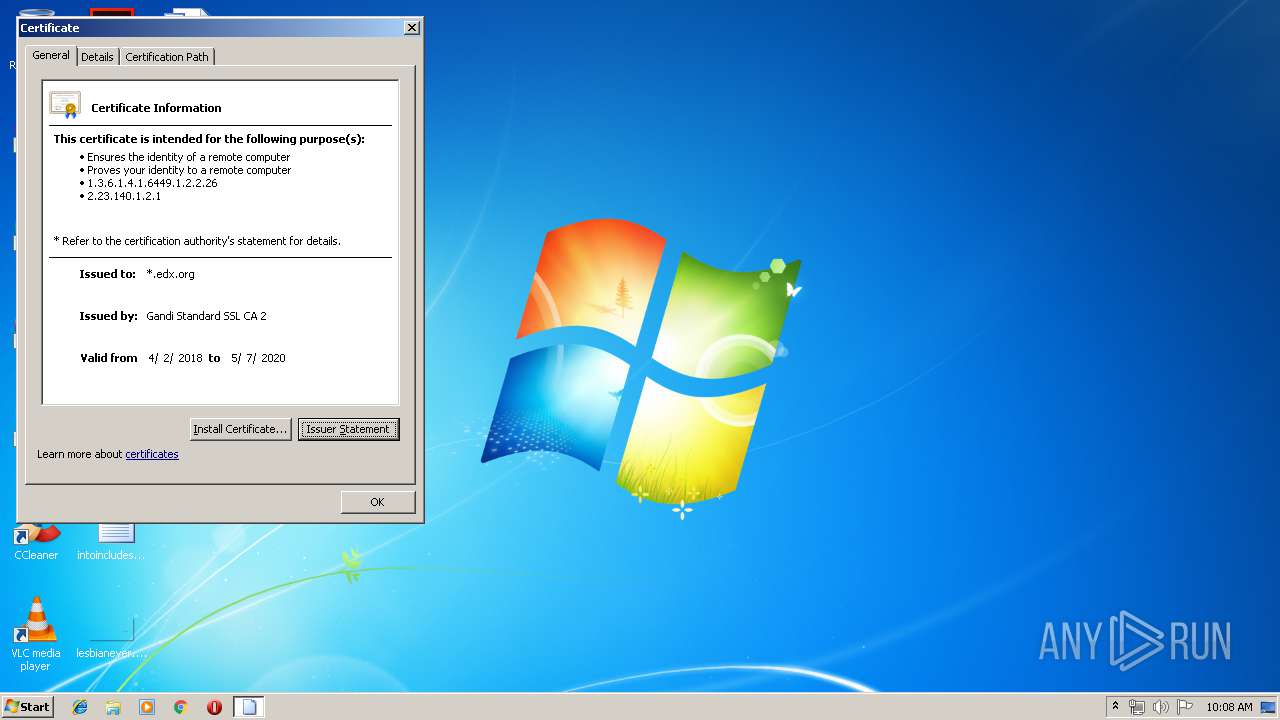
| File name: | -edxorg.crt |
| Full analysis: | https://app.any.run/tasks/26d22ac1-e2ea-4047-bce6-da29094b7e37 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 09:08:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | text/plain |
| File info: | PEM certificate |
| MD5: | 713C9AED152ECD6E6AA1815A731A1081 |
| SHA1: | 70F61190356E84E2E30F2C76B6923A83D23039D7 |
| SHA256: | F6BFE2D4292E4D3A169C77C386E7CE71DAACD90A0CD06BDBA8003BEEA7CE3E8B |
| SSDEEP: | 48:LrsyUKhcHnKzSqHr5WagDozqlvRVd7r0oq6DLLtG8FCH1uN:LrTUxHKzjbzYvRkJ67Y9Hy |
MALICIOUS
Changes settings of System certificates
- rundll32.exe (PID: 252)
SUSPICIOUS
Adds / modifies Windows certificates
- rundll32.exe (PID: 252)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cer | | | Internet Security Certificate (100) |
|---|
Total processes
33
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtOpenCER C:\Users\admin\AppData\Local\Temp\-edxorg.crt | C:\Windows\system32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
50
Read events
32
Write events
16
Delete events
2
Modification events
| (PID) Process: | (252) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (252) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 0F000000010000001400000085FEF11B4F47FE3952F98301C9F98976FEFEE0CE09000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030353000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C01400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB5748501D00000001000000100000005B3B67000EEB80022E42605B6B3B72400B000000010000000E000000740068006100770074006500000003000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B812000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
| (PID) Process: | (252) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (252) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 190000000100000010000000DC73F9B71E16D51D26527D32B11A6A3D09000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030353000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C01400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB5748501D00000001000000100000005B3B67000EEB80022E42605B6B3B72400B000000010000000E000000740068006100770074006500000003000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B812000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
| (PID) Process: | (252) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\CA\Certificates\247106A405B288A46E70A0262717162D0903E734 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000247106A405B288A46E70A0262717162D0903E734140000000100000014000000B390A7D8C9AF4ECD613C9F7CAD5D7F41FD6930EA0400000001000000100000001A9A69A81F6DA92D87F7694E16D8B8790F00000001000000300000009E9609372F45B5101548E8AF9A20E0DBF5932DEA9B9AF86759C2029BC3B53E306E6491F6B15BF00B1E2DEE3BB8D43D2219000000010000001000000043E6FA09A3B9D0DE6FBE3AACD184C8FD180000000100000010000000EA6089055218053DD01E37E1D806EEDF2000000001000000ED050000308205E9308203D1A003020102021005E4DC3B9438AB3B8597CBA6A19850E3300D06092A864886F70D01010C0500308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F72697479301E170D3134303931323030303030305A170D3234303931313233353935395A305F310B3009060355040613024652310E300C060355040813055061726973310E300C060355040713055061726973310E300C060355040A130547616E64693120301E0603550403131747616E6469205374616E646172642053534C204341203230820122300D06092A864886F70D01010105000382010F003082010A028201010094042DA6799574FFD5003CF5AED894B1297CC08F0B0B89B98283976E3728F5A21ACFD2920B9BA8D387947384109FDC35CBC22D92AC21B9CB3BFC40C1C18321F0BFF8F69CFA9C8210C0D08E4EE50D4CB0915C90B4A4405116DAE484122D055CA11F17192451AA7AEAE1071B868D0172F2E7D48323399EE0E14C1F6B22A3B41066B0ED8296D76E6AB4F23FB542FCDD8AB5ABBA2D1D3A759B31DC3E9DAC5BD3410D6CB01BF53AF579EA21A2F8F433524B242D1EA499B16D48BCB812FE72707CF7FB0275F48DDED6DAC0A0321A52DF386B2E45383F3F049600FDA1F4A2BBD517D6277C1B5859955E8A12FD9CAB813E52284851856BF391B2863F29B56E0362EED6050203010001A382017530820171301F0603551D230418301680145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB301D0603551D0E04160414B390A7D8C9AF4ECD613C9F7CAD5D7F41FD6930EA300E0603551D0F0101FF04040302018630120603551D130101FF040830060101FF020100301D0603551D250416301406082B0601050507030106082B0601050507030230220603551D20041B3019300D060B2B06010401B2310102021A3008060667810C01020130500603551D1F044930473045A043A041863F687474703A2F2F63726C2E7573657274727573742E636F6D2F55534552547275737452534143657274696669636174696F6E417574686F726974792E63726C307606082B06010505070101046A3068303F06082B060105050730028633687474703A2F2F6372742E7573657274727573742E636F6D2F555345525472757374525341416464547275737443412E637274302506082B060105050730018619687474703A2F2F6F6373702E7573657274727573742E636F6D300D06092A864886F70D01010C050003820201005867FD72B26AD77C6196197ED94346D1267DC853FA66B06B2DA7D3AA56F73A88D03B72C950FDF759B2AA68F58C7303BB956517CE2F1CDD9813A291C9EEA1406E3C98D65CF3B2223C2DEE1BA4E1DE202416F28C1173913AF6FACE240287CA93ECB4B6C81617C572FC2740F613FE93A69D51EF3C2BD877579B8C653A352536B7B58A636F072793B1608D80DB96D47A8F2DAB1C88C96E7ED6651FAF5DCA163F2846DCA035E5F9E9E5D596880C4FC6B77767488427B61FB068DBACBF77B090B8A2C91C325D02BA2543814247BBD8E18F0C0C465FEE46336B031482D37ECD8FAF90D68E247D4042B46A6A17C69597E1F238CDA7EDB4274093DF72A9B8C666633738642230A23BF1B9C87BC8FB293AAB1A72D206124EF682D4236F3EC393E5D8B6C0DEDC2316D61330B7A09A0E2C5506007001CFEA391D80DB88F7A520B85BFD3126698F2D0A61833A47A613542C1EE3ED44CABC6A1F280E51D9DE0E9F75CD0E0395CAF9C5A92A2DFE41A4A147AE0DC2F93966334A5BE18428596C7D941776E44582AD7020FDD26F63A8D7FAA033FA37CBF7B2659EDA506F3FE4A7F38E5D58329770232EE7FDC4159B9C278F32ED17AD58813129111A9BD4FC6C9528C74E0507A6FD1DBC19E2E8B7B9118A2D701252858D8C334A0FFC9992E06370DAA594476307E758C7315F053D3655FE83B2E8A6ADD7E9E6027488745CDA34DB90D26D510A23D623 | |||
| (PID) Process: | (252) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\CA\Certificates\EAB040689A0D805B5D6FD654FC168CFF00B78BE3 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000EAB040689A0D805B5D6FD654FC168CFF00B78BE31400000001000000140000005379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB040000000100000010000000DB78CBD190952735D940BC80AC2432C00F0000000100000030000000435FE6564241D6B3828352EF9BE443D511C21F0AFB325C4038A5820F00D87774A8EF2193DDAAE065B2572FAF2BF0EE63190000000100000010000000EA6089055218053DD01E37E1D806EEDF18000000010000001000000045ED9BBC5E43D3B9ECD63C060DB78E5C20000000010000007B050000308205773082045FA003020102021013EA28705BF4ECED0C36630980614336300D06092A864886F70D01010C0500306F310B300906035504061302534531143012060355040A130B416464547275737420414231263024060355040B131D41646454727573742045787465726E616C20545450204E6574776F726B312230200603550403131941646454727573742045787465726E616C20434120526F6F74301E170D3030303533303130343833385A170D3230303533303130343833385A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A381F43081F1301F0603551D23041830168014ADBD987A34B426F7FAC42654EF03BDE024CB541A301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF30110603551D20040A300830060604551D200030440603551D1F043D303B3039A037A0358633687474703A2F2F63726C2E7573657274727573742E636F6D2F416464547275737445787465726E616C4341526F6F742E63726C303506082B0601050507010104293027302506082B060105050730018619687474703A2F2F6F6373702E7573657274727573742E636F6D300D06092A864886F70D01010C050003820101009365F63783950F5EC3821C1FD677E73C8AC0AA09F0E90B26F1E0C26A75A1C779C9B95260C829120EF0AD03D609C476DFE5A68195A746DA8257A99592C5B68F03226C3377C17B32176E07CE5A14413A05241BF614063BA825240EBBCC2A75DDB970413F7CD0633621071F46FF60A491E167BCDE1F7E1914C9636791EA67076BB48F8BC06E437DC3A1806CB21EBC53857DDC90A1A4BC2DEF4672573505BFBB46BB6E6D3799B6FF239291C66E40F88F2956EA5FD55F1453ACF04F61EAF722CCA7560BE2B8341F26D97B1905683FBA3CD43806A2D3E68F0EE3B4716D4042C584B440952BF465A04879F61D8163969D4F75E0F87CE48EA9D1F2AD8AB38CC721CDC2EF | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 252 | rundll32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4B523CA12942AC5B9E152203CBAA4034 | binary | |
MD5:— | SHA256:— | |||
| 252 | rundll32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E0968A1E3A40D2582E7FD463BAEB59CD | binary | |
MD5:— | SHA256:— | |||
| 252 | rundll32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E0968A1E3A40D2582E7FD463BAEB59CD | der | |
MD5:— | SHA256:— | |||
| 252 | rundll32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4B523CA12942AC5B9E152203CBAA4034 | der | |
MD5:1A9A69A81F6DA92D87F7694E16D8B879 | SHA256:B9F2164323638DCE0B92218B43C41C1B2B2696389329DB19F5CF7AD49B5CB372 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
252 | rundll32.exe | GET | 200 | 91.199.212.52:80 | http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
252 | rundll32.exe | GET | 200 | 91.199.212.52:80 | http://crt.usertrust.com/GandiStandardSSLCA2.crt | GB | der | 1.48 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
252 | rundll32.exe | 91.199.212.52:80 | crt.usertrust.com | Comodo CA Ltd | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crt.usertrust.com |
| whitelisted |