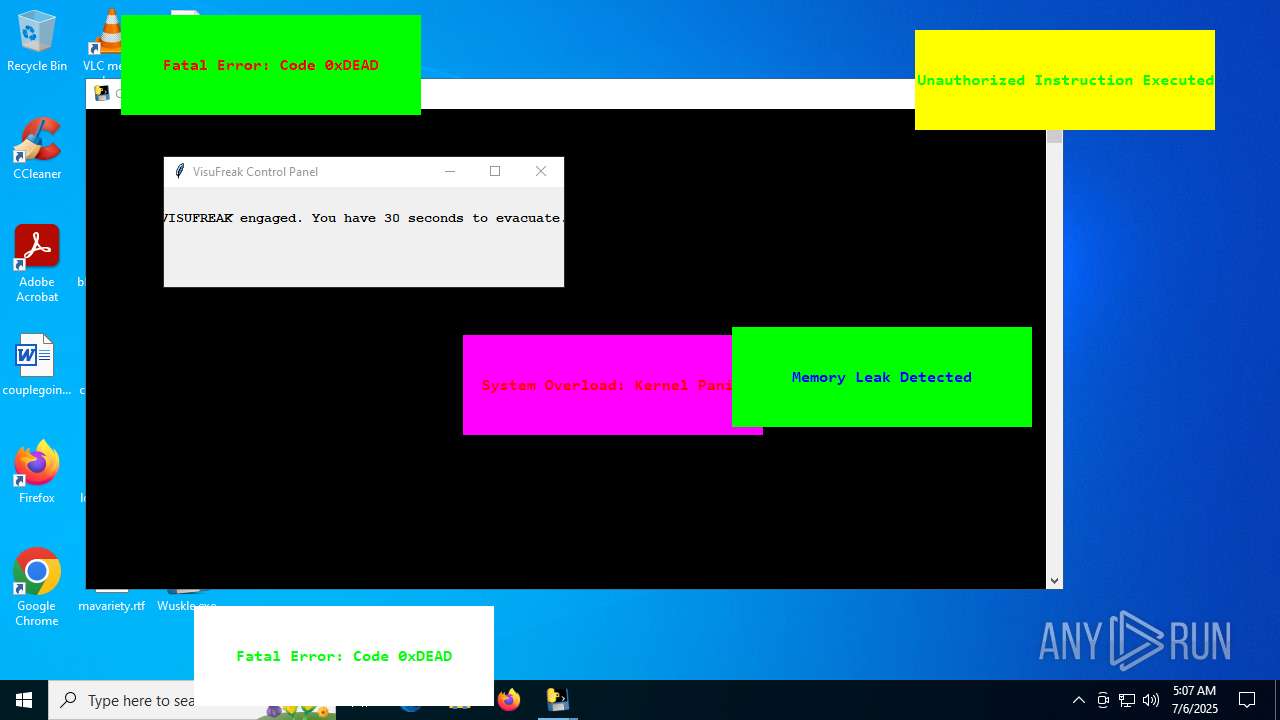
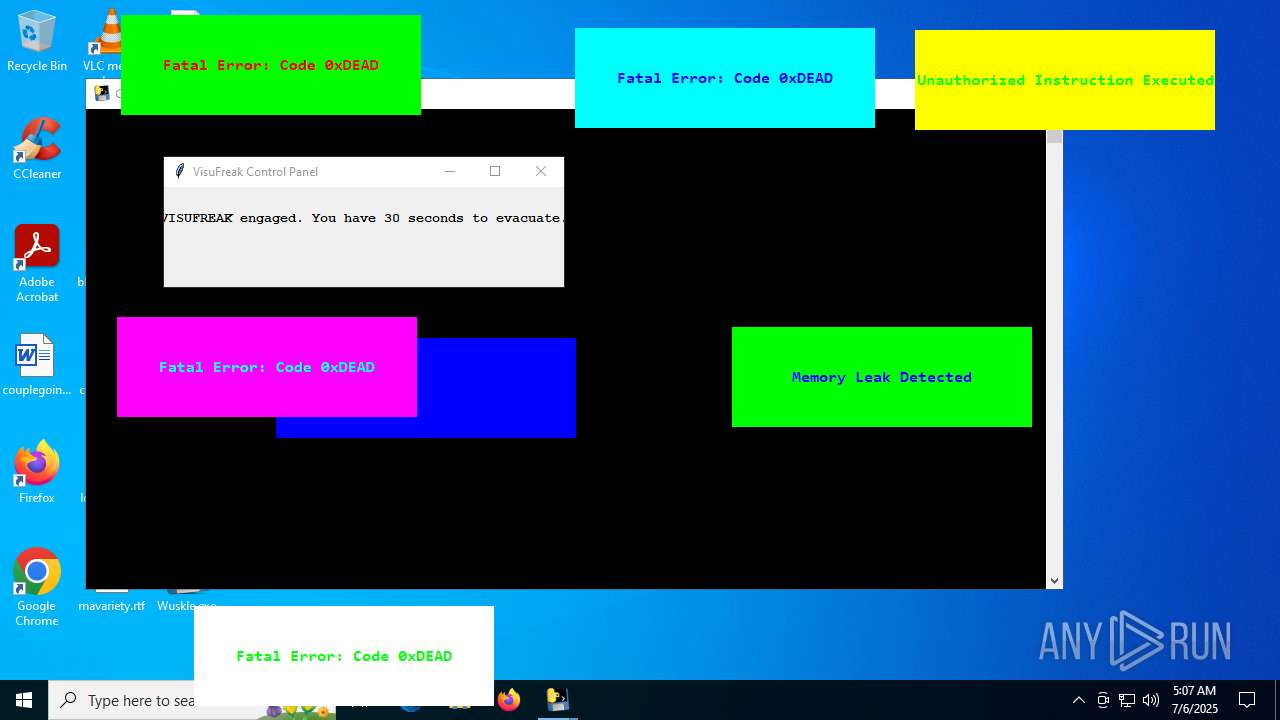
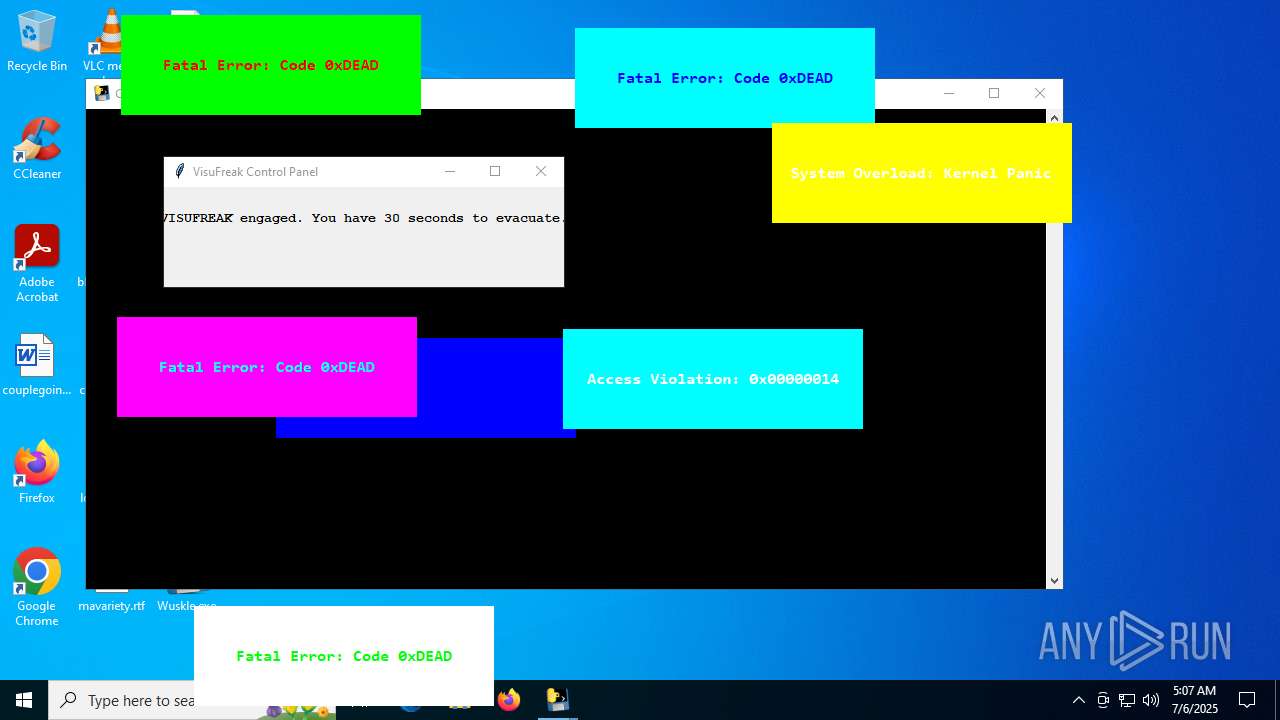
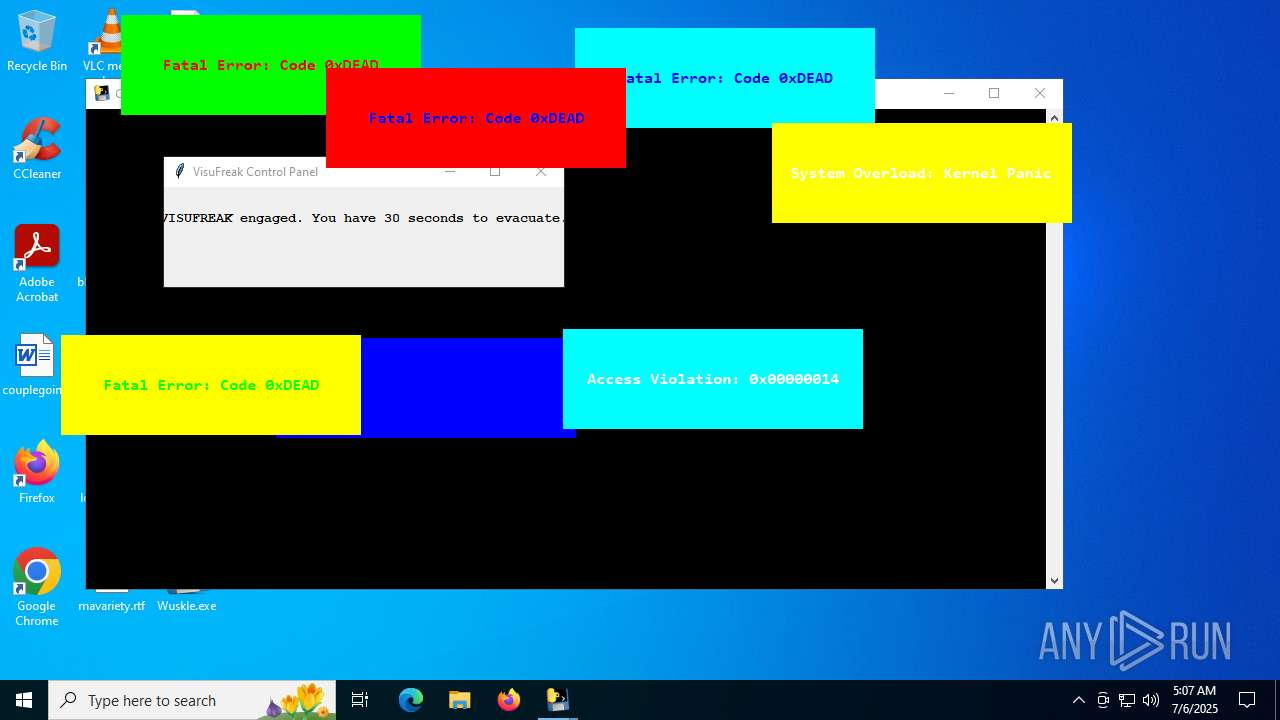
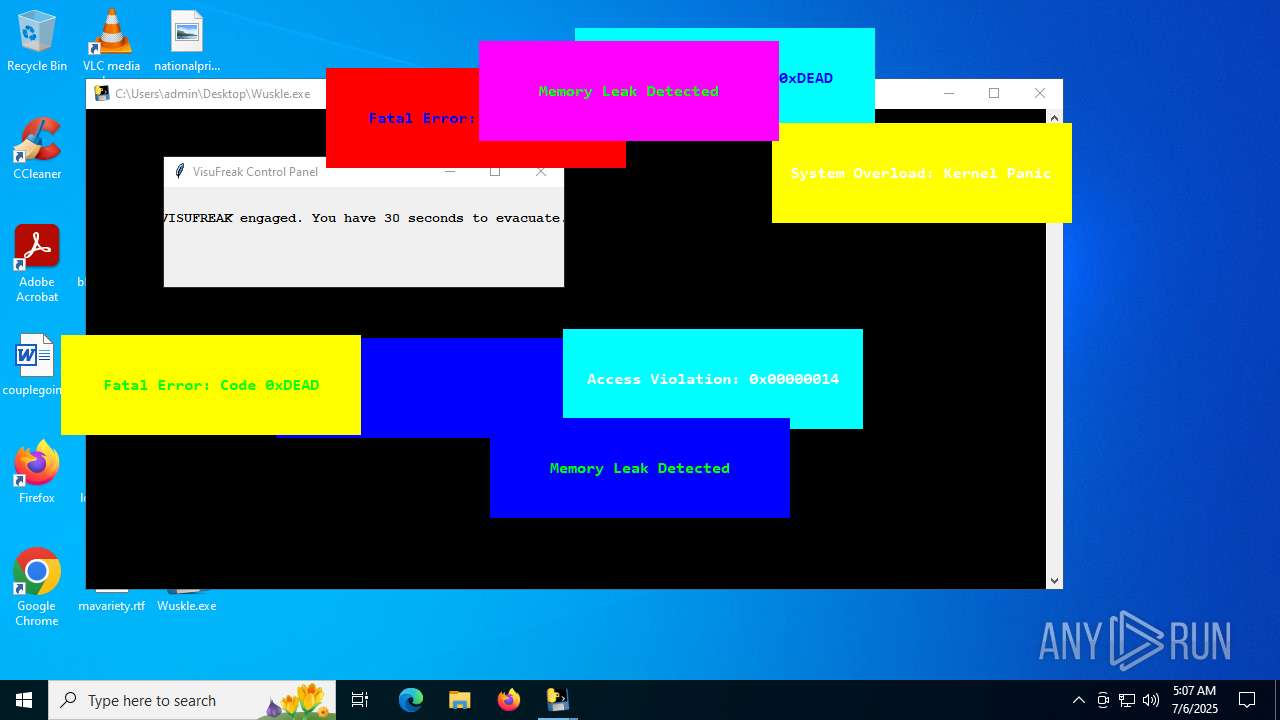
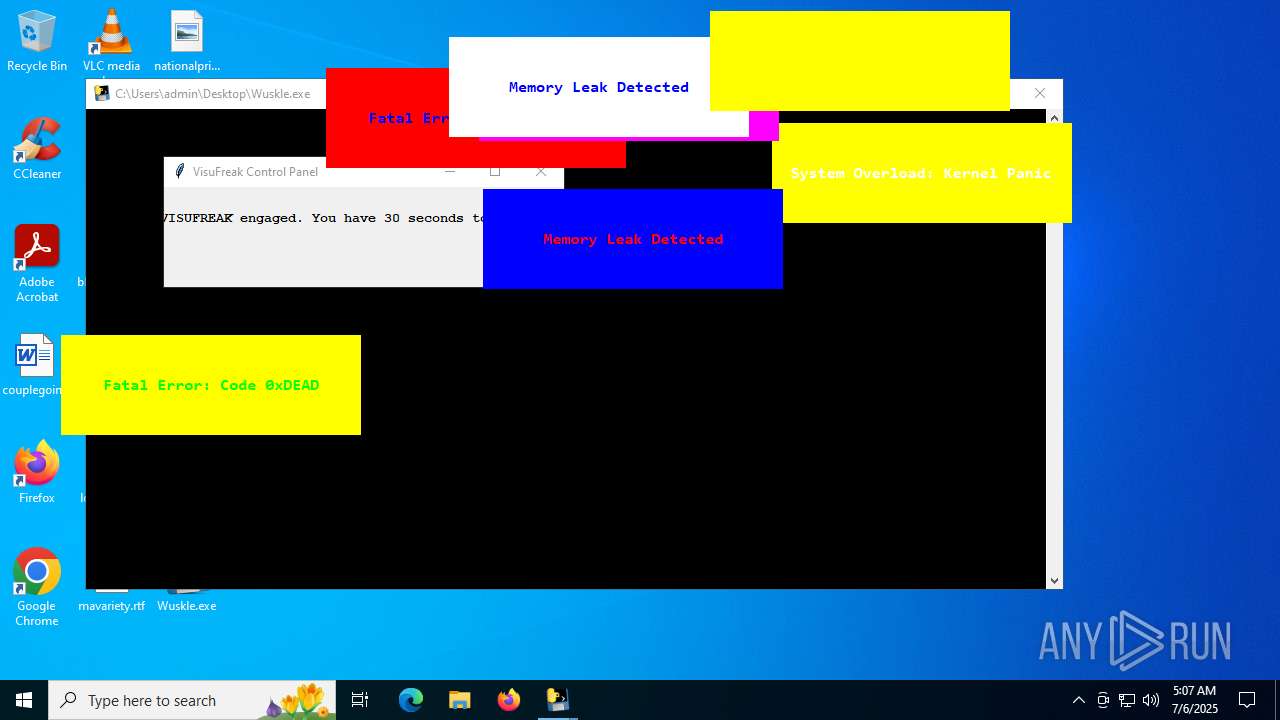
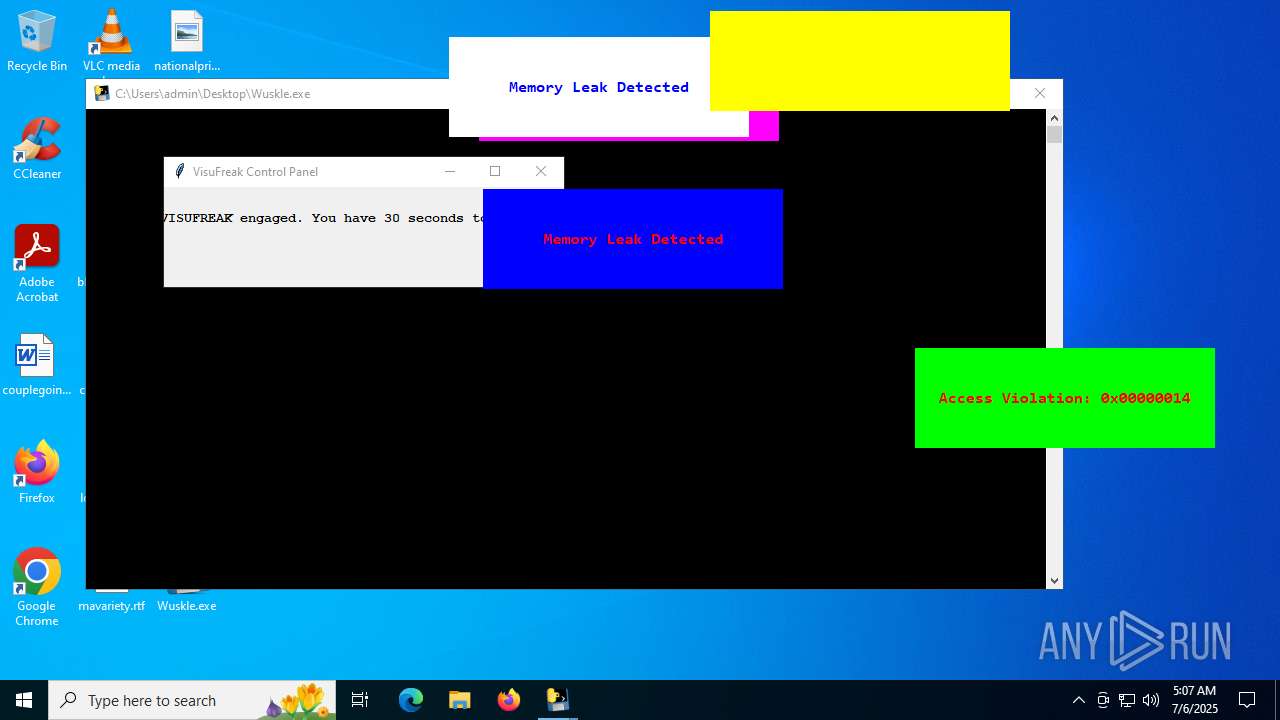
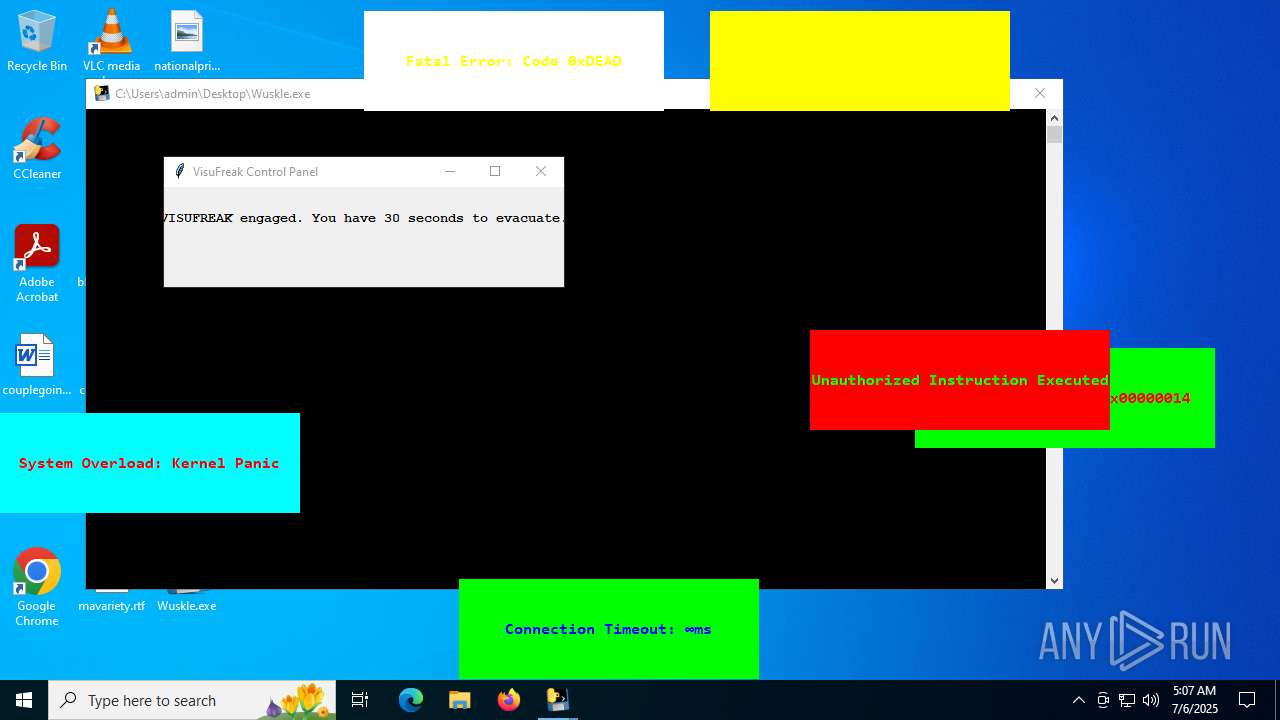
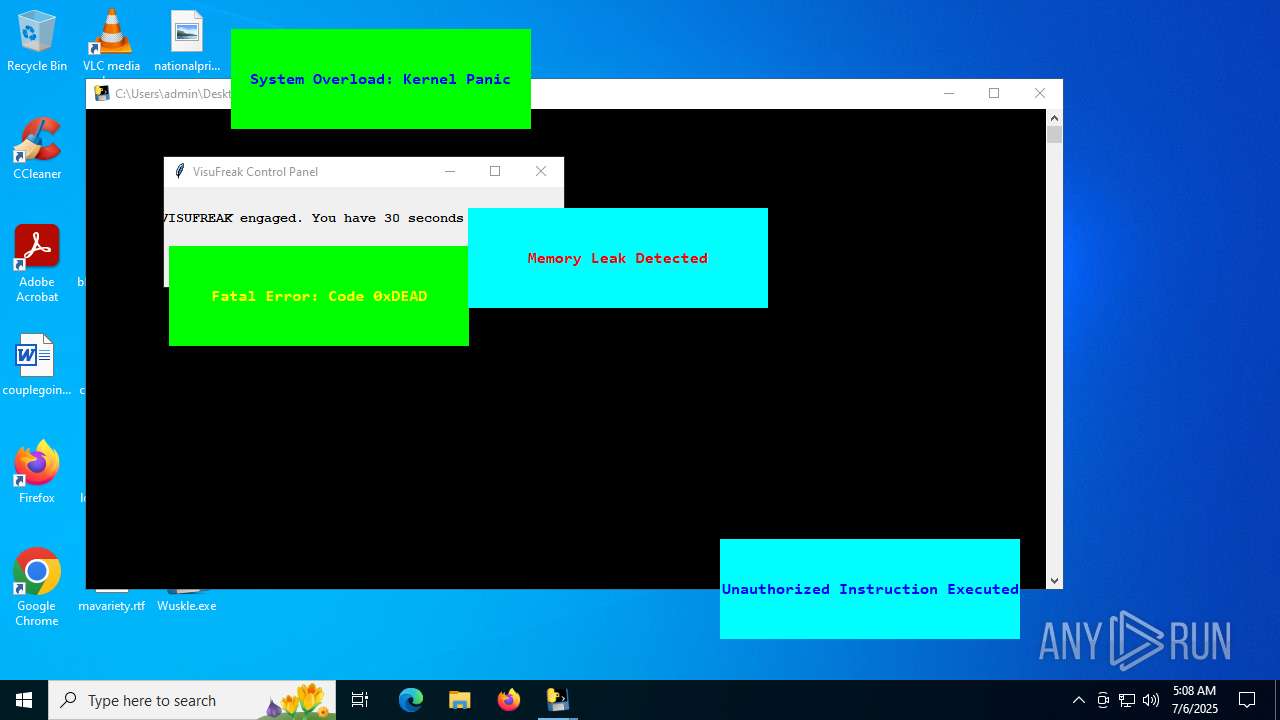
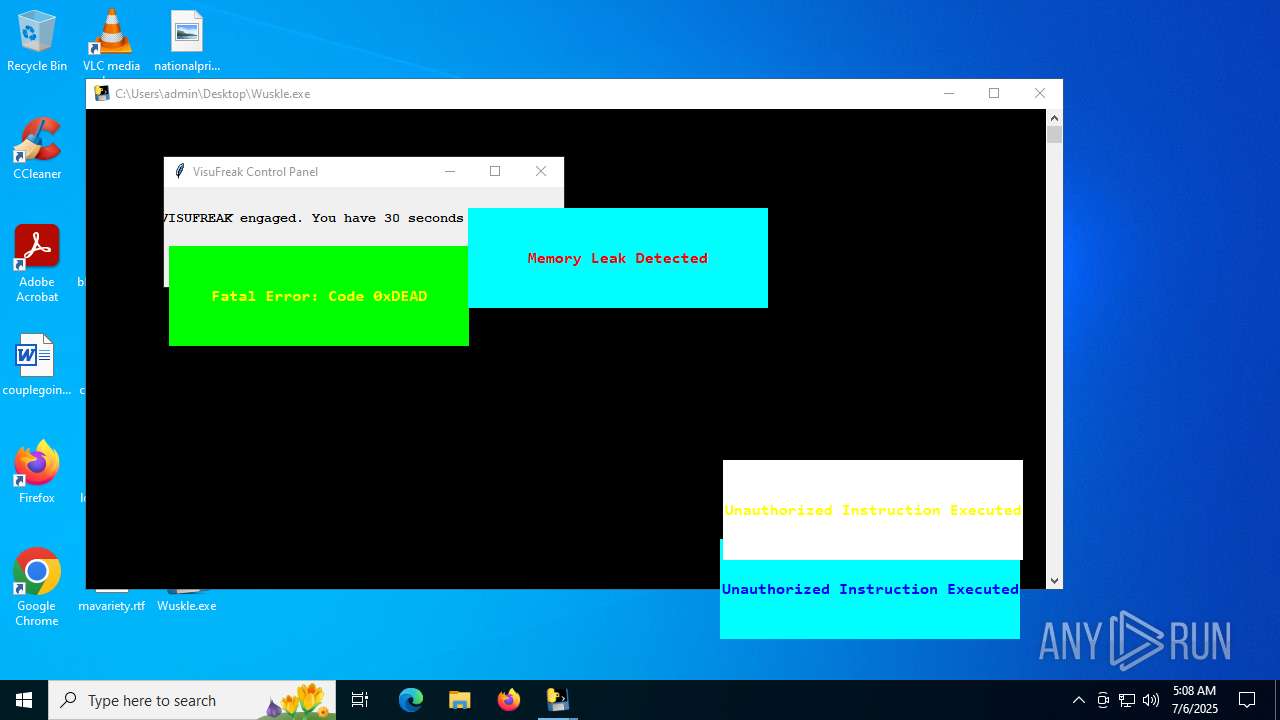
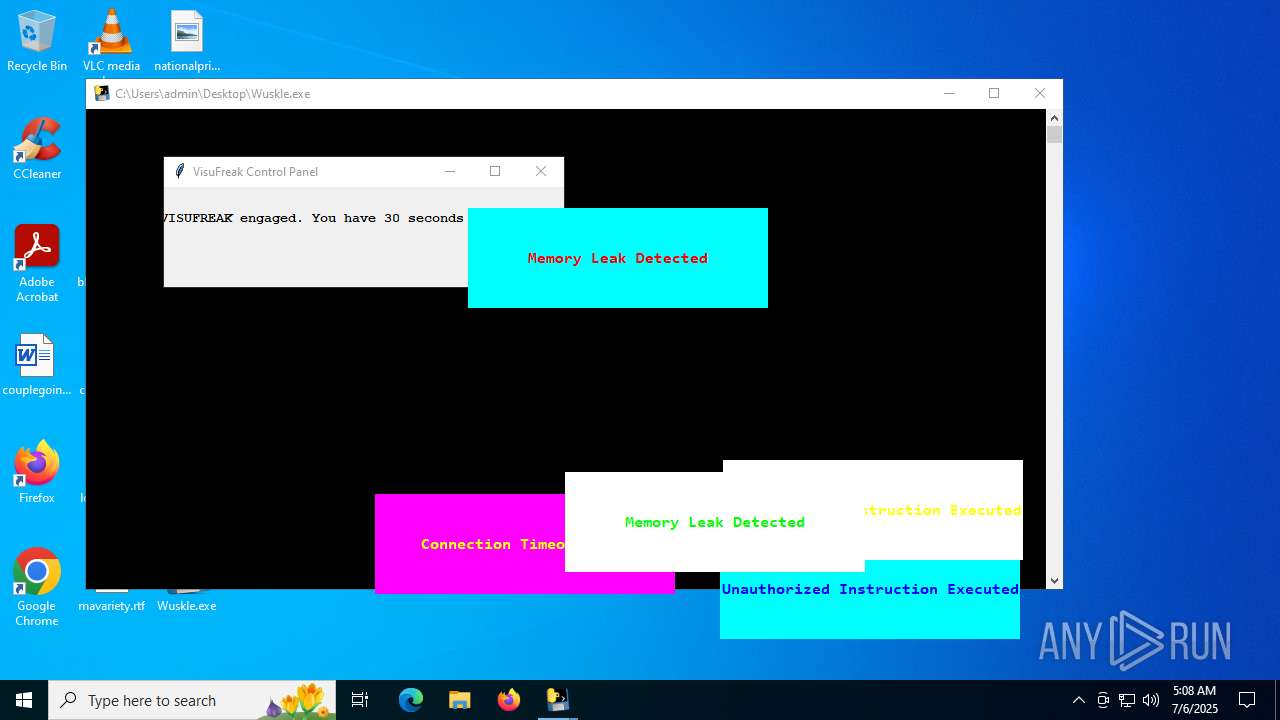
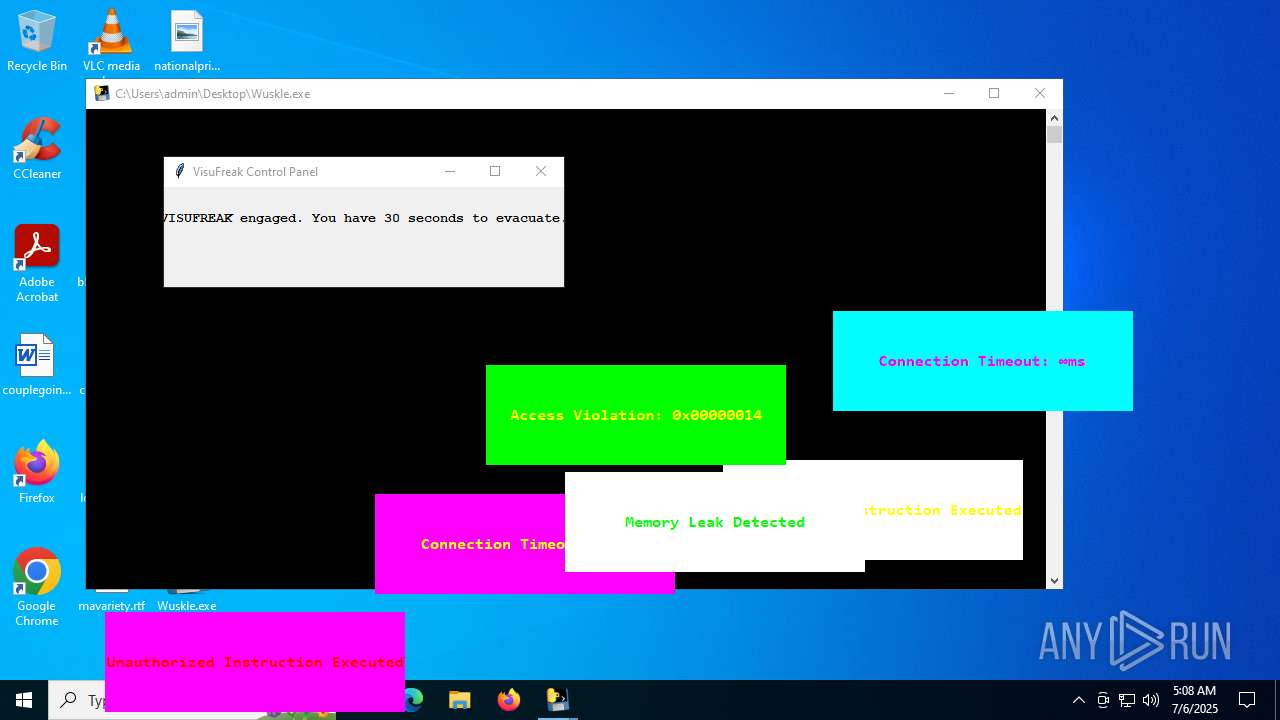
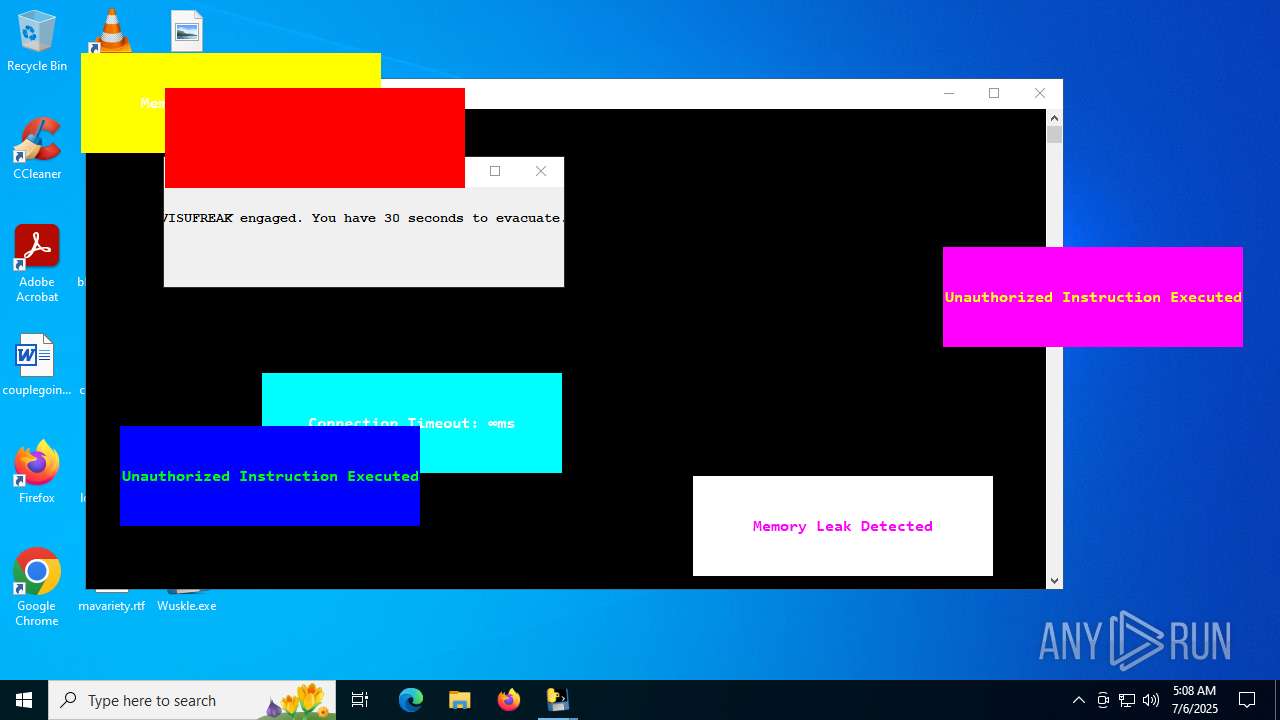
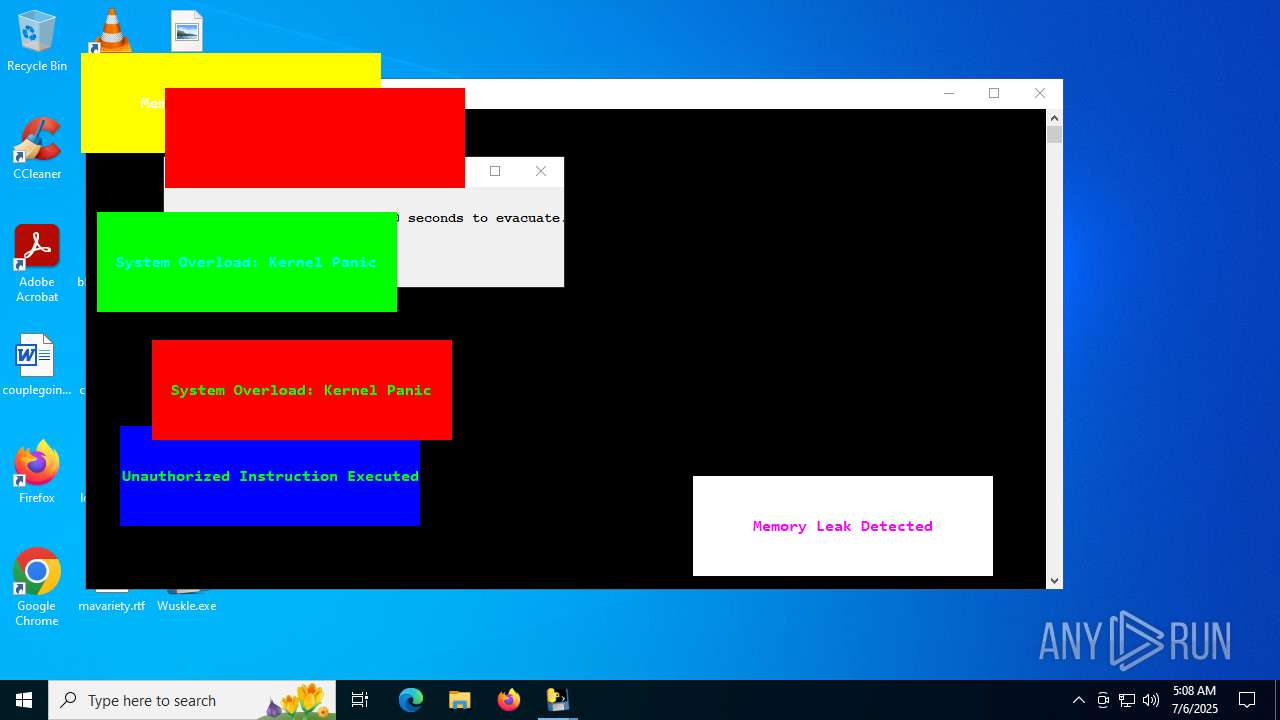
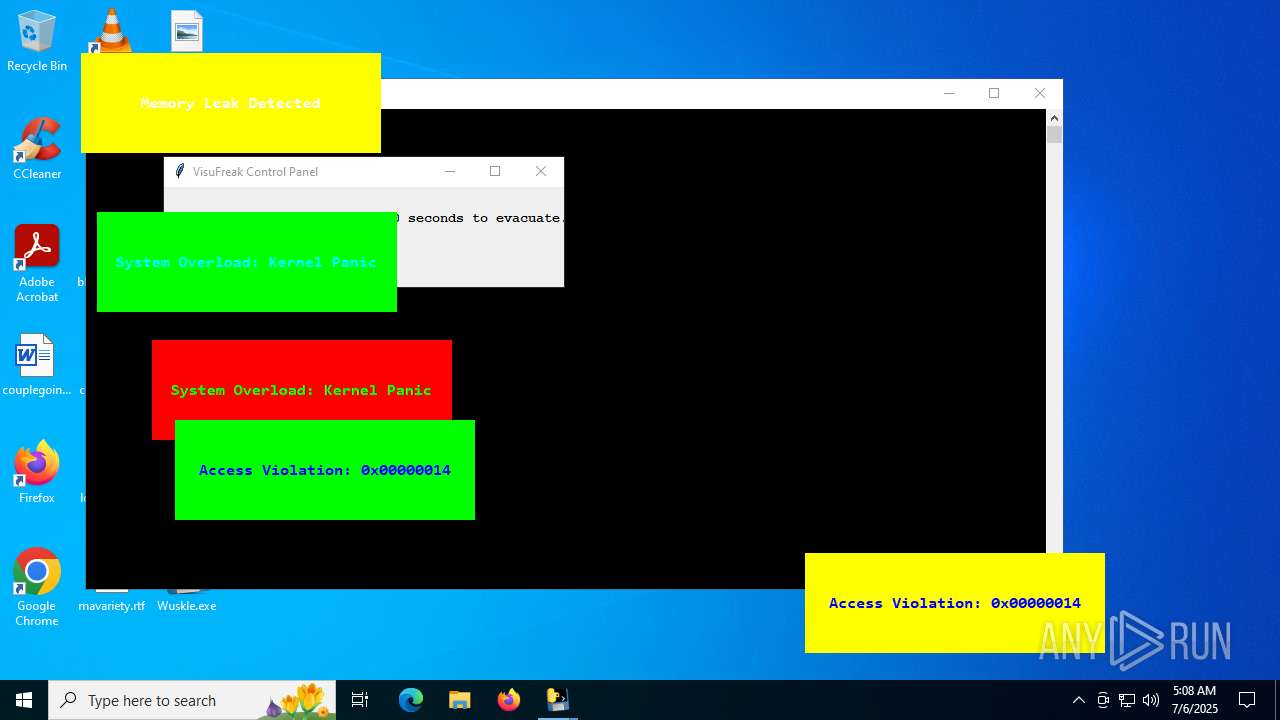
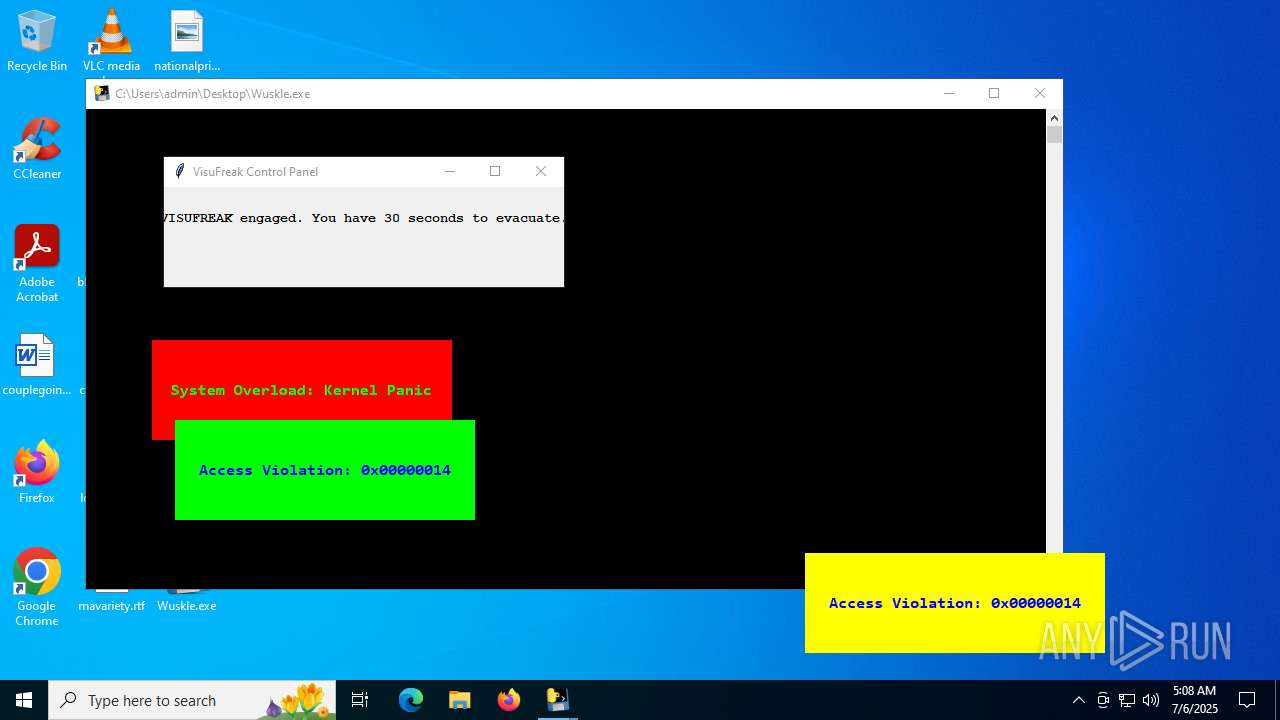
| File name: | Wuskle.exe |
| Full analysis: | https://app.any.run/tasks/0e894bfc-52d7-4a46-9e65-46d56ea1e803 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2025, 05:07:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | A8074C5466513535C1AE10911828B305 |
| SHA1: | E64C758B77F114688732DC5244F196B8F6B222F5 |
| SHA256: | F73F453F23D6DBBC3160697AC7DEF7928518EDF85803CE9CB3293790B19FB2B5 |
| SSDEEP: | 98304:YD/lTFQvqeLnc1ZaDPHUFK/uXbQx2UQmgyvOYVAYwVf9TtYw9pk9dbX3pI30iLVk:kLKVh2TaMHrOTyMNUfkGrCKv7AW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- Wuskle.exe (PID: 2324)
Application launched itself
- Wuskle.exe (PID: 2324)
Process drops python dynamic module
- Wuskle.exe (PID: 2324)
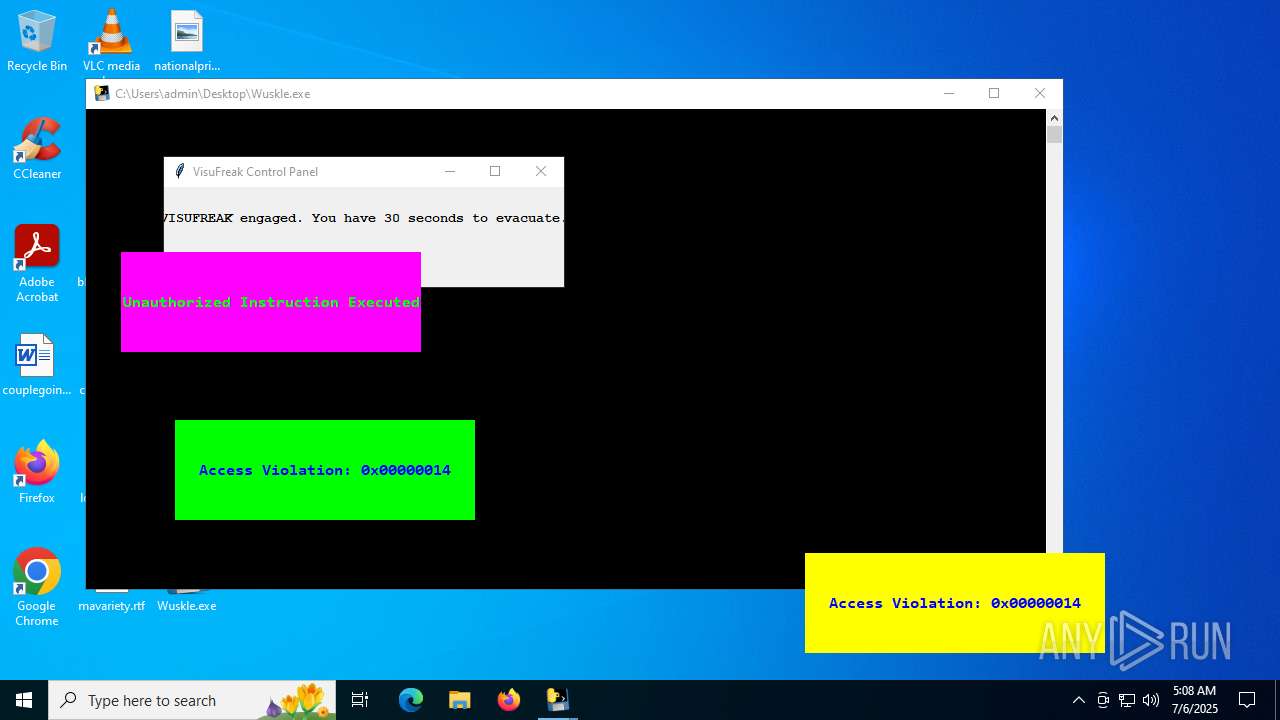
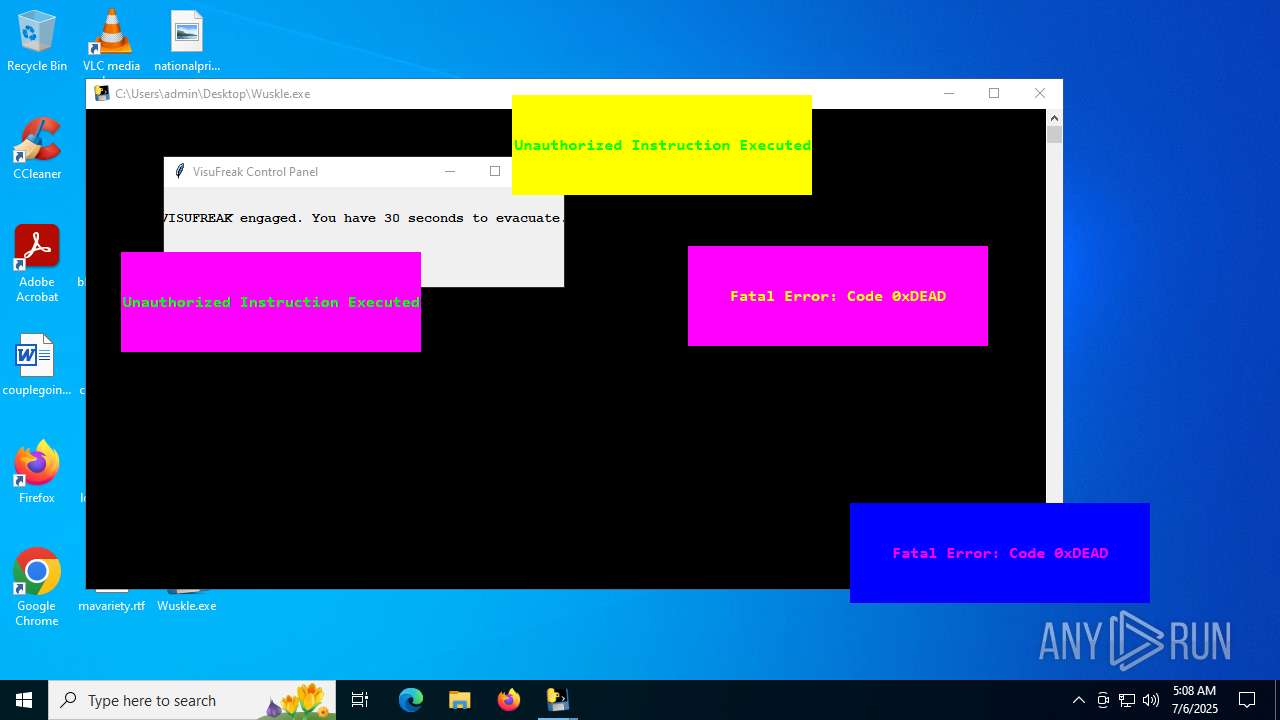
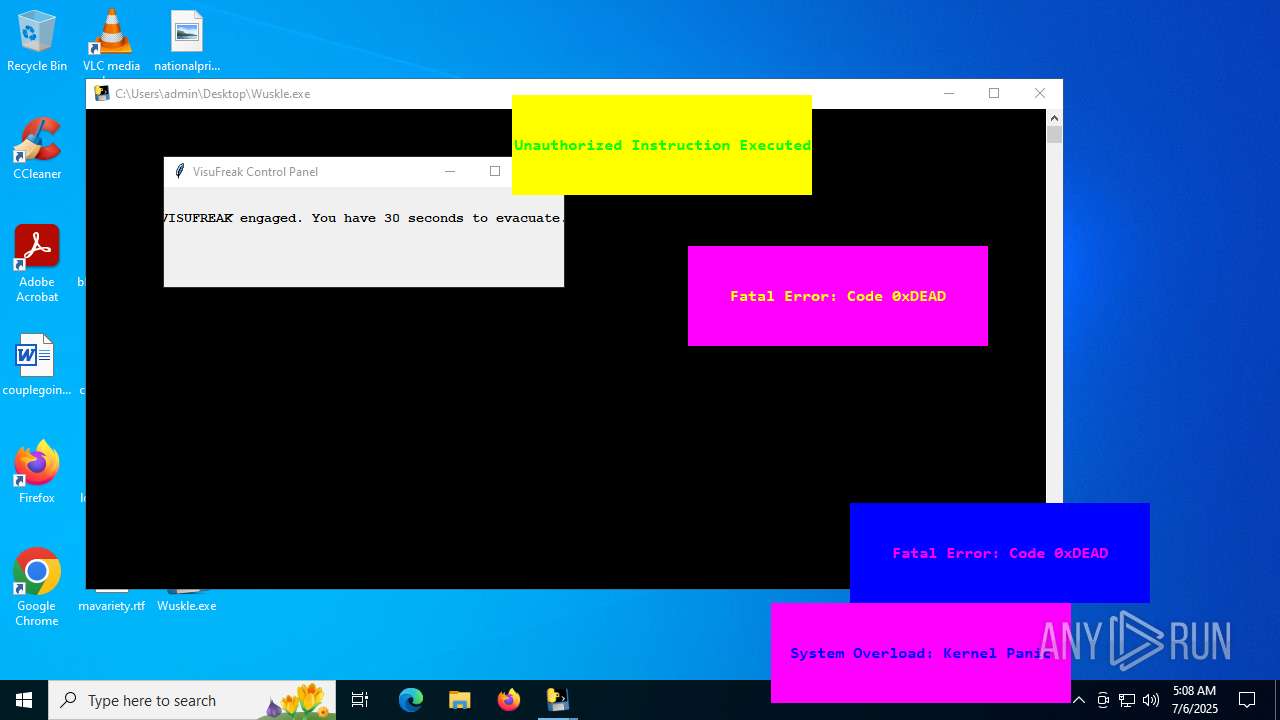
There is functionality for taking screenshot (YARA)
- Wuskle.exe (PID: 1812)
The process drops C-runtime libraries
- Wuskle.exe (PID: 2324)
Executable content was dropped or overwritten
- Wuskle.exe (PID: 2324)
Loads Python modules
- Wuskle.exe (PID: 1812)
INFO
PyInstaller has been detected (YARA)
- Wuskle.exe (PID: 2324)
- Wuskle.exe (PID: 1812)
The sample compiled with english language support
- Wuskle.exe (PID: 2324)
Reads the computer name
- Wuskle.exe (PID: 1812)
- Wuskle.exe (PID: 2324)
Reads the software policy settings
- slui.exe (PID: 5600)
Checks supported languages
- Wuskle.exe (PID: 1812)
- Wuskle.exe (PID: 2324)
Create files in a temporary directory
- Wuskle.exe (PID: 2324)
Checks proxy server information
- slui.exe (PID: 5600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:07:06 05:05:03+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 179712 |
| InitializedDataSize: | 155136 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc650 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
135
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1332 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Wuskle.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | "C:\Users\admin\Desktop\Wuskle.exe" | C:\Users\admin\Desktop\Wuskle.exe | — | Wuskle.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2324 | "C:\Users\admin\Desktop\Wuskle.exe" | C:\Users\admin\Desktop\Wuskle.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5600 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 764
Read events
3 764
Write events
0
Delete events
0
Modification events
Executable files
53
Suspicious files
3
Text files
924
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_hashlib.pyd | executable | |
MD5:CF4120BAD9A7F77993DD7A95568D83D7 | SHA256:14765E83996FE6D50AEDC11BB41D7C427A3E846A6A6293A4A46F7EA7E3F14148 | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_socket.pyd | executable | |
MD5:69C4A9A654CF6D1684B73A431949B333 | SHA256:8DAEFAFF53E6956F5AEA5279A7C71F17D8C63E2B0D54031C3B9E82FCB0FB84DB | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_tcl_data\auto.tcl | text | |
MD5:97EFA9EBE840EA051F9706504C8BD783 | SHA256:08113823951619D659EB03A1F6ACD2F9500E1264795219125A5DF7B83CABCB99 | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_tcl_data\encoding\cp1253.enc | text | |
MD5:441B86A0DE77F25C91DF1CD4685F651D | SHA256:5B8D47451F847C1BDE12CACA3739CA29860553C0B6399EE990D51B26F9A69722 | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_lzma.pyd | executable | |
MD5:3E73BC69EFB418E76D38BE5857A77027 | SHA256:6F48E7EBA363CB67F3465A6C91B5872454B44FC30B82710DFA4A4489270CE95C | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_tcl_data\encoding\cp1258.enc | text | |
MD5:12BCEAE6B6A5FAE5AE9C42F5998BA485 | SHA256:29D93DEE7C01B2264778BC6B75F6EF76EA6AC53E9F4A334D83707229E7F482D2 | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_tcl_data\encoding\cp1254.enc | text | |
MD5:5FA9162BEC5A4DEA97B5EA2840CFB065 | SHA256:31639CA96A4D3602D59BD012540FE179917E0561CB11A0D0B61F1B950EB76911 | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_tcl_data\encoding\cp1256.enc | text | |
MD5:D50DFAFEE5C605C5C00A25A9EEE4D4CF | SHA256:29340EA8E5AD3532BF67FA77CC852F055081B1238925CB109908AA72804CCC04 | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_tcl_data\encoding\ascii.enc | text | |
MD5:9E3A454FA480E9A99D2D5ACDAA775233 | SHA256:FB87BF197F4F485B08EA81F7534BC07D9C3A538D022424BE11011A1FE3C413FD | |||
| 2324 | Wuskle.exe | C:\Users\admin\AppData\Local\Temp\_MEI23242\_tcl_data\encoding\cp1257.enc | text | |
MD5:CC3D24543FDD4644BBBD4AAB30CA71BC | SHA256:C15AB85438728BF2C60D72B1A66AF80E8B1CE3CF5EB08BA6421FF1B2F73ACDF4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4916 | RUXIMICS.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
4916 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4916 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4916 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4916 | RUXIMICS.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |