| File name: | f5c3be9a1434d1861a5dfb7d11422361b50b9d65d2b501c35f31f43f32c4b007.msi |
| Full analysis: | https://app.any.run/tasks/8111a52b-4171-4d42-bf77-b168cb2e9637 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 15:44:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
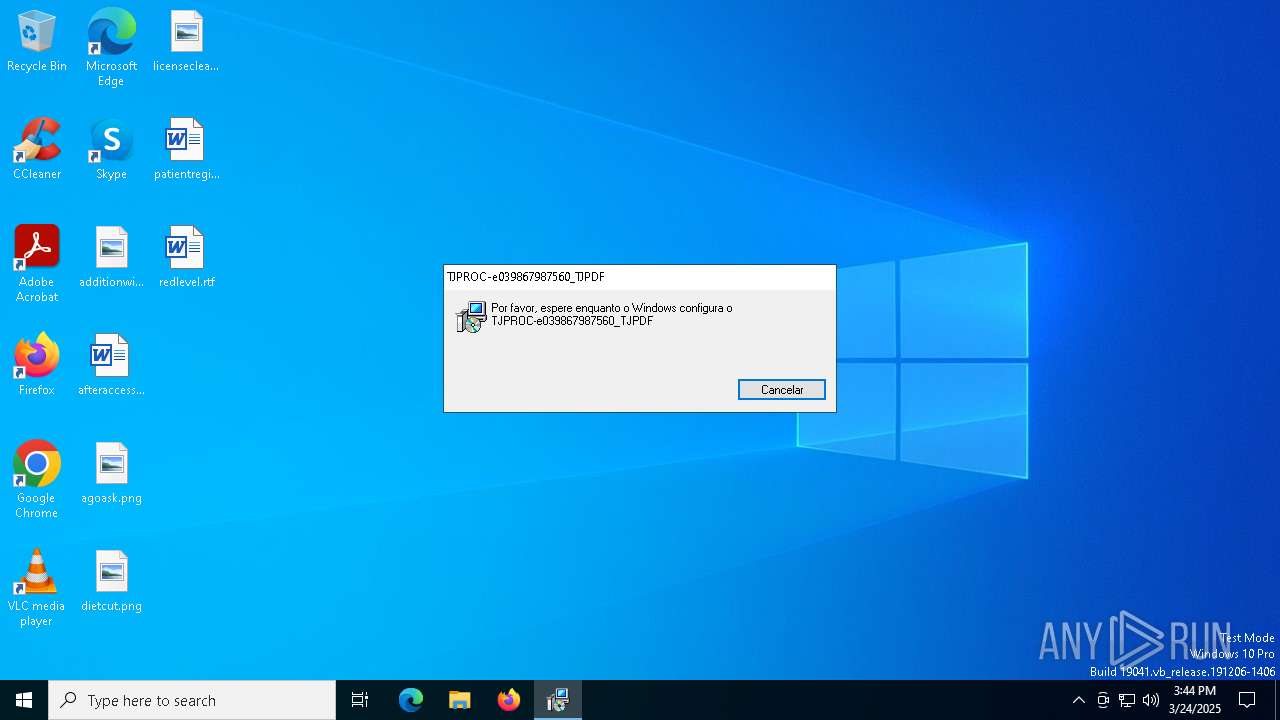
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 1252, Revision Number: {35550E07-87F1-4430-A971-5A91C91C9B4F}, Number of Words: 10, Subject: TJPROC-e039867987560_TJPDF, Author: TJPROC-e039867987560_TJPDF, Name of Creating Application: Advanced Installer 18.3 build e2a0201b, Template: ;1046, Comments: A base dados do instalador contm a lgica e os dados necessrios para instalar o TJPROC-e039867987560_TJPDF., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 9AA1516A18A675CB1972F8FC12194F5A |
| SHA1: | 62E941DE8BD0531EDC38E42EEF43A6789D1F0A35 |
| SHA256: | F5C3BE9A1434D1861A5DFB7D11422361B50B9D65D2B501C35F31F43F32C4B007 |
| SSDEEP: | 98304:w211T/eCYI956FANGMfdeV9E+od2Y+6DGjUvNW/Fbuloi9yAfdABRu22iVMQPIOa:Hk+P |
MALICIOUS
Changes the autorun value in the registry
- msiexec.exe (PID: 7560)
SUSPICIOUS
The process drops C-runtime libraries
- msiexec.exe (PID: 7356)
- msiexec.exe (PID: 7444)
Process drops legitimate windows executable
- msiexec.exe (PID: 7356)
- msiexec.exe (PID: 7444)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7444)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7560)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 7356)
Reads the BIOS version
- bcmUshUpgr.adeSersWvice-64.exe (PID: 7880)
There is functionality for taking screenshot (YARA)
- bcmUshUpgr.adeSersWvice-64.exe (PID: 7880)
INFO
Checks supported languages
- msiexec.exe (PID: 7444)
- msiexec.exe (PID: 7560)
- bcmUshUpgr.adeSersWvice-64.exe (PID: 7880)
Create files in a temporary directory
- msiexec.exe (PID: 7356)
The sample compiled with english language support
- msiexec.exe (PID: 7356)
- msiexec.exe (PID: 7444)
- msiexec.exe (PID: 7560)
Reads the computer name
- msiexec.exe (PID: 7444)
- msiexec.exe (PID: 7560)
- bcmUshUpgr.adeSersWvice-64.exe (PID: 7880)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7444)
- msiexec.exe (PID: 7560)
Reads Environment values
- msiexec.exe (PID: 7560)
- bcmUshUpgr.adeSersWvice-64.exe (PID: 7880)
Checks proxy server information
- msiexec.exe (PID: 7560)
- BackgroundTransferHost.exe (PID: 2600)
- slui.exe (PID: 5548)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7560)
Creates files or folders in the user directory
- msiexec.exe (PID: 7560)
- BackgroundTransferHost.exe (PID: 2600)
Reads the software policy settings
- msiexec.exe (PID: 7560)
- BackgroundTransferHost.exe (PID: 2600)
- slui.exe (PID: 7672)
- slui.exe (PID: 5548)
- bcmUshUpgr.adeSersWvice-64.exe (PID: 7880)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 728)
- BackgroundTransferHost.exe (PID: 1532)
- BackgroundTransferHost.exe (PID: 8112)
- BackgroundTransferHost.exe (PID: 2600)
- BackgroundTransferHost.exe (PID: 1272)
Process checks computer location settings
- msiexec.exe (PID: 7560)
Themida protector has been detected
- bcmUshUpgr.adeSersWvice-64.exe (PID: 7880)
Compiled with Borland Delphi (YARA)
- bcmUshUpgr.adeSersWvice-64.exe (PID: 7880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {35550E07-87F1-4430-A971-5A91C91C9B4F} |
| Words: | 10 |
| Subject: | TJPROC-e039867987560_TJPDF |
| Author: | TJPROC-e039867987560_TJPDF |
| LastModifiedBy: | - |
| Software: | Advanced Installer 18.3 build e2a0201b |
| Template: | ;1046 |
| Comments: | A base dados do instalador contêm a lógica e os dados necessários para instalar o TJPROC-e039867987560_TJPDF. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
151
Monitored processes
13
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7356 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\f5c3be9a1434d1861a5dfb7d11422361b50b9d65d2b501c35f31f43f32c4b007.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7444 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7560 | C:\Windows\syswow64\MsiExec.exe -Embedding 55FEF4B200FDA47DB2DB4D9A060A3B49 | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7640 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 219
Read events
7 167
Write events
39
Delete events
13
Modification events
| (PID) Process: | (7444) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 141D0000D74A619FD39CDB01 | |||
| (PID) Process: | (7444) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 83CF94DED72469219FD964C611A7D2DA6A0094FEDD12382FAECEF57FA110306D | |||
| (PID) Process: | (7444) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (7560) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings |
| Operation: | write | Name: | JITDebug |
Value: 0 | |||
| (PID) Process: | (7560) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7560) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7560) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (728) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (728) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (728) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
12
Suspicious files
29
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2600 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\240e0af3-ac84-4ada-b341-1a0fe35a17aa.down_data | — | |
MD5:— | SHA256:— | |||
| 7560 | msiexec.exe | C:\Users\admin\ZDW@$4V@_\1 | executable | |
MD5:8A242AEBA83C7DA62DFF095417CCCD31 | SHA256:51915EE49701927A930A033AC2B84C3303B8CF7AC88869B0D2BA6AABC5FA66F8 | |||
| 7560 | msiexec.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\bangaliu[1].jpg | compressed | |
MD5:B1D0A219F2CD923773D08D3E809E6703 | SHA256:3B778C7177BBD47FC4A24B7F52AE37E8B5C56BF072BDDFE1068FCCFA70EB535C | |||
| 7560 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:11507E21FBC18C6B5D3AB0E81CB03A3B | SHA256:CAA97A0422E3BD7DE8660E63DF77F1F4455BE30B4DC7558F40C5A52EB959BF08 | |||
| 7444 | msiexec.exe | C:\Windows\Installer\MSID545.tmp | executable | |
MD5:20C782EB64C81AC14C83A853546A8924 | SHA256:0ED6836D55180AF20F71F7852E3D728F2DEFE22AA6D2526C54CFBBB4B48CC6A1 | |||
| 7444 | msiexec.exe | C:\Windows\Installer\MSID40C.tmp | executable | |
MD5:20C782EB64C81AC14C83A853546A8924 | SHA256:0ED6836D55180AF20F71F7852E3D728F2DEFE22AA6D2526C54CFBBB4B48CC6A1 | |||
| 2600 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:3949F0AE6EDB23DBA9A23F973CED1B53 | SHA256:5588A0A4A7940B73DE8392D29111FDDAD5606F1BFD45BFF549D590012C219679 | |||
| 7560 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C94D55264BB8C7430CDA7D64C77EBE4D | binary | |
MD5:5CA6356FC86C7EC1F4B19506950586F9 | SHA256:C27143C7C53A25A82B379D0C2FEC25DB99CB42199244656BB32BE00602C78627 | |||
| 2600 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
| 7444 | msiexec.exe | C:\Windows\Installer\10d0bf.msi | executable | |
MD5:9AA1516A18A675CB1972F8FC12194F5A | SHA256:F5C3BE9A1434D1861A5DFB7D11422361B50B9D65D2B501C35F31F43F32C4B007 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
34
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.157:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.157:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7560 | msiexec.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7560 | msiexec.exe | GET | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgM99LaYMze68xKPx1ZiZWD3Qg%3D%3D | unknown | — | — | whitelisted |
7380 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2600 | BackgroundTransferHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3132 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3132 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.157:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.157:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
othund.octabracessorioscom.com |
| unknown |
arc.msn.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r10.o.lencr.org |
| whitelisted |