| URL: | https://www.aiqianxq.com/utf8/minipage/top_side_ads_360.html?tck=e0203a |
| Full analysis: | https://app.any.run/tasks/ef0d2853-2375-4350-91f9-c2a8c67245f4 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2020, 05:23:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6875D81C0A574E439ABB987AD77E1E49 |
| SHA1: | D979304E9FA9E21044F932E5181B1424F67065A7 |
| SHA256: | F6BFEDF18789F979838A12FCA39E5709CFFC75C450A78408F1E98DEF15C8CFB0 |
| SSDEEP: | 3:N8DSLjuqNAAKKQLBA6NCURG3C:2OLKOUVCUgS |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 1404)
INFO
Reads the hosts file
- chrome.exe (PID: 1404)
- chrome.exe (PID: 460)
Reads settings of System Certificates
- chrome.exe (PID: 460)
Application launched itself
- chrome.exe (PID: 1404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
70
Monitored processes
35
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13080364357607980672 --mojo-platform-channel-handle=4644 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=7971574373412660034 --mojo-platform-channel-handle=1636 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5701912831919169058 --mojo-platform-channel-handle=4348 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5408001862584554080 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2240 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5994811627893255654 --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3896 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=18386621700647839076 --mojo-platform-channel-handle=4920 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "https://www.aiqianxq.com/utf8/minipage/top_side_ads_360.html?tck=e0203a" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7574017467093588952 --mojo-platform-channel-handle=3892 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1528 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17595389540398226085 --mojo-platform-channel-handle=3492 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,2249942421517559100,7704110724703682479,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15664098653190010930 --mojo-platform-channel-handle=3872 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
625
Read events
522
Write events
98
Delete events
5
Modification events
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1404-13223798608055375 |
Value: 259 | |||
| (PID) Process: | (1404) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
35
Text files
323
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF39aa25.TMP | text | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF39a9e6.TMP | text | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF39a9d7.TMP | text | |
MD5:— | SHA256:— | |||
| 1404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
40
DNS requests
31
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
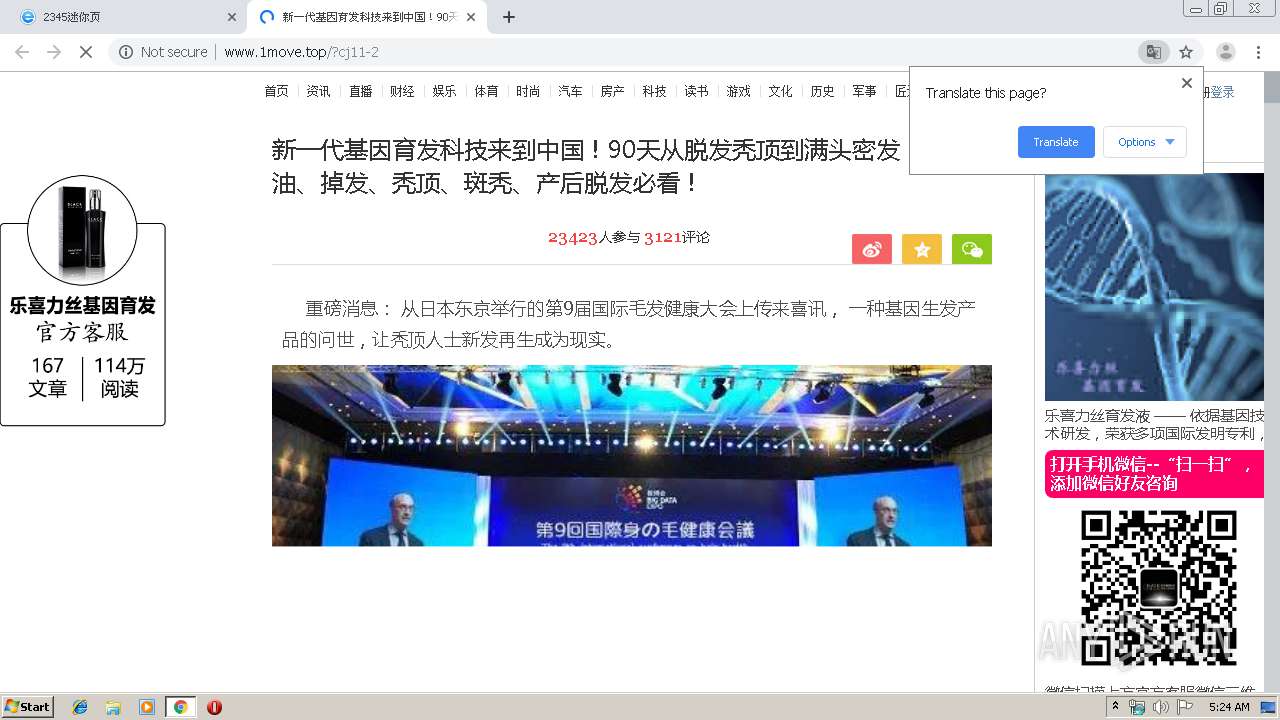
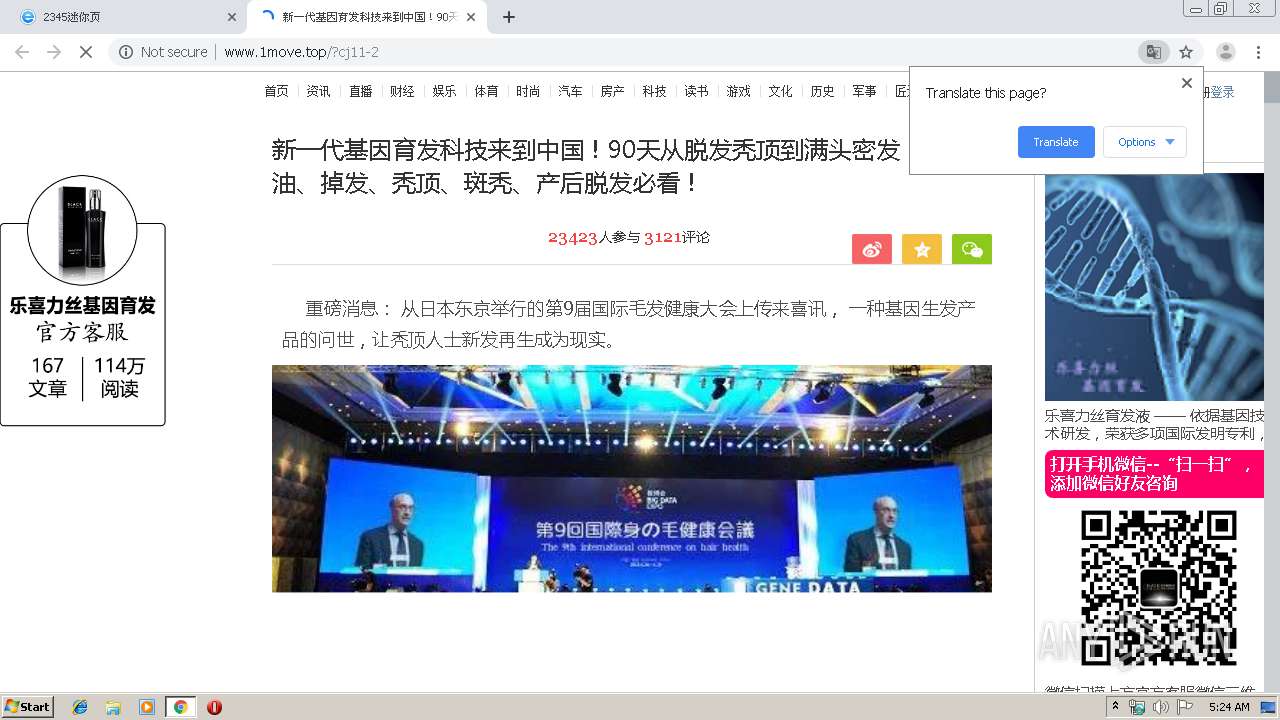
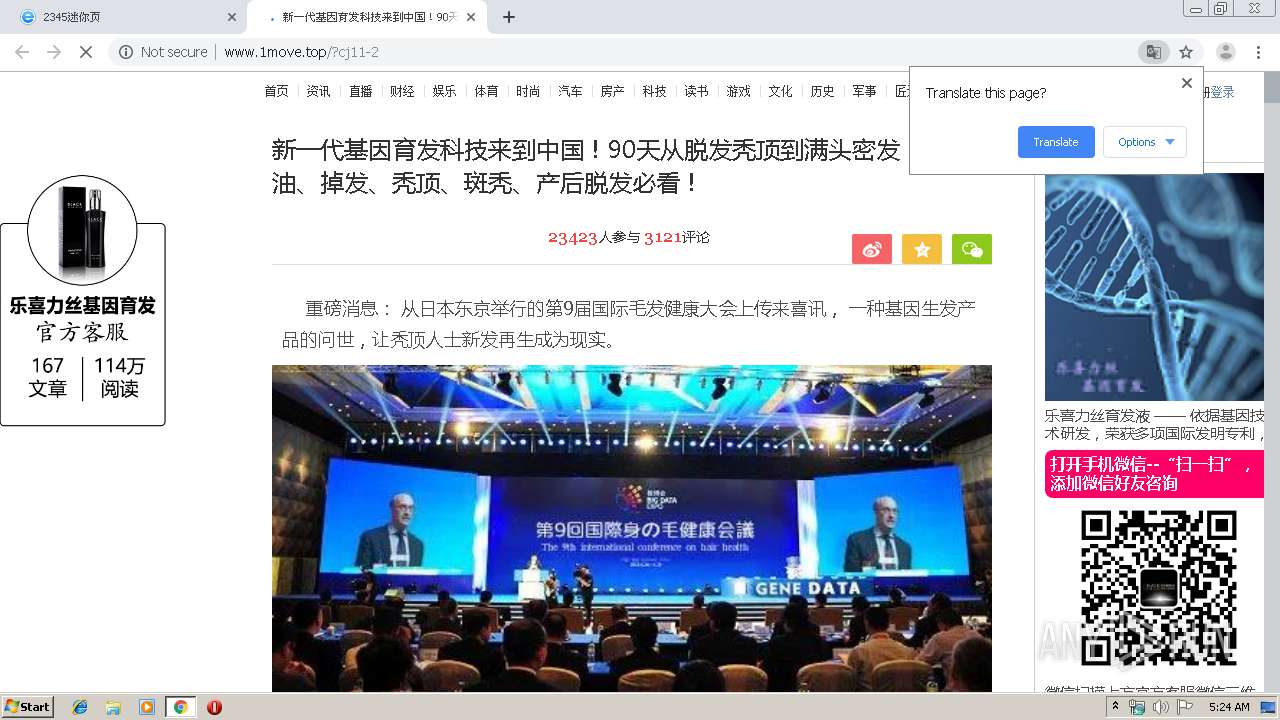
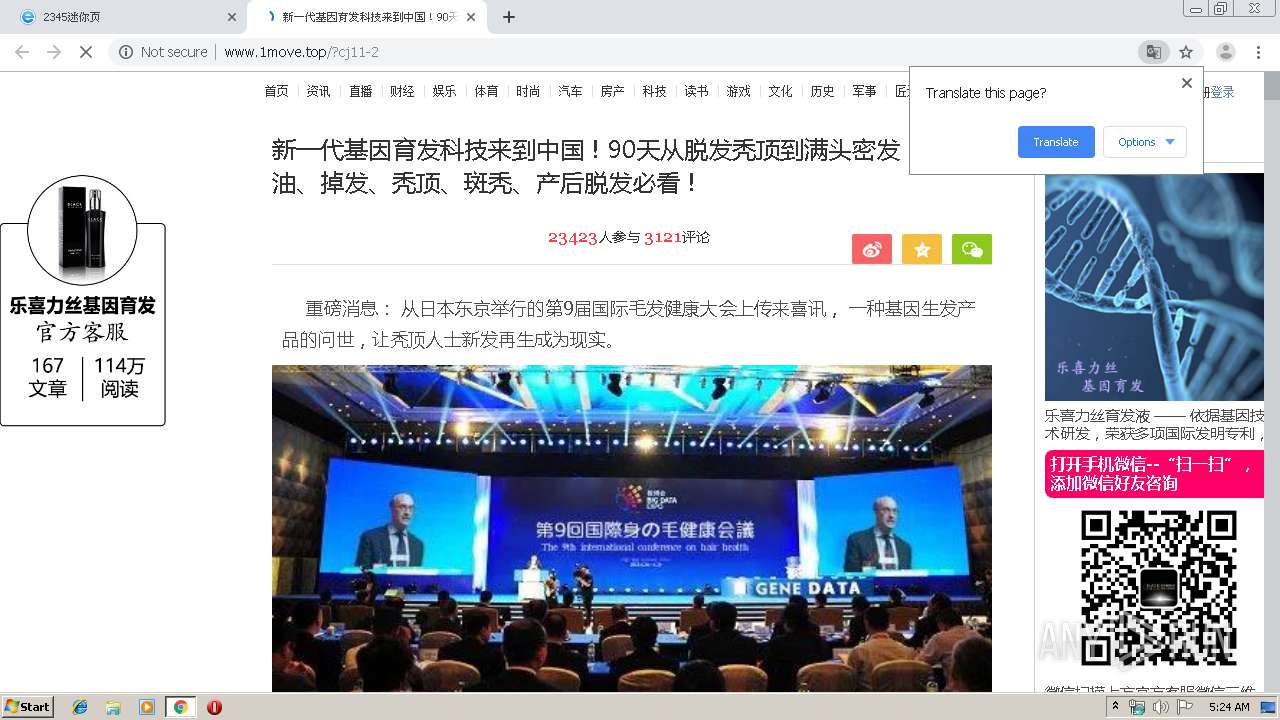
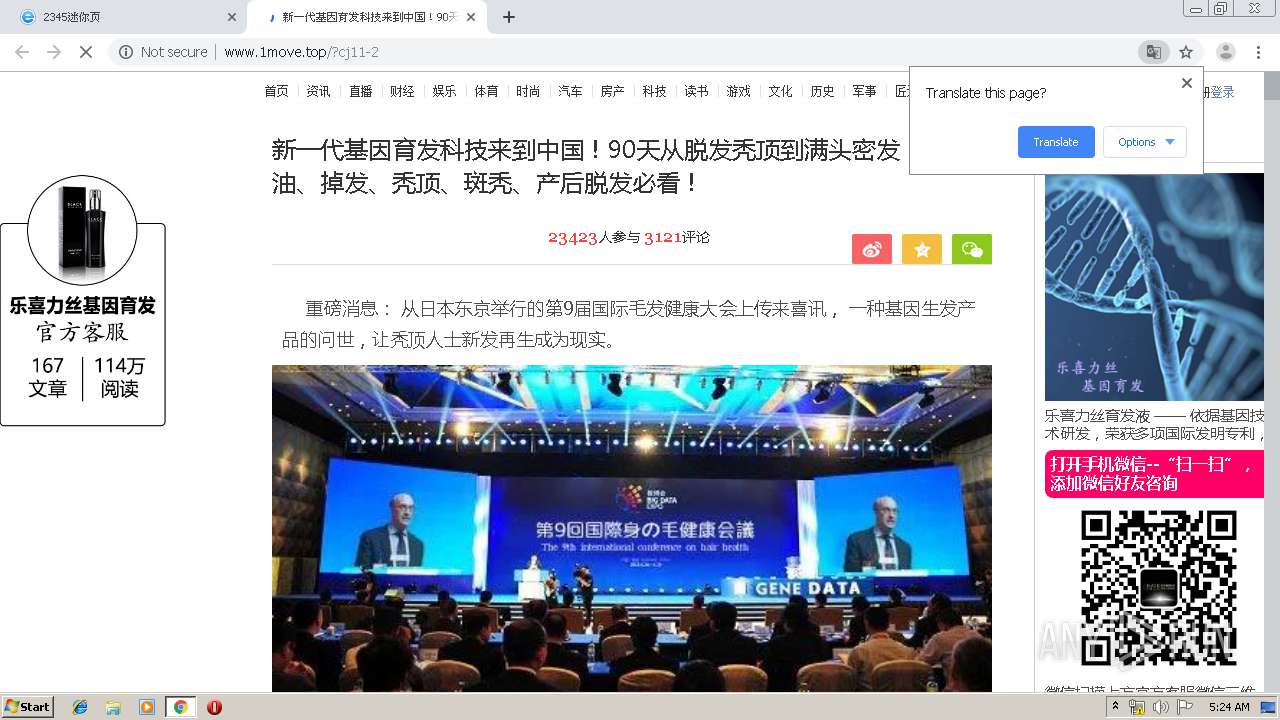
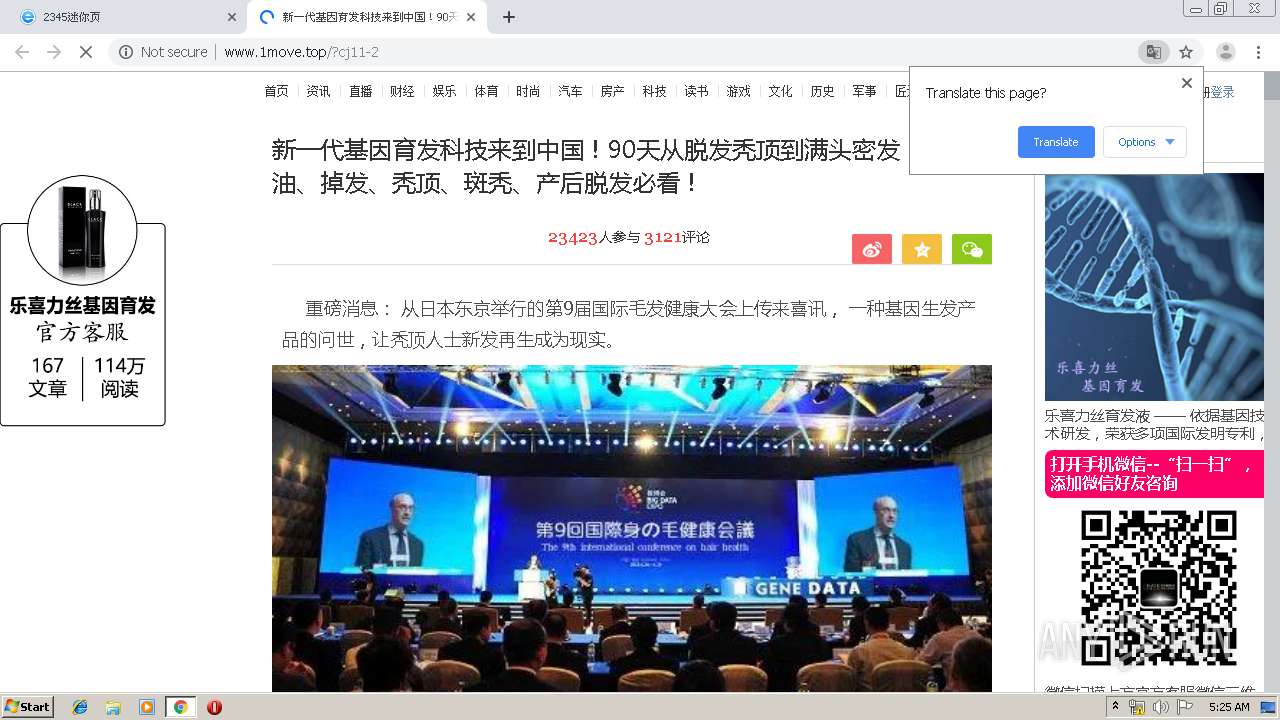
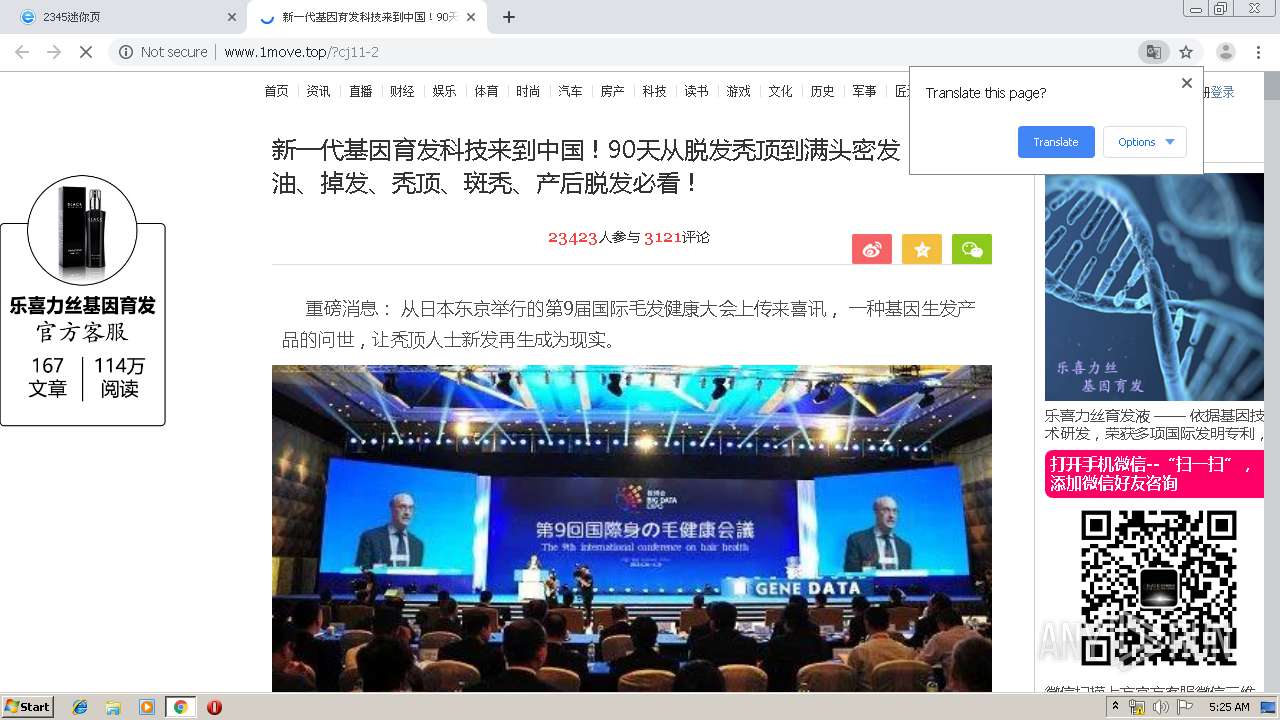
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/?cj11-2 | CN | html | 14.7 Kb | suspicious |
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/css/base.css | CN | text | 13.2 Kb | suspicious |
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/css/hy.css | CN | text | 23.6 Kb | suspicious |
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/img/touxiang_3.jpg | CN | image | 68.0 Kb | suspicious |
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/js/wx.js | CN | text | 278 b | suspicious |
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/img/toux.jpg | CN | image | 13.4 Kb | suspicious |
460 | chrome.exe | GET | 302 | 216.58.205.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 507 b | whitelisted |
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/picture/1.jpg | CN | image | 35.7 Kb | suspicious |
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/picture/2.jpg | CN | image | 29.8 Kb | suspicious |
460 | chrome.exe | GET | 200 | 122.114.61.96:80 | http://www.1move.top/picture/shitu_3.jpg | CN | image | 72.9 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
460 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
460 | chrome.exe | 61.147.204.56:443 | www.aiqianxq.com | AS Number for CHINANET jiangsu province backbone | CN | suspicious |
460 | chrome.exe | 172.217.18.4:443 | www.google.com | Google Inc. | US | whitelisted |
460 | chrome.exe | 172.217.16.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
460 | chrome.exe | 180.163.239.211:443 | show-g.mediav.com | China Telecom (Group) | CN | malicious |
460 | chrome.exe | 42.62.12.134:443 | union2.50bang.org | China Unicom Beijing Province Network | CN | unknown |
460 | chrome.exe | 104.192.110.245:443 | jx.cdn.qhstatic.com | Beijing Qihu Technology Company Limited | US | suspicious |
460 | chrome.exe | 221.130.199.240:443 | s3.nzbdw.com | Guangdong Mobile Communication Co.Ltd. | CN | malicious |
460 | chrome.exe | 216.58.210.14:443 | clients2.google.com | Google Inc. | US | whitelisted |
460 | chrome.exe | 172.217.16.131:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.aiqianxq.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
show-g.mediav.com |
| whitelisted |
union2.50bang.org |
| suspicious |
jx.cdn.qhstatic.com |
| suspicious |
max-l.mediav.com |
| unknown |
s3.nzbdw.com |
| unknown |
ssl.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
460 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
460 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
460 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |