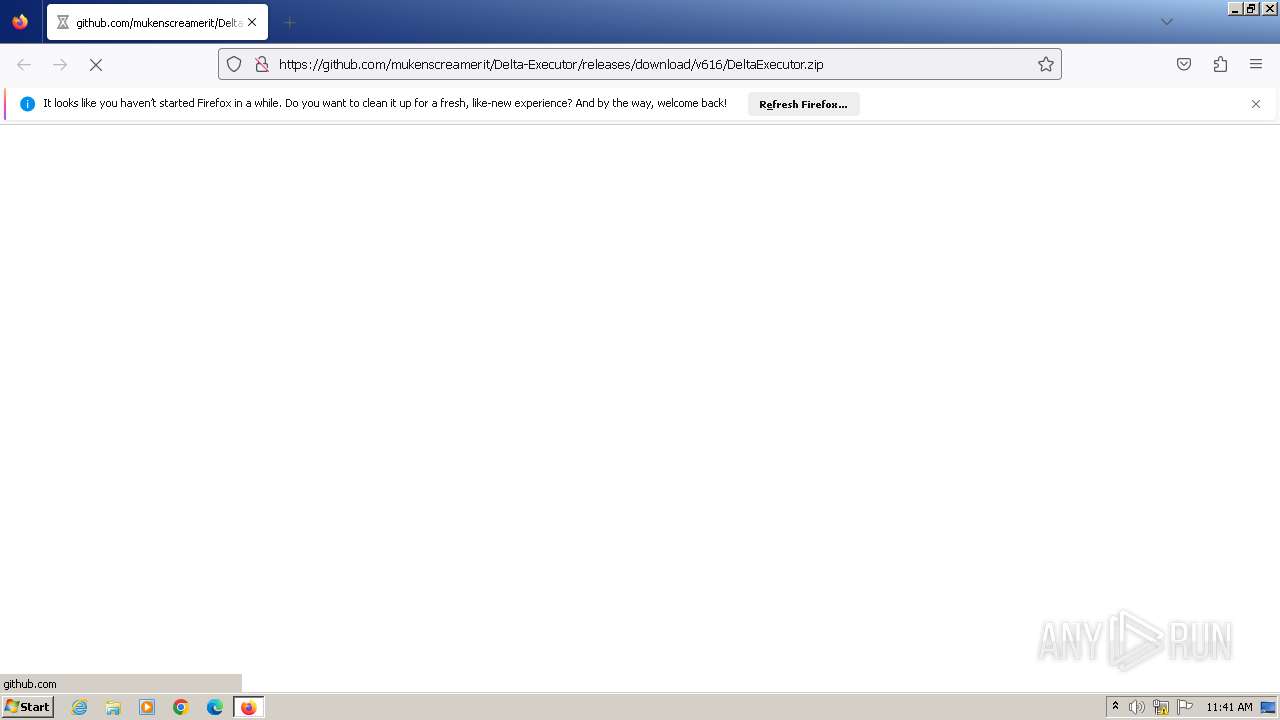
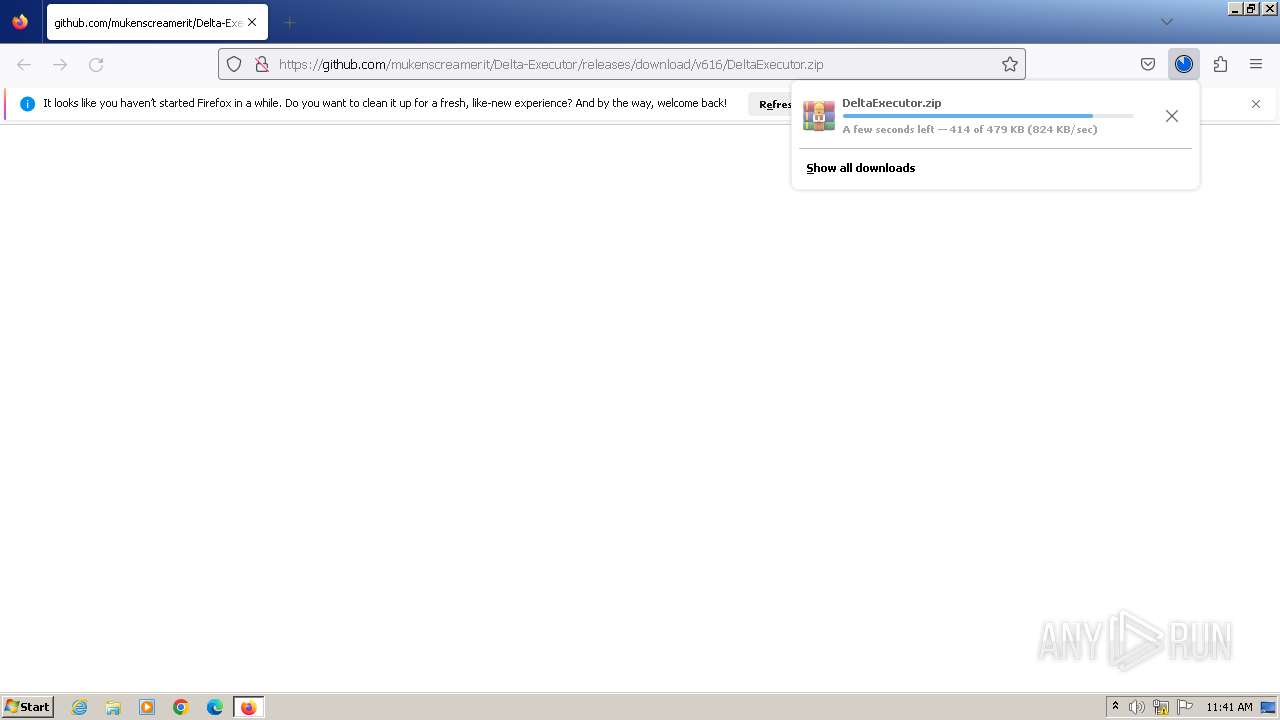
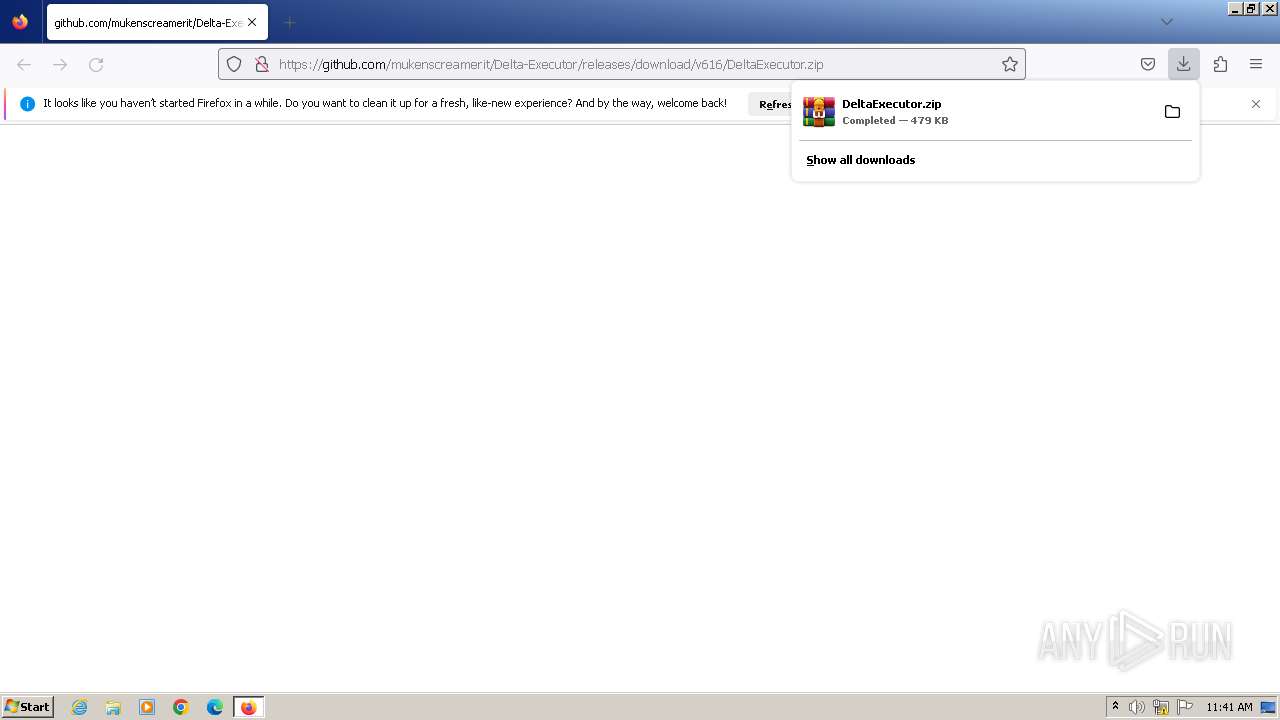
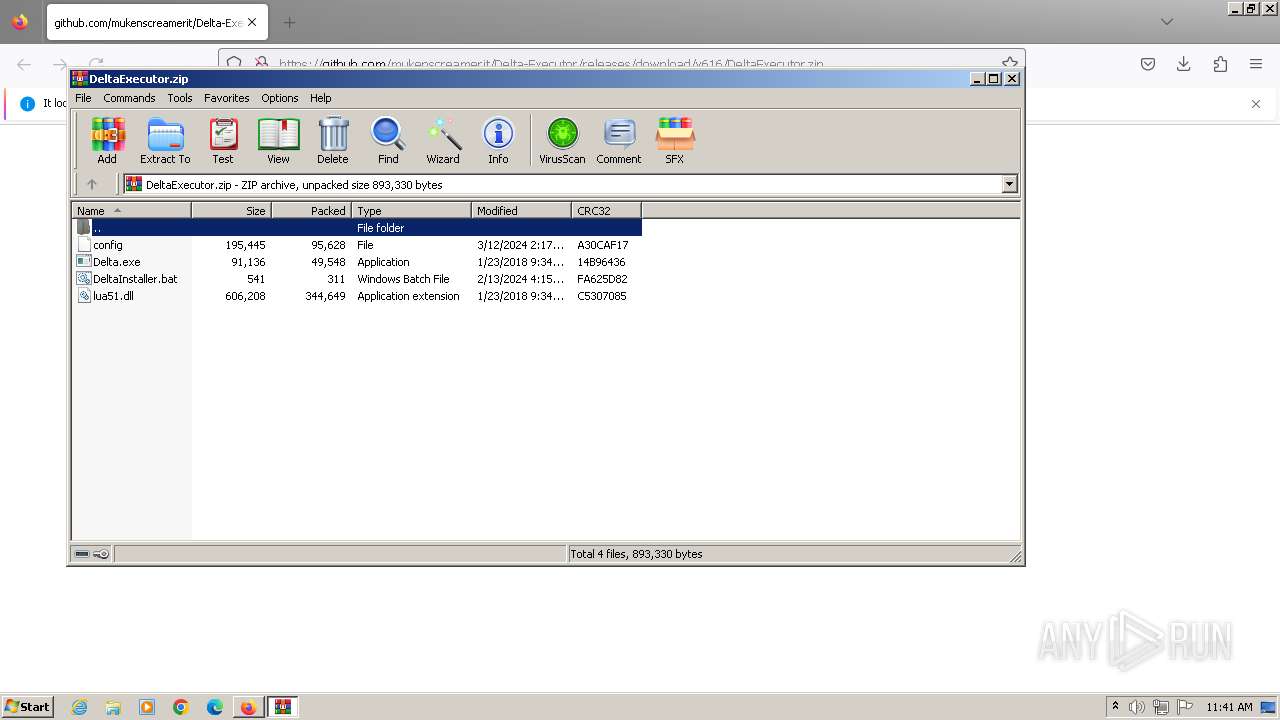
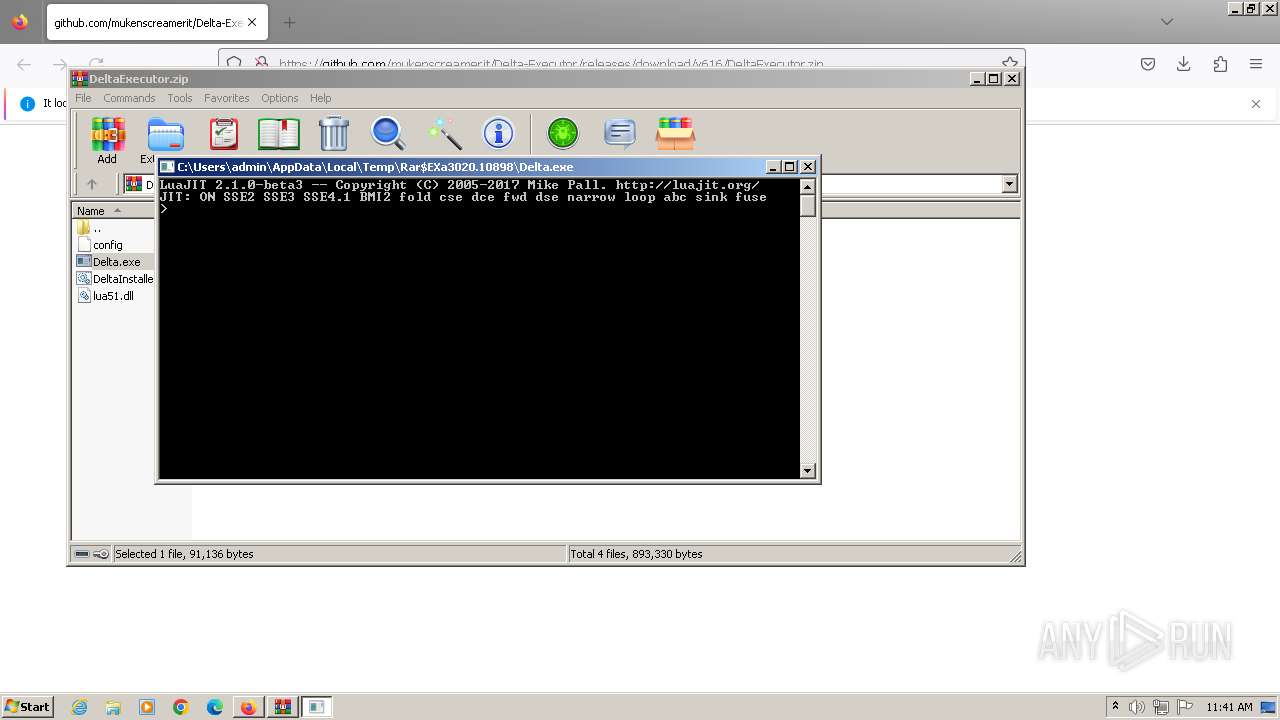
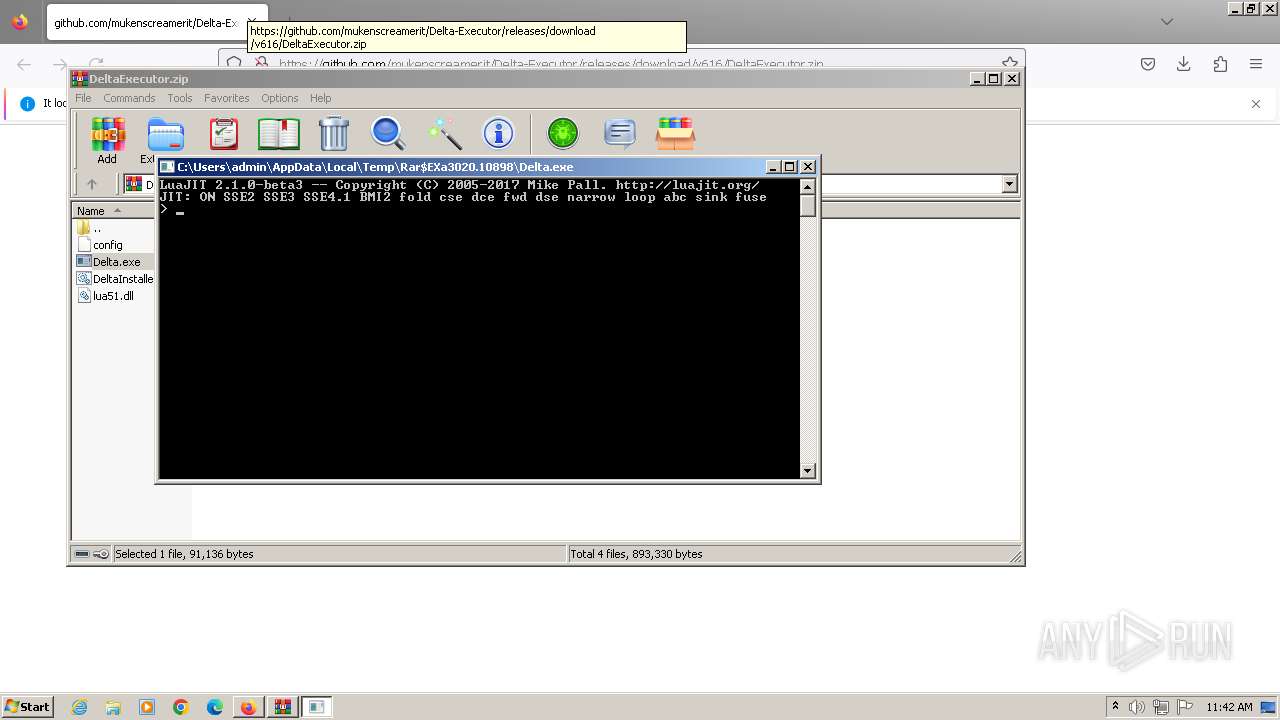
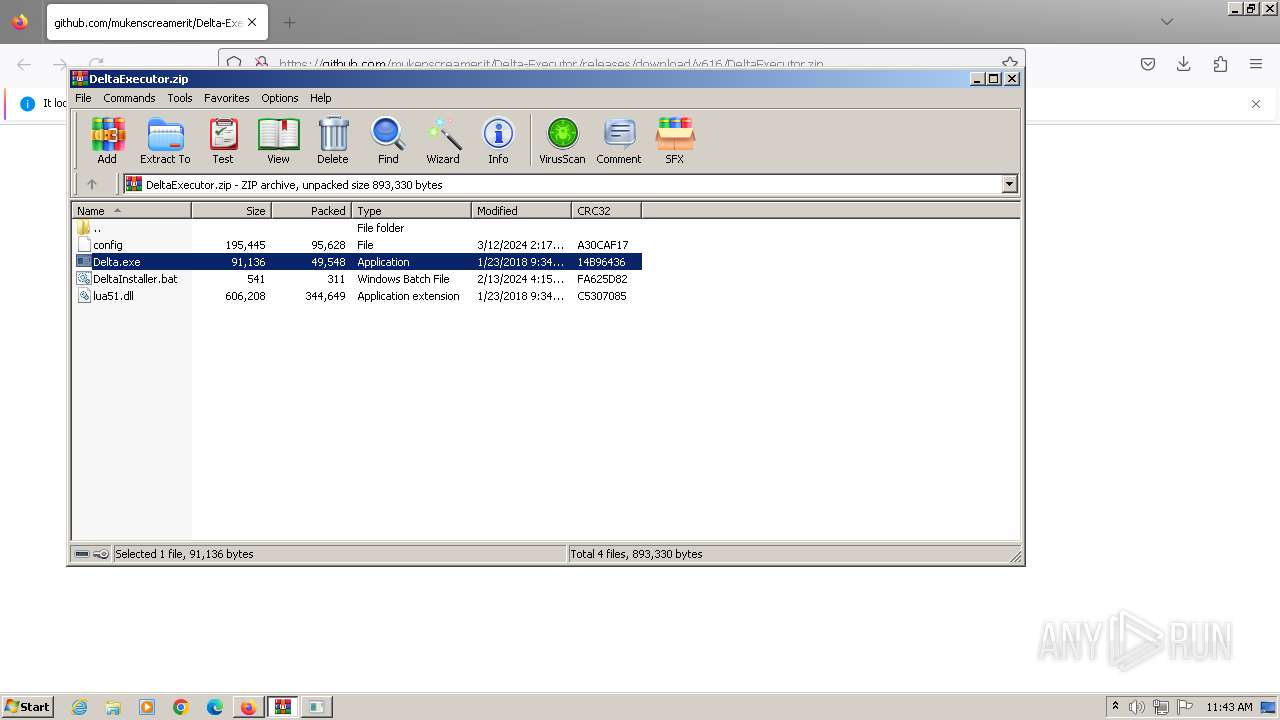
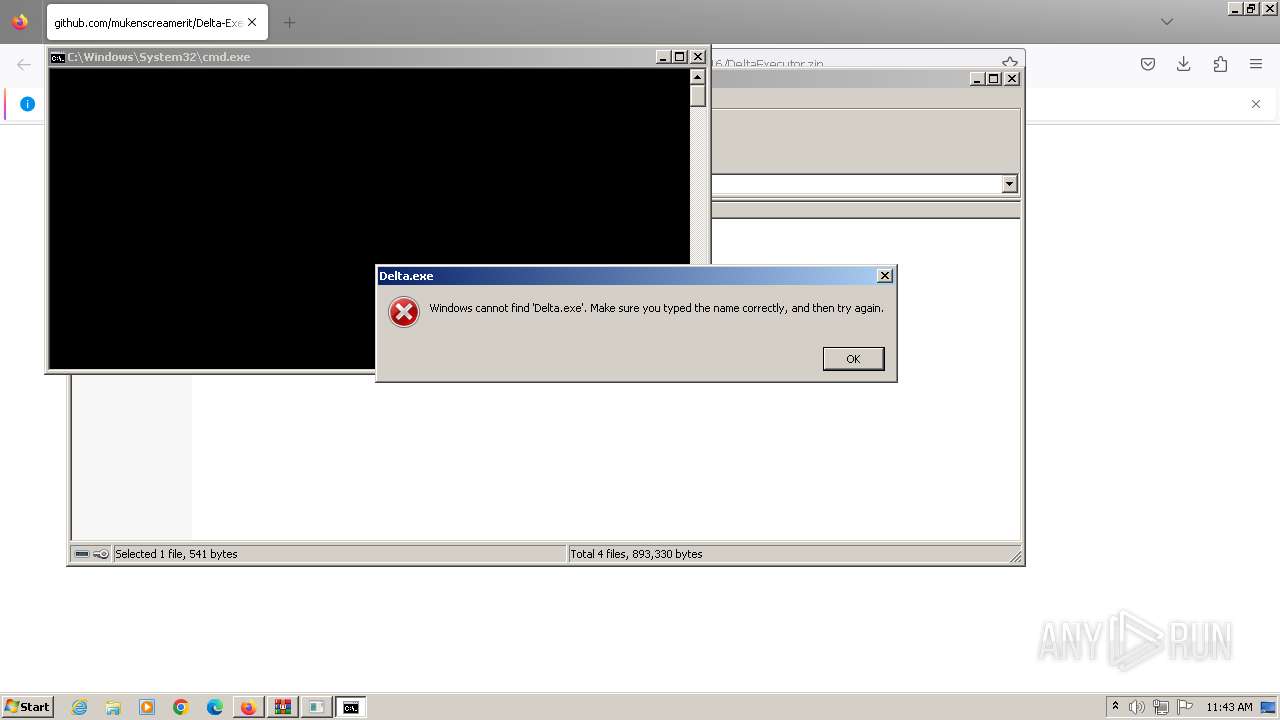
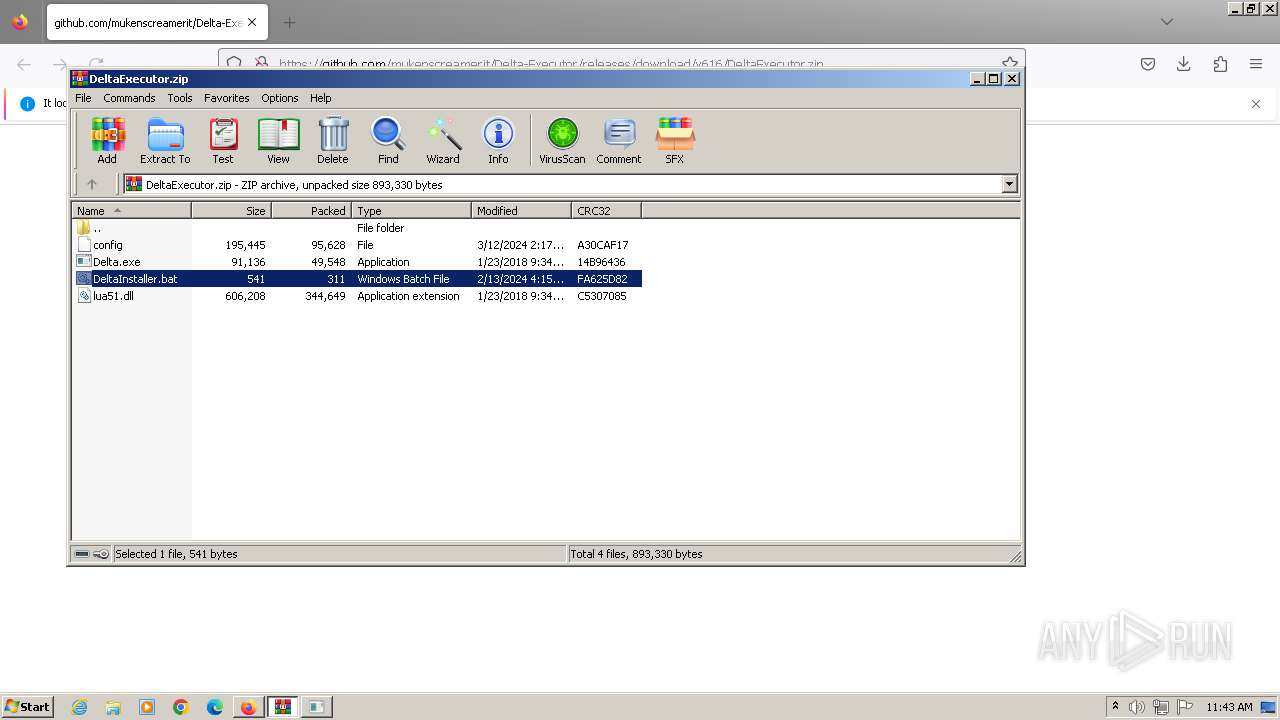
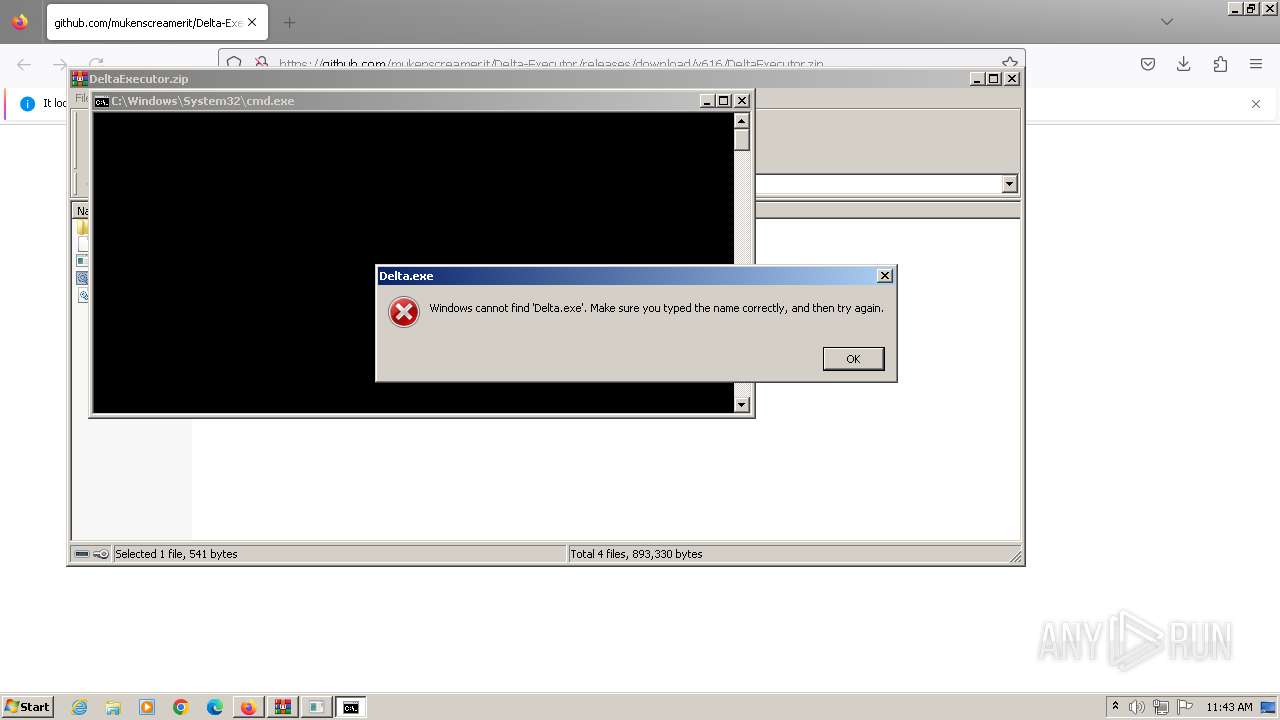
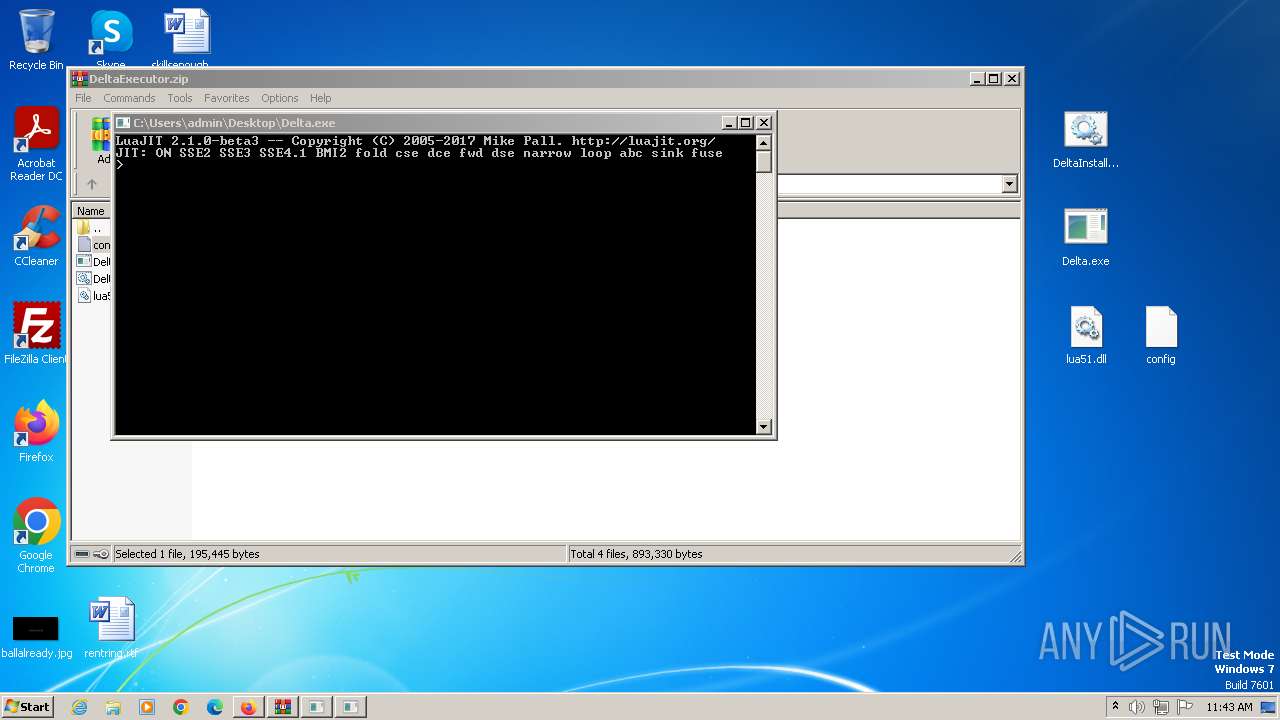
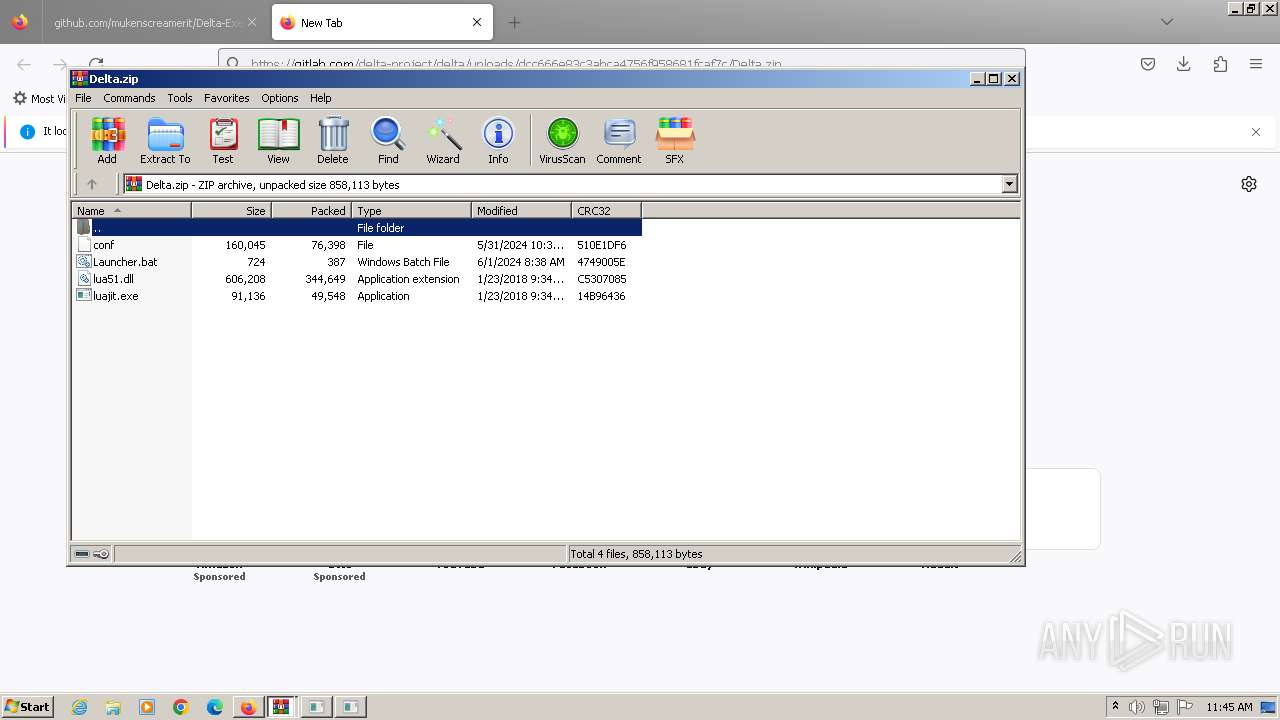
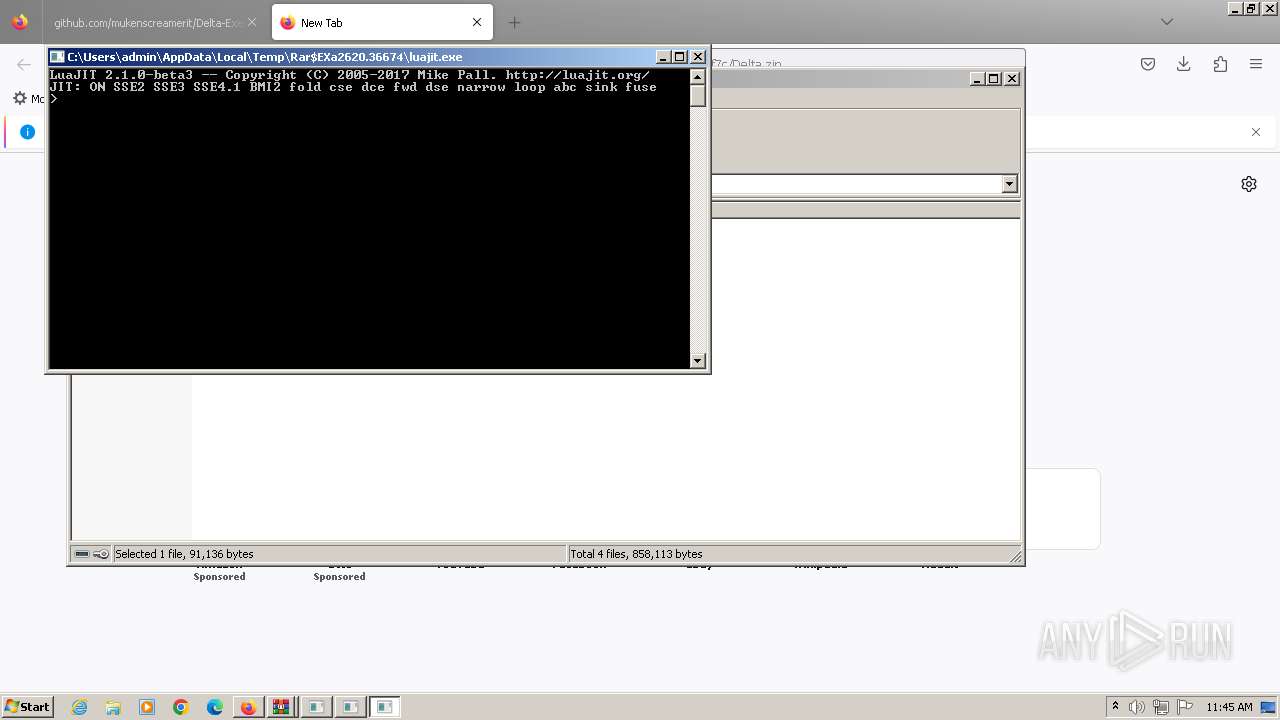
| URL: | https://github.com/mukenscreamerit/Delta-Executor/releases/download/v616/DeltaExecutor.zip |
| Full analysis: | https://app.any.run/tasks/e6b73450-c1eb-4dfc-927d-969b3c13024b |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2024, 10:41:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8BC79689C1A8021EDB61FD050BF57DFD |
| SHA1: | 02429B2586512038EF7E46E4C4D963B813974618 |
| SHA256: | F6DE58C1882DD22FE634E26A58B36BD17967A073B30A35F4CCCD9E46456B35A8 |
| SSDEEP: | 3:N8tEd4CDGAAJREdCHs4E2kCYBqKo:2uuCDGAAJidqDr+cP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3020)
- Delta.exe (PID: 3384)
- WinRAR.exe (PID: 2620)
Reads the Internet Settings
- wscript.exe (PID: 3556)
- cmd.exe (PID: 3432)
- cmd.exe (PID: 3928)
- cmd.exe (PID: 2988)
- wscript.exe (PID: 1944)
- cmd.exe (PID: 3192)
- wscript.exe (PID: 3644)
- cmd.exe (PID: 316)
- Delta.exe (PID: 3384)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3432)
- cmd.exe (PID: 3928)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 2988)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 316)
The process executes VB scripts
- cmd.exe (PID: 3432)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 316)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3020)
- wscript.exe (PID: 3556)
- wscript.exe (PID: 1944)
- wscript.exe (PID: 3644)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3020)
- wscript.exe (PID: 3556)
- wscript.exe (PID: 3644)
- wscript.exe (PID: 1944)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3556)
- wscript.exe (PID: 1944)
- wscript.exe (PID: 3644)
Checks Windows Trust Settings
- Delta.exe (PID: 3384)
Reads settings of System Certificates
- Delta.exe (PID: 3384)
INFO
Application launched itself
- firefox.exe (PID: 4004)
- firefox.exe (PID: 3988)
Drops the executable file immediately after the start
- firefox.exe (PID: 4004)
- WinRAR.exe (PID: 3020)
- WinRAR.exe (PID: 2620)
Reads the computer name
- wmpnscfg.exe (PID: 2868)
- Delta.exe (PID: 3384)
Checks supported languages
- wmpnscfg.exe (PID: 2868)
- Delta.exe (PID: 2948)
- Delta.exe (PID: 3532)
- Delta.exe (PID: 3384)
- luajit.exe (PID: 664)
Manual execution by a user
- wmpnscfg.exe (PID: 2868)
- WinRAR.exe (PID: 3020)
- Delta.exe (PID: 3532)
- cmd.exe (PID: 3192)
- WinRAR.exe (PID: 2620)
The process uses the downloaded file
- firefox.exe (PID: 4004)
- WinRAR.exe (PID: 3020)
- WinRAR.exe (PID: 2620)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3020)
- firefox.exe (PID: 4004)
- WinRAR.exe (PID: 2620)
Checks proxy server information
- Delta.exe (PID: 3384)
Reads the machine GUID from the registry
- Delta.exe (PID: 3384)
Reads the software policy settings
- Delta.exe (PID: 3384)
Creates files or folders in the user directory
- Delta.exe (PID: 3384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
32
Malicious processes
4
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa3020.20865\DeltaInstaller.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 664 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2620.36674\luajit.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2620.36674\luajit.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4004.0.710246824\1943171102" -parentBuildID 20230710165010 -prefsHandle 1112 -prefMapHandle 1104 -prefsLen 28523 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {0d06e98a-e12b-43e7-b36f-74853385c675} 4004 "\\.\pipe\gecko-crash-server-pipe.4004" 1184 163aaaf0 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4004.7.600364152\108694998" -childID 6 -isForBrowser -prefsHandle 4236 -prefMapHandle 4204 -prefsLen 29209 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {9e3a4b3b-af82-4ec4-ab78-8741784899c6} 4004 "\\.\pipe\gecko-crash-server-pipe.4004" 4192 2164d560 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4004.4.309769837\364064125" -childID 3 -isForBrowser -prefsHandle 3708 -prefMapHandle 3632 -prefsLen 29102 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {202485f2-6671-48bd-85d1-754a5fee5209} 4004 "\\.\pipe\gecko-crash-server-pipe.4004" 3720 21651f70 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4004.2.1308676865\972166805" -childID 1 -isForBrowser -prefsHandle 1992 -prefMapHandle 1964 -prefsLen 24491 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {a82456ff-cac6-4f7e-b1aa-d9fca06343a4} 4004 "\\.\pipe\gecko-crash-server-pipe.4004" 1968 1b5939b0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 1856 | "C:\Windows\system32\cacls.exe" "C:\Windows\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4004.3.1313828601\572381746" -childID 2 -isForBrowser -prefsHandle 2908 -prefMapHandle 2904 -prefsLen 34225 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {6d26fb53-70ed-48da-ae84-6e702bf8ae2d} 4004 "\\.\pipe\gecko-crash-server-pipe.4004" 2920 1eed9e00 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 1888 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4004.6.188136627\1795893928" -childID 5 -isForBrowser -prefsHandle 3816 -prefMapHandle 3820 -prefsLen 34225 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {44254fa3-f238-478f-97ef-c74d2415d303} 4004 "\\.\pipe\gecko-crash-server-pipe.4004" 3920 216519b0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 1944 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\getadmin.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
37 621
Read events
37 387
Write events
217
Delete events
17
Modification events
| (PID) Process: | (3988) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 74127AE200000000 | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 79DC7BE200000000 | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (4004) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
Executable files
10
Suspicious files
154
Text files
55
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4004 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:04BADC0A17F546BBD91CC2404D2776D9 | SHA256:54CD83D3031D15EA1F5B1C5D73416C0B2F9151F93E130DD525DDA488A8EB9110 | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:A4C0253717519EB0B07D5D8DD14F5D02 | SHA256:115B88AA451EA9D5CD010C60DB4B97759E55ECE806CF6C4EBA737C6290C0D044 | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cert9.db-journal | binary | |
MD5:CB0B43B644687BFB9FAC45CE5DC65C04 | SHA256:CDB88CE61378B23B8FF86B6928CAE9E4A91B9D2D266DBD568401144EF1F468DB | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\activity-stream.discovery_stream.json.tmp | binary | |
MD5:FB2CBE7C93EE7EA99CB5A630524EEC3F | SHA256:091CA620F098BD470BD85AB8AA6010E12F6F0BD3F4914B36EFC17673913872D1 | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\activity-stream.discovery_stream.json | binary | |
MD5:FB2CBE7C93EE7EA99CB5A630524EEC3F | SHA256:091CA620F098BD470BD85AB8AA6010E12F6F0BD3F4914B36EFC17673913872D1 | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\datareporting\glean\db\data.safe.tmp | dbf | |
MD5:7FBA44CB533472C1E260D1F28892D86B | SHA256:14FB5CDA1708000576F35C39C15F80A0C653AFAF42ED137A3D31678F94B6E8BF | |||
| 4004 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\datareporting\glean\db\data.safe.bin | dbf | |
MD5:7FBA44CB533472C1E260D1F28892D86B | SHA256:14FB5CDA1708000576F35C39C15F80A0C653AFAF42ED137A3D31678F94B6E8BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
65
DNS requests
143
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4004 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | unknown |
4004 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
4004 | firefox.exe | POST | 200 | 23.58.120.82:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
4004 | firefox.exe | POST | 200 | 23.58.120.82:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
4004 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | unknown |
4004 | firefox.exe | POST | 200 | 23.58.120.82:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
4004 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | unknown |
4004 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | unknown |
4004 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | unknown |
4004 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4004 | firefox.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
4004 | firefox.exe | 142.250.186.74:443 | safebrowsing.googleapis.com | — | — | whitelisted |
4004 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
4004 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
4004 | firefox.exe | 104.18.38.233:80 | ocsp.sectigo.com | CLOUDFLARENET | — | shared |
4004 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
github.com |
| shared |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| shared |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
ocsp.sectigo.com |
| whitelisted |
ocsp.comodoca.com.cdn.cloudflare.net |
| whitelisted |