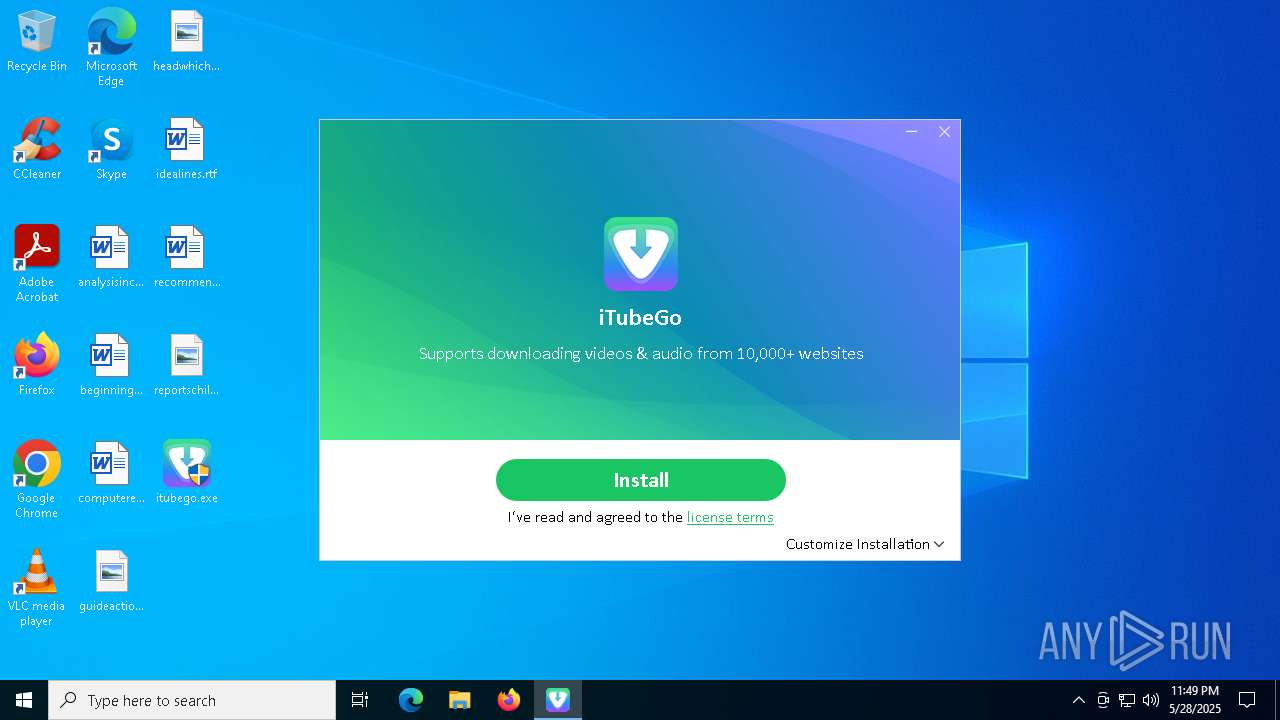
| File name: | itubego.exe |
| Full analysis: | https://app.any.run/tasks/e39d8d82-820f-4773-9329-1ada1e637318 |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2025, 23:49:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | E3AC7FCA8B3A801AF158CE08B3EB2161 |
| SHA1: | E3459E6BA40C431B164F9FE42DCDD0059CE9628C |
| SHA256: | F5E9CCEEEC50CBDE2E648EE6BEA98F0496901A00750C3E1366195EAED3A32699 |
| SSDEEP: | 98304:f/G/ZBf6s7c9PFad+pw7zsECD7goRpl9tfYa+pk2OE0Ab663Ox79MXdFu55nlzzU:xGke5wT0Q6 |
MALICIOUS
Changes Windows Defender settings
- itubego.exe (PID: 3268)
Adds path to the Windows Defender exclusion list
- itubego.exe (PID: 3268)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- itubego.exe (PID: 3268)
Script adds exclusion path to Windows Defender
- itubego.exe (PID: 3268)
INFO
Reads the machine GUID from the registry
- itubego.exe (PID: 3268)
Creates files in the program directory
- itubego.exe (PID: 3268)
The sample compiled with chinese language support
- itubego.exe (PID: 3268)
Checks supported languages
- itubego.exe (PID: 3268)
Create files in a temporary directory
- itubego.exe (PID: 3268)
Reads the computer name
- itubego.exe (PID: 3268)
Checks proxy server information
- itubego.exe (PID: 3268)
- BackgroundTransferHost.exe (PID: 8056)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7152)
- powershell.exe (PID: 5428)
- powershell.exe (PID: 5216)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5216)
- powershell.exe (PID: 7152)
- powershell.exe (PID: 5428)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 8056)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 4172)
- BackgroundTransferHost.exe (PID: 6656)
- BackgroundTransferHost.exe (PID: 8056)
- BackgroundTransferHost.exe (PID: 7844)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 8056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:16 02:04:22+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 2240000 |
| InitializedDataSize: | 1054720 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ded53 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 25.3.25.1 |
| ProductVersionNumber: | 5.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileDescription: | iTubeGo |
| FileVersion: | 25.3.25.1 |
| LegalCopyright: | Copyright (c) 2025 iTubeGo Studio. All rights reserved. |
| ProductName: | iTubeGo |
| ProductVersion: | 5.2.0.0 |
Total processes
152
Monitored processes
15
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1276 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\Desktop\itubego.exe" | C:\Users\admin\Desktop\itubego.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: iTubeGo Version: 25.3.25.1 Modules
| |||||||||||||||
| 4172 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5216 | powershell.exe -Command Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Roaming\WvEdgeBrowser' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | itubego.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5248 | "C:\Users\admin\Desktop\itubego.exe" | C:\Users\admin\Desktop\itubego.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: iTubeGo Exit code: 3221226540 Version: 25.3.25.1 Modules
| |||||||||||||||
| 5428 | powershell.exe -Command Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Local\Temp\\tmp123_downloader' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | itubego.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6656 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 961
Read events
24 944
Write events
17
Delete events
0
Modification events
| (PID) Process: | (7844) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7844) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7844) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8056) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8056) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8056) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4172) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4172) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4172) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6656) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
5
Text files
55
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\config.ini | text | |
MD5:E676AE41D9657FDFEE475F7D5C669CC8 | SHA256:D89C5C63BA586A8B0DAE4DA8A1264D64DE9696A9DF67EF329D93BA592C97333C | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\language\de.ini | text | |
MD5:2E0F07585F0ECB04D295248849E8B8DD | SHA256:0A2C63C116A18DC24B6967C3C6E508163A836996A684E2D09E8E10C8D9EBE926 | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\app.ico | image | |
MD5:B3B3AB6DE17BB09A57EDAA05E7E55301 | SHA256:A06671799875CA56B7BD186FAC0655AD51FBFB2860ADF3F2E92CC228A399F2A4 | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\language\en.ini | text | |
MD5:761DCB59FD2BDC0796911ED7E995D4D4 | SHA256:F5E520096EC75AA7017C9B2753C64EB7BF27D6B3CE3AE841C811DB5BFB966516 | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\language\hi.ini | text | |
MD5:5DCCA38D140728158C75AB05BE09AAAE | SHA256:421257032BC752FFC3A8E720E0F73C1422C422EC2905F0F6C6EE021FD58C8C93 | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\language\es.ini | text | |
MD5:66D8BBC0FBA6281109ED4568C9B1AEE7 | SHA256:93CDA998D6CED85788D0274C17787D261A428D71555594367DA9AAE97EFCF0ED | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\language\fr.ini | text | |
MD5:C411B773802DBB3CA3EDF2CC0B5E04FD | SHA256:EDC686FDB599E190EFF6E0DA49195AB8E42FD7A83B5865F0F78B61B4495C9E70 | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\language\it.ini | text | |
MD5:9564AC6854CE94449A653C980E7CB8DF | SHA256:51D924CE54B9708E2D54A414541ACB24CFF2EB46511C7B250EE1597C05EED4CC | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\language\pt.ini | text | |
MD5:0B6440DD0E975F026D3C87716A26EB02 | SHA256:D95861F2FE8EE5FB2BC970150305DC91DE56C94D96B037C932B0BD334D5B013D | |||
| 3268 | itubego.exe | C:\Users\admin\AppData\Local\Temp\tmp123_downloader\Cache\10bcba\language\ko.ini | text | |
MD5:28E843EBF0E252632F8230491ADA90D8 | SHA256:C0A807891343CF2B6EC68C8CA4E6B78938BA16A2562E6CDBC79872D935A527F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
61
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.186.142:443 | https://www.google-analytics.com/g/collect?v=2&sct=1&seg=1&tid=G-V9BVQVS970&cid=989857505410153.524510151999745&sid=1748476173&en=Product_iTubeGo&ep.action=DownloaderVersion_iTubeGo&ep.label=5.2.0.0_iTubeGo | unknown | — | — | unknown |
— | — | GET | 200 | 172.67.72.188:443 | https://download.itubego.com/updateinfo/itubego_update_win.json | unknown | binary | 988 b | unknown |
— | — | GET | 204 | 142.250.186.142:443 | https://www.google-analytics.com/g/collect?v=2&sct=1&seg=1&tid=G-V9BVQVS970&cid=989857505410153.524510151999745&sid=1748476173&en=Progress_iTubeGo&ep.action=DownloaderStart_iTubeGo | unknown | — | — | unknown |
— | — | GET | 204 | 142.250.186.142:443 | https://www.google-analytics.com/g/collect?v=2&sct=1&seg=1&tid=G-V9BVQVS970&cid=989857505410153.524510151999745&sid=1748476173&en=Progress_iTubeGo&ep.action=ClickInstall_iTubeGo | unknown | — | — | unknown |
— | — | POST | 200 | 20.190.159.2:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | GET | — | 104.26.12.246:443 | https://download.itubego.com/itubego/win/itubego_v10.3.1_x64.exe | unknown | — | — | unknown |
— | — | POST | 200 | 20.190.159.2:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.23:443 | https://login.live.com/RST2.srf | unknown | xml | 11.3 Kb | whitelisted |
— | — | GET | 200 | 20.199.58.43:443 | https://arc.msn.com/v3/Delivery/Placement?pubid=da63df93-3dbc-42ae-a505-b34988683ac7&pid=310091&adm=2&w=1&h=1&wpx=1&hpx=1&fmt=json&cltp=app&dim=le&rafb=0&nct=1&pm=1&cfmt=text,image,poly&sft=jpeg,png,gif&topt=1&poptin=0&localid=w:AC7699B0-48EA-FD22-C8DC-06A02098A0F0&ctry=US&time=20250528T235017Z&lc=en-US&pl=en-US&idtp=mid&uid=9115d6d1-9f4e-4053-9297-2a8c833b3912&aid=00000000-0000-0000-0000-000000000000&ua=WindowsShellClient%2F9.0.40929.0%20%28Windows%29&asid=c48ab789efc74d5e940eee6e01ef872b&ctmode=MultiSession&arch=x64&betaedgever=0.0.0.0&canedgever=0.0.0.0&cdm=1&cdmver=10.0.19041.3636&devedgever=0.0.0.0&devfam=Windows.Desktop&devform=Unknown&devosver=10.0.19045.4046&disphorzres=1280&dispsize=15.3&dispvertres=720&fosver=16299&isu=0&lo=4061749&metered=false&nettype=ethernet&npid=sc-310091&oemName=DELL&oemid=DELL&ossku=Professional&prevosver=15063&rver=2&smBiosDm=DELL&stabedgever=122.0.2365.59&tl=2&tsu=1452279&waasBldFlt=1&waasCfgExp=1&waasCfgSet=1&waasRetail=1&waasRing=&svoffered=2 | unknown | binary | 4.37 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.129:443 | https://login.live.com/RST2.srf | unknown | xml | 11.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5796 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
864 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
864 | RUXIMICS.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5796 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
864 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
download.itubego.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |