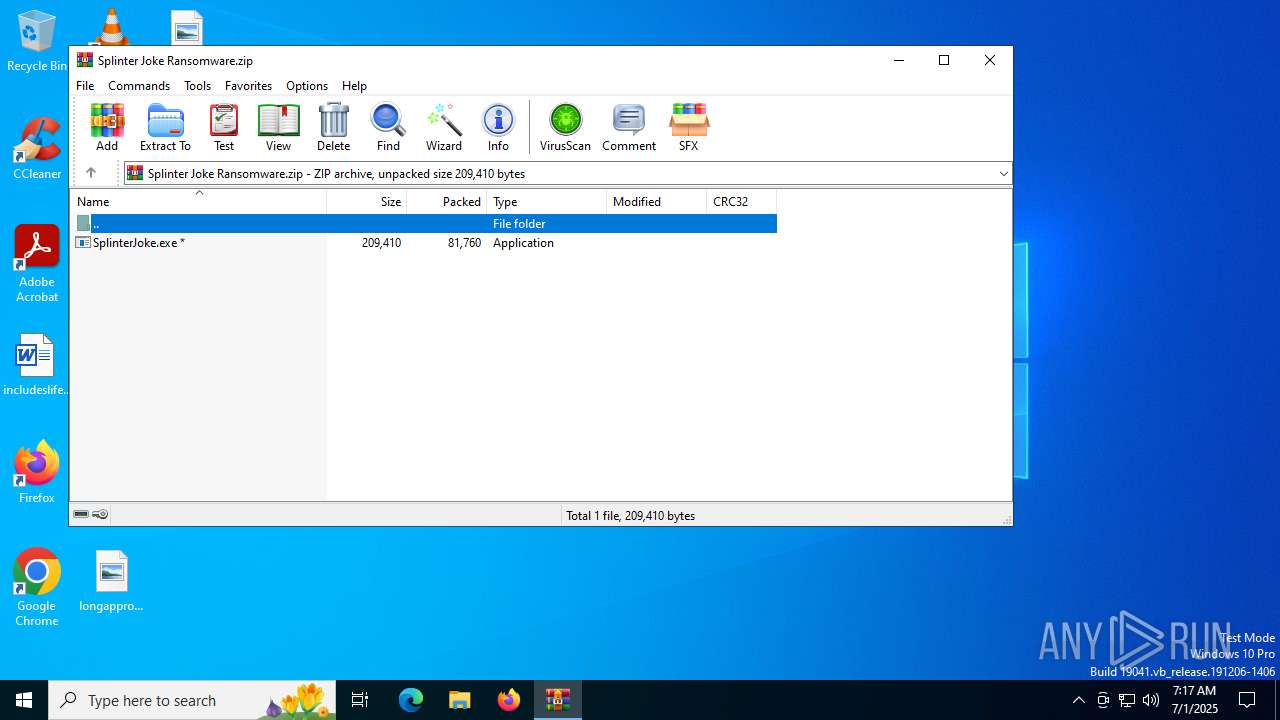
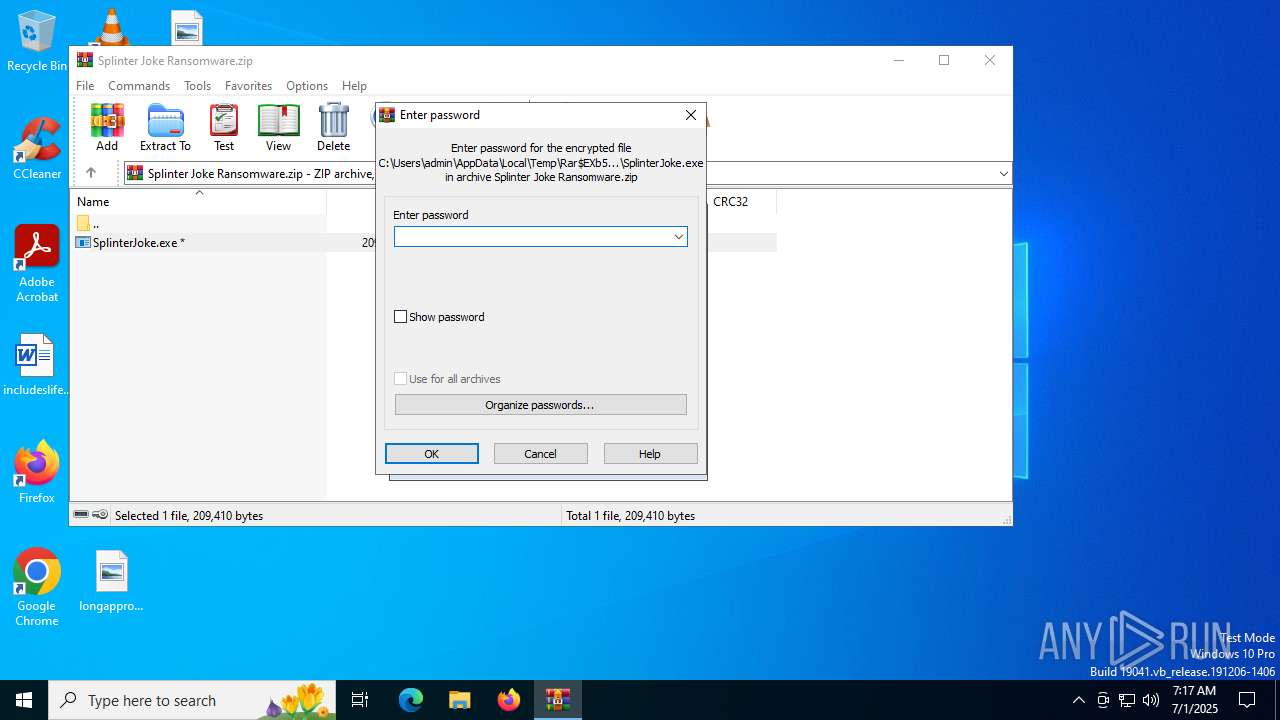
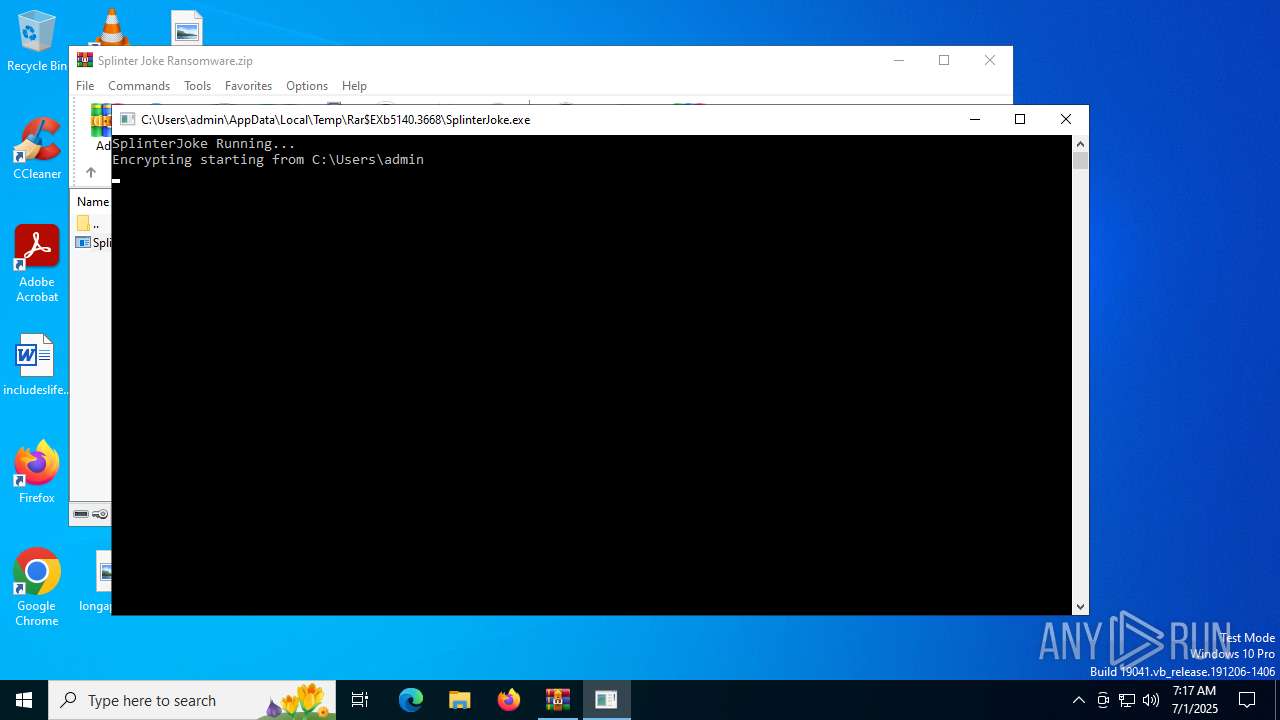
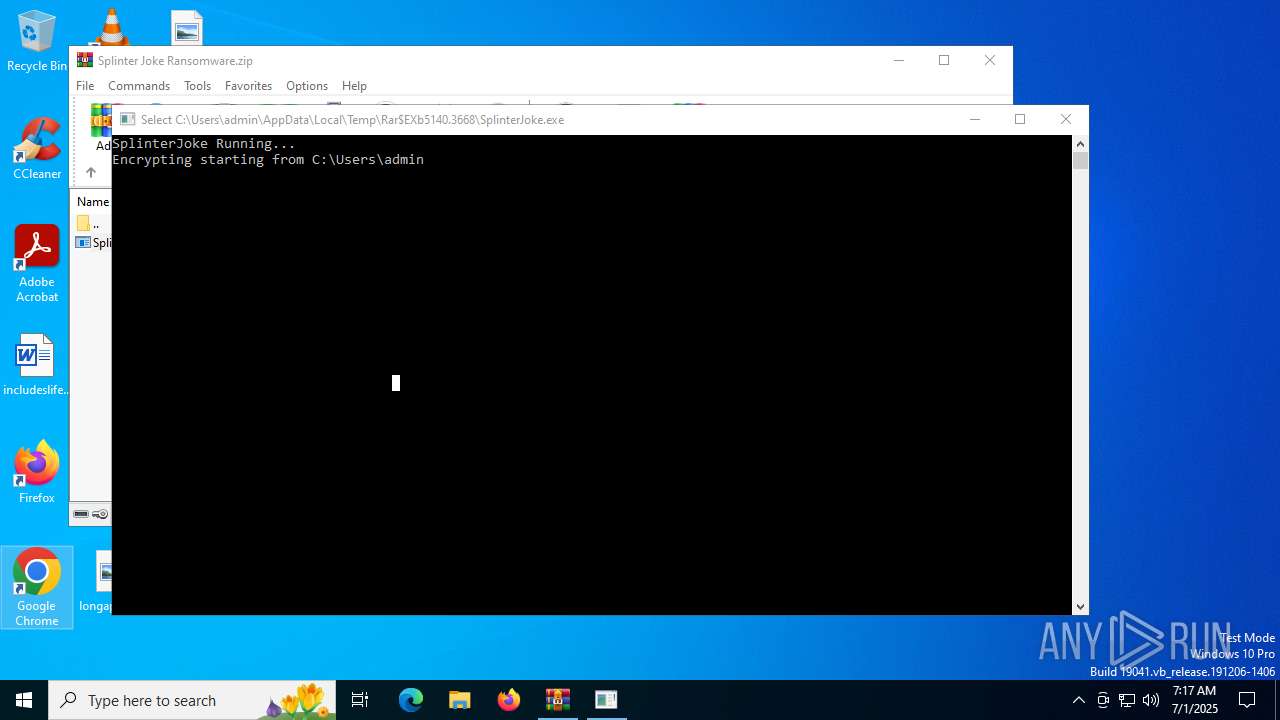
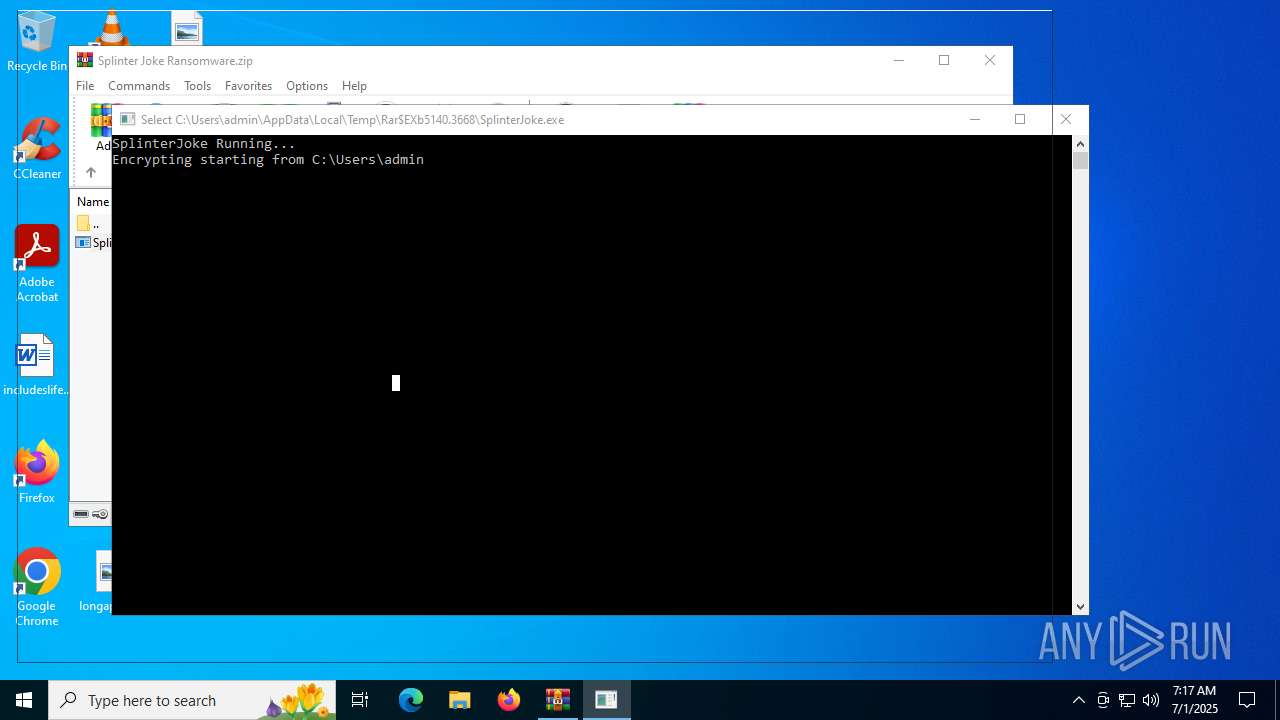
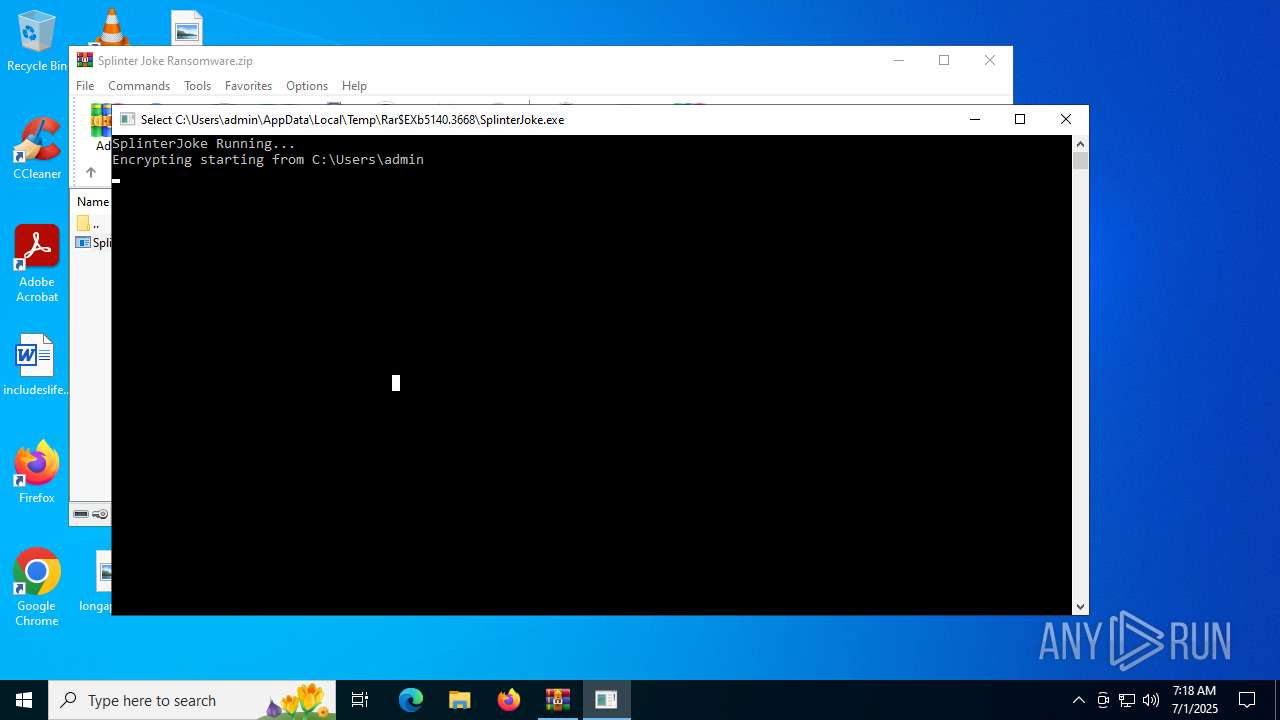
| File name: | Splinter Joke Ransomware.zip |
| Full analysis: | https://app.any.run/tasks/d19c0643-4d90-4a95-bef6-c4269165ee46 |
| Verdict: | Malicious activity |
| Analysis date: | July 01, 2025, 07:16:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | D8C92B8E8C55931089360A535D148A71 |
| SHA1: | D491E0FD50F5542409E62197265806B561B9F89A |
| SHA256: | F62606CF5A468F03A9A676C811995544D93E62C4AA6508548FFC19B2343398FC |
| SSDEEP: | 3072:Hb0KieeDriXi2N1NaIyQNHLTadOV+EzkH:bA69nyQNHLkZSkH |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5140)
Modifies files in the Chrome extension folder
- SplinterJoke.exe (PID: 7104)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5140)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5140)
Checks supported languages
- SplinterJoke.exe (PID: 7104)
Reads the computer name
- SplinterJoke.exe (PID: 7104)
Manual execution by a user
- chrome.exe (PID: 5716)
Application launched itself
- chrome.exe (PID: 5716)
- chrmstp.exe (PID: 6664)
- chrmstp.exe (PID: 7592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 81760 |
| ZipUncompressedSize: | 209410 |
| ZipFileName: | SplinterJoke.exe |
Total processes
180
Monitored processes
44
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --field-trial-handle=6684,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=1940 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --string-annotations --field-trial-handle=6220,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=6188 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3104,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=2948 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=2608,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=3760 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1980,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=1976 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --field-trial-handle=3876,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=3888 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --string-annotations --field-trial-handle=6044,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=6668 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --field-trial-handle=6572,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=7080 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --string-annotations --field-trial-handle=2376,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=2392 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3560,i,15949054147245554173,11047223478413218788,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version --mojo-platform-channel-handle=3716 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
9 782
Read events
9 755
Write events
25
Delete events
2
Modification events
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Splinter Joke Ransomware.zip | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
15
Suspicious files
1 421
Text files
253
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\{C310C6EF-5667-4A0B-A41F-7B94CE3E6917}.SplinterJoke | — | |
MD5:— | SHA256:— | |||
| 5140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb5140.3668\SplinterJoke.exe | executable | |
MD5:671AD98A0E0C83DEFA386673BED208C4 | SHA256:67628A5F04C7099346DD18957A4BC5179F5C3A07B41CA0D2A9E708DCAB54D16D | |||
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\IconCacheAcro65536.dat.SplinterJoke | binary | |
MD5:AAFD69D3370276F89C6B94AFFAD373C2 | SHA256:43AAD9E50C6ECBF8E3DD6B76A5ED9366B0F72F733ECEB3642E9AD8105C8D3386 | |||
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents | binary | |
MD5:BF046705B0F349A2AF49E5750D8B04E4 | SHA256:A3122E8B19BF4BCCD38E46F87E44C584DD8B4A51C073C811A113E2F821FA44B4 | |||
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents.SplinterJoke | binary | |
MD5:BF046705B0F349A2AF49E5750D8B04E4 | SHA256:A3122E8B19BF4BCCD38E46F87E44C584DD8B4A51C073C811A113E2F821FA44B4 | |||
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:465F19E40FFA5F5095B832E49F542EAA | SHA256:09C8022EECE9A0C06F8EFDF8D4353785BF548AD54335B3DF01EE2CFDA30F0B2F | |||
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:F544FB4B5D6B756D2FDF733E9F412D3D | SHA256:62668024D6DDA056C1F0BC510DE1AF5981560F4A00286A991CA564207EFB247A | |||
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\UserCache64.bin | binary | |
MD5:A288333ACB522F2487EC54F92380CD81 | SHA256:749BA07B9DC131DF21C042C4B390DAAC1E0F0937DA82BF556E96E748DBF39AA7 | |||
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\IconCacheAcro65536.dat | binary | |
MD5:AAFD69D3370276F89C6B94AFFAD373C2 | SHA256:43AAD9E50C6ECBF8E3DD6B76A5ED9366B0F72F733ECEB3642E9AD8105C8D3386 | |||
| 7104 | SplinterJoke.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst.SplinterJoke | binary | |
MD5:465F19E40FFA5F5095B832E49F542EAA | SHA256:09C8022EECE9A0C06F8EFDF8D4353785BF548AD54335B3DF01EE2CFDA30F0B2F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
48
DNS requests
52
Threats
37
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5444 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1204 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1204 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4400 | chrome.exe | GET | 200 | 142.250.186.78:80 | http://clients2.google.com/time/1/current?cup2key=8:zIZ5-vYF2eEpoP05ZfzV6UcQg3tftSgMbsy_vXnJ-54&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4400 | chrome.exe | GET | 302 | 172.217.16.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1232 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5444 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5444 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potentially Bad Traffic | ET INFO Possible Chrome Plugin install |
4400 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4400 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4400 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4400 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4400 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4400 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4400 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4400 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |