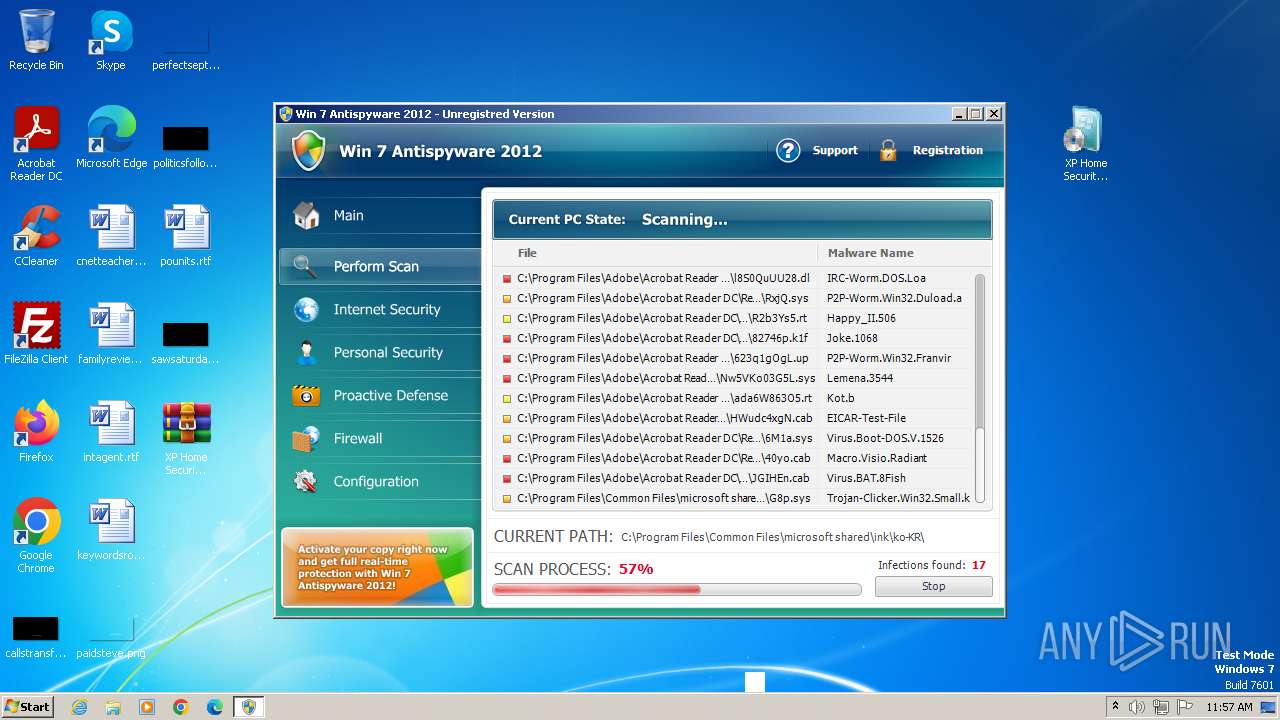
| File name: | XP Home Security 2012.zip |
| Full analysis: | https://app.any.run/tasks/a5210790-703e-4c9d-94f1-49a9e46f6182 |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2024, 10:54:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
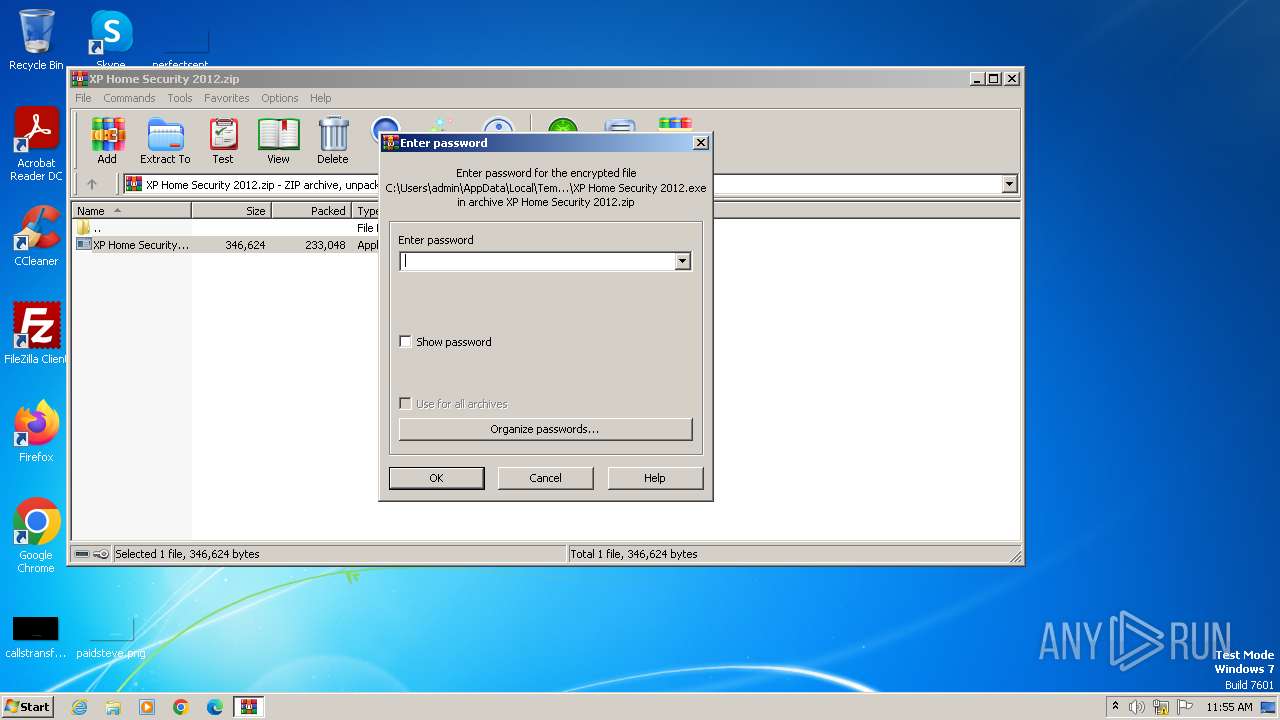
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 773AAEDD7C9F0715718A1CEB51A2545A |
| SHA1: | C1D430D71B8DBACBB0A851C6BCB468D5C9F266A9 |
| SHA256: | F68CAC5BF99FC78855AC64454A8637D049818BEA9005860D7D237D8549BB225E |
| SSDEEP: | 6144:irlwNSOmim2tSJNW101O07w5nsMeYsAe0CowsxoJCA2T/Eq8PshuU:iibmiVAg01F7s5elU3xu2T/EqthuU |
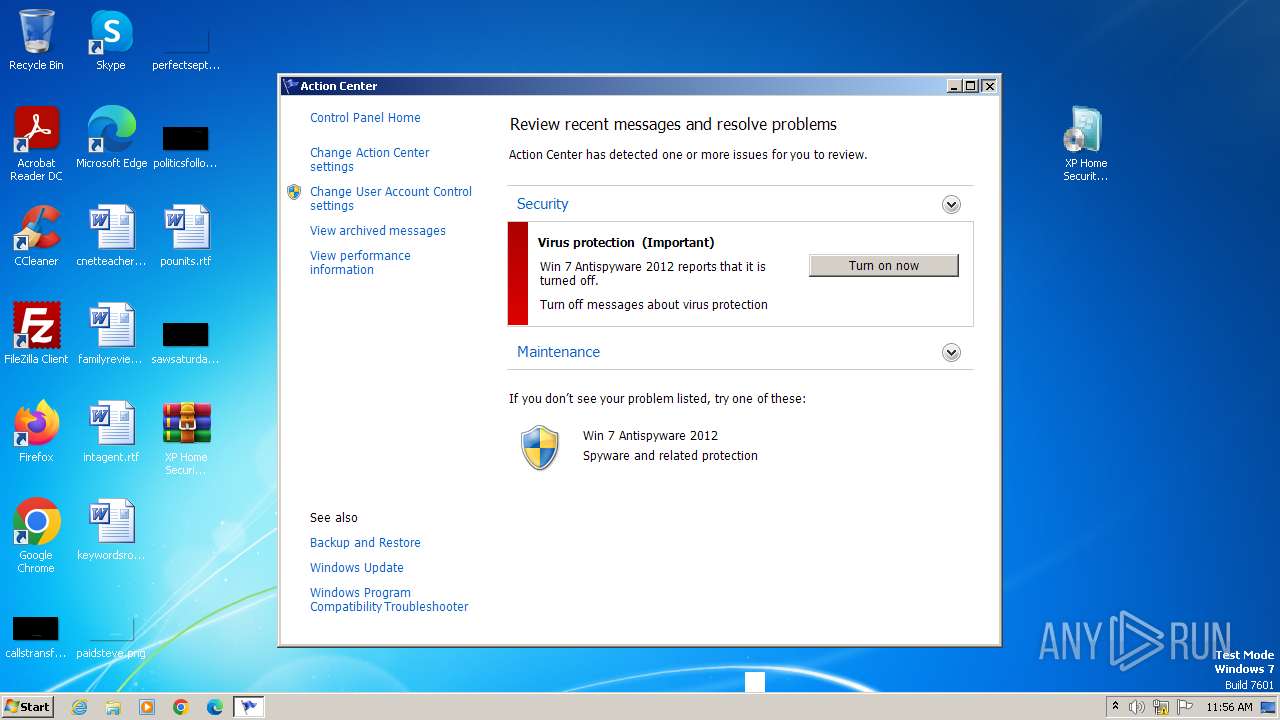
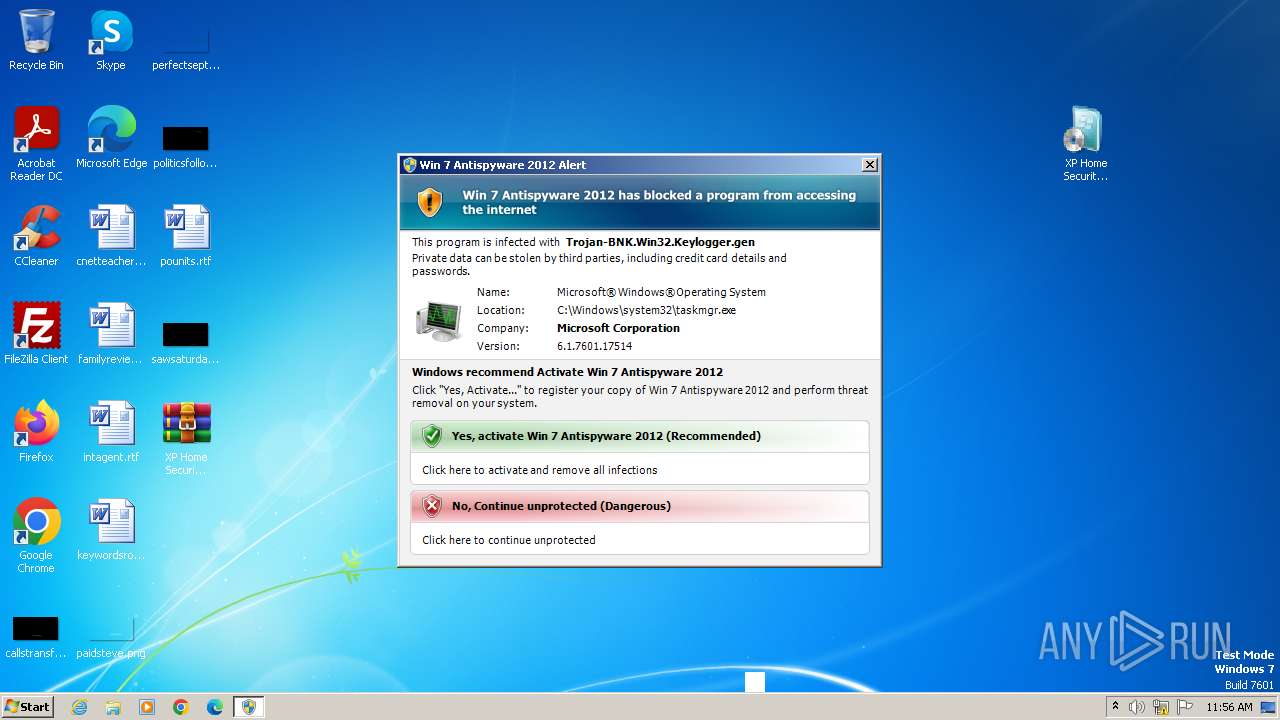
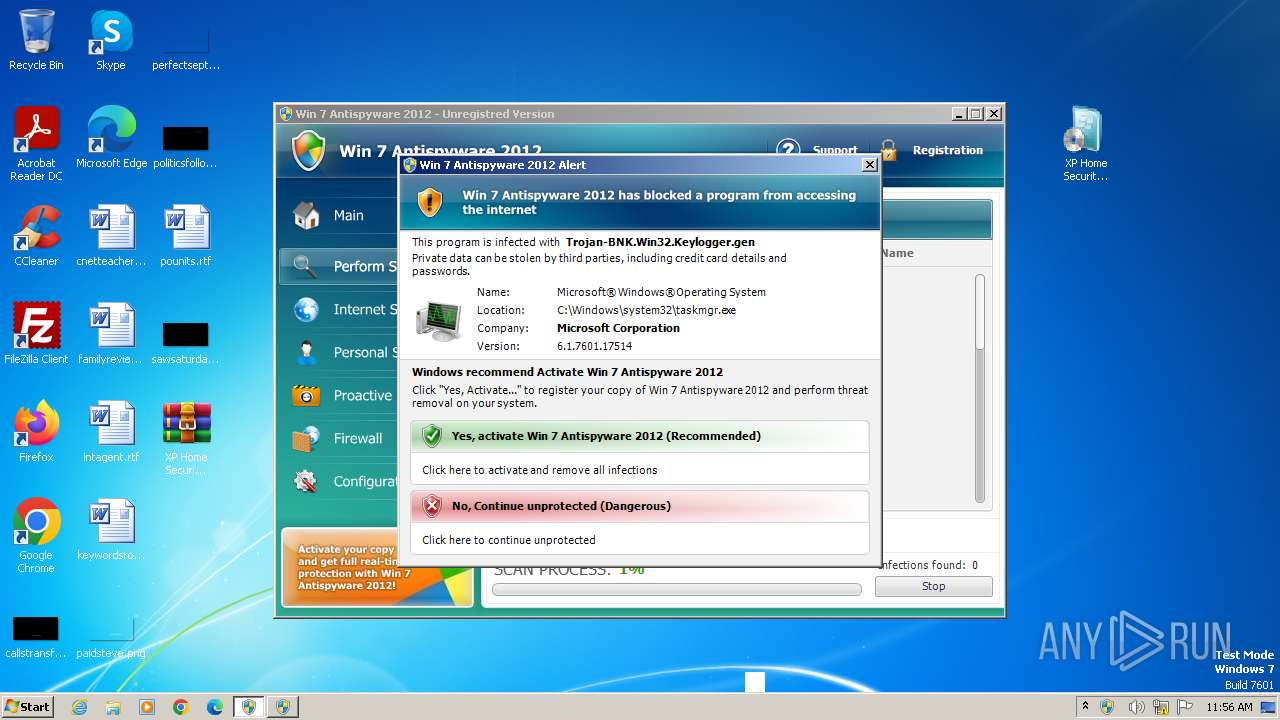
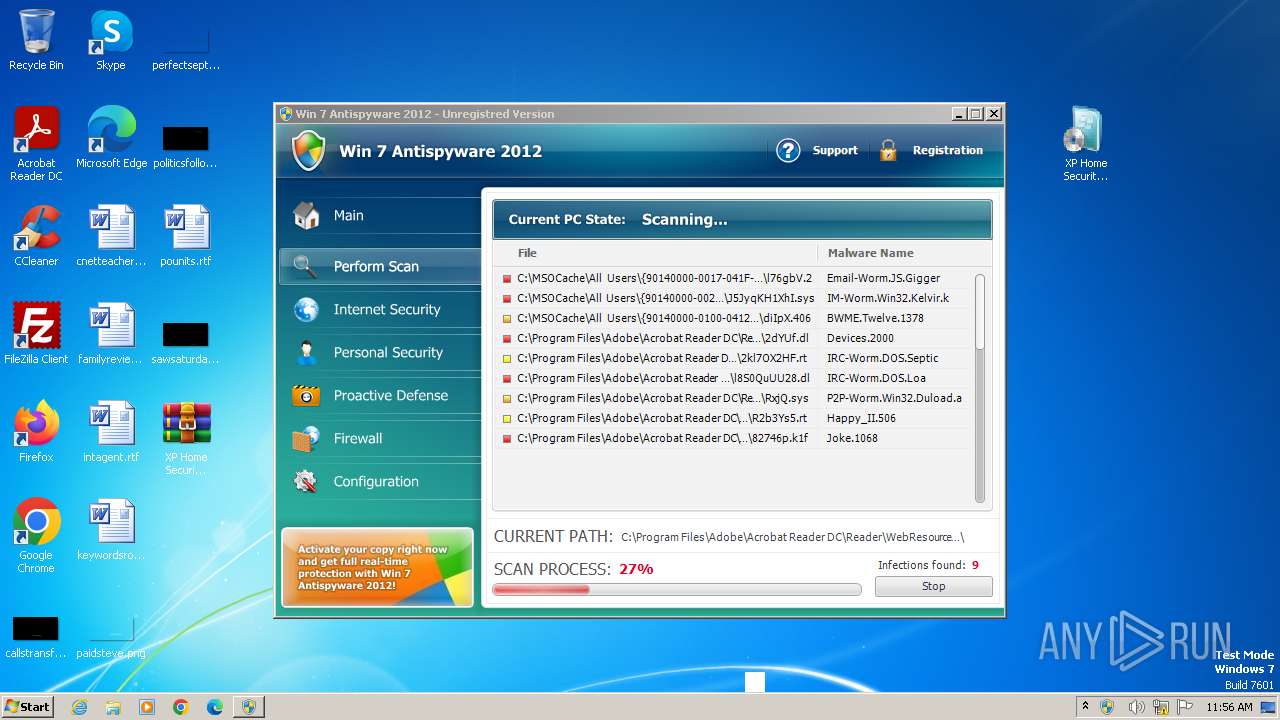
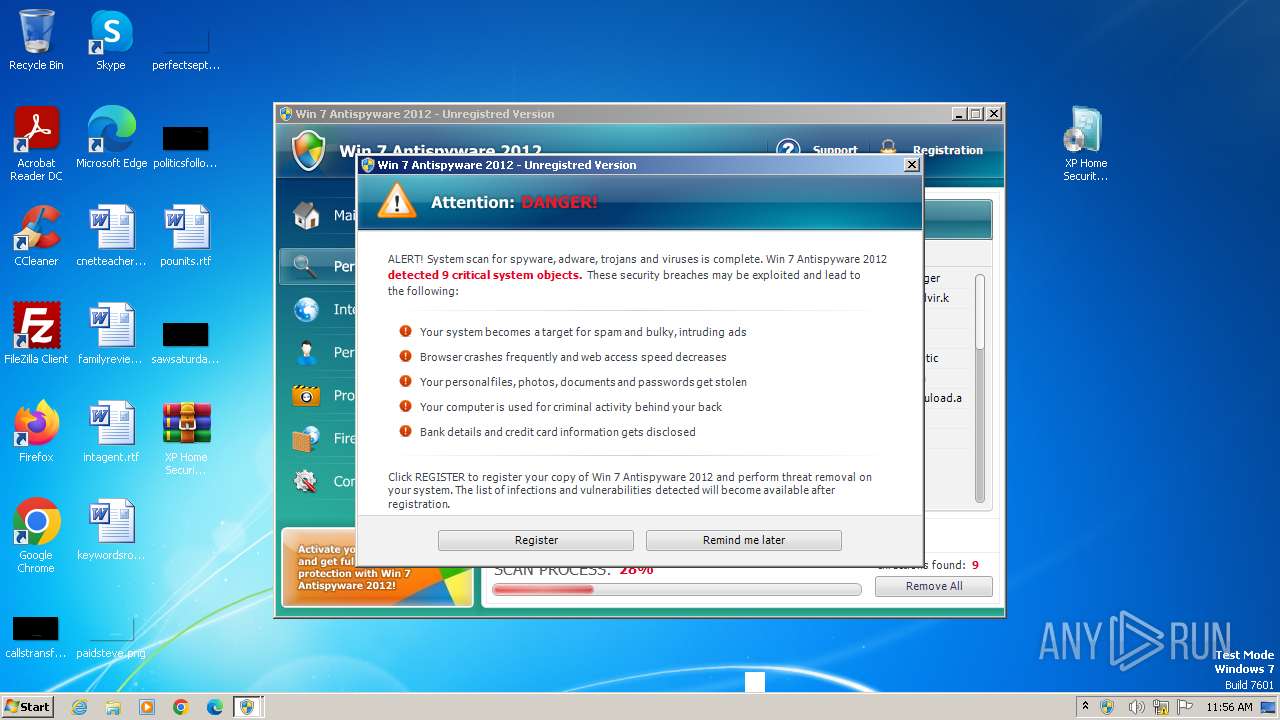
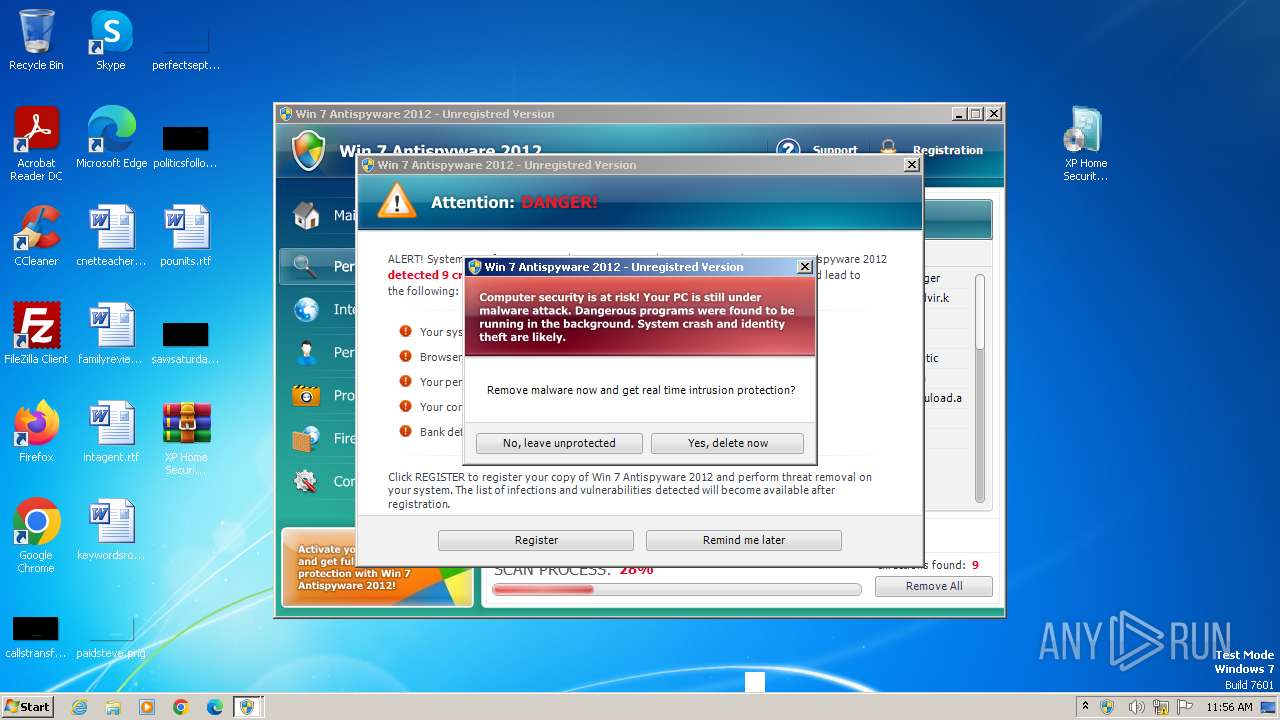
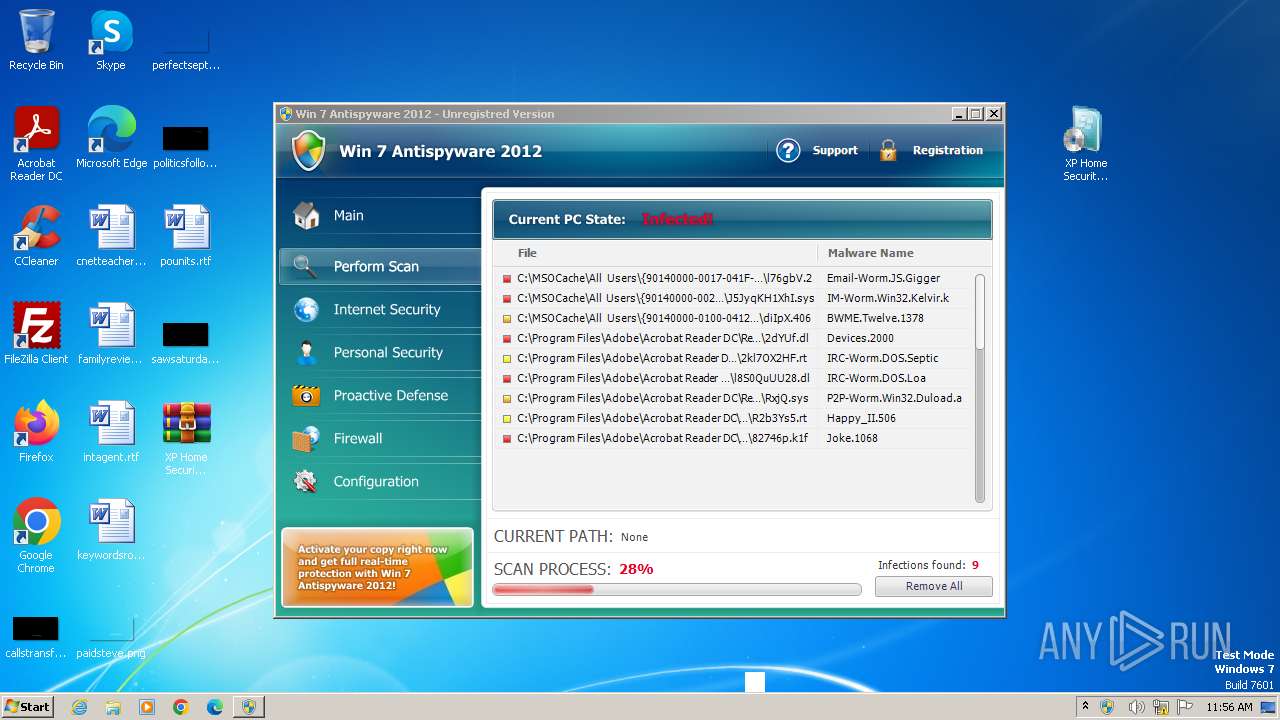
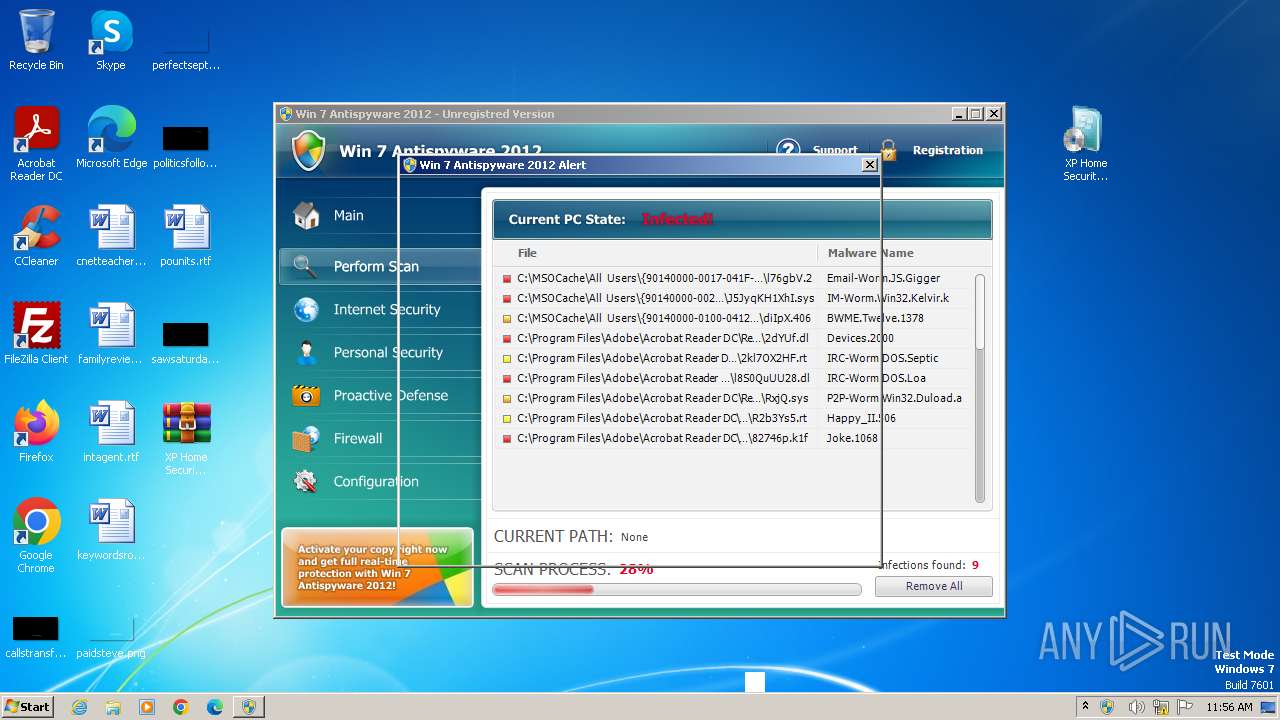
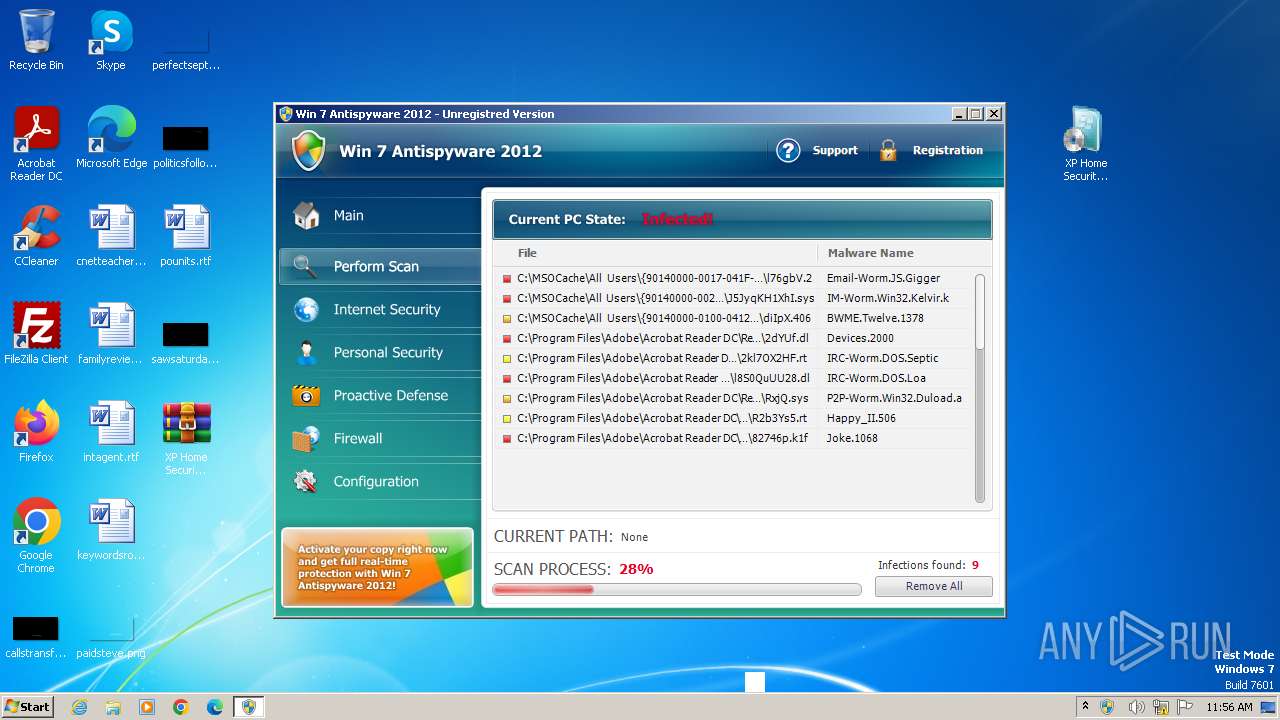
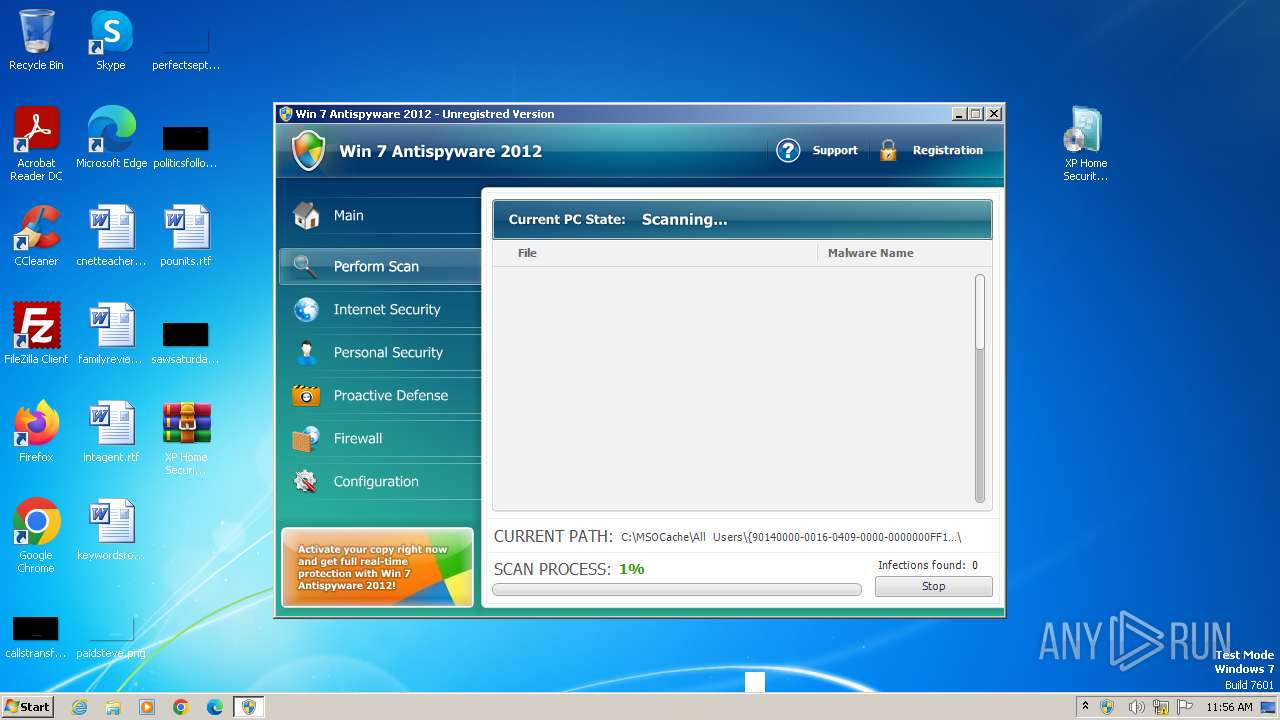
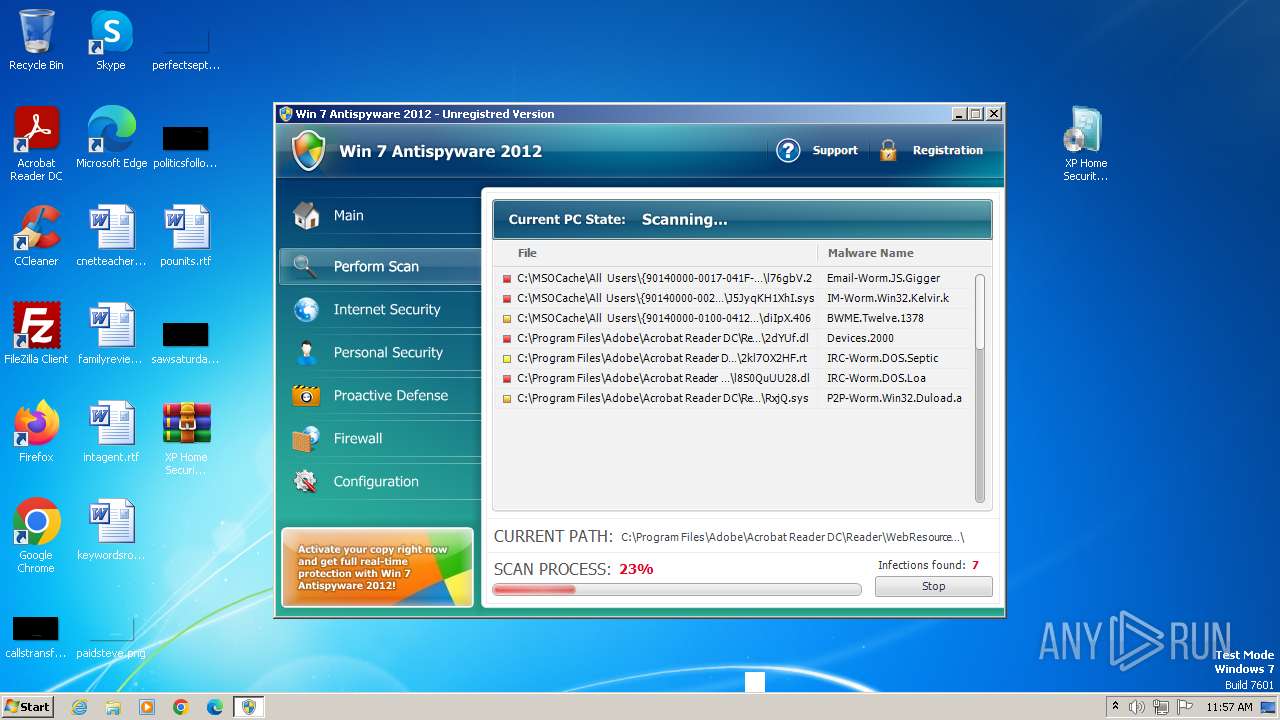
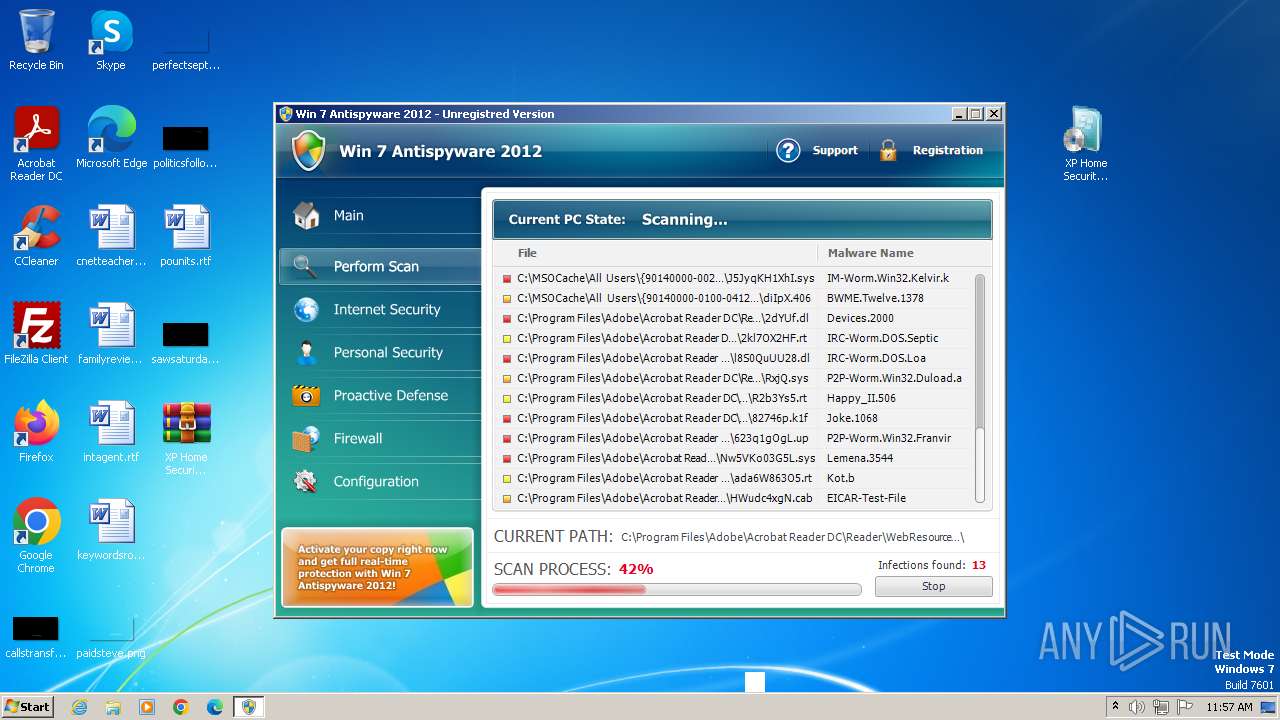
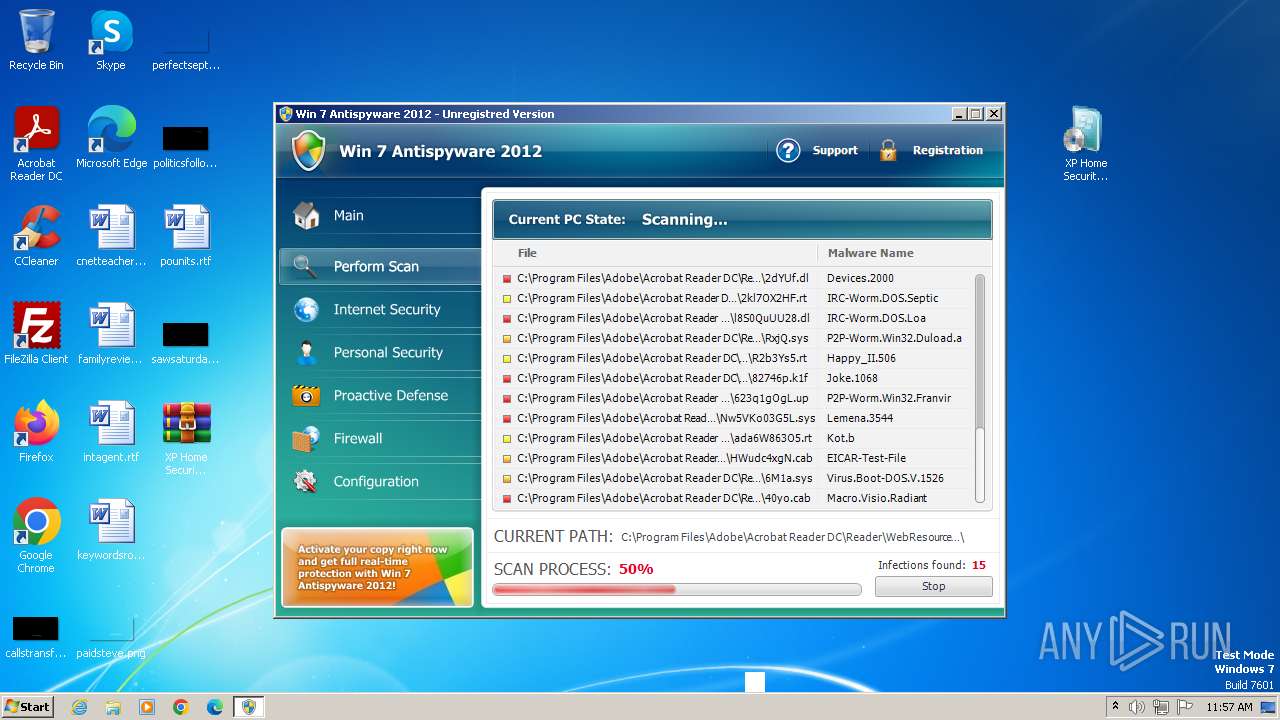
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3980)
- XP Home Security 2012.exe (PID: 1116)
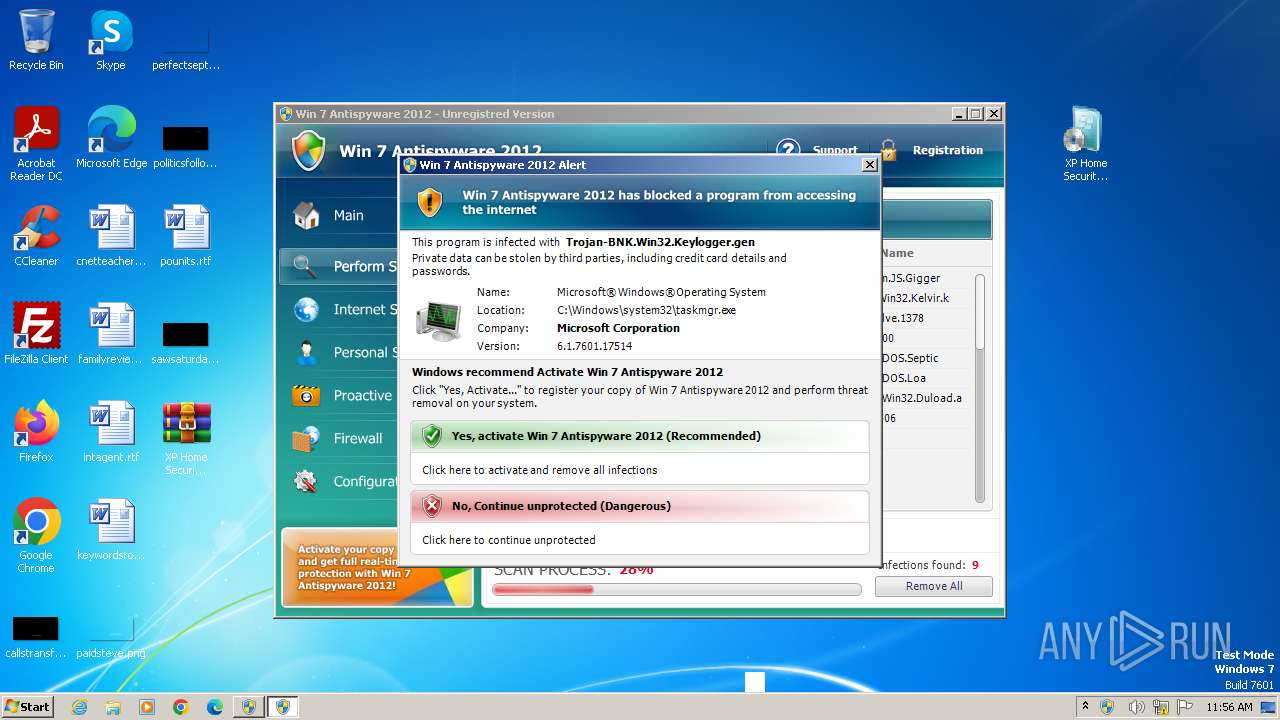
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3980)
- XP Home Security 2012.exe (PID: 1116)
Starts a Microsoft application from unusual location
- XP Home Security 2012.exe (PID: 1116)
Executable content was dropped or overwritten
- XP Home Security 2012.exe (PID: 1116)
Changes default file association
- XP Home Security 2012.exe (PID: 1116)
Reads Microsoft Outlook installation path
- XP Home Security 2012.exe (PID: 1116)
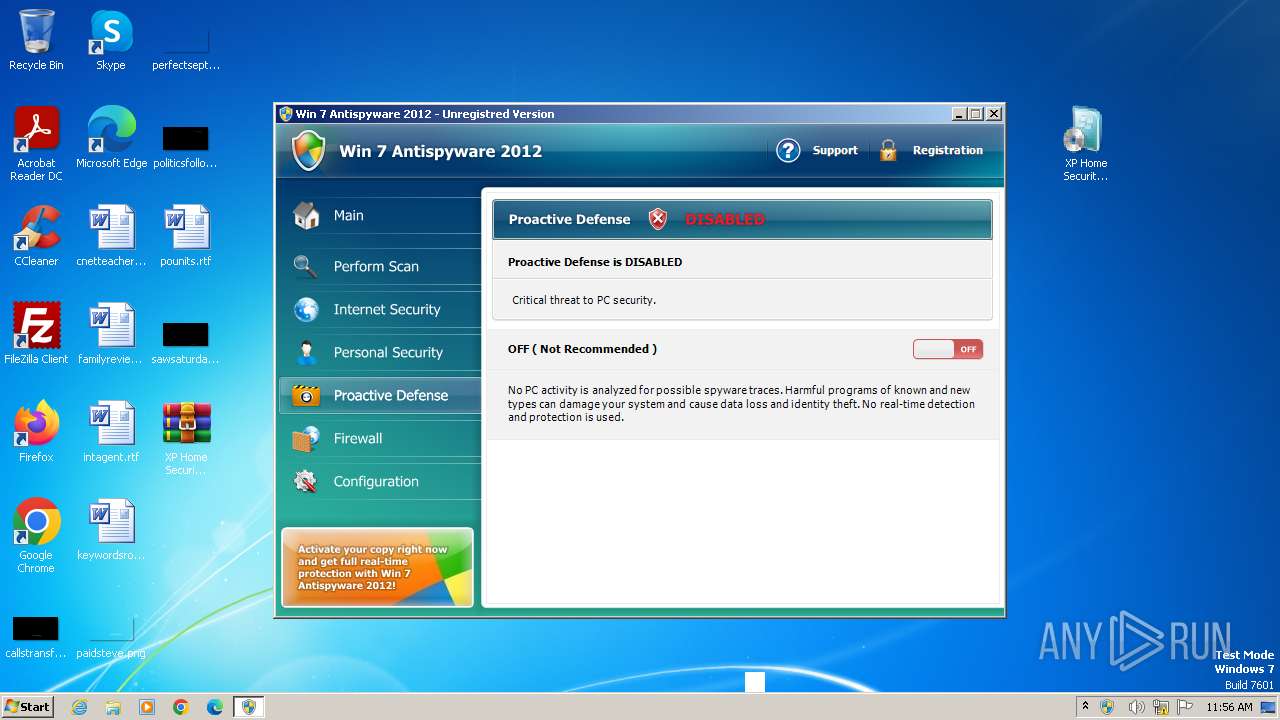
INFO
Manual execution by a user
- XP Home Security 2012.exe (PID: 1116)
- uoz.exe (PID: 568)
- uoz.exe (PID: 2236)
- wmpnscfg.exe (PID: 2532)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3980)
Checks supported languages
- XP Home Security 2012.exe (PID: 1116)
- uoz.exe (PID: 568)
- uoz.exe (PID: 2236)
- wmpnscfg.exe (PID: 2532)
Creates files or folders in the user directory
- XP Home Security 2012.exe (PID: 1116)
Reads the computer name
- XP Home Security 2012.exe (PID: 1116)
- wmpnscfg.exe (PID: 2532)
Reads the machine GUID from the registry
- XP Home Security 2012.exe (PID: 1116)
Creates files in the program directory
- XP Home Security 2012.exe (PID: 1116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2018:08:18 16:07:12 |
| ZipCRC: | 0x3ba39e6f |
| ZipCompressedSize: | 233048 |
| ZipUncompressedSize: | 346624 |
| ZipFileName: | XP Home Security 2012.exe |
Total processes
40
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Users\admin\AppData\Local\uoz.exe" -a "C:\Windows\system32\taskmgr.exe" /4 | C:\Users\admin\AppData\Local\uoz.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sidebar droptarget Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\Desktop\XP Home Security 2012.exe" | C:\Users\admin\Desktop\XP Home Security 2012.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sidebar droptarget Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1132 | C:\Windows\system32\wbem\unsecapp.exe -Embedding | C:\Windows\System32\wbem\unsecapp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sink to receive asynchronous callbacks for WMI client application Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\AppData\Local\uoz.exe" -a "C:\Windows\system32\taskmgr.exe" /4 | C:\Users\admin\AppData\Local\uoz.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sidebar droptarget Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2532 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\XP Home Security 2012.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 774
Read events
3 741
Write events
33
Delete events
0
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\XP Home Security 2012.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2236 | uoz.exe | C:\users\admin\appdata\roaming\3f48b916 | binary | |
MD5:1FFFAD35C98A797B9E17EB03F7D59FA9 | SHA256:9A955A4453A8A2FCDB5784DB692B7D63ECFF907843DECD4EFBD8E27426FF1CC5 | |||
| 1116 | XP Home Security 2012.exe | C:\Users\admin\AppData\Local\uoz.exe | executable | |
MD5:1E8615F03FD397E3128A3367E5951B2D | SHA256:AD9A9565CF528FC6E0809E694B6A13659AEC10D14CBCF7138AAB14F1CA08C4BF | |||
| 2236 | uoz.exe | C:\programdata\c5c2a88a | binary | |
MD5:1EC9851C1C808D3A0484F0C358DA237E | SHA256:1C57DD0715CADF54CC13356A89A75057BCB46F9991209CECE0EE6B96AD63DDD8 | |||
| 2236 | uoz.exe | C:\users\admin\appdata\roaming\microsoft\windows\templates\11c05e7d | binary | |
MD5:011F28B43653B004550509261FA93950 | SHA256:74AD6DB44232008EE1F584C9551EF45EA6235902308F7DCE7BB741D4988EE1B0 | |||
| 2236 | uoz.exe | C:\users\admin\appdata\local\2b614819 | binary | |
MD5:6F968BA037B83F6B49B253DD406B96E9 | SHA256:6D7F90ED9D43D19D8560407F9EB3886D3C9EB7FBAA1F599CB1F1B9C1C56236B6 | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3980.44915\XP Home Security 2012.exe | executable | |
MD5:1E8615F03FD397E3128A3367E5951B2D | SHA256:AD9A9565CF528FC6E0809E694B6A13659AEC10D14CBCF7138AAB14F1CA08C4BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
100
DNS requests
48
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1116 | XP Home Security 2012.exe | 49.13.77.253:80 | suxopuxoki.com | Hetzner Online GmbH | DE | unknown |
1116 | XP Home Security 2012.exe | 20.236.44.162:80 | microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1116 | XP Home Security 2012.exe | 20.112.250.133:80 | microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1116 | XP Home Security 2012.exe | 20.76.201.171:80 | microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1116 | XP Home Security 2012.exe | 20.70.246.20:80 | microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | AU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
suxopuxoki.com |
| unknown |
wisobivesu.com |
| unknown |
fonywonunisiwu.com |
| unknown |
huxogelew.com |
| unknown |
xopimynycerev.com |
| unknown |
nibycexadytyn.com |
| unknown |
nypucevys.com |
| unknown |
pulumacugefel.com |
| unknown |
sucejukas.com |
| unknown |
qikodutef.com |
| unknown |