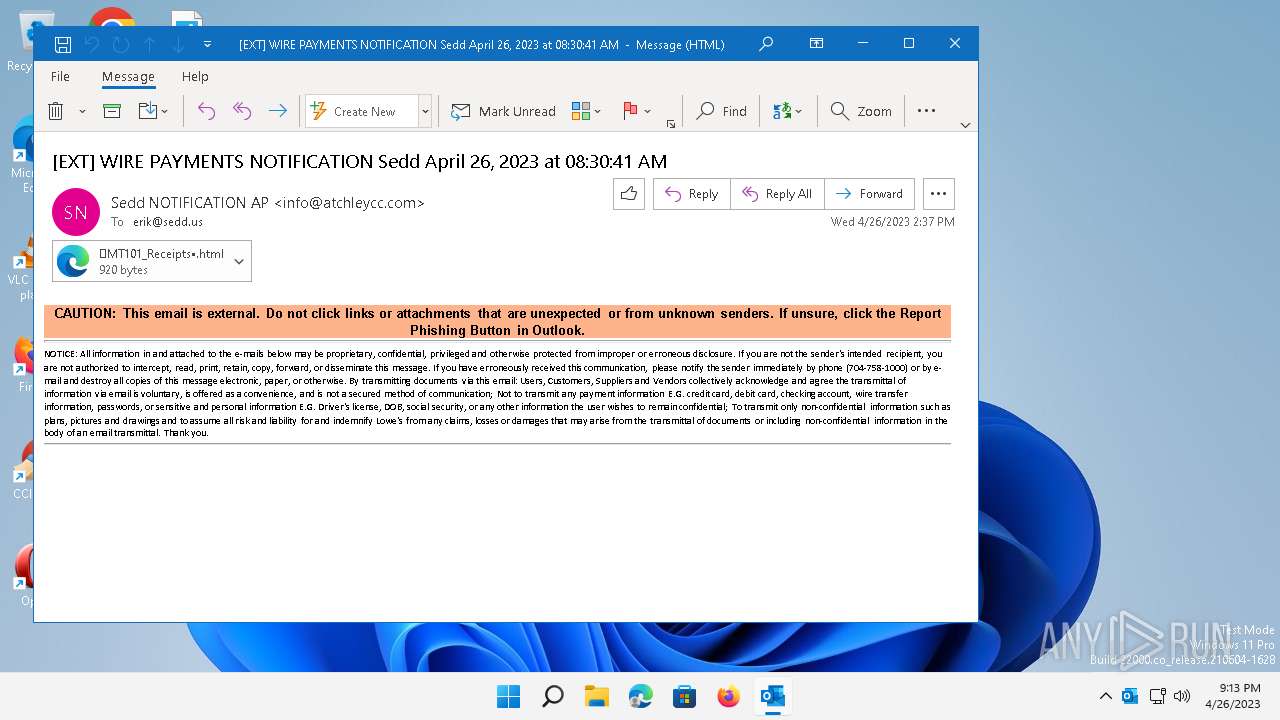
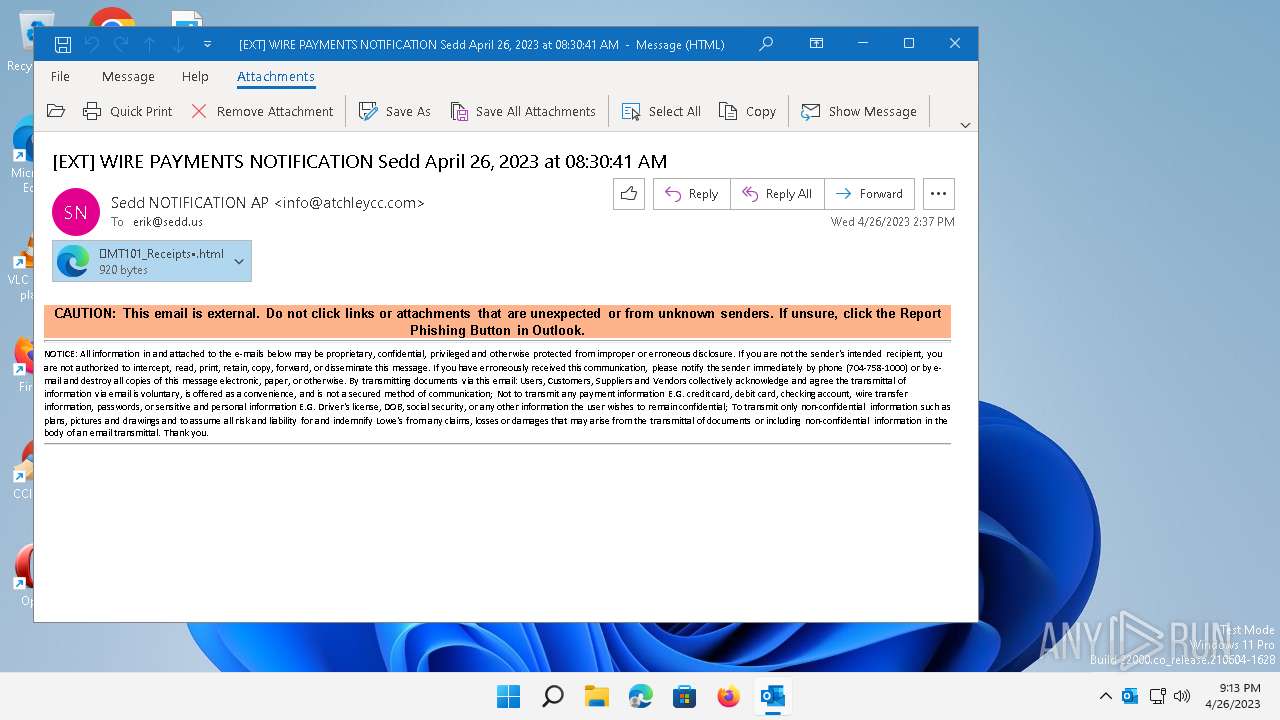
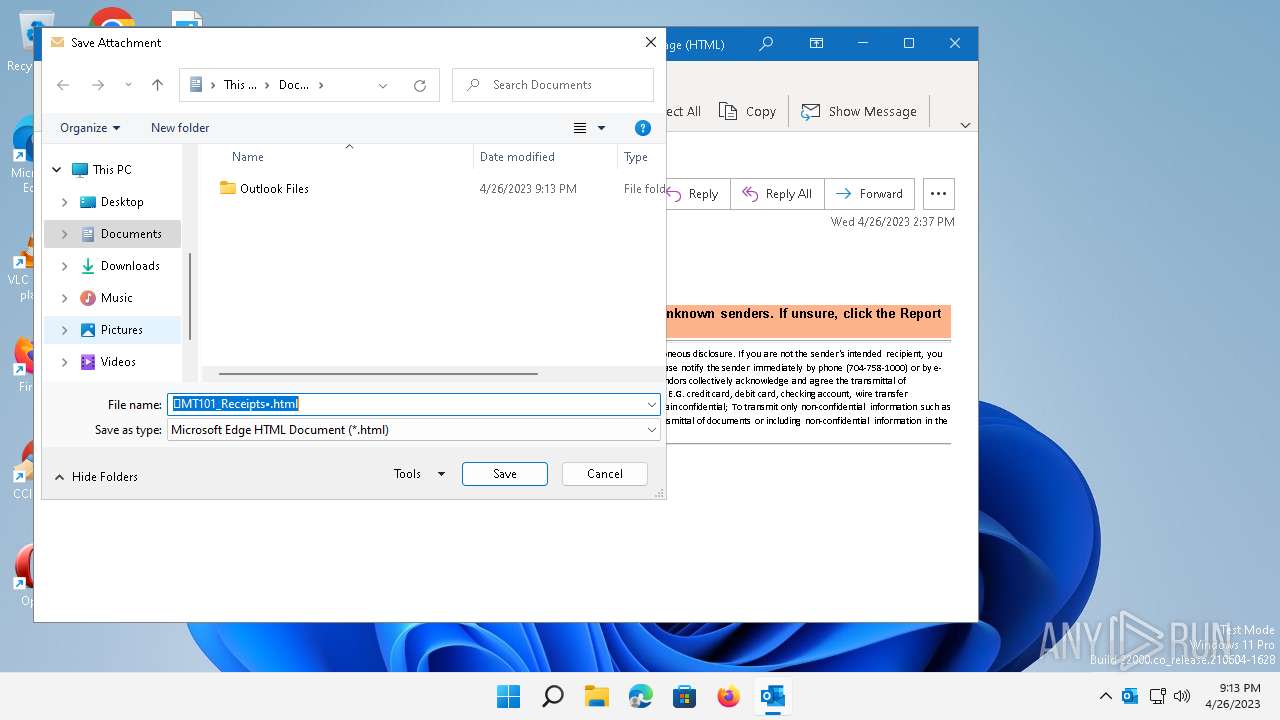
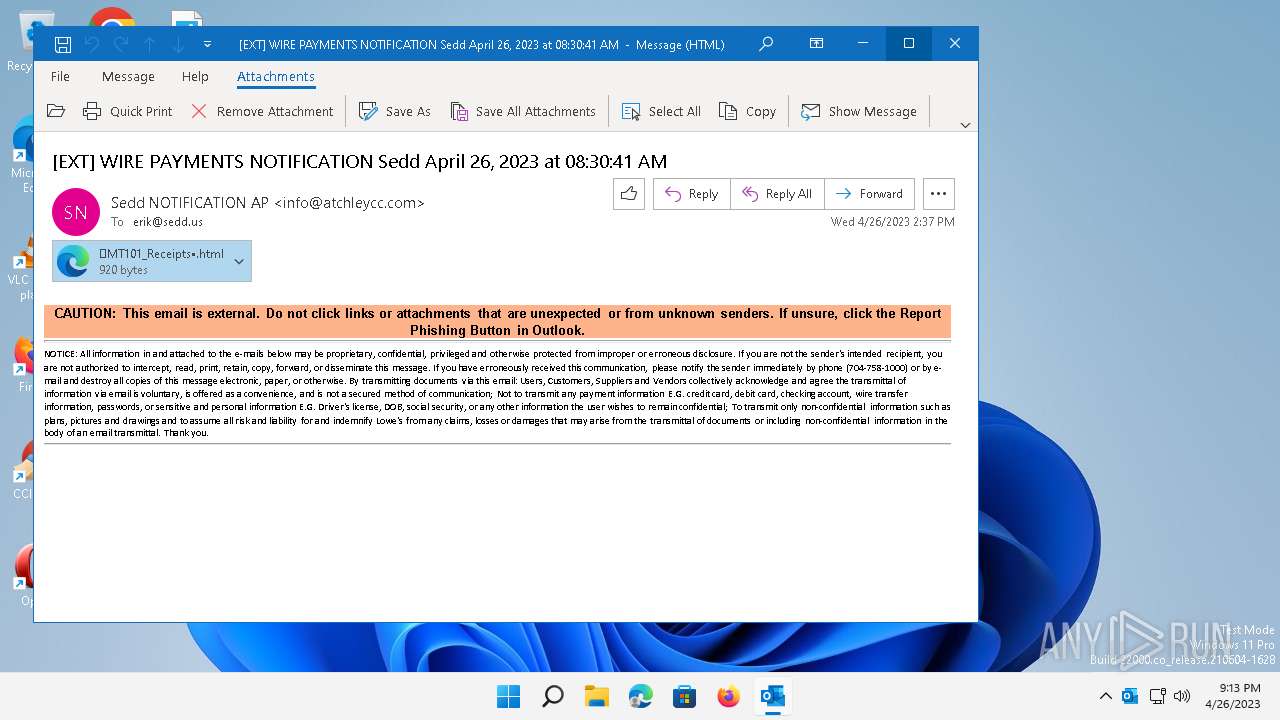
| File name: | message - 2023-04-27T060613.211.eml |
| Full analysis: | https://app.any.run/tasks/1e96312d-2fdc-4941-be92-88dadfb3abf6 |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2023, 04:13:26 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 4F2C0B802A8FA2D880B1127D88A9644D |
| SHA1: | 77F94A1513CF487A13B0BB57A80328BD580D1AD8 |
| SHA256: | F608B4215E47CF239A125F9CB7C832011F9B91C05C2178E0C78BB50F4A11F003 |
| SSDEEP: | 384:xZ9i8okJ1DdjvHELM7VXNxCdUe23xrNocWNk89vjc6g7/Q5i4BNom:xZ9i8XJRZvHELM7Vdg6bIz9vjDCoi4TF |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- elevation_service.exe (PID: 8028)
INFO
Reads the computer name
- elevation_service.exe (PID: 8028)
Checks supported languages
- elevation_service.exe (PID: 8028)
The process checks LSA protection
- elevation_service.exe (PID: 8028)
Reads product name
- OUTLOOK.EXE (PID: 2320)
The process uses the downloaded file
- chrome.exe (PID: 7872)
- chrome.exe (PID: 7572)
- chrome.exe (PID: 6972)
- chrome.exe (PID: 6348)
- chrome.exe (PID: 7496)
- OUTLOOK.EXE (PID: 2320)
Manual execution by a user
- chrome.exe (PID: 1760)
Application launched itself
- chrome.exe (PID: 1760)
Create files in a temporary directory
- chrome.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
167
Monitored processes
33
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1760 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | explorer.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\message - 2023-04-27T060613.211.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.15601.20142 Modules
| |||||||||||||||
| 3276 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2372 --field-trial-handle=1832,i,3933020361088949081,2753698671261493075,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 3372 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2116 --field-trial-handle=1832,i,3933020361088949081,2753698671261493075,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 3476 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5556 --field-trial-handle=1832,i,3933020361088949081,2753698671261493075,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 4304 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.22000.1 --gpu-preferences=UAAAAAAAAADoAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAACQAAAAAAAAAAAAAAAAAAAAAAAAABgAAAAAAAAAGAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=4872 --field-trial-handle=1832,i,3933020361088949081,2753698671261493075,131072 /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 4988 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4860 --field-trial-handle=1832,i,3933020361088949081,2753698671261493075,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 5384 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2212 --field-trial-handle=1832,i,3933020361088949081,2753698671261493075,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 5424 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=112.0.5615.50 --initial-client-data=0x110,0x114,0x118,0xec,0x11c,0x7ff8d5e3aa60,0x7ff8d5e3aa70,0x7ff8d5e3aa80 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 5540 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAABgAAAAAAAAAGAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1828 --field-trial-handle=1832,i,3933020361088949081,2753698671261493075,131072 /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
Total events
29 838
Read events
28 958
Write events
480
Delete events
400
Modification events
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01A012000000001000AE4EF13C07000000000000000700000000000000 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 1 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 1 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 1 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 1 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 1 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 1 | |||
Executable files
0
Suspicious files
388
Text files
178
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - No Account.pst | — | |
MD5:— | SHA256:— | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:1A10DE3CDEF94261F42AB289C2EF2DA3 | SHA256:BCFA38866F624F44224F46303D504272DEB14489FFC325B8FB003B5D8864B152 | |||
| 1760 | chrome.exe | C:\USERS\ADMIN\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\LAST VERSION | text | |
MD5:6938856FB4E39ADCAA9D9664D679E7E3 | SHA256:9FC3A390773A9E5326F7731EF4D54D80400FB7C36BAA62CA81AC2CA8141EDBD3 | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2320 | OUTLOOK.EXE | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\TOKENBROKER\CACHE\5475CB191E478C39370A215B2DA98A37E9DC813D.TBRES | binary | |
MD5:AC15EF1BEEF7D0B910A224BDC3F937A1 | SHA256:3264A4E2D3320E8F61C92F3A95340BD9DAB15CC7EF45ADA2A24716E811EB9427 | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\4D0A6173-CB38-44CE-B1DE-8489CF3FAEF7 | xml | |
MD5:FD0AB7FE3880B8A23559D8791AE5D17B | SHA256:BE5CF6C01B628D479CE26757D263F11A9071E24BED9B8CB74B98027018C99B43 | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\D975EFB7.tmp | binary | |
MD5:4002FC2D0835DA723339A6A7DA21CF12 | SHA256:A9187F7BA7772D8152F444CF35264E5932D2C2A6945E5FD91B9028263070930D | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:0513000B574471B8B928607A1BEC0877 | SHA256:CE0A566E3F0F9498B3D935D181E6B5F452B8E28D56DABE3C746288280737E6C2 | |||
| 2320 | OUTLOOK.EXE | C:\ProgramData\Microsoft\Office\Licenses\5\Perpetual\21661362613116367064193984360 | binary | |
MD5:4002FC2D0835DA723339A6A7DA21CF12 | SHA256:A9187F7BA7772D8152F444CF35264E5932D2C2A6945E5FD91B9028263070930D | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | binary | |
MD5:090E02C4E724C79E52A4F5F4A27A909D | SHA256:68FFE68D1E4BC216B6BADE91F5D431D116900C4199B2A79E2F752E7F9E8ED96D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
34
DNS requests
44
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3372 | chrome.exe | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | — | — | whitelisted |
1496 | svchost.exe | GET | 304 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7390236c44285166 | US | — | — | whitelisted |
2320 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
1496 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1480 | svchost.exe | GET | 200 | 13.107.4.52:80 | http://www.msftconnecttest.com/connecttest.txt | US | text | 22 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1496 | svchost.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1496 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2320 | OUTLOOK.EXE | 52.109.28.62:443 | odc.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | suspicious |
2320 | OUTLOOK.EXE | 13.89.178.27:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
2320 | OUTLOOK.EXE | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3372 | chrome.exe | 142.250.185.67:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3372 | chrome.exe | 142.250.185.109:443 | accounts.google.com | GOOGLE | US | suspicious |
3372 | chrome.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
3372 | chrome.exe | 142.250.186.78:443 | clients2.google.com | GOOGLE | US | whitelisted |
3372 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
ols.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1480 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |