| download: | jelma.exe |
| Full analysis: | https://app.any.run/tasks/e00de23f-4309-40e1-933b-541f61aec3d3 |
| Verdict: | Malicious activity |
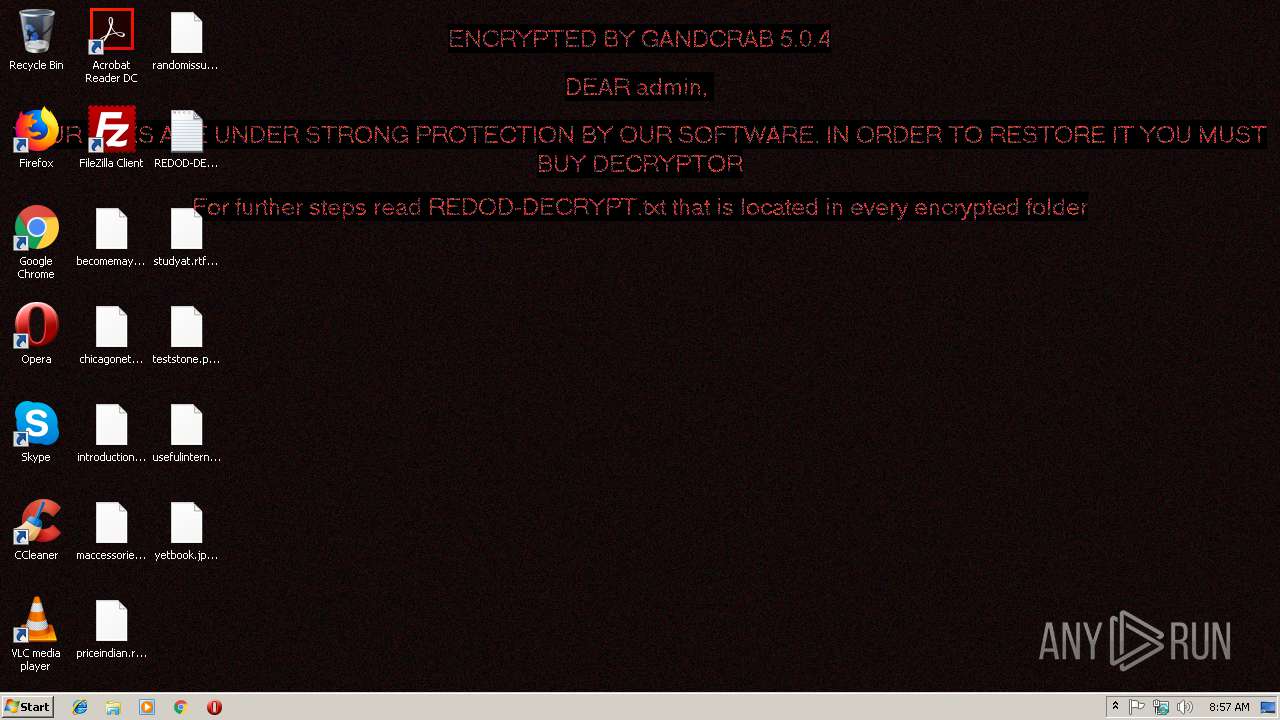
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | November 08, 2018, 08:56:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6D497A11457912BFF6D4B92B5E383037 |
| SHA1: | D8E41FDC4ACC037AC3F4155321B62E9E14FD9220 |
| SHA256: | F6E4A44A1C6BD6A79041746337FBBA4E725ABB70AFB48D676A60DD3BA0C5C65F |
| SSDEEP: | 12288:T0HVVyZ0fNuTJHLvpkMPrQ4YVZq3Yu8/Cv9qFe4K:TKHcTFLvprs4YVcIu8sl4K |
MALICIOUS
Writes file to Word startup folder
- jelma.exe (PID: 3880)
Dropped file may contain instructions of ransomware
- jelma.exe (PID: 3880)
Deletes shadow copies
- jelma.exe (PID: 3880)
GandCrab keys found
- jelma.exe (PID: 3880)
Connects to CnC server
- jelma.exe (PID: 3880)
Actions looks like stealing of personal data
- jelma.exe (PID: 3880)
Renames files like Ransomware
- jelma.exe (PID: 3880)
SUSPICIOUS
Creates files like Ransomware instruction
- jelma.exe (PID: 3880)
Creates files in the user directory
- jelma.exe (PID: 3880)
INFO
Dropped object may contain TOR URL's
- jelma.exe (PID: 3880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:11:07 22:21:42+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 288256 |
| InitializedDataSize: | 256000 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x17780 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.4.7.366 |
| ProductVersionNumber: | 5.4.7.366 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Nextstep Textarea Slwcars Seagate Affrdable |
| CompanyName: | Softplicity |
| InternalName: | Korn Slves |
| LegalCopyright: | Softplicity Copyright (c) 2014 - . All rights reserved. |
| ProductName: | Korn Slves |
| ProductVersion: | 5.4.7.366 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 07-Nov-2018 21:21:42 |
| Detected languages: |
|
| FileDescription: | Nextstep Textarea Slwcars Seagate Affrdable |
| CompanyName: | Softplicity |
| InternalName: | Korn Slves |
| LegalCopyright: | Softplicity Copyright (c) 2014 - . All rights reserved. |
| ProductName: | Korn Slves |
| ProductVersion: | 5.4.7.366 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 07-Nov-2018 21:21:42 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00046561 | 0x00046600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.3967 |
.rdata | 0x00048000 | 0x00012FA6 | 0x00013000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.87471 |
.data | 0x0005B000 | 0x00003D08 | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.05469 |
.rsrc | 0x0005F000 | 0x00029940 | 0x00029A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.59437 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.13982 | 570 | Latin 1 / Western European | English - United States | RT_MANIFEST |
28 | 7.59851 | 91588 | Latin 1 / Western European | English - United States | RCDATA |
190 | 2.96024 | 82 | Latin 1 / Western European | English - United States | RT_MENU |
230 | 7.76429 | 17936 | Latin 1 / Western European | English - United States | RCDATA |
2065 | 3.3485 | 678 | Latin 1 / Western European | English - United States | RT_STRING |
2066 | 3.22471 | 816 | Latin 1 / Western European | English - United States | RT_STRING |
2067 | 3.30079 | 908 | Latin 1 / Western European | English - United States | RT_STRING |
2068 | 3.46008 | 740 | Latin 1 / Western European | English - United States | RT_STRING |
2069 | 3.35967 | 720 | Latin 1 / Western European | English - United States | RT_STRING |
2070 | 3.25792 | 1132 | Latin 1 / Western European | English - United States | RT_STRING |
Imports
ADVAPI32.dll |
AVIFIL32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
KERNEL32.dll |
MSVFW32.dll |
ODBC32.dll |
OLEAUT32.dll |
PSAPI.DLL |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1392 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | jelma.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3880 | "C:\Users\admin\AppData\Local\Temp\jelma.exe" | C:\Users\admin\AppData\Local\Temp\jelma.exe | explorer.exe | ||||||||||||
User: admin Company: Softplicity Integrity Level: MEDIUM Description: Nextstep Textarea Slwcars Seagate Affrdable Exit code: 0 Modules
| |||||||||||||||
Total events
125
Read events
94
Write events
31
Delete events
0
Modification events
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_CURRENT_USER\Software\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E007200650064006F0064000000 | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A40000525341310008000001000100C9C9F56953917131333883BCE56093D2252FC4035DFAD193A4D3616F4C927E8166DE1B9EC1CCEB5842CD989DAB3EC31C249209249B1A447E07866C3C4BBB8A5328FE84103DDF59FEAB8A93C0868A68EF7E51ADBFFAB128050DA3F0BB63727B9097C4F03B20814E5A54835546967786B920AFAFA61B3DEF5EEDA5497A363AB0A825AF768783236ED4A6D3391D91770D662B120076EC1DCE761117D0DEDF7DA9AD3B7BADE17B58F267FEE008F70CC0B03EFFFFB1F2EC927A64C3682B4CB62AD78C5EEEA064A2132FEA5E3EE4EEF257B4F7D308A40DFF145754E05E2814D1EB925685C9D0EB254B110FA23D69E5399E660DC73D0B04293DA8718BB046880B1405C6 | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | private |
Value: 9404000033D7033CF2E5147FE854B0D84B8F804683050D551F46AD368FF505861287E508E42A96A967BA1A95801489FE996DE9FE6168F9DA543AFA1F3A6FCAB005BFD7B08F330626198FE37EA70ED957F2852B7192BFFA2221C79532C400439BA66B72A521F056C76ECC2C39C478DDC8B6DC5A9A49D21308755AE7711909579199E23DC12DF615DB0869C61C5925C06E67C817AEFFBECC4AE5A3710EC1B86E778C86D5378DCD886690445DC90E738A1D2CBE22E30B0BB4B48B745395BE43239C15528406F224663FD1EA25B60C5D7324FBB52984DE7FB97ABAAE98EC3C73E71F8B5DE47429147CECD557988D4D4D2FBA1819C55E5E9B7B20D4C9C8702CEF4D031B6B242C6E32086100A09B800423CB2A8556123982178A614BF6F2E15F83D0B8E35029F36051D6336878A4CAD0BC1B4A71EBB1316285EB323BFAEC6177BB9FFC048244A64DE618A606CA778B108C534424A8EB9F83463E4031206BA38044F0AE0E2B32DAF11F6A5D72B2D9A9F77AE89B62F3BA547F61D411AFF9CDB7CB87DF5C4D69706090304C2310B1A1D0CFBD97382512F1748E5817C87102B24F46895E5D7EB67EA622775A3268B3DEA22E7435DC91C529B40D602A039D840E82082D94E524972E11B58AB00662D4F72F4D985432C56ABDE80C05EF4F01D3FED09A8E944AA2554F6D4D60959878C9A4FA7F816FCEDA6F8D014AFE39921F97F0D2FBEE0902B412E485F42CF8106F2C1B68772F6006EBCBC1BF1536DE71FA1C19F4E2F9C6347E7238F2914CB5E1FC7BE00FB25FD0FC6CA450100EC65E52A265A7E3B06FFCE59F648224DA9BC3A73DD0FA55E211EC84472C22A63371516E54F0E36B19385C864E5A5BA141B6AB18C20447DCA242EE618E0F0706DCBDE97A1841025ECF4A4B686F853E13D4F6C4422E9454F51711480891701557B8F4FC988F06138DFDE1148E2E605CE11EC0A5D17026E83162CAFDD692EF19C9641F680B75B2D48DD9A87BF98B5D91DD56B2E2E9B8F8BFB645E605DF1011AA53D7163FCFFA9947138B1B7A0DAAFAC822486FC3AD44E9290743AB842DE0FF03EF96FFD8E50637F462DC62221E852CEDAF08E92D815C7962A9E0967A088DA5F996A661F04D91966088EFB39BED3001A05D1F7B711C594773855BDF91C98534E6D7351974ECC7A717167FDDEC0FA190EA510854049270369782CAEBAD2DA573F35BB10DF549127C55EAA95916EF1AAFB9C3FF5E0B18CD47DE7DAB6F52C7DF879316AB7FE01908BA2B101703AB874EFB5F241363381E8A1E1B46C3B559030974EDAD9C4DC379B860559D511C902102A42F155F76A923D1B1B9A2F2A8F610E75C51E80C51E8F384A047E51625D17C69B35C431637A3AA9B3A44D8E9858FB24AF2575E7816FDDC63C264520055B9ED0A229932153D90EB310CB45926B596B74AD17A75B8CF76865C0D8137EE9D007EF9E81D6BB1FF3C3E15493FCCBF79C95779268256930E9F4AB0F85005601A278472770F6EA66A6D8704C118C4DA5F914E0F19E69F3678C561DFFF964E15C701195B220A6D737DDC70205D694C03629629C0E2F71722C380114D75F659433C18D5911A8FA319F8D26D656948BB1EB007B672AFE59754E6C6214FE1525DAE47E0EA8975A6B1D70A8E6F1EF20EF1243E6E74F5C0D513A2313234A77A95F4E98AE473DC72989994C2AE9A4C4BBFAD9326466BEB0E27918D72C1E9962981AB5D82FC5B3C3CBB1591DC4DE4F88CD4BDADEA6F8257EBFB2D74D4F4CC850972D00982C6159AB87A0D0C01E19998F9174BF5B4CB637E62385F8C48C16ECDEF557CEDDE14FB3A7E1DA82A28FB07C1A0EBD631A1E6BC4D102AD218FB83DF356A5A5D8E8ECF8788717C1C0C1495743451D693E03FE99597250FD0B704C7854808721DD13065B9289120EB6F8459A81EB76A6D4948CF7EA68E8D9C4468407C78F73A92B3A2C162BE97E02E67DE26B68430DBE943C99593D45E205F2084A53DF5C89C9E61C239436624985EB829843979ADF99AB2B422A1E36E751FE6378C708E8D9C8CAE068D7F48ADB5D8001950D2B6D1A138CB38CDF4BA8E09776902A1B475F3589F48F0E9152C10C63BE5C84E7F53A7785CB81FC27C870FE59E4E240E0CE87C1144B01B63C21F028EF964026565DC31C8872DDA882F2577DFE1486094DDD58C784CDEEB4396A71AFB74F59C8BC3631ECA039862D207D18F4EE08EA1ED8DA3204A24252FA44D5FF97C22A8D1372534FB9DB436834A796B848D2B79A2F621D352E5EC5F49EDB82486AD0AA506033F58222BE9E32B3D79AA20070074BE28F8306083C041A414A2753D8F136B66EC2898100599A7E72128E65B5C611E13280D6039D4DDEDA8549BB425E5F5321022985D5F9FF17C270A3878158A1AC2B7C1CE | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jelma_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jelma_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jelma_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jelma_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3880) jelma.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jelma_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
0
Suspicious files
280
Text files
211
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3880 | jelma.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\REDOD-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\Users\admin\AppData\Roaming\REDOD-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\Users\admin\.oracle_jre_usage\REDOD-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3880 | jelma.exe | C:\Users\admin\AppData\Roaming\Adobe\REDOD-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
60
DNS requests
27
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3880 | jelma.exe | GET | — | 78.46.77.98:80 | http://www.2mmotorsport.biz/ | DE | — | — | suspicious |
3880 | jelma.exe | GET | 301 | 80.244.187.247:80 | http://www.hotelfarinet.com/ | GB | — | — | malicious |
3880 | jelma.exe | GET | 301 | 212.59.186.61:80 | http://www.morcote-residenza.com/ | CH | — | — | malicious |
3880 | jelma.exe | GET | — | 212.59.186.61:80 | http://www.hotelweisshorn.com/ | CH | — | — | malicious |
3880 | jelma.exe | GET | 301 | 83.166.138.7:80 | http://www.whitepod.com/ | CH | — | — | whitelisted |
3880 | jelma.exe | GET | 302 | 192.185.159.253:80 | http://www.pizcam.com/ | US | — | — | malicious |
3880 | jelma.exe | GET | 301 | 104.24.23.22:80 | http://www.belvedere-locarno.com/ | US | — | — | shared |
3880 | jelma.exe | GET | 301 | 83.138.82.107:80 | http://www.swisswellness.com/ | DE | — | — | whitelisted |
3880 | jelma.exe | GET | — | 217.26.53.37:80 | http://www.hrk-ramoz.com/ | CH | — | — | malicious |
3880 | jelma.exe | GET | 200 | 217.26.53.161:80 | http://www.haargenau.biz/ | CH | html | 13.3 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3880 | jelma.exe | 78.46.77.98:443 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
3880 | jelma.exe | 74.220.215.73:80 | www.bizziniinfissi.com | Unified Layer | US | malicious |
3880 | jelma.exe | 78.46.77.98:80 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
3880 | jelma.exe | 217.26.53.161:80 | www.haargenau.biz | Hostpoint AG | CH | malicious |
3880 | jelma.exe | 192.185.159.253:443 | www.pizcam.com | CyrusOne LLC | US | malicious |
3880 | jelma.exe | 192.185.159.253:80 | www.pizcam.com | CyrusOne LLC | US | malicious |
3880 | jelma.exe | 83.166.138.7:80 | www.whitepod.com | Infomaniak Network SA | CH | malicious |
3880 | jelma.exe | 83.138.82.107:80 | www.swisswellness.com | hostNET Medien GmbH | DE | suspicious |
3880 | jelma.exe | 83.138.82.107:443 | www.swisswellness.com | hostNET Medien GmbH | DE | suspicious |
3880 | jelma.exe | 83.166.138.7:443 | www.whitepod.com | Infomaniak Network SA | CH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
www.swisswellness.com |
| whitelisted |
www.hotelweisshorn.com |
| unknown |
www.whitepod.com |
| whitelisted |
www.hardrockhoteldavos.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3880 | jelma.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
3880 | jelma.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3880 | jelma.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3880 | jelma.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3880 | jelma.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
3880 | jelma.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3880 | jelma.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
3880 | jelma.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3880 | jelma.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
3880 | jelma.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
Process | Message |
|---|---|
jelma.exe | Minidump failed! |