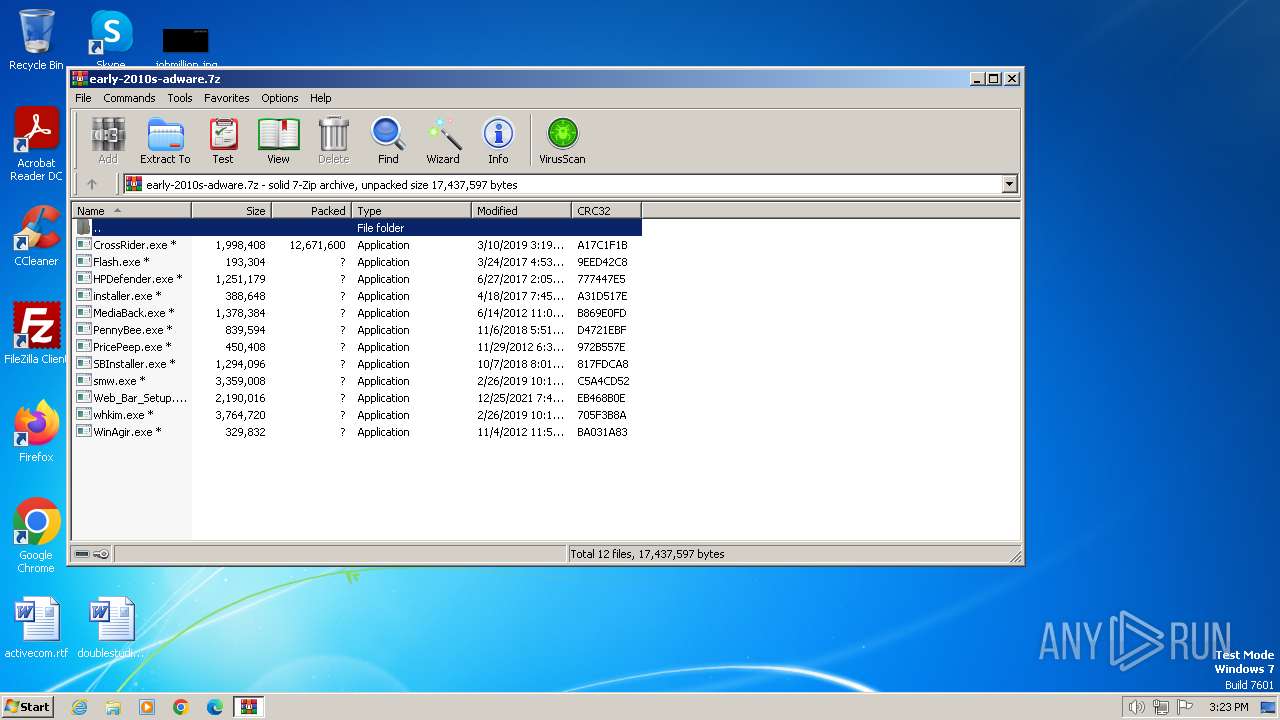
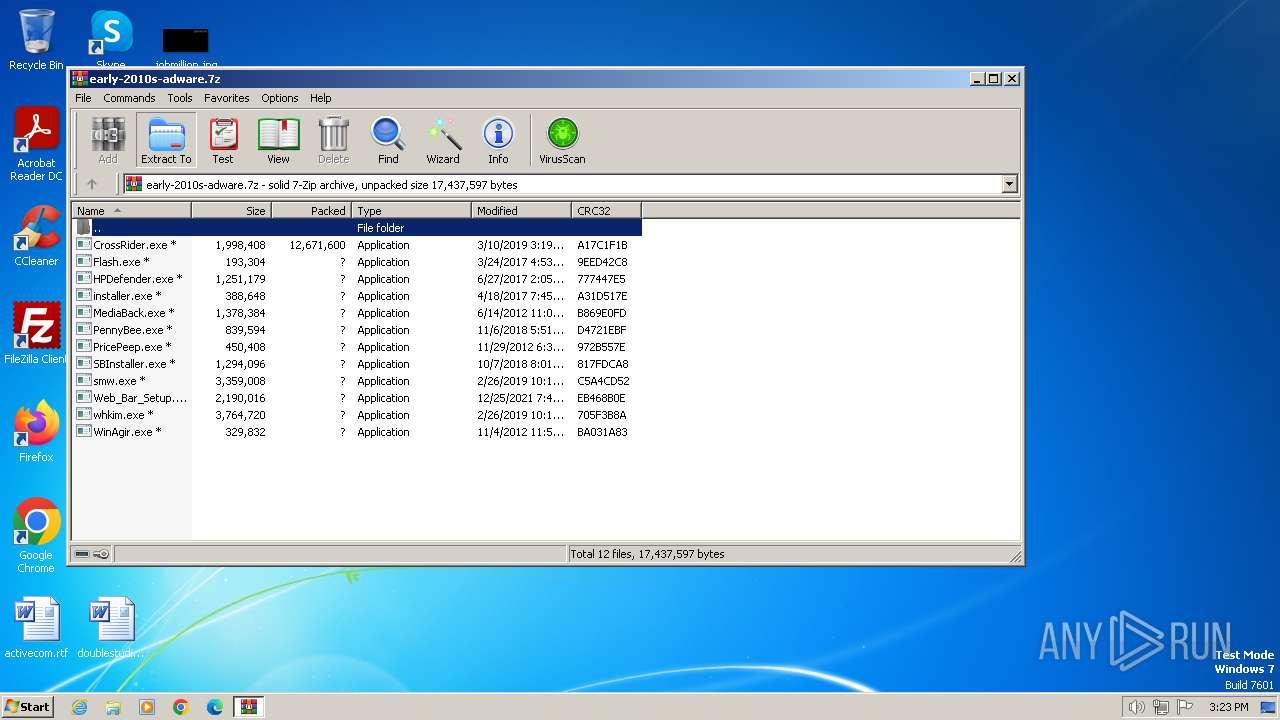
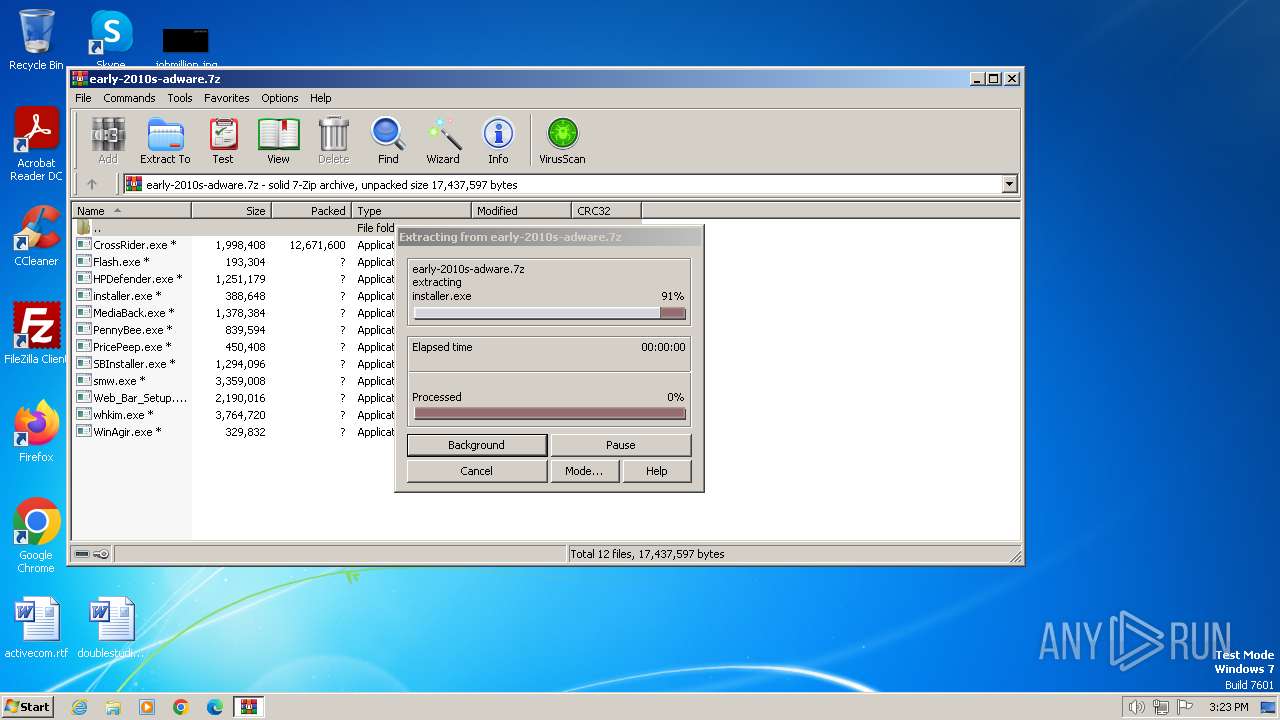
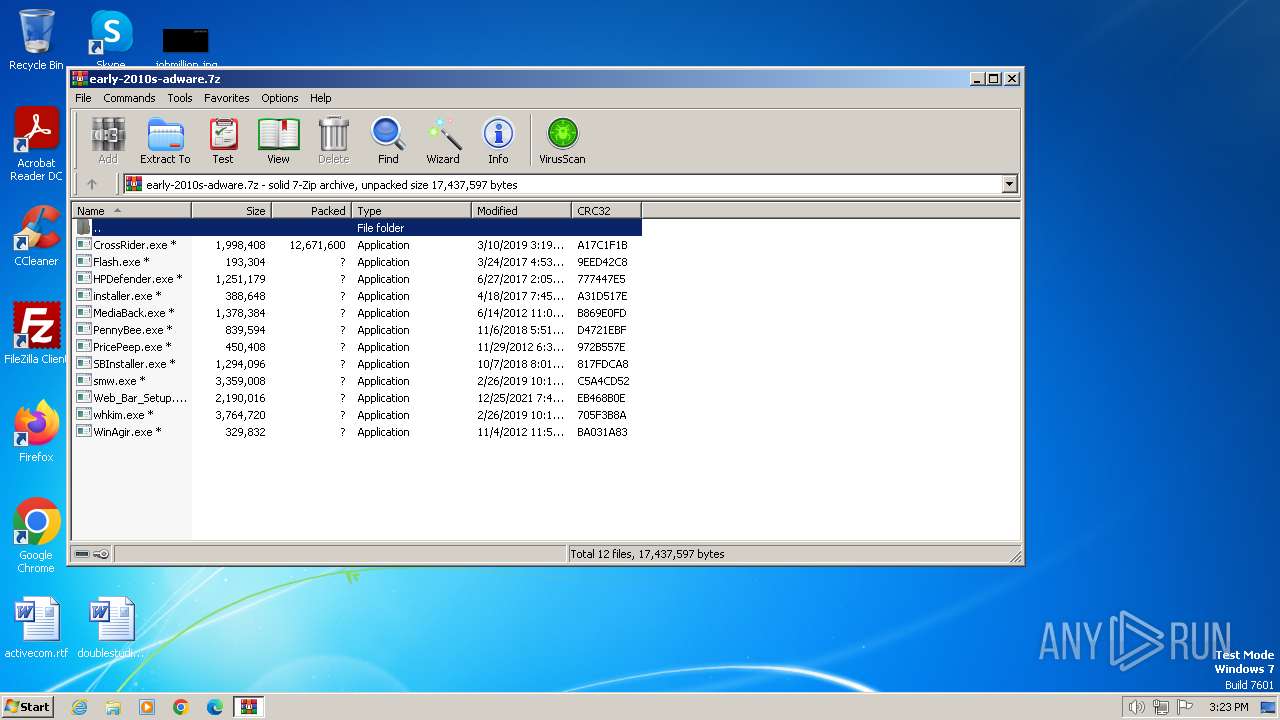
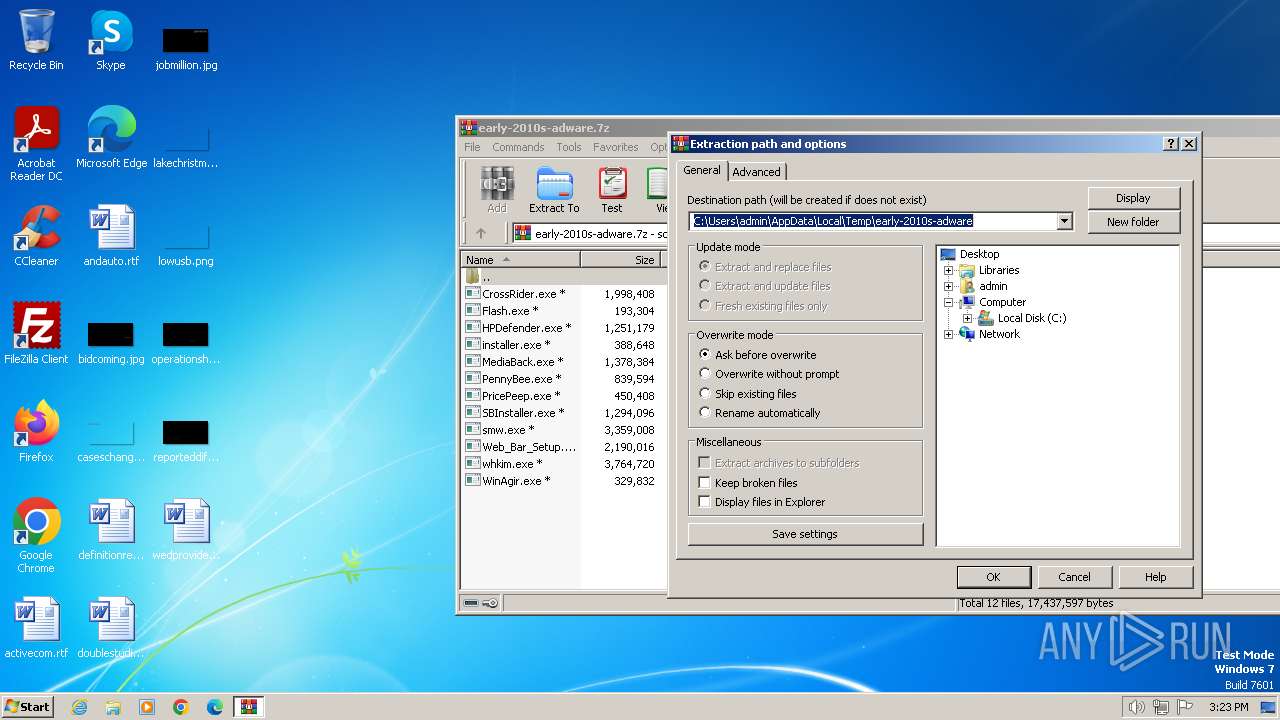
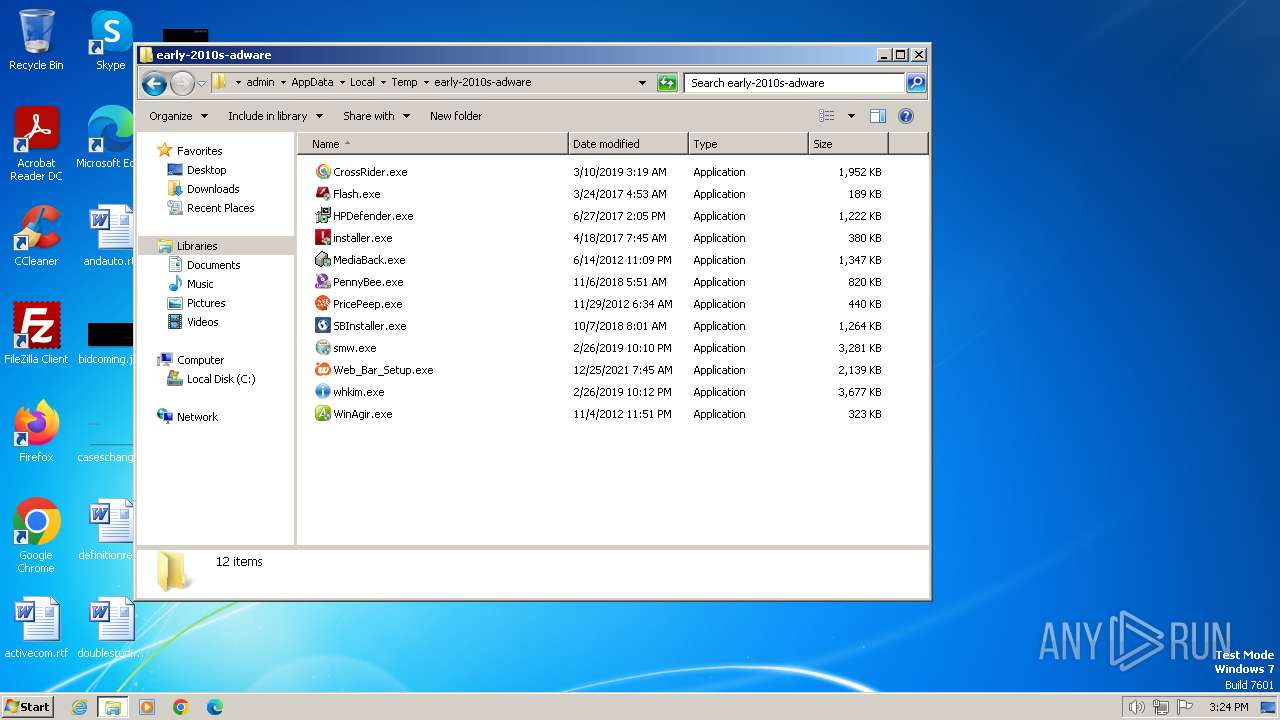
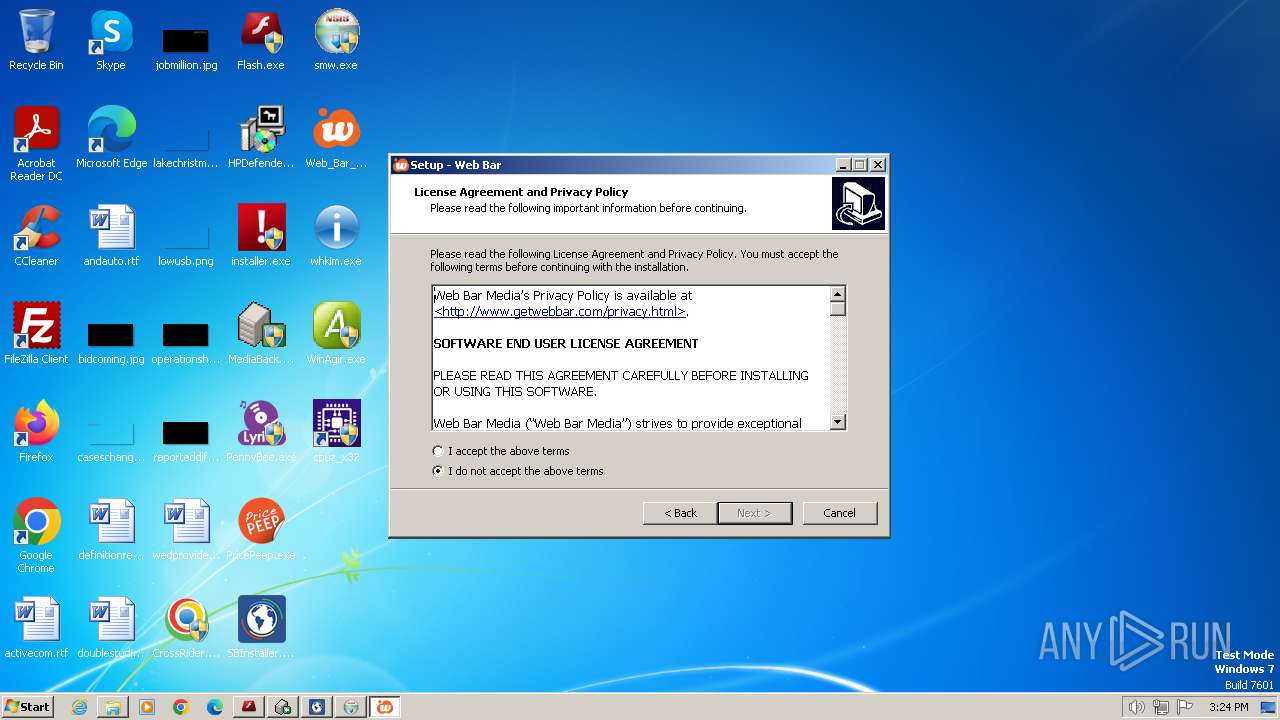
| File name: | early-2010s-adware.7z |
| Full analysis: | https://app.any.run/tasks/77fb8612-545a-4bd6-b903-5f9e638a6845 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2024, 15:22:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C0137B76D986D63D1A96C8E4E2266E05 |
| SHA1: | 78ECA78558E3F2E23766C76B54B06DC9E99AEA85 |
| SHA256: | F6CA92E7AFE93E719BBE70561A9216A295B92353EA5C6F87D403FB5BAB456184 |
| SSDEEP: | 98304:shBk3pQNTEvtsQdxHymmZT3IfgTdp1mJxRwFqlWv5ueaw8dS+C0S+1Fpuh5GL+SG:QfVE3sTN8M2MT0b45UESDYawSHI |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3668)
- HPDefender.exe (PID: 968)
- MediaBack.exe (PID: 480)
- PricePeep.exe (PID: 3528)
- SBInstaller.exe (PID: 3036)
- PennyBee.exe (PID: 316)
- Web_Bar_Setup.exe (PID: 3312)
- smw.exe (PID: 1592)
- PricePeep.exe (PID: 2024)
- Web_Bar_Setup.exe (PID: 548)
- WinAgir.exe (PID: 3564)
- Web_Bar_Setup.tmp (PID: 2448)
- CrossRider.exe (PID: 2256)
- 781.exe (PID: 956)
- wb.exe (PID: 2576)
- wb.exe (PID: 3356)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- WinAgir.exe (PID: 3056)
- PricePeep.exe (PID: 3956)
- PricePeep.exe (PID: 3104)
- HPDefender.exe (PID: 912)
Changes the autorun value in the registry
- CpuzApp.exe (PID: 3504)
- SBInstaller.exe (PID: 3036)
- CpuzApp.exe (PID: 3124)
Actions looks like stealing of personal data
- PricePeep.exe (PID: 2024)
- smu.exe (PID: 2832)
- smu.exe (PID: 3768)
Connects to the CnC server
- PricePeep.exe (PID: 2024)
- wb.exe (PID: 3356)
- PricePeep.exe (PID: 3104)
Steals credentials from Web Browsers
- smu.exe (PID: 2832)
- smu.exe (PID: 3768)
Changes the AppInit_DLLs value (autorun option)
- smu.exe (PID: 3768)
Starts CMD.EXE for self-deleting
- smw.exe (PID: 1592)
Creates a writable file in the system directory
- winaux.exe (PID: 3228)
- MediaBack.exe (PID: 480)
Opens an HTTP connection (SCRIPT)
- lyricsgizm.exe (PID: 896)
Creates internet connection object (SCRIPT)
- lyricsgizm.exe (PID: 896)
Sends HTTP request (SCRIPT)
- lyricsgizm.exe (PID: 896)
Create files in the Startup directory
- Flash.exe (PID: 3952)
SUSPICIOUS
Executable content was dropped or overwritten
- HPDefender.exe (PID: 968)
- MediaBack.exe (PID: 480)
- PricePeep.exe (PID: 3528)
- SBInstaller.exe (PID: 3036)
- PennyBee.exe (PID: 316)
- smw.exe (PID: 1592)
- PricePeep.exe (PID: 2024)
- Web_Bar_Setup.exe (PID: 3312)
- Web_Bar_Setup.exe (PID: 548)
- WinAgir.exe (PID: 3564)
- Web_Bar_Setup.tmp (PID: 2448)
- CrossRider.exe (PID: 2256)
- 781.exe (PID: 956)
- wb.exe (PID: 2576)
- wb.exe (PID: 3356)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- WinAgir.exe (PID: 3056)
- PricePeep.exe (PID: 3956)
- PricePeep.exe (PID: 3104)
- HPDefender.exe (PID: 912)
Malware-specific behavior (creating "System.dll" in Temp)
- SBInstaller.exe (PID: 3036)
- PennyBee.exe (PID: 316)
- smw.exe (PID: 1592)
- PricePeep.exe (PID: 2024)
- WinAgir.exe (PID: 3564)
- MediaBack.exe (PID: 480)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- WinAgir.exe (PID: 3056)
- PricePeep.exe (PID: 3104)
The process creates files with name similar to system file names
- SBInstaller.exe (PID: 3036)
- PennyBee.exe (PID: 316)
- smw.exe (PID: 1592)
- PricePeep.exe (PID: 2024)
- WinAgir.exe (PID: 3564)
- Web_Bar_Setup.tmp (PID: 2448)
- wb.exe (PID: 2576)
- wb.exe (PID: 3356)
- smu.exe (PID: 3768)
- MediaBack.exe (PID: 480)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- WinAgir.exe (PID: 3056)
- PricePeep.exe (PID: 3104)
Reads the Internet Settings
- PennyBee.exe (PID: 316)
- PricePeep.exe (PID: 2024)
- lyricsgizm.exe (PID: 2476)
- WinAgir.exe (PID: 3564)
- 781.exe (PID: 956)
- wbsvc.exe (PID: 2160)
- smu.exe (PID: 2832)
- wb.exe (PID: 2576)
- smw.exe (PID: 1592)
- Your.exe (PID: 696)
- lyricsgizm.exe (PID: 896)
- wbsvc.exe (PID: 1848)
- wb.exe (PID: 3356)
- dopeload.exe (PID: 3636)
- Flash.exe (PID: 3952)
- smu.exe (PID: 2732)
- wscript.exe (PID: 2472)
- PricePeep.exe (PID: 3104)
Reads security settings of Internet Explorer
- PennyBee.exe (PID: 316)
- PricePeep.exe (PID: 2024)
- WinAgir.exe (PID: 3564)
- 781.exe (PID: 956)
- wbsvc.exe (PID: 2160)
- smu.exe (PID: 2832)
- smw.exe (PID: 1592)
- smu.exe (PID: 3768)
- sma.exe (PID: 3588)
- sma.exe (PID: 1880)
- sma.exe (PID: 2780)
- sma.exe (PID: 3772)
- Your.exe (PID: 696)
- winaux.exe (PID: 3228)
- lyricsgizm.exe (PID: 896)
- wbsvc.exe (PID: 1848)
- wb.exe (PID: 3356)
- dopeload.exe (PID: 3636)
- Flash.exe (PID: 3952)
- PricePeep.exe (PID: 3104)
Application launched itself
- PricePeep.exe (PID: 3528)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 3892)
- cmd.exe (PID: 2372)
- PricePeep.exe (PID: 3956)
Searches for installed software
- PricePeep.exe (PID: 2024)
- CrossRider.exe (PID: 2256)
- 781.exe (PID: 956)
- smu.exe (PID: 3768)
- SBInstaller.exe (PID: 3036)
- Your.exe (PID: 696)
- PricePeep.exe (PID: 3104)
- WinAgir.exe (PID: 3056)
Creates a software uninstall entry
- PricePeep.exe (PID: 2024)
- HPDefender.exe (PID: 968)
- PennyBee.exe (PID: 316)
- WinAgir.exe (PID: 3564)
- Your.exe (PID: 696)
- SBInstaller.exe (PID: 3036)
- smw.exe (PID: 1592)
- MediaBack.exe (PID: 480)
- PricePeep.exe (PID: 3104)
- HPDefender.exe (PID: 912)
Reads the Windows owner or organization settings
- Web_Bar_Setup.tmp (PID: 2448)
- MediaBack.exe (PID: 480)
Process drops legitimate windows executable
- Web_Bar_Setup.tmp (PID: 2448)
Checks for Java to be installed
- ISightHost.exe (PID: 3108)
- ISightHost.exe (PID: 2172)
- ISightHost.exe (PID: 2800)
Creates/Modifies COM task schedule object
- PricePeep.exe (PID: 2024)
- WinAgir.exe (PID: 3564)
Checks Windows Trust Settings
- WinAgir.exe (PID: 3564)
- wbsvc.exe (PID: 2160)
- winaux.exe (PID: 3228)
- wb.exe (PID: 3356)
- Flash.exe (PID: 3952)
Reads settings of System Certificates
- WinAgir.exe (PID: 3564)
- wbsvc.exe (PID: 2160)
- wb.exe (PID: 3356)
- Flash.exe (PID: 3952)
Executes as Windows Service
- winaux.exe (PID: 3228)
- smu.exe (PID: 3768)
Starts itself from another location
- CrossRider.exe (PID: 2256)
The process executes via Task Scheduler
- lyricsgizm.exe (PID: 3068)
- wscript.exe (PID: 2472)
Drops a system driver (possible attempt to evade defenses)
- smw.exe (PID: 1592)
Starts application with an unusual extension
- smw.exe (PID: 1592)
Starts CMD.EXE for commands execution
- ns9564.tmp (PID: 3416)
- nsA66D.tmp (PID: 3348)
- nsABAD.tmp (PID: 2792)
- nsAE3F.tmp (PID: 2160)
- smw.exe (PID: 1592)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 2372)
- cmd.exe (PID: 3892)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 2072)
Starts SC.EXE for service management
- smw.exe (PID: 1592)
Creates FileSystem object to access computer's file system (SCRIPT)
- smp.exe (PID: 2036)
- smp.exe (PID: 2712)
Checks whether a specific file exists (SCRIPT)
- smp.exe (PID: 2036)
- smp.exe (PID: 2712)
Reads Microsoft Outlook installation path
- Your.exe (PID: 696)
- wb.exe (PID: 3356)
- lyricsgizm.exe (PID: 896)
Changes Internet Explorer settings (feature browser emulation)
- Your.exe (PID: 696)
- wb.exe (PID: 3356)
Creates a Folder object (SCRIPT)
- smp.exe (PID: 2712)
Reads the date of Windows installation
- smp.exe (PID: 2712)
Reads Internet Explorer settings
- Your.exe (PID: 696)
- wb.exe (PID: 3356)
- lyricsgizm.exe (PID: 896)
Process requests binary or script from the Internet
- Your.exe (PID: 696)
- Flash.exe (PID: 3952)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2396)
Detected use of alternative data streams (AltDS)
- smu.exe (PID: 3768)
Changes the title of the Internet Explorer window
- Flash.exe (PID: 3952)
- iexplore.exe (PID: 2876)
Changes the Home page of Internet Explorer
- Flash.exe (PID: 3952)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2472)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 2472)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3668)
Manual execution by a user
- Flash.exe (PID: 2592)
- installer.exe (PID: 2384)
- explorer.exe (PID: 3732)
- HPDefender.exe (PID: 968)
- Flash.exe (PID: 3980)
- MediaBack.exe (PID: 1784)
- installer.exe (PID: 844)
- MediaBack.exe (PID: 480)
- PennyBee.exe (PID: 3556)
- PricePeep.exe (PID: 3528)
- SBInstaller.exe (PID: 3036)
- PennyBee.exe (PID: 316)
- smw.exe (PID: 2348)
- smw.exe (PID: 1592)
- Web_Bar_Setup.exe (PID: 3312)
- whkim.exe (PID: 2984)
- WinAgir.exe (PID: 3132)
- WinAgir.exe (PID: 3564)
- CrossRider.exe (PID: 3936)
- CrossRider.exe (PID: 2256)
- installer.exe (PID: 2532)
- installer.exe (PID: 3080)
- Flash.exe (PID: 3156)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- WinAgir.exe (PID: 3548)
- PricePeep.exe (PID: 3956)
- WinAgir.exe (PID: 3056)
- HPDefender.exe (PID: 912)
- installer.exe (PID: 3444)
- installer.exe (PID: 2496)
Checks supported languages
- Flash.exe (PID: 3980)
- HPDefender.exe (PID: 968)
- installer.exe (PID: 844)
- MediaBack.exe (PID: 480)
- PennyBee.exe (PID: 316)
- PricePeep.exe (PID: 3528)
- SBInstaller.exe (PID: 3036)
- CpuzApp.exe (PID: 3504)
- Web_Bar_Setup.exe (PID: 3312)
- smw.exe (PID: 1592)
- whkim.exe (PID: 2984)
- PricePeep.exe (PID: 2024)
- Web_Bar_Setup.exe (PID: 548)
- WinAgir.exe (PID: 3564)
- Web_Bar_Setup.tmp (PID: 3900)
- Web_Bar_Setup.tmp (PID: 2448)
- ISightHost.exe (PID: 3108)
- java.exe (PID: 2104)
- java.exe (PID: 3052)
- CpuzApp.exe (PID: 3296)
- lyricsgizm.exe (PID: 2476)
- winaux.exe (PID: 2940)
- winaux.exe (PID: 3156)
- winaux.exe (PID: 3932)
- winaux.exe (PID: 3944)
- winaux.exe (PID: 3228)
- CrossRider.exe (PID: 2256)
- 781.exe (PID: 956)
- lyricsgizm.exe (PID: 3068)
- wbsvc.exe (PID: 2160)
- smu.exe (PID: 2832)
- wb.exe (PID: 2576)
- ns9564.tmp (PID: 3416)
- java.exe (PID: 1840)
- smu.exe (PID: 3768)
- ISightHost.exe (PID: 2172)
- java.exe (PID: 2468)
- sma.exe (PID: 3588)
- sma.exe (PID: 1880)
- sma.exe (PID: 2780)
- nsA66D.tmp (PID: 3348)
- smp.exe (PID: 2036)
- sma.exe (PID: 3772)
- nsABAD.tmp (PID: 2792)
- Your.exe (PID: 696)
- smi32.exe (PID: 2500)
- nsAE3F.tmp (PID: 2160)
- smp.exe (PID: 1644)
- smp.exe (PID: 2712)
- smi32.exe (PID: 2660)
- lyricsgizm.exe (PID: 896)
- wbsvc.exe (PID: 1848)
- ISightHost.exe (PID: 2800)
- wb.exe (PID: 3356)
- java.exe (PID: 3936)
- java.exe (PID: 912)
- winaspi32.exe (PID: 2072)
- dopeload.exe (PID: 3636)
- dopewars.exe (PID: 2640)
- dopewars.exe (PID: 3496)
- installer.exe (PID: 3080)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- smu.exe (PID: 2732)
- WinAgir.exe (PID: 3056)
- PricePeep.exe (PID: 3956)
- PricePeep.exe (PID: 3104)
- HPDefender.exe (PID: 912)
- CpuzApp.exe (PID: 3124)
- installer.exe (PID: 2496)
- smi32.exe (PID: 3464)
- CpuzApp.exe (PID: 980)
- smi32.exe (PID: 2544)
- smi32.exe (PID: 2172)
Reads the computer name
- HPDefender.exe (PID: 968)
- Flash.exe (PID: 3980)
- PennyBee.exe (PID: 316)
- PricePeep.exe (PID: 3528)
- SBInstaller.exe (PID: 3036)
- CpuzApp.exe (PID: 3504)
- smw.exe (PID: 1592)
- PricePeep.exe (PID: 2024)
- Web_Bar_Setup.tmp (PID: 3900)
- WinAgir.exe (PID: 3564)
- Web_Bar_Setup.tmp (PID: 2448)
- ISightHost.exe (PID: 3108)
- CpuzApp.exe (PID: 3296)
- lyricsgizm.exe (PID: 2476)
- winaux.exe (PID: 2940)
- winaux.exe (PID: 3932)
- winaux.exe (PID: 3944)
- winaux.exe (PID: 3228)
- winaux.exe (PID: 3156)
- CrossRider.exe (PID: 2256)
- 781.exe (PID: 956)
- lyricsgizm.exe (PID: 3068)
- wbsvc.exe (PID: 2160)
- smu.exe (PID: 2832)
- wb.exe (PID: 2576)
- ISightHost.exe (PID: 2172)
- sma.exe (PID: 3588)
- sma.exe (PID: 2780)
- sma.exe (PID: 1880)
- smu.exe (PID: 3768)
- sma.exe (PID: 3772)
- smp.exe (PID: 2036)
- Your.exe (PID: 696)
- smp.exe (PID: 2712)
- smp.exe (PID: 1644)
- lyricsgizm.exe (PID: 896)
- wbsvc.exe (PID: 1848)
- wb.exe (PID: 3356)
- ISightHost.exe (PID: 2800)
- MediaBack.exe (PID: 480)
- dopewars.exe (PID: 2640)
- dopeload.exe (PID: 3636)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- smu.exe (PID: 2732)
- WinAgir.exe (PID: 3056)
- PricePeep.exe (PID: 3956)
- PricePeep.exe (PID: 3104)
- HPDefender.exe (PID: 912)
- CpuzApp.exe (PID: 3124)
- CpuzApp.exe (PID: 980)
Create files in a temporary directory
- HPDefender.exe (PID: 968)
- MediaBack.exe (PID: 480)
- PennyBee.exe (PID: 316)
- PricePeep.exe (PID: 3528)
- SBInstaller.exe (PID: 3036)
- Web_Bar_Setup.exe (PID: 3312)
- smw.exe (PID: 1592)
- Web_Bar_Setup.exe (PID: 548)
- WinAgir.exe (PID: 3564)
- Web_Bar_Setup.tmp (PID: 2448)
- ISightHost.exe (PID: 3108)
- java.exe (PID: 2104)
- PricePeep.exe (PID: 2024)
- java.exe (PID: 3052)
- 781.exe (PID: 956)
- CrossRider.exe (PID: 2256)
- wb.exe (PID: 2576)
- ISightHost.exe (PID: 2172)
- java.exe (PID: 2468)
- java.exe (PID: 1840)
- wb.exe (PID: 3356)
- ISightHost.exe (PID: 2800)
- java.exe (PID: 3936)
- java.exe (PID: 912)
- winaspi32.exe (PID: 2072)
- dopeload.exe (PID: 3636)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- WinAgir.exe (PID: 3056)
- PricePeep.exe (PID: 3956)
- PricePeep.exe (PID: 3104)
- HPDefender.exe (PID: 912)
Process checks whether UAC notifications are on
- PricePeep.exe (PID: 3528)
- PricePeep.exe (PID: 3956)
Reads the machine GUID from the registry
- SBInstaller.exe (PID: 3036)
- PennyBee.exe (PID: 316)
- PricePeep.exe (PID: 2024)
- Web_Bar_Setup.tmp (PID: 2448)
- ISightHost.exe (PID: 3108)
- lyricsgizm.exe (PID: 2476)
- WinAgir.exe (PID: 3564)
- 781.exe (PID: 956)
- lyricsgizm.exe (PID: 3068)
- wbsvc.exe (PID: 2160)
- smu.exe (PID: 2832)
- wb.exe (PID: 2576)
- ISightHost.exe (PID: 2172)
- smu.exe (PID: 3768)
- sma.exe (PID: 3588)
- sma.exe (PID: 1880)
- sma.exe (PID: 3772)
- smp.exe (PID: 2036)
- sma.exe (PID: 2780)
- Your.exe (PID: 696)
- smp.exe (PID: 1644)
- smp.exe (PID: 2712)
- winaux.exe (PID: 3228)
- lyricsgizm.exe (PID: 896)
- ISightHost.exe (PID: 2800)
- wb.exe (PID: 3356)
- winaspi32.exe (PID: 2072)
- dopeload.exe (PID: 3636)
- Flash.exe (PID: 3952)
- SBInstaller.exe (PID: 3984)
- smu.exe (PID: 2732)
- PricePeep.exe (PID: 3104)
Creates files or folders in the user directory
- HPDefender.exe (PID: 968)
- PricePeep.exe (PID: 2024)
- PennyBee.exe (PID: 316)
- WinAgir.exe (PID: 3564)
- 781.exe (PID: 956)
- wb.exe (PID: 2576)
- SBInstaller.exe (PID: 3036)
- Your.exe (PID: 696)
- smp.exe (PID: 2712)
- wb.exe (PID: 3356)
- lyricsgizm.exe (PID: 896)
- Flash.exe (PID: 3952)
- PricePeep.exe (PID: 3104)
Creates files in the program directory
- PennyBee.exe (PID: 316)
- java.exe (PID: 2104)
- PricePeep.exe (PID: 2024)
- WinAgir.exe (PID: 3564)
- smw.exe (PID: 1592)
- wbsvc.exe (PID: 2160)
- Web_Bar_Setup.tmp (PID: 2448)
- smu.exe (PID: 2832)
- wb.exe (PID: 2576)
- smp.exe (PID: 2712)
- MediaBack.exe (PID: 480)
- dopewars.exe (PID: 2640)
- Flash.exe (PID: 3952)
Checks proxy server information
- PennyBee.exe (PID: 316)
- PricePeep.exe (PID: 2024)
- lyricsgizm.exe (PID: 2476)
- WinAgir.exe (PID: 3564)
- 781.exe (PID: 956)
- lyricsgizm.exe (PID: 3068)
- smu.exe (PID: 2832)
- sma.exe (PID: 3588)
- sma.exe (PID: 2780)
- sma.exe (PID: 1880)
- smu.exe (PID: 3768)
- sma.exe (PID: 3772)
- Your.exe (PID: 696)
- winaux.exe (PID: 3228)
- lyricsgizm.exe (PID: 896)
- wb.exe (PID: 3356)
- Flash.exe (PID: 3952)
- smu.exe (PID: 2732)
- PricePeep.exe (PID: 3104)
Reads the software policy settings
- WinAgir.exe (PID: 3564)
- wbsvc.exe (PID: 2160)
- winaux.exe (PID: 3228)
- wb.exe (PID: 3356)
- Flash.exe (PID: 3952)
Creates a software uninstall entry
- Web_Bar_Setup.tmp (PID: 2448)
Reads Environment values
- wb.exe (PID: 2576)
- smw.exe (PID: 1592)
- smp.exe (PID: 2036)
- Your.exe (PID: 696)
- smp.exe (PID: 2712)
- lyricsgizm.exe (PID: 896)
- wb.exe (PID: 3356)
Reads product name
- Your.exe (PID: 696)
Application launched itself
- msedge.exe (PID: 3760)
- iexplore.exe (PID: 2876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
210
Monitored processes
116
Malicious processes
29
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Users\admin\Desktop\PennyBee.exe" | C:\Users\admin\Desktop\PennyBee.exe | explorer.exe | ||||||||||||
User: admin Company: lyricsgizm Integrity Level: HIGH Description: Main Installer Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 480 | "C:\Users\admin\Desktop\MediaBack.exe" | C:\Users\admin\Desktop\MediaBack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\Desktop\Web_Bar_Setup.exe" /SPAWNWND=$20278 /NOTIFYWND=$801EE | C:\Users\admin\Desktop\Web_Bar_Setup.exe | Web_Bar_Setup.tmp | ||||||||||||
User: admin Company: Web Bar Media Integrity Level: HIGH Description: Web Bar Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 572 | "C:\Program Files\Microsoft\Edge\Application\109.0.1518.115\BHO\ie_to_edge_stub.exe" --create-cache-container=0 | C:\Program Files\Microsoft\Edge\Application\109.0.1518.115\BHO\ie_to_edge_stub.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IEToEdge BHO Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 696 | "C:\Users\admin\AppData\Local\Your\Your.exe" /firstrun | C:\Users\admin\AppData\Local\Your\Your.exe | SBInstaller.exe | ||||||||||||
User: admin Company: Springtech LTD Integrity Level: MEDIUM Description: Desktop web search Exit code: 0 Version: 2.29.0.24 Modules
| |||||||||||||||
| 844 | "C:\Users\admin\Desktop\installer.exe" | C:\Users\admin\Desktop\installer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Installer Exit code: 4294967295 Version: 1.0.0.1 Modules
| |||||||||||||||
| 896 | C:\ProgramData\lyricsgizm\lyricsgizm.exe | C:\ProgramData\lyricsgizm\lyricsgizm.exe | PennyBee.exe | ||||||||||||
User: admin Company: Video Song Gizmos Agent Integrity Level: HIGH Exit code: 0 Version: 1.1.0.12 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Java\jre1.8.0_271\bin\java.exe" -version | C:\Program Files\Java\jre1.8.0_271\bin\java.exe | — | ISightHost.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 912 | "C:\Users\admin\Desktop\HPDefender.exe" | C:\Users\admin\Desktop\HPDefender.exe | explorer.exe | ||||||||||||
User: admin Company: so near with their lips Integrity Level: MEDIUM Description: together. Villanous thoughts Exit code: 0 Version: 15.21.597.6931 Modules
| |||||||||||||||
| 956 | "C:\Users\admin\AppData\Local\Temp\\781.exe" /asru | C:\Users\admin\AppData\Local\Temp\781.exe | CrossRider.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 106.0.0.0 Modules
| |||||||||||||||
Total events
184 663
Read events
181 031
Write events
3 005
Delete events
627
Modification events
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\early-2010s-adware.7z | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
122
Suspicious files
137
Text files
256
Unknown types
65
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\HPDefender.exe | executable | |
MD5:CEAEFFC316D1D952E34611E7DFC60FAD | SHA256:581F39631897307665AFC5F9F343EE25468E81967B8D2B8706C76067E9DF3338 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\PennyBee.exe | executable | |
MD5:CE82328636D917085664F07AE6767EF5 | SHA256:A304949D56D4664B807A02D60243122DD59804F1AE0BBD49AFD02B189CA1DDDC | |||
| 968 | HPDefender.exe | C:\Users\admin\AppData\Local\Temp\nsu15E3.tmp\nsProcess.dll | executable | |
MD5:F0438A894F3A7E01A4AAE8D1B5DD0289 | SHA256:30C6C3DD3CC7FCEA6E6081CE821ADC7B2888542DAE30BF00E881C0A105EB4D11 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\CrossRider.exe | executable | |
MD5:C359B1996E911B652B42011BD6BBFD87 | SHA256:0CAE1EF0A97EAE1E8F061E9015FCDE96B48E7F8491FD70534B5E373B87EB4B4C | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\installer.exe | executable | |
MD5:E9C54F04632871BF5D429964B53CA1E1 | SHA256:ECD061BB175898879DDE68CA11AD1EA9FA6D52E334CC3A78AC70DC37A1AE8E5F | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\PricePeep.exe | executable | |
MD5:115E8A3579B3435C12B22E566BB0E123 | SHA256:7E1DA0C43606EF23B71CADE66246FC53458D363DDD86D31EE6F55569585FC901 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\MediaBack.exe | executable | |
MD5:FB2410A9A356327D16650B3B97F61DAA | SHA256:2348AE8EF84FF79518BE22686D58987909924662843958340F33169E26FCB081 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\Flash.exe | executable | |
MD5:D1BAFC44D0D9E573758172F45694DBA1 | SHA256:A2BA2E085F7475517068AE95927A3762455AF72323B50834D2E9EA26ABE416AA | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\smw.exe | executable | |
MD5:5F146F30856087B52E39BE7072A125FE | SHA256:E0410A686B08042A01B81D2EB53E938DAC59D2F049766BD5AEF8B1CB66B96062 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\early-2010s-adware\whkim.exe | executable | |
MD5:2BCE4A069AB5B4CA54C1B97B2E79049E | SHA256:D4BAEFEA68D19D86A1DB175693EAB4D60798380117CCECCDFF8258E547D02050 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
70
TCP/UDP connections
185
DNS requests
99
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2024 | PricePeep.exe | GET | 302 | 77.247.179.84:80 | http://rpt.myshopres.com/reporter/JSReport.aspx?distributorid=50001&channelid=1&builddate=1337842865&clientversion=2.1.0.12&reportid=1009&browser=all&status=started | unknown | text | 11 b | unknown |
2024 | PricePeep.exe | GET | 200 | 15.197.204.56:80 | http://ww1.myshopres.com/ | unknown | html | 524 b | unknown |
2024 | PricePeep.exe | GET | 200 | 77.247.179.84:80 | http://rpt.myshopres.com/reporter/JSReport.aspx?distributorid=50001&channelid=1&builddate=1337842865&clientversion=2.1.0.12&reportid=1009&browser=all&status=completedSuccessfully | unknown | html | 631 b | unknown |
3564 | WinAgir.exe | GET | 301 | 199.36.158.100:80 | http://www.pluginsoft.co.kr/config/auto_config.txt | unknown | — | — | unknown |
3564 | WinAgir.exe | GET | 304 | 184.24.77.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e89b961cac9375f3 | unknown | — | — | unknown |
3564 | WinAgir.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
3564 | WinAgir.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3564 | WinAgir.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/s/gts1d4/qJZQFfzliN8/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQC0buZPqCMjDRJuu2GSFUg7 | unknown | binary | 472 b | unknown |
956 | 781.exe | GET | 302 | 93.115.28.104:80 | http://ipgeoapi.com/ | unknown | text | 11 b | unknown |
956 | 781.exe | GET | 200 | 199.59.243.225:80 | http://survey-smiles.com/ | unknown | html | 1.03 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2024 | PricePeep.exe | 77.247.179.84:80 | rpt.myshopres.com | NForce Entertainment B.V. | NL | unknown |
2024 | PricePeep.exe | 15.197.204.56:80 | ww1.myshopres.com | AMAZON-02 | US | unknown |
3564 | WinAgir.exe | 199.36.158.100:80 | www.pluginsoft.co.kr | FASTLY | US | unknown |
3564 | WinAgir.exe | 199.36.158.100:443 | www.pluginsoft.co.kr | FASTLY | US | unknown |
3564 | WinAgir.exe | 184.24.77.201:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3564 | WinAgir.exe | 172.217.18.3:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
956 | 781.exe | 93.115.28.104:80 | ipgeoapi.com | UAB Cherry Servers | LT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ws.xcodelib.net |
| unknown |
rpt.myshopres.com |
| unknown |
ww1.myshopres.com |
| unknown |
tracking.instnode.com |
| unknown |
www.pluginsoft.co.kr |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
pluginsoft.co.kr |
| unknown |
ipgeoapi.com |
| unknown |
survey-smiles.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2024 | PricePeep.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2024 | PricePeep.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2024 | PricePeep.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1880 | sma.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
2780 | sma.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
3952 | Flash.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
3104 | PricePeep.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
3104 | PricePeep.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
3356 | wb.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
7 ETPRO signatures available at the full report
Process | Message |
|---|---|
lyricsgizm.exe | 02/18/24 15:24:25 (6843) -~- ProccesId: 2476, ThreadId: 884 -~- OnInitDialog -~- Starting agent process cmdline: "C:\ProgramData\lyricsgizm\lyricsgizm.exe" /InstallOn=0 /closebr=0 /active=24 /update=24 /interval=2880 /pubId=1001 /affId=10010047 /appId=111 /uId={541629DA-2F3B-4262-9DA4-5C952A5A1B35} /version=3.0.0.0 /Override=false /Firstime=1 /IEhome=0 /IEsearch=0 /FFhome=0 /FFsearch=0 /CHhome=0 /CHsearch=0 /FFaddon= /CHaddon= /AutoSP= /regAppName=lyricsgizm /curSID=S-1-5-21-1302019708-1500728564-335382590-1000 /logf=C:\Users\admin\AppData\Local\Temp\lyricsgizm_installer_{541629DA-2F3B-4262-9DA4-5C952A5A1B35}_1708269855.txt /chPol=0 /mac=12A9866C77DE /tst=None
|
lyricsgizm.exe | 02/18/24 15:24:25 (6843) -~- ProccesId: 2476, ThreadId: 884 -~- OnInitDialog -~- First time running
|
lyricsgizm.exe | 02/18/24 15:24:25 (6843) -~- ProccesId: 2476, ThreadId: 884 -~- FirstTimeStat -~- Install starting, sending stats
|
lyricsgizm.exe | 02/18/24 15:24:25 (6859) -~- ProccesId: 2476, ThreadId: 884 -~- SendStats -~- ws.xcodelib.net/ytlyrics/bho/report.php?type=install&sch=4&affId=10010047&pubId=1001&appId=111&agver=1.1.0.12&fferr=scss&chrerr=scss&guid={541629DA-2F3B-4262-9DA4-5C952A5A1B35}&override=false&affIdLast=none&os=6.1&manu=&ff=115.0.2 (x86 en-US)&ch=109.0.5414.120&ie=11.0.9600.19596&mac=12A9866C77DE&newagnt=0&sltm=0&wktm=27<m=18_02_15_24_25&tst=none&x=112
|
lyricsgizm.exe | 02/18/24 15:24:41 (22765) -~- ProccesId: 2476, ThreadId: 884 -~- SendStats -~- Error 12007 encountered at: Error 0x2ee7 at Failed HttpSendRequest
|
lyricsgizm.exe | 02/18/24 15:24:41 (22765) -~- ProccesId: 2476, ThreadId: 884 -~- UpdateRegistryFromArguments -~- Updating registry
|
lyricsgizm.exe | 02/18/24 15:24:41 (22765) -~- ProccesId: 2476, ThreadId: 884 -~- StartWorkerTasks -~- Starting tasks
|
lyricsgizm.exe | 02/18/24 15:24:45 (26906) -~- ProccesId: 2476, ThreadId: 884 -~- EndInstallStat -~- Install finished, sending stats
|
lyricsgizm.exe | 02/18/24 15:24:45 (26906) -~- ProccesId: 2476, ThreadId: 884 -~- SetTaskComment -~- Comment is: {"regs":{"ffErr":""}}
|
lyricsgizm.exe | 02/18/24 15:24:45 (26906) -~- ProccesId: 2476, ThreadId: 884 -~- SetTaskComment -~- Comment is: {"regs":{"chromeErr":"","ffErr":""}}
|