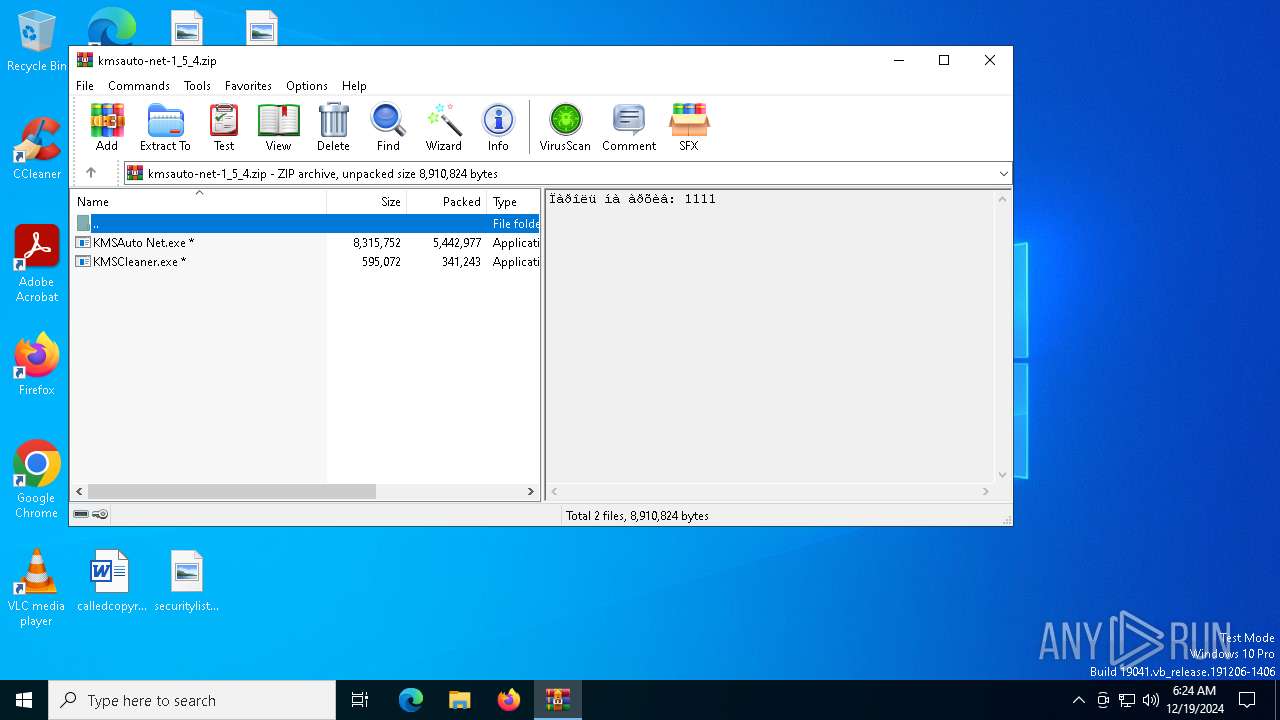
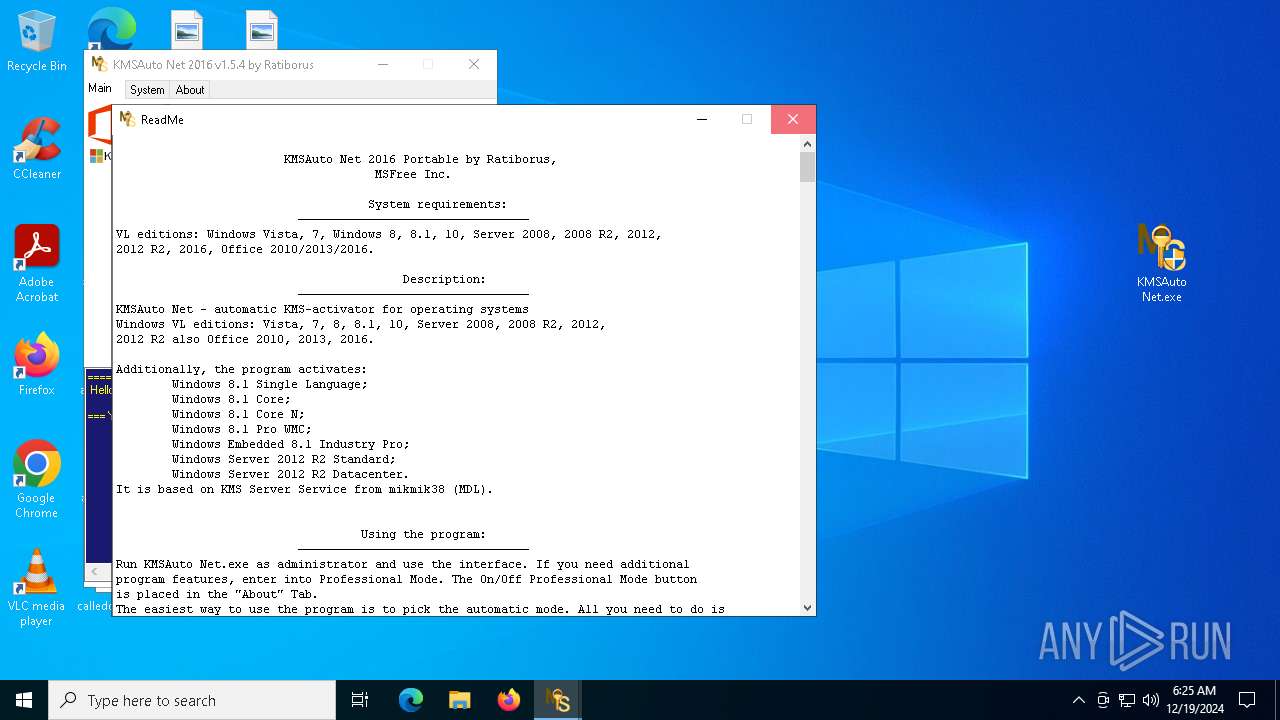
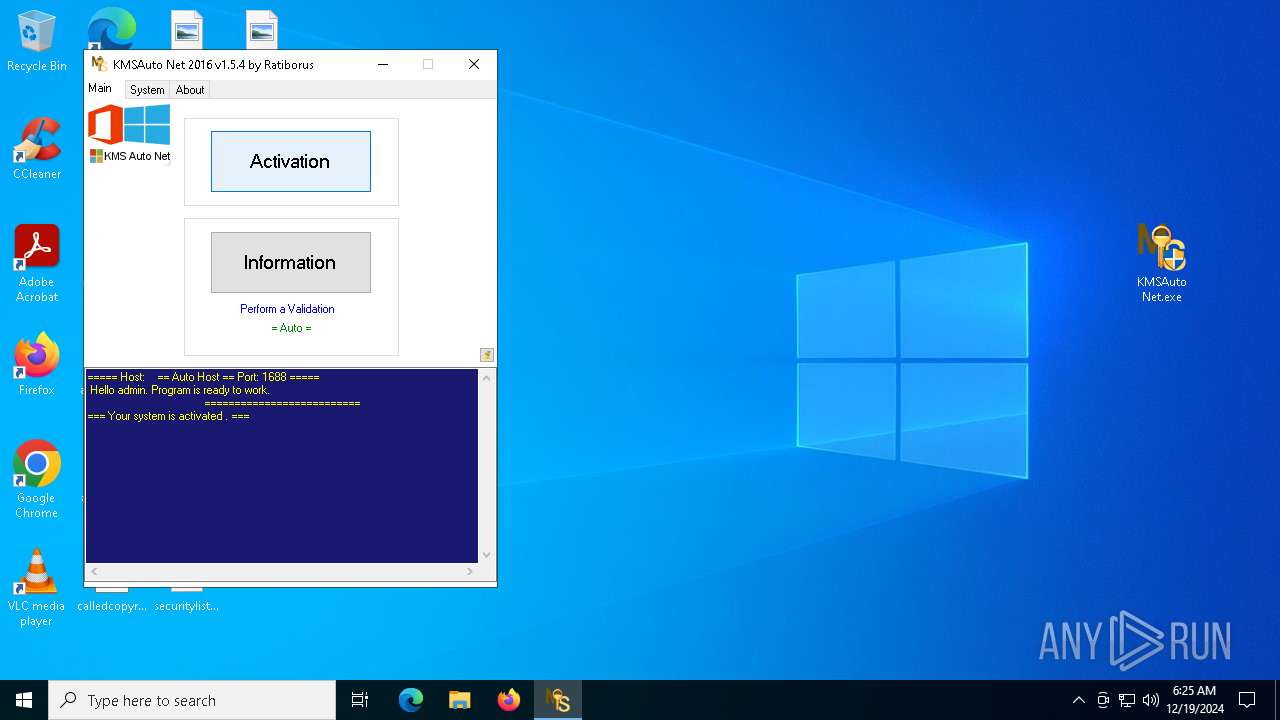
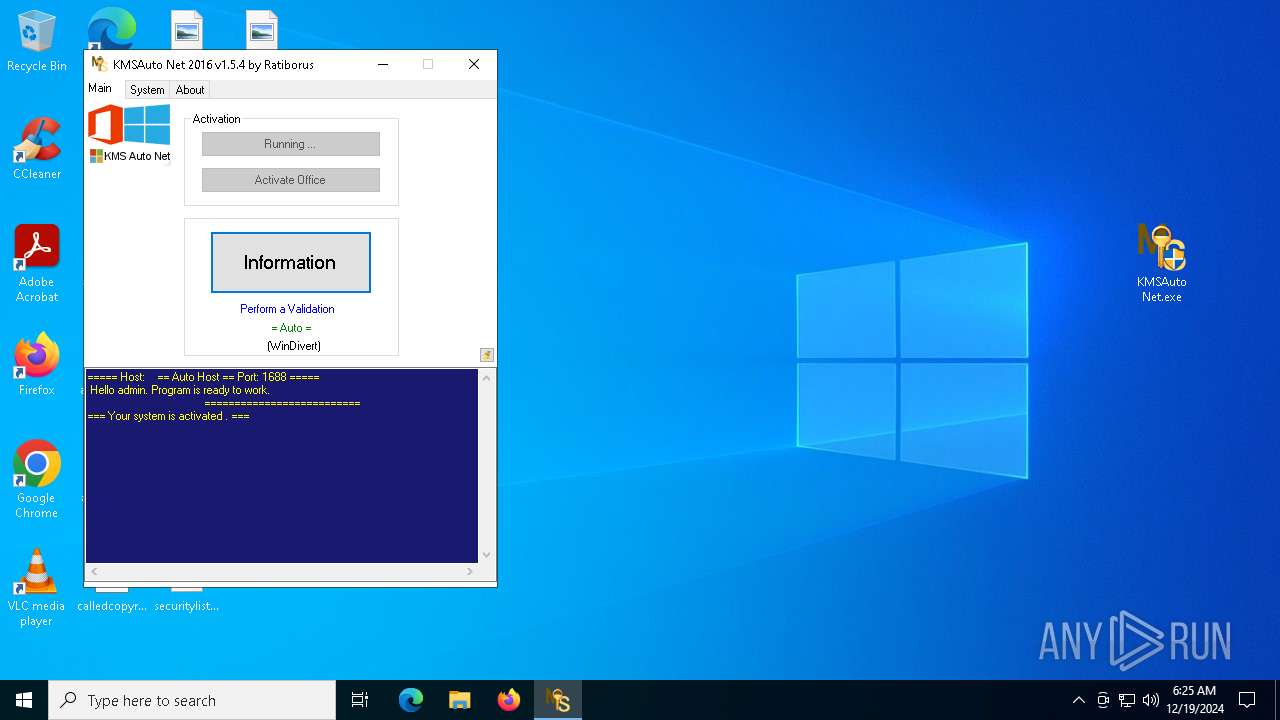
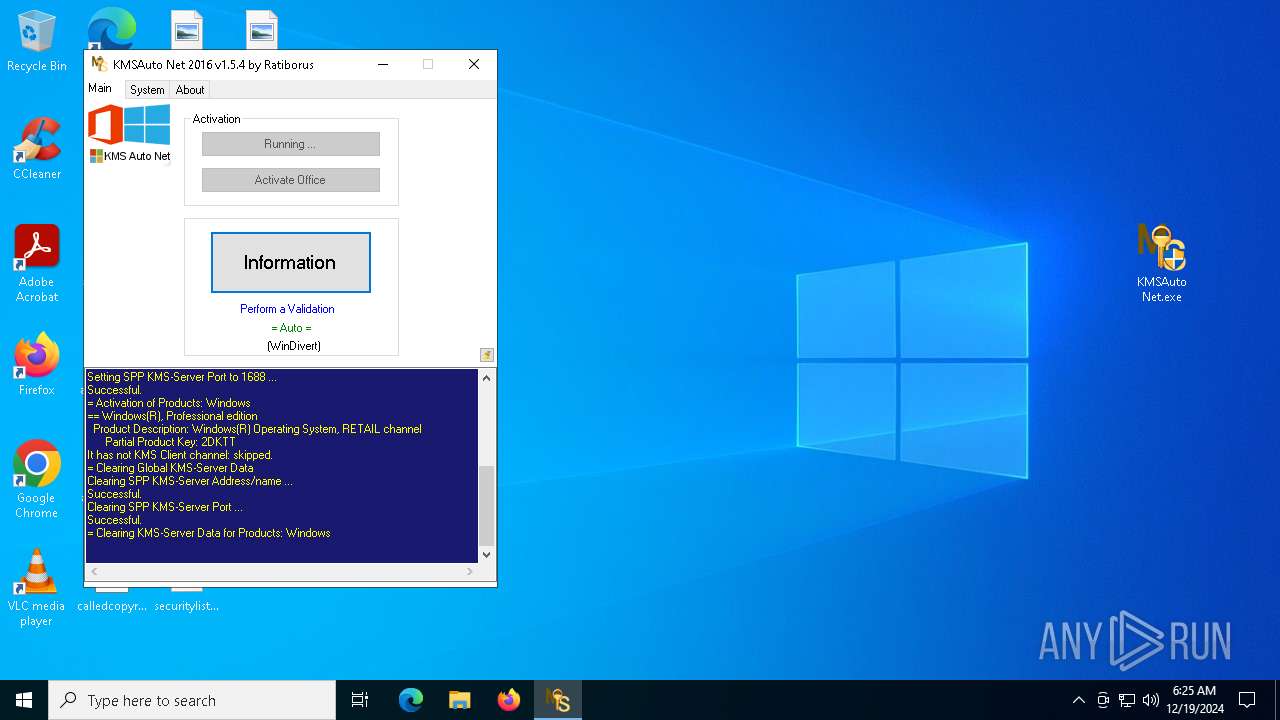
| File name: | kmsauto-net-1_5_4.zip |
| Full analysis: | https://app.any.run/tasks/de1da4b8-c3b1-4222-beb4-c61cd08e7453 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2024, 06:24:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
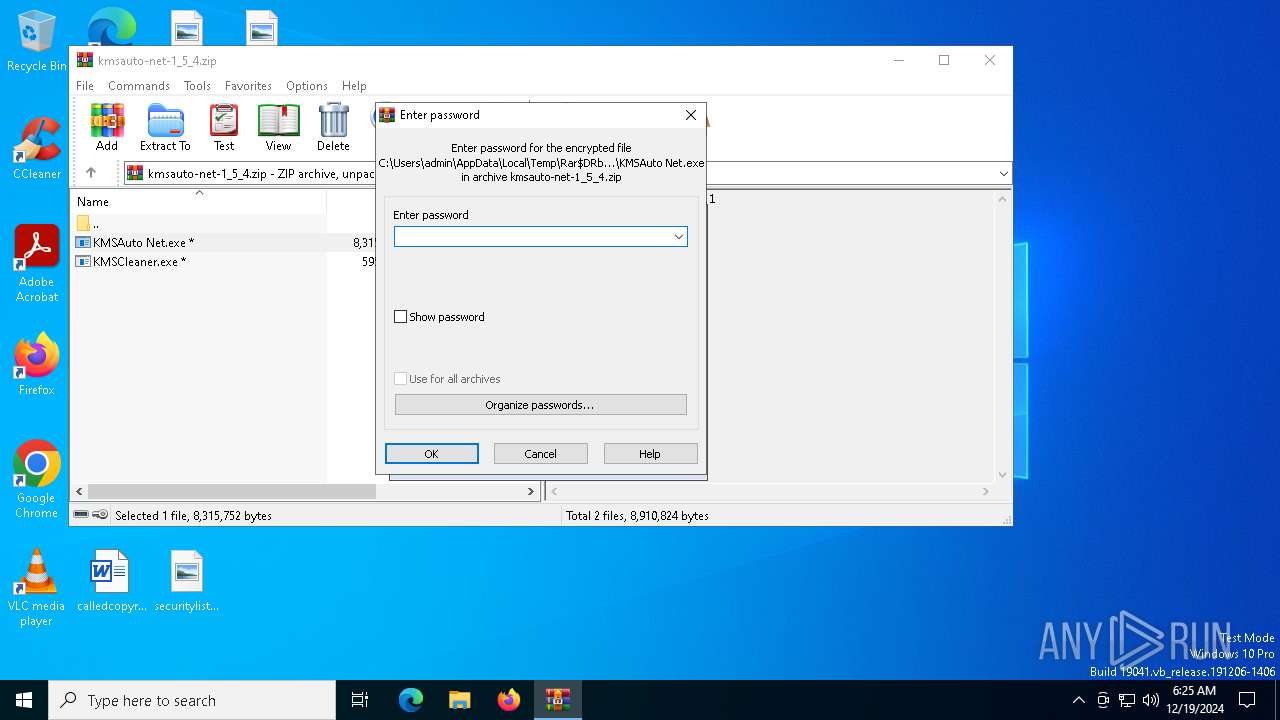
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 77B1A945EBA1451B24D08A1D3B99E08C |
| SHA1: | D20F524A697408607652377EF6568CCBE95E17E9 |
| SHA256: | F5C4883CD596C64288B1581F6B59999CD123A6C180B89E8388063A973FFDD7B6 |
| SSDEEP: | 98304:/iDT1ubpC9gd1vqNp8CBxpxmjre32BwpwMbwuM8UVsdpf9MBp8Pr3KPrlhf+/6Si:2xdYRo34 |
MALICIOUS
Executing a file with an untrusted certificate
- KMSAuto Net.exe (PID: 7024)
- KMSAuto Net.exe (PID: 7076)
- FakeClient.exe (PID: 5916)
SUSPICIOUS
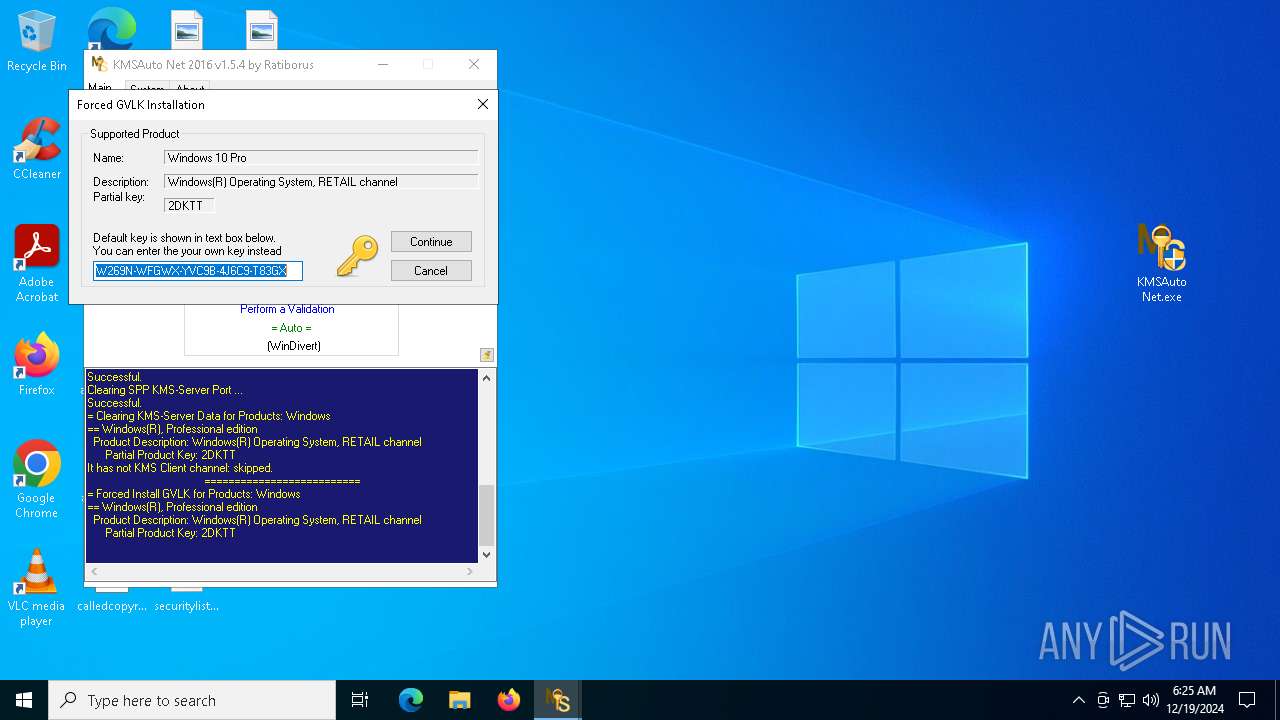
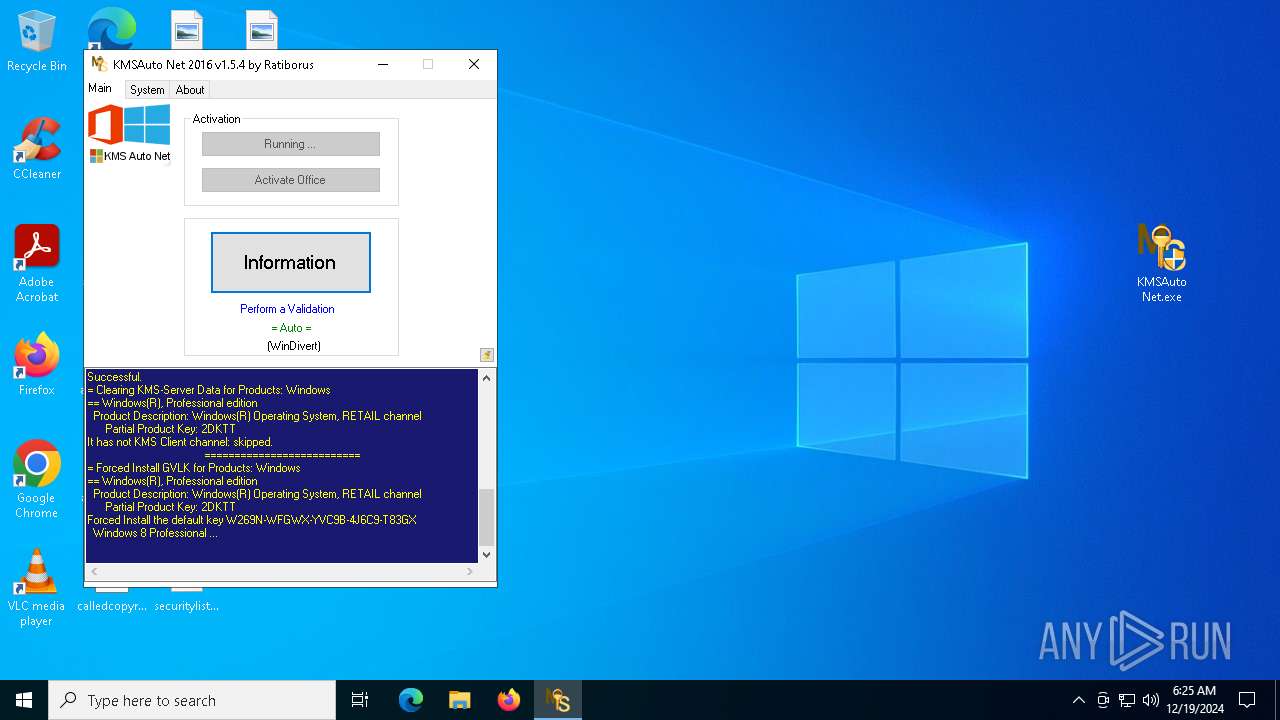
KMS tool has been detected
- KMSAuto Net.exe (PID: 7024)
- KMSAuto Net.exe (PID: 7076)
- KMSAuto Net.exe (PID: 7076)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 7076)
- cmd.exe (PID: 2800)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 7076)
Starts application with an unusual extension
- cmd.exe (PID: 3144)
- cmd.exe (PID: 6780)
- cmd.exe (PID: 3296)
- cmd.exe (PID: 6196)
Executable content was dropped or overwritten
- wzt.dat (PID: 6184)
- bin.dat (PID: 7000)
- AESDecoder.exe (PID: 5400)
- KMSAuto Net.exe (PID: 7076)
- bin_x64.dat (PID: 4536)
- bin_x64.dat (PID: 6424)
Adds/modifies Windows certificates
- certmgr.exe (PID: 6440)
- certmgr.exe (PID: 3836)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 7076)
Process drops legitimate windows executable
- wzt.dat (PID: 6184)
- bin_x64.dat (PID: 4536)
- bin_x64.dat (PID: 6424)
Drops a system driver (possible attempt to evade defenses)
- bin_x64.dat (PID: 4536)
- bin_x64.dat (PID: 6424)
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 7076)
Application launched itself
- cmd.exe (PID: 2800)
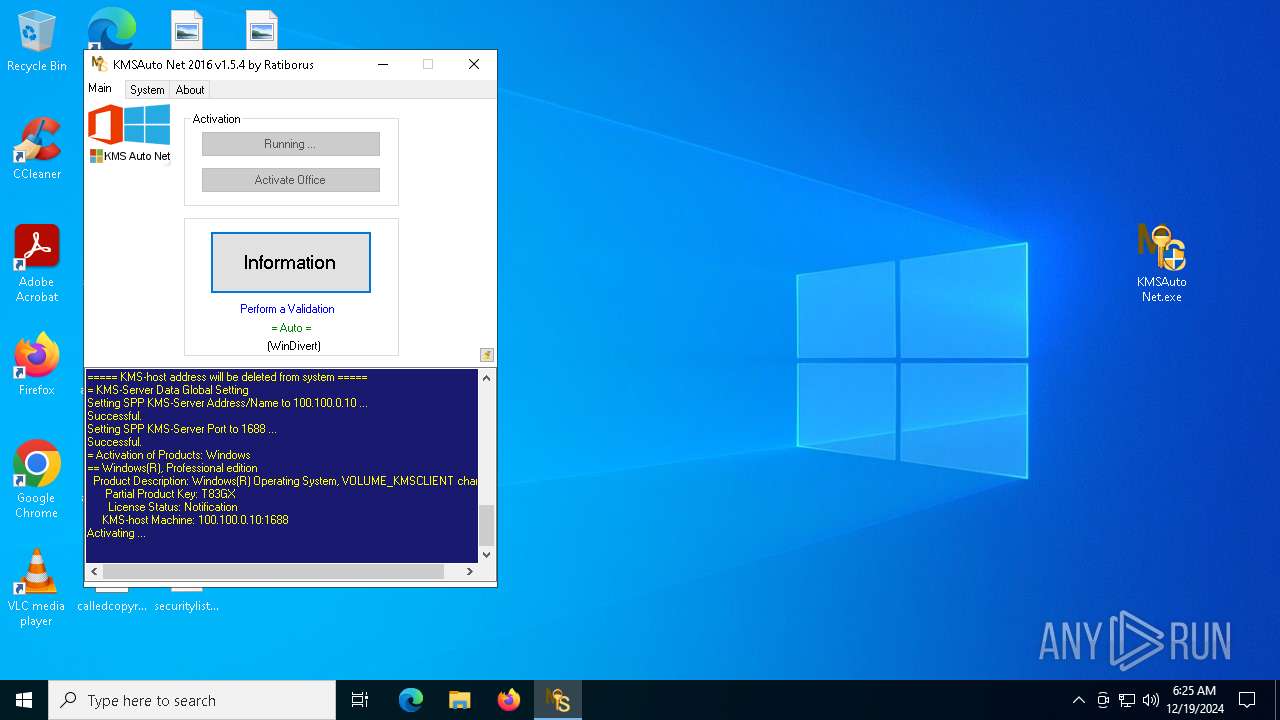
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 7076)
Executes as Windows Service
- KMSSS.exe (PID: 6556)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 6536)
Uses REG/REGEDIT.EXE to modify registry
- KMSAuto Net.exe (PID: 7076)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 7076)
INFO
Checks supported languages
- KMSAuto Net.exe (PID: 7076)
- wzt.dat (PID: 6184)
- certmgr.exe (PID: 3836)
- certmgr.exe (PID: 6440)
- bin.dat (PID: 7000)
- AESDecoder.exe (PID: 5400)
- bin_x64.dat (PID: 4536)
- bin_x64.dat (PID: 6424)
Reads the computer name
- KMSAuto Net.exe (PID: 7076)
Creates a new folder
- cmd.exe (PID: 7156)
- cmd.exe (PID: 2512)
Reads the machine GUID from the registry
- KMSAuto Net.exe (PID: 7076)
The process uses the downloaded file
- WinRAR.exe (PID: 6584)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6584)
Manual execution by a user
- KMSAuto Net.exe (PID: 7076)
- KMSAuto Net.exe (PID: 7024)
Reads Environment values
- KMSAuto Net.exe (PID: 7076)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 7076)
Reads product name
- KMSAuto Net.exe (PID: 7076)
The sample compiled with english language support
- KMSAuto Net.exe (PID: 7076)
- wzt.dat (PID: 6184)
- bin_x64.dat (PID: 4536)
- bin_x64.dat (PID: 6424)
UPX packer has been detected
- KMSAuto Net.exe (PID: 7076)
Creates files in the program directory
- KMSAuto Net.exe (PID: 7076)
- bin.dat (PID: 7000)
- wzt.dat (PID: 6184)
- bin_x64.dat (PID: 4536)
- KMSSS.exe (PID: 6556)
- bin_x64.dat (PID: 6424)
Adds a route via ROUTE.EXE
- ROUTE.EXE (PID: 68)
Sends debugging messages
- FakeClient.exe (PID: 5916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2018:10:15 09:59:34 |
| ZipCRC: | 0x0da1fbfe |
| ZipCompressedSize: | 5442977 |
| ZipUncompressedSize: | 8315752 |
| ZipFileName: | KMSAuto Net.exe |
Total processes
208
Monitored processes
79
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | route -p add 100.100.0.10 0.0.0.0 IF 1 | C:\Windows\System32\ROUTE.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Route Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | C:\WINDOWS\Sysnative\cmd.exe /D /c del /F /Q "test.test" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | svchost.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | C:\WINDOWS\Sysnative\Netsh Advfirewall Firewall delete rule name="0pen Port KMS" protocol=TCP | C:\Windows\System32\netsh.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\WINDOWS\Sysnative\cmd.exe" /c rd "C:\ProgramData\KMSAuto\wzt" /S /Q | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 253
Read events
6 223
Write events
28
Delete events
2
Modification events
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\kmsauto-net-1_5_4.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
26
Suspicious files
11
Text files
6
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7076 | KMSAuto Net.exe | C:\Users\admin\AppData\Local\MSfree Inc\kmsauto.ini | text | |
MD5:AF6A20FD7DFADCD582CCF2B1BFAAF82B | SHA256:0BEE97833A70AA9BA271E93226DACE849836C64919FBFE15543D694E219D4AF2 | |||
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6584.32268\KMSAuto Net.exe | executable | |
MD5:F1FE671BCEFD4630E5ED8B87C9283534 | SHA256:58D6FEC4BA24C32D38C9A0C7C39DF3CB0E91F500B323E841121D703C7B718681 | |||
| 6184 | wzt.dat | C:\ProgramData\KMSAuto\wzt\certmgr.exe | executable | |
MD5:9D4F1124B2D870583268D19317D564AE | SHA256:EBAD2237B3E7CDF65385CCCE5099E82C7EC5080E737C97CE4E542CDBEA8D418D | |||
| 3288 | cmd.exe | C:\Users\admin\Desktop\test.test | text | |
MD5:9F06243ABCB89C70E0C331C61D871FA7 | SHA256:837CCB607E312B170FAC7383D7CCFD61FA5072793F19A25E75FBACB56539B86B | |||
| 6184 | wzt.dat | C:\ProgramData\KMSAuto\wzt\wzteam.cer | binary | |
MD5:76B56D90E6F1DA030A8B85E64579F25A | SHA256:FD2D7DF0220DD65EE23D0090299DFCC356F6F8F7167BAE9ADF7D08CEFAF39D02 | |||
| 7076 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\bin.dat | executable | |
MD5:4D2E5AFFE6D1CCB42F6650FD57448A9B | SHA256:3CBF7C0231B3266B4A6946DCF9AAA39C2BF077F6E459CA9EAD39C516CBFCE74C | |||
| 7000 | bin.dat | C:\ProgramData\KMSAuto\bin\KMSSS.exe.aes | binary | |
MD5:41E0D8AB5104DA2068739109EC3599F4 | SHA256:38D1DBDC7C7A64253E6D4B52225B0BFD7716405C731A107F0C6BA9573A73A77F | |||
| 7076 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\wzt.dat | executable | |
MD5:822DA2319294F2B768BFE9ED4EEBAC15 | SHA256:17B74D4EA905FAC0BA6857F78F47EE1E940675AF1BC27DED69FE2941318106EF | |||
| 4536 | bin_x64.dat | C:\ProgramData\KMSAuto\bin\driver\x64TAP1\OemVista.inf | binary | |
MD5:87868193626DC756D10885F46D76F42E | SHA256:B5728E42EA12C67577CB9188B472005EE74399B6AC976E7F72B48409BAEE3B41 | |||
| 4536 | bin_x64.dat | C:\ProgramData\KMSAuto\bin\driver\x64TAP2\tapoas.inf | binary | |
MD5:61243CB103543EE3163BF16DF69BCB54 | SHA256:1652B1DE2F15EEACBD06E0AB14ADA5A466316FFD3AB88D4A2A46CFCBD25FDFA1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
34
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6264 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6084 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6084 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6264 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1520 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.183:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
FakeClient.exe | WdfCoInstaller: [12/19/2024 06:25.35.149] ReadComponents: WdfSection for Driver Service windivert using KMDF lib version Major 0x1, minor 0x9
|
FakeClient.exe | WdfCoInstaller: [12/19/2024 06:25.35.164] BootApplication: GetStartType error error(87) The parameter is incorrect.
Driver Service name windivert
|
FakeClient.exe | WdfCoInstaller: [12/19/2024 06:25.35.164] BootApplication: could not open service windivert, error error(1060) The specified service does not exist as an installed service.
|