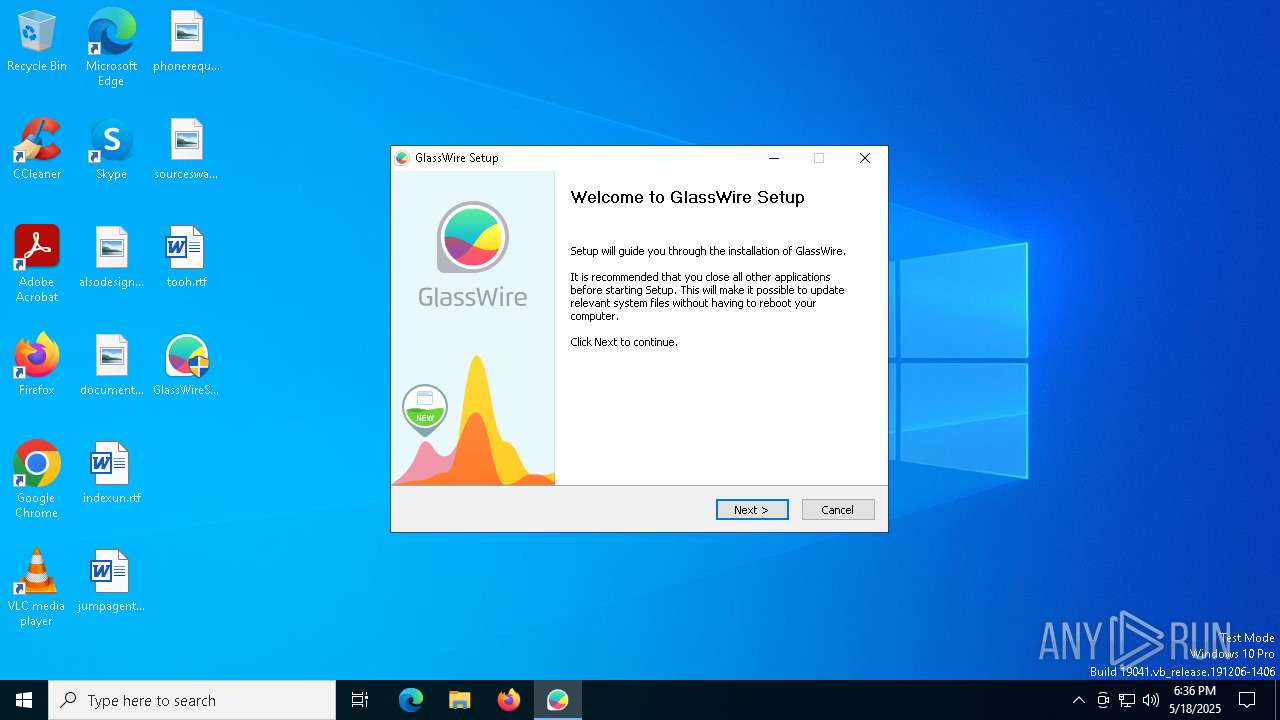
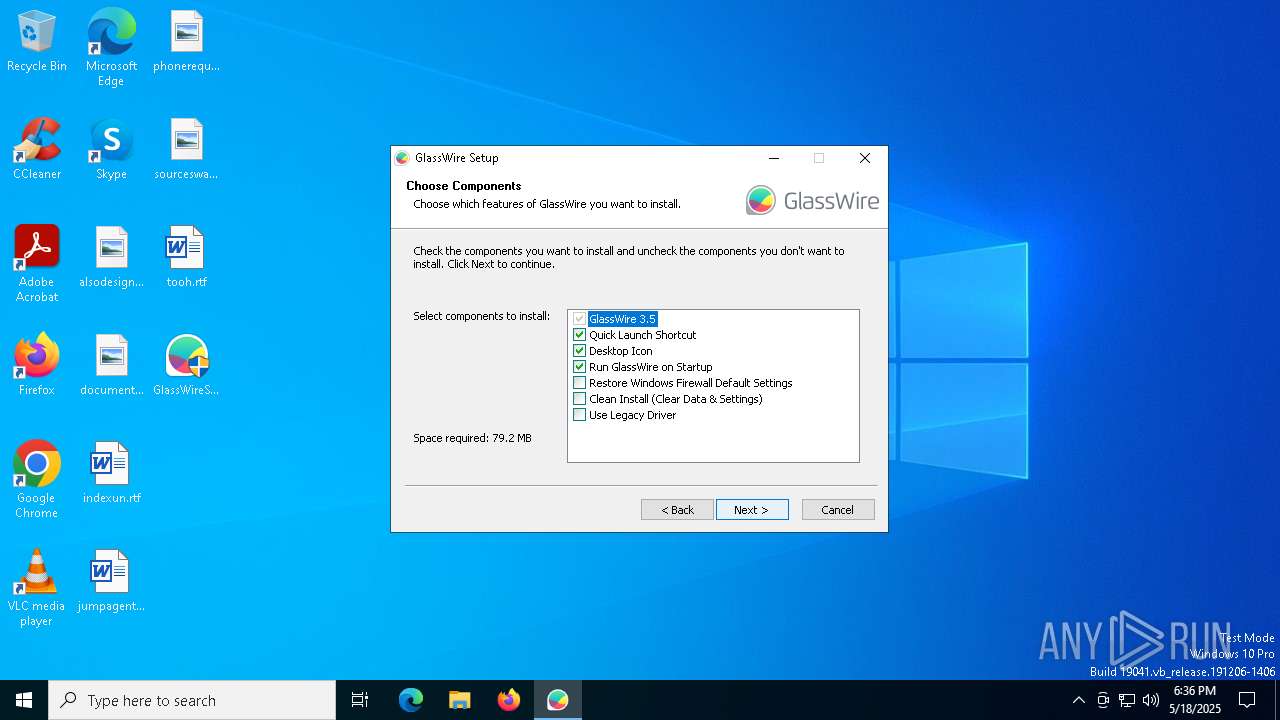
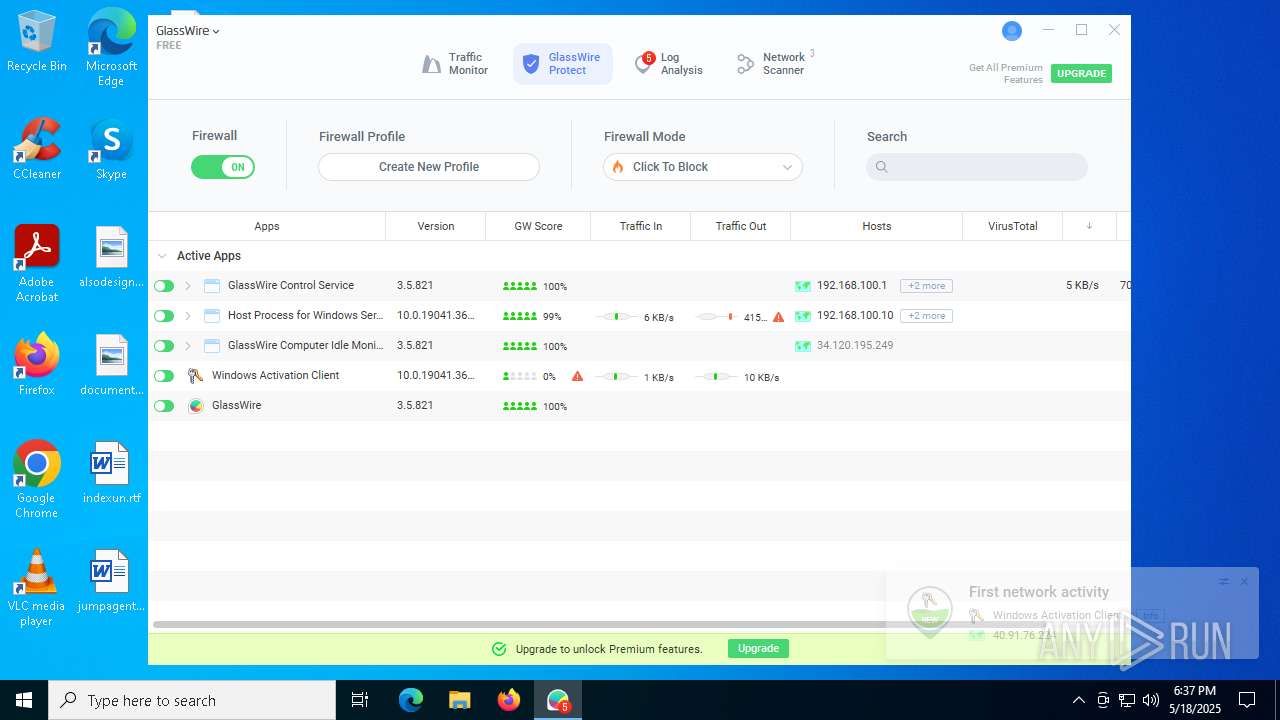
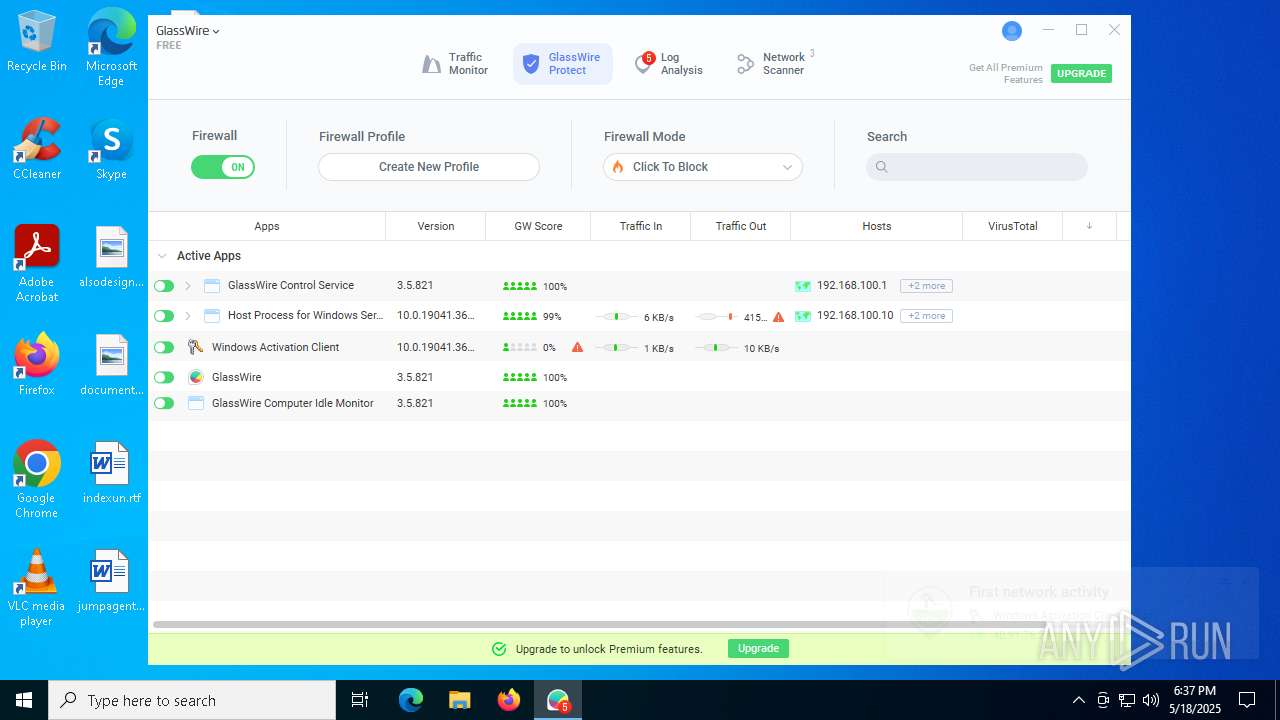
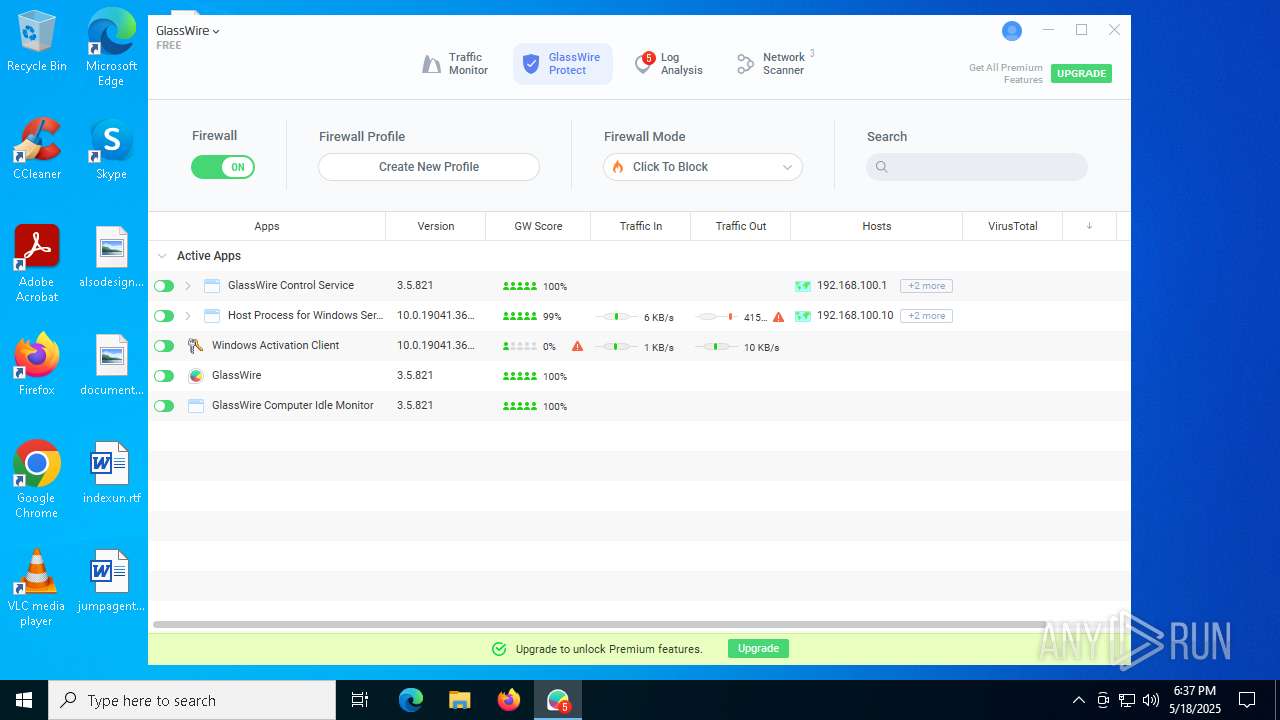
| File name: | GlassWireSetup.exe |
| Full analysis: | https://app.any.run/tasks/56dab9dd-41f0-445d-8a76-8eeeba990428 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 18:34:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | D4F00E685D637E999243AD5AA96C3ED2 |
| SHA1: | 7995C07CFFA3C4E631D0FFD196FC5C24C4F315BC |
| SHA256: | F6A21594C80BA4AA5DCAC7DE02628C7DE01AE8505F38BF9F89CECC2DC27DF49C |
| SSDEEP: | 786432:3KqTn83X1gWIJ3+4CTKRP4rRvQsOkUtrHQblTugaU8Zbg54:3AgN+4CTKRPYGkUtrHutJN28e |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 968)
- GlassWireSetup.exe (PID: 7680)
SUSPICIOUS
The process creates files with name similar to system file names
- GlassWireSetup.exe (PID: 7680)
Malware-specific behavior (creating "System.dll" in Temp)
- GlassWireSetup.exe (PID: 7680)
Process drops legitimate windows executable
- GlassWireSetup.exe (PID: 7680)
- vc_redist.x86.exe (PID: 7784)
- vc_redist.x86.exe (PID: 7808)
- VC_redist.x86.exe (PID: 7856)
- msiexec.exe (PID: 4120)
- VC_redist.x86.exe (PID: 5256)
Executable content was dropped or overwritten
- GlassWireSetup.exe (PID: 7680)
- vc_redist.x86.exe (PID: 7784)
- vc_redist.x86.exe (PID: 7808)
- VC_redist.x86.exe (PID: 5048)
- VC_redist.x86.exe (PID: 7856)
- VC_redist.x86.exe (PID: 5256)
- drvinst.exe (PID: 4488)
- rundll32.exe (PID: 4464)
- drvinst.exe (PID: 2800)
Starts a Microsoft application from unusual location
- vc_redist.x86.exe (PID: 7784)
- vc_redist.x86.exe (PID: 7808)
- VC_redist.x86.exe (PID: 7856)
Searches for installed software
- vc_redist.x86.exe (PID: 7808)
- dllhost.exe (PID: 7900)
Reads security settings of Internet Explorer
- vc_redist.x86.exe (PID: 7808)
Starts itself from another location
- vc_redist.x86.exe (PID: 7808)
Executes as Windows Service
- VSSVC.exe (PID: 7944)
- GWCtlSrv.exe (PID: 5020)
There is functionality for taking screenshot (YARA)
- GlassWireSetup.exe (PID: 7680)
Application launched itself
- VC_redist.x86.exe (PID: 2960)
- VC_redist.x86.exe (PID: 5048)
The process drops C-runtime libraries
- msiexec.exe (PID: 4120)
Drops a system driver (possible attempt to evade defenses)
- GlassWireSetup.exe (PID: 7680)
- rundll32.exe (PID: 4464)
- drvinst.exe (PID: 2800)
Uses RUNDLL32.EXE to load library
- GlassWireSetup.exe (PID: 7680)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- GlassWireSetup.exe (PID: 7680)
- wevtutil.exe (PID: 6392)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 660)
INFO
The sample compiled with english language support
- GlassWireSetup.exe (PID: 7680)
- vc_redist.x86.exe (PID: 7784)
- vc_redist.x86.exe (PID: 7808)
- VC_redist.x86.exe (PID: 7856)
- msiexec.exe (PID: 4120)
- VC_redist.x86.exe (PID: 5256)
- VC_redist.x86.exe (PID: 5048)
Checks supported languages
- GlassWireSetup.exe (PID: 7680)
- vc_redist.x86.exe (PID: 7784)
- vc_redist.x86.exe (PID: 7808)
- VC_redist.x86.exe (PID: 7856)
Create files in a temporary directory
- GlassWireSetup.exe (PID: 7680)
- vc_redist.x86.exe (PID: 7808)
Reads the computer name
- vc_redist.x86.exe (PID: 7784)
- vc_redist.x86.exe (PID: 7808)
- VC_redist.x86.exe (PID: 7856)
Process checks computer location settings
- vc_redist.x86.exe (PID: 7808)
Manages system restore points
- SrTasks.exe (PID: 5404)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:15+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x351c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.5.821.0 |
| ProductVersionNumber: | 3.5.821.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | GlassWire |
| FileDescription: | GlassWire Setup |
| FileVersion: | 3,5,821,0 |
| LegalCopyright: | (c) 2025 GlassWire |
| OriginalFileName: | glasswire-setup-3.5.821.0-full.exe |
| ProductName: | GlassWire |
| ProductVersion: | 3,5,821,0 |
Total processes
174
Monitored processes
44
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\WINDOWS\explorer.exe" "C:\Program Files (x86)\GlassWire\glasswire.exe" | C:\Windows\explorer.exe | — | GlassWireSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wevtutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\WINDOWS\system32\net.exe" start gwdrv | C:\Windows\System32\net.exe | — | GlassWireSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | "C:\Program Files (x86)\GlassWire\GWCrashpadHandler.exe" --no-rate-limit --database=C:\ProgramData\glasswire\.sentry-native\system-service --metrics-dir=C:\ProgramData\glasswire\.sentry-native\system-service --url=https://o987771.ingest.us.sentry.io:443/api/4507899343601664/minidump/?sentry_client=sentry.native/0.7.8&sentry_key=04e57d3832851252464860012085bbb2 --attachment=C:\ProgramData\glasswire\.sentry-native\system-service\7ccf9baf-afad-423f-974e-751c38af2f9c.run\__sentry-event --attachment=C:\ProgramData\glasswire\.sentry-native\system-service\7ccf9baf-afad-423f-974e-751c38af2f9c.run\__sentry-breadcrumb1 --attachment=C:\ProgramData\glasswire\.sentry-native\system-service\7ccf9baf-afad-423f-974e-751c38af2f9c.run\__sentry-breadcrumb2 --initial-client-data=0x364,0x368,0x36c,0x340,0x370,0x207f94c,0x207f960,0x207f970 | C:\Program Files (x86)\GlassWire\GWCrashpadHandler.exe | — | GWCtlSrv.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\GlassWire\GWCtlSrv.exe" "-s" | C:\Program Files (x86)\GlassWire\GWCtlSrv.exe | GlassWireSetup.exe | ||||||||||||
User: admin Company: GlassWire Integrity Level: HIGH Description: GlassWire Control Service Exit code: 0 Version: 3.5.821.0 Modules
| |||||||||||||||
| 2152 | "C:\Program Files (x86)\GlassWire\GlassWire.exe" | C:\Program Files (x86)\GlassWire\GlassWire.exe | explorer.exe | ||||||||||||
User: admin Company: GlassWire Integrity Level: MEDIUM Description: GlassWire Version: 3.5.821.0 Modules
| |||||||||||||||
| 2800 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{edd5494f-332a-7944-8eeb-48e615e6755e}\gwdrv.inf" "9" "4e7eab47b" "00000000000001D4" "WinSta0\Default" "00000000000001DC" "208" "C:\WINDOWS\system32\drivers" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2960 | "C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe" -uninstall -quiet -burn.related.upgrade -burn.ancestors={4373d0b5-4457-4a80-bad9-029de8df097b} -burn.filehandle.self=1124 -burn.embedded BurnPipe.{88A2A0DD-B433-4B86-84A9-EF38717C5190} {4B71ED56-27A6-40C9-B026-7100399D19BD} 7856 | C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe | — | VC_redist.x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 3676 | C:\WINDOWS\system32\net1 start gwdrv | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
54 850
Read events
53 836
Write events
725
Delete events
289
Modification events
| (PID) Process: | (7900) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000282D61A523C8DB01DC1E0000F41E0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7856) VC_redist.x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F5C65EA523C8DB01B01E0000B41E0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7900) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000C799B4A523C8DB01DC1E0000F41E0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7900) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000C799B4A523C8DB01DC1E0000F41E0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7900) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000000B63B9A523C8DB01DC1E0000F41E0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7900) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000815CBEA523C8DB01DC1E0000F41E0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7900) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000828C7DA623C8DB01DC1E0000F41E0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7900) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000004447FA623C8DB01DC1E0000E41F0000E80300000100000000000000000000001964C2EA07EC46479B7870F663FFE32900000000000000000000000000000000 | |||
| (PID) Process: | (7944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000C3B394A623C8DB01081F0000AC100000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
103
Suspicious files
121
Text files
95
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7808 | vc_redist.x86.exe | C:\Windows\Temp\{9FC718EA-E34C-431C-BBA1-991597465F96}\.ba\license.rtf | text | |
MD5:04B33F0A9081C10E85D0E495A1294F83 | SHA256:8099DC3CF9502C335DA829E5C755948A12E3E6DE490EB492A99DEB673D883D8B | |||
| 7808 | vc_redist.x86.exe | C:\Windows\Temp\{9FC718EA-E34C-431C-BBA1-991597465F96}\.ba\1029\thm.wxl | xml | |
MD5:16343005D29EC431891B02F048C7F581 | SHA256:07FB3EC174F25DFBE532D9D739234D9DFDA8E9D34F01FE660C5B4D56989FA779 | |||
| 7808 | vc_redist.x86.exe | C:\Windows\Temp\{9FC718EA-E34C-431C-BBA1-991597465F96}\.ba\1028\license.rtf | text | |
MD5:2B063D92663595DFE4781AE687A03D86 | SHA256:44C76290F7A2E45940E8338912FEB49BCF4E071CFA85D2D34762857743ACBC8D | |||
| 7680 | GlassWireSetup.exe | C:\Users\admin\AppData\Local\Temp\nsa10B7.tmp\eventlog.man | xml | |
MD5:690FF28D524728616F1ADA1B5071BF13 | SHA256:909D481F3FBFDFBCC18B9C9743F8C9C00D822671013A8BB521D9F3E7E949FC6D | |||
| 7680 | GlassWireSetup.exe | C:\Users\admin\AppData\Local\Temp\nsa10B7.tmp\GWInstSt.exe | executable | |
MD5:3165072385F1C183BF25FFC27D67685A | SHA256:C3FC3942BE83E3EA62B1802304C1DA542E11AEA73EA148E9EC5FCC267A619B83 | |||
| 7808 | vc_redist.x86.exe | C:\Windows\Temp\{9FC718EA-E34C-431C-BBA1-991597465F96}\.ba\wixstdba.dll | executable | |
MD5:F68F43F809840328F4E993A54B0D5E62 | SHA256:E921F69B9FB4B5AD4691809D06896C5F1D655AB75E0CE94A372319C243C56D4E | |||
| 7808 | vc_redist.x86.exe | C:\Windows\Temp\{9FC718EA-E34C-431C-BBA1-991597465F96}\.ba\thm.wxl | xml | |
MD5:FBFCBC4DACC566A3C426F43CE10907B6 | SHA256:70400F181D00E1769774FF36BCD8B1AB5FBC431418067D31B876D18CC04EF4CE | |||
| 7784 | vc_redist.x86.exe | C:\Windows\Temp\{3DD4C0A9-B833-4A20-95CD-6C41EF635934}\.cr\vc_redist.x86.exe | executable | |
MD5:38B9328B53A786141DC7D54992AA03BC | SHA256:32E2651799071C5E6C51BDAF0DF7823526B25B2F34C01F9472BB159044D62C11 | |||
| 7680 | GlassWireSetup.exe | C:\Users\admin\AppData\Local\Temp\nsa10B7.tmp\vc_redist.x86.exe | executable | |
MD5:D38126688B5647BF209606D07A90C2E6 | SHA256:ED1967C2AC27D806806D121601B526F84E497AE1B99ED139C0C4C6B50147DF4A | |||
| 7808 | vc_redist.x86.exe | C:\Windows\Temp\{9FC718EA-E34C-431C-BBA1-991597465F96}\.ba\thm.xml | xml | |
MD5:F62729C6D2540015E072514226C121C7 | SHA256:F13BAE0EC08C91B4A315BB2D86EE48FADE597E7A5440DCE6F751F98A3A4D6916 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
90
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2104 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |