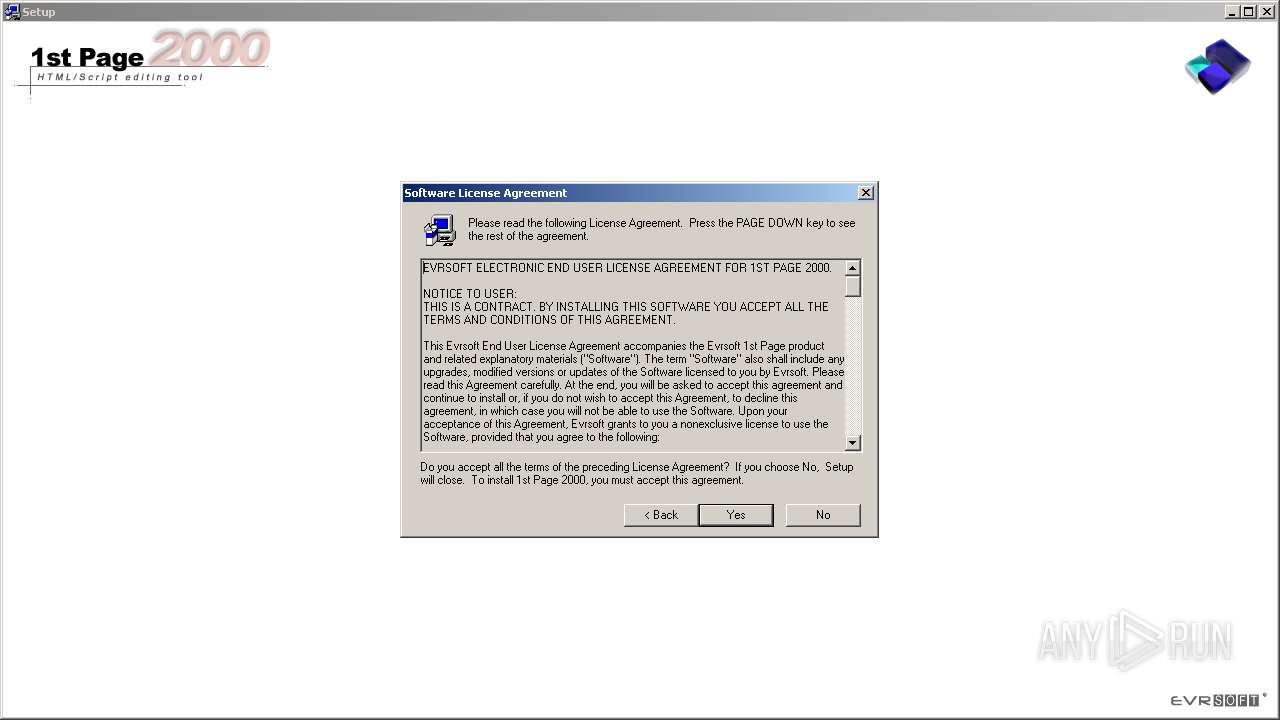
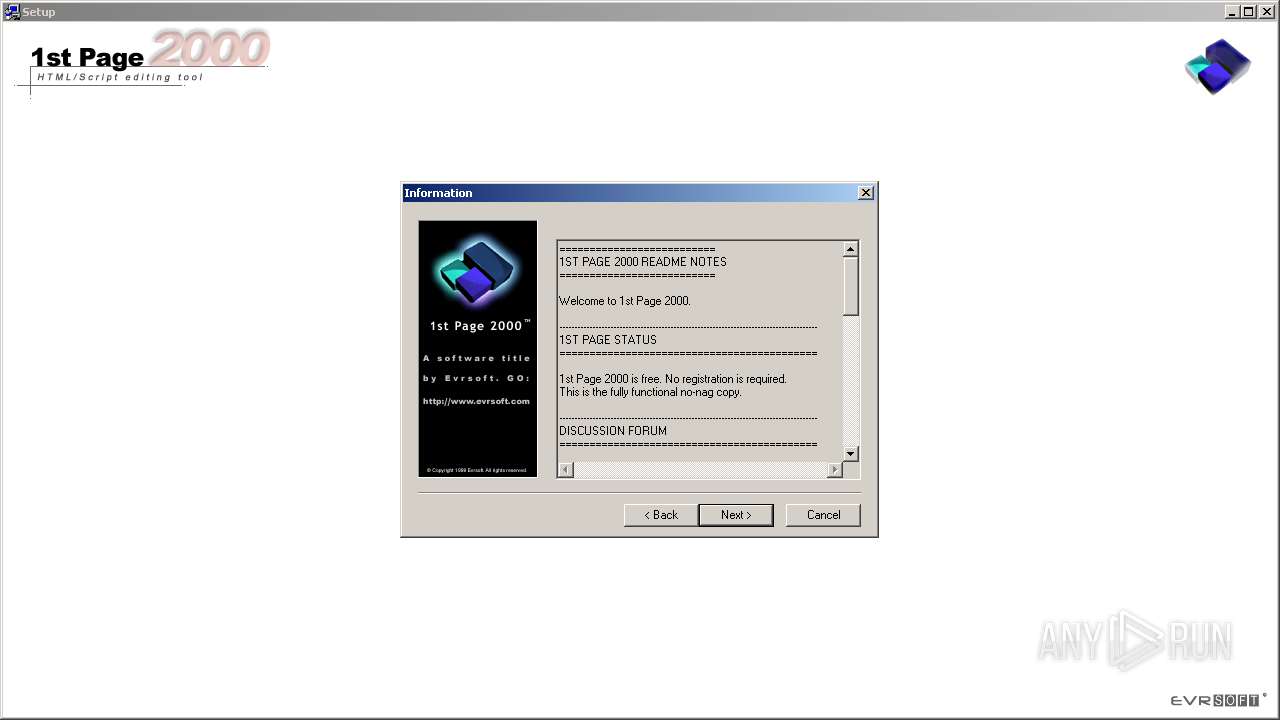
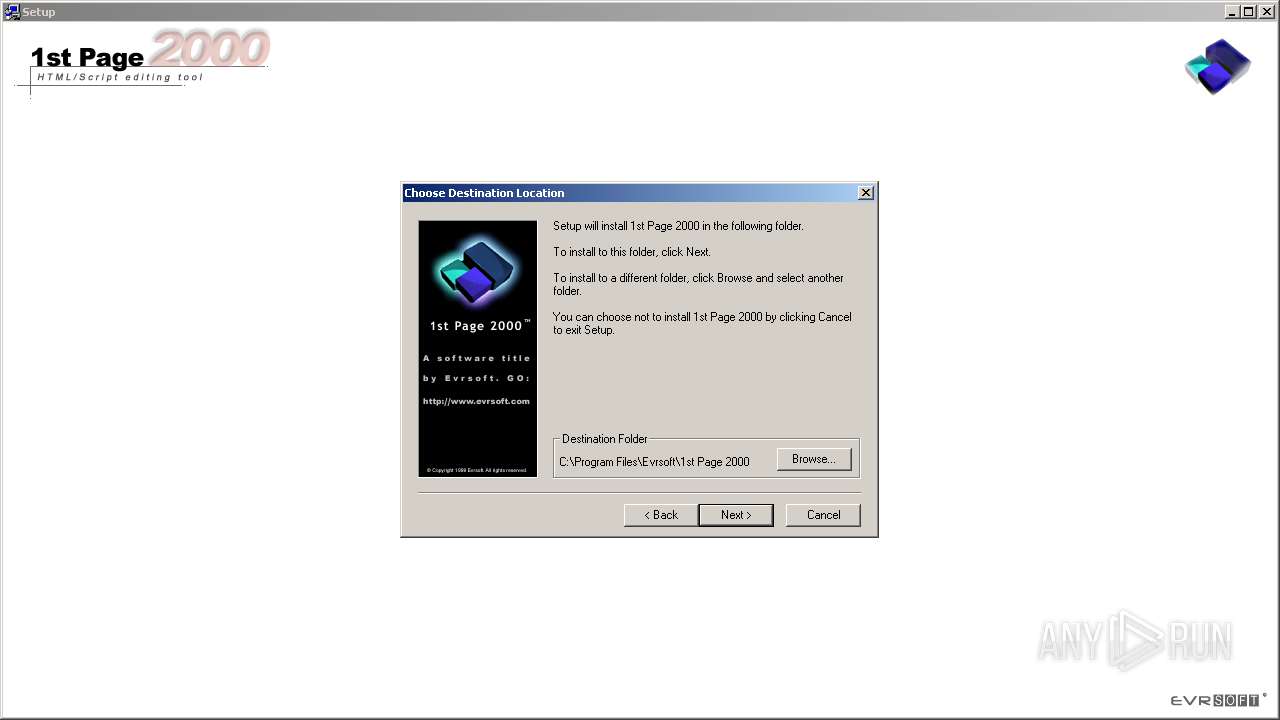
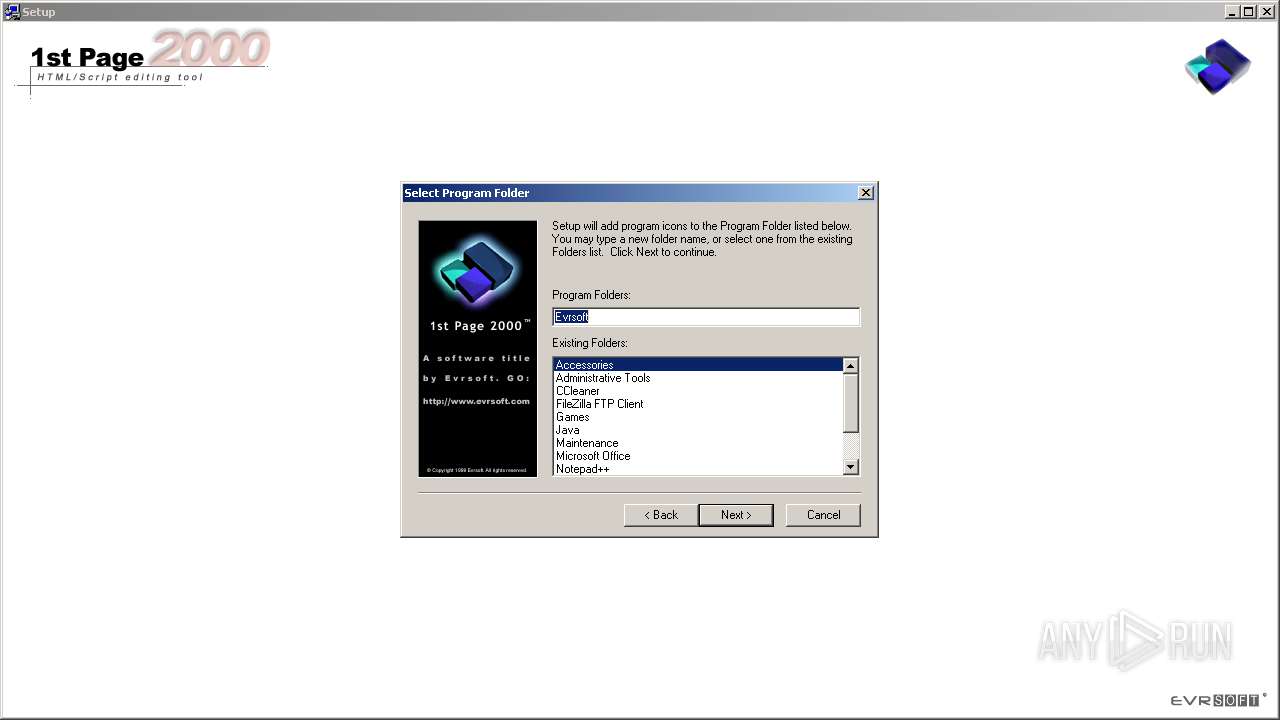
| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/9f164b8c-6e29-45f8-8874-4ccc9e27ce65 |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2024, 17:05:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive |
| MD5: | BC7DF98E1993DB13FBDC4EAD72295381 |
| SHA1: | D6CDF733CAE488C6D97C48C46FAB9C901A170F00 |
| SHA256: | F729B2B41C59FBBE89D62B1E654D10C97E32772E432594AF0AE52B062853C116 |
| SSDEEP: | 98304:TCeKV1dqumjdo9J6w8x+sVIRnuh/l1ZLQWcs0mQ8FpEDeoFYEoajPlvFRJr1rmlk:xn7nGsS70wT3 |
MALICIOUS
Drops the executable file immediately after the start
- setup.exe (PID: 4092)
- _INS5176._MP (PID: 2032)
Creates a writable file in the system directory
- _INS5176._MP (PID: 2032)
SUSPICIOUS
Process drops legitimate windows executable
- _INS5176._MP (PID: 2032)
Starts application with an unusual extension
- ntvdm.exe (PID: 2204)
Executable content was dropped or overwritten
- setup.exe (PID: 4092)
- ntvdm.exe (PID: 2204)
- _INS5176._MP (PID: 2032)
Reads the Windows owner or organization settings
- _INS5176._MP (PID: 2032)
INFO
Checks supported languages
- setup.exe (PID: 4092)
- _INS5176._MP (PID: 2032)
- 1stPage.exe (PID: 2768)
Create files in a temporary directory
- ntvdm.exe (PID: 2204)
- setup.exe (PID: 4092)
- _INS5176._MP (PID: 2032)
Reads the computer name
- _INS5176._MP (PID: 2032)
- 1stPage.exe (PID: 2768)
Drops the executable file immediately after the start
- ntvdm.exe (PID: 2204)
Manual execution by a user
- 1stPage.exe (PID: 2768)
Creates files in the program directory
- _INS5176._MP (PID: 2032)
Reads the machine GUID from the registry
- 1stPage.exe (PID: 2768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ 4.x (53) |
|---|---|---|
| .exe | | | InstallShield setup (16.9) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (12.2) |
| .exe | | | Win64 Executable (generic) (10.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1998:03:26 15:31:20+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 69120 |
| InitializedDataSize: | 75776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc110 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.5.0 |
| ProductVersionNumber: | 2.1.5.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | InstallShield Software Corporation |
| FileDescription: | PackageForTheWeb Stub |
| FileVersion: | 2.02.001 |
| InternalName: | STUB.EXE |
| LegalCopyright: | Copyright © 1996 InstallShield Software Corporation |
| OriginalFileName: | STUB32.EXE |
| ProductName: | PackageForTheWeb Stub |
| ProductVersion: | 2.02.001 |
Total processes
44
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | — | explorer.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: MEDIUM Description: PackageForTheWeb Stub Exit code: 3221226540 Version: 2.02.001 Modules
| |||||||||||||||
| 2032 | C:\Users\admin\AppData\Local\Temp\_INS5176._MP | C:\Users\admin\AppData\Local\Temp\_INS5176._MP | ntvdm.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield Engine Exit code: 0 Version: 5.10.145.0 Modules
| |||||||||||||||
| 2204 | "C:\Windows\system32\ntvdm.exe" -i1 -ws | C:\Windows\System32\ntvdm.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2768 | "C:\Program Files\Evrsoft\1st Page 2000\1stPage.exe" | C:\Program Files\Evrsoft\1st Page 2000\1stPage.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4092 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | explorer.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: PackageForTheWeb Stub Exit code: 0 Version: 2.02.001 Modules
| |||||||||||||||
Total events
822
Read events
822
Write events
0
Delete events
0
Modification events
Executable files
27
Suspicious files
20
Text files
915
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\pftw1.pkg | — | |
MD5:— | SHA256:— | |||
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\data1.cab | — | |
MD5:— | SHA256:— | |||
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\_ISDEL.EXE | executable | |
MD5:1F9BBFAAB8DEC9AC4416E5BE2D22E315 | SHA256:DAD294B71F24B1EB140D3536AB7ABD0336977FE92A18BE38ABE4F1A5BE91939A | |||
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\os.dat | text | |
MD5:AF1D8D9435CB10FE2F4B4215EAF6BEC4 | SHA256:2F148CB3D32AB70A315B5A853761C2702B6DEEF6FFAFF6AA76D513B945CE7EF7 | |||
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\SETUP.EXE | executable | |
MD5:AFE10D250B2C1850B37827C1D4E01EEF | SHA256:26ADEA53490125FD31E300DA97EF48B9DDC583753789051746B9A31406B418CF | |||
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\_sys1.cab | compressed | |
MD5:AA384718B3DE6D9F312F8A260F86B155 | SHA256:6EA5629A4C6E9FC7224D0B53CFFB5B9CE71618649F9E5AAA22ECC90735C5A038 | |||
| 2204 | ntvdm.exe | C:\Windows\_delis43.ini | text | |
MD5:09F15232D24969690451E3B826A45C9B | SHA256:0D87965B74FA6A57FE876567FD7B392105E2343AC1612E763D4CEBA5024D1E7E | |||
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\DATA.TAG | text | |
MD5:FE4D57D5392E7832ACA01C50DC7D15B3 | SHA256:2EABC3BEEA122FF93533CC263CC90D10622214F585EADFFBAA3F88CC64DDFA6A | |||
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\lang.dat | text | |
MD5:90E64689804B4F4B0197C07290965A3C | SHA256:EB1E8EA9707BC2F6EB4B4CC4D022E6ACF0B79E0C66F8406478269EEAB05693B8 | |||
| 4092 | setup.exe | C:\Users\admin\AppData\Local\Temp\pft36D4~tmp\_INST32I.EX_ | binary | |
MD5:4251C8E7962CE3CA98FDCBE096C1D270 | SHA256:065443568C396564EC51C72F54F81990C49E4B0CECE780ACBFC6A7494B65A3E0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |