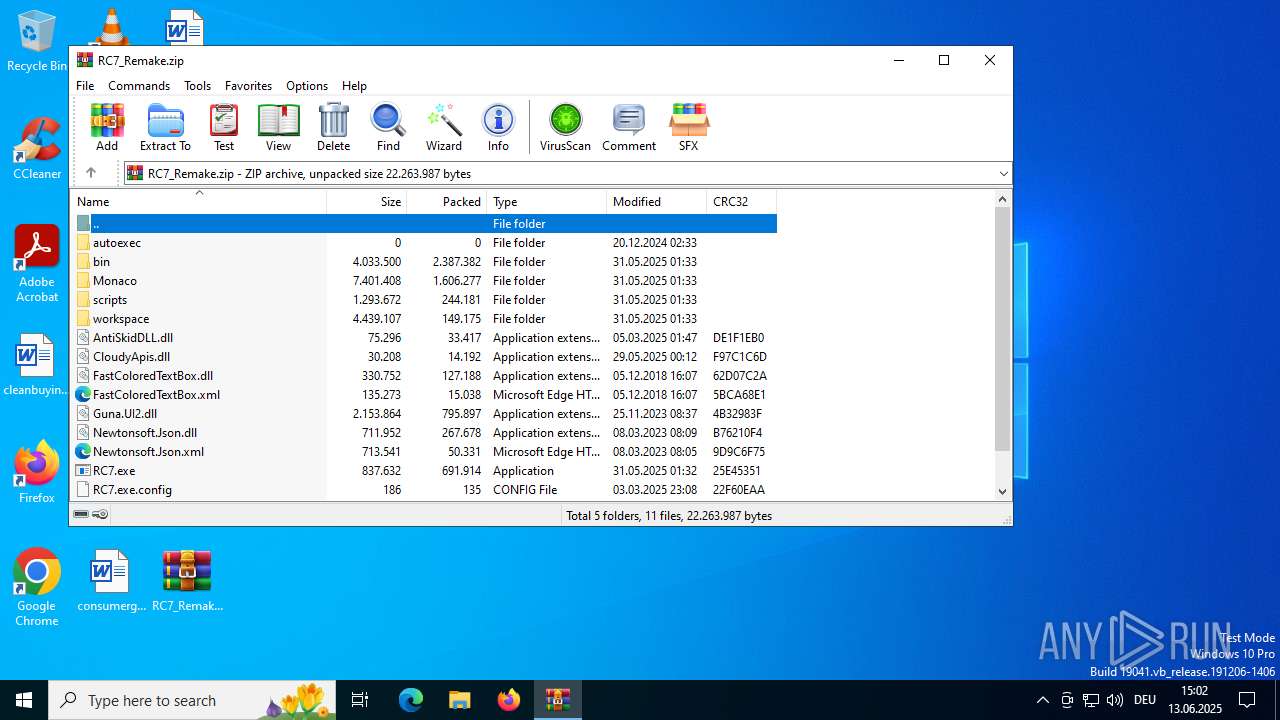
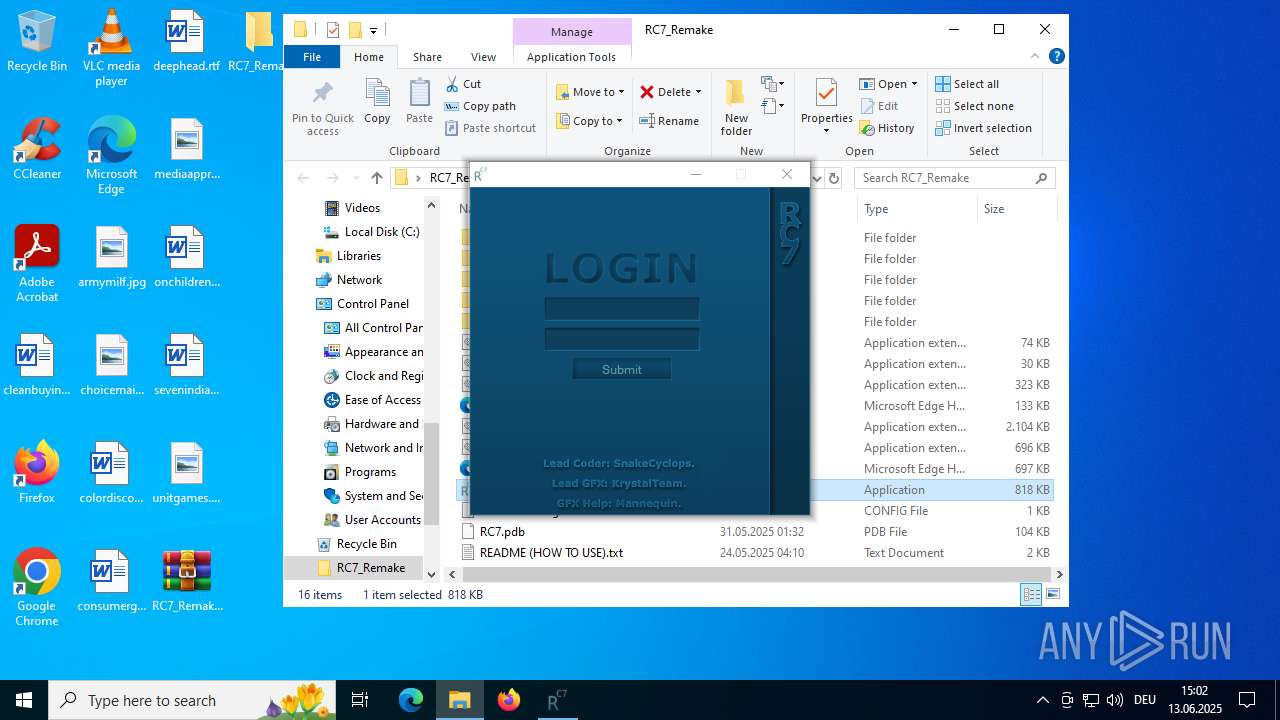
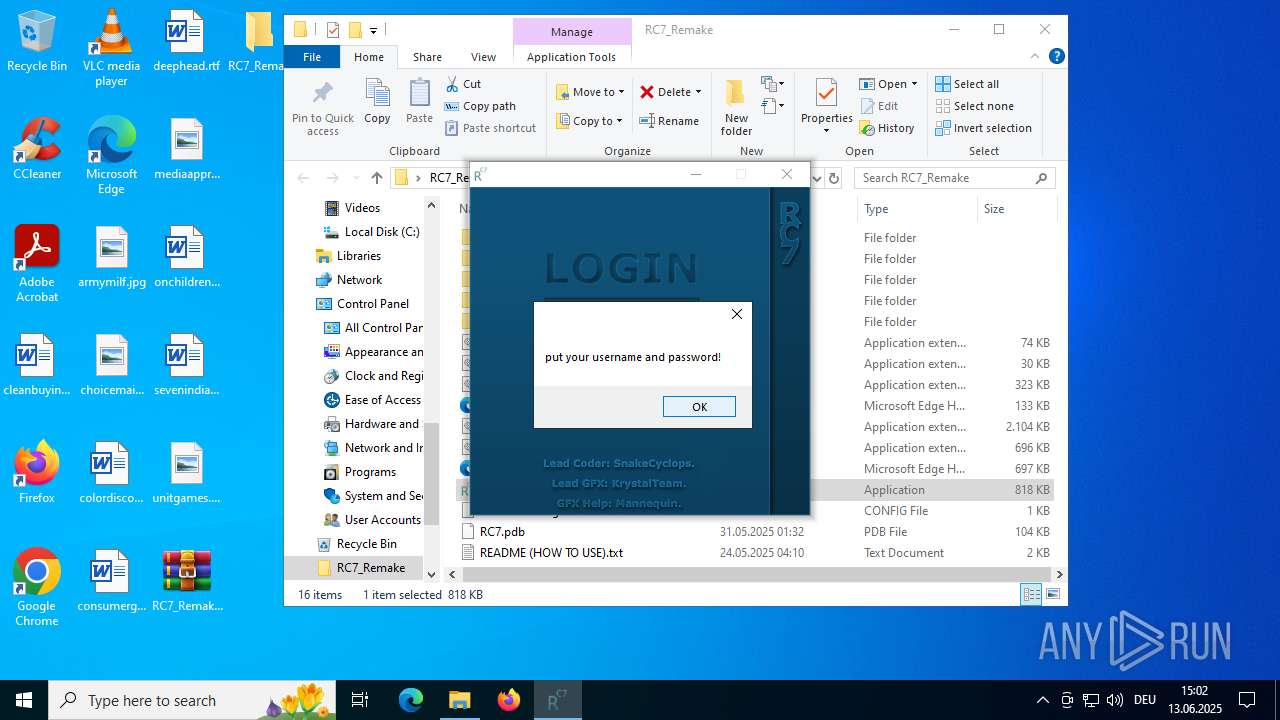
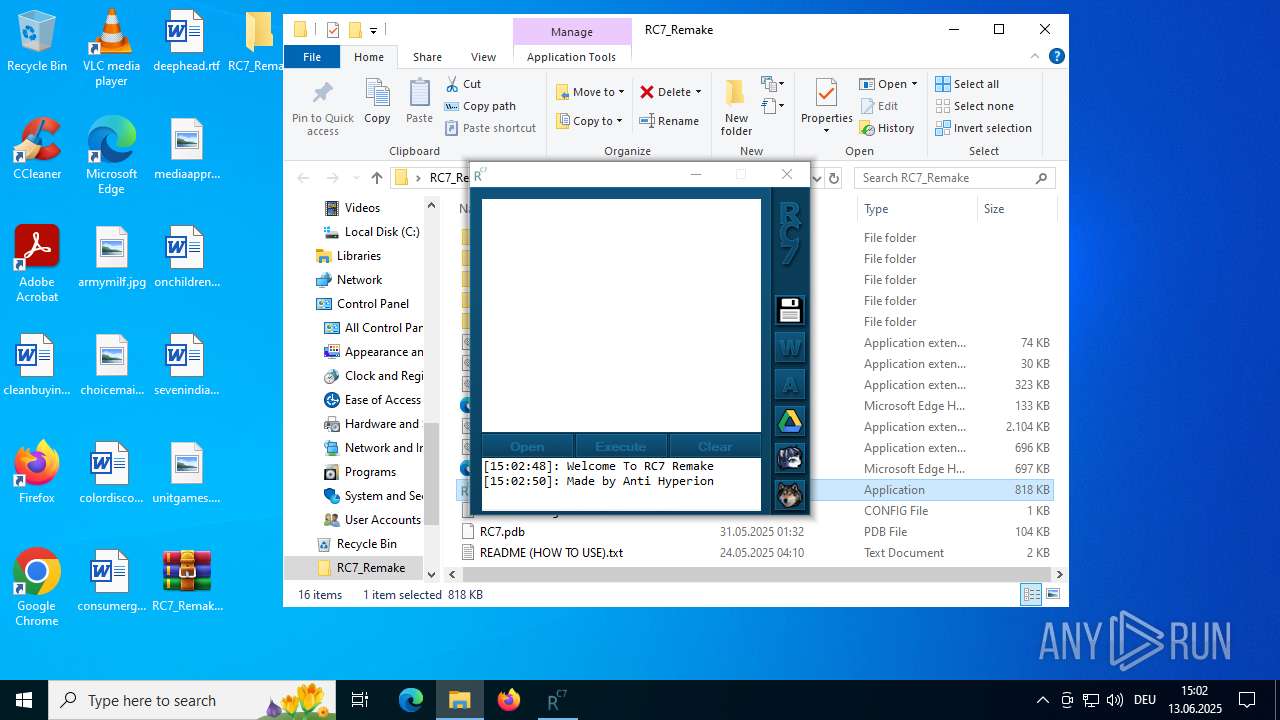
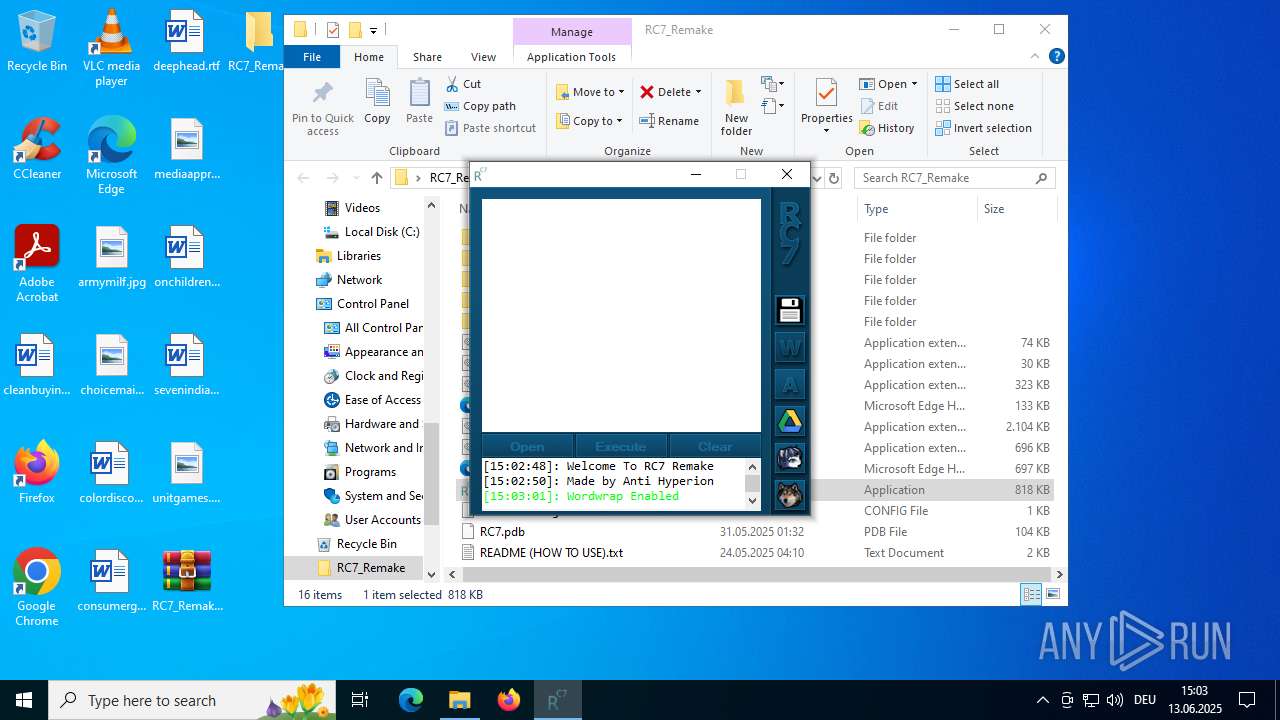
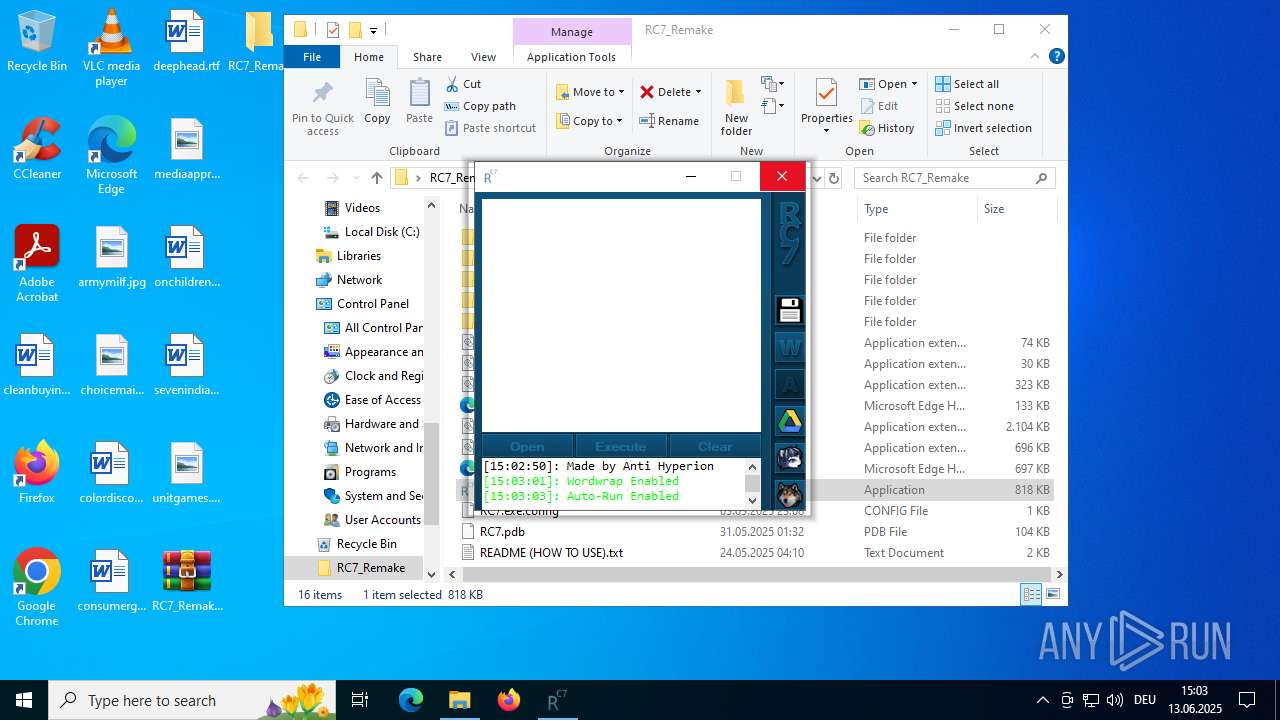
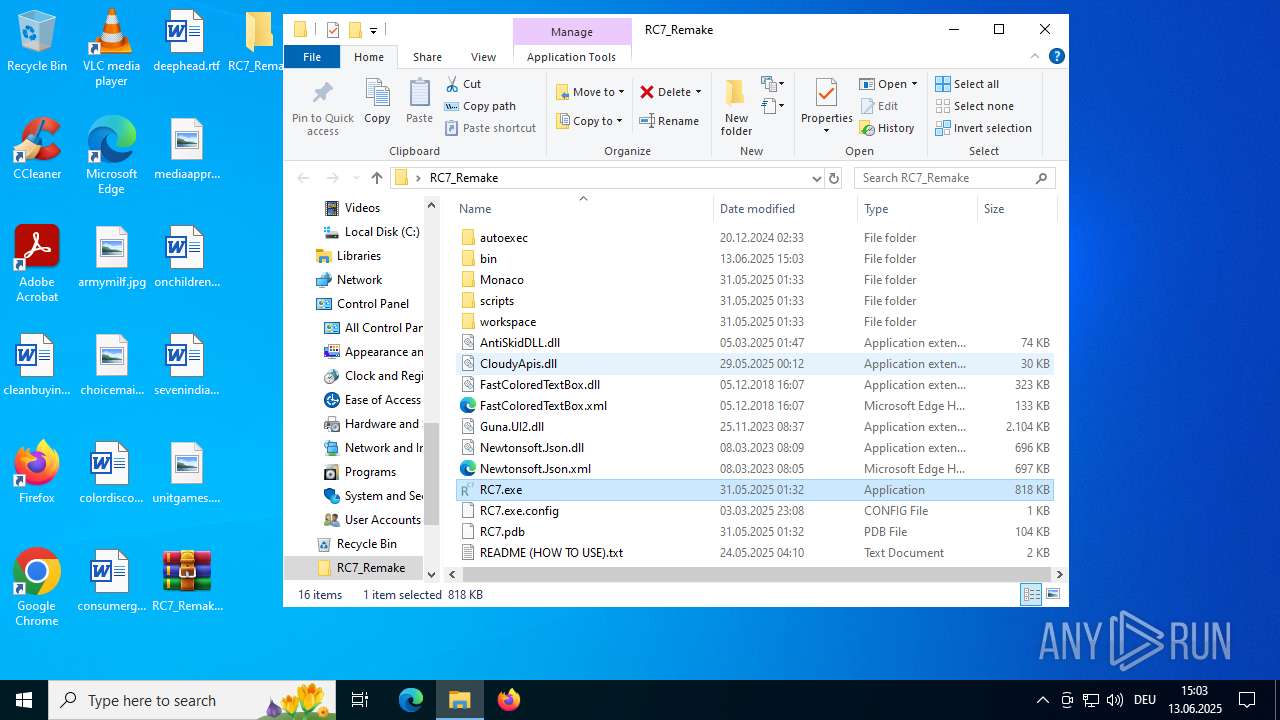
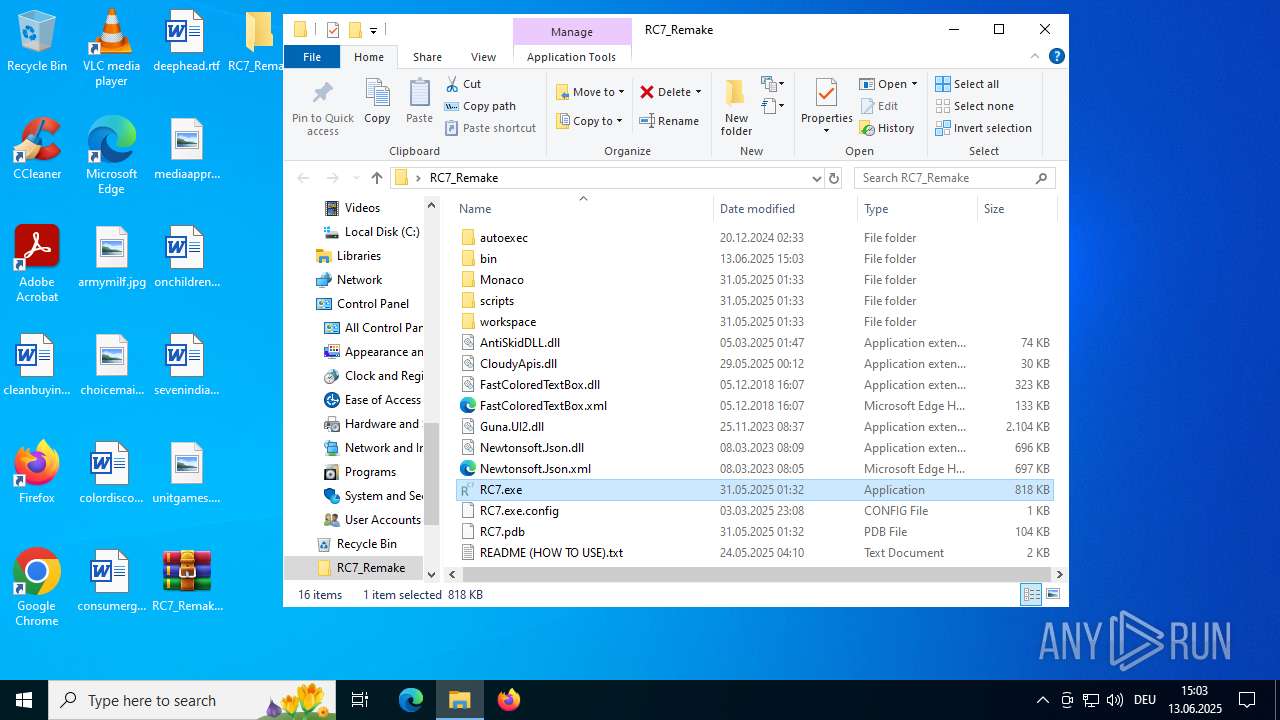
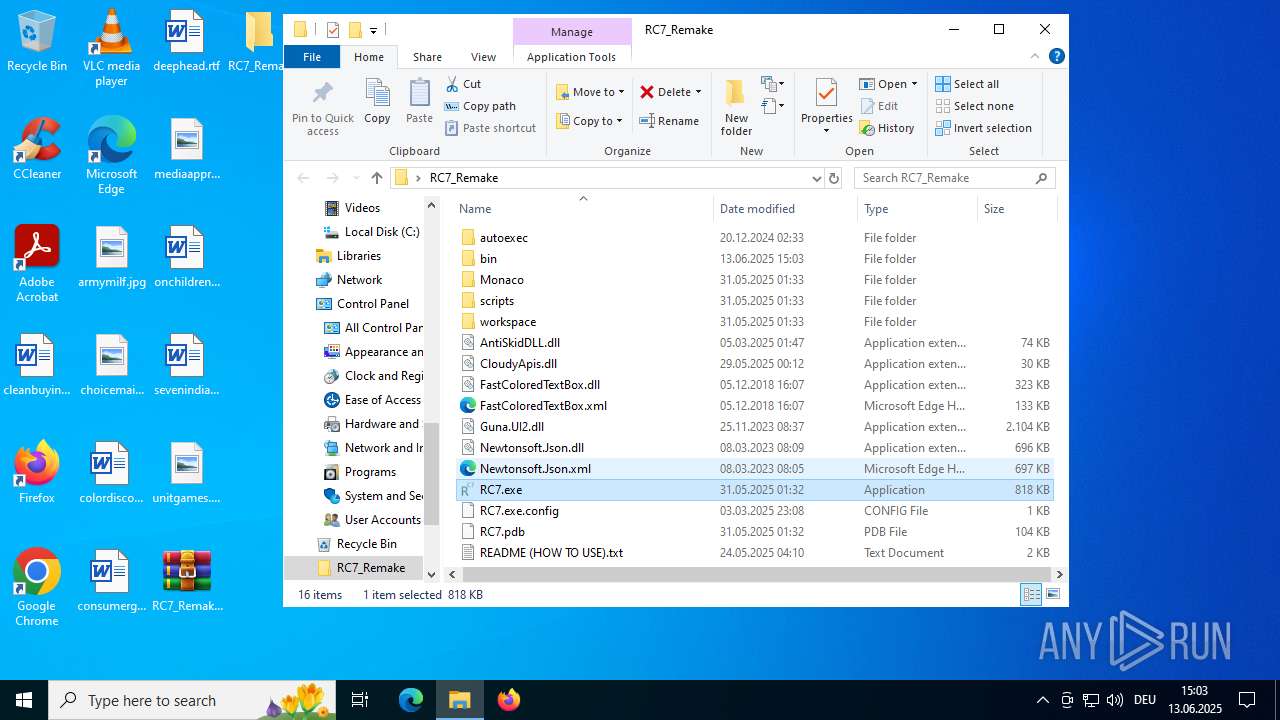
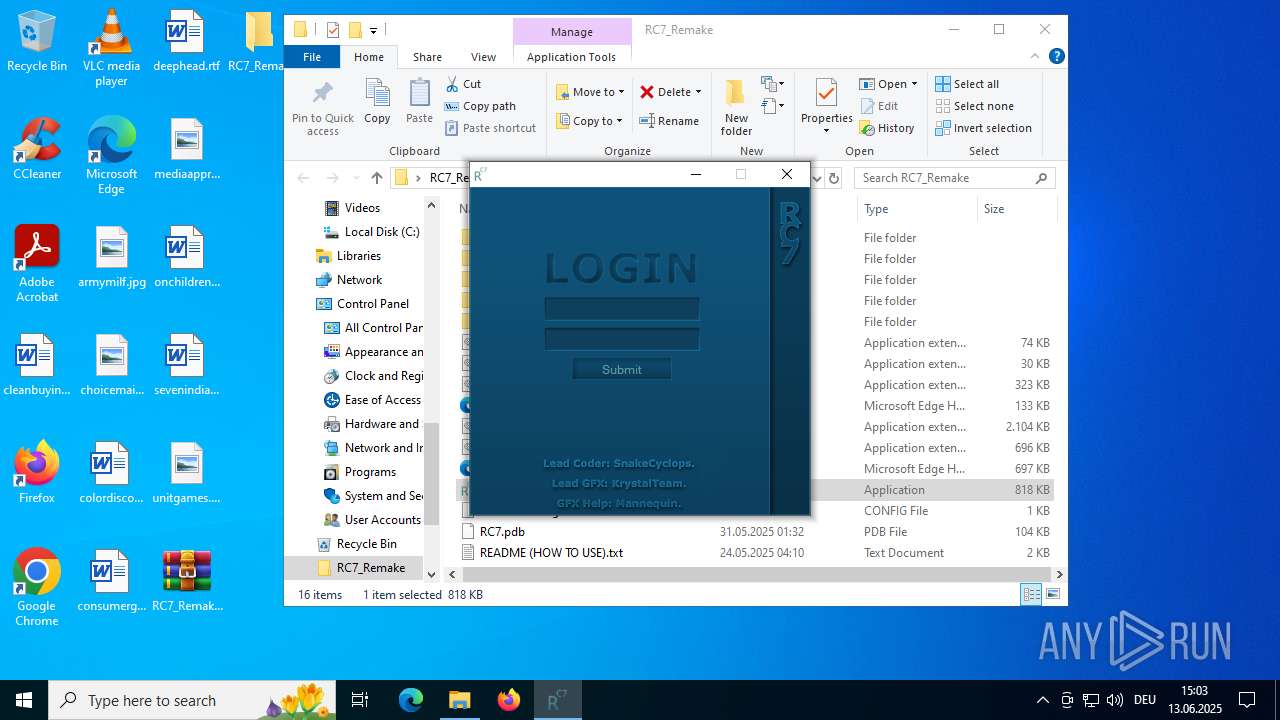
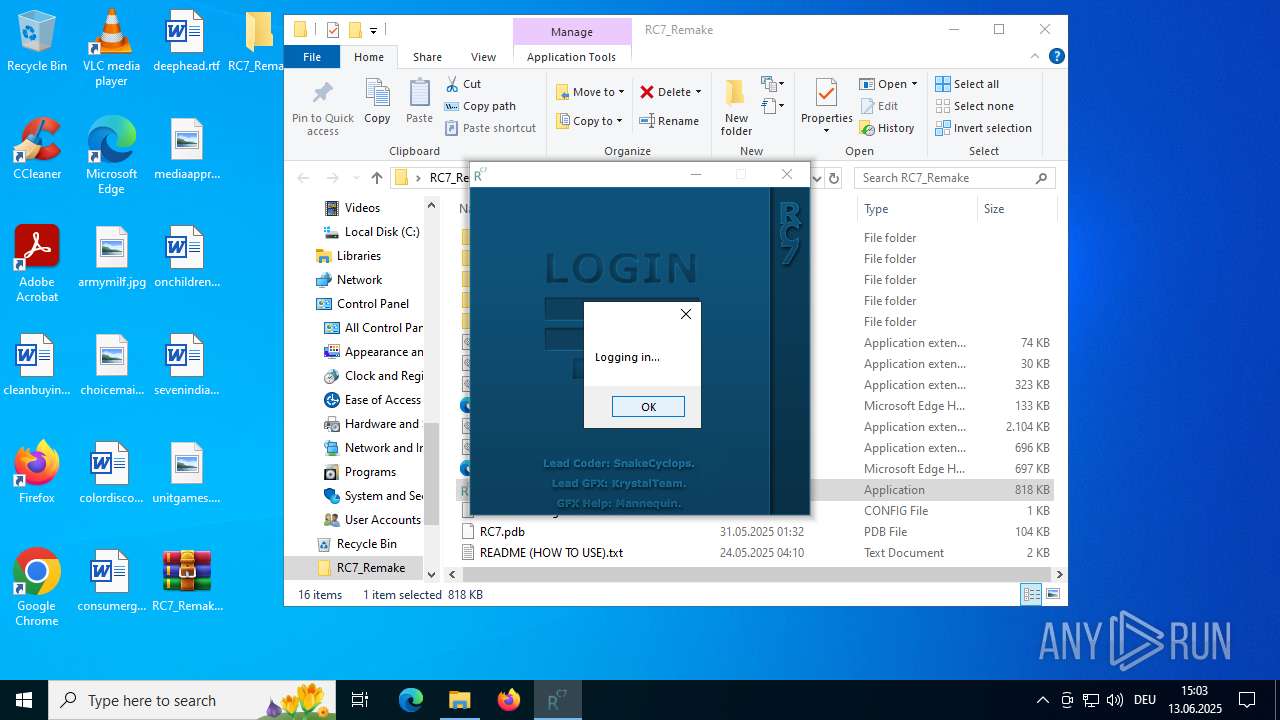
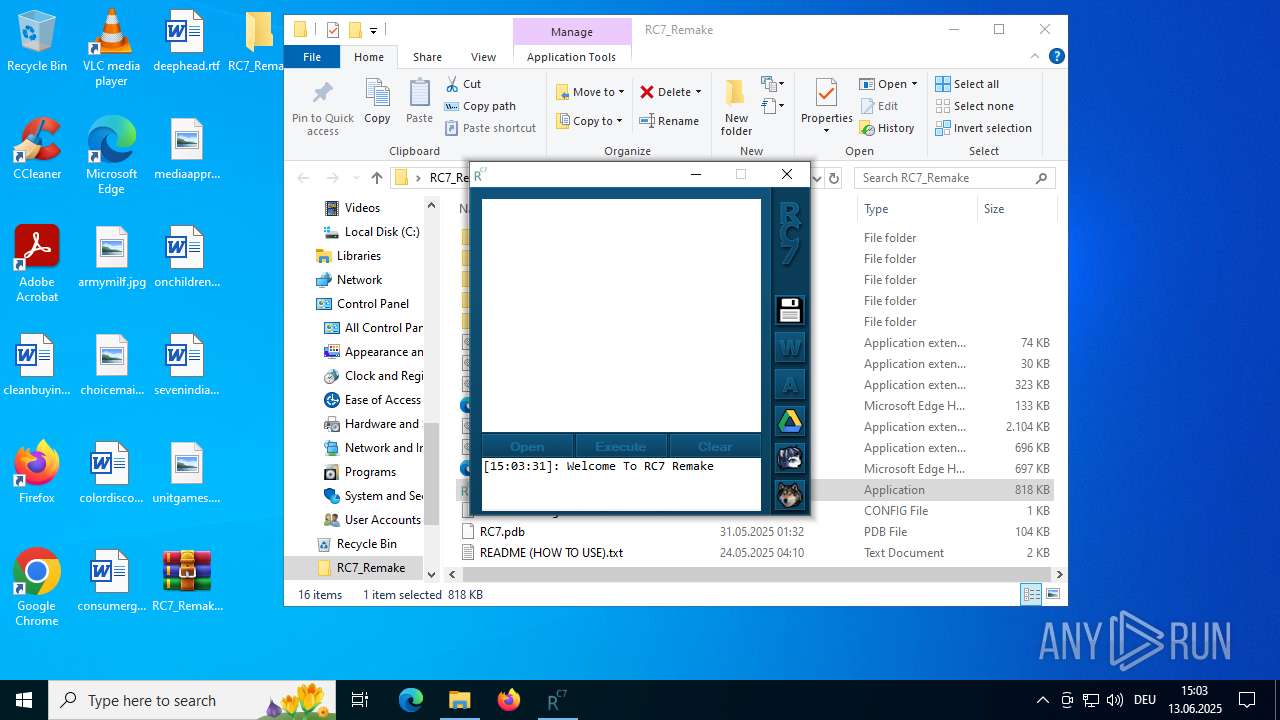
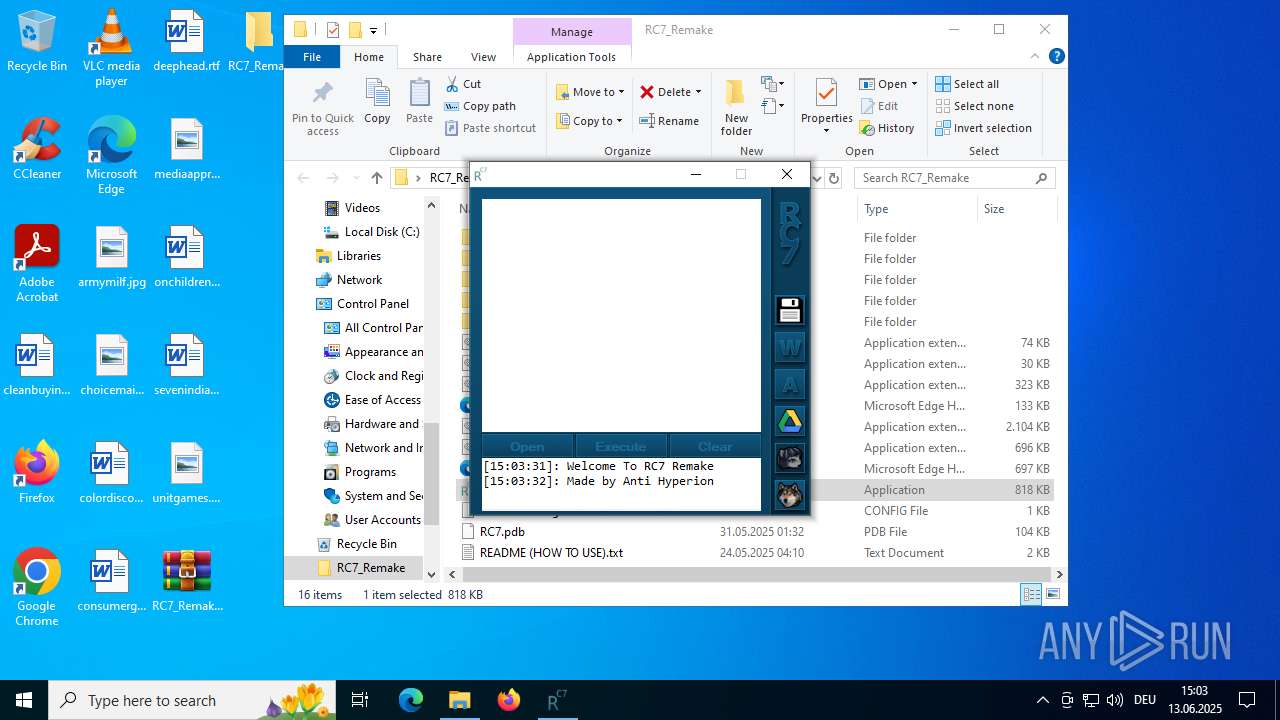
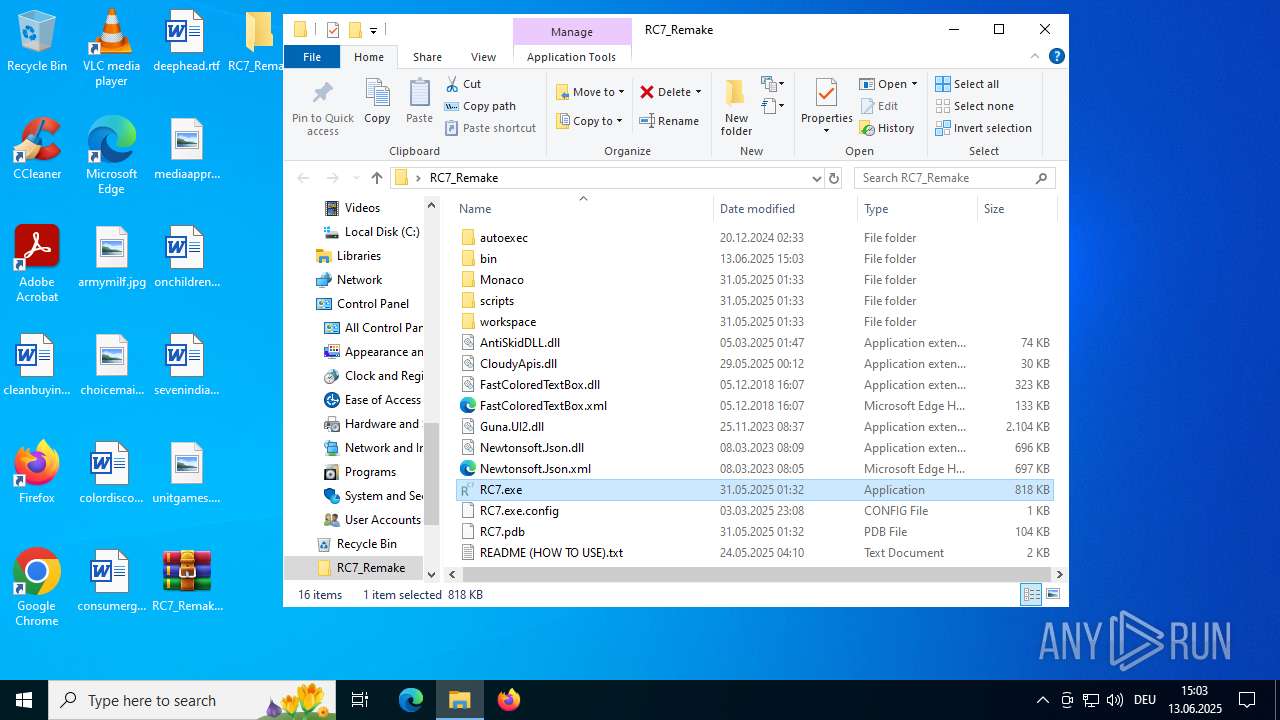
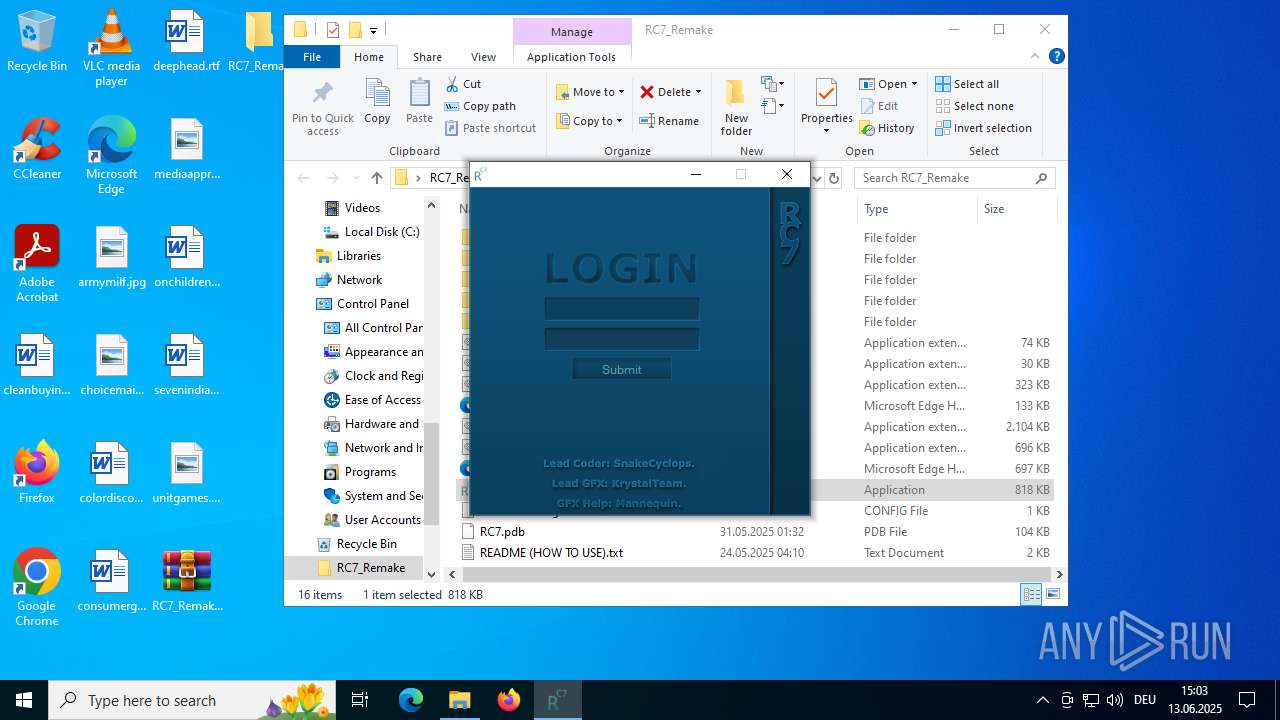
| download: | /attachments/1378827527958564884/1378827528197898361/RC7_Remake.zip |
| Full analysis: | https://app.any.run/tasks/a981140a-2e2d-4341-a215-89dd2bb5ed37 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 13:01:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 34EDEDECB4BBD17446D8EE64BBA979E4 |
| SHA1: | DF7B8CB75A0EA6DD8BE29D7DBBF78DD1142D59ED |
| SHA256: | F6F193EC2FBCFD4E6DD443592AAF1F9FE240C248AD57303FA54928F08FF02F45 |
| SSDEEP: | 98304:2I114ZkDjUqVJhoOisF5QBc8lcqo7DuWjiE6vJMkOk9GFD7RabcD+cH46V5xl7UJ:bEtVjMpr1KPt1 |
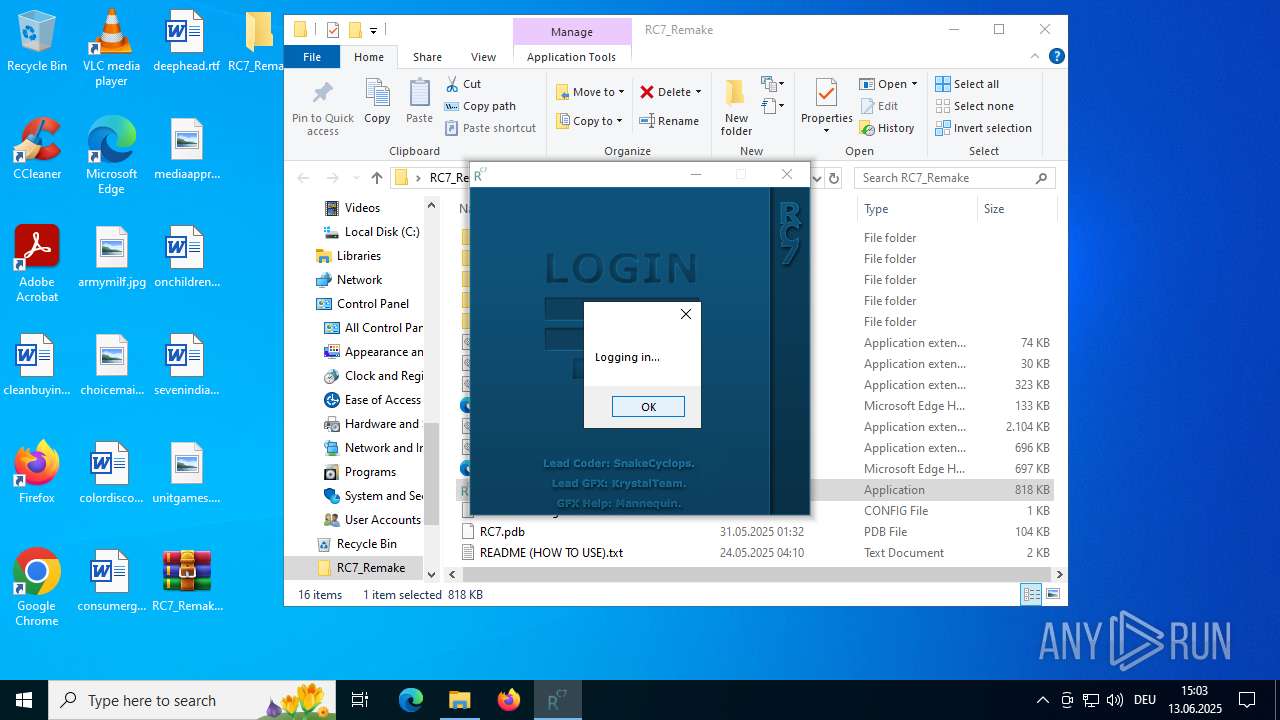
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6268)
SUSPICIOUS
Reads the BIOS version
- RC7.exe (PID: 5184)
- RC7.exe (PID: 2972)
- RC7.exe (PID: 4920)
Reads security settings of Internet Explorer
- RC7.exe (PID: 5184)
- RC7.exe (PID: 4920)
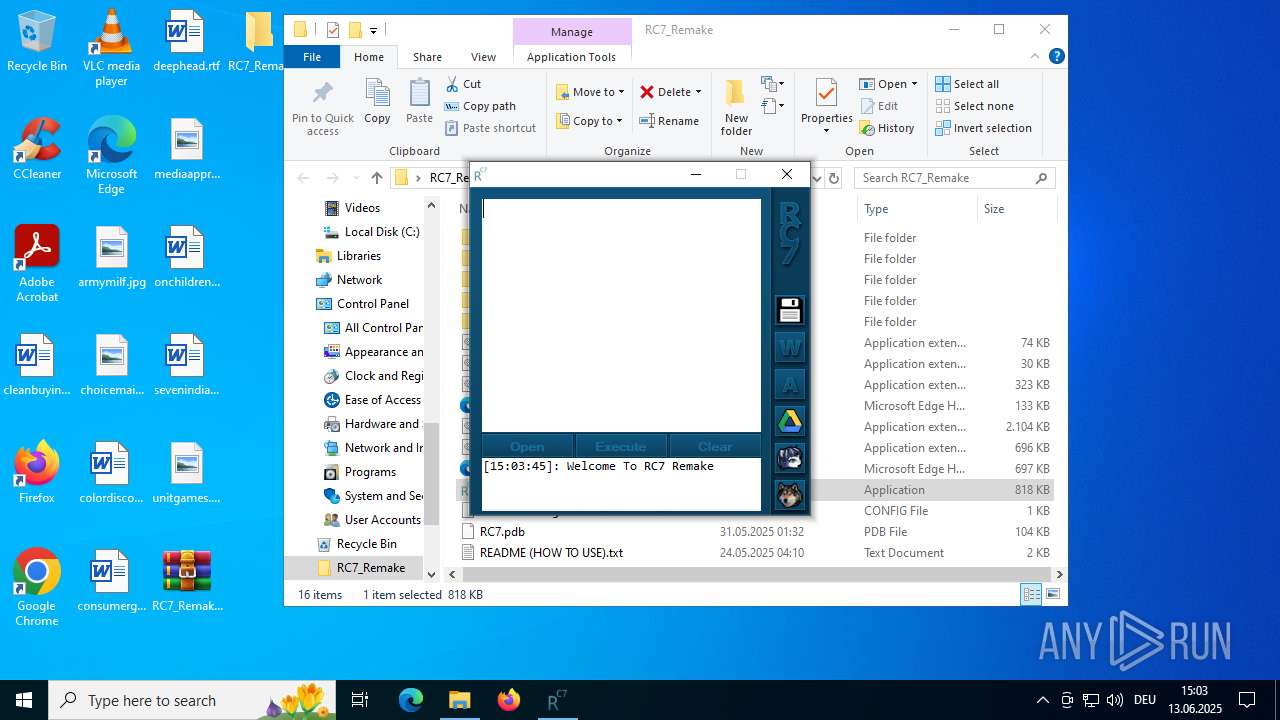
There is functionality for taking screenshot (YARA)
- RC7.exe (PID: 5184)
Executable content was dropped or overwritten
- RC7.exe (PID: 5184)
Read disk information to detect sandboxing environments
- RC7.exe (PID: 2972)
- RC7.exe (PID: 5184)
- RC7.exe (PID: 4920)
The process checks if it is being run in the virtual environment
- RC7.exe (PID: 2972)
- RC7.exe (PID: 5184)
- RC7.exe (PID: 4920)
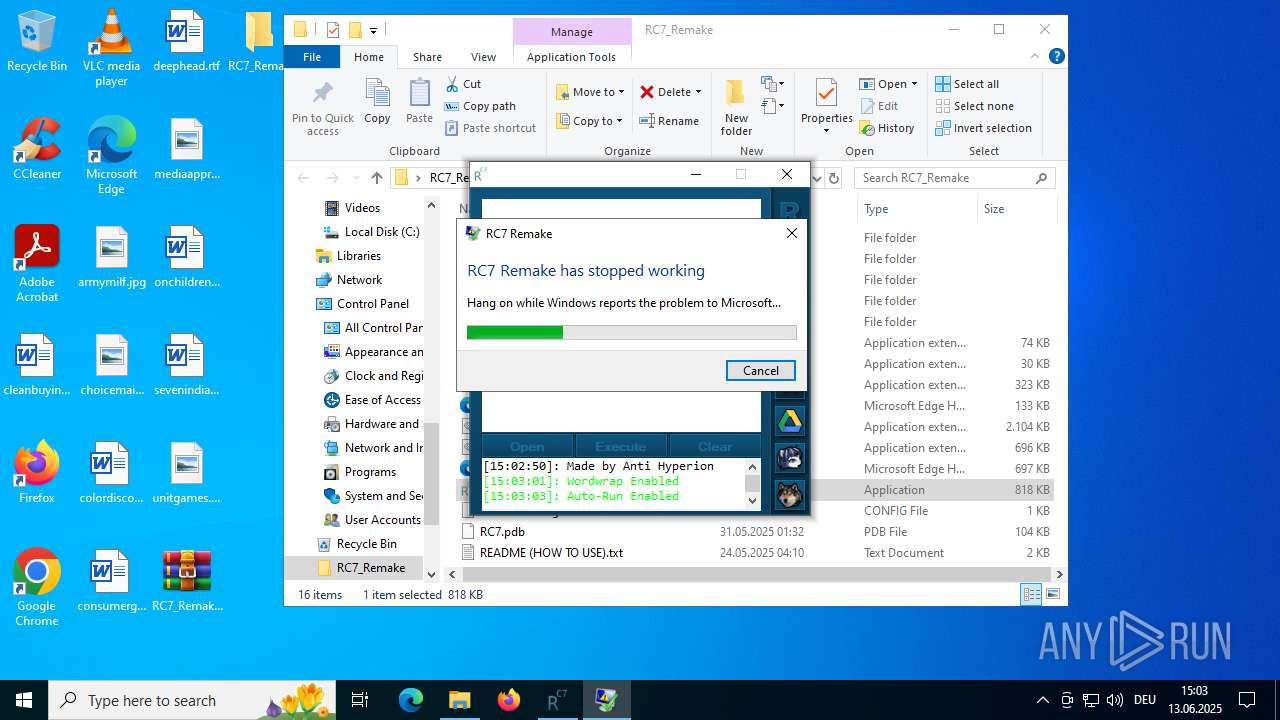
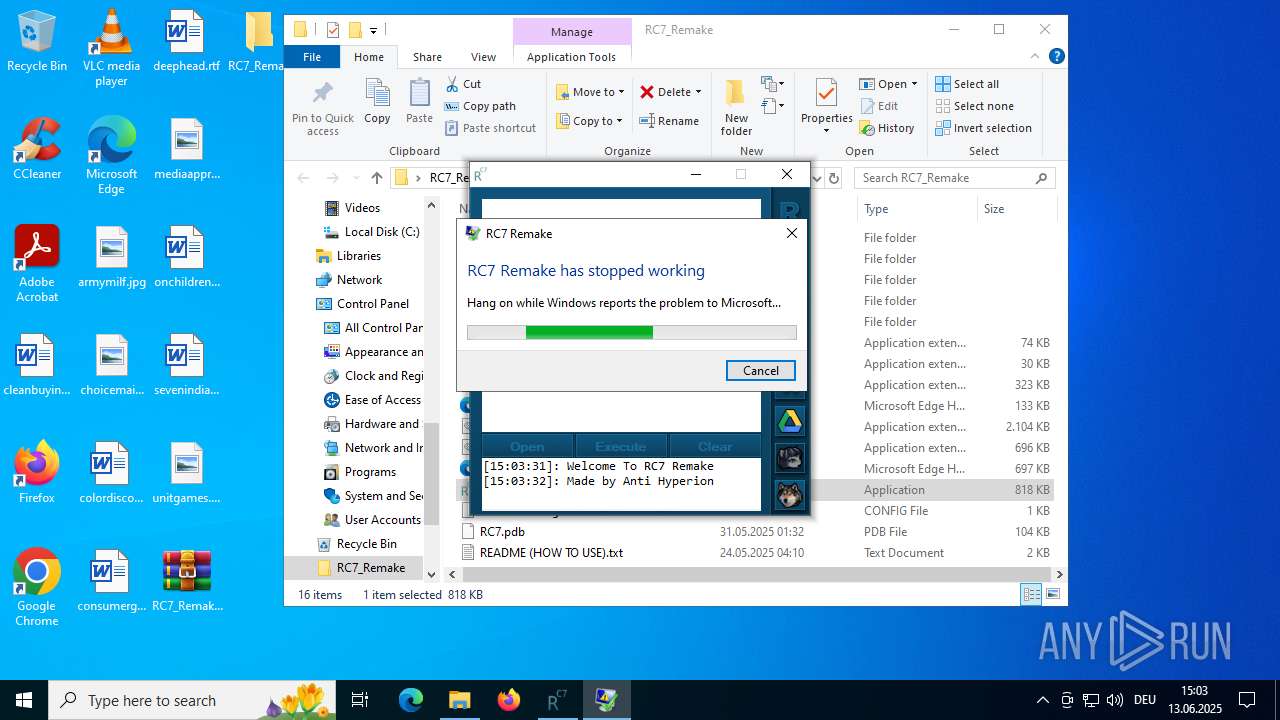
Executes application which crashes
- RC7.exe (PID: 5184)
- RC7.exe (PID: 2972)
INFO
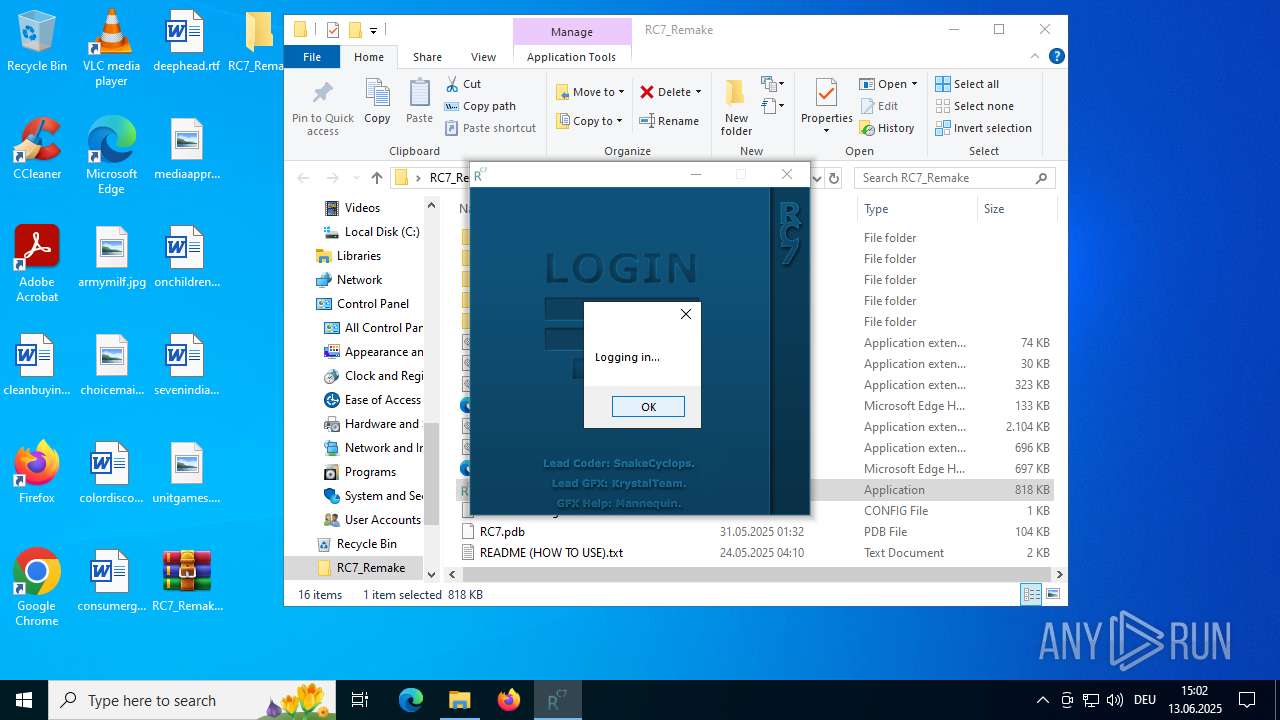
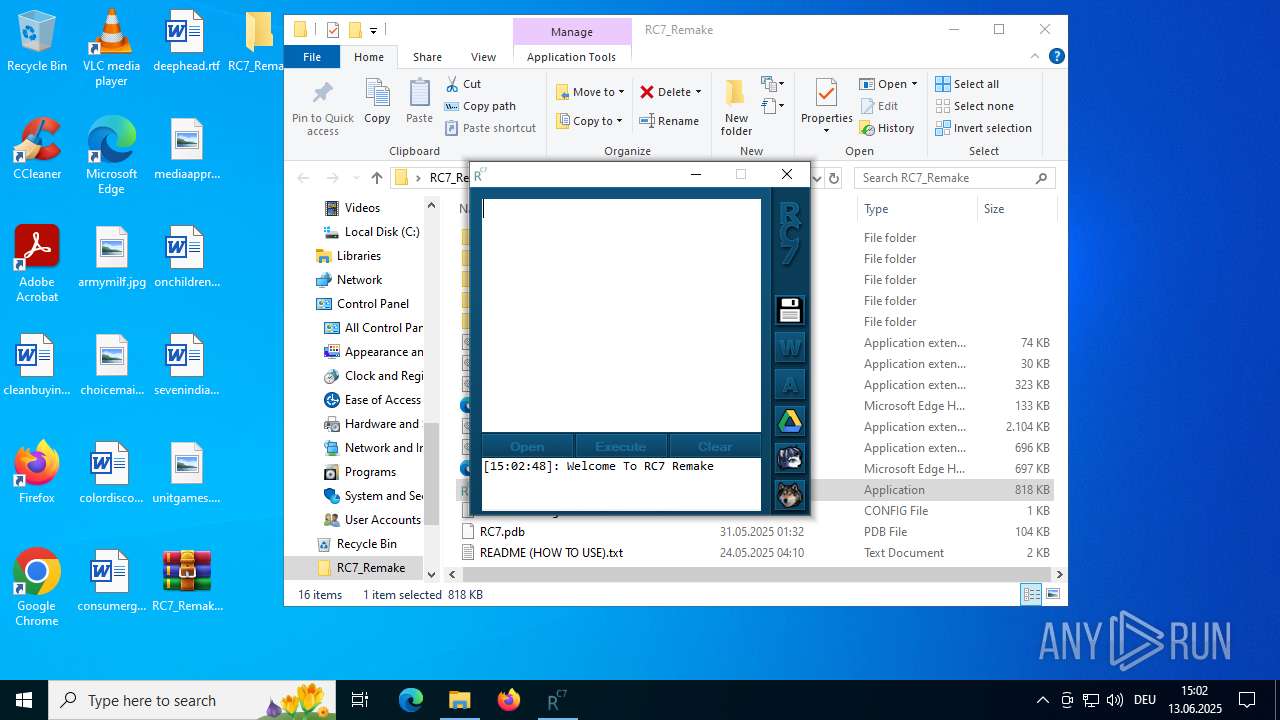
Manual execution by a user
- WinRAR.exe (PID: 4116)
- RC7.exe (PID: 5184)
- RC7.exe (PID: 2972)
- RC7.exe (PID: 4920)
Reads the computer name
- RC7.exe (PID: 5184)
- RC7.exe (PID: 2972)
- RC7.exe (PID: 4920)
The sample compiled with english language support
- WinRAR.exe (PID: 4116)
- RC7.exe (PID: 5184)
Reads the machine GUID from the registry
- RC7.exe (PID: 5184)
- RC7.exe (PID: 2972)
- RC7.exe (PID: 4920)
Checks supported languages
- RC7.exe (PID: 5184)
- RC7.exe (PID: 2972)
- RC7.exe (PID: 4920)
Disables trace logs
- RC7.exe (PID: 5184)
Checks proxy server information
- RC7.exe (PID: 5184)
- WerFault.exe (PID: 2536)
- WerFault.exe (PID: 7040)
- slui.exe (PID: 4120)
Reads the software policy settings
- RC7.exe (PID: 5184)
- WerFault.exe (PID: 2536)
- WerFault.exe (PID: 7040)
- slui.exe (PID: 4120)
Creates files or folders in the user directory
- WerFault.exe (PID: 2536)
- WerFault.exe (PID: 7040)
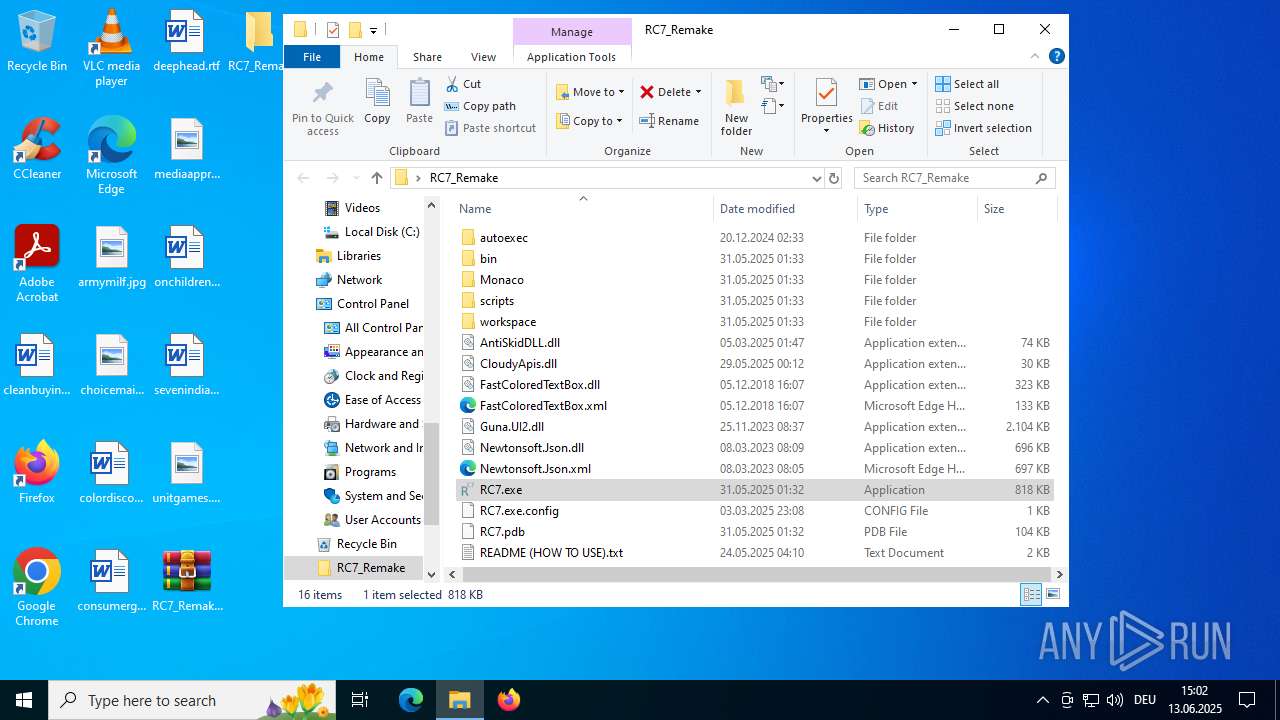
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4116)
Reads Environment values
- RC7.exe (PID: 2972)
- RC7.exe (PID: 5184)
- RC7.exe (PID: 4920)
Confuser has been detected (YARA)
- RC7.exe (PID: 5184)
- RC7.exe (PID: 2972)
Application launched itself
- msedge.exe (PID: 3884)
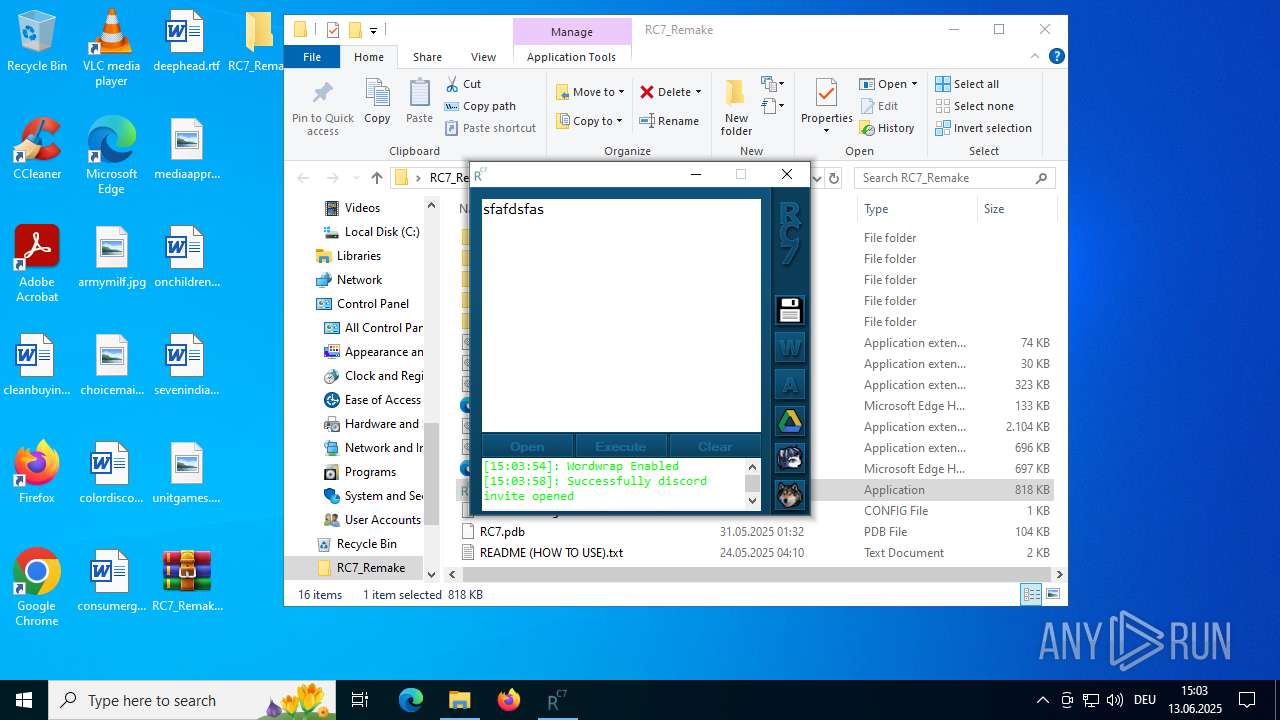
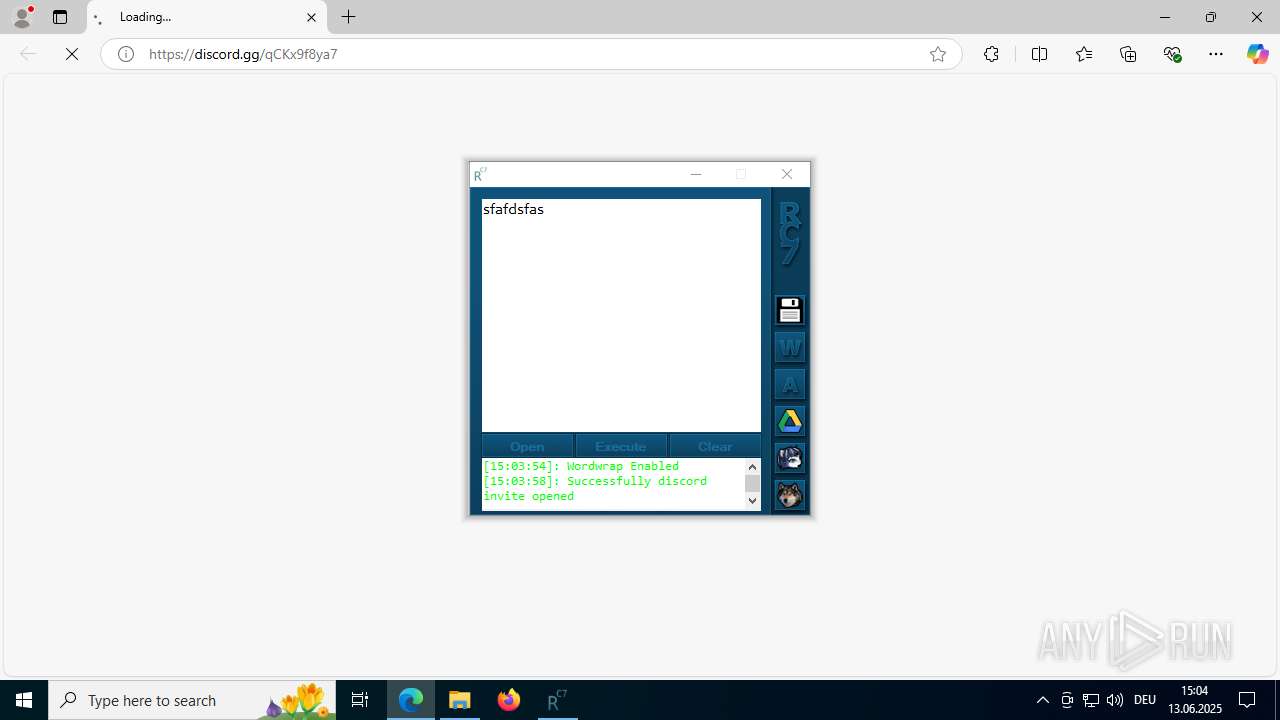
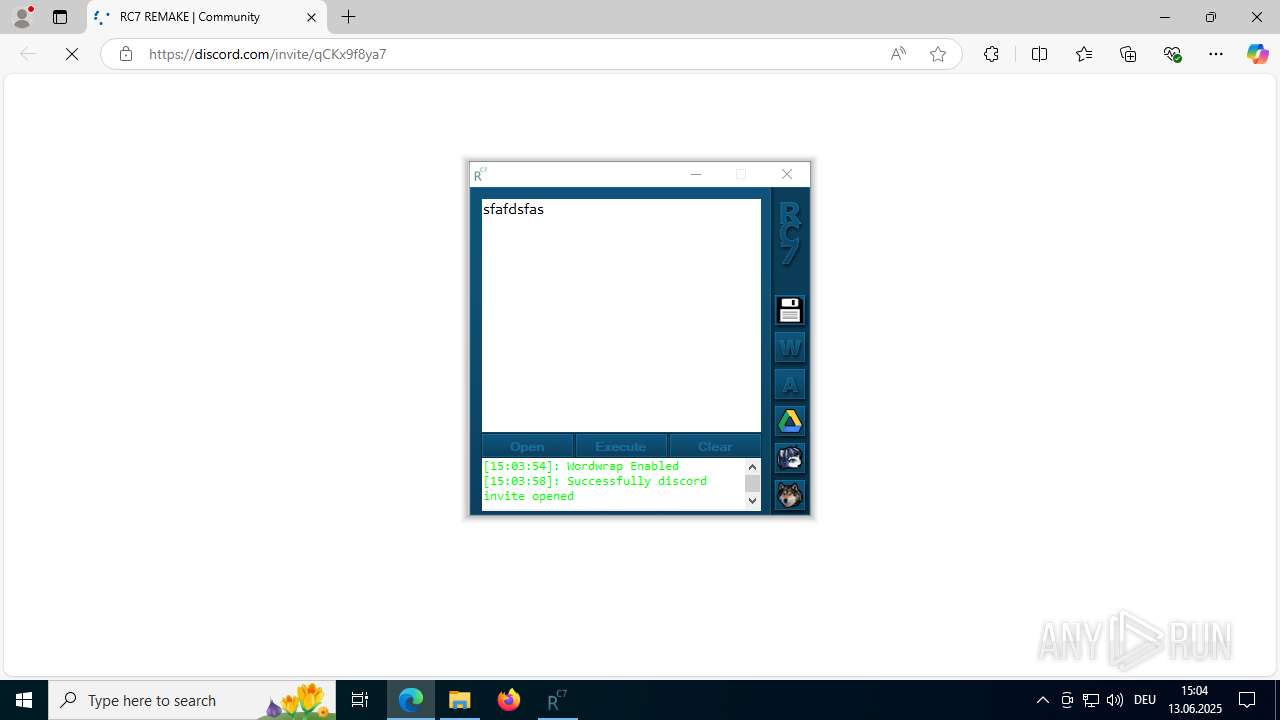
Attempting to use instant messaging service
- msedge.exe (PID: 5952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:19 22:33:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | autoexec/ |
Total processes
149
Monitored processes
22
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4272,i,6281404578922323868,12606856483420455506,262144 --variations-seed-version --mojo-platform-channel-handle=4312 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 620 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3636,i,6281404578922323868,12606856483420455506,262144 --variations-seed-version --mojo-platform-channel-handle=3668 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1212 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5276,i,6281404578922323868,12606856483420455506,262144 --variations-seed-version --mojo-platform-channel-handle=5388 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2044 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc4076f208,0x7ffc4076f214,0x7ffc4076f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2536 | C:\WINDOWS\system32\WerFault.exe -u -p 5184 -s 4776 | C:\Windows\System32\WerFault.exe | RC7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2972 | "C:\Users\admin\Desktop\RC7_Remake\RC7.exe" | C:\Users\admin\Desktop\RC7_Remake\RC7.exe | explorer.exe | ||||||||||||
User: admin Company: Krystal Team Revival Integrity Level: MEDIUM Description: RC7 Remake Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3196 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --always-read-main-dll --field-trial-handle=5268,i,6281404578922323868,12606856483420455506,262144 --variations-seed-version --mojo-platform-channel-handle=5240 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2800,i,6281404578922323868,12606856483420455506,262144 --variations-seed-version --mojo-platform-channel-handle=2816 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3884 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://discord.gg/qCKx9f8ya7 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | RC7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
33 131
Read events
33 035
Write events
94
Delete events
2
Modification events
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\RC7_Remake.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
14
Suspicious files
174
Text files
62
Unknown types
43
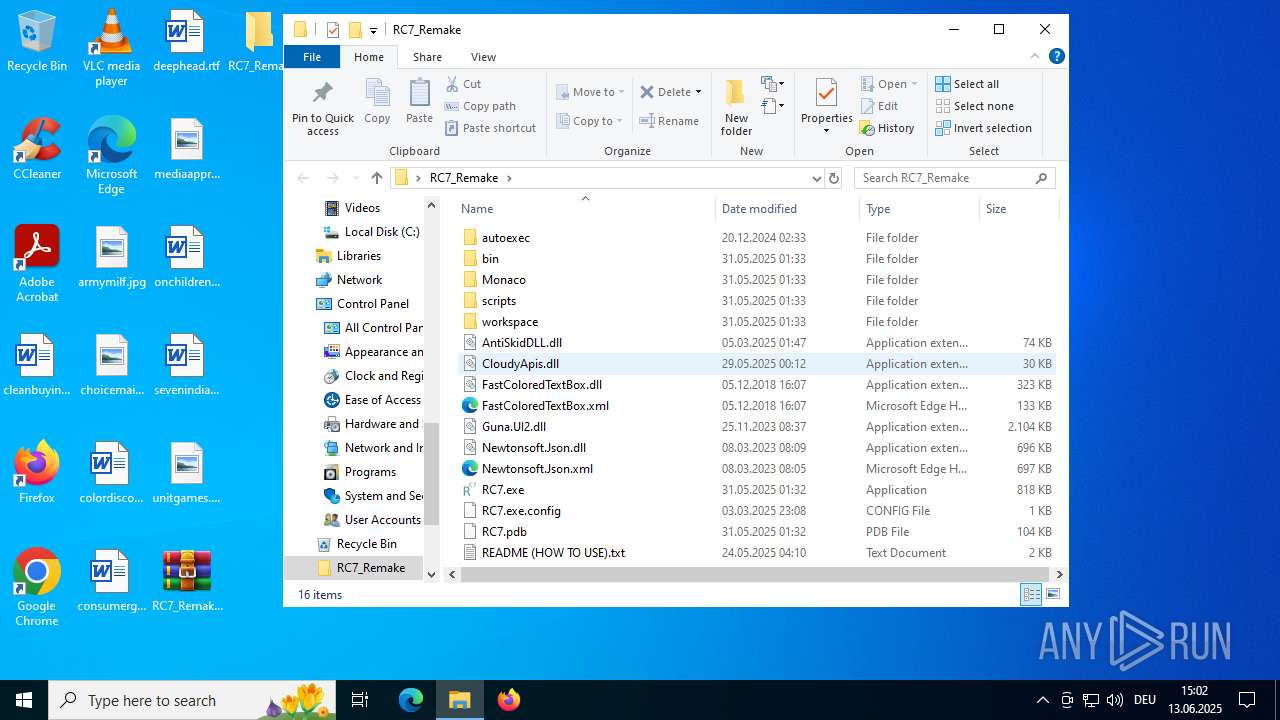
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\Monaco\vs\basic-languages\css\css.js | binary | |
MD5:49AD30F1151CFD7A74677FDC6DD13DA9 | SHA256:BD331FD3BD2C37B0C3150035325F163AC9266BF6D942310764815E676D856D91 | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\bin\Multiple_ROBLOX.exe | executable | |
MD5:AED655395747A6602479F6032D3C099F | SHA256:3D6123DC6FFBD1A11D73229988203052809BD17617B24A034C1122C8F4983DB4 | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\Monaco\vs\basic-languages\coffee\coffee.js | binary | |
MD5:9D0C4AC1691EED0A480C3E9246490D29 | SHA256:E706C9F8E5C5A0CB01B2F4E4879EC34A050D6EB2A8840284EB7BADD9D78099F9 | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\Monaco\vs\base\worker\workerMain.js | s | |
MD5:27EAD90C7702154755785E0E53398755 | SHA256:BDF9433692A08851E13DD58504EEF19F51BD2EC7241923A68EDF5772E0E53AF5 | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\Monaco\vs\basic-languages\fsharp\fsharp.js | binary | |
MD5:DE122B3BC44A8714F386DC80282DCB12 | SHA256:1390079BABC117D3F376735780D98F409F317EB4628D17106642C6933EA1DA7F | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\Monaco\vs\basic-languages\less\less.js | s | |
MD5:696EF3DCA27B4F9313DEBA6F99710154 | SHA256:ED8D1A9DA4E62D1CFFE4C83580C9DF57D688E850A45ACE72C11BDEB064520A16 | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\Monaco\vs\basic-languages\csp\csp.js | s | |
MD5:22ADA25D590811DCFF4E5F5D698E583B | SHA256:4B5A5D7D50986B86B00833447E097C0F01A4388CE1765B48E7E371D06E3A4789 | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\bin\RobloxPlayerLauncher.exe | executable | |
MD5:2C852B9D329284E85FCA0E1CCA876ACA | SHA256:3A8EDC56B985CB0E13DF87EC94D04C69E164498C7342BE7348EE7681C9ABDDD3 | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\Monaco\vs\basic-languages\go\go.js | binary | |
MD5:5B4484C914CD97AFF4510B803F2517EF | SHA256:46D1757C3CD3DBC3C7B465A338880144922A1C34C30E36F06FF2DB8C2FF75B86 | |||
| 4116 | WinRAR.exe | C:\Users\admin\Desktop\RC7_Remake\Monaco\vs\basic-languages\cpp\cpp.js | binary | |
MD5:0A16509E6CD0155FB622E785CFE976C7 | SHA256:A7C2BEA7CA3D9E203A3A286735945FE010C8F4F8D46620386EE8BEFC6A78B32B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
80
TCP/UDP connections
59
DNS requests
28
Threats
63
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/CloudyExecugor/frontend/releases/download/reareaaaa/libcrypto-3-x64.dll | unknown | — | — | unknown |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/CloudyExecugor/frontend/releases/download/reareaaaa/libssl-3-x64.dll | unknown | — | — | unknown |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/CloudyExecugor/frontend/releases/download/reareaaaa/xxhash.dll | unknown | — | — | unknown |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/CloudyExecugor/frontend/releases/download/reareaaaa/Cloudy.dll | unknown | — | — | unknown |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/CloudyExecugor/frontend/releases/download/reareaaaa/zstd.dll | unknown | — | — | unknown |
— | — | GET | 301 | 162.159.136.232:443 | https://discord.gg/qCKx9f8ya7 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
keyauth.win |
| malicious |
activation-v2.sls.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain in DNS Lookup (keyauth .win) |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
5952 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
5952 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
5952 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
5952 | msedge.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |