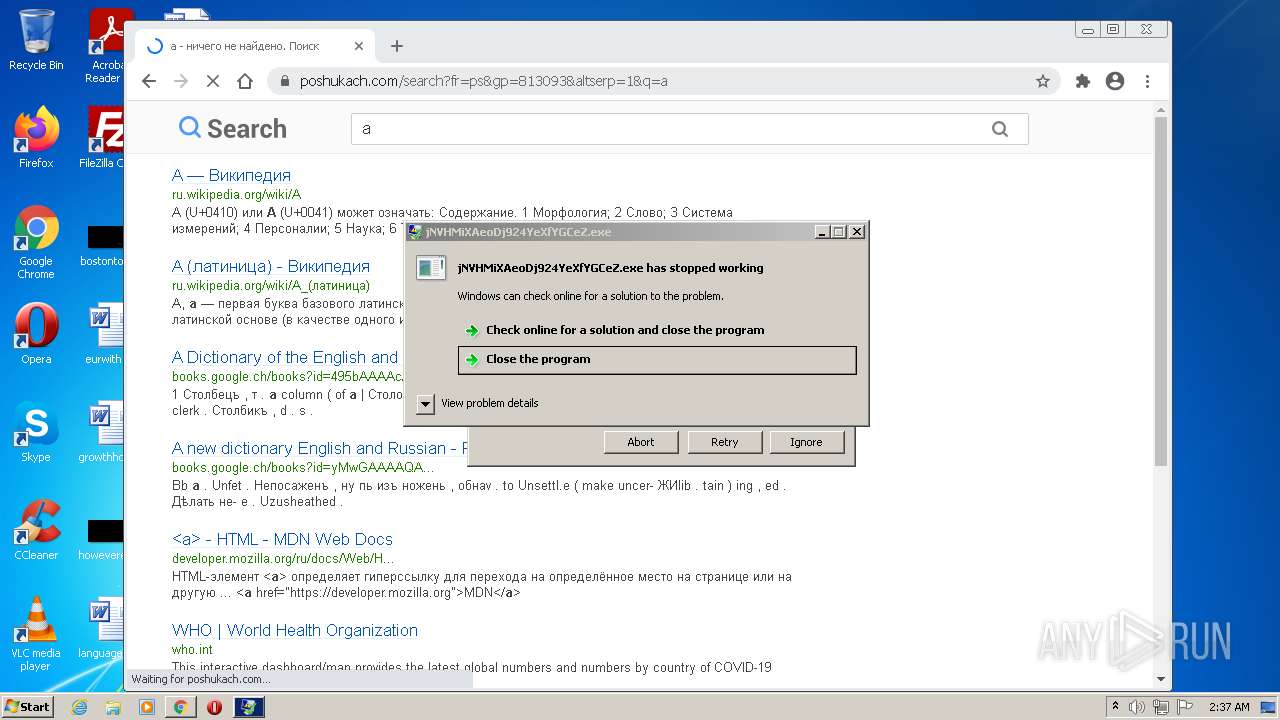
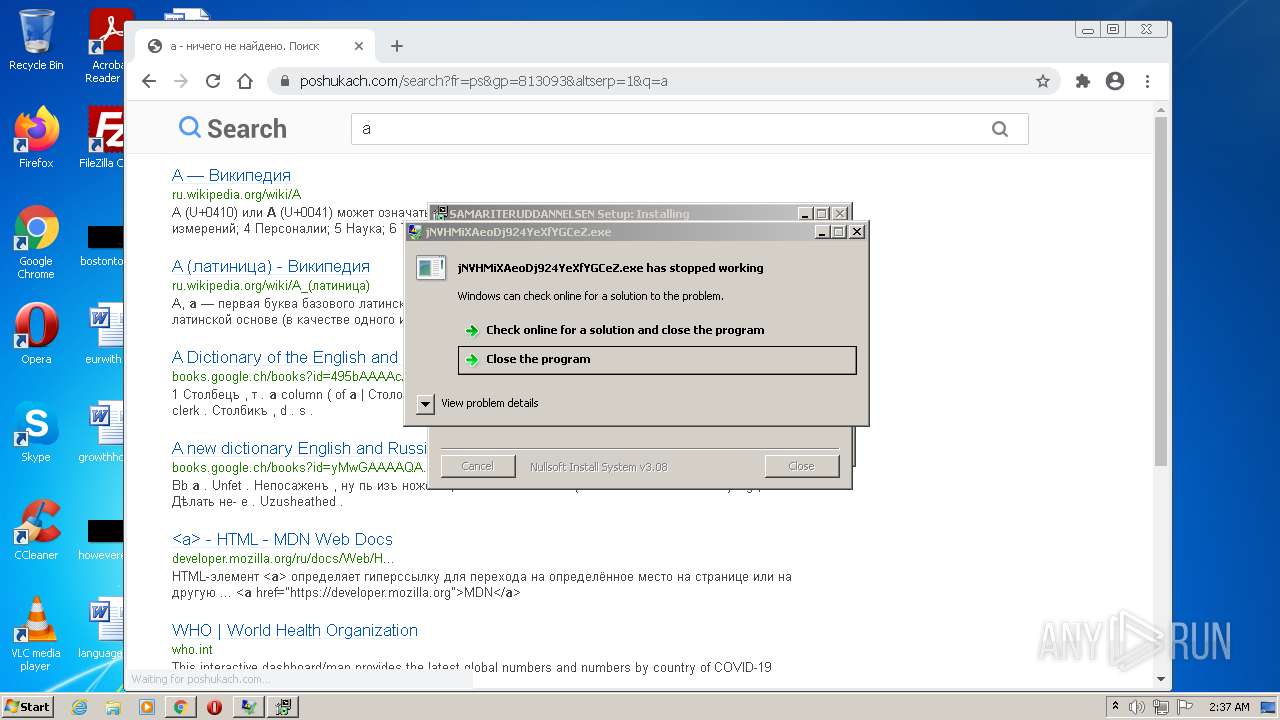
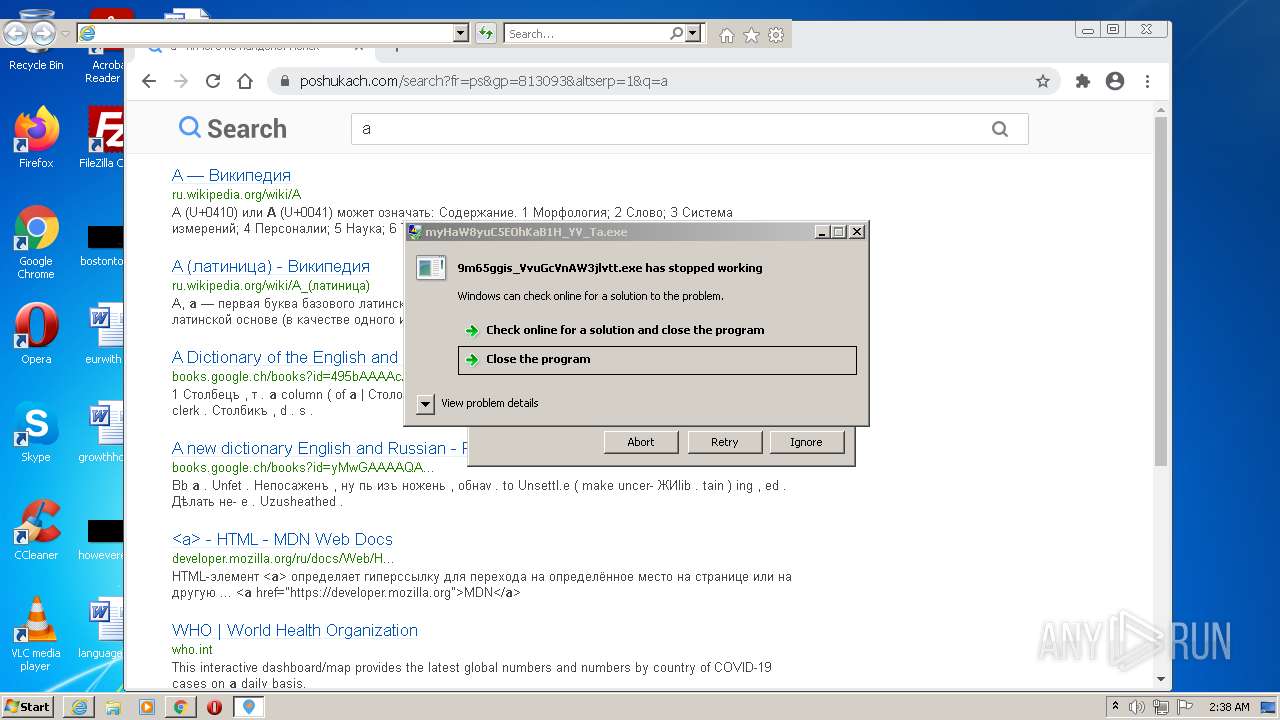
MALICIOUS
Application was dropped or rewritten from another process
- Setup.exe (PID: 3712)
- Setup.exe (PID: 2056)
- YolaProduct.exe (PID: 2728)
- tmn7Sjo6IZn07qqz6H1i1Sh2.exe (PID: 2136)
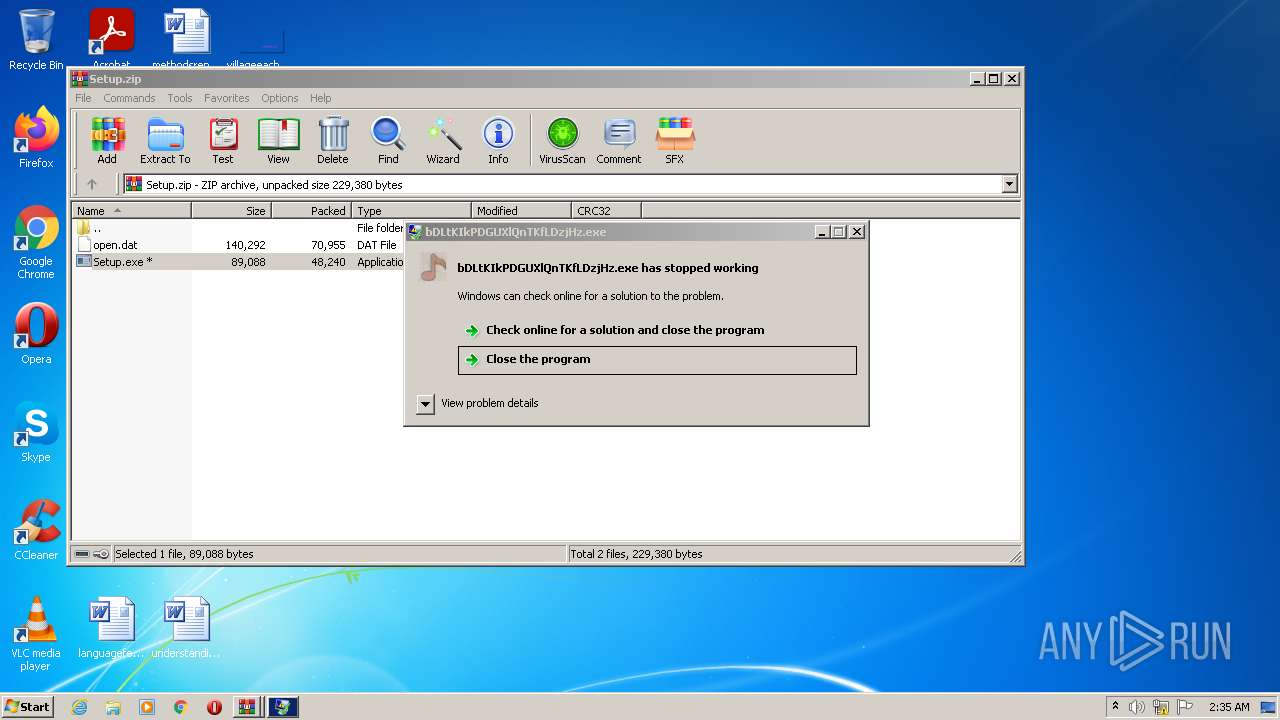
- bDLtKIkPDGUXlQnTKfLDzjHz.exe (PID: 3876)
- wLbwZiwylmvvsUg60goenS7x.exe (PID: 2836)
- lot6B1KTP_pdbqUFCU6MiDGA.exe (PID: 2608)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- gy1gLxA3MZWOpa_WnCvGPQNw.exe (PID: 3840)
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- XYxaWZnV6_ZHK4LEdZASMPgy.exe (PID: 3028)
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- XEPXrEV4VjKgc6Un0W8KFWRN.exe (PID: 3684)
- 4E57.tmp.exe (PID: 3092)
- 8LAXyC_p8pInUFq3lMbg2W3C.exe (PID: 2972)
- 6396.tmp.exe (PID: 2412)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- 2140854479.exe (PID: 2324)
- 2108352564.exe (PID: 304)
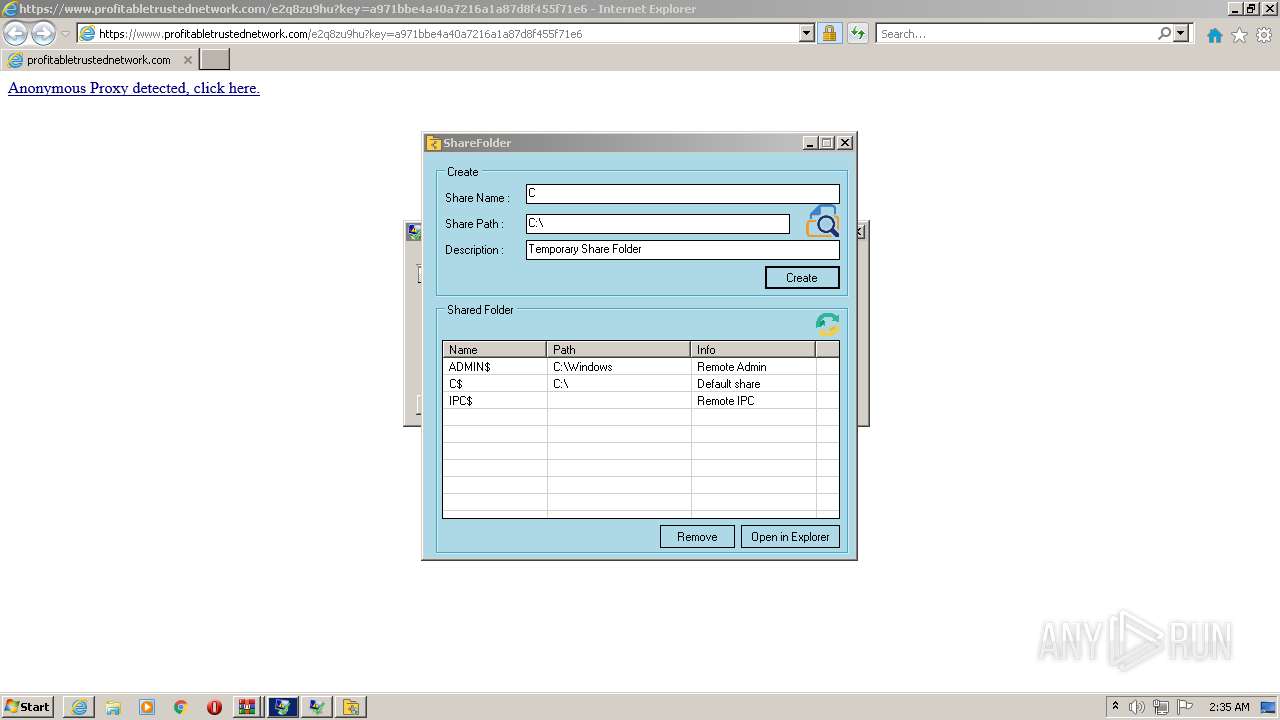
- foldershare.exe (PID: 3948)
- Xuvoqexaete.exe (PID: 3184)
- RnV3tDYP3fMyu10AW3eGaYqY.exe (PID: 2264)
- Manocabitae.exe (PID: 3328)
- installer.exe (PID: 4540)
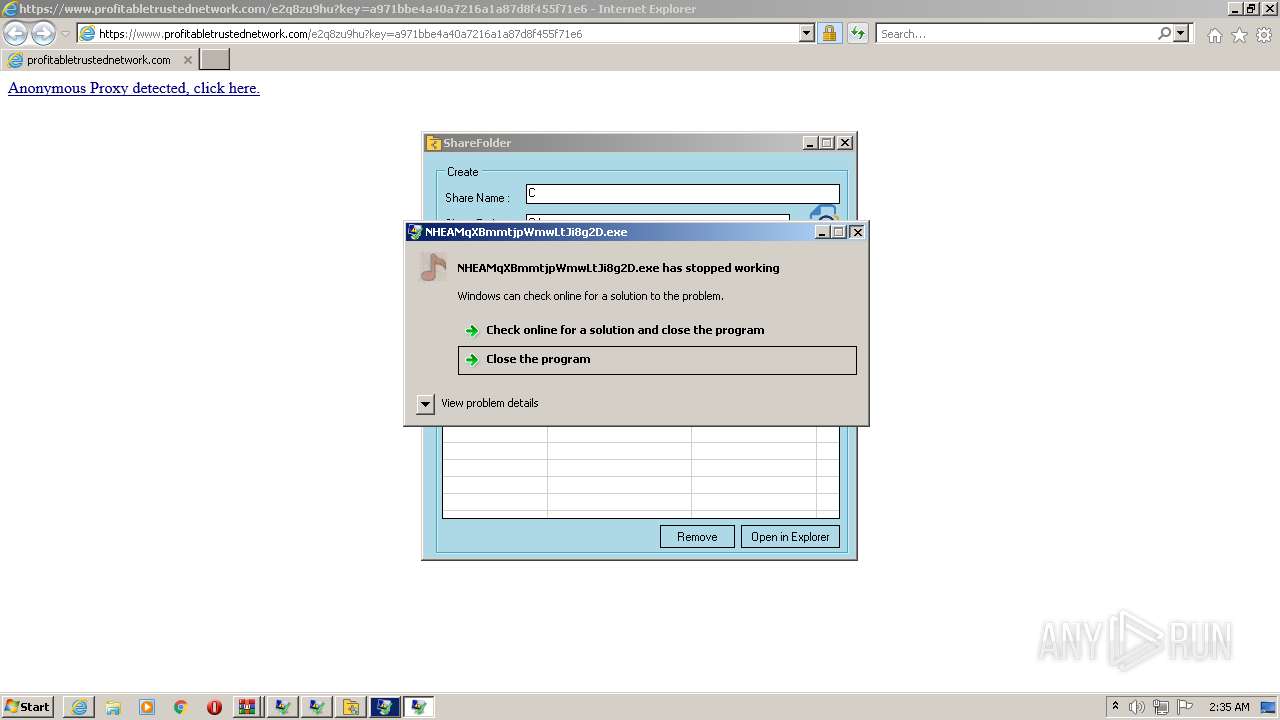
- NHEAMqXBmmtjpWmwLtJi8g2D.exe (PID: 5952)
- FolderShare.exe (PID: 2328)
- Hk3e5hUMBDXd60gA40t4ttwB.exe (PID: 3700)
- Install.exe (PID: 2008)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 684)
- EfrTS2cJrKrF9tU_CWt5DE4q.exe (PID: 4372)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 448)
- Install.exe (PID: 1712)
- OE41lqQEeScsiOPNwE1i9MNs.exe (PID: 4380)
- d76d02a6-6d7a-49c0-990d-5ff753f5541d.exe (PID: 2980)
- da02c158-e213-4a39-a4e4-a7a43dfeebaf.exe (PID: 4480)
- e3393c64-838a-41ac-92ee-42d077e2b298.exe (PID: 3172)
- be134b63-f3ed-48db-90de-f18bf51ecad9.exe (PID: 4324)
- FolderShare.exe (PID: 2012)
- FolderShare.exe (PID: 3284)
- oobeldr.exe (PID: 4144)
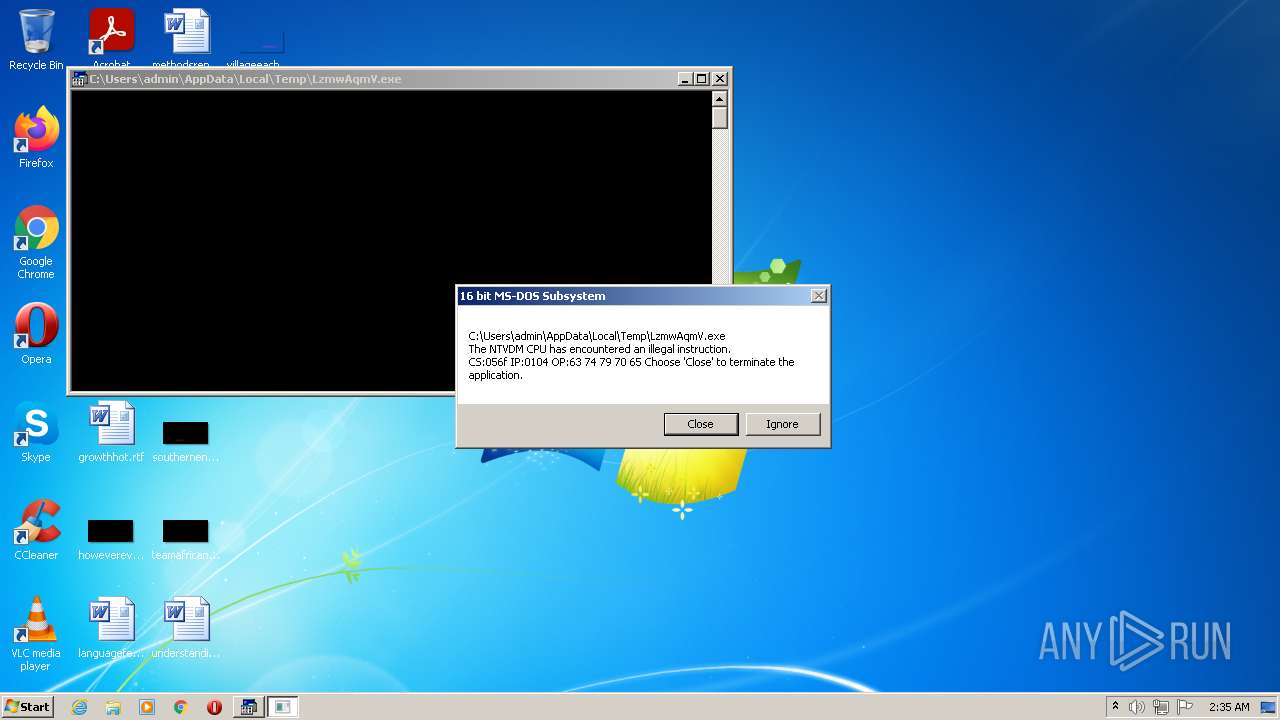
- LzmwAqmV.exe (PID: 4244)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- whw.exe (PID: 2508)
- e3dwefw.exe (PID: 4660)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- rBNZVTf.exe (PID: 1944)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- cab39dba-df17-44a9-944a-4e677ad59ba6.exe (PID: 5284)
- random.exe (PID: 2788)
- random.exe (PID: 4600)
- 161.exe (PID: 5712)
- a7b5240e-6154-478d-83bc-4fd17c9ace16.exe (PID: 5048)
- compan.exe (PID: 5264)
- appforpr3.exe (PID: 5316)
- Skype.exe (PID: 932)
- GrCDlHD.exe (PID: 3500)
- tapinstall.exe (PID: 4420)
- tapinstall.exe (PID: 5784)
- BumperWW.exe (PID: 3944)
- 0a9edfa1-4ad7-43cc-ad6e-7ad86348d19b.exe (PID: 3948)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- mask_svc.exe (PID: 2664)
- e476fe3b-0a9e-4566-a7bf-93dc815990e9.exe (PID: 4460)
- mask_svc.exe (PID: 3636)
- 6675827.exe (PID: 5128)
- 8087404.exe (PID: 4892)
- mask_svc.exe (PID: 4212)
- toolspab3.exe (PID: 392)
- autosubplayer.exe (PID: 4320)
- toolspab3.exe (PID: 856)
- vZKafuKKBs.exe (PID: 4644)
- gcleaner.exe (PID: 3572)
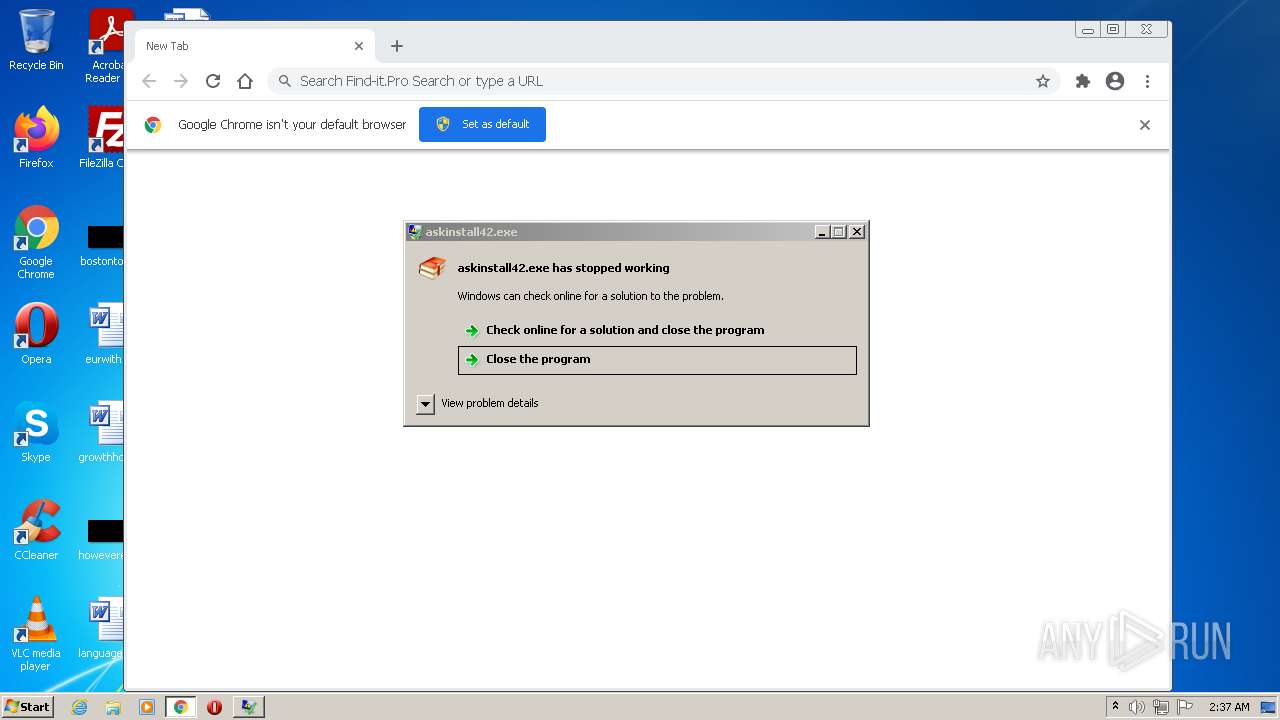
- askinstall42.exe (PID: 4832)
- Mmw6nxnPN4KNnjEZRFVLE8nS.exe (PID: 1940)
- setupWW1.exe (PID: 3416)
- ningli.exe (PID: 2148)
- ningli.exe (PID: 5152)
- RobCleanerInstlr842628.exe (PID: 5240)
- y08ZnvqEG9elxfTdvTJ1sNn2.exe (PID: 5780)
- 5kXjAgmXrycB6KYf6f_jxABW.exe (PID: 5940)
- mF4cAQIt3HG_K0iyqfbLSUgZ.exe (PID: 1712)
- mMkNQwcrxJo9Fac4EU9aFY3M.exe (PID: 4340)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- rodUdBfXS1K_82Xcij0P21Gl.exe (PID: 3772)
- toolspab2.exe (PID: 4892)
- toolspab2.exe (PID: 3792)
- toolspab2.exe (PID: 2576)
- XL_Q3_tQ9xsjQZ97ANEODGxC.exe (PID: 2288)
- oVUJDrxMkuXvEIKvf0tAZARQ.exe (PID: 4228)
- toolspab2.exe (PID: 4764)
- cnq2OFKbJxjmA8IFszJ1eBv9.exe (PID: 3908)
- m3hNcTJjxaMhPKSDC0pebxfF.exe (PID: 4988)
- XL_Q3_tQ9xsjQZ97ANEODGxC.exe (PID: 3788)
- DiF_p0nJlYu_PaiWDXNFPgds.exe (PID: 2300)
- mpRCIeopmt9ljZw2RlIFPmAU.exe (PID: 2672)
- SkypeCall.exe (PID: 1908)
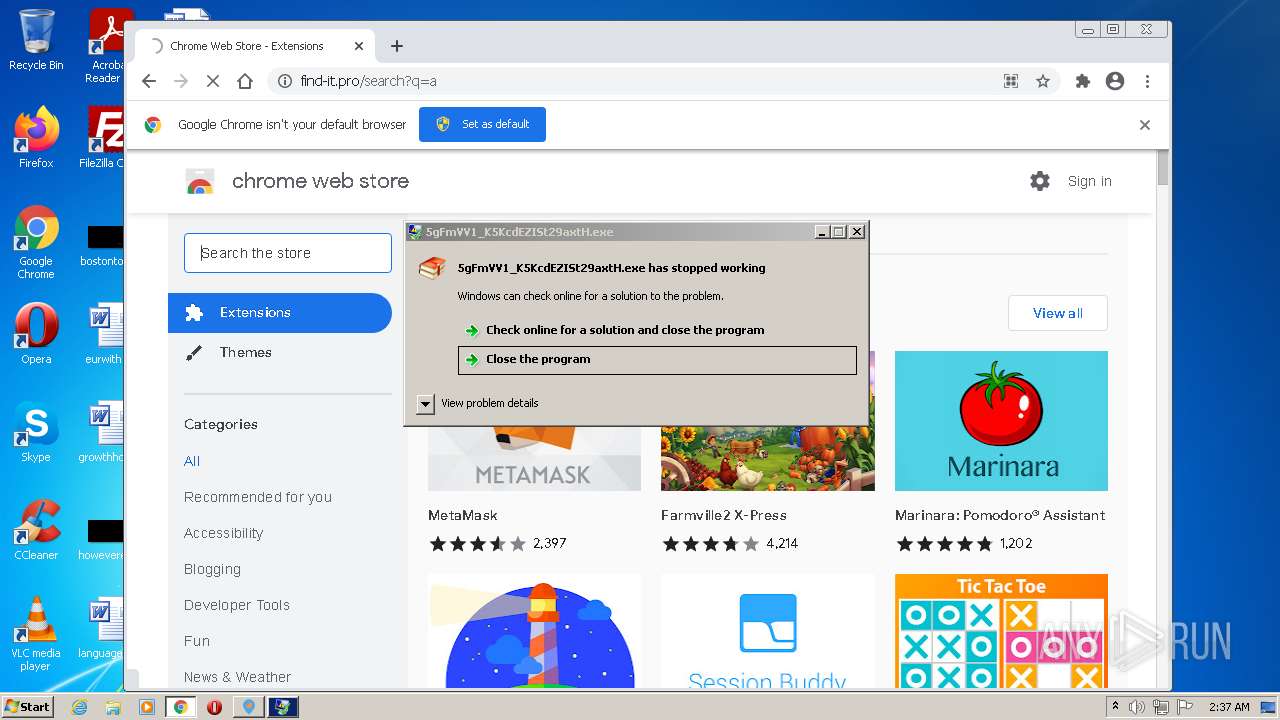
- 5gFmVV1_K5KcdEZISt29axtH.exe (PID: 5320)
- installer.exe (PID: 4072)
- yucyWdqfn4VZ5ppnVCnH9WSx.exe (PID: 4128)
- 517A.tmp.exe (PID: 6112)
- 5249137.exe (PID: 4268)
- RROhpXCwf_yy4nUf8P_Bumb4.exe (PID: 3604)
- 6229933.exe (PID: 2488)
- 6C37.tmp.exe (PID: 4788)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- wi3kHVFdALN7gKkOODFO1Bf2.exe (PID: 4412)
- SHesypalori.exe (PID: 784)
- nIwkJ3NyeUqrSBqzgclO8UpJ.exe (PID: 1248)
- Install.exe (PID: 5604)
- QNTiCURCOPYLfn5DY1cxPsb_.exe (PID: 3436)
- 609cecf0-d857-44ec-9889-96f74d16b573.exe (PID: 3488)
- U02XooqrUpC35QCI7LfEbTvM.exe (PID: 2960)
- 64957901-7123-4944-bef1-eb580816d9f4.exe (PID: 4256)
- Install.exe (PID: 4568)
- b1fd6d9d-915b-41bf-89b9-c8f45ae35a0a.exe (PID: 2684)
- MaskVPNUpdate.exe (PID: 2528)
- 4afb4e54-6c7c-428f-bc9f-b73da43b5986.exe (PID: 1244)
- 16b6b06e-4529-49fb-9238-a4190aaea354.exe (PID: 1516)
- 07bd4b3a-5579-4792-b414-969915d09db1.exe (PID: 4864)
- POp7YcvBq_iBSXjPDUu3jMZq.exe (PID: 4812)
- sIGlpcOj409XIIXz_MxTPI0f.exe (PID: 6036)
- T5qgYjHO2swRx3odddOWt1iA.exe (PID: 2932)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
- gXR3LnTkVr_A5Wu2fjqZnIgq.exe (PID: 5328)
- myHaW8yuC5EOhKaB1H_YV_Ta.exe (PID: 4512)
- J4jxleDPfzWENFGiWtAZ7J0C.exe (PID: 5732)
- v6rRqy39NiR5vd8orjDd7xOs.exe (PID: 6832)
- 1KPXa4tWwVKo4Ujosf8rYhux.exe (PID: 5176)
- nH6w2_8ew6Clk3jfZX215fvF.exe (PID: 932)
- s33zVhbrQHP2KNvnWJv3lkX2.exe (PID: 6800)
- ETKJsDBjLNKmmA8APYe59Mt1.exe (PID: 8108)
- s33zVhbrQHP2KNvnWJv3lkX2.exe (PID: 4092)
- gXR3LnTkVr_A5Wu2fjqZnIgq.exe (PID: 7836)
- AjtguB8MYJVD6XXYsVsajabZ.exe (PID: 6852)
- nec9RrUzAn8eXZdKGatvXuQR.exe (PID: 7024)
- NPQpbHyrbXKNeDvAuu66TWPf.exe (PID: 3180)
- aeb1c8a8-22cc-473a-a8a0-97c94c66160a.exe (PID: 6276)
- VedOY0yQ_rn7KR6Kx7u805ks.exe (PID: 7848)
- k7IXpemtWNtlL0cPOY9kIl_H.exe (PID: 4192)
- F8F5.tmp.exe (PID: 5592)
- 9da61c9d-7522-4bbc-91c5-e6352a108a09.exe (PID: 8184)
- f76ae109-bf54-45c6-b7e8-3beb8af8d55c.exe (PID: 7524)
- GcUIQmlpOqe0dsslLxJJn9Uh.exe (PID: 6760)
- 92O9eq6j8LZXnGK51uulqmqP.exe (PID: 5820)
- MyNotes License Agreement.exe (PID: 3704)
- installer.exe (PID: 5032)
Actions looks like stealing of personal data
- WinRAR.exe (PID: 2024)
- svchost.exe (PID: 860)
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- AppLaunch.exe (PID: 3064)
- 2140854479.exe (PID: 2324)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- RegAsm.exe (PID: 4972)
- AppLaunch.exe (PID: 5424)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- LzmwAqmV.exe (PID: 4244)
- whw.exe (PID: 2508)
- Proxyupd.exe (PID: 2680)
- da02c158-e213-4a39-a4e4-a7a43dfeebaf.exe (PID: 4480)
- d76d02a6-6d7a-49c0-990d-5ff753f5541d.exe (PID: 2980)
- GrCDlHD.exe (PID: 3500)
- jg1_1faf.exe (PID: 4928)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- Skype.exe (PID: 932)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- setupWW1.exe (PID: 3416)
- 41c3b0fa-e7c8-4ca1-a053-ac6be3b11ea7.exe (PID: 2396)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- Proxytest.exe (PID: 3452)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- SkypeCall.exe (PID: 1908)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- AppLaunch.exe (PID: 4540)
Drops executable file immediately after starts
- Setup.exe (PID: 2056)
- tmn7Sjo6IZn07qqz6H1i1Sh2.exe (PID: 2136)
- wLbwZiwylmvvsUg60goenS7x.exe (PID: 2836)
- lot6B1KTP_pdbqUFCU6MiDGA.exe (PID: 2608)
- 8LAXyC_p8pInUFq3lMbg2W3C.exe (PID: 2972)
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- foldershare.exe (PID: 3948)
- foldershare.tmp (PID: 3680)
- 161.exe (PID: 5712)
- 161.tmp (PID: 3640)
- DrvInst.exe (PID: 2888)
Disables Windows Defender
- YolaProduct.exe (PID: 2728)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- Cube_WW9.exe (PID: 5832)
- Cube_WW6.exe (PID: 4780)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
Changes settings of System certificates
- YolaProduct.exe (PID: 2728)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- tapinstall.exe (PID: 4420)
- 161.tmp (PID: 3640)
Connects to CnC server
- YolaProduct.exe (PID: 2728)
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- gy1gLxA3MZWOpa_WnCvGPQNw.exe (PID: 3840)
- AppLaunch.exe (PID: 3064)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- AppLaunch.exe (PID: 5424)
- RegAsm.exe (PID: 4972)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- Proxyupd.exe (PID: 2680)
- whw.exe (PID: 2508)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- jg1_1faf.exe (PID: 4928)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- Skype.exe (PID: 932)
- Cube_WW9.exe (PID: 5832)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- Proxytest.exe (PID: 3452)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- oVUJDrxMkuXvEIKvf0tAZARQ.exe (PID: 4228)
- SkypeCall.exe (PID: 1908)
- DiF_p0nJlYu_PaiWDXNFPgds.exe (PID: 2300)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- Cube_WW6.exe (PID: 4780)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- GxkzeclbRO6fsAj5eQpALE1r.exe (PID: 5828)
- AppLaunch.exe (PID: 3544)
- RegAsm.exe (PID: 2124)
- AppLaunch.exe (PID: 4540)
- v6rRqy39NiR5vd8orjDd7xOs.exe (PID: 6832)
- l58AyrpWc_x3uK64FIAv2U0g.exe (PID: 5844)
- yLNfk8Wo9h9hCpCbfVNs9hdl.exe (PID: 6024)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
- T5qgYjHO2swRx3odddOWt1iA.exe (PID: 2932)
- mKNGqUoarnlCnNBAH1Gpxgt5.exe (PID: 4776)
Loads dropped or rewritten executable
- lot6B1KTP_pdbqUFCU6MiDGA.exe (PID: 2608)
- wLbwZiwylmvvsUg60goenS7x.exe (PID: 2836)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- 2140854479.exe (PID: 2324)
- WerFault.exe (PID: 1300)
- WerFault.exe (PID: 3956)
- MsiExec.exe (PID: 2940)
- MsiExec.exe (PID: 5692)
- installer.exe (PID: 4540)
- MsiExec.exe (PID: 3444)
- rundll32.exe (PID: 5072)
- rundll32.exe (PID: 4844)
- rundll32.exe (PID: 5584)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- rundll32.EXE (PID: 2604)
- mask_svc.exe (PID: 4212)
- 5kXjAgmXrycB6KYf6f_jxABW.exe (PID: 5940)
- y08ZnvqEG9elxfTdvTJ1sNn2.exe (PID: 5780)
- rundll32.exe (PID: 5804)
- installer.exe (PID: 4072)
- MsiExec.exe (PID: 5672)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- MaskVPNUpdate.exe (PID: 2528)
- sIGlpcOj409XIIXz_MxTPI0f.exe (PID: 6036)
- POp7YcvBq_iBSXjPDUu3jMZq.exe (PID: 4812)
- MyNotes License Agreement.exe (PID: 3704)
- MsiExec.exe (PID: 7804)
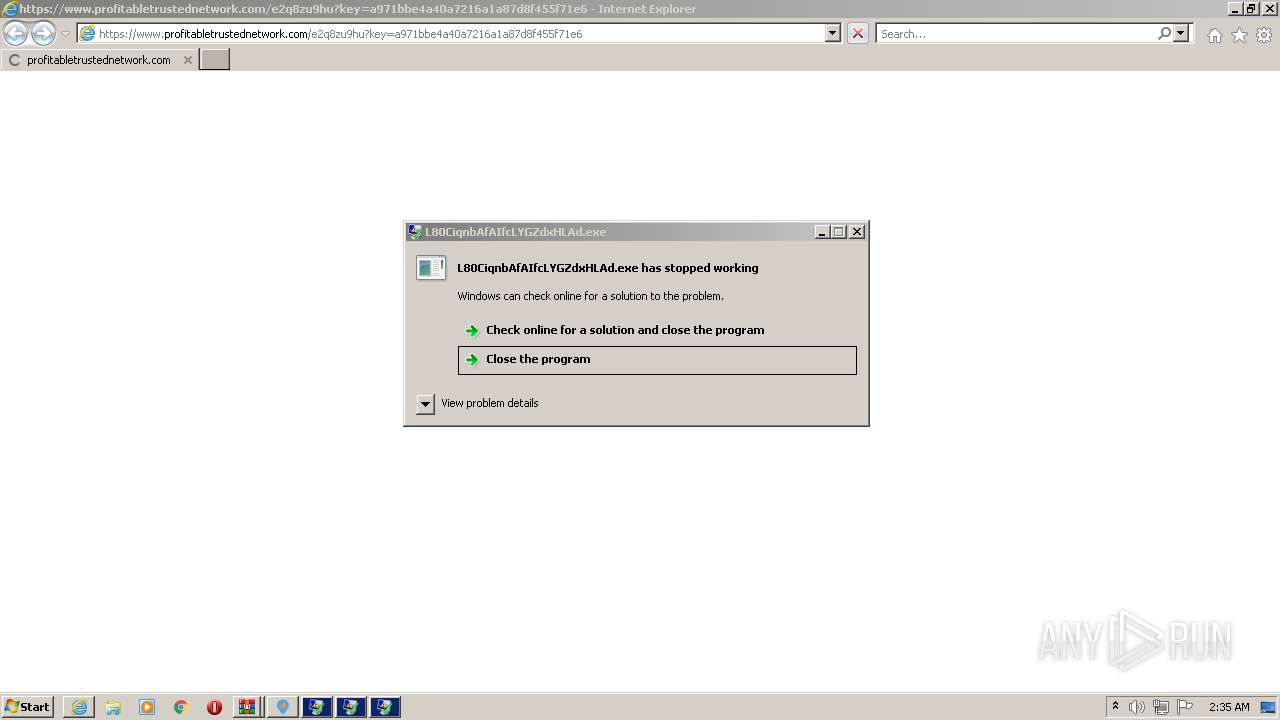
REDLINE was detected
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- AppLaunch.exe (PID: 3064)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- AppLaunch.exe (PID: 5424)
- RegAsm.exe (PID: 4972)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- Proxyupd.exe (PID: 2680)
- whw.exe (PID: 2508)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- Skype.exe (PID: 932)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- Proxytest.exe (PID: 3452)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- oVUJDrxMkuXvEIKvf0tAZARQ.exe (PID: 4228)
- SkypeCall.exe (PID: 1908)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- DiF_p0nJlYu_PaiWDXNFPgds.exe (PID: 2300)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- GxkzeclbRO6fsAj5eQpALE1r.exe (PID: 5828)
- AppLaunch.exe (PID: 3544)
- RegAsm.exe (PID: 2124)
- AppLaunch.exe (PID: 4540)
- v6rRqy39NiR5vd8orjDd7xOs.exe (PID: 6832)
- mKNGqUoarnlCnNBAH1Gpxgt5.exe (PID: 4776)
- l58AyrpWc_x3uK64FIAv2U0g.exe (PID: 5844)
- yLNfk8Wo9h9hCpCbfVNs9hdl.exe (PID: 6024)
- T5qgYjHO2swRx3odddOWt1iA.exe (PID: 2932)
Steals credentials from Web Browsers
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- AppLaunch.exe (PID: 3064)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- 2140854479.exe (PID: 2324)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- RegAsm.exe (PID: 4972)
- AppLaunch.exe (PID: 5424)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- Proxyupd.exe (PID: 2680)
- whw.exe (PID: 2508)
- GrCDlHD.exe (PID: 3500)
- jg1_1faf.exe (PID: 4928)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- Skype.exe (PID: 932)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- SkypeCall.exe (PID: 1908)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- AppLaunch.exe (PID: 4540)
- Proxytest.exe (PID: 3452)
VIDAR was detected
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- 2140854479.exe (PID: 2324)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- eP2zoDXXj8JTcj7ImFefr1oj.exe (PID: 6820)
Writes to a start menu file
- 6396.tmp.exe (PID: 2412)
- 6C37.tmp.exe (PID: 4788)
Uses Task Scheduler to run other applications
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- Install.exe (PID: 1712)
- e3dwefw.exe (PID: 4660)
- oobeldr.exe (PID: 4144)
- rBNZVTf.exe (PID: 1944)
- GrCDlHD.exe (PID: 3500)
- rundll32.EXE (PID: 2604)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- Install.exe (PID: 4568)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
Uses Task Scheduler to autorun other applications
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- GrCDlHD.exe (PID: 3500)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2508)
- schtasks.exe (PID: 3708)
- schtasks.exe (PID: 5124)
- schtasks.exe (PID: 4720)
- MsiExec.exe (PID: 3444)
- svchost.exe (PID: 860)
- schtasks.exe (PID: 3688)
- schtasks.exe (PID: 4748)
- schtasks.exe (PID: 2164)
- schtasks.exe (PID: 3132)
- schtasks.exe (PID: 5072)
- schtasks.exe (PID: 2100)
- schtasks.exe (PID: 4976)
- schtasks.exe (PID: 2360)
- installer.exe (PID: 4540)
- schtasks.exe (PID: 5796)
- schtasks.exe (PID: 5040)
- schtasks.exe (PID: 5252)
- schtasks.exe (PID: 4496)
- schtasks.exe (PID: 4784)
- schtasks.exe (PID: 2460)
- schtasks.exe (PID: 1972)
- schtasks.exe (PID: 4496)
- schtasks.exe (PID: 3604)
- schtasks.exe (PID: 6004)
- schtasks.exe (PID: 5912)
- schtasks.exe (PID: 2360)
- schtasks.exe (PID: 3316)
- schtasks.exe (PID: 2064)
- schtasks.exe (PID: 5948)
- schtasks.exe (PID: 6688)
- schtasks.exe (PID: 7000)
Stealing of credential data
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- 2140854479.exe (PID: 2324)
- da02c158-e213-4a39-a4e4-a7a43dfeebaf.exe (PID: 4480)
- d76d02a6-6d7a-49c0-990d-5ff753f5541d.exe (PID: 2980)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- 609cecf0-d857-44ec-9889-96f74d16b573.exe (PID: 3488)
- 07bd4b3a-5579-4792-b414-969915d09db1.exe (PID: 4864)
- 9da61c9d-7522-4bbc-91c5-e6352a108a09.exe (PID: 8184)
- 7sajwPvVrOy42ae83rMif0Bc.exe (PID: 3016)
Changes the autorun value in the registry
- Lukako.exe (PID: 3432)
- DrvInst.exe (PID: 4872)
- svchost.exe (PID: 860)
- e02338bb-99d0-4165-9028-5397664a1740.exe (PID: 2392)
- MyNotes License Agreement.exe (PID: 3704)
Runs injected code in another process
- rundll32.exe (PID: 5072)
- rundll32.exe (PID: 4844)
- rundll32.exe (PID: 5584)
- rundll32.exe (PID: 5804)
Application was injected by another process
- svchost.exe (PID: 860)
Registers / Runs the DLL via REGSVR32.EXE
- H4pRLgO3H8_jrYS9l_JuDbxF.exe (PID: 700)
- BdixTxxgTbhpQWf8TWYqRB4H.exe (PID: 6804)
Loads the Task Scheduler DLL interface
- schtasks.exe (PID: 5496)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 3736)
- schtasks.exe (PID: 4272)
Modifies exclusions in Windows Defender
- reg.exe (PID: 3028)
- reg.exe (PID: 5836)
- reg.exe (PID: 2488)
- reg.exe (PID: 2936)
- reg.exe (PID: 3016)
- reg.exe (PID: 5892)
- reg.exe (PID: 4648)
- reg.exe (PID: 5664)
- reg.exe (PID: 4884)
Modifies files in Chrome extension folder
- GrCDlHD.exe (PID: 3500)
RACCOON was detected
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2024)
- WinRAR.exe (PID: 2196)
- Setup.exe (PID: 2056)
- YolaProduct.exe (PID: 2728)
- lot6B1KTP_pdbqUFCU6MiDGA.exe (PID: 2608)
- tmn7Sjo6IZn07qqz6H1i1Sh2.exe (PID: 2136)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- wLbwZiwylmvvsUg60goenS7x.exe (PID: 2836)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- gy1gLxA3MZWOpa_WnCvGPQNw.exe (PID: 3840)
- bDLtKIkPDGUXlQnTKfLDzjHz.exe (PID: 3876)
- wOBpSuaHg7ptIGHnfMNr6bzY.exe (PID: 772)
- XYxaWZnV6_ZHK4LEdZASMPgy.exe (PID: 3028)
- XEPXrEV4VjKgc6Un0W8KFWRN.exe (PID: 3684)
- 4E57.tmp.exe (PID: 3092)
- 8LAXyC_p8pInUFq3lMbg2W3C.exe (PID: 2972)
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- Lukako.exe (PID: 3432)
- 6396.tmp.exe (PID: 2412)
- cmd.exe (PID: 3092)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- Xuvoqexaete.exe (PID: 3184)
- cmd.exe (PID: 3532)
- 2140854479.exe (PID: 2324)
- L80CiqnbAfAIfcLYGZdxHLAd.exe (PID: 2456)
- AppLaunch.exe (PID: 3064)
- Manocabitae.exe (PID: 3328)
- cmd.exe (PID: 4032)
- 2108352564.exe (PID: 304)
- foldershare.exe (PID: 3948)
- foldershare.tmp (PID: 3680)
- Hk3e5hUMBDXd60gA40t4ttwB.exe (PID: 3700)
- FolderShare.exe (PID: 2328)
- cmd.exe (PID: 2536)
- ICn0axqbZM4uVQnycdocpNd3.exe (PID: 3740)
- Install.exe (PID: 2008)
- Install.exe (PID: 1712)
- RnV3tDYP3fMyu10AW3eGaYqY.exe (PID: 2264)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- cmd.exe (PID: 916)
- 88d6XwLrKd8_Fx1EzRFgSLL2.exe (PID: 4420)
- installer.exe (PID: 4540)
- AppLaunch.exe (PID: 5424)
- RegAsm.exe (PID: 4972)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- powershell.EXE (PID: 3740)
- NHEAMqXBmmtjpWmwLtJi8g2D.exe (PID: 5952)
- IJHqj9FP0VgKogr8WrN6tD6S.exe (PID: 2156)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 448)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- EfrTS2cJrKrF9tU_CWt5DE4q.exe (PID: 4372)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 684)
- cmd.exe (PID: 4720)
- OE41lqQEeScsiOPNwE1i9MNs.exe (PID: 4380)
- H4pRLgO3H8_jrYS9l_JuDbxF.exe (PID: 700)
- d76d02a6-6d7a-49c0-990d-5ff753f5541d.exe (PID: 2980)
- da02c158-e213-4a39-a4e4-a7a43dfeebaf.exe (PID: 4480)
- be134b63-f3ed-48db-90de-f18bf51ecad9.exe (PID: 4324)
- e3393c64-838a-41ac-92ee-42d077e2b298.exe (PID: 3172)
- LzmwAqmV.exe (PID: 4244)
- zjh.exe (PID: 268)
- RobCleanerInstlr3138332.exe (PID: 1436)
- FolderShare.exe (PID: 3284)
- inst1.exe (PID: 5236)
- Proxyupd.exe (PID: 2680)
- zjh.exe (PID: 5772)
- setup.exe (PID: 3628)
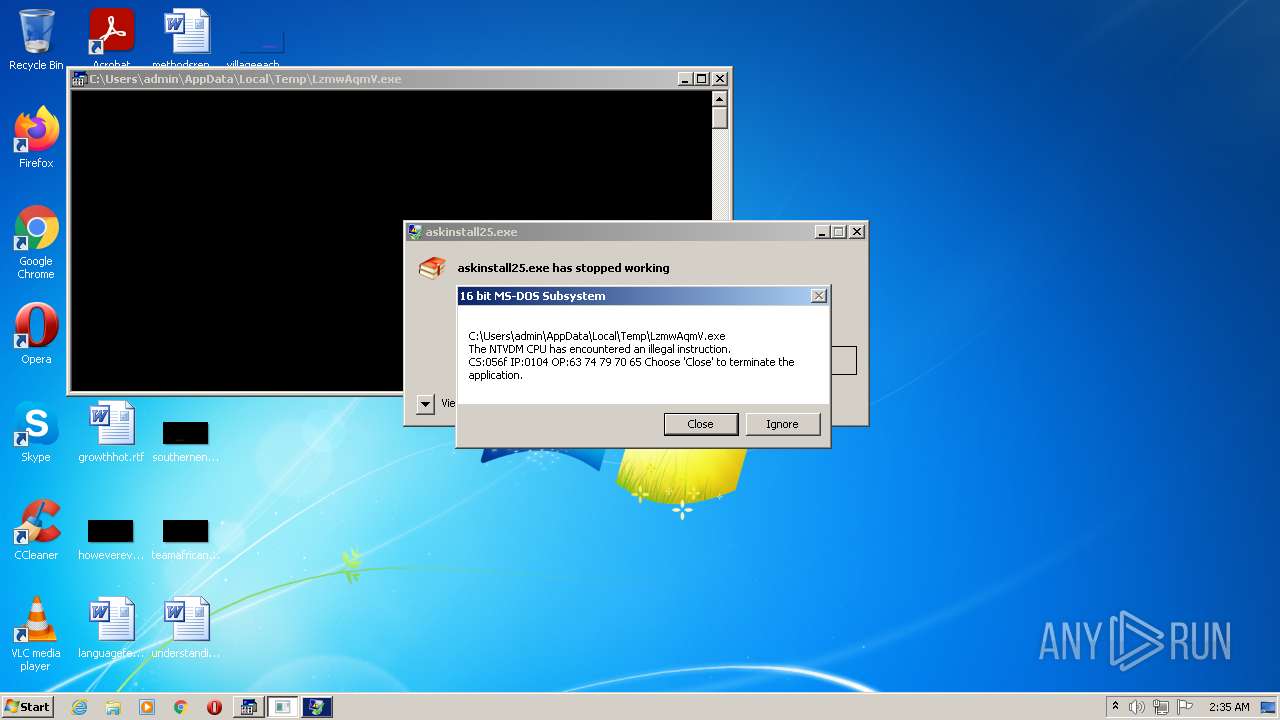
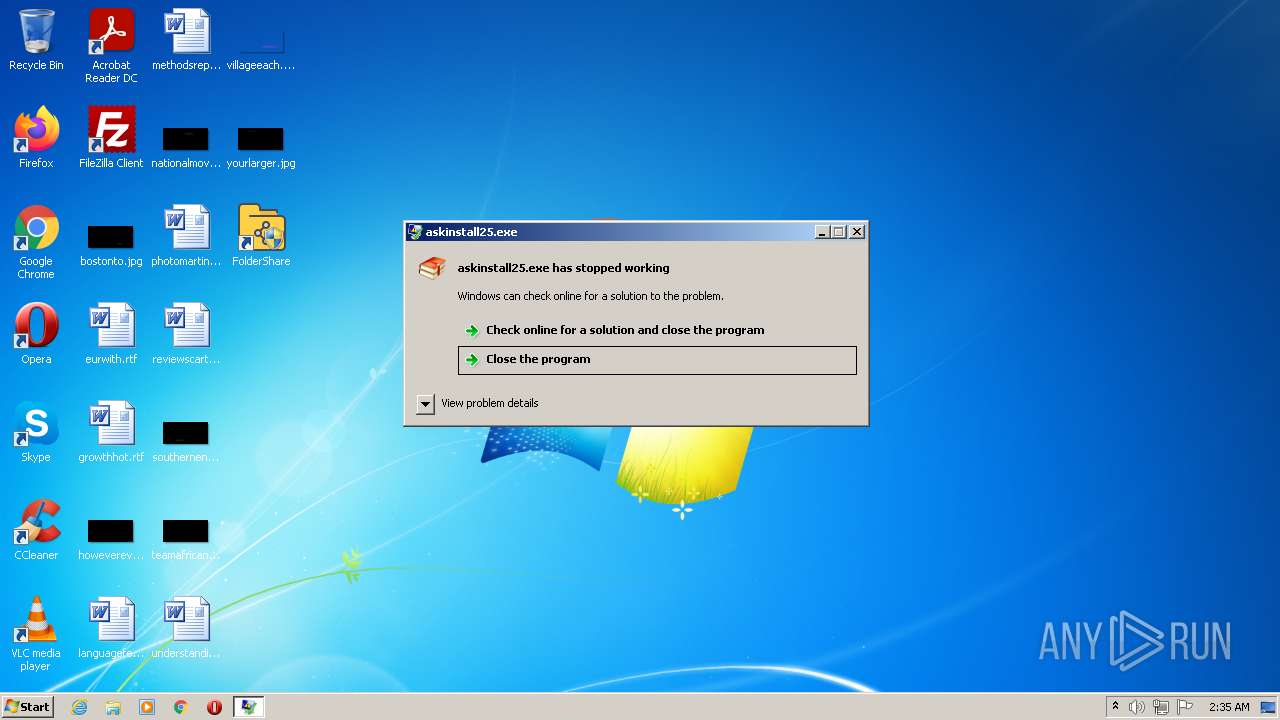
- askinstall25.exe (PID: 3544)
- MyNotes Installation.exe (PID: 3532)
- anytime1.exe (PID: 1284)
- anytime3.exe (PID: 4624)
- anytime2.exe (PID: 4408)
- anytime4.exe (PID: 2168)
- logger.exe (PID: 3360)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- whw.exe (PID: 2508)
- e3dwefw.exe (PID: 4660)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- rBNZVTf.exe (PID: 1944)
- oobeldr.exe (PID: 4144)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- cab39dba-df17-44a9-944a-4e677ad59ba6.exe (PID: 5284)
- powershell.EXE (PID: 1364)
- cmd.exe (PID: 3292)
- 161.exe (PID: 5712)
- 161.tmp (PID: 3640)
- a7b5240e-6154-478d-83bc-4fd17c9ace16.exe (PID: 5048)
- cmd.exe (PID: 424)
- random.exe (PID: 2788)
- random.exe (PID: 4600)
- tapinstall.exe (PID: 5784)
- cmd.exe (PID: 5108)
- cmd.exe (PID: 2416)
- cmd.exe (PID: 5848)
- compan.exe (PID: 5264)
- tapinstall.exe (PID: 4420)
- DrvInst.exe (PID: 2888)
- appforpr3.exe (PID: 5316)
- cmd.exe (PID: 2500)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 4604)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 2756)
- Skype.exe (PID: 932)
- wscript.exe (PID: 2240)
- GrCDlHD.exe (PID: 3500)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 4120)
- BumperWW.exe (PID: 3944)
- cmd.exe (PID: 4864)
- toolspab2.exe (PID: 4764)
- inst2.exe (PID: 2720)
- jg1_1faf.exe (PID: 4928)
- Cube_WW9.exe (PID: 5832)
- toolspab2.exe (PID: 3792)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- DrvInst.exe (PID: 4872)
- 0a9edfa1-4ad7-43cc-ad6e-7ad86348d19b.exe (PID: 3948)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- mask_svc.exe (PID: 2664)
- e476fe3b-0a9e-4566-a7bf-93dc815990e9.exe (PID: 4460)
- mask_svc.exe (PID: 3636)
- mask_svc.exe (PID: 4212)
- 6675827.exe (PID: 5128)
- 8087404.exe (PID: 4892)
- cmd.exe (PID: 4612)
- autosubplayer.exe (PID: 4320)
- cmd.exe (PID: 5040)
- cmd.exe (PID: 1244)
- cmd.exe (PID: 3876)
- toolspab3.exe (PID: 392)
- toolspab3.exe (PID: 856)
- cmd.exe (PID: 2328)
- vZKafuKKBs.exe (PID: 4644)
- nsE209.tmp (PID: 3140)
- nsEBAF.tmp (PID: 4232)
- lighteningplayer-cache-gen.exe (PID: 3924)
- powershell.exe (PID: 3444)
- cmd.exe (PID: 5020)
- askinstall42.exe (PID: 4832)
- cmd.exe (PID: 4568)
- gcleaner.exe (PID: 3572)
- Mmw6nxnPN4KNnjEZRFVLE8nS.exe (PID: 1940)
- cmd.exe (PID: 5980)
- setupWW1.exe (PID: 3416)
- appforpr3.exe (PID: 2368)
- askinstall35.exe (PID: 3708)
- toolspab2.exe (PID: 4892)
- Proxytest.exe (PID: 3452)
- ningli.exe (PID: 2148)
- OneCleanerInst942914.exe (PID: 4152)
- setup.exe (PID: 3772)
- ningli.exe (PID: 5152)
- inst2.exe (PID: 444)
- Cube_WW6.exe (PID: 4780)
- RobCleanerInstlr842628.exe (PID: 5240)
- cmd.exe (PID: 6100)
- toolspab2.exe (PID: 2576)
- cmd.exe (PID: 3008)
- 41c3b0fa-e7c8-4ca1-a053-ac6be3b11ea7.exe (PID: 2396)
- e02338bb-99d0-4165-9028-5397664a1740.exe (PID: 2392)
- y08ZnvqEG9elxfTdvTJ1sNn2.exe (PID: 5780)
- 5kXjAgmXrycB6KYf6f_jxABW.exe (PID: 5940)
- 4408358444083584.exe (PID: 5088)
- mF4cAQIt3HG_K0iyqfbLSUgZ.exe (PID: 1712)
- oVUJDrxMkuXvEIKvf0tAZARQ.exe (PID: 4228)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- XL_Q3_tQ9xsjQZ97ANEODGxC.exe (PID: 2288)
- mMkNQwcrxJo9Fac4EU9aFY3M.exe (PID: 4340)
- 4b6700ea-650a-4f16-8c51-22072b2e29b3.exe (PID: 752)
- rodUdBfXS1K_82Xcij0P21Gl.exe (PID: 3772)
- DiF_p0nJlYu_PaiWDXNFPgds.exe (PID: 2300)
- cnq2OFKbJxjmA8IFszJ1eBv9.exe (PID: 3908)
- m3hNcTJjxaMhPKSDC0pebxfF.exe (PID: 4988)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- jVVYIdHncQbq2ekzrCb1gbHb.exe (PID: 4684)
- mpRCIeopmt9ljZw2RlIFPmAU.exe (PID: 2672)
- mpRCIeopmt9ljZw2RlIFPmAU.tmp (PID: 2124)
- cmd.exe (PID: 396)
- XL_Q3_tQ9xsjQZ97ANEODGxC.exe (PID: 3788)
- SkypeCall.exe (PID: 1908)
- 5gFmVV1_K5KcdEZISt29axtH.exe (PID: 5320)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- cmd.exe (PID: 3632)
- yucyWdqfn4VZ5ppnVCnH9WSx.exe (PID: 4128)
- installer.exe (PID: 4072)
- Lukako.exe (PID: 4544)
- MyNotes License Agreement.exe (PID: 3704)
- 517A.tmp.exe (PID: 6112)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- 5249137.exe (PID: 4268)
- RROhpXCwf_yy4nUf8P_Bumb4.exe (PID: 3604)
- 6C37.tmp.exe (PID: 4788)
- cmd.exe (PID: 1844)
- 6229933.exe (PID: 2488)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- wi3kHVFdALN7gKkOODFO1Bf2.exe (PID: 4412)
- SHesypalori.exe (PID: 784)
- nIwkJ3NyeUqrSBqzgclO8UpJ.exe (PID: 1248)
- 9m65ggis_VvuGcVnAW3jlvtt.exe (PID: 3988)
- h106eivZdLiWNrqhNHKkIk9g.exe (PID: 4544)
- 7sajwPvVrOy42ae83rMif0Bc.exe (PID: 3016)
- GxkzeclbRO6fsAj5eQpALE1r.exe (PID: 5828)
- AppLaunch.exe (PID: 4540)
- Install.exe (PID: 5604)
- Install.exe (PID: 4568)
- 609cecf0-d857-44ec-9889-96f74d16b573.exe (PID: 3488)
- AppLaunch.exe (PID: 3544)
- jNVHMiXAeoDj924YeXfYGCeZ.exe (PID: 4408)
- QNTiCURCOPYLfn5DY1cxPsb_.exe (PID: 3436)
- U02XooqrUpC35QCI7LfEbTvM.exe (PID: 2960)
- 64957901-7123-4944-bef1-eb580816d9f4.exe (PID: 4256)
- 4afb4e54-6c7c-428f-bc9f-b73da43b5986.exe (PID: 1244)
- RegAsm.exe (PID: 2124)
- b1fd6d9d-915b-41bf-89b9-c8f45ae35a0a.exe (PID: 2684)
- MaskVPNUpdate.exe (PID: 2528)
- 16b6b06e-4529-49fb-9238-a4190aaea354.exe (PID: 1516)
- 07bd4b3a-5579-4792-b414-969915d09db1.exe (PID: 4864)
- T5qgYjHO2swRx3odddOWt1iA.exe (PID: 2932)
- sIGlpcOj409XIIXz_MxTPI0f.exe (PID: 6036)
- POp7YcvBq_iBSXjPDUu3jMZq.exe (PID: 4812)
- cmd.exe (PID: 592)
- gXR3LnTkVr_A5Wu2fjqZnIgq.exe (PID: 5328)
- myHaW8yuC5EOhKaB1H_YV_Ta.exe (PID: 4512)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
- J4jxleDPfzWENFGiWtAZ7J0C.exe (PID: 5732)
- nH6w2_8ew6Clk3jfZX215fvF.exe (PID: 932)
- DRQkfbJytDlv8Zi9oYaf_5jk.exe (PID: 6672)
- 1KPXa4tWwVKo4Ujosf8rYhux.exe (PID: 5176)
- s33zVhbrQHP2KNvnWJv3lkX2.exe (PID: 6800)
- cmd.exe (PID: 2444)
- v6rRqy39NiR5vd8orjDd7xOs.exe (PID: 6832)
- gXR3LnTkVr_A5Wu2fjqZnIgq.exe (PID: 7836)
- ETKJsDBjLNKmmA8APYe59Mt1.exe (PID: 8108)
- eP2zoDXXj8JTcj7ImFefr1oj.exe (PID: 6820)
- nec9RrUzAn8eXZdKGatvXuQR.exe (PID: 7024)
- mKNGqUoarnlCnNBAH1Gpxgt5.exe (PID: 4776)
- IxyXV9ZlQNJc2XKhqPPj9ozU.exe (PID: 8124)
- AjtguB8MYJVD6XXYsVsajabZ.exe (PID: 6852)
- s33zVhbrQHP2KNvnWJv3lkX2.exe (PID: 4092)
- aeb1c8a8-22cc-473a-a8a0-97c94c66160a.exe (PID: 6276)
- NPQpbHyrbXKNeDvAuu66TWPf.tmp (PID: 6632)
- NPQpbHyrbXKNeDvAuu66TWPf.exe (PID: 3180)
- VedOY0yQ_rn7KR6Kx7u805ks.exe (PID: 7848)
- cmd.exe (PID: 5756)
- k7IXpemtWNtlL0cPOY9kIl_H.exe (PID: 4192)
- l58AyrpWc_x3uK64FIAv2U0g.exe (PID: 5844)
- F8F5.tmp.exe (PID: 5592)
- BdixTxxgTbhpQWf8TWYqRB4H.exe (PID: 6804)
- 9da61c9d-7522-4bbc-91c5-e6352a108a09.exe (PID: 8184)
- Lukako.exe (PID: 6956)
- f76ae109-bf54-45c6-b7e8-3beb8af8d55c.exe (PID: 7524)
- yLNfk8Wo9h9hCpCbfVNs9hdl.exe (PID: 6024)
- cmd.exe (PID: 5748)
- installer.exe (PID: 5032)
- 92O9eq6j8LZXnGK51uulqmqP.exe (PID: 5820)
- GcUIQmlpOqe0dsslLxJJn9Uh.exe (PID: 6760)
Application launched itself
- WinRAR.exe (PID: 2196)
- msiexec.exe (PID: 5900)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 684)
- zjh.exe (PID: 268)
- random.exe (PID: 2788)
- toolspab2.exe (PID: 4764)
- rundll32.exe (PID: 3468)
- toolspab3.exe (PID: 392)
- ningli.exe (PID: 2148)
- toolspab2.exe (PID: 4892)
- XL_Q3_tQ9xsjQZ97ANEODGxC.exe (PID: 2288)
- s33zVhbrQHP2KNvnWJv3lkX2.exe (PID: 6800)
- gXR3LnTkVr_A5Wu2fjqZnIgq.exe (PID: 5328)
Reads the computer name
- WinRAR.exe (PID: 2196)
- WinRAR.exe (PID: 2024)
- Setup.exe (PID: 2056)
- YolaProduct.exe (PID: 2728)
- lot6B1KTP_pdbqUFCU6MiDGA.exe (PID: 2608)
- wLbwZiwylmvvsUg60goenS7x.exe (PID: 2836)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- wOBpSuaHg7ptIGHnfMNr6bzY.exe (PID: 772)
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- gy1gLxA3MZWOpa_WnCvGPQNw.exe (PID: 3840)
- XYxaWZnV6_ZHK4LEdZASMPgy.exe (PID: 3028)
- XEPXrEV4VjKgc6Un0W8KFWRN.exe (PID: 3684)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- 4E57.tmp.exe (PID: 3092)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- Lukako.exe (PID: 3432)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- Xuvoqexaete.exe (PID: 3184)
- AppLaunch.exe (PID: 3064)
- Manocabitae.exe (PID: 3328)
- foldershare.tmp (PID: 3680)
- ICn0axqbZM4uVQnycdocpNd3.exe (PID: 3740)
- FolderShare.exe (PID: 2328)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- Install.exe (PID: 1712)
- 2140854479.exe (PID: 2324)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- installer.exe (PID: 4540)
- RegAsm.exe (PID: 4972)
- AppLaunch.exe (PID: 5424)
- powershell.EXE (PID: 3740)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 448)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 684)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- EfrTS2cJrKrF9tU_CWt5DE4q.exe (PID: 4372)
- IJHqj9FP0VgKogr8WrN6tD6S.exe (PID: 2156)
- OE41lqQEeScsiOPNwE1i9MNs.exe (PID: 4380)
- H4pRLgO3H8_jrYS9l_JuDbxF.exe (PID: 700)
- d76d02a6-6d7a-49c0-990d-5ff753f5541d.exe (PID: 2980)
- da02c158-e213-4a39-a4e4-a7a43dfeebaf.exe (PID: 4480)
- e3393c64-838a-41ac-92ee-42d077e2b298.exe (PID: 3172)
- be134b63-f3ed-48db-90de-f18bf51ecad9.exe (PID: 4324)
- LzmwAqmV.exe (PID: 4244)
- FolderShare.exe (PID: 3284)
- RobCleanerInstlr3138332.exe (PID: 1436)
- zjh.exe (PID: 268)
- zjh.exe (PID: 5772)
- askinstall25.exe (PID: 3544)
- MyNotes Installation.exe (PID: 3532)
- anytime1.exe (PID: 1284)
- anytime2.exe (PID: 4408)
- anytime3.exe (PID: 4624)
- anytime4.exe (PID: 2168)
- logger.exe (PID: 3360)
- Proxyupd.exe (PID: 2680)
- setup.exe (PID: 3628)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- whw.exe (PID: 2508)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- cab39dba-df17-44a9-944a-4e677ad59ba6.exe (PID: 5284)
- powershell.EXE (PID: 1364)
- 161.tmp (PID: 3640)
- a7b5240e-6154-478d-83bc-4fd17c9ace16.exe (PID: 5048)
- random.exe (PID: 2788)
- random.exe (PID: 4600)
- tapinstall.exe (PID: 5784)
- compan.exe (PID: 5264)
- tapinstall.exe (PID: 4420)
- DrvInst.exe (PID: 2888)
- appforpr3.exe (PID: 5316)
- Skype.exe (PID: 932)
- wscript.exe (PID: 2240)
- GrCDlHD.exe (PID: 3500)
- BumperWW.exe (PID: 3944)
- Cube_WW9.exe (PID: 5832)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- DrvInst.exe (PID: 4872)
- jg1_1faf.exe (PID: 4928)
- 0a9edfa1-4ad7-43cc-ad6e-7ad86348d19b.exe (PID: 3948)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- mask_svc.exe (PID: 2664)
- e476fe3b-0a9e-4566-a7bf-93dc815990e9.exe (PID: 4460)
- mask_svc.exe (PID: 3636)
- 6675827.exe (PID: 5128)
- mask_svc.exe (PID: 4212)
- 8087404.exe (PID: 4892)
- autosubplayer.exe (PID: 4320)
- vZKafuKKBs.exe (PID: 4644)
- powershell.exe (PID: 3444)
- askinstall42.exe (PID: 4832)
- gcleaner.exe (PID: 3572)
- setupWW1.exe (PID: 3416)
- ningli.exe (PID: 2148)
- OneCleanerInst942914.exe (PID: 4152)
- ningli.exe (PID: 5152)
- Cube_WW6.exe (PID: 4780)
- askinstall35.exe (PID: 3708)
- RobCleanerInstlr842628.exe (PID: 5240)
- appforpr3.exe (PID: 2368)
- Proxytest.exe (PID: 3452)
- setup.exe (PID: 3772)
- 41c3b0fa-e7c8-4ca1-a053-ac6be3b11ea7.exe (PID: 2396)
- e02338bb-99d0-4165-9028-5397664a1740.exe (PID: 2392)
- 5kXjAgmXrycB6KYf6f_jxABW.exe (PID: 5940)
- y08ZnvqEG9elxfTdvTJ1sNn2.exe (PID: 5780)
- 4408358444083584.exe (PID: 5088)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- 4b6700ea-650a-4f16-8c51-22072b2e29b3.exe (PID: 752)
- rodUdBfXS1K_82Xcij0P21Gl.exe (PID: 3772)
- oVUJDrxMkuXvEIKvf0tAZARQ.exe (PID: 4228)
- cnq2OFKbJxjmA8IFszJ1eBv9.exe (PID: 3908)
- m3hNcTJjxaMhPKSDC0pebxfF.exe (PID: 4988)
- mMkNQwcrxJo9Fac4EU9aFY3M.exe (PID: 4340)
- mpRCIeopmt9ljZw2RlIFPmAU.tmp (PID: 2124)
- SkypeCall.exe (PID: 1908)
- 5gFmVV1_K5KcdEZISt29axtH.exe (PID: 5320)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- DiF_p0nJlYu_PaiWDXNFPgds.exe (PID: 2300)
- jVVYIdHncQbq2ekzrCb1gbHb.exe (PID: 4684)
- installer.exe (PID: 4072)
- yucyWdqfn4VZ5ppnVCnH9WSx.exe (PID: 4128)
- 517A.tmp.exe (PID: 6112)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- MyNotes License Agreement.exe (PID: 3704)
- Lukako.exe (PID: 4544)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- 5249137.exe (PID: 4268)
- RROhpXCwf_yy4nUf8P_Bumb4.exe (PID: 3604)
- 6229933.exe (PID: 2488)
- wi3kHVFdALN7gKkOODFO1Bf2.exe (PID: 4412)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- h106eivZdLiWNrqhNHKkIk9g.exe (PID: 4544)
- SHesypalori.exe (PID: 784)
- AppLaunch.exe (PID: 4540)
- 7sajwPvVrOy42ae83rMif0Bc.exe (PID: 3016)
- GxkzeclbRO6fsAj5eQpALE1r.exe (PID: 5828)
- AppLaunch.exe (PID: 3544)
- Install.exe (PID: 4568)
- RegAsm.exe (PID: 2124)
- 4afb4e54-6c7c-428f-bc9f-b73da43b5986.exe (PID: 1244)
- 64957901-7123-4944-bef1-eb580816d9f4.exe (PID: 4256)
- 609cecf0-d857-44ec-9889-96f74d16b573.exe (PID: 3488)
- MaskVPNUpdate.exe (PID: 2528)
- 16b6b06e-4529-49fb-9238-a4190aaea354.exe (PID: 1516)
- sIGlpcOj409XIIXz_MxTPI0f.exe (PID: 6036)
- POp7YcvBq_iBSXjPDUu3jMZq.exe (PID: 4812)
- b1fd6d9d-915b-41bf-89b9-c8f45ae35a0a.exe (PID: 2684)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
- 1KPXa4tWwVKo4Ujosf8rYhux.exe (PID: 5176)
- 07bd4b3a-5579-4792-b414-969915d09db1.exe (PID: 4864)
- gXR3LnTkVr_A5Wu2fjqZnIgq.exe (PID: 7836)
- ETKJsDBjLNKmmA8APYe59Mt1.exe (PID: 8108)
- gXR3LnTkVr_A5Wu2fjqZnIgq.exe (PID: 5328)
- nec9RrUzAn8eXZdKGatvXuQR.exe (PID: 7024)
- v6rRqy39NiR5vd8orjDd7xOs.exe (PID: 6832)
- mKNGqUoarnlCnNBAH1Gpxgt5.exe (PID: 4776)
- DRQkfbJytDlv8Zi9oYaf_5jk.exe (PID: 6672)
- aeb1c8a8-22cc-473a-a8a0-97c94c66160a.exe (PID: 6276)
- AjtguB8MYJVD6XXYsVsajabZ.exe (PID: 6852)
- T5qgYjHO2swRx3odddOWt1iA.exe (PID: 2932)
- NPQpbHyrbXKNeDvAuu66TWPf.tmp (PID: 6632)
- nH6w2_8ew6Clk3jfZX215fvF.exe (PID: 932)
- VedOY0yQ_rn7KR6Kx7u805ks.exe (PID: 7848)
- k7IXpemtWNtlL0cPOY9kIl_H.exe (PID: 4192)
- l58AyrpWc_x3uK64FIAv2U0g.exe (PID: 5844)
- eP2zoDXXj8JTcj7ImFefr1oj.exe (PID: 6820)
- BdixTxxgTbhpQWf8TWYqRB4H.exe (PID: 6804)
- 9da61c9d-7522-4bbc-91c5-e6352a108a09.exe (PID: 8184)
- IxyXV9ZlQNJc2XKhqPPj9ozU.exe (PID: 8124)
- Lukako.exe (PID: 6956)
- F8F5.tmp.exe (PID: 5592)
- yLNfk8Wo9h9hCpCbfVNs9hdl.exe (PID: 6024)
- f76ae109-bf54-45c6-b7e8-3beb8af8d55c.exe (PID: 7524)
- installer.exe (PID: 5032)
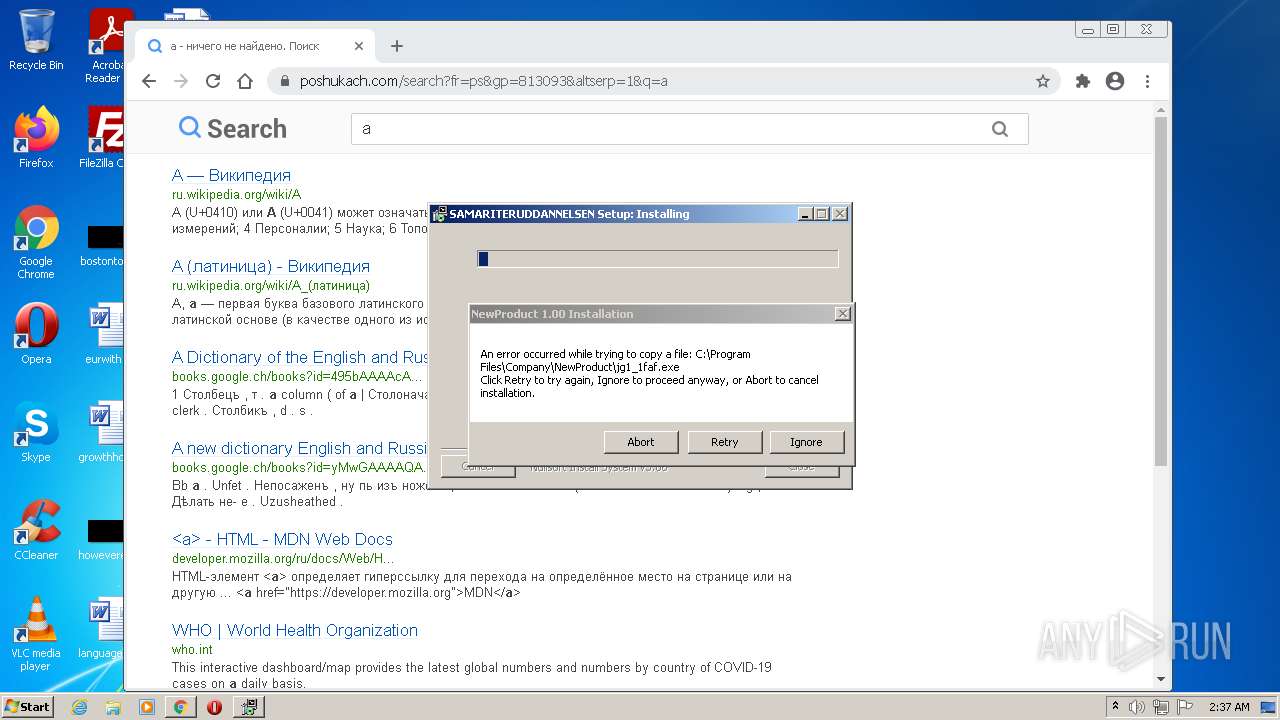
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2024)
- Setup.exe (PID: 2056)
- YolaProduct.exe (PID: 2728)
- wLbwZiwylmvvsUg60goenS7x.exe (PID: 2836)
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- Lukako.exe (PID: 3432)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 448)
- XEPXrEV4VjKgc6Un0W8KFWRN.exe (PID: 3684)
- XYxaWZnV6_ZHK4LEdZASMPgy.exe (PID: 3028)
- AppLaunch.exe (PID: 3064)
- EfrTS2cJrKrF9tU_CWt5DE4q.exe (PID: 4372)
- RegAsm.exe (PID: 4972)
- zjh.exe (PID: 5772)
- Manocabitae.exe (PID: 3328)
- compan.exe (PID: 5264)
- RobCleanerInstlr3138332.exe (PID: 1436)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- Cube_WW9.exe (PID: 5832)
- RobCleanerInstlr842628.exe (PID: 5240)
- cnq2OFKbJxjmA8IFszJ1eBv9.exe (PID: 3908)
- Cube_WW6.exe (PID: 4780)
- m3hNcTJjxaMhPKSDC0pebxfF.exe (PID: 4988)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- SHesypalori.exe (PID: 784)
- ETKJsDBjLNKmmA8APYe59Mt1.exe (PID: 8108)
- AjtguB8MYJVD6XXYsVsajabZ.exe (PID: 6852)
- GcUIQmlpOqe0dsslLxJJn9Uh.exe (PID: 6760)
- AppLaunch.exe (PID: 3544)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2024)
- Setup.exe (PID: 2056)
- YolaProduct.exe (PID: 2728)
- tmn7Sjo6IZn07qqz6H1i1Sh2.exe (PID: 2136)
- wLbwZiwylmvvsUg60goenS7x.exe (PID: 2836)
- lot6B1KTP_pdbqUFCU6MiDGA.exe (PID: 2608)
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- 8LAXyC_p8pInUFq3lMbg2W3C.exe (PID: 2972)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- gy1gLxA3MZWOpa_WnCvGPQNw.exe (PID: 3840)
- 6396.tmp.exe (PID: 2412)
- Lukako.exe (PID: 3432)
- foldershare.exe (PID: 3948)
- foldershare.tmp (PID: 3680)
- Hk3e5hUMBDXd60gA40t4ttwB.exe (PID: 3700)
- Install.exe (PID: 2008)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- Manocabitae.exe (PID: 3328)
- installer.exe (PID: 4540)
- 2140854479.exe (PID: 2324)
- msiexec.exe (PID: 5900)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 448)
- XEPXrEV4VjKgc6Un0W8KFWRN.exe (PID: 3684)
- XYxaWZnV6_ZHK4LEdZASMPgy.exe (PID: 3028)
- AppLaunch.exe (PID: 3064)
- Install.exe (PID: 1712)
- AppLaunch.exe (PID: 5424)
- EfrTS2cJrKrF9tU_CWt5DE4q.exe (PID: 4372)
- RegAsm.exe (PID: 4972)
- zjh.exe (PID: 5772)
- 161.exe (PID: 5712)
- 161.tmp (PID: 3640)
- tapinstall.exe (PID: 4420)
- DrvInst.exe (PID: 2888)
- compan.exe (PID: 5264)
- rBNZVTf.exe (PID: 1944)
- RobCleanerInstlr3138332.exe (PID: 1436)
- GrCDlHD.exe (PID: 3500)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- cab39dba-df17-44a9-944a-4e677ad59ba6.exe (PID: 5284)
- a7b5240e-6154-478d-83bc-4fd17c9ace16.exe (PID: 5048)
- Cube_WW9.exe (PID: 5832)
- e476fe3b-0a9e-4566-a7bf-93dc815990e9.exe (PID: 4460)
- Cube_WW6.exe (PID: 4780)
- RobCleanerInstlr842628.exe (PID: 5240)
- cnq2OFKbJxjmA8IFszJ1eBv9.exe (PID: 3908)
- m3hNcTJjxaMhPKSDC0pebxfF.exe (PID: 4988)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- SHesypalori.exe (PID: 784)
- MyNotes License Agreement.exe (PID: 3704)
- AppLaunch.exe (PID: 4540)
- Install.exe (PID: 4568)
- ETKJsDBjLNKmmA8APYe59Mt1.exe (PID: 8108)
- AjtguB8MYJVD6XXYsVsajabZ.exe (PID: 6852)
- installer.exe (PID: 4072)
- GcUIQmlpOqe0dsslLxJJn9Uh.exe (PID: 6760)
- 16b6b06e-4529-49fb-9238-a4190aaea354.exe (PID: 1516)
- AppLaunch.exe (PID: 3544)
- 7sajwPvVrOy42ae83rMif0Bc.exe (PID: 3016)
Checks for external IP
- YolaProduct.exe (PID: 2728)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- Cube_WW9.exe (PID: 5832)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- Cube_WW6.exe (PID: 4780)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
Adds / modifies Windows certificates
- YolaProduct.exe (PID: 2728)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
Drops a file that was compiled in debug mode
- YolaProduct.exe (PID: 2728)
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- 6396.tmp.exe (PID: 2412)
- Lukako.exe (PID: 3432)
- foldershare.tmp (PID: 3680)
- Manocabitae.exe (PID: 3328)
- 2140854479.exe (PID: 2324)
- installer.exe (PID: 4540)
- msiexec.exe (PID: 5900)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- 161.tmp (PID: 3640)
- tapinstall.exe (PID: 4420)
- DrvInst.exe (PID: 2888)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- cab39dba-df17-44a9-944a-4e677ad59ba6.exe (PID: 5284)
- a7b5240e-6154-478d-83bc-4fd17c9ace16.exe (PID: 5048)
- Cube_WW9.exe (PID: 5832)
- e476fe3b-0a9e-4566-a7bf-93dc815990e9.exe (PID: 4460)
- Cube_WW6.exe (PID: 4780)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- SHesypalori.exe (PID: 784)
- MyNotes License Agreement.exe (PID: 3704)
- 16b6b06e-4529-49fb-9238-a4190aaea354.exe (PID: 1516)
- installer.exe (PID: 4072)
- GcUIQmlpOqe0dsslLxJJn9Uh.exe (PID: 6760)
- 7sajwPvVrOy42ae83rMif0Bc.exe (PID: 3016)
Drops a file with too old compile date
- gy1gLxA3MZWOpa_WnCvGPQNw.exe (PID: 3840)
- YolaProduct.exe (PID: 2728)
- 8LAXyC_p8pInUFq3lMbg2W3C.exe (PID: 2972)
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- Lukako.exe (PID: 3432)
- foldershare.exe (PID: 3948)
- foldershare.tmp (PID: 3680)
- AppLaunch.exe (PID: 5424)
- 161.tmp (PID: 3640)
- Manocabitae.exe (PID: 3328)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- Cube_WW9.exe (PID: 5832)
- Cube_WW6.exe (PID: 4780)
- AppLaunch.exe (PID: 4540)
Creates files in the user directory
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- 6396.tmp.exe (PID: 2412)
- installer.exe (PID: 4540)
- powershell.EXE (PID: 3740)
- RegAsm.exe (PID: 4972)
- e3dwefw.exe (PID: 4660)
- powershell.EXE (PID: 1364)
- compan.exe (PID: 5264)
- GrCDlHD.exe (PID: 3500)
- cab39dba-df17-44a9-944a-4e677ad59ba6.exe (PID: 5284)
- a7b5240e-6154-478d-83bc-4fd17c9ace16.exe (PID: 5048)
- autosubplayer.exe (PID: 4320)
- e02338bb-99d0-4165-9028-5397664a1740.exe (PID: 2392)
- rodUdBfXS1K_82Xcij0P21Gl.exe (PID: 3772)
- installer.exe (PID: 4072)
- e476fe3b-0a9e-4566-a7bf-93dc815990e9.exe (PID: 4460)
- MyNotes License Agreement.exe (PID: 3704)
- 4b6700ea-650a-4f16-8c51-22072b2e29b3.exe (PID: 752)
- 6C37.tmp.exe (PID: 4788)
- 1KPXa4tWwVKo4Ujosf8rYhux.exe (PID: 5176)
Dropped object may contain URLs of mainers pools
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
Reads Environment values
- 4E57.tmp.exe (PID: 3092)
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- Lukako.exe (PID: 3432)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- Xuvoqexaete.exe (PID: 3184)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- Manocabitae.exe (PID: 3328)
- AppLaunch.exe (PID: 3064)
- installer.exe (PID: 4540)
- RegAsm.exe (PID: 4972)
- MsiExec.exe (PID: 5692)
- MsiExec.exe (PID: 2940)
- 2140854479.exe (PID: 2324)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- EfrTS2cJrKrF9tU_CWt5DE4q.exe (PID: 4372)
- AppLaunch.exe (PID: 5424)
- XEPXrEV4VjKgc6Un0W8KFWRN.exe (PID: 3684)
- XYxaWZnV6_ZHK4LEdZASMPgy.exe (PID: 3028)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- anytime2.exe (PID: 4408)
- anytime3.exe (PID: 4624)
- anytime1.exe (PID: 1284)
- anytime4.exe (PID: 2168)
- logger.exe (PID: 3360)
- Proxyupd.exe (PID: 2680)
- whw.exe (PID: 2508)
- vssvc.exe (PID: 3188)
- da02c158-e213-4a39-a4e4-a7a43dfeebaf.exe (PID: 4480)
- d76d02a6-6d7a-49c0-990d-5ff753f5541d.exe (PID: 2980)
- RobCleanerInstlr3138332.exe (PID: 1436)
- DrvInst.exe (PID: 4872)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- cab39dba-df17-44a9-944a-4e677ad59ba6.exe (PID: 5284)
- a7b5240e-6154-478d-83bc-4fd17c9ace16.exe (PID: 5048)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- Skype.exe (PID: 932)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- 161.tmp (PID: 3640)
- OneCleanerInst942914.exe (PID: 4152)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- 41c3b0fa-e7c8-4ca1-a053-ac6be3b11ea7.exe (PID: 2396)
- e476fe3b-0a9e-4566-a7bf-93dc815990e9.exe (PID: 4460)
- Proxytest.exe (PID: 3452)
- 4b6700ea-650a-4f16-8c51-22072b2e29b3.exe (PID: 752)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- installer.exe (PID: 4072)
- 517A.tmp.exe (PID: 6112)
- Lukako.exe (PID: 4544)
- SkypeCall.exe (PID: 1908)
- DiF_p0nJlYu_PaiWDXNFPgds.exe (PID: 2300)
- oVUJDrxMkuXvEIKvf0tAZARQ.exe (PID: 4228)
- MsiExec.exe (PID: 5672)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- SHesypalori.exe (PID: 784)
- RobCleanerInstlr842628.exe (PID: 5240)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- AppLaunch.exe (PID: 4540)
- cnq2OFKbJxjmA8IFszJ1eBv9.exe (PID: 3908)
- RegAsm.exe (PID: 2124)
- m3hNcTJjxaMhPKSDC0pebxfF.exe (PID: 4988)
- GxkzeclbRO6fsAj5eQpALE1r.exe (PID: 5828)
- nec9RrUzAn8eXZdKGatvXuQR.exe (PID: 7024)
- v6rRqy39NiR5vd8orjDd7xOs.exe (PID: 6832)
- MsiExec.exe (PID: 7804)
- F8F5.tmp.exe (PID: 5592)
- Lukako.exe (PID: 6956)
Reads the Windows organization settings
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- foldershare.tmp (PID: 3680)
- installer.exe (PID: 4540)
- msiexec.exe (PID: 5900)
- 161.tmp (PID: 3640)
- mpRCIeopmt9ljZw2RlIFPmAU.tmp (PID: 2124)
- installer.exe (PID: 4072)
- NPQpbHyrbXKNeDvAuu66TWPf.tmp (PID: 6632)
Reads Windows owner or organization settings
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- foldershare.tmp (PID: 3680)
- installer.exe (PID: 4540)
- msiexec.exe (PID: 5900)
- 161.tmp (PID: 3640)
- mpRCIeopmt9ljZw2RlIFPmAU.tmp (PID: 2124)
- installer.exe (PID: 4072)
- NPQpbHyrbXKNeDvAuu66TWPf.tmp (PID: 6632)
Creates files in the program directory
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- 2140854479.exe (PID: 2324)
- msiexec.exe (PID: 5900)
- WerFault.exe (PID: 1300)
- WerFault.exe (PID: 3956)
- svchost.exe (PID: 860)
- BumperWW.exe (PID: 3944)
- GrCDlHD.exe (PID: 3500)
- jg1_1faf.exe (PID: 4928)
- autosubplayer.exe (PID: 4320)
- lighteningplayer-cache-gen.exe (PID: 3924)
- setupWW1.exe (PID: 3416)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- RROhpXCwf_yy4nUf8P_Bumb4.exe (PID: 3604)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
Creates a directory in Program Files
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- Lukako.exe (PID: 3432)
- foldershare.tmp (PID: 3680)
- msiexec.exe (PID: 5900)
- 161.tmp (PID: 3640)
- BumperWW.exe (PID: 3944)
- GrCDlHD.exe (PID: 3500)
- autosubplayer.exe (PID: 4320)
Reads the cookies of Google Chrome
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- AppLaunch.exe (PID: 3064)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- RegAsm.exe (PID: 4972)
- AppLaunch.exe (PID: 5424)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- Proxyupd.exe (PID: 2680)
- whw.exe (PID: 2508)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- Skype.exe (PID: 932)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- SkypeCall.exe (PID: 1908)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- AppLaunch.exe (PID: 4540)
- Proxytest.exe (PID: 3452)
Reads the cookies of Mozilla Firefox
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- AppLaunch.exe (PID: 3064)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- RegAsm.exe (PID: 4972)
- AppLaunch.exe (PID: 5424)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- Proxyupd.exe (PID: 2680)
- whw.exe (PID: 2508)
- jg1_1faf.exe (PID: 4928)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- Skype.exe (PID: 932)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- SkypeCall.exe (PID: 1908)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- AppLaunch.exe (PID: 4540)
- Proxytest.exe (PID: 3452)
Searches for installed software
- aEqWjH1oGgfNkqojh_nVIQfl.exe (PID: 3188)
- sMh7UqxEUEGN5MPje_NImF30.exe (PID: 2484)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- jmWVfqr6bshxnaq8NMYRzSC_.exe (PID: 3248)
- AppLaunch.exe (PID: 3064)
- 2140854479.exe (PID: 2324)
- RegAsm.exe (PID: 4972)
- AppLaunch.exe (PID: 5424)
- wdDgvounchQLFKVrWPAzIHDl.exe (PID: 3656)
- 3S1kq7WeVJHTw3O_jkLiMAm5.exe (PID: 3496)
- whw.exe (PID: 2508)
- Proxyupd.exe (PID: 2680)
- da02c158-e213-4a39-a4e4-a7a43dfeebaf.exe (PID: 4480)
- d76d02a6-6d7a-49c0-990d-5ff753f5541d.exe (PID: 2980)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- Skype.exe (PID: 932)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- Proxytest.exe (PID: 3452)
- 41c3b0fa-e7c8-4ca1-a053-ac6be3b11ea7.exe (PID: 2396)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- amfm09EWQD0W4SGzifUVRa9r.exe (PID: 2588)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- SkypeCall.exe (PID: 1908)
- FpVd_Ml69qW1QNUAECxFHHB_.exe (PID: 5308)
- AppLaunch.exe (PID: 4540)
Starts CMD.EXE for commands execution
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- gy1gLxA3MZWOpa_WnCvGPQNw.exe (PID: 3840)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- forfiles.exe (PID: 3784)
- forfiles.exe (PID: 2408)
- Manocabitae.exe (PID: 3328)
- 2140854479.exe (PID: 2324)
- 161.tmp (PID: 3640)
- appforpr3.exe (PID: 5316)
- rBNZVTf.exe (PID: 1944)
- GrCDlHD.exe (PID: 3500)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- appforpr3.exe (PID: 2368)
- mMkNQwcrxJo9Fac4EU9aFY3M.exe (PID: 4340)
- rodUdBfXS1K_82Xcij0P21Gl.exe (PID: 3772)
- forfiles.exe (PID: 4544)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- compan.exe (PID: 5264)
- forfiles.exe (PID: 2352)
- nH6w2_8ew6Clk3jfZX215fvF.exe (PID: 932)
- SHesypalori.exe (PID: 784)
Starts CMD.EXE for self-deleting
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- 2140854479.exe (PID: 2324)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- rodUdBfXS1K_82Xcij0P21Gl.exe (PID: 3772)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- compan.exe (PID: 5264)
Creates files in the Windows directory
- svchost.exe (PID: 860)
- schtasks.exe (PID: 5496)
- DrvInst.exe (PID: 2888)
- cmd.exe (PID: 2756)
- rBNZVTf.exe (PID: 1944)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 3736)
- DrvInst.exe (PID: 4872)
- GrCDlHD.exe (PID: 3500)
- schtasks.exe (PID: 4272)
Reads CPU info
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- RegAsm.exe (PID: 4972)
- 2140854479.exe (PID: 2324)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- RegAsm.exe (PID: 2124)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1656)
- iexplore.exe (PID: 4436)
Starts Internet Explorer
- Xuvoqexaete.exe (PID: 3184)
- compan.exe (PID: 5264)
Reads mouse settings
- 2108352564.exe (PID: 304)
- compan.exe (PID: 5264)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2536)
- MsiExec.exe (PID: 5692)
- cmd.exe (PID: 4720)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 4864)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 396)
- cmd.exe (PID: 592)
- cmd.exe (PID: 5756)
- MsiExec.exe (PID: 7804)
Starts itself from another location
- Hk3e5hUMBDXd60gA40t4ttwB.exe (PID: 3700)
- e02338bb-99d0-4165-9028-5397664a1740.exe (PID: 2392)
- nIwkJ3NyeUqrSBqzgclO8UpJ.exe (PID: 1248)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 1764)
- cmd.exe (PID: 2652)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 4604)
- wscript.exe (PID: 2240)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 5040)
- cmd.exe (PID: 1244)
- cmd.exe (PID: 2828)
- cmd.exe (PID: 7056)
Executed as Windows Service
- msiexec.exe (PID: 5900)
- vssvc.exe (PID: 3188)
- mask_svc.exe (PID: 4212)
Starts Microsoft Installer
- installer.exe (PID: 4540)
- installer.exe (PID: 4072)
PowerShell script executed
- powershell.EXE (PID: 3740)
- powershell.EXE (PID: 1364)
- powershell.EXE (PID: 1564)
Executed via Task Scheduler
- powershell.EXE (PID: 3740)
- oobeldr.exe (PID: 4144)
- rBNZVTf.exe (PID: 1944)
- powershell.EXE (PID: 1364)
- GrCDlHD.exe (PID: 3500)
- rundll32.EXE (PID: 2604)
- chrome.exe (PID: 2216)
- powershell.EXE (PID: 1564)
Reads the date of Windows installation
- powershell.EXE (PID: 3740)
- powershell.EXE (PID: 1364)
Creates a software uninstall entry
- msiexec.exe (PID: 5900)
- BumperWW.exe (PID: 3944)
- GrCDlHD.exe (PID: 3500)
- autosubplayer.exe (PID: 4320)
- setupWW1.exe (PID: 3416)
- MyNotes License Agreement.exe (PID: 3704)
Executed via WMI
- rundll32.exe (PID: 5072)
- rundll32.exe (PID: 4844)
- rundll32.exe (PID: 5584)
- rundll32.exe (PID: 5804)
Removes files from Windows directory
- svchost.exe (PID: 860)
- DrvInst.exe (PID: 2888)
- rBNZVTf.exe (PID: 1944)
- DrvInst.exe (PID: 4872)
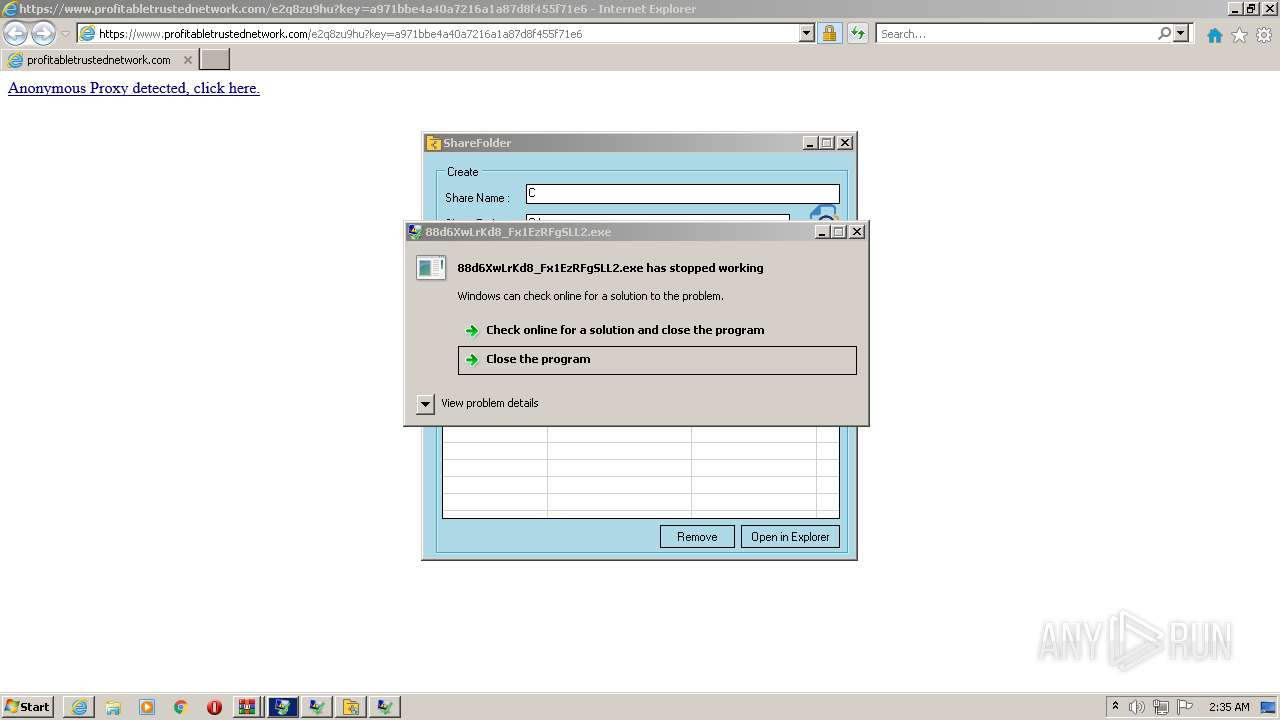
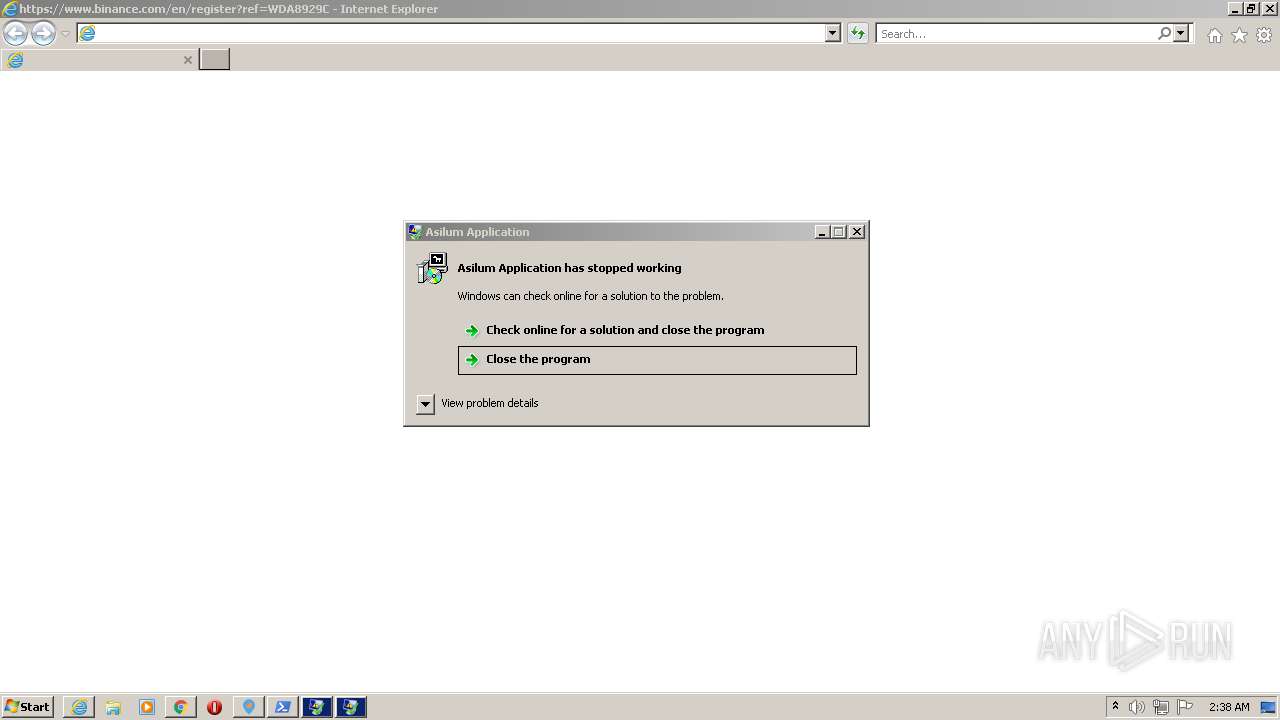
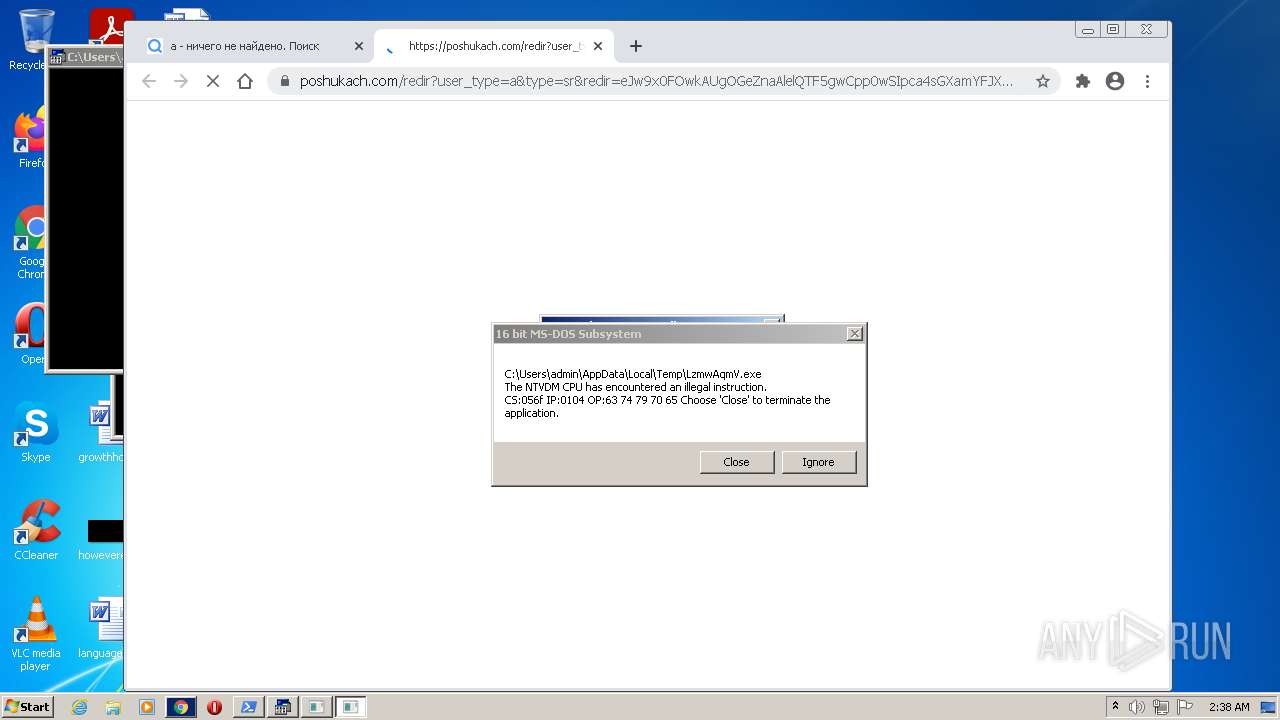
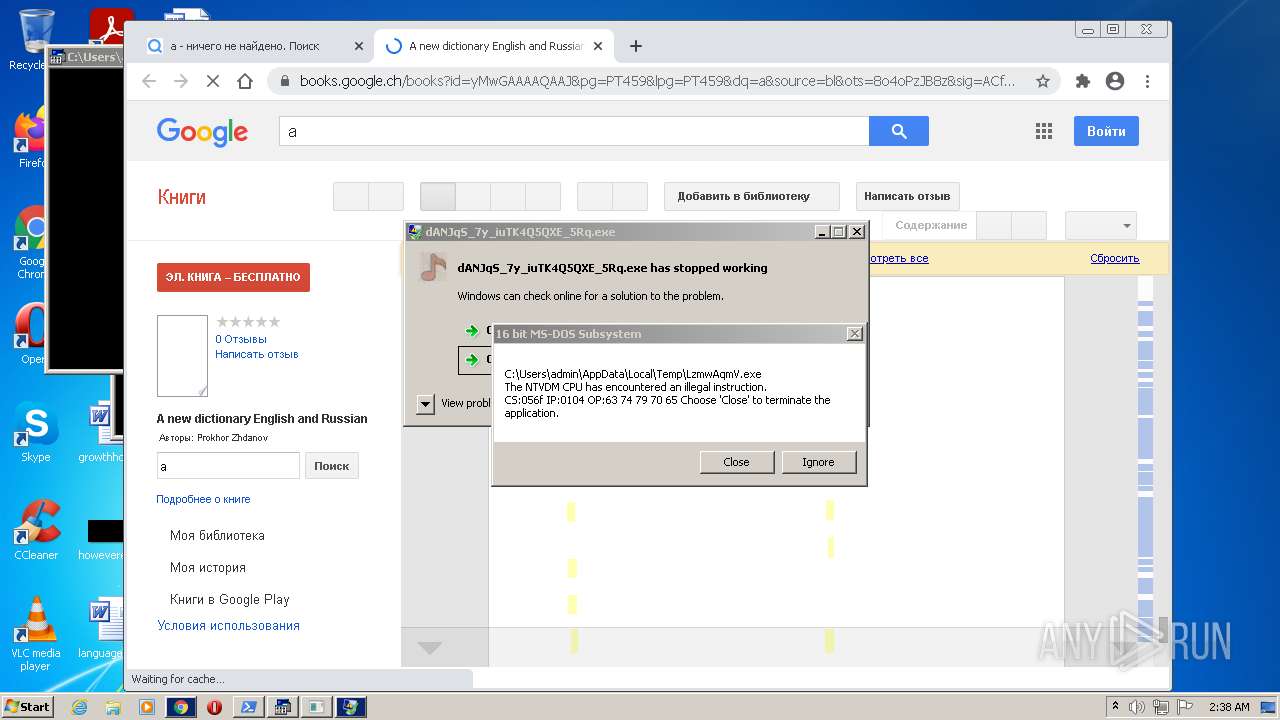
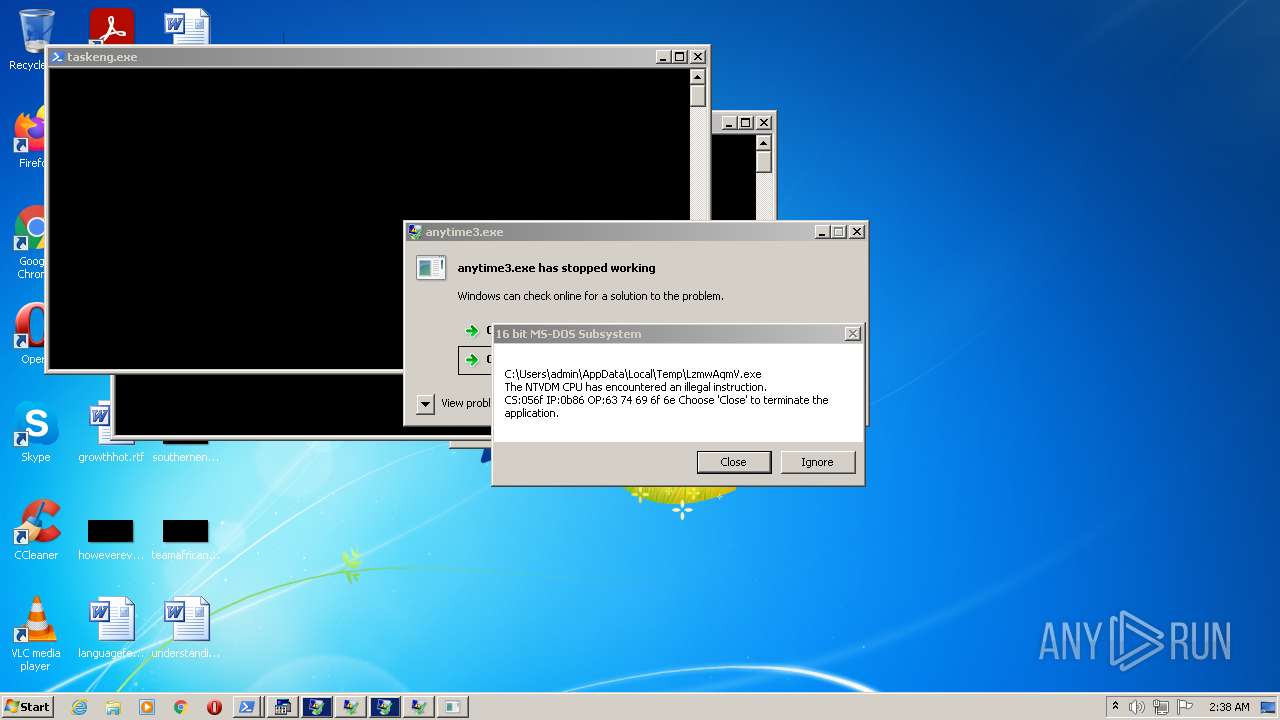
Executes application which crashes
- anytime1.exe (PID: 1284)
Creates files in the driver directory
- DrvInst.exe (PID: 2888)
- DrvInst.exe (PID: 4872)
Executed via COM
- DrvInst.exe (PID: 2888)
- DrvInst.exe (PID: 4872)
Executes scripts
- rBNZVTf.exe (PID: 1944)
Modifies files in Chrome extension folder
- chrome.exe (PID: 5584)
- chrome.exe (PID: 3812)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 5576)
- rundll32.exe (PID: 3468)
- control.exe (PID: 5028)
- control.exe (PID: 2052)
- control.exe (PID: 4936)
- control.exe (PID: 4856)
- control.exe (PID: 7344)
Reads default file associations for system extensions
- 8087404.exe (PID: 4892)
- 6675827.exe (PID: 5128)
- yucyWdqfn4VZ5ppnVCnH9WSx.exe (PID: 4128)
- 5249137.exe (PID: 4268)
- 6229933.exe (PID: 2488)
- k7IXpemtWNtlL0cPOY9kIl_H.exe (PID: 4192)
Starts application with an unusual extension
- autosubplayer.exe (PID: 4320)
Executes PowerShell scripts
- nsE209.tmp (PID: 3140)
INFO
Checks supported languages
- NOTEPAD.EXE (PID: 2480)
- WerFault.exe (PID: 3956)
- WerFault.exe (PID: 1300)
- PING.EXE (PID: 1408)
- schtasks.exe (PID: 3708)
- schtasks.exe (PID: 2508)
- svchost.exe (PID: 860)
- iexplore.exe (PID: 2484)
- iexplore.exe (PID: 1656)
- taskkill.exe (PID: 1132)
- forfiles.exe (PID: 2408)
- forfiles.exe (PID: 3784)
- cmd.exe (PID: 1764)
- reg.exe (PID: 2444)
- cmd.exe (PID: 2652)
- reg.exe (PID: 3696)
- timeout.exe (PID: 2764)
- msiexec.exe (PID: 5900)
- MsiExec.exe (PID: 2940)
- msiexec.exe (PID: 4432)
- schtasks.exe (PID: 4720)
- schtasks.exe (PID: 5124)
- MsiExec.exe (PID: 5692)
- taskkill.exe (PID: 6112)
- MsiExec.exe (PID: 3444)
- taskkill.exe (PID: 5620)
- timeout.exe (PID: 2928)
- gpupdate.exe (PID: 4796)
- rundll32.exe (PID: 5072)
- regsvr32.exe (PID: 4844)
- schtasks.exe (PID: 3688)
- schtasks.exe (PID: 5496)
- schtasks.exe (PID: 4748)
- ntvdm.exe (PID: 3176)
- rundll32.exe (PID: 4844)
- schtasks.exe (PID: 2164)
- schtasks.exe (PID: 5072)
- schtasks.exe (PID: 3132)
- gpupdate.exe (PID: 508)
- vssvc.exe (PID: 3188)
- taskkill.exe (PID: 1764)
- schtasks.exe (PID: 2100)
- reg.exe (PID: 2928)
- reg.exe (PID: 3028)
- reg.exe (PID: 5836)
- reg.exe (PID: 2488)
- reg.exe (PID: 3016)
- reg.exe (PID: 2936)
- reg.exe (PID: 4648)
- reg.exe (PID: 5892)
- reg.exe (PID: 4884)
- reg.exe (PID: 5664)
- reg.exe (PID: 1524)
- reg.exe (PID: 5036)
- reg.exe (PID: 3948)
- reg.exe (PID: 2964)
- reg.exe (PID: 2608)
- reg.exe (PID: 2688)
- reg.exe (PID: 4516)
- schtasks.exe (PID: 3224)
- reg.exe (PID: 3620)
- schtasks.exe (PID: 4976)
- chrome.exe (PID: 2872)
- chrome.exe (PID: 5884)
- schtasks.exe (PID: 2360)
- reg.exe (PID: 4776)
- chrome.exe (PID: 4860)
- reg.exe (PID: 5388)
- rundll32.exe (PID: 5584)
- chrome.exe (PID: 5020)
- schtasks.exe (PID: 3736)
- taskkill.exe (PID: 5396)
- schtasks.exe (PID: 5796)
- chrome.exe (PID: 276)
- schtasks.exe (PID: 5040)
- chrome.exe (PID: 5584)
- schtasks.exe (PID: 5252)
- chrome.exe (PID: 5596)
- chrome.exe (PID: 296)
- chrome.exe (PID: 2320)
- chrome.exe (PID: 5476)
- chrome.exe (PID: 4236)
- chrome.exe (PID: 5176)
- chrome.exe (PID: 1376)
- chrome.exe (PID: 4820)
- schtasks.exe (PID: 4784)
- schtasks.exe (PID: 4496)
- schtasks.exe (PID: 1972)
- schtasks.exe (PID: 2460)
- rundll32.EXE (PID: 2604)
- schtasks.exe (PID: 4272)
- schtasks.exe (PID: 4496)
- schtasks.exe (PID: 6004)
- schtasks.exe (PID: 5912)
- chrome.exe (PID: 2216)
- chrome.exe (PID: 2692)
- schtasks.exe (PID: 3604)
- chrome.exe (PID: 3172)
- chrome.exe (PID: 2896)
- chrome.exe (PID: 2404)
- chrome.exe (PID: 4764)
- chrome.exe (PID: 5148)
- chrome.exe (PID: 2908)
- chrome.exe (PID: 5236)
- chrome.exe (PID: 5992)
- reg.exe (PID: 2324)
- schtasks.exe (PID: 3316)
- schtasks.exe (PID: 2360)
- reg.exe (PID: 5980)
- control.exe (PID: 5576)
- rundll32.exe (PID: 3468)
- rundll32.exe (PID: 2656)
- rundll32.exe (PID: 4780)
- control.exe (PID: 5028)
- timeout.exe (PID: 5596)
- chrome.exe (PID: 3812)
- chrome.exe (PID: 3912)
- chrome.exe (PID: 4812)
- chrome.exe (PID: 4188)
- chrome.exe (PID: 1408)
- chrome.exe (PID: 6136)
- chrome.exe (PID: 2476)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 5668)
- chrome.exe (PID: 4588)
- chrome.exe (PID: 4120)
- taskkill.exe (PID: 5584)
- chrome.exe (PID: 4676)
- chrome.exe (PID: 3432)
- chrome.exe (PID: 5756)
- chrome.exe (PID: 4416)
- rundll32.exe (PID: 5804)
- taskkill.exe (PID: 3520)
- MsiExec.exe (PID: 5672)
- chrome.exe (PID: 2544)
- rundll32.exe (PID: 5772)
- chrome.exe (PID: 4104)
- control.exe (PID: 2052)
- control.exe (PID: 4936)
- PING.EXE (PID: 1324)
- chrome.exe (PID: 4388)
- rundll32.exe (PID: 568)
- schtasks.exe (PID: 5948)
- schtasks.exe (PID: 2064)
- control.exe (PID: 4856)
- chrome.exe (PID: 5996)
- chrome.exe (PID: 2688)
- rundll32.exe (PID: 2244)
- chrome.exe (PID: 2212)
- chrome.exe (PID: 2420)
- iexplore.exe (PID: 5336)
- msiexec.exe (PID: 2628)
- cmd.exe (PID: 2828)
- iexplore.exe (PID: 4436)
- reg.exe (PID: 5320)
- taskkill.exe (PID: 4300)
- cmd.exe (PID: 7056)
- reg.exe (PID: 7156)
- forfiles.exe (PID: 2352)
- chrome.exe (PID: 7168)
- PING.EXE (PID: 7484)
- schtasks.exe (PID: 6688)
- chrome.exe (PID: 7400)
- MsiExec.exe (PID: 7804)
- control.exe (PID: 7344)
- chrome.exe (PID: 4872)
- rundll32.exe (PID: 7724)
- taskkill.exe (PID: 6272)
- schtasks.exe (PID: 7000)
- regsvr32.exe (PID: 5572)
- taskkill.exe (PID: 7436)
- schtasks.exe (PID: 5568)
- forfiles.exe (PID: 4544)
Reads settings of System Certificates
- YolaProduct.exe (PID: 2728)
- k6Dhtr7SnTUoJqATo2cB0jI4.exe (PID: 2584)
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- Lukako.exe (PID: 3432)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- Xuvoqexaete.exe (PID: 3184)
- iexplore.exe (PID: 1656)
- iexplore.exe (PID: 2484)
- 2140854479.exe (PID: 2324)
- Manocabitae.exe (PID: 3328)
- installer.exe (PID: 4540)
- RegAsm.exe (PID: 4972)
- msiexec.exe (PID: 5900)
- AppLaunch.exe (PID: 3064)
- MsiExec.exe (PID: 5692)
- BqAMy4mFWg3REKgWUHPWJQ_3.exe (PID: 448)
- AppLaunch.exe (PID: 5424)
- EfrTS2cJrKrF9tU_CWt5DE4q.exe (PID: 4372)
- XEPXrEV4VjKgc6Un0W8KFWRN.exe (PID: 3684)
- XYxaWZnV6_ZHK4LEdZASMPgy.exe (PID: 3028)
- zjh.exe (PID: 5772)
- anytime1.exe (PID: 1284)
- anytime3.exe (PID: 4624)
- anytime4.exe (PID: 2168)
- anytime2.exe (PID: 4408)
- logger.exe (PID: 3360)
- MyNotes Installation.exe (PID: 3532)
- askinstall25.exe (PID: 3544)
- random.exe (PID: 4600)
- tapinstall.exe (PID: 4420)
- 161.tmp (PID: 3640)
- DrvInst.exe (PID: 2888)
- compan.exe (PID: 5264)
- da02c158-e213-4a39-a4e4-a7a43dfeebaf.exe (PID: 4480)
- d76d02a6-6d7a-49c0-990d-5ff753f5541d.exe (PID: 2980)
- RobCleanerInstlr3138332.exe (PID: 1436)
- Cube_WW9.exe (PID: 5832)
- GrCDlHD.exe (PID: 3500)
- DrvInst.exe (PID: 4872)
- chrome.exe (PID: 5476)
- 78f8513b-0e62-4453-be43-79da43d6e78a.exe (PID: 6060)
- 3cad49fc-6bd9-4df2-bf44-0e449c3e00b7.exe (PID: 4896)
- cab39dba-df17-44a9-944a-4e677ad59ba6.exe (PID: 5284)
- a7b5240e-6154-478d-83bc-4fd17c9ace16.exe (PID: 5048)
- a3fe428d-132b-4400-b1e2-ff673ea7074a.exe (PID: 1128)
- c6af7eef-1dd1-4071-a35b-b4fc5b6b53fd.exe (PID: 4580)
- chrome.exe (PID: 3172)
- bveuj8br4ZnvX4_ibaSTSaVx.exe (PID: 2876)
- Skype.exe (PID: 932)
- askinstall42.exe (PID: 4832)
- 54436333-9a34-4e44-b3ba-ca34075f6df0.exe (PID: 4560)
- chrome.exe (PID: 3812)
- ningli.exe (PID: 5152)
- Cube_WW6.exe (PID: 4780)
- OneCleanerInst942914.exe (PID: 4152)
- fc9829e3-c17a-4ee2-a5e1-cca41998dcc2.exe (PID: 4904)
- e476fe3b-0a9e-4566-a7bf-93dc815990e9.exe (PID: 4460)
- mmnXMVqH00ie_UMohWWQSuTi.exe (PID: 1376)
- rodUdBfXS1K_82Xcij0P21Gl.exe (PID: 3772)
- 5gFmVV1_K5KcdEZISt29axtH.exe (PID: 5320)
- 83a33a9a-3e03-46da-b9c8-72f5fdc494cc.exe (PID: 2756)
- 4b6700ea-650a-4f16-8c51-22072b2e29b3.exe (PID: 752)
- 41c3b0fa-e7c8-4ca1-a053-ac6be3b11ea7.exe (PID: 2396)
- installer.exe (PID: 4072)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- Lukako.exe (PID: 4544)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- RobCleanerInstlr842628.exe (PID: 5240)
- SHesypalori.exe (PID: 784)
- mask_svc.exe (PID: 4212)
- AppLaunch.exe (PID: 4540)
- cnq2OFKbJxjmA8IFszJ1eBv9.exe (PID: 3908)
- m3hNcTJjxaMhPKSDC0pebxfF.exe (PID: 4988)
- gXR3LnTkVr_A5Wu2fjqZnIgq.exe (PID: 7836)
- LSjkaEh9we711ovrGm_ADI8D.exe (PID: 4720)
- 1KPXa4tWwVKo4Ujosf8rYhux.exe (PID: 5176)
- nec9RrUzAn8eXZdKGatvXuQR.exe (PID: 7024)
- iexplore.exe (PID: 4436)
- eP2zoDXXj8JTcj7ImFefr1oj.exe (PID: 6820)
Checks Windows Trust Settings
- YolaProduct.exe (PID: 2728)
- sh76mCEqE3pvpQRXBwFAi72B.exe (PID: 1580)
- ejiA3pAAxByIFNFOGVoyGd6i.exe (PID: 1080)
- nj4sqxb3Lr7ljfuJPEdZta84.exe (PID: 2236)
- iexplore.exe (PID: 1656)
- iexplore.exe (PID: 2484)
- 2140854479.exe (PID: 2324)
- installer.exe (PID: 4540)
- msiexec.exe (PID: 5900)
- MsiExec.exe (PID: 5692)
- powershell.EXE (PID: 3740)
- MyNotes Installation.exe (PID: 3532)
- askinstall25.exe (PID: 3544)
- powershell.EXE (PID: 1364)
- tapinstall.exe (PID: 4420)
- DrvInst.exe (PID: 2888)
- compan.exe (PID: 5264)
- wscript.exe (PID: 2240)
- GrCDlHD.exe (PID: 3500)
- DrvInst.exe (PID: 4872)
- powershell.exe (PID: 3444)
- Cube_WW9.exe (PID: 5832)
- askinstall42.exe (PID: 4832)
- rodUdBfXS1K_82Xcij0P21Gl.exe (PID: 3772)
- 5gFmVV1_K5KcdEZISt29axtH.exe (PID: 5320)
- installer.exe (PID: 4072)
- De_9C4IOJWbvdNmktbSY6ENY.exe (PID: 4164)
- Cube_WW6.exe (PID: 4780)
- 6iTVaBk8qwF8RaeMJhXhp9ZY.exe (PID: 4952)
- 1KPXa4tWwVKo4Ujosf8rYhux.exe (PID: 5176)
- iexplore.exe (PID: 4436)
- eP2zoDXXj8JTcj7ImFefr1oj.exe (PID: 6820)
Dropped object may contain Bitcoin addresses
- YolaProduct.exe (PID: 2728)
- RegAsm.exe (PID: 4972)
- Cube_WW9.exe (PID: 5832)
- MyNotes License Agreement.exe (PID: 3704)
- Cube_WW6.exe (PID: 4780)
Loads dropped or rewritten executable
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- foldershare.tmp (PID: 3680)
- 161.tmp (PID: 3640)
- mpRCIeopmt9ljZw2RlIFPmAU.tmp (PID: 2124)
- NPQpbHyrbXKNeDvAuu66TWPf.tmp (PID: 6632)
Reads the computer name
- WerFault.exe (PID: 1300)
- WerFault.exe (PID: 3956)
- PING.EXE (PID: 1408)
- schtasks.exe (PID: 3708)
- schtasks.exe (PID: 2508)
- iexplore.exe (PID: 1656)
- iexplore.exe (PID: 2484)
- taskkill.exe (PID: 1132)
- msiexec.exe (PID: 5900)
- MsiExec.exe (PID: 2940)
- msiexec.exe (PID: 4432)
- schtasks.exe (PID: 5124)
- schtasks.exe (PID: 4720)
- MsiExec.exe (PID: 5692)
- taskkill.exe (PID: 6112)
- MsiExec.exe (PID: 3444)
- taskkill.exe (PID: 5620)
- rundll32.exe (PID: 5072)
- schtasks.exe (PID: 3688)
- schtasks.exe (PID: 5496)
- gpupdate.exe (PID: 4796)
- schtasks.exe (PID: 4748)
- rundll32.exe (PID: 4844)
- schtasks.exe (PID: 2164)
- schtasks.exe (PID: 3132)
- schtasks.exe (PID: 5072)
- gpupdate.exe (PID: 508)
- vssvc.exe (PID: 3188)
- taskkill.exe (PID: 1764)
- schtasks.exe (PID: 2100)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 4976)
- chrome.exe (PID: 2872)
- schtasks.exe (PID: 2360)
- chrome.exe (PID: 4860)
- rundll32.exe (PID: 5584)
- schtasks.exe (PID: 3736)
- taskkill.exe (PID: 5396)
- chrome.exe (PID: 5584)
- schtasks.exe (PID: 5796)
- schtasks.exe (PID: 5040)
- chrome.exe (PID: 4236)
- chrome.exe (PID: 5476)
- schtasks.exe (PID: 5252)
- chrome.exe (PID: 4820)
- schtasks.exe (PID: 4784)
- schtasks.exe (PID: 4496)
- schtasks.exe (PID: 2460)
- schtasks.exe (PID: 1972)
- schtasks.exe (PID: 4496)
- schtasks.exe (PID: 4272)
- schtasks.exe (PID: 3604)
- schtasks.exe (PID: 6004)
- schtasks.exe (PID: 5912)
- chrome.exe (PID: 2216)
- rundll32.EXE (PID: 2604)
- chrome.exe (PID: 2896)
- chrome.exe (PID: 3172)
- chrome.exe (PID: 5992)
- schtasks.exe (PID: 3316)
- schtasks.exe (PID: 2360)
- control.exe (PID: 5576)
- control.exe (PID: 5028)
- chrome.exe (PID: 3812)
- chrome.exe (PID: 4188)
- chrome.exe (PID: 4120)
- chrome.exe (PID: 1408)
- taskkill.exe (PID: 5584)
- taskkill.exe (PID: 3520)
- rundll32.exe (PID: 5804)
- chrome.exe (PID: 4416)
- MsiExec.exe (PID: 5672)
- control.exe (PID: 2052)
- control.exe (PID: 4936)
- PING.EXE (PID: 1324)
- schtasks.exe (PID: 5948)
- schtasks.exe (PID: 2064)
- control.exe (PID: 4856)
- iexplore.exe (PID: 5336)
- chrome.exe (PID: 2420)
- msiexec.exe (PID: 2628)
- iexplore.exe (PID: 4436)
- taskkill.exe (PID: 4300)
- PING.EXE (PID: 7484)
- schtasks.exe (PID: 6688)
- MsiExec.exe (PID: 7804)
- control.exe (PID: 7344)
- taskkill.exe (PID: 6272)
- schtasks.exe (PID: 7000)
- taskkill.exe (PID: 7436)
Application was dropped or rewritten from another process
- 8LAXyC_p8pInUFq3lMbg2W3C.tmp (PID: 3760)
- Lukako.exe (PID: 3432)
- foldershare.tmp (PID: 3680)
- 161.tmp (PID: 3640)
- mpRCIeopmt9ljZw2RlIFPmAU.tmp (PID: 2124)
- Lukako.exe (PID: 4544)
- NPQpbHyrbXKNeDvAuu66TWPf.tmp (PID: 6632)
- Lukako.exe (PID: 6956)
Application launched itself
- iexplore.exe (PID: 2484)
- chrome.exe (PID: 2872)
- chrome.exe (PID: 5584)
- chrome.exe (PID: 2216)
- chrome.exe (PID: 3812)
- iexplore.exe (PID: 5336)
Changes internet zones settings
- iexplore.exe (PID: 2484)
- iexplore.exe (PID: 5336)
Creates files in the program directory
- Lukako.exe (PID: 3432)
- foldershare.tmp (PID: 3680)
- 161.tmp (PID: 3640)
Creates files in the user directory
- iexplore.exe (PID: 1656)
Reads internet explorer settings
- iexplore.exe (PID: 1656)
Creates a software uninstall entry
- foldershare.tmp (PID: 3680)
- 161.tmp (PID: 3640)
Reads Microsoft Office registry keys
- MsiExec.exe (PID: 2940)
- MsiExec.exe (PID: 5692)
- MsiExec.exe (PID: 5672)
Check for Java to be installed
- MsiExec.exe (PID: 2940)
- MsiExec.exe (PID: 5692)
- MsiExec.exe (PID: 5672)
Reads the date of Windows installation
- iexplore.exe (PID: 2484)
- chrome.exe (PID: 2420)
Manual execution by user
- FolderShare.exe (PID: 2012)
- FolderShare.exe (PID: 3284)
- chrome.exe (PID: 2872)
- chrome.exe (PID: 5584)
- chrome.exe (PID: 3812)
Searches for installed software
- DrvInst.exe (PID: 2888)
Reads the hosts file
- chrome.exe (PID: 2872)
- chrome.exe (PID: 5584)
- chrome.exe (PID: 5476)
- chrome.exe (PID: 2216)
- chrome.exe (PID: 3172)
- chrome.exe (PID: 3812)
- chrome.exe (PID: 1408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Setup/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:09:11 22:15:01 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
641
Monitored processes
442
Malicious processes
136
Suspicious processes
58
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\AppData\Local\Temp\zjh.exe" | C:\Users\admin\AppData\Local\Temp\zjh.exe | — | LzmwAqmV.exe | |||||||||||
User: admin Company: DCloud Integrity Level: HIGH Description: HBuilder X Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x69b3d988,0x69b3d998,0x69b3d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 9 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,15060846022507745445,9000948567788643099,131072 --enable-features=PasswordImport --lang=en-US --disable-client-side-phishing-detection --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1916 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 9 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 304 | "C:\Users\admin\AppData\Local\Temp\2108352564.exe" | C:\Users\admin\AppData\Local\Temp\2108352564.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 392 | C:\Users\admin\AppData\Local\Temp\kezmetus.4gp\toolspab3.exe | C:\Users\admin\AppData\Local\Temp\kezmetus.4gp\toolspab3.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 396 | "C:\Windows\System32\cmd.exe" /c taskkill /im "mMkNQwcrxJo9Fac4EU9aFY3M.exe" /f & erase "C:\Users\admin\Pictures\Adobe Films\mMkNQwcrxJo9Fac4EU9aFY3M.exe" & exit | C:\Windows\System32\cmd.exe | — | mMkNQwcrxJo9Fac4EU9aFY3M.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 424 | "C:\Windows\System32\cmd.exe" /k C:\Users\admin\AppData\Local\Temp\r3rswk4c.xkd\random.exe & exit | C:\Windows\System32\cmd.exe | — | Manocabitae.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 444 | "C:\Program Files\Company\NewProduct\inst2.exe" | C:\Program Files\Company\NewProduct\inst2.exe | — | setupWW1.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: NTFS Information Dump Exit code: 0 Version: 1.2 Modules
| |||||||||||||||
| 448 | "C:\Users\admin\Pictures\Adobe Films\BqAMy4mFWg3REKgWUHPWJQ_3.exe" -u | C:\Users\admin\Pictures\Adobe Films\BqAMy4mFWg3REKgWUHPWJQ_3.exe | BqAMy4mFWg3REKgWUHPWJQ_3.exe | ||||||||||||
User: admin Company: initool Integrity Level: HIGH Description: initool Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 508 | "C:\Windows\system32\gpupdate.exe" /force | C:\Windows\system32\gpupdate.exe | — | powershell.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft� Group Policy Update Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
427 668
Read events
422 279
Write events
5 184
Delete events
205
Modification events
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\McAfee+Total+Protection+2022+Crack+Full+Free+Here!.zip | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
403
Suspicious files
300
Text files
381
Unknown types
228
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2728 | YolaProduct.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2728 | YolaProduct.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 2728 | YolaProduct.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 2728 | YolaProduct.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\PL_Client[1].bmp | binary | |
MD5:— | SHA256:— | |||
| 2728 | YolaProduct.exe | C:\Users\admin\Documents\Ei8DrAmaYu9K8ghN89CsjOW1.tmp | binary | |
MD5:— | SHA256:— | |||
| 2728 | YolaProduct.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\NiceProcessX32[1].bmp | executable | |
MD5:— | SHA256:— | |||
| 2728 | YolaProduct.exe | C:\Users\admin\Pictures\Adobe Films\tmn7Sjo6IZn07qqz6H1i1Sh2.exe | executable | |
MD5:— | SHA256:— | |||
| 860 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 2136 | tmn7Sjo6IZn07qqz6H1i1Sh2.exe | C:\Users\admin\AppData\Local\Temp\pidHTSIGEi8DrAmaYu9K8ghN89.dll | executable | |
MD5:— | SHA256:— | |||
| 2728 | YolaProduct.exe | C:\Users\admin\Pictures\Adobe Films\d2Xj82dwawQ_uUin1Y3Bpvuo.exe | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
437
TCP/UDP connections
979
DNS requests
380
Threats
2 103
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2728 | YolaProduct.exe | GET | — | 172.67.133.215:80 | http://wfsdragon.ru/api/setStats.php | US | — | — | malicious |
2728 | YolaProduct.exe | HEAD | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | — | — | malicious |
2728 | YolaProduct.exe | HEAD | 200 | 212.193.30.29:80 | http://212.193.30.29/download/Service.bmp | RU | — | — | malicious |
2728 | YolaProduct.exe | HEAD | 200 | 185.215.113.208:80 | http://185.215.113.208/ferrari.exe | PT | — | — | malicious |
2728 | YolaProduct.exe | HEAD | 200 | 185.112.83.8:80 | http://185.112.83.8/install6.exe | RU | — | — | suspicious |
2728 | YolaProduct.exe | HEAD | 404 | 212.193.30.45:80 | http://212.193.30.45/WW/file8.exe | RU | — | — | malicious |
2728 | YolaProduct.exe | GET | 404 | 212.193.30.45:80 | http://212.193.30.45/WW/file7.exe | RU | — | — | malicious |
2728 | YolaProduct.exe | HEAD | 404 | 212.193.30.29:80 | http://212.193.30.29/WW/file3.exe | RU | — | — | malicious |
2728 | YolaProduct.exe | HEAD | 404 | 212.193.30.29:80 | http://212.193.30.29/WW/file4.exe | RU | — | — | malicious |
2728 | YolaProduct.exe | HEAD | 404 | 85.209.157.230:80 | http://tg8.cllgxx.com/sr21/siww1047.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2728 | YolaProduct.exe | 45.144.225.57:80 | — | — | — | malicious |
2728 | YolaProduct.exe | 172.67.75.166:443 | db-ip.com | — | US | malicious |
2728 | YolaProduct.exe | 185.215.113.208:80 | — | Ebonyhorizon Telecomunicacoes S.A. | PT | malicious |
2728 | YolaProduct.exe | 212.193.30.29:80 | — | — | RU | malicious |
2728 | YolaProduct.exe | 185.112.83.8:80 | — | Total Server Solutions L.L.C. | RU | suspicious |
2728 | YolaProduct.exe | 212.193.30.45:80 | — | — | RU | malicious |
2728 | YolaProduct.exe | 52.218.104.171:80 | zayech.s3.eu-west-1.amazonaws.com | Amazon.com, Inc. | IE | unknown |
2728 | YolaProduct.exe | 52.219.47.217:80 | ellissa.s3.eu-central-1.amazonaws.com | — | DE | unknown |
2728 | YolaProduct.exe | 85.209.157.230:80 | stylesheet.faseaegasdfase.com | — | — | suspicious |
— | — | 212.193.30.45:80 | — | — | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
wfsdragon.ru |
| malicious |
cdn.discordapp.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ipinfo.io |
| shared |
db-ip.com |
| whitelisted |
api.db-ip.com |
| shared |
stylesheet.faseaegasdfase.com |
| malicious |
baanrabiengfah.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2728 | YolaProduct.exe | A Network Trojan was detected | ET MALWARE User-Agent (???) |
2728 | YolaProduct.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2728 | YolaProduct.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2728 | YolaProduct.exe | A Network Trojan was detected | ET MALWARE User-Agent (???) |
2728 | YolaProduct.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2728 | YolaProduct.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2728 | YolaProduct.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2728 | YolaProduct.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
2728 | YolaProduct.exe | A Network Trojan was detected | ET TROJAN Win32/Unk.HRESQ! MultiDownloader Checkin |
2728 | YolaProduct.exe | A Network Trojan was detected | ET TROJAN Win32/Unk.HRESQ! MultiDownloader Checkin |
1056 ETPRO signatures available at the full report
Process | Message |
|---|---|
lighteningplayer-cache-gen.exe | main libvlc debug: VLC media player - 3.0.7 Vetinari
|
lighteningplayer-cache-gen.exe | main libvlc debug: Copyright � 1996-2018 the VideoLAN team
|
lighteningplayer-cache-gen.exe | main libvlc debug: revision 3.0.2-225-gc9e3360dd4
|
lighteningplayer-cache-gen.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-twolame' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-x264' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--build=x86_64-pc-linux-gnu' 'build_alias=x86_64-pc-linux-gnu' 'host_alias=i686-w64-mingw32'
|
lighteningplayer-cache-gen.exe | main libvlc debug: using multimedia timers as clock source
|
lighteningplayer-cache-gen.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
lighteningplayer-cache-gen.exe | main libvlc debug: searching plug-in modules
|
lighteningplayer-cache-gen.exe | main libvlc debug: ignoring plugins cache file
|
lighteningplayer-cache-gen.exe | main libvlc debug: recursively browsing `C:\Program Files\lighteningplayer\plugins'
|
lighteningplayer-cache-gen.exe | main libvlc debug: saving plugins cache C:\Program Files\lighteningplayer\plugins\plugins.dat
|