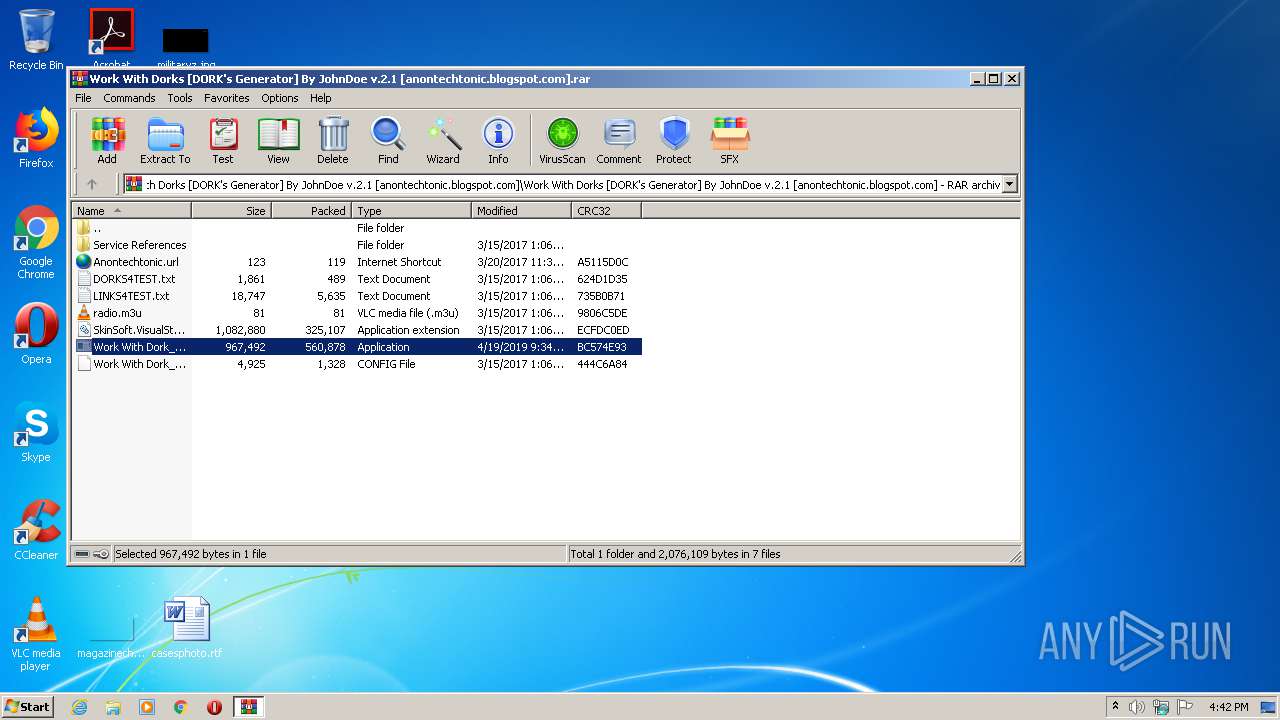
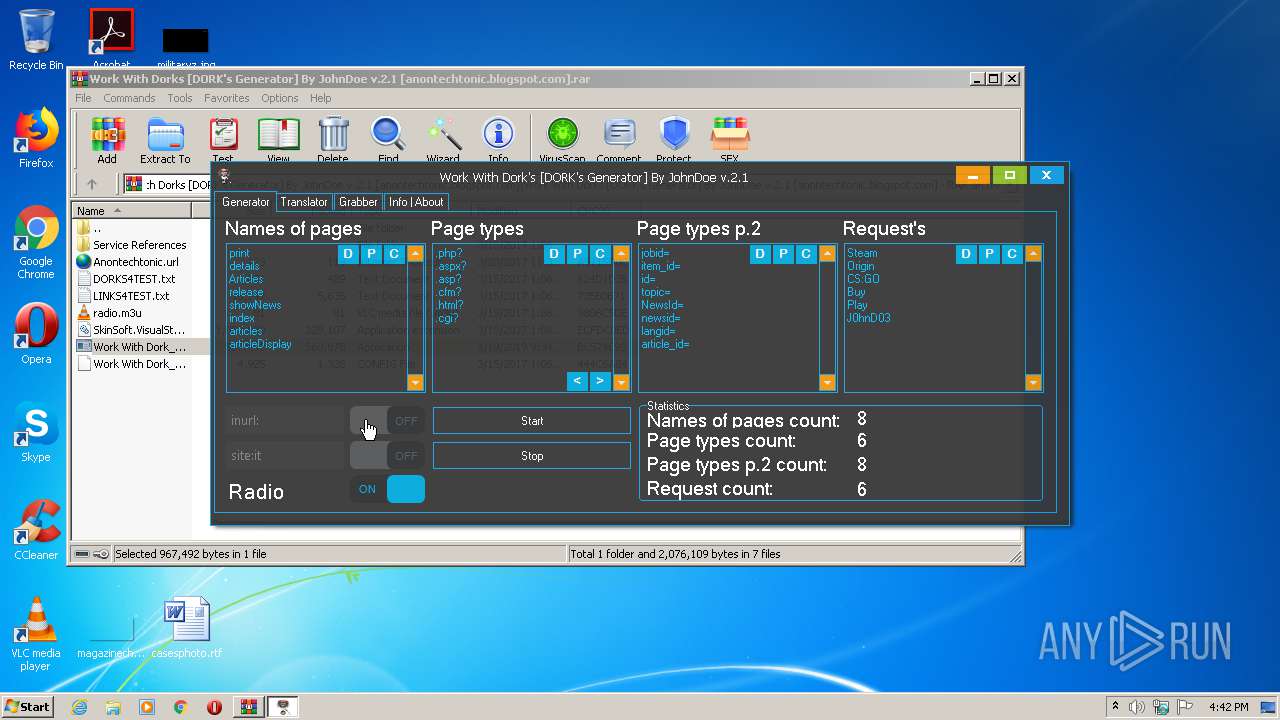
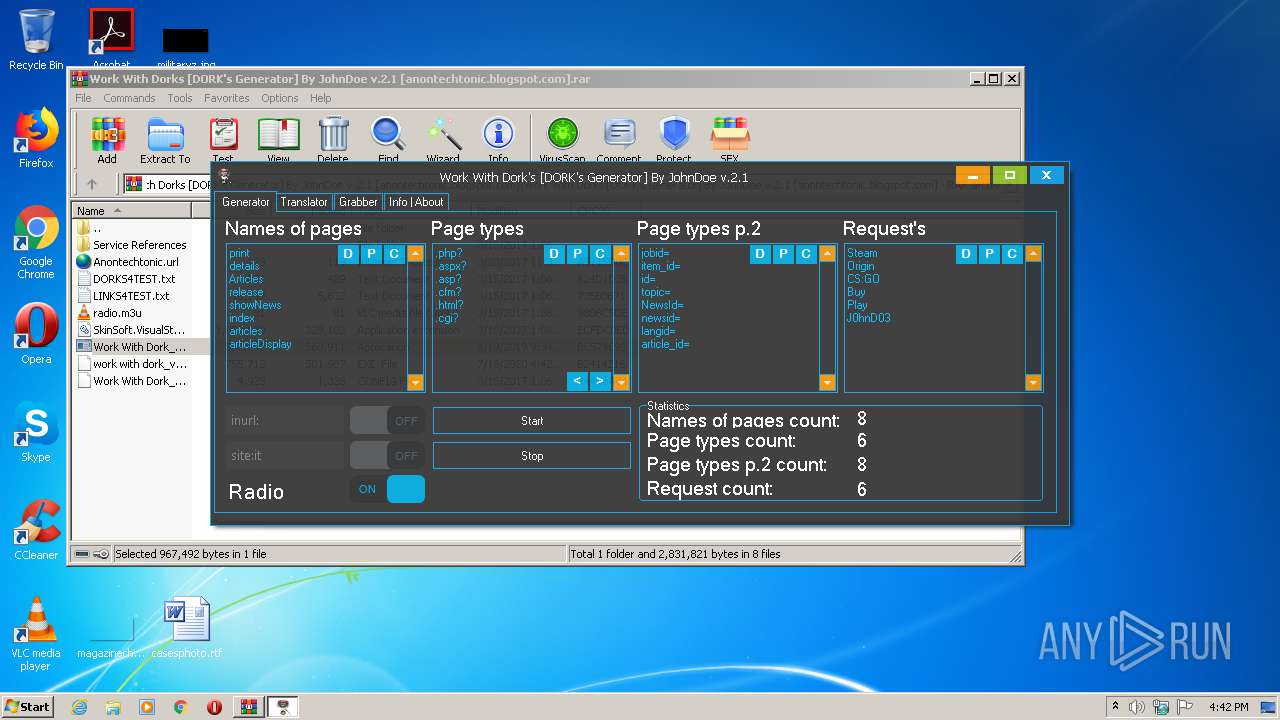
| File name: | Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com].rar |
| Full analysis: | https://app.any.run/tasks/8bac6d4e-f4ce-452a-b96f-9659287b0da3 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2020, 15:42:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 98ACB78090075D641ADA5E2BA83DA99A |
| SHA1: | 6381E89688EFBB43C666E6F09EB6CEFDE06F6F5C |
| SHA256: | F5EC241660F60A5AEA4E8A254E18A0AB334079F9DE8E549C1DCC2B65D53E458A |
| SSDEEP: | 12288:18fk93NocONArLbl18L/rrQXkQyskQQKVZuSjyuDvKx3WNIWwULs2yf+:18fk93N1O0LP8jnkPy0yu+xWNIWHMf+ |
MALICIOUS
Application was dropped or rewritten from another process
- icsys.icn.exe (PID: 3892)
- work with dork_v_2_1.exe (PID: 180)
- Work With Dork_v_2_1.exe (PID: 3812)
- work with dork_v_2_1.exe (PID: 1708)
- icsys.icn.exe (PID: 2972)
- Work With Dork_v_2_1.exe (PID: 2376)
Loads dropped or rewritten executable
- work with dork_v_2_1.exe (PID: 180)
- work with dork_v_2_1.exe (PID: 1708)
SUSPICIOUS
Starts itself from another location
- Work With Dork_v_2_1.exe (PID: 2376)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 752)
- Work With Dork_v_2_1.exe (PID: 2376)
- Work With Dork_v_2_1.exe (PID: 3812)
- work with dork_v_2_1.exe (PID: 180)
Starts application with an unusual extension
- Work With Dork_v_2_1.exe (PID: 2376)
- Work With Dork_v_2_1.exe (PID: 3812)
Reads Internet Cache Settings
- work with dork_v_2_1.exe (PID: 180)
- work with dork_v_2_1.exe (PID: 1708)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
41
Monitored processes
7
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | "c:\users\admin\appdata\local\temp\rar$exa752.28784\work with dorks [dork's generator] by johndoe v.2.1 [anontechtonic.blogspot.com]\work with dorks [dork's generator] by johndoe v.2.1 [anontechtonic.blogspot.com]\work with dork_v_2_1.exe " | c:\users\admin\appdata\local\temp\rar$exa752.28784\work with dorks [dork's generator] by johndoe v.2.1 [anontechtonic.blogspot.com]\work with dorks [dork's generator] by johndoe v.2.1 [anontechtonic.blogspot.com]\work with dork_v_2_1.exe | Work With Dork_v_2_1.exe | ||||||||||||
User: admin Company: J0hnD03 SoftWare Integrity Level: MEDIUM Description: Work With Dork_v_2_1 Exit code: 3221225547 Version: 2.1.0.0 Modules
| |||||||||||||||
| 752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com].rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1708 | "c:\users\admin\appdata\local\temp\rar$exa752.30811\work with dorks [dork's generator] by johndoe v.2.1 [anontechtonic.blogspot.com]\work with dorks [dork's generator] by johndoe v.2.1 [anontechtonic.blogspot.com]\work with dork_v_2_1.exe " | c:\users\admin\appdata\local\temp\rar$exa752.30811\work with dorks [dork's generator] by johndoe v.2.1 [anontechtonic.blogspot.com]\work with dorks [dork's generator] by johndoe v.2.1 [anontechtonic.blogspot.com]\work with dork_v_2_1.exe | Work With Dork_v_2_1.exe | ||||||||||||
User: admin Company: J0hnD03 SoftWare Integrity Level: MEDIUM Description: Work With Dork_v_2_1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 2376 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa752.28784\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dork_v_2_1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa752.28784\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dork_v_2_1.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2972 | C:\Users\admin\AppData\Local\icsys.icn.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | — | Work With Dork_v_2_1.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3812 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa752.30811\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dork_v_2_1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa752.30811\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dork_v_2_1.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3892 | C:\Users\admin\AppData\Local\icsys.icn.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | — | Work With Dork_v_2_1.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
902
Read events
824
Write events
77
Delete events
1
Modification events
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com].rar | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-10046 |
Value: Internet Shortcut | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
10
Suspicious files
6
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa752.28784\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Service References\TranslatorService\configuration.svcinfo | — | |
MD5:— | SHA256:— | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa752.28784\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Service References\TranslatorService\configuration91.svcinfo | — | |
MD5:— | SHA256:— | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa752.28784\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Service References\TranslatorService\Reference.svcmap | — | |
MD5:— | SHA256:— | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa752.28784\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Service References\TranslatorService\Reference.vb | — | |
MD5:— | SHA256:— | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa752.28784\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Service References\TranslatorService\SoapService.wsdl | — | |
MD5:— | SHA256:— | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa752.28784\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Work With Dorks [DORK's Generator] By JohnDoe v.2.1 [anontechtonic.blogspot.com]\Service References\TranslatorService\SoapService1.wsdl | — | |
MD5:— | SHA256:— | |||
| 2376 | Work With Dork_v_2_1.exe | C:\Users\admin\AppData\Local\Temp\~DF1DF452769A6FFC5C.TMP | — | |
MD5:— | SHA256:— | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rar_752.29245 | — | |
MD5:— | SHA256:— | |||
| 3892 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DF33C53941E9B436C2.TMP | — | |
MD5:— | SHA256:— | |||
| 180 | work with dork_v_2_1.exe | C:\Users\admin\AppData\Local\J0hnD03_SoftWare\work_with_dork_v_2_1.exe _Url_v1jjephybn5lmgxi0awh43gycntyclcg\2.1.0.0\0nulmbsr.newcfg | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
6
DNS requests
1
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
180 | work with dork_v_2_1.exe | GET | — | 163.172.84.49:80 | http://play.newtone.fm/live_01 | FR | — | — | unknown |
180 | work with dork_v_2_1.exe | GET | — | 163.172.84.49:80 | http://play.newtone.fm/live_01 | FR | — | — | unknown |
1708 | work with dork_v_2_1.exe | GET | — | 163.172.84.49:80 | http://play.newtone.fm/live_01 | FR | — | — | unknown |
1708 | work with dork_v_2_1.exe | GET | — | 163.172.84.49:80 | http://play.newtone.fm/live_01 | FR | — | — | unknown |
1708 | work with dork_v_2_1.exe | GET | — | 163.172.84.49:80 | http://play.newtone.fm/live_01 | FR | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
180 | work with dork_v_2_1.exe | 163.172.84.49:80 | play.newtone.fm | Online S.a.s. | FR | unknown |
1708 | work with dork_v_2_1.exe | 163.172.84.49:80 | play.newtone.fm | Online S.a.s. | FR | unknown |
— | — | 163.172.84.49:80 | play.newtone.fm | Online S.a.s. | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
play.newtone.fm |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
180 | work with dork_v_2_1.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
1708 | work with dork_v_2_1.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |