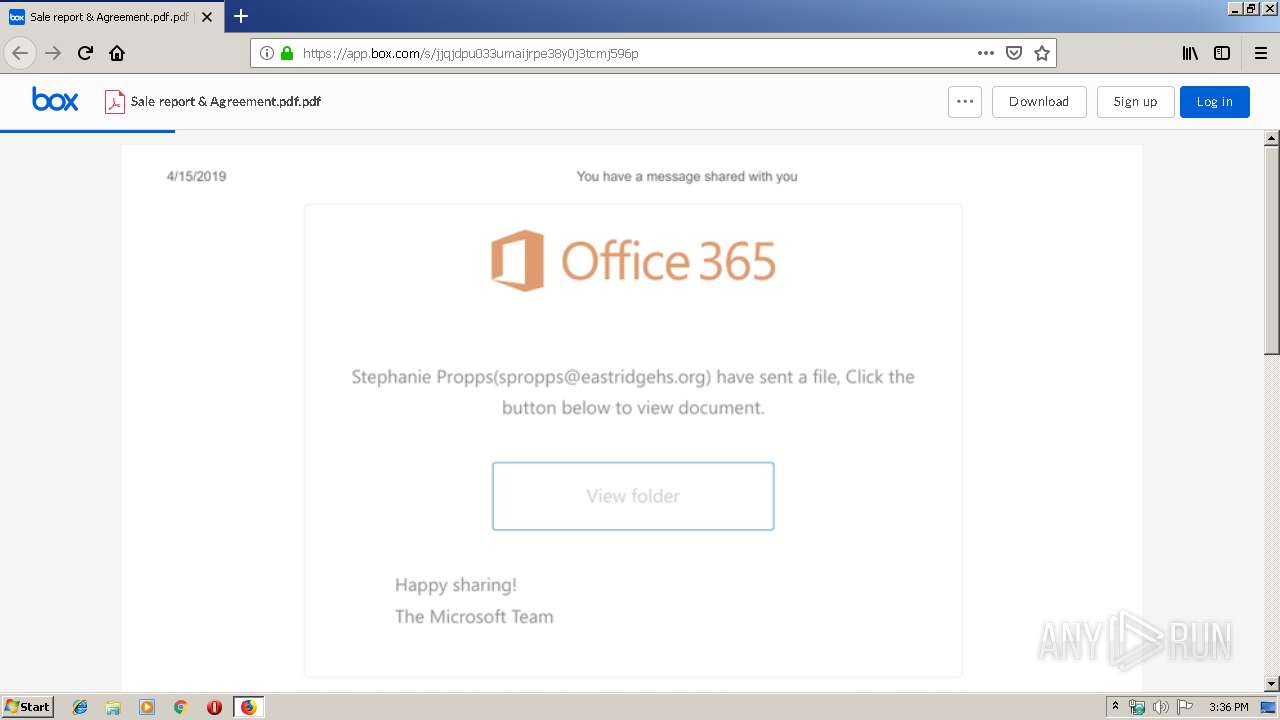
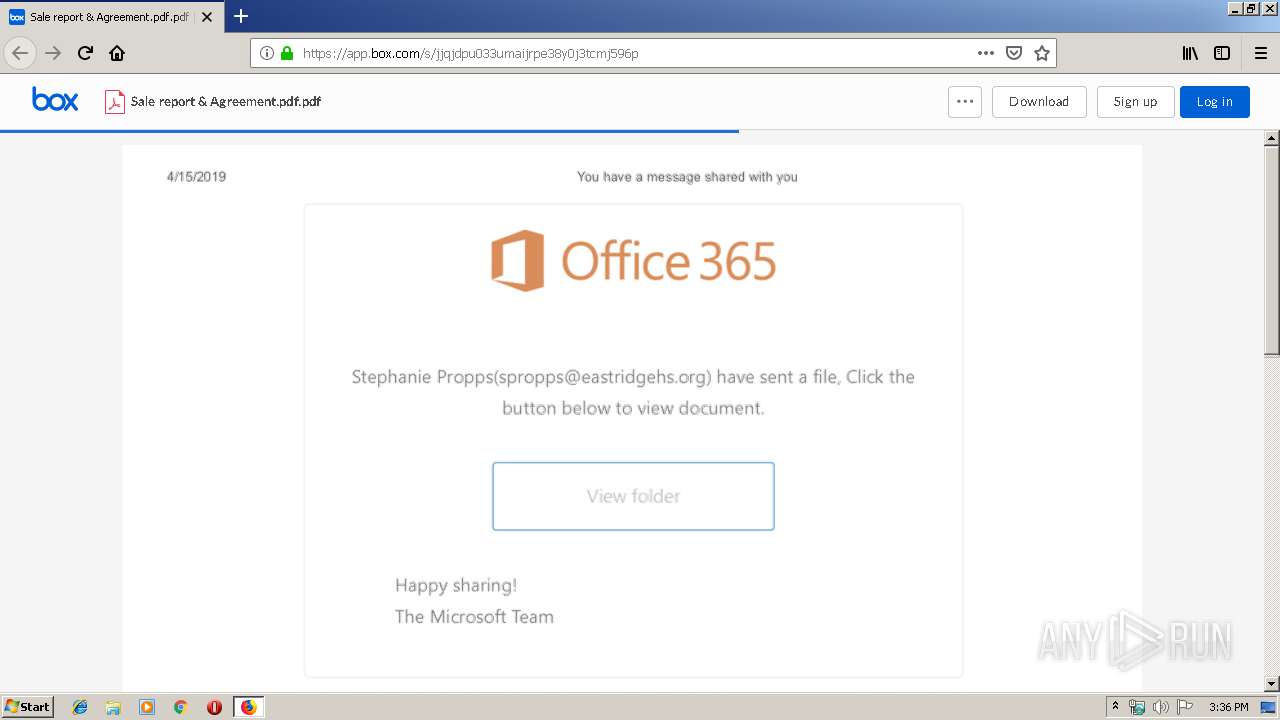
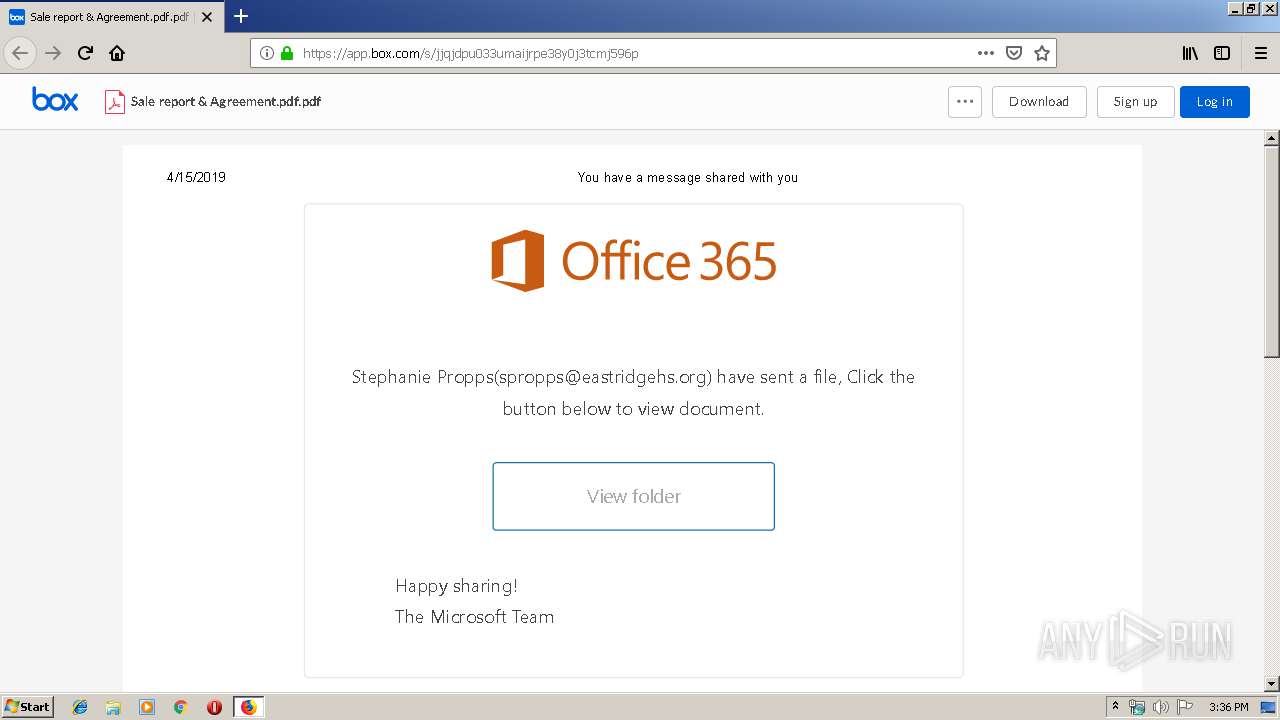
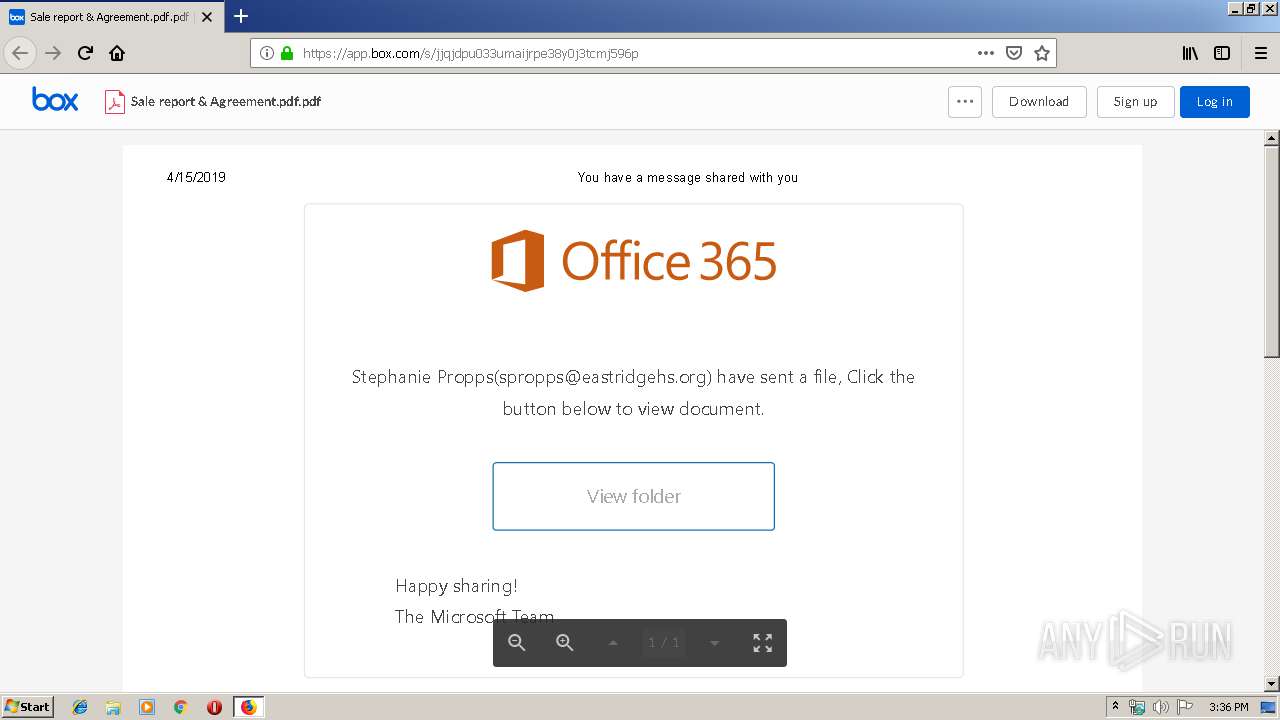
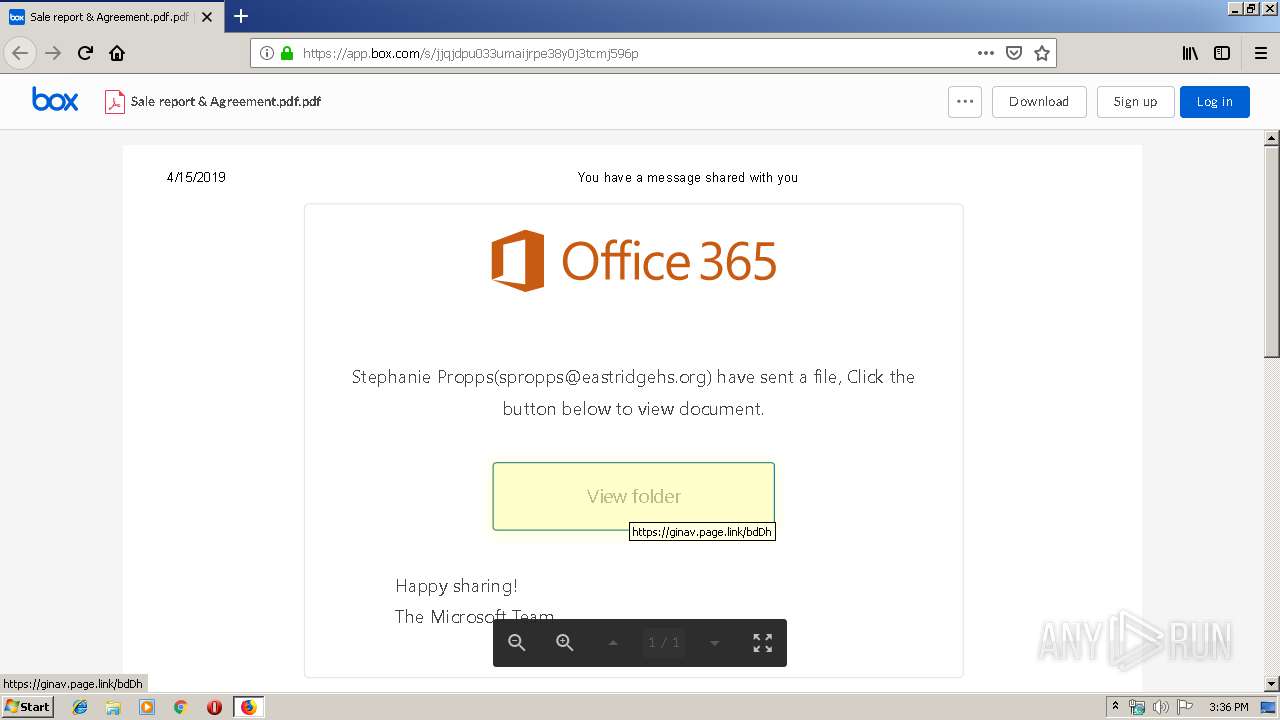
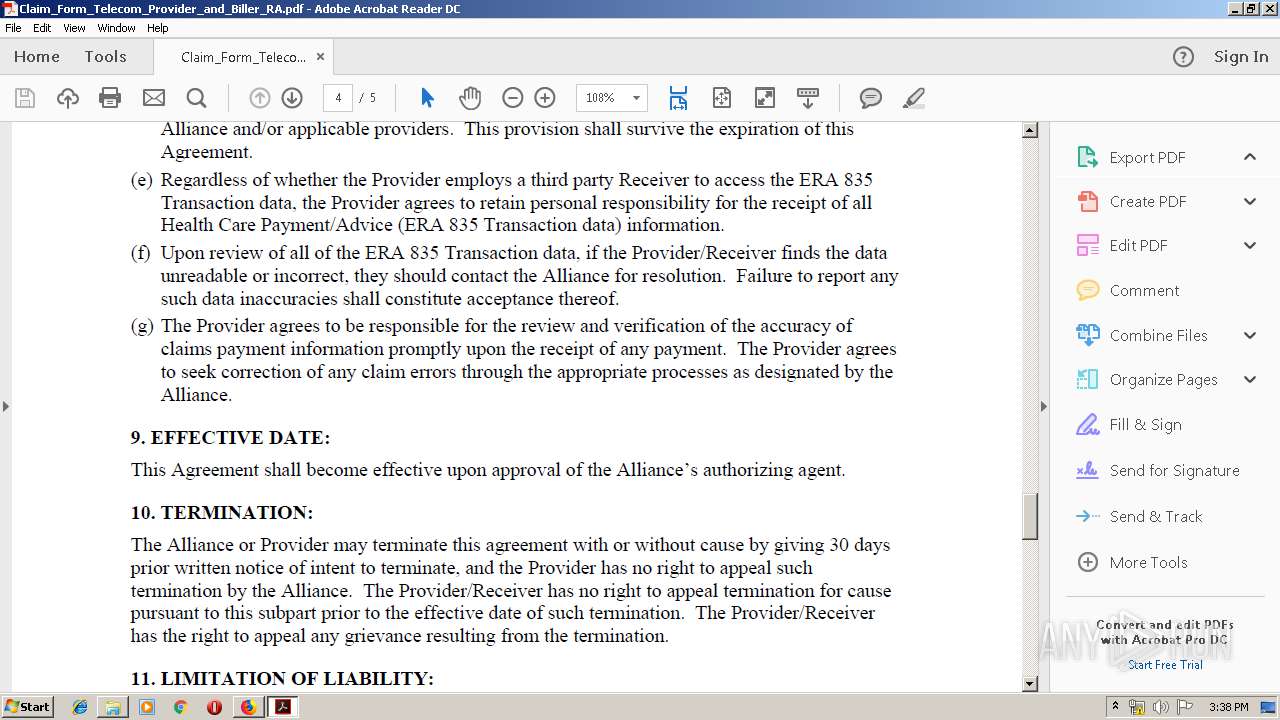
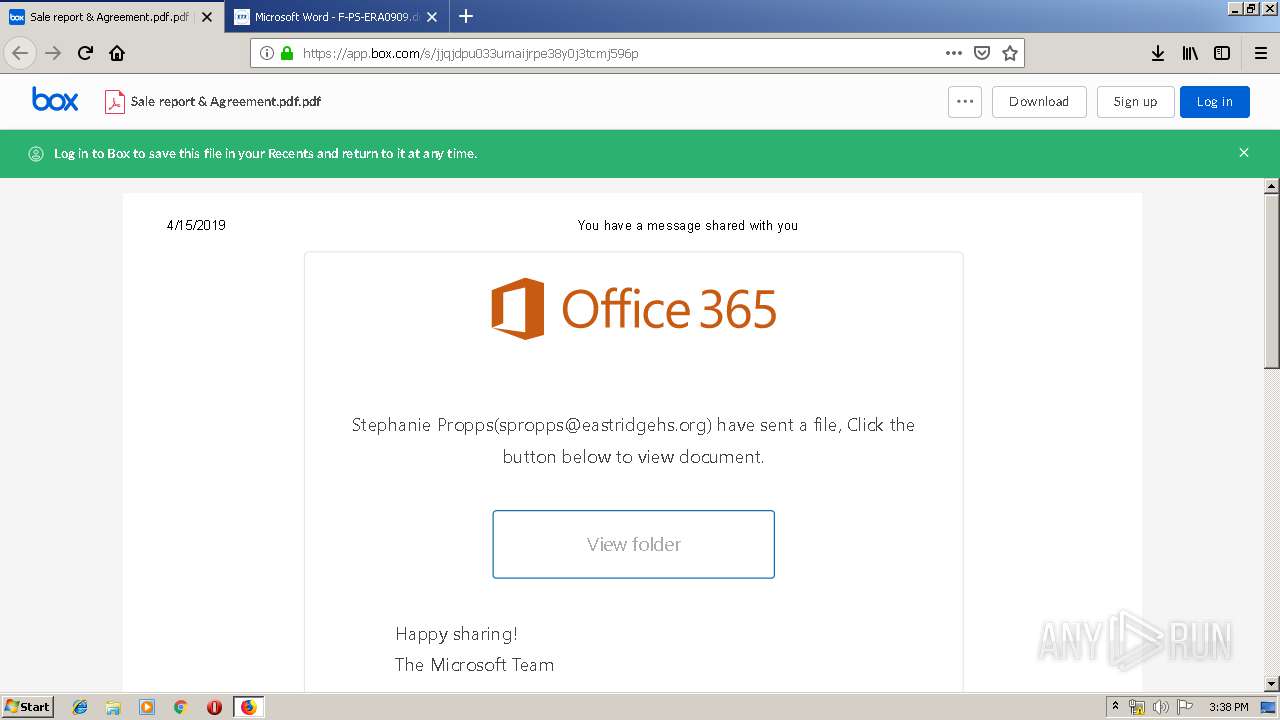
| URL: | https://app.box.com/s/jjqjdpu033umaijrpe38y0j3tcmj596p |
| Full analysis: | https://app.any.run/tasks/4214e172-9065-4b06-9eb5-0921ac44e589 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 14:36:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 08EEABE61BA779EE063FD7DC09D5294B |
| SHA1: | 6563E9E8E4C26BBD16EF67F9334C0FC05085673D |
| SHA256: | F6C32D0DF9E63E4AAC2E6A2C0C9E366F182AD706EED51F4C306D6A81A1CDF412 |
| SSDEEP: | 3:N8aqLdmWU56VRdlleV2P:2aqkT56H5VP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the program directory
- AdobeARM.exe (PID: 676)
INFO
Application launched itself
- firefox.exe (PID: 2836)
- AcroRd32.exe (PID: 2924)
- RdrCEF.exe (PID: 3932)
Reads CPU info
- firefox.exe (PID: 2836)
Creates files in the user directory
- firefox.exe (PID: 2836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
13
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 676 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2836.27.428333166\1300500139" -childID 4 -isForBrowser -prefsHandle 3760 -prefMapHandle 3792 -prefsLen 5978 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2836 "\\.\pipe\gecko-crash-server-pipe.2836" 3804 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 2252 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2836.20.959684223\1414960890" -childID 3 -isForBrowser -prefsHandle 3300 -prefMapHandle 3228 -prefsLen 5824 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2836 "\\.\pipe\gecko-crash-server-pipe.2836" 3472 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3932.0.1881114368\1143653741" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2628 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2836.6.181342058\1211746250" -childID 1 -isForBrowser -prefsHandle 828 -prefMapHandle 1768 -prefsLen 1 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2836 "\\.\pipe\gecko-crash-server-pipe.2836" 1772 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://app.box.com/s/jjqjdpu033umaijrpe38y0j3tcmj596p | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
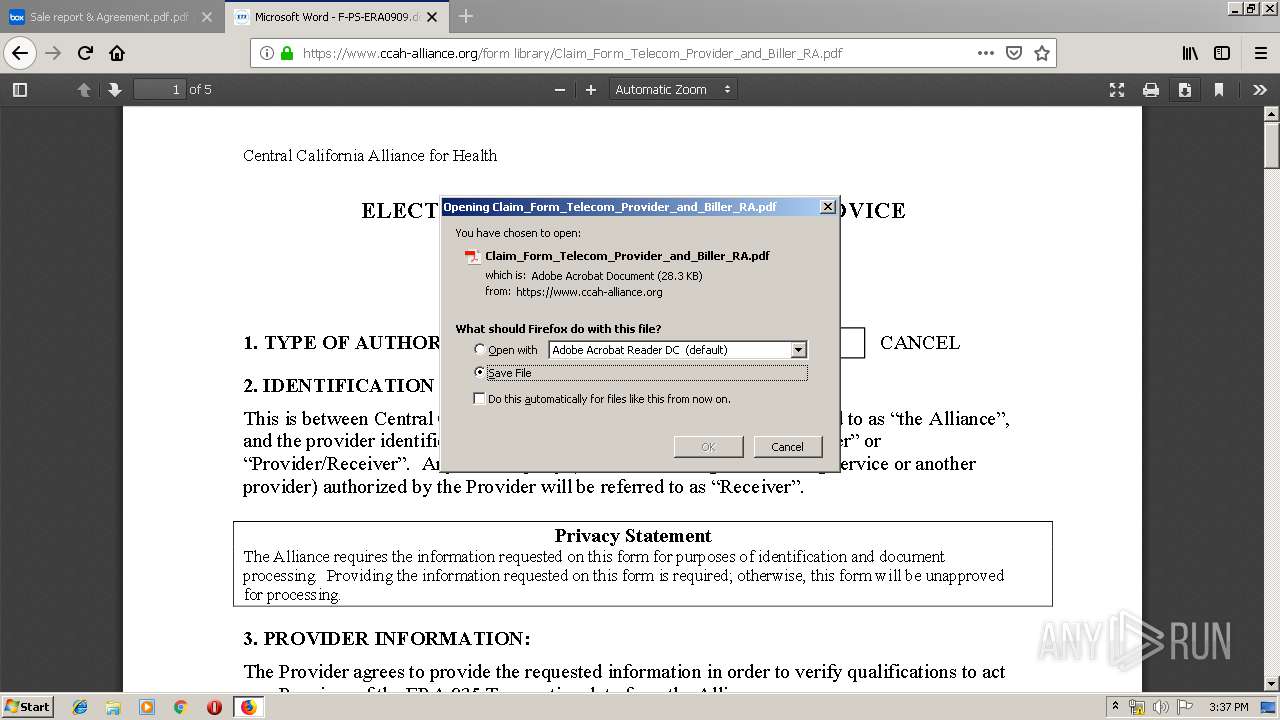
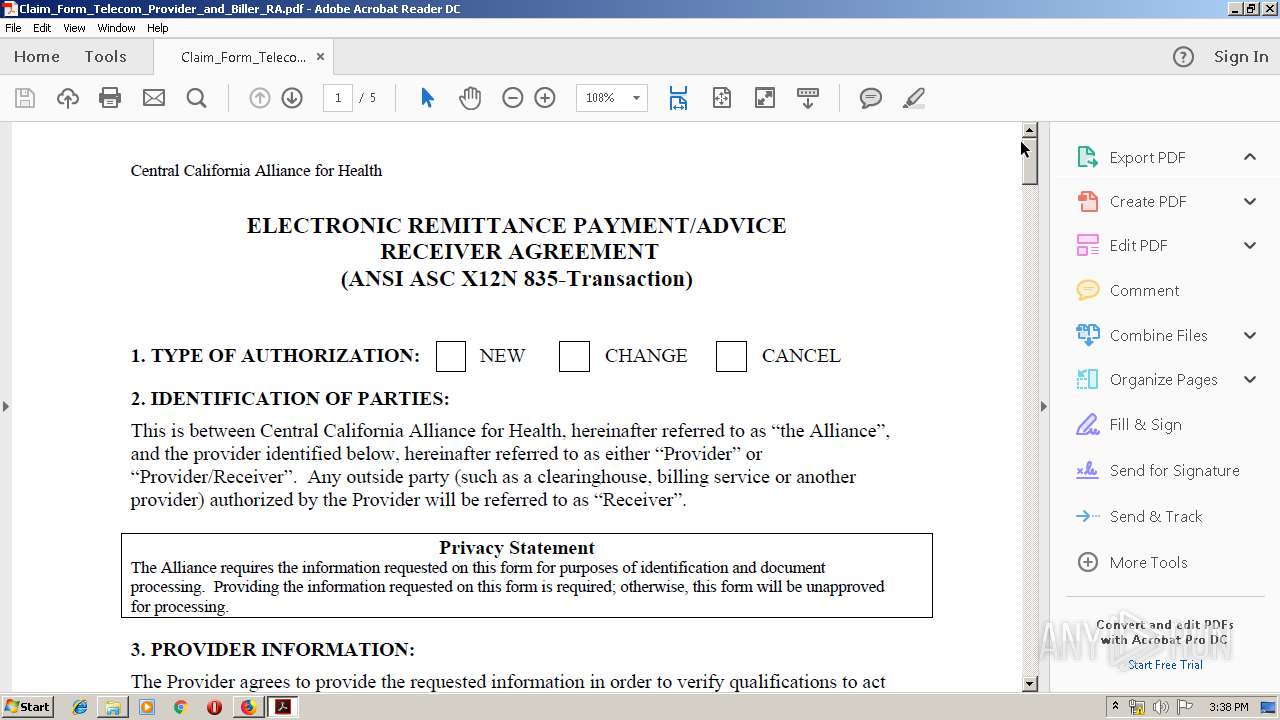
| 2924 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Downloads\Claim_Form_Telecom_Provider_and_Biller_RA.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3004 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3932.1.598421289\1783665411" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3116 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2836.13.533959745\780894971" -childID 2 -isForBrowser -prefsHandle 2600 -prefMapHandle 2604 -prefsLen 216 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2836 "\\.\pipe\gecko-crash-server-pipe.2836" 2616 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
Total events
1 547
Read events
1 449
Write events
98
Delete events
0
Modification events
| (PID) Process: | (2836) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2836) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006E000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2836) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2836) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3240) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3240) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (2924) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | aFS |
Value: DOS | |||
| (PID) Process: | (2924) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tDIText |
Value: /C/Users/admin/Downloads/Claim_Form_Telecom_Provider_and_Biller_RA.pdf | |||
| (PID) Process: | (2924) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tFileName |
Value: Claim_Form_Telecom_Provider_and_Biller_RA.pdf | |||
| (PID) Process: | (2924) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tFileSource |
Value: local | |||
Executable files
0
Suspicious files
91
Text files
53
Unknown types
69
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2836 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\cache2\trash28653 | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\test-malware-simple.sbstore | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\test-malware-simple.pset | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\test-phish-simple.sbstore | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\test-phish-simple.pset | — | |
MD5:— | SHA256:— | |||
| 2836 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\test-unwanted-simple.sbstore | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
61
DNS requests
107
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
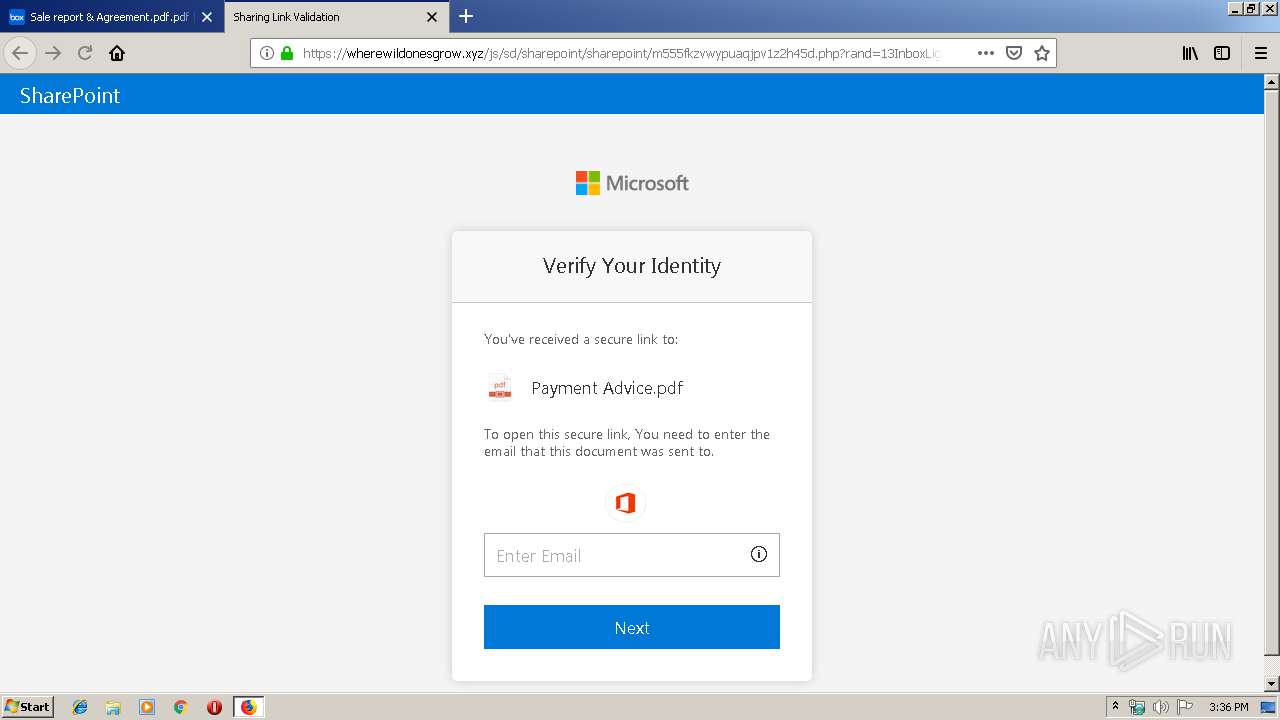
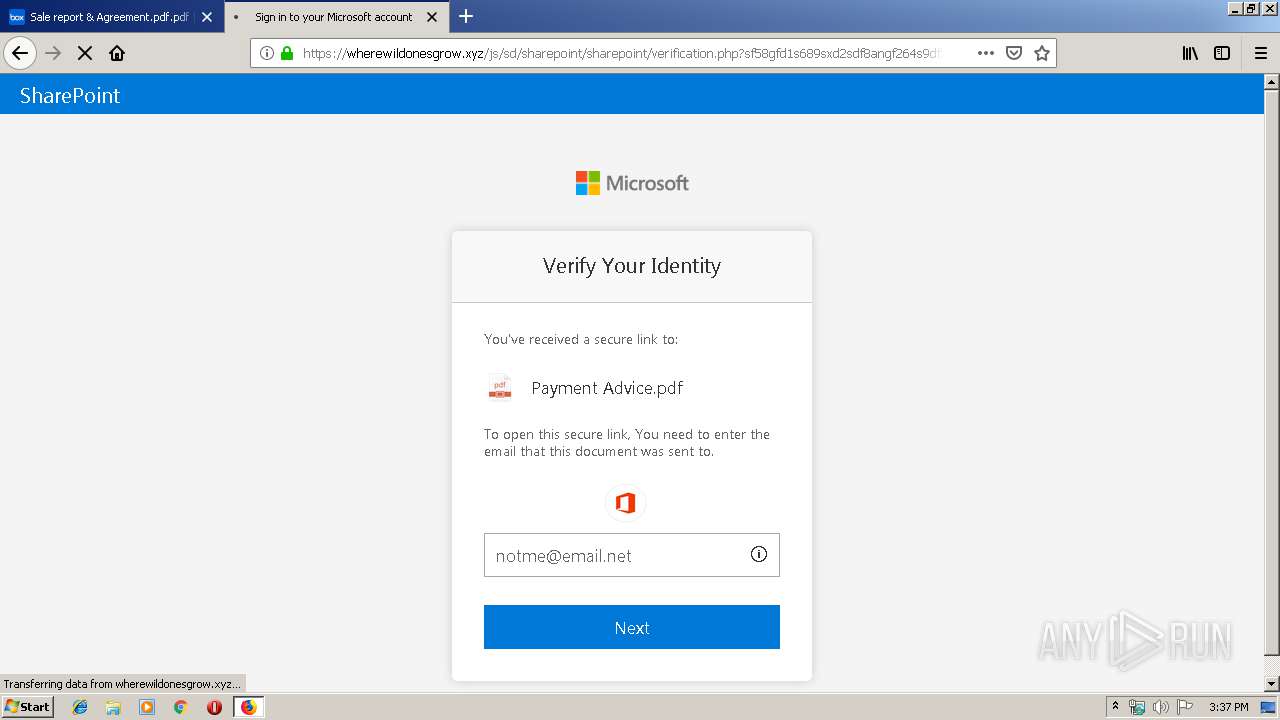
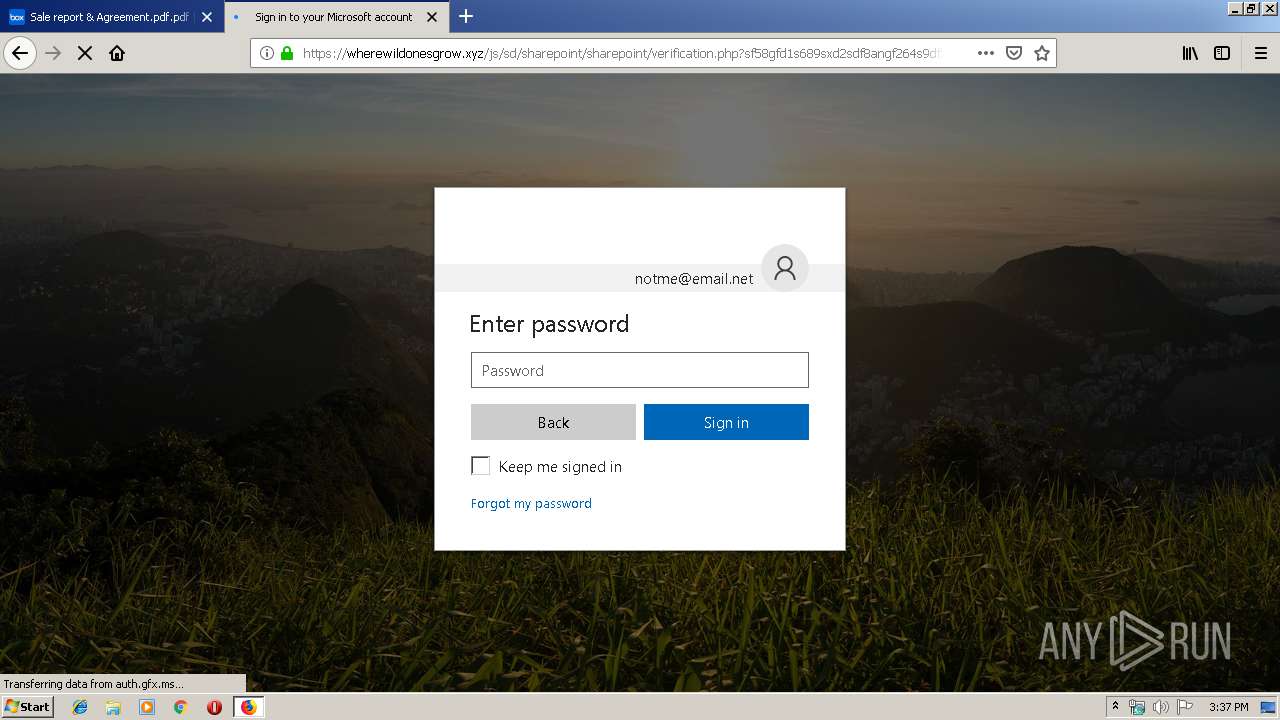
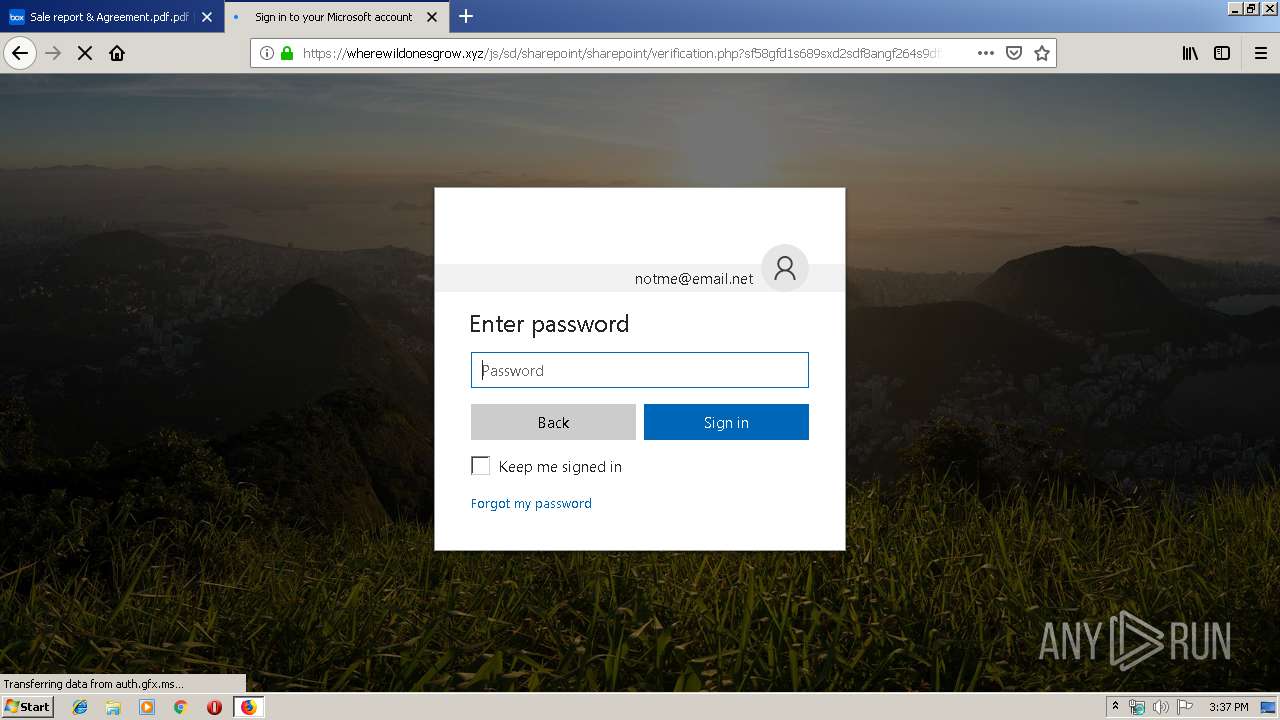
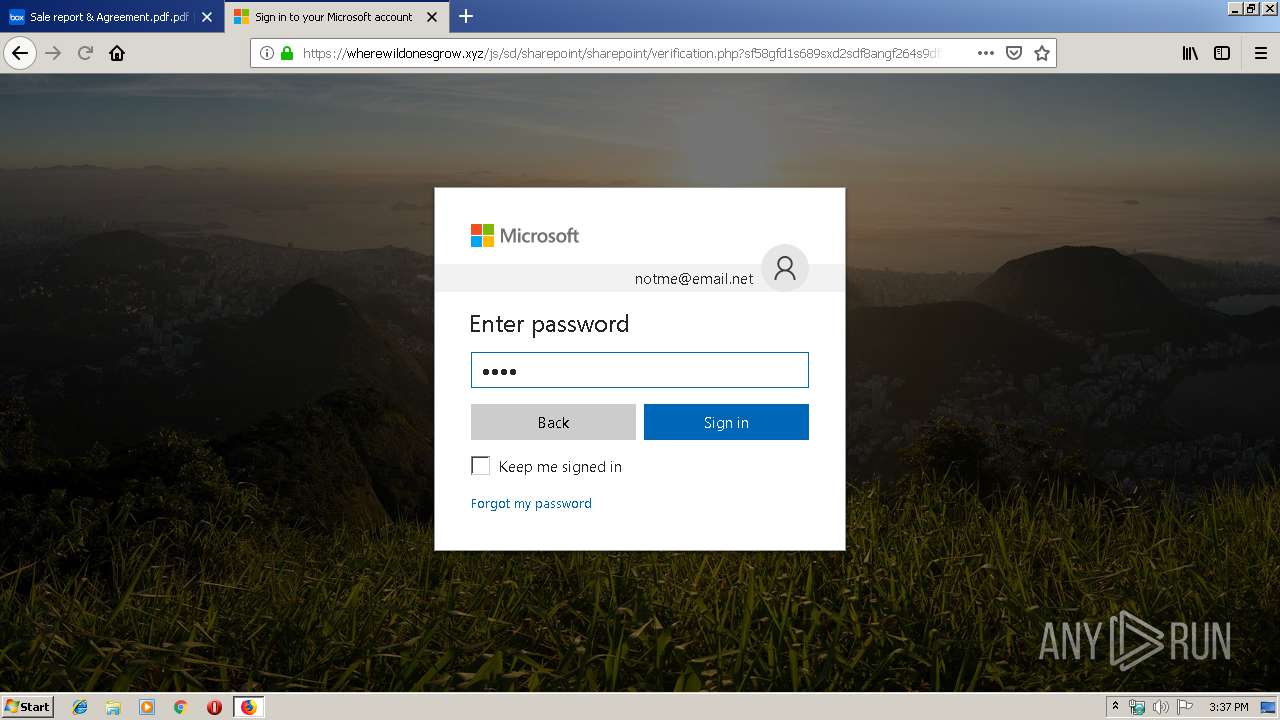
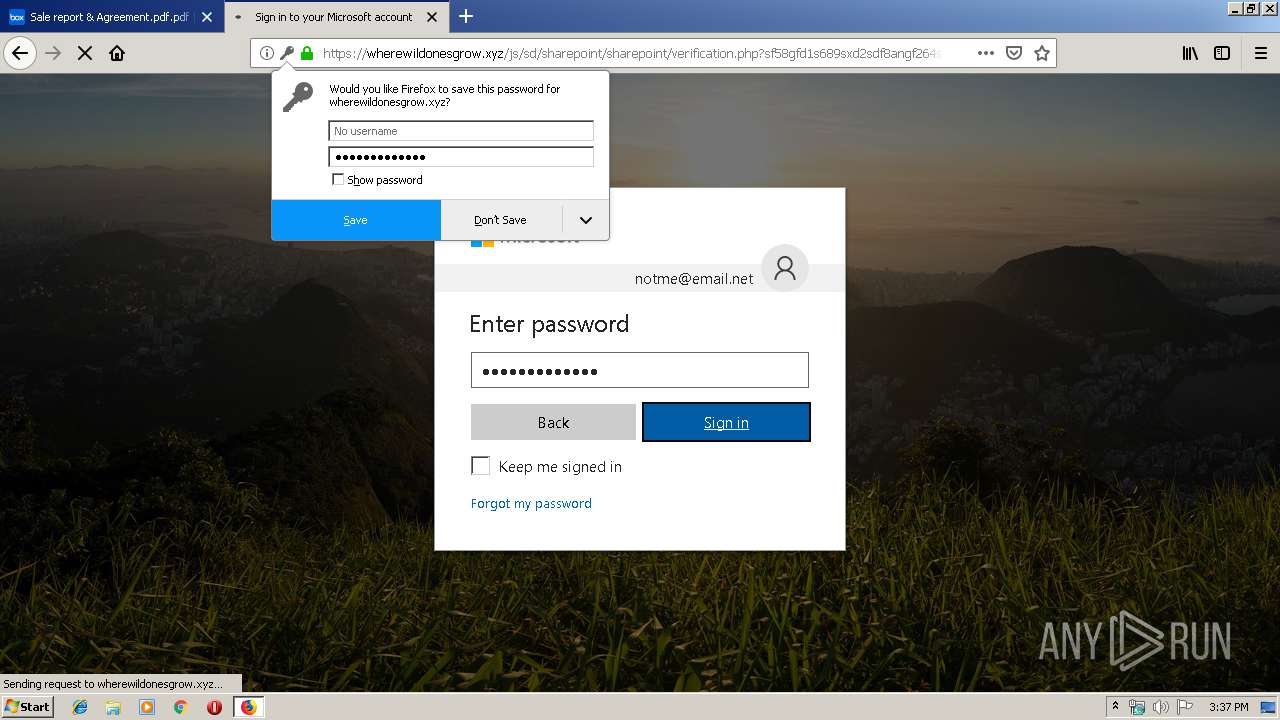
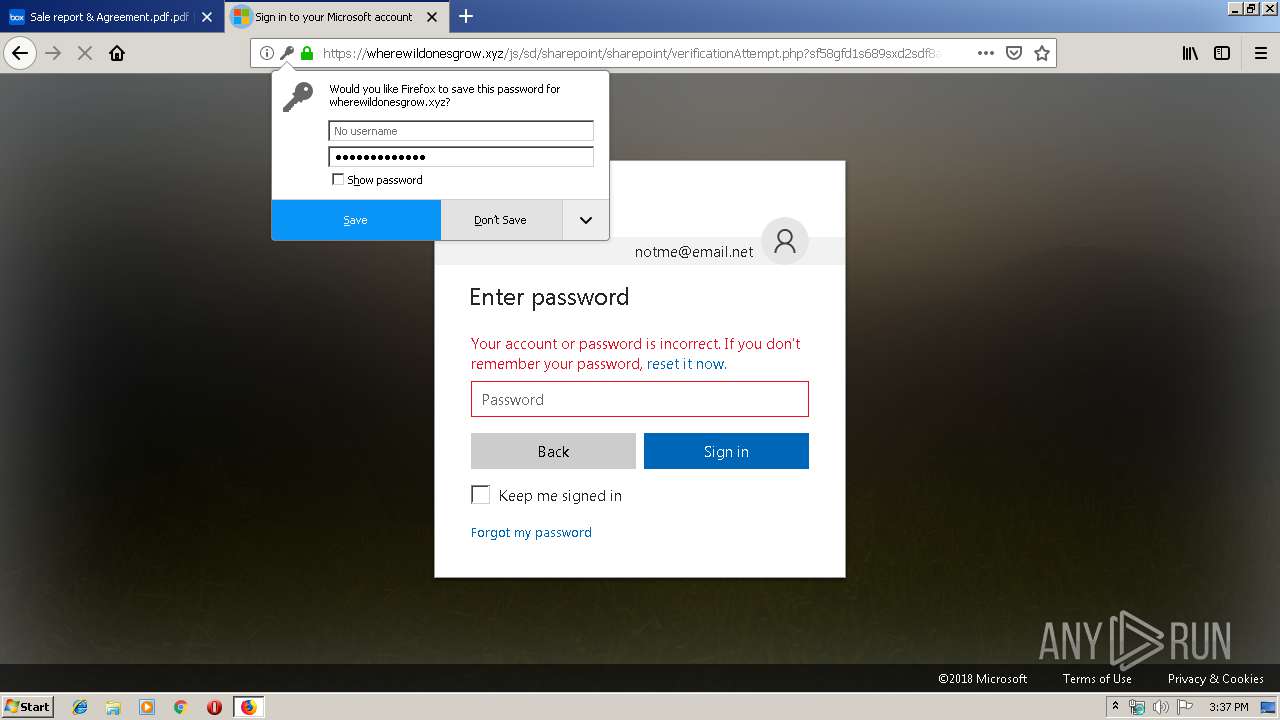
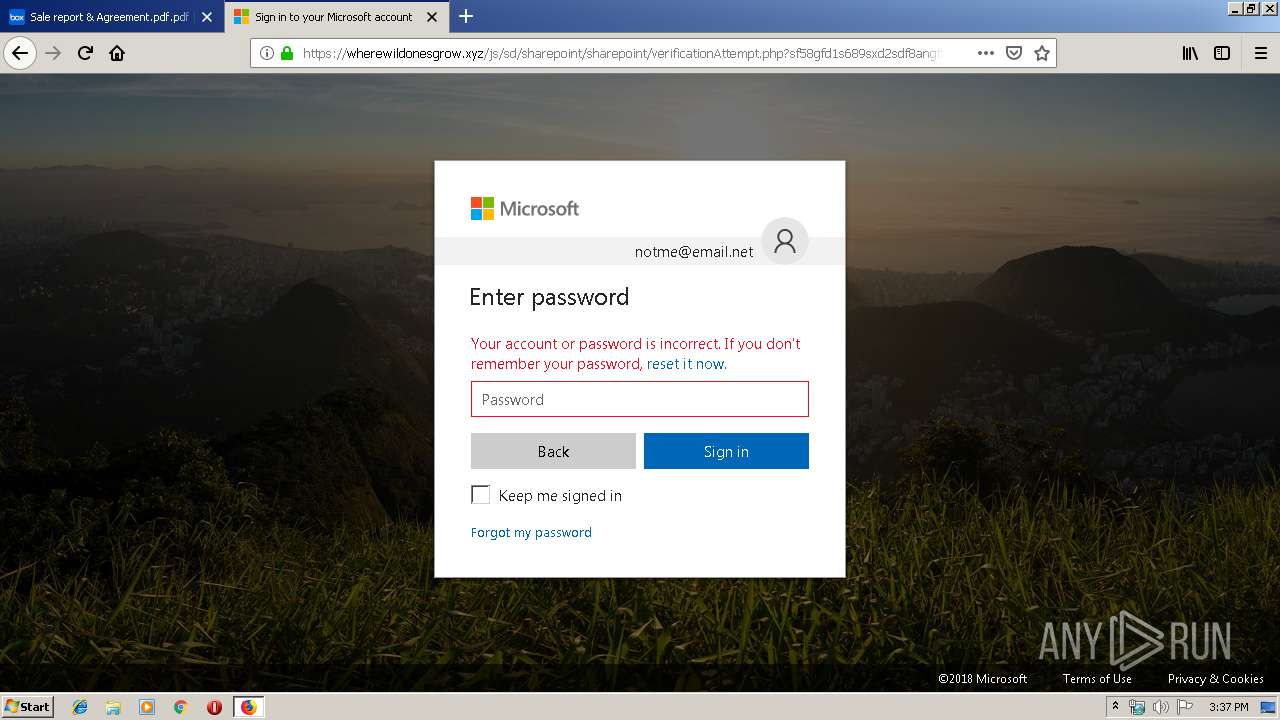
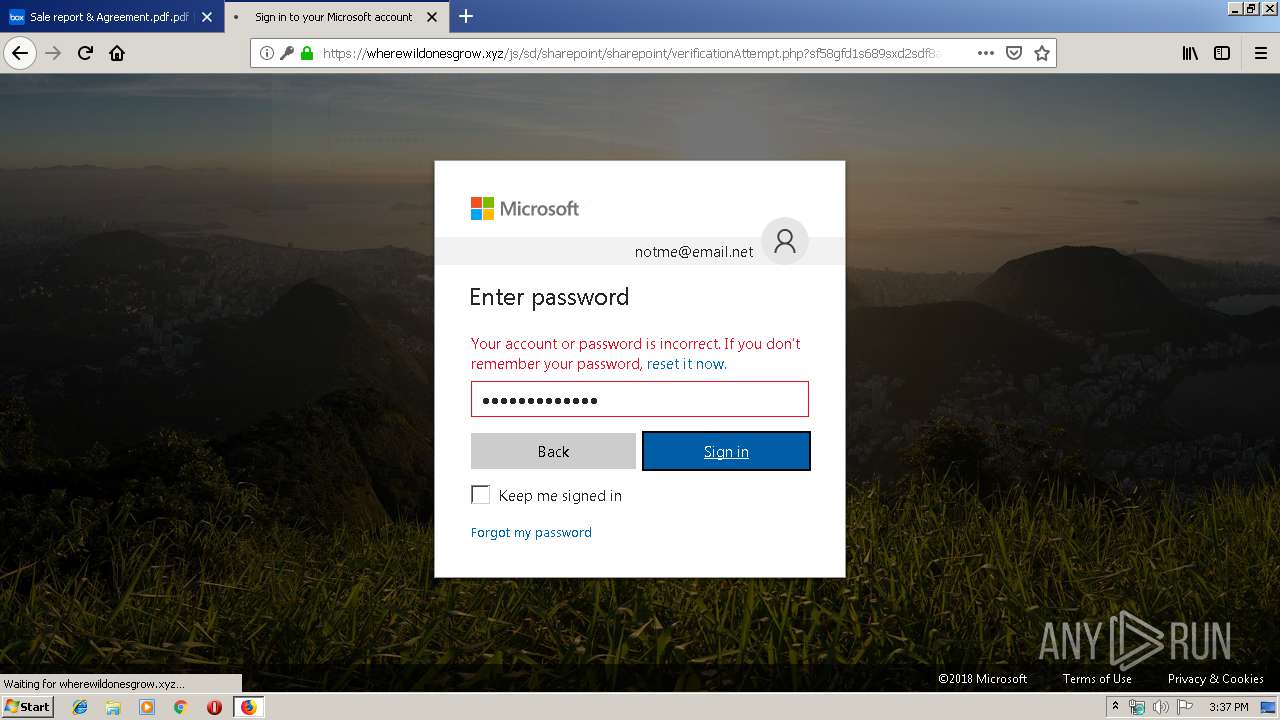
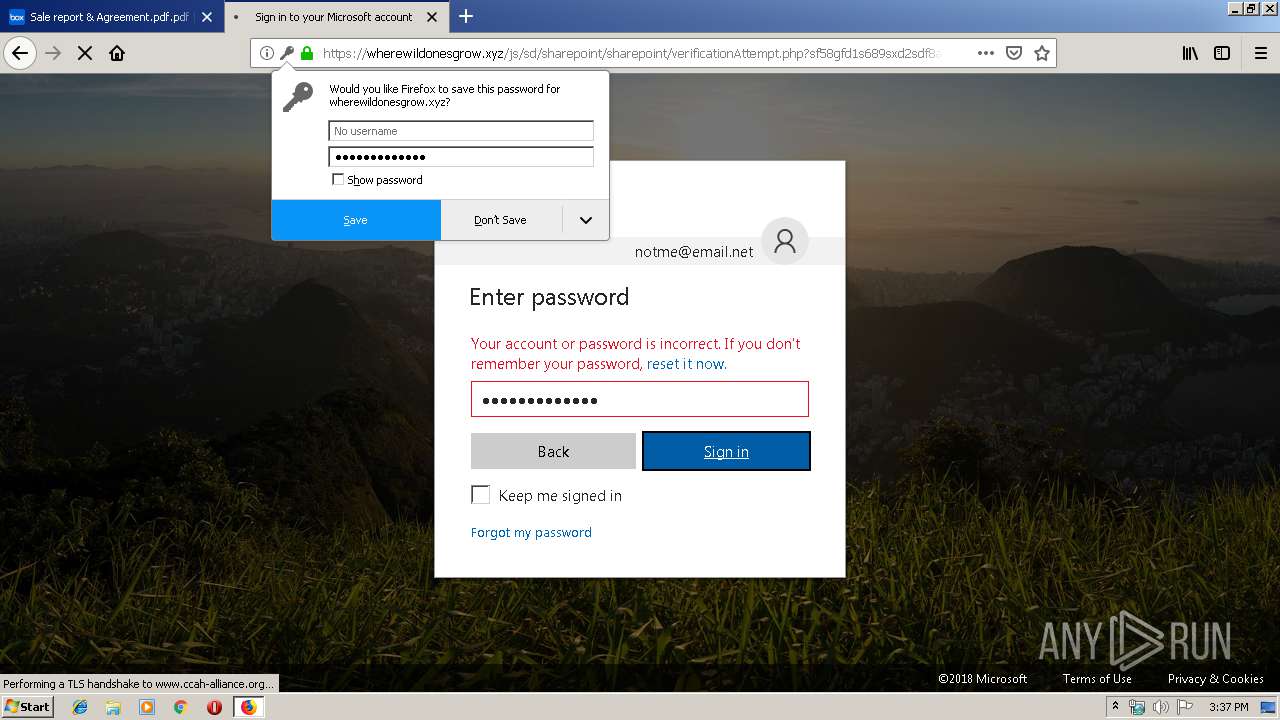
2836 | firefox.exe | GET | 301 | 104.27.178.8:80 | http://wherewildonesgrow.xyz/js/sd/sharepoint/sharepoint/ | US | — | — | shared |
2836 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://status.geotrust.com/ | US | der | 471 b | whitelisted |
2836 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://status.geotrust.com/ | US | der | 471 b | whitelisted |
2836 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2836 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://status.geotrust.com/ | US | der | 471 b | whitelisted |
2836 | firefox.exe | GET | 200 | 104.27.179.8:80 | http://wherewildonesgrow.xyz/.well-known/http-opportunistic | US | text | 101 b | shared |
2836 | firefox.exe | POST | 200 | 104.18.24.243:80 | http://ocsp.msocsp.com/ | US | der | 1.79 Kb | whitelisted |
2836 | firefox.exe | POST | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
2836 | firefox.exe | POST | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
2836 | firefox.exe | POST | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2836 | firefox.exe | 52.88.150.81:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
2836 | firefox.exe | 185.235.236.198:443 | app.box.com | — | — | unknown |
2836 | firefox.exe | 52.34.132.219:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
2836 | firefox.exe | 93.184.220.29:80 | status.geotrust.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2836 | firefox.exe | 52.222.173.224:443 | snippets.cdn.mozilla.net | Amazon.com, Inc. | US | unknown |
2836 | firefox.exe | 172.217.18.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2836 | firefox.exe | 104.16.74.20:443 | cdn01.boxcdn.net | Cloudflare Inc | US | shared |
2836 | firefox.exe | 185.235.236.197:443 | api.box.com | — | — | suspicious |
2836 | firefox.exe | 185.235.236.200:443 | public.boxcloud.com | — | — | unknown |
2836 | firefox.exe | 52.24.56.107:443 | shavar.services.mozilla.com | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
app.box.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
status.geotrust.com |
| whitelisted |
cs9.wac.phicdn.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2836 | firefox.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |