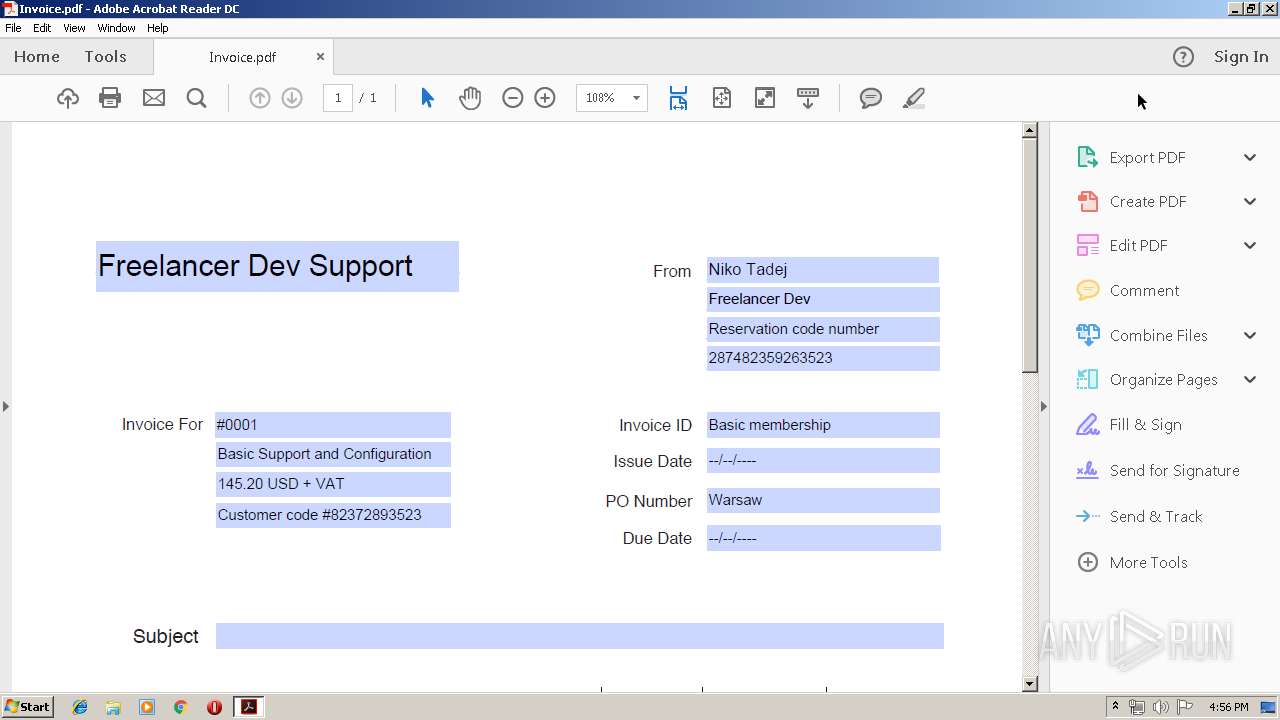
| File name: | 7z1900.msi |
| Full analysis: | https://app.any.run/tasks/58edcd2e-723b-4de1-9f96-752f51072dc0 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2019, 15:56:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Dec 11 11:47:44 2009, Security: 0, Code page: 1252, Revision Number: {E0F63E23-BB2A-4641-AC60-A866CEBD2E50}, Number of Words: 10, Subject: PDF Files and Configuration of Computer, Author: DF Files and Configuration of Computer, Name of Creating Application: Advanced Installer 15.9 build daae28bc, Template: ;1033, Comments: This installer database contains the logic and data required to install PDF Files and Configuration of Computer., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 1860AF916B007F1013EF5746E95400CD |
| SHA1: | 0E41C17B397D1ABB448445F520F5B4AE236BE77E |
| SHA256: | F64936BCB446AB56B259D8BCD1D47E452485B98A7D7182F2A02FD899DBDA55F5 |
| SSDEEP: | 98304:RYDo9Ai6UtaL9u8/vN/auoq3IovBYRN1IP/MjdSZbhSr:76UIY8t/S0vB6NCP/M02r |
MALICIOUS
Writes to a start menu file
- msiexec.exe (PID: 1544)
SUSPICIOUS
Executed via COM
- DrvInst.exe (PID: 4084)
Executed as Windows Service
- vssvc.exe (PID: 1832)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1544)
Creates files in the user directory
- msiexec.exe (PID: 1544)
Reads Environment values
- MSI1BBD.tmp (PID: 4056)
Creates files in the program directory
- AdobeARM.exe (PID: 2672)
INFO
Searches for installed software
- msiexec.exe (PID: 1544)
Low-level read access rights to disk partition
- vssvc.exe (PID: 1832)
Application launched itself
- msiexec.exe (PID: 1544)
- AcroRd32.exe (PID: 3860)
- RdrCEF.exe (PID: 3396)
Changes settings of System certificates
- DrvInst.exe (PID: 4084)
Starts application with an unusual extension
- msiexec.exe (PID: 1544)
Adds / modifies Windows certificates
- DrvInst.exe (PID: 4084)
Manual execution by user
- explorer.exe (PID: 3444)
Application was dropped or rewritten from another process
- MSI1BBD.tmp (PID: 4056)
Reads Internet Cache Settings
- AcroRd32.exe (PID: 3860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2009:12:11 11:47:44 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {E0F63E23-BB2A-4641-AC60-A866CEBD2E50} |
| Words: | 10 |
| Subject: | PDF Files and Configuration of Computer |
| Author: | DF Files and Configuration of Computer |
| LastModifiedBy: | - |
| Software: | Advanced Installer 15.9 build daae28bc |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install PDF Files and Configuration of Computer. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
50
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1252 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3396.0.1675586573\490431651" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1484 | C:\Windows\system32\MsiExec.exe -Embedding A1CF15C7F14732B281D4895315175C5F | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1544 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1832 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Invoice.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2328 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2360 | C:\Windows\system32\MsiExec.exe -Embedding 9F2485B627A83CF8560E340571BBE917 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
| 2900 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\7z1900.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3396 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
1 209
Read events
963
Write events
234
Delete events
12
Modification events
| (PID) Process: | (2900) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1544) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000AA9E95A9EF51D501080600009C0C0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1544) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000AA9E95A9EF51D501080600009C0C0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1544) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 24 | |||
| (PID) Process: | (1544) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000A426BEA9EF51D501080600009C0C0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1544) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000A426BEA9EF51D501080600003C0B0000E8030000010000000000000000000000728D2C4AB0E64A46A5D2EABE1D2A8CBB0000000000000000 | |||
| (PID) Process: | (1832) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000007439D1A9EF51D50128070000A40F0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1832) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000007439D1A9EF51D50128070000E40E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1832) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000007439D1A9EF51D50128070000900B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1832) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000007439D1A9EF51D50128070000E80B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
15
Text files
49
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CabD56A.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\TarD56B.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CabD57B.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\TarD57C.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CabD639.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\TarD63A.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSID754.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSID7D2.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSID7F2.tmp | — | |
MD5:— | SHA256:— | |||
| 2900 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSID841.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
7
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3860 | AcroRd32.exe | GET | 304 | 2.16.186.97:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
3860 | AcroRd32.exe | GET | 304 | 2.16.186.97:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
3860 | AcroRd32.exe | GET | 304 | 2.16.186.97:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
2900 | msiexec.exe | GET | 200 | 67.27.150.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.6 Kb | whitelisted |
3860 | AcroRd32.exe | GET | 304 | 2.16.186.97:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
2900 | msiexec.exe | GET | 200 | 23.111.11.204:80 | http://repository.certum.pl/ctnca.cer | US | der | 959 b | whitelisted |
3860 | AcroRd32.exe | GET | 304 | 2.16.186.97:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2900 | msiexec.exe | 23.111.11.204:80 | repository.certum.pl | netDNA | US | unknown |
3860 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
3860 | AcroRd32.exe | 2.16.186.97:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
2900 | msiexec.exe | 67.27.150.254:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
repository.certum.pl |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ardownload2.adobe.com |
| whitelisted |