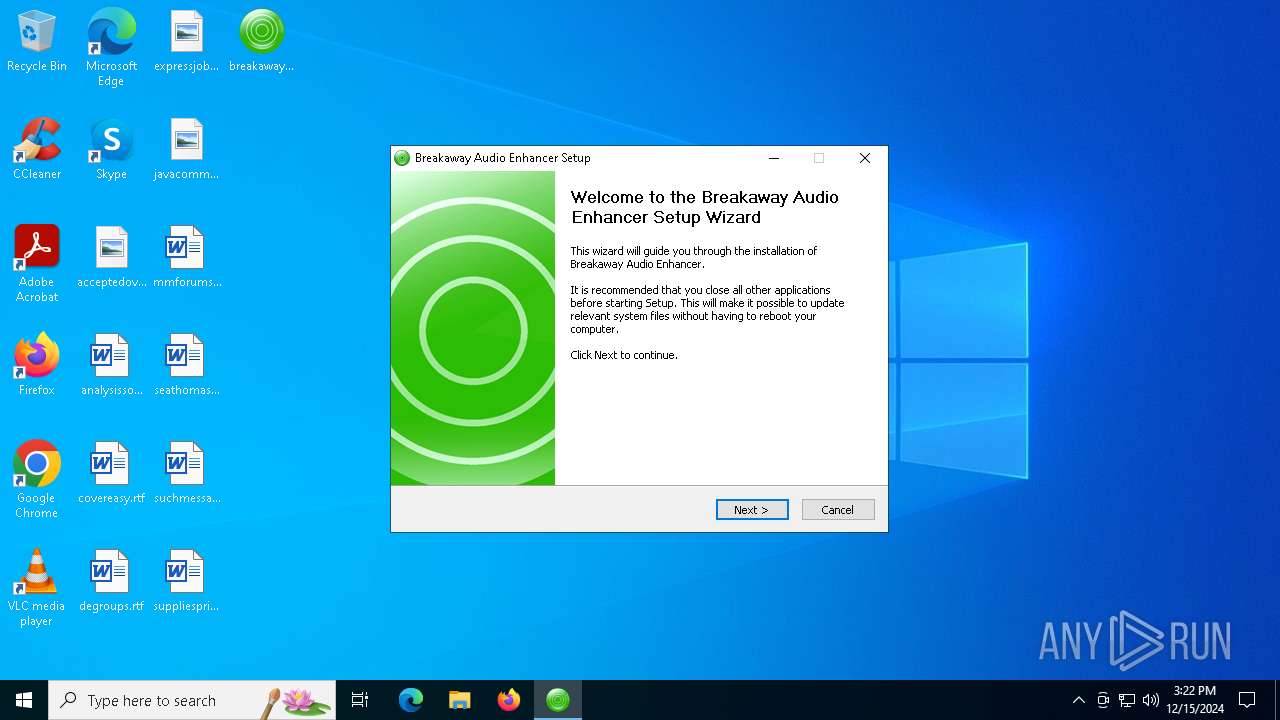
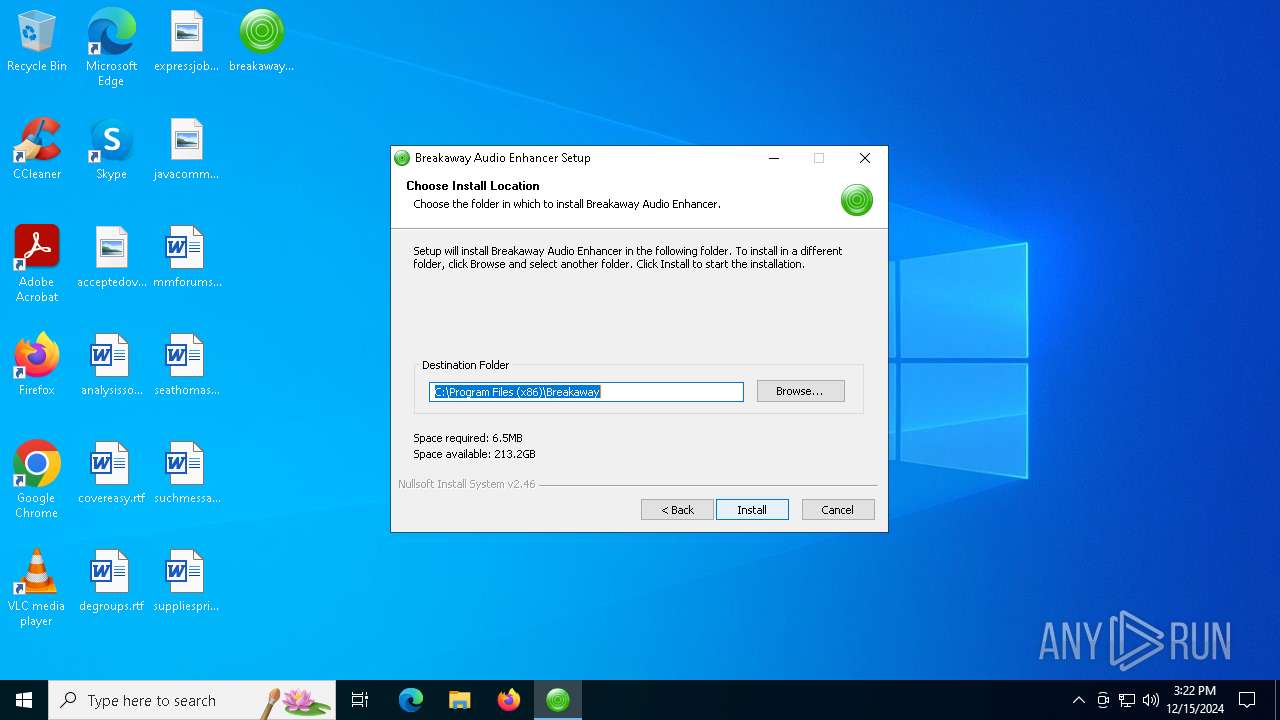
| File name: | breakaway_setup_1.40.03.exe |
| Full analysis: | https://app.any.run/tasks/5bdb6b88-379b-4aec-bc86-505d604c756a |
| Verdict: | Malicious activity |
| Analysis date: | December 15, 2024, 15:21:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | F618AF7EDBD7461C887B494A31F8AEBB |
| SHA1: | 8DCFA50E5249DCD79021585516FF224AE5D4FE05 |
| SHA256: | F73F8733E46AE192C46A4383413435B3EABF69A602CF6141CB805785C0ABF019 |
| SSDEEP: | 98304:pvyqdxigyaE87Q2xTdE6zx/xXG1B7w907jLknJj40zxMpp/PHkA7oosxSD3wsTDc:Zw8u2J |
MALICIOUS
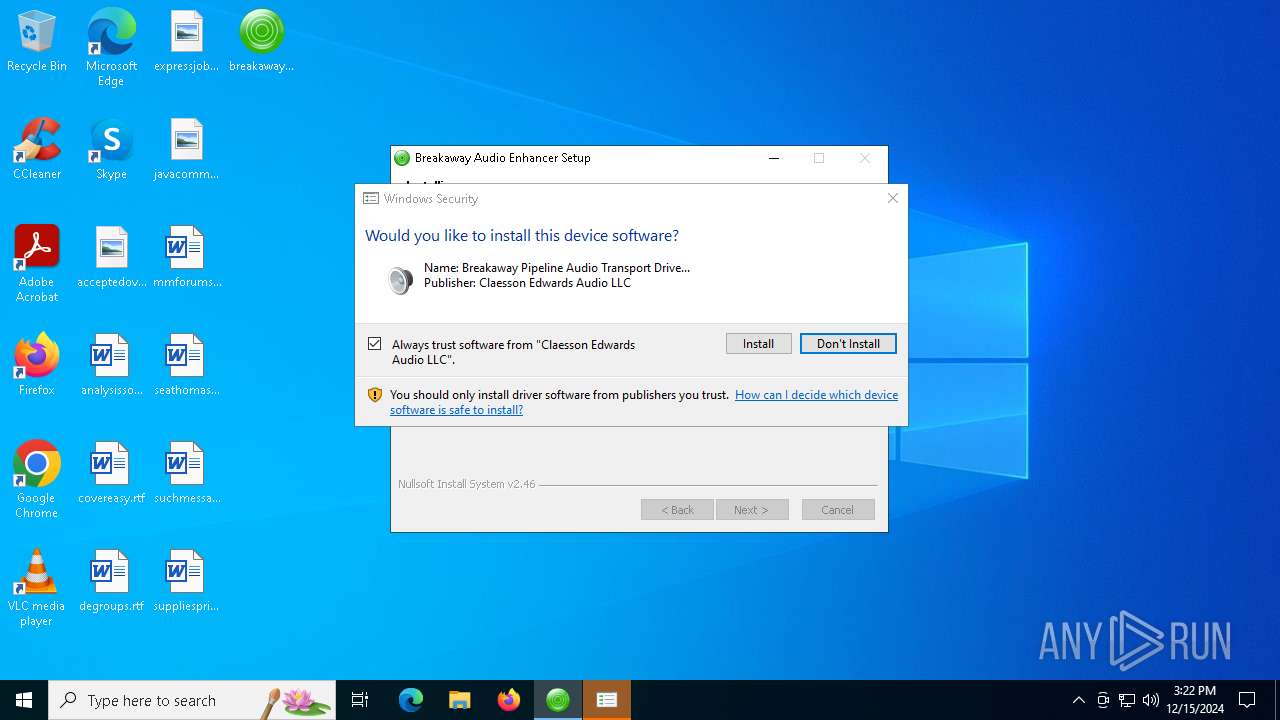
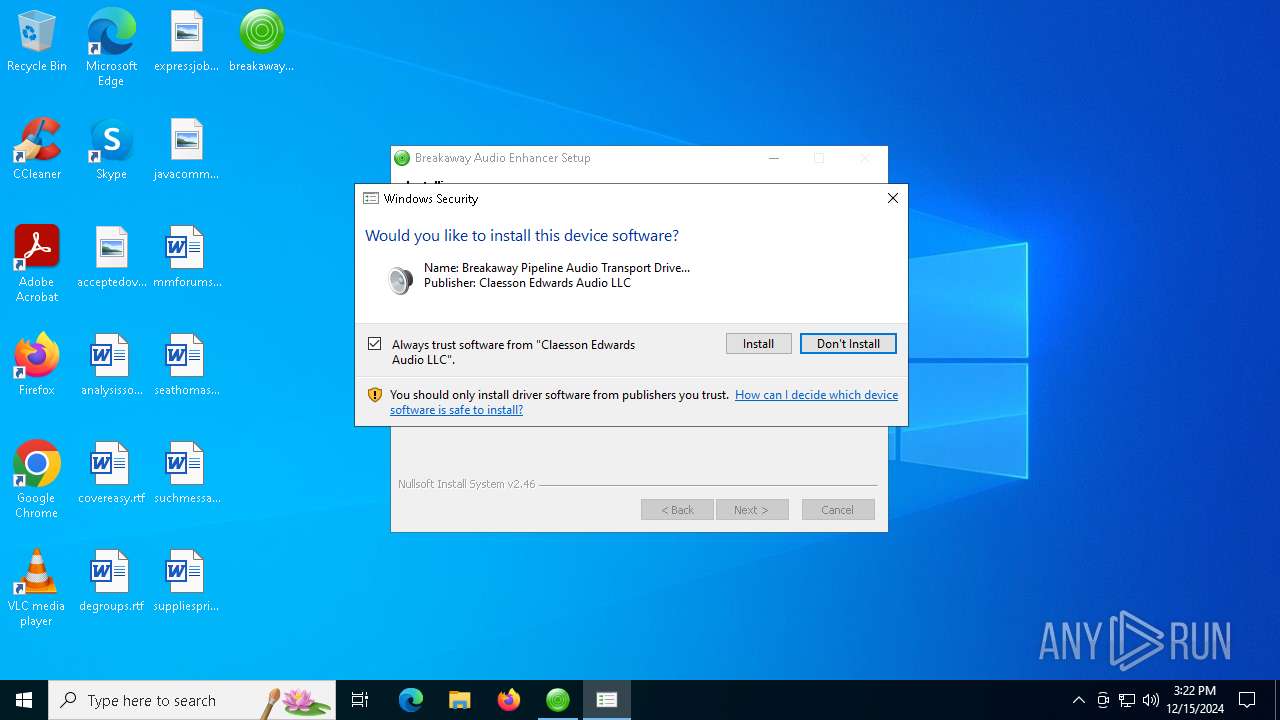
Executing a file with an untrusted certificate
- breakaway_setup_1.40.03.exe (PID: 6412)
- breakaway_setup_1.40.03.exe (PID: 6660)
- breakaway.exe (PID: 6232)
Registers / Runs the DLL via REGSVR32.EXE
- breakaway_setup_1.40.03.exe (PID: 6660)
Changes the autorun value in the registry
- breakaway_setup_1.40.03.exe (PID: 6660)
SUSPICIOUS
The process creates files with name similar to system file names
- breakaway_setup_1.40.03.exe (PID: 6412)
- breakaway_setup_1.40.03.exe (PID: 6660)
Executable content was dropped or overwritten
- breakaway_setup_1.40.03.exe (PID: 6412)
- breakaway_setup_1.40.03.exe (PID: 6660)
- wdmdrvmgr.exe (PID: 6928)
- drvinst.exe (PID: 7000)
- drvinst.exe (PID: 3524)
Malware-specific behavior (creating "System.dll" in Temp)
- breakaway_setup_1.40.03.exe (PID: 6412)
- breakaway_setup_1.40.03.exe (PID: 6660)
Reads security settings of Internet Explorer
- breakaway_setup_1.40.03.exe (PID: 6412)
- wdmdrvmgr.exe (PID: 6928)
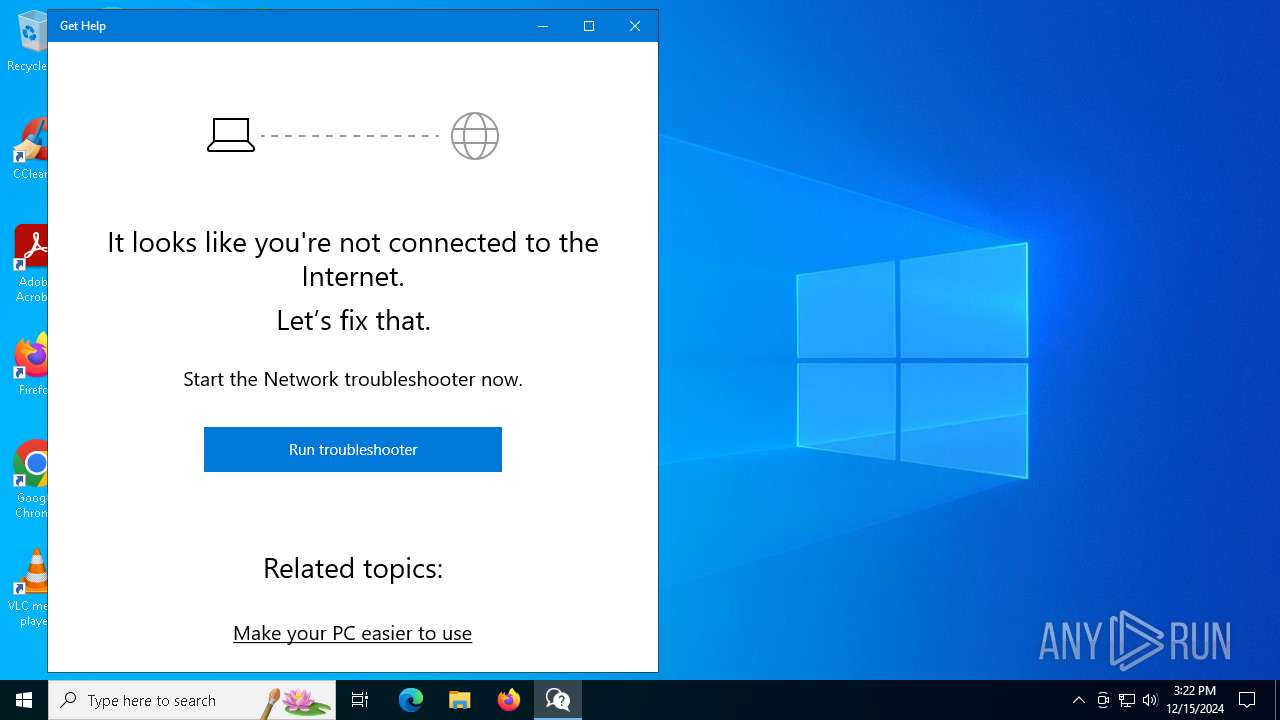
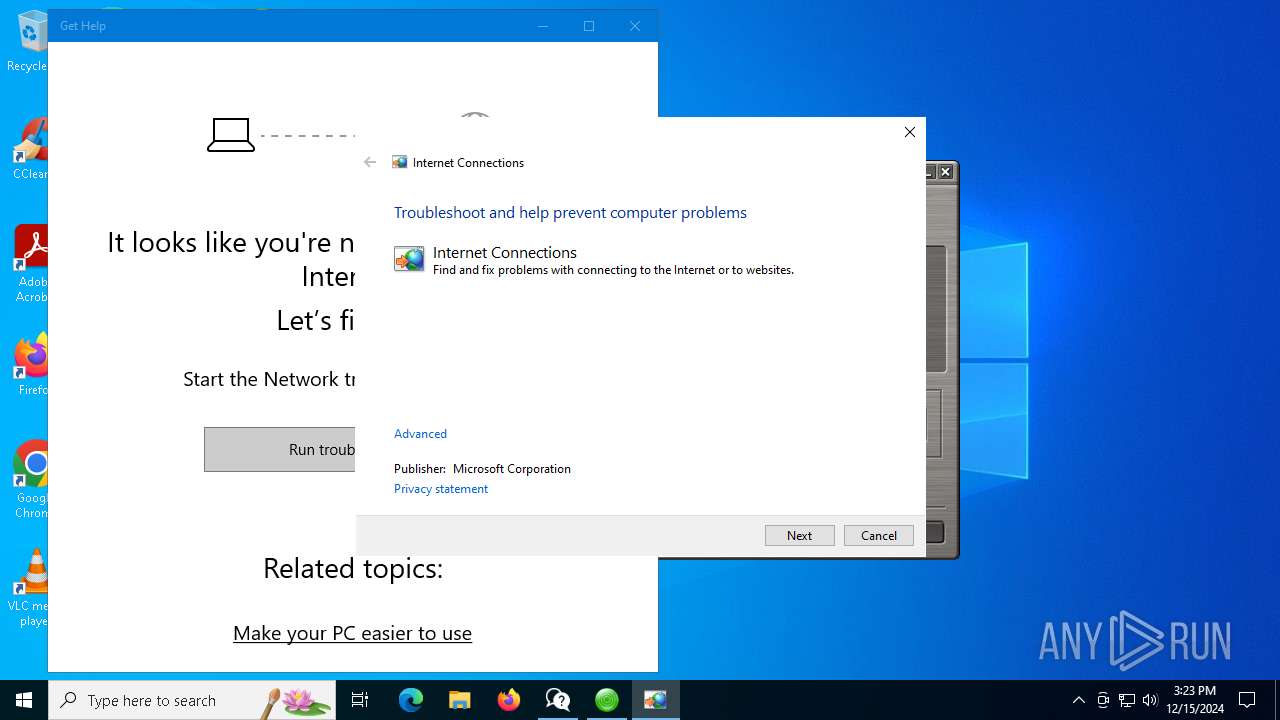
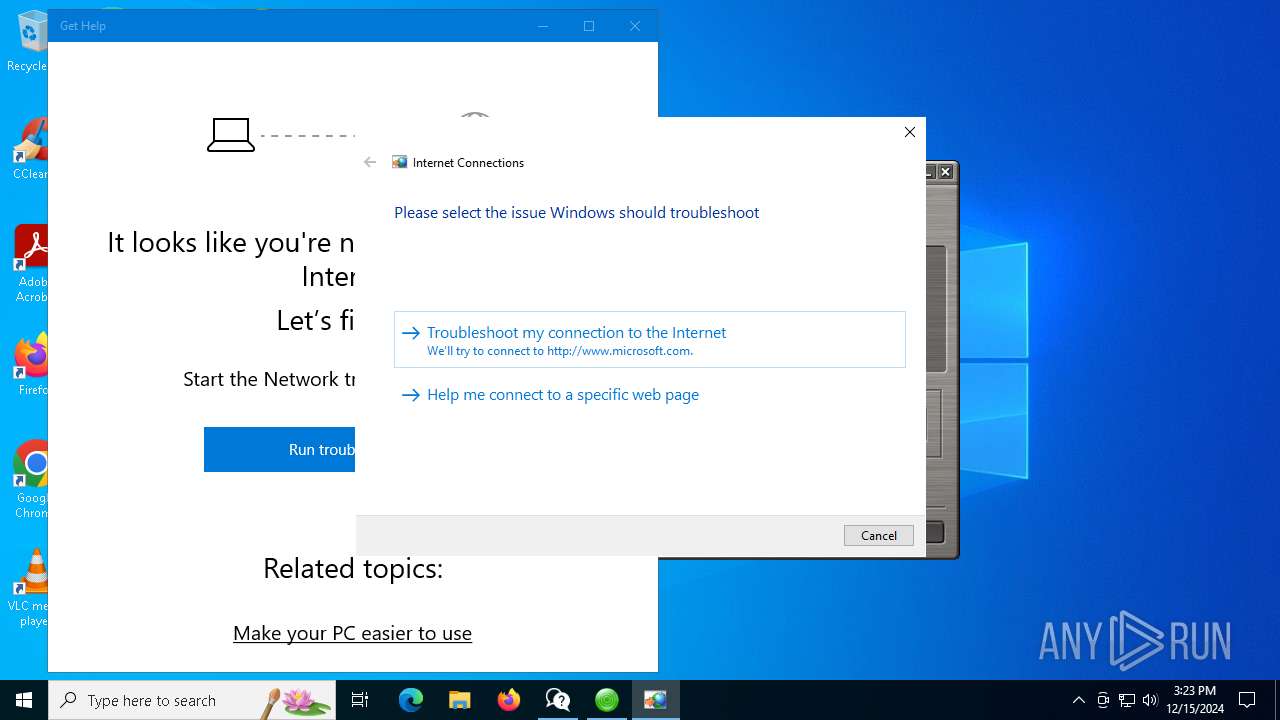
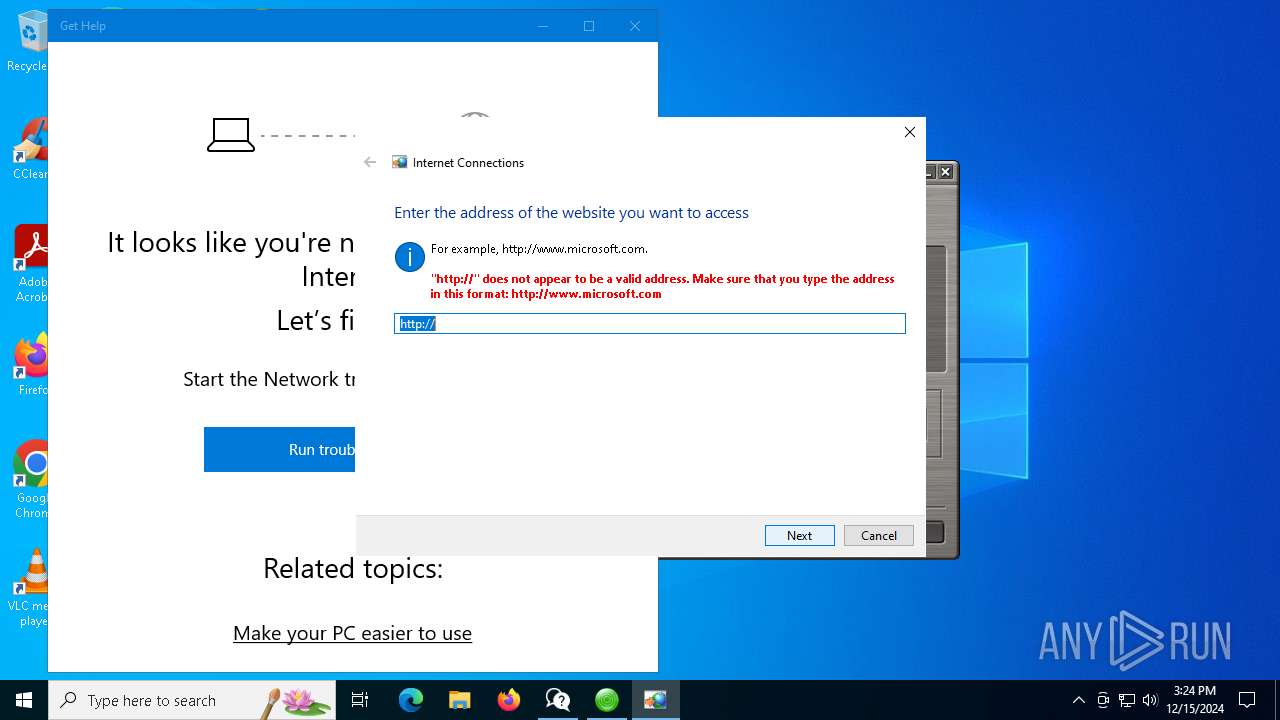
- GetHelp.exe (PID: 1296)
Application launched itself
- breakaway_setup_1.40.03.exe (PID: 6412)
Drops a system driver (possible attempt to evade defenses)
- breakaway_setup_1.40.03.exe (PID: 6660)
- wdmdrvmgr.exe (PID: 6928)
- drvinst.exe (PID: 7000)
- drvinst.exe (PID: 3524)
Checks Windows Trust Settings
- wdmdrvmgr.exe (PID: 6928)
- drvinst.exe (PID: 7000)
Creates or modifies Windows services
- drvinst.exe (PID: 3524)
Creates files in the driver directory
- drvinst.exe (PID: 3524)
- drvinst.exe (PID: 7000)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 5244)
Reads the BIOS version
- breakaway.exe (PID: 6232)
Creates a software uninstall entry
- breakaway_setup_1.40.03.exe (PID: 6660)
INFO
Checks supported languages
- breakaway_setup_1.40.03.exe (PID: 6412)
- breakaway_setup_1.40.03.exe (PID: 6660)
- wdmdrvmgr.exe (PID: 6928)
- drvinst.exe (PID: 7000)
- GetHelp.exe (PID: 1296)
- drvinst.exe (PID: 3524)
- breakaway.exe (PID: 6232)
Process checks whether UAC notifications are on
- breakaway_setup_1.40.03.exe (PID: 6412)
Create files in a temporary directory
- breakaway_setup_1.40.03.exe (PID: 6412)
- breakaway_setup_1.40.03.exe (PID: 6660)
- wdmdrvmgr.exe (PID: 6928)
- breakaway.exe (PID: 6232)
- sdiagnhost.exe (PID: 1536)
Reads the computer name
- breakaway_setup_1.40.03.exe (PID: 6412)
- breakaway_setup_1.40.03.exe (PID: 6660)
- wdmdrvmgr.exe (PID: 6928)
- GetHelp.exe (PID: 1296)
- drvinst.exe (PID: 3524)
- drvinst.exe (PID: 7000)
- breakaway.exe (PID: 6232)
The process uses the downloaded file
- breakaway_setup_1.40.03.exe (PID: 6412)
- sdiagnhost.exe (PID: 1536)
Process checks computer location settings
- breakaway_setup_1.40.03.exe (PID: 6412)
Creates files in the program directory
- breakaway_setup_1.40.03.exe (PID: 6660)
- breakaway.exe (PID: 6232)
Reads the machine GUID from the registry
- wdmdrvmgr.exe (PID: 6928)
- drvinst.exe (PID: 7000)
Reads the software policy settings
- wdmdrvmgr.exe (PID: 6928)
- rundll32.exe (PID: 7028)
- drvinst.exe (PID: 7000)
The sample compiled with english language support
- wdmdrvmgr.exe (PID: 6928)
- drvinst.exe (PID: 7000)
- breakaway_setup_1.40.03.exe (PID: 6660)
- drvinst.exe (PID: 3524)
Adds/modifies Windows certificates
- drvinst.exe (PID: 7000)
Reads security settings of Internet Explorer
- HelpPane.exe (PID: 7076)
- rundll32.exe (PID: 7028)
- sdiagnhost.exe (PID: 1536)
Reads Environment values
- GetHelp.exe (PID: 1296)
Sends debugging messages
- breakaway.exe (PID: 6232)
Gets data length (POWERSHELL)
- sdiagnhost.exe (PID: 1536)
Creates files or folders in the user directory
- breakaway_setup_1.40.03.exe (PID: 6660)
Uses string replace method (POWERSHELL)
- sdiagnhost.exe (PID: 1536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
141
Monitored processes
13
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "C:\Program Files\WindowsApps\Microsoft.GetHelp_10.1706.13331.0_x64__8wekyb3d8bbwe\GetHelp.exe" -ServerName:App.AppXc53jt7x72yk6zj4f70fb3gxetfvdh22w.mca | C:\Program Files\WindowsApps\Microsoft.GetHelp_10.1706.13331.0_x64__8wekyb3d8bbwe\GetHelp.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1536 | C:\WINDOWS\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1744 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Breakaway\badeskband2_64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | breakaway_setup_1.40.03.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | DrvInst.exe "2" "11" "ROOT\MEDIA\0000" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:3beb73af0c48fa1f:DevInst:4.15.0.7317:eumusdesign_vac_wdm_lcs," "42adb0273" "00000000000001C4" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | /s "C:\Program Files (x86)\Breakaway\badeskband2_64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
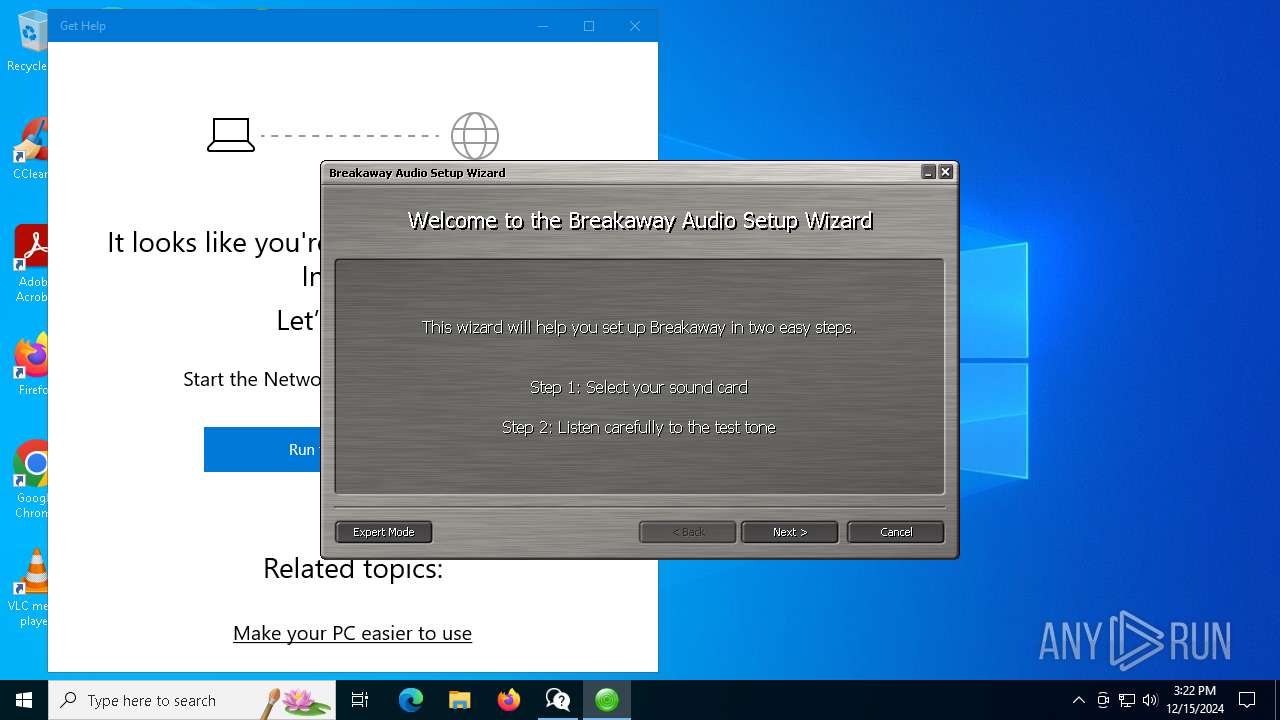
| 6232 | "C:\Program Files (x86)\Breakaway\breakaway.exe" first | C:\Program Files (x86)\Breakaway\breakaway.exe | breakaway_setup_1.40.03.exe | ||||||||||||
User: admin Company: ClaessonEdwards LLC Integrity Level: MEDIUM Description: Breakaway Audio Enhancer Version: 1,3,0,05 Modules
| |||||||||||||||
| 6412 | "C:\Users\admin\Desktop\breakaway_setup_1.40.03.exe" | C:\Users\admin\Desktop\breakaway_setup_1.40.03.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6660 | "C:\Users\admin\Desktop\breakaway_setup_1.40.03.exe" /UAC:602EE /NCRC | C:\Users\admin\Desktop\breakaway_setup_1.40.03.exe | breakaway_setup_1.40.03.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
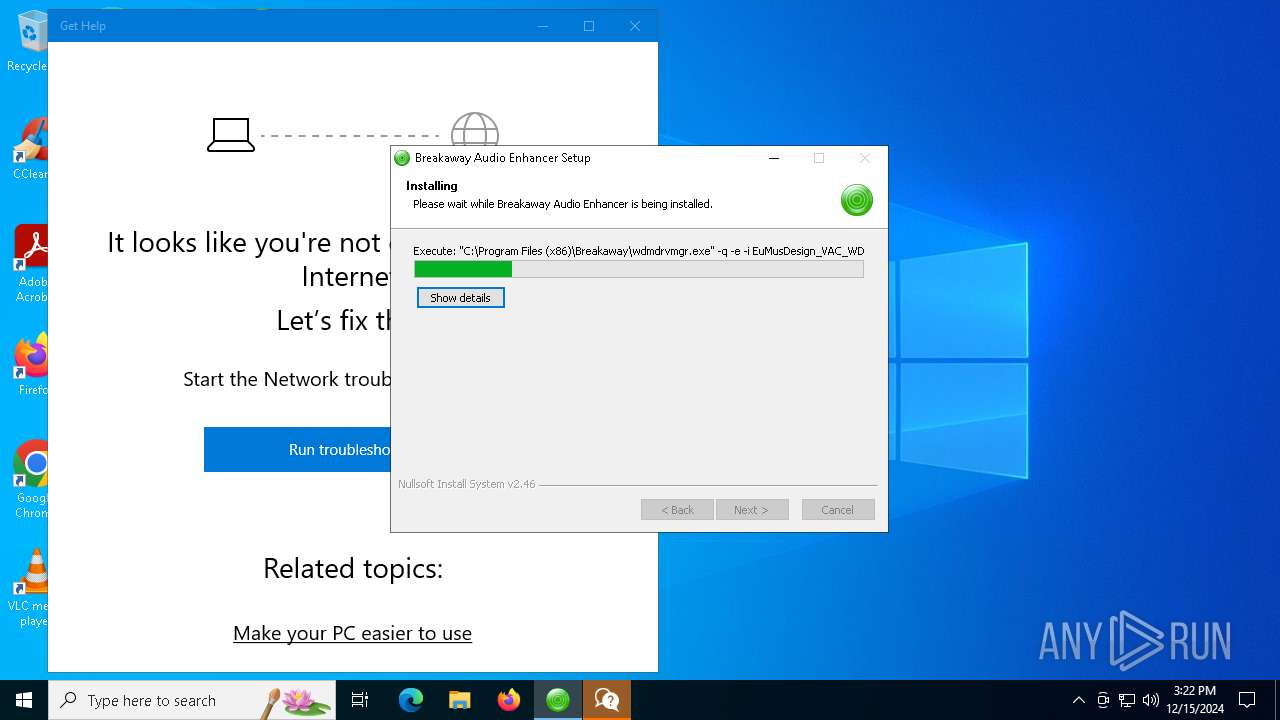
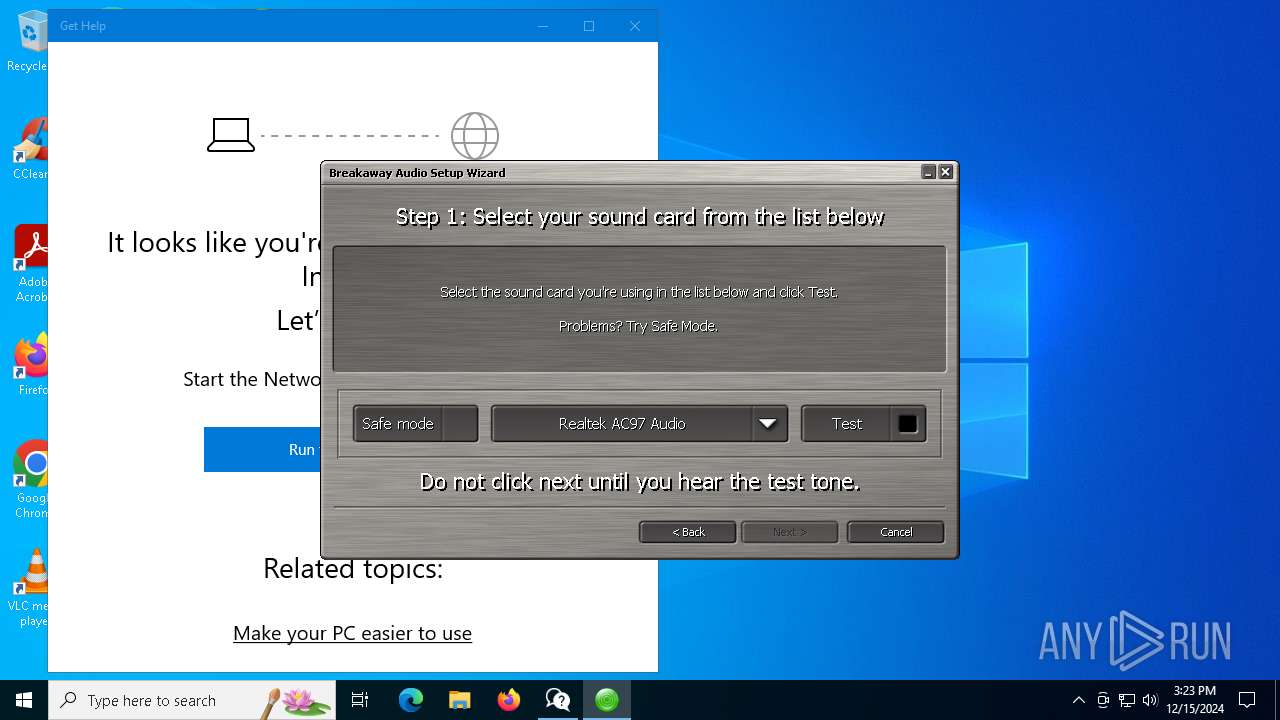
| 6928 | "C:\Program Files (x86)\Breakaway\wdmdrvmgr.exe" -q -e -i EuMusDesign_VAC_WDM_lcs "C:\Program Files (x86)\Breakaway\vaclcskd.inf" | C:\Program Files (x86)\Breakaway\wdmdrvmgr.exe | breakaway_setup_1.40.03.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
15 446
Read events
14 735
Write events
703
Delete events
8
Modification events
| (PID) Process: | (6928) wdmdrvmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Multimedia\Sound Mapper |
| Operation: | write | Name: | Record |
Value: Microphone (2- Realtek AC'97 Au | |||
| (PID) Process: | (6928) wdmdrvmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Multimedia\Sound Mapper |
| Operation: | write | Name: | Playback |
Value: Speakers (2- Realtek AC'97 Audi | |||
| (PID) Process: | (6928) wdmdrvmgr.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\Enum\ROOT\MEDIA\0000 |
| Operation: | write | Name: | CSConfigFlags |
Value: 1 | |||
| (PID) Process: | (6928) wdmdrvmgr.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (1296) GetHelp.exe | Key: | \REGISTRY\A\{ee561d1b-8402-a66b-d7fc-a8e58616c9e1}\LocalState |
| Operation: | write | Name: | PreviouslyLaunched |
Value: 01106D9D2D054FDB01 | |||
| (PID) Process: | (7076) HelpPane.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Assistance\Client\1.0\Settings |
| Operation: | write | Name: | IsConnected |
Value: 0 | |||
| (PID) Process: | (7076) HelpPane.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Assistance\Client\1.0\Settings |
| Operation: | write | Name: | UseLanguageAlternative |
Value: 0 | |||
| (PID) Process: | (7076) HelpPane.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7076) HelpPane.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7076) HelpPane.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
19
Suspicious files
9
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6412 | breakaway_setup_1.40.03.exe | C:\Users\admin\AppData\Local\Temp\nsf644C.tmp\System.dll | executable | |
MD5:C17103AE9072A06DA581DEC998343FC1 | SHA256:DC58D8AD81CACB0C1ED72E33BFF8F23EA40B5252B5BB55D393A0903E6819AE2F | |||
| 6660 | breakaway_setup_1.40.03.exe | C:\Users\admin\AppData\Local\Temp\nsl672A.tmp\nsDialogs.dll | executable | |
MD5:C10E04DD4AD4277D5ADC951BB331C777 | SHA256:E31AD6C6E82E603378CB6B80E67D0E0DCD9CF384E1199AC5A65CB4935680021A | |||
| 6412 | breakaway_setup_1.40.03.exe | C:\Users\admin\AppData\Local\Temp\nsf644C.tmp\UAC.dll | executable | |
MD5:B7D7324F2128531C9777D837516B65A6 | SHA256:530DC2B26366FC86072487438317A5723A10FF8B38522F9E813DF19146A31033 | |||
| 6928 | wdmdrvmgr.exe | C:\Users\admin\AppData\Local\Temp\{6e249792-10be-3d47-a4de-d030fef304a0}\SETAA3E.tmp | cat | |
MD5:B6636EF3B38DA6498F41F77743B34A53 | SHA256:9FE335B4786B05EA92682B27911025D2077AC46628ADB8A815AA27E31ABB01A2 | |||
| 6928 | wdmdrvmgr.exe | C:\Users\admin\AppData\Local\Temp\{6e249792-10be-3d47-a4de-d030fef304a0}\x64\SETAA1E.tmp | executable | |
MD5:B1664AF2F44874221E7DEAA6A940A24D | SHA256:F51F8B9A39E60548D135C43D02A36D7710871D34EEF9AEA51B2C5A3E210AD470 | |||
| 6660 | breakaway_setup_1.40.03.exe | C:\Program Files (x86)\Breakaway\wdmdrvmgr.exe | executable | |
MD5:1444BA708306661DDC8C51180A4385AC | SHA256:221C3DDAEF72163499FD35238BC0C62AA81DBE76F8CFEB33A1EC21DC631CCFC7 | |||
| 6928 | wdmdrvmgr.exe | C:\Users\admin\AppData\Local\Temp\{6e249792-10be-3d47-a4de-d030fef304a0}\vaclcskd.cat | cat | |
MD5:B6636EF3B38DA6498F41F77743B34A53 | SHA256:9FE335B4786B05EA92682B27911025D2077AC46628ADB8A815AA27E31ABB01A2 | |||
| 7000 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{61f7b136-a68f-484b-9c1a-36fbd06a3b50}\x64\SETAAAB.tmp | executable | |
MD5:B1664AF2F44874221E7DEAA6A940A24D | SHA256:F51F8B9A39E60548D135C43D02A36D7710871D34EEF9AEA51B2C5A3E210AD470 | |||
| 6928 | wdmdrvmgr.exe | C:\Users\admin\AppData\Local\Temp\{6e249792-10be-3d47-a4de-d030fef304a0}\SETAA3F.tmp | ini | |
MD5:12F388FF48FBF569A365EC7F6002A1D9 | SHA256:B8A1D8CEE90759B9768B48BC1622FD0625B76B580EB4EB9CE90B43F3EC44AC10 | |||
| 6928 | wdmdrvmgr.exe | C:\Users\admin\AppData\Local\Temp\{6e249792-10be-3d47-a4de-d030fef304a0}\vaclcskd.inf | ini | |
MD5:12F388FF48FBF569A365EC7F6002A1D9 | SHA256:B8A1D8CEE90759B9768B48BC1622FD0625B76B580EB4EB9CE90B43F3EC44AC10 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
19
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
440 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
440 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3976 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
breakaway.exe |
%s------------------------------------------------
--- WinLicense Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|