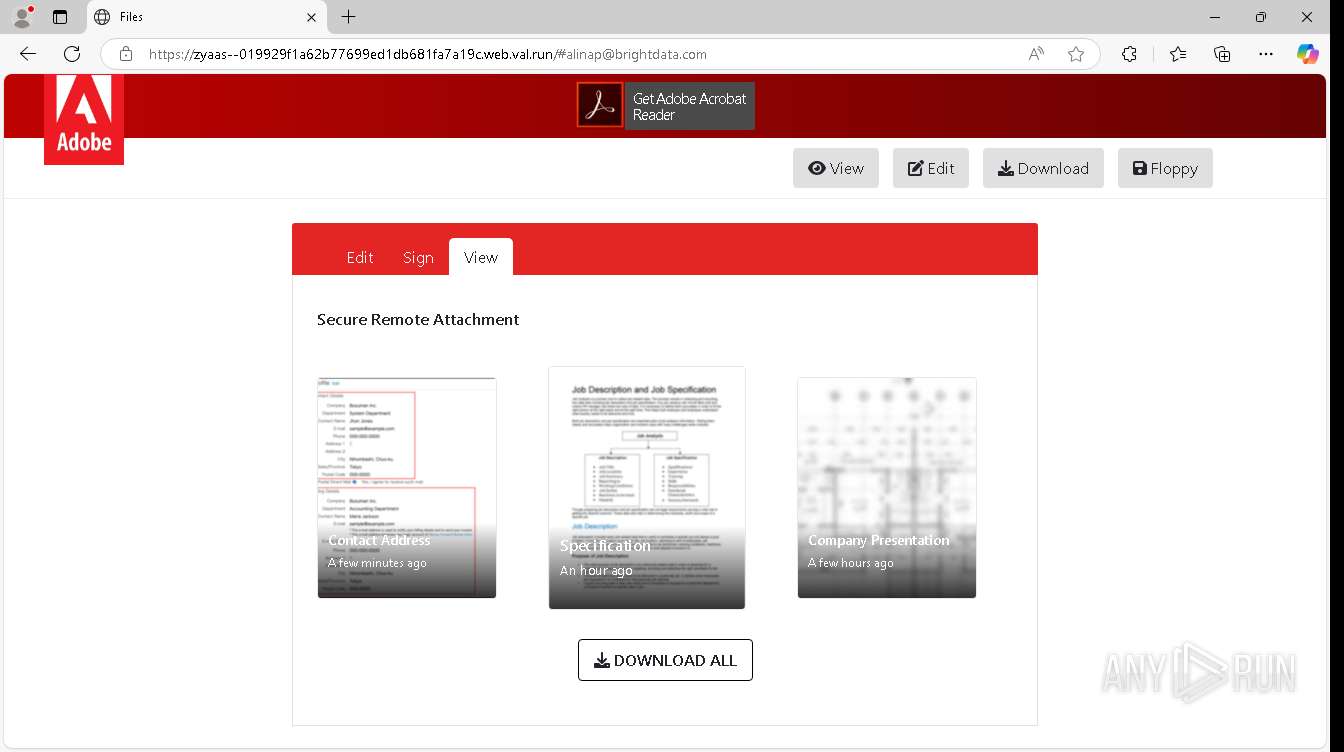
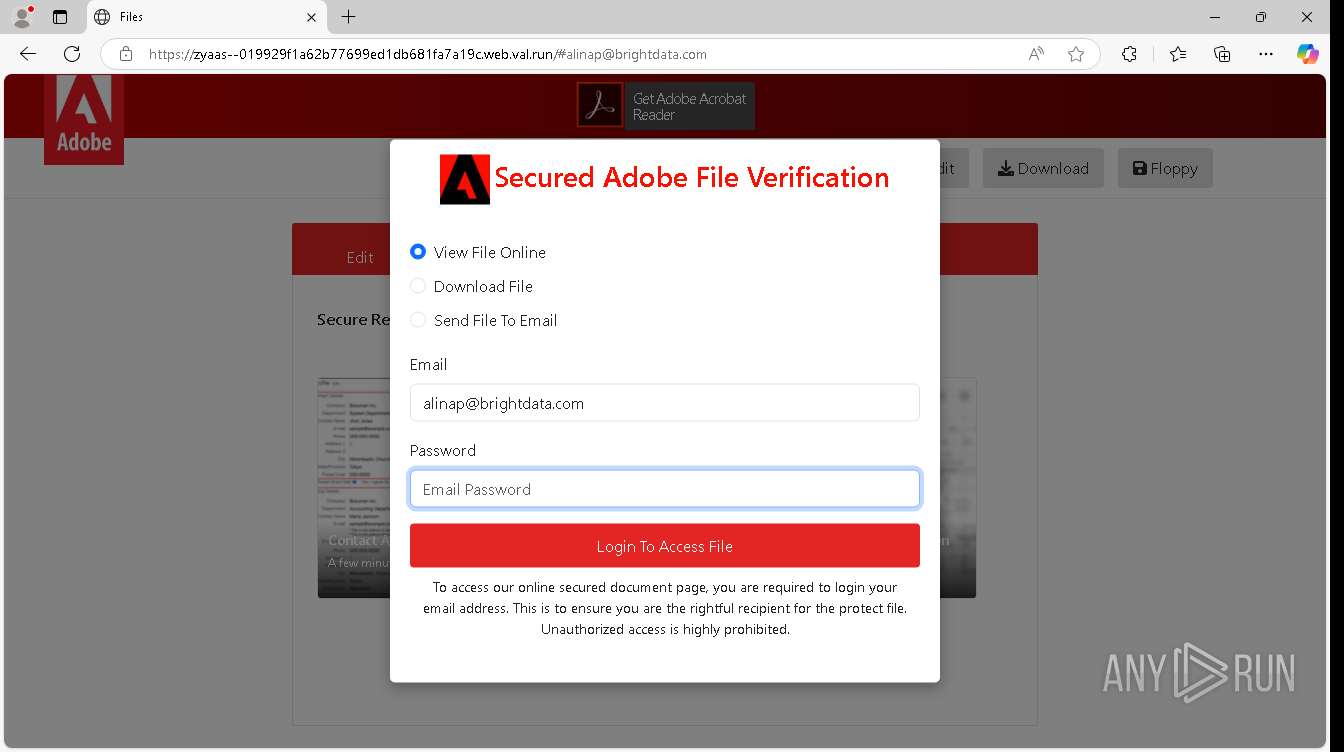
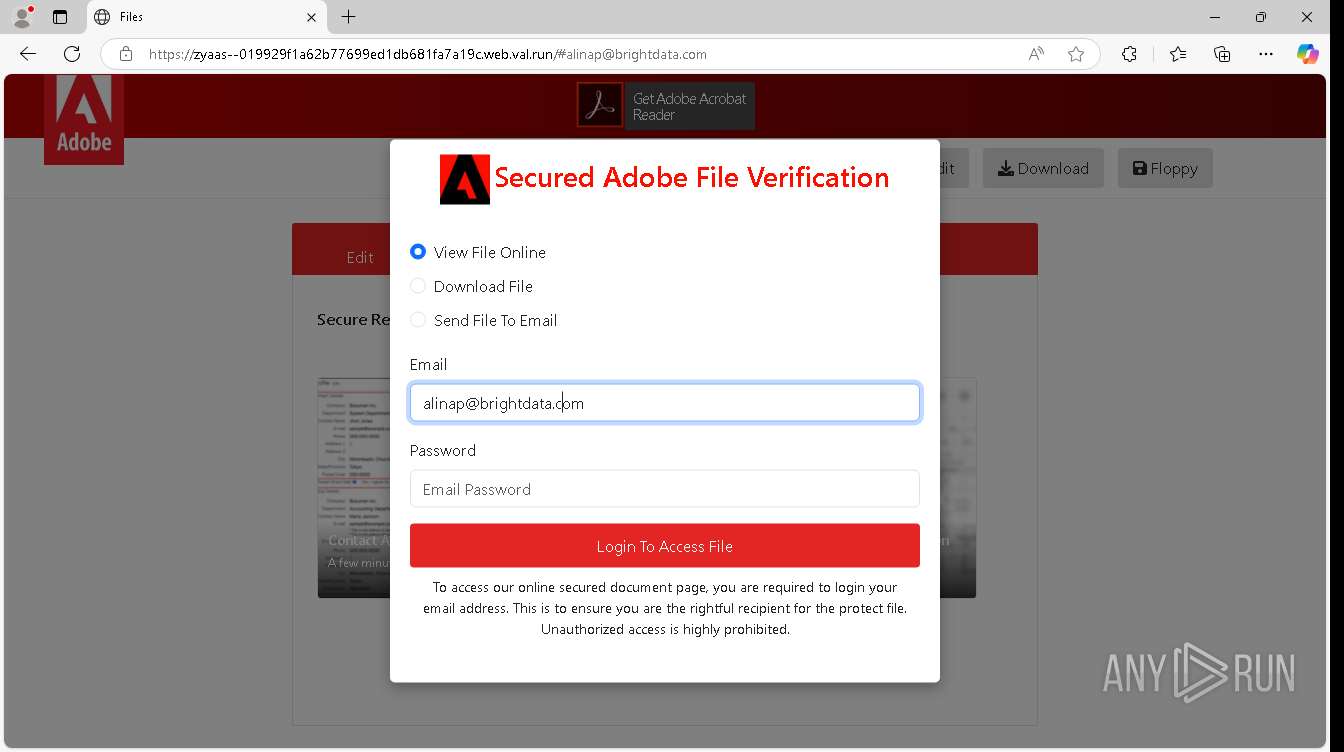
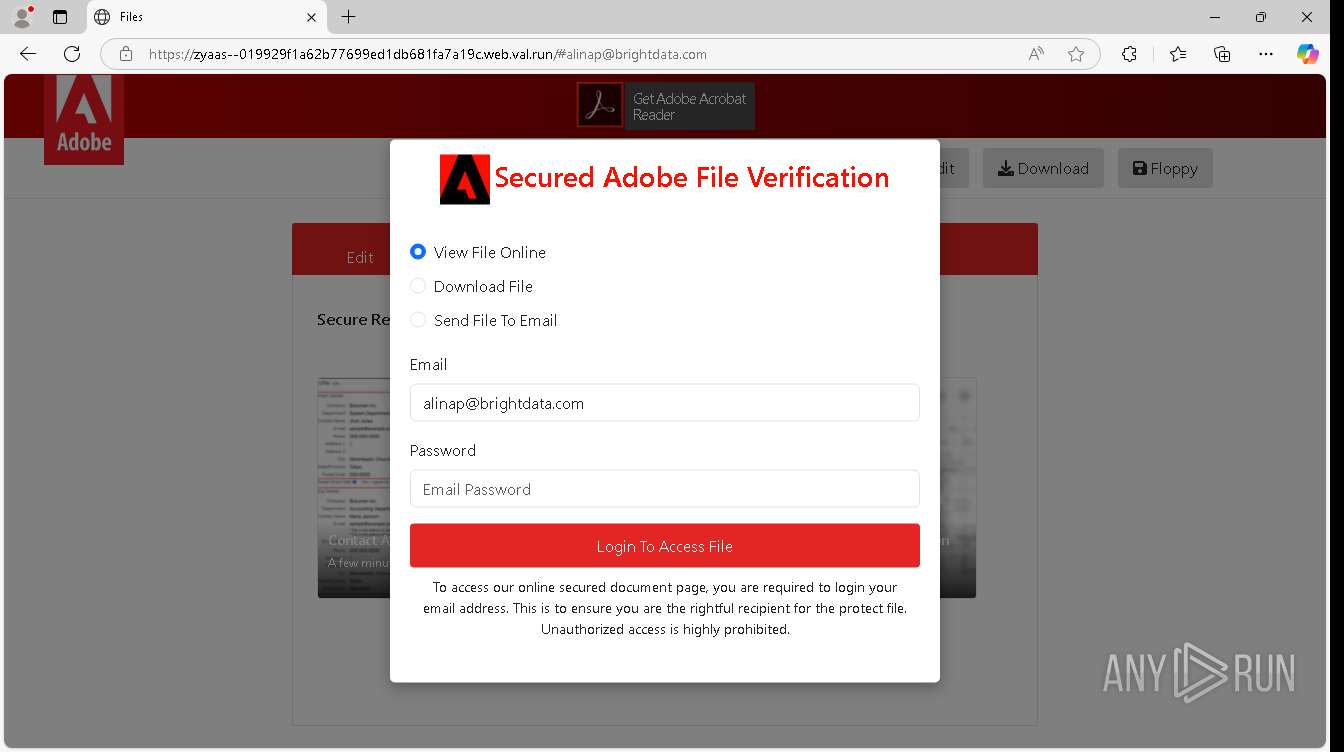
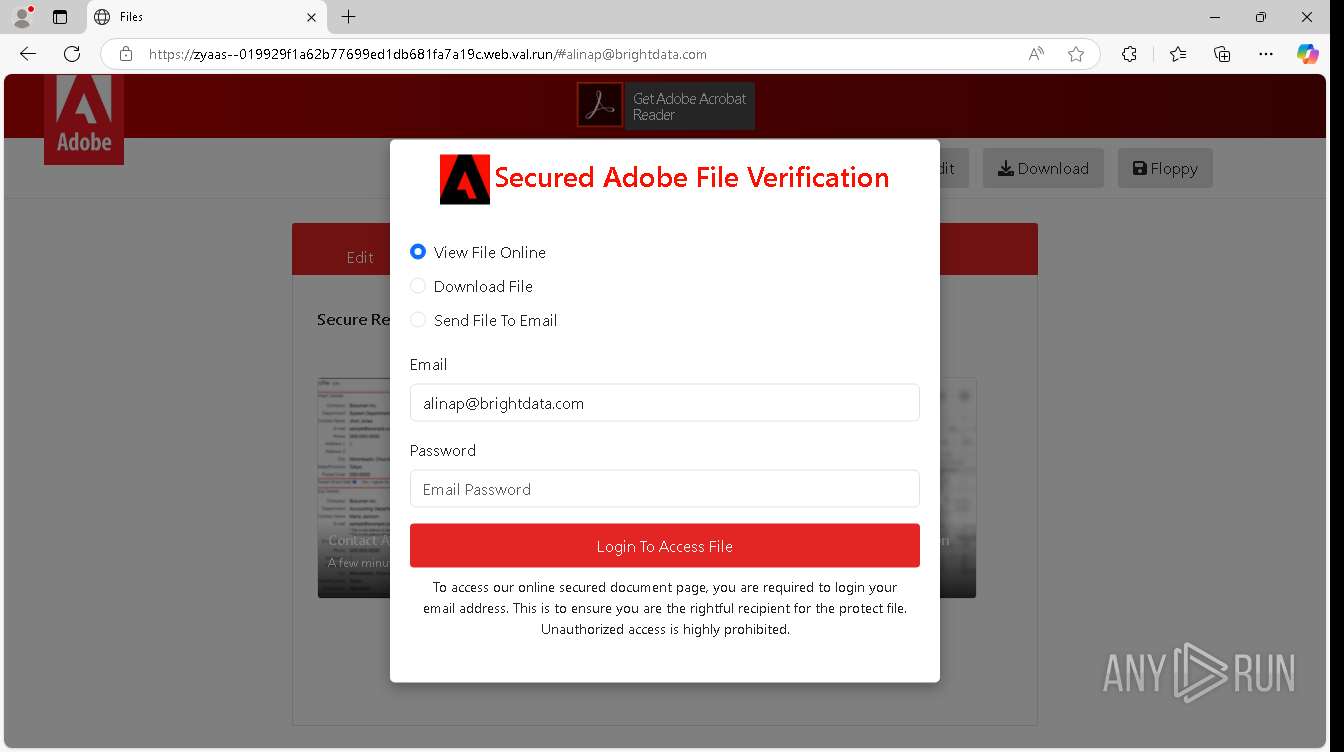
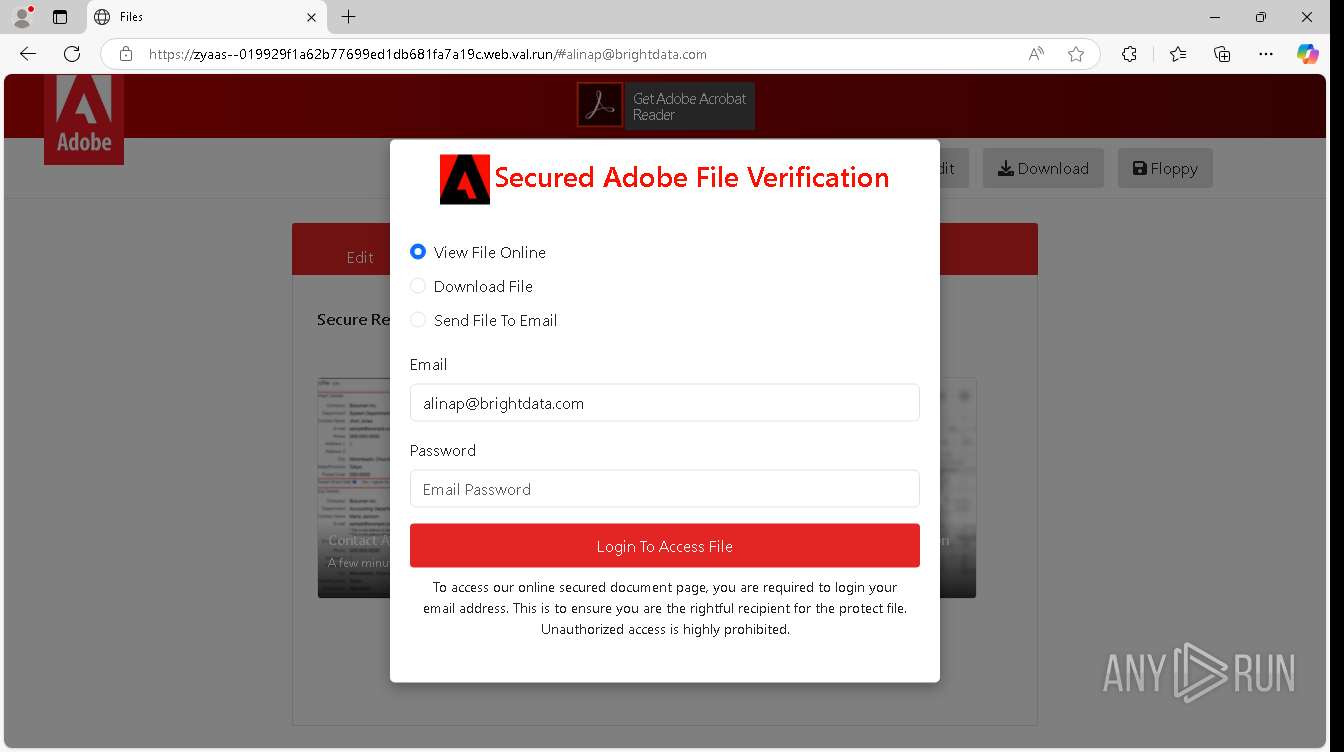
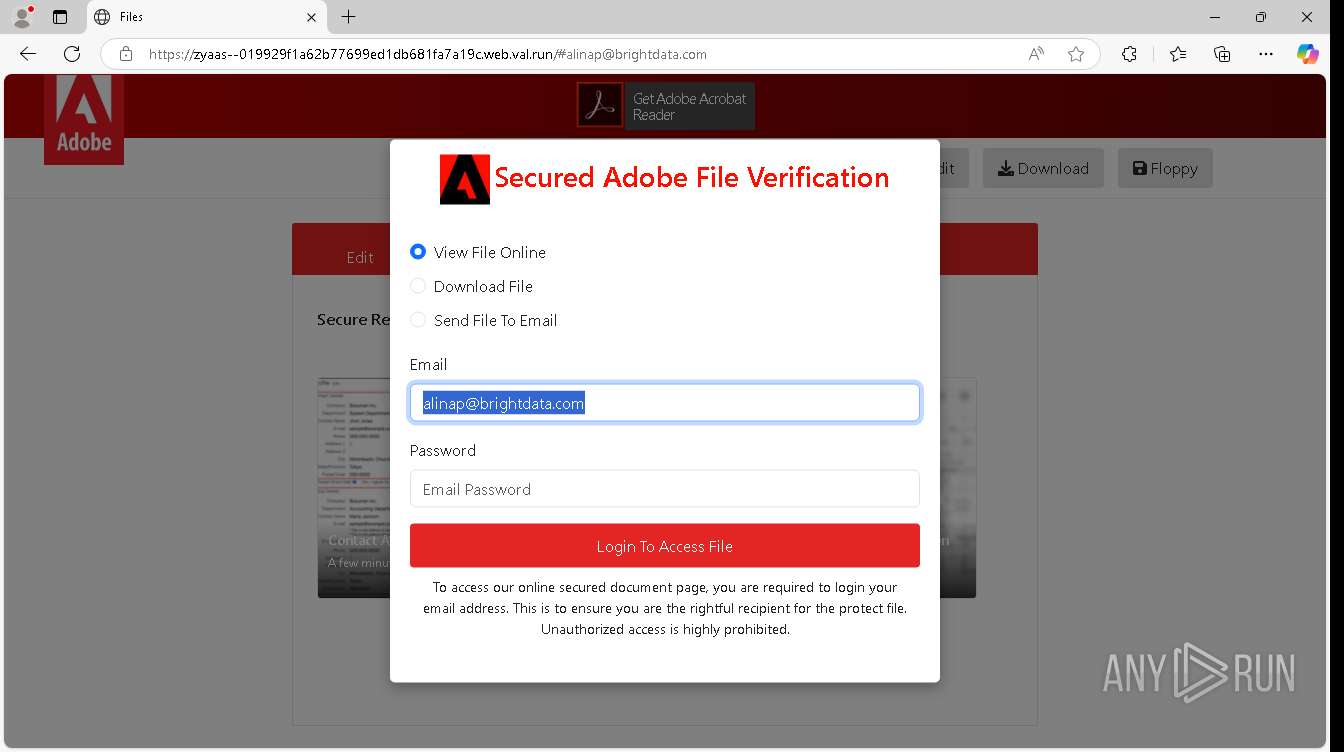
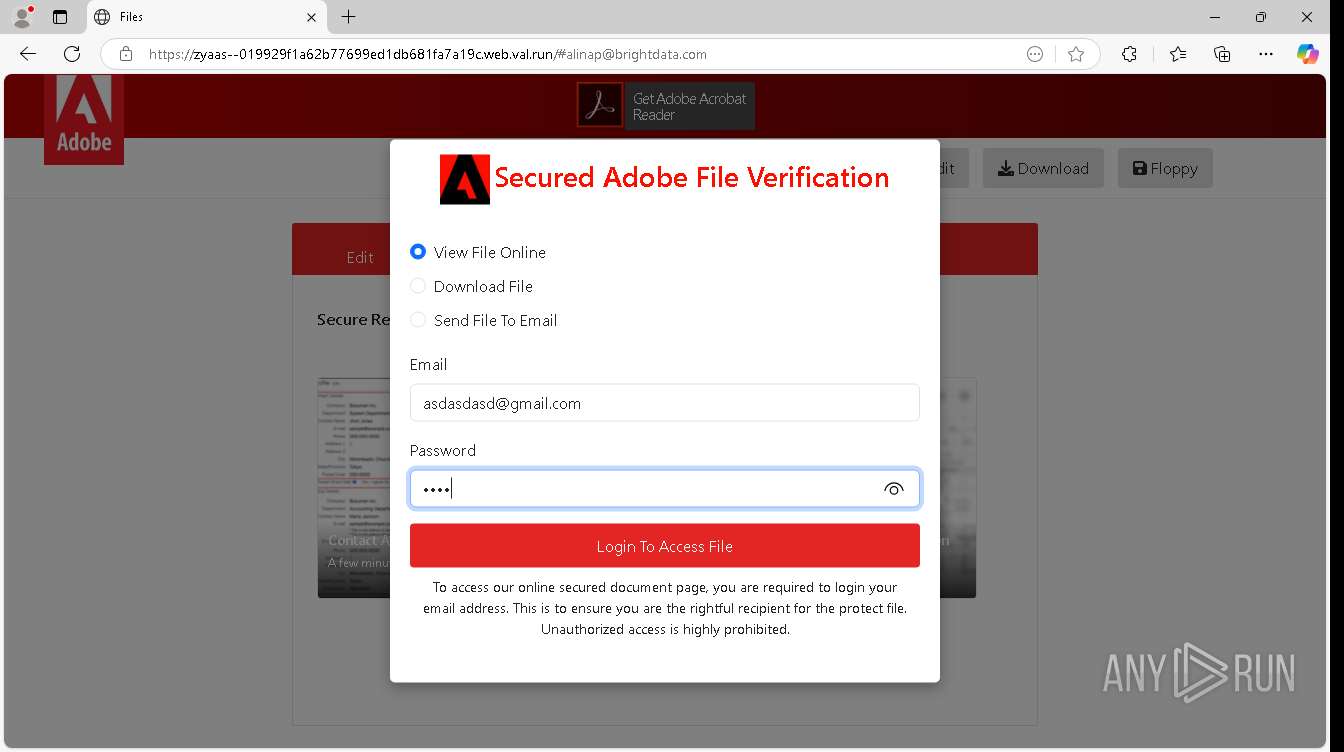
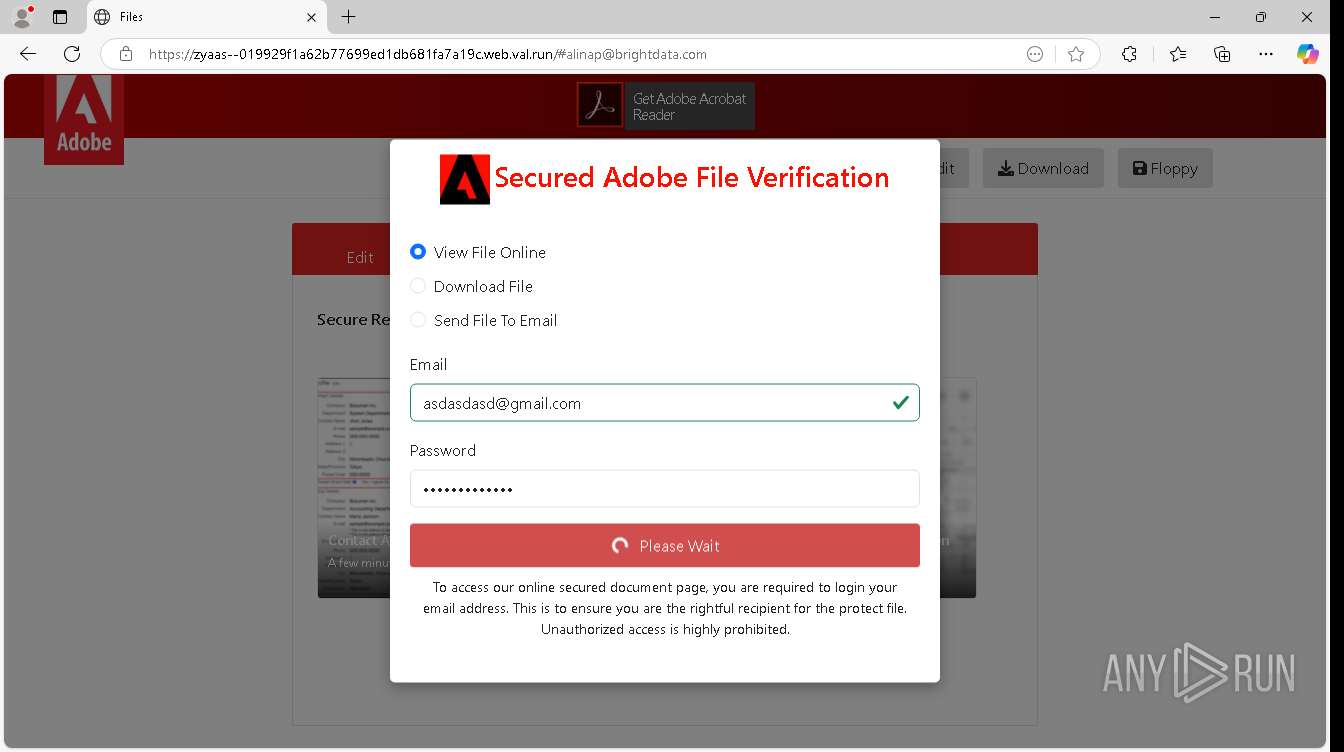
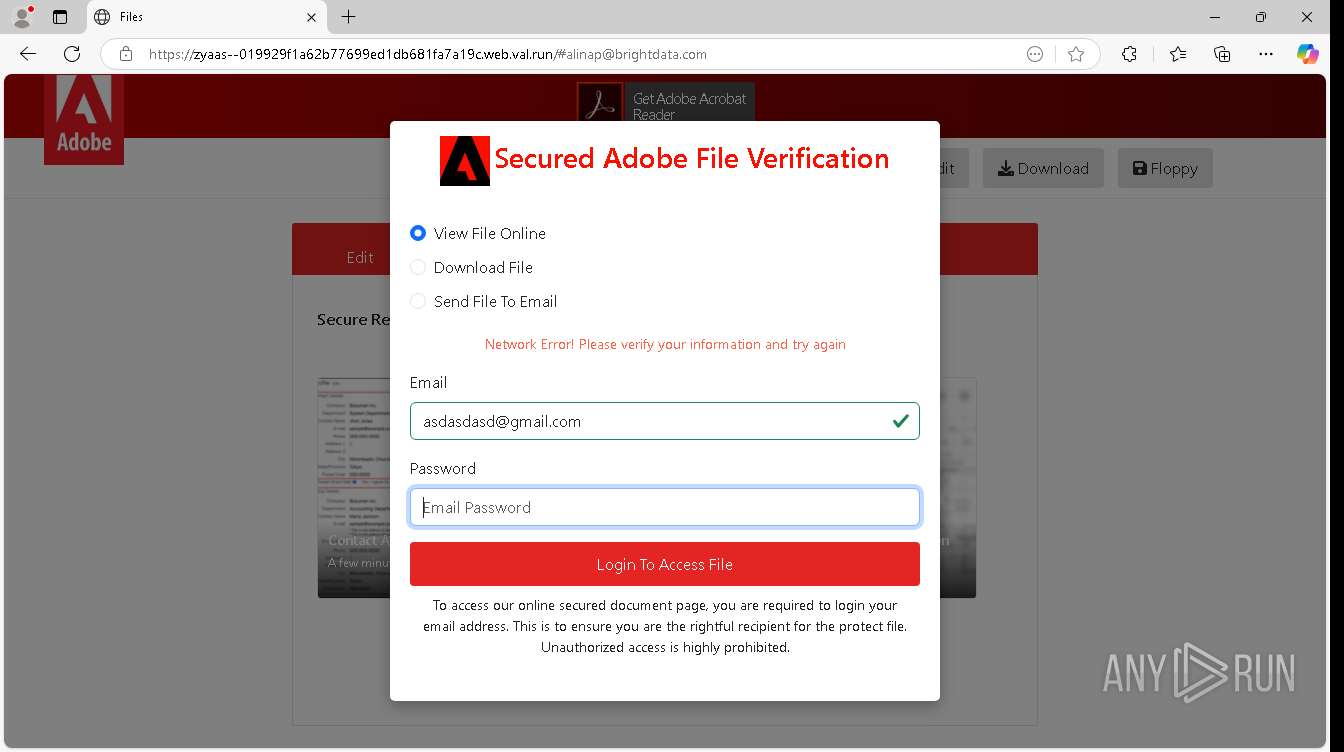
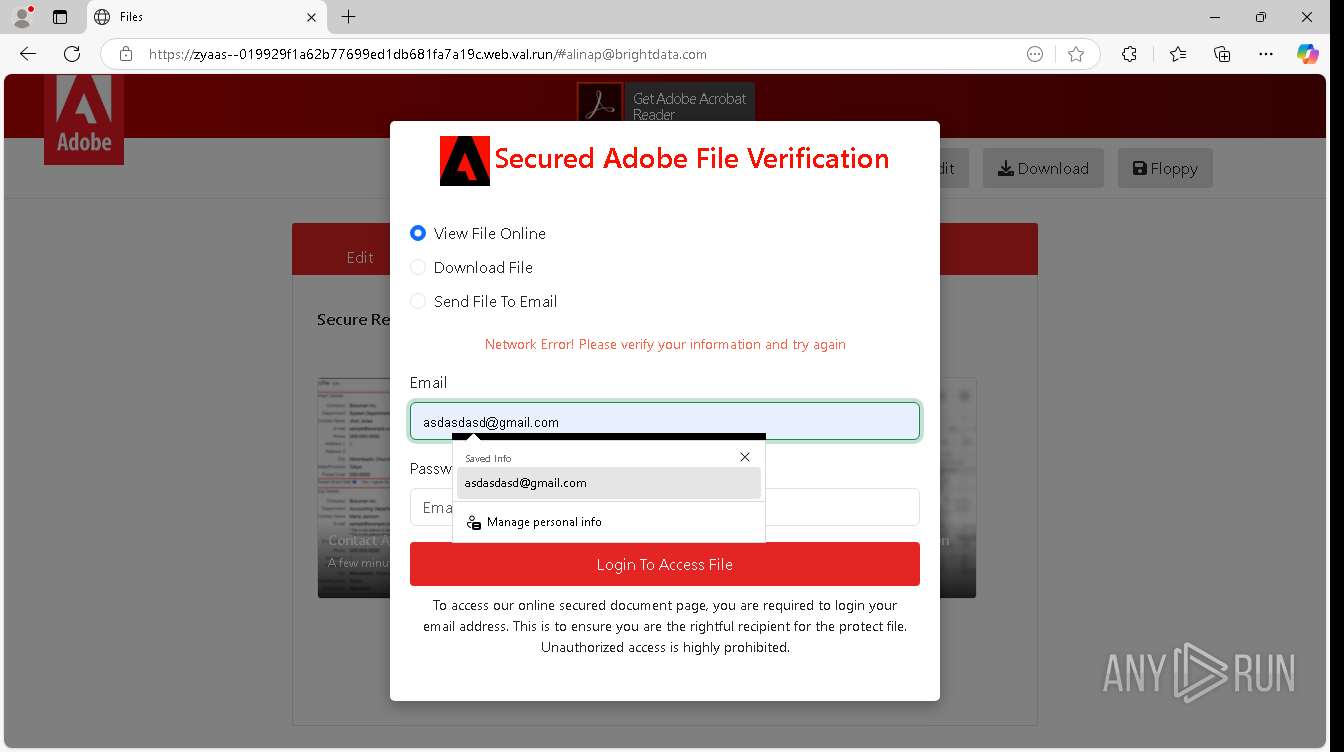
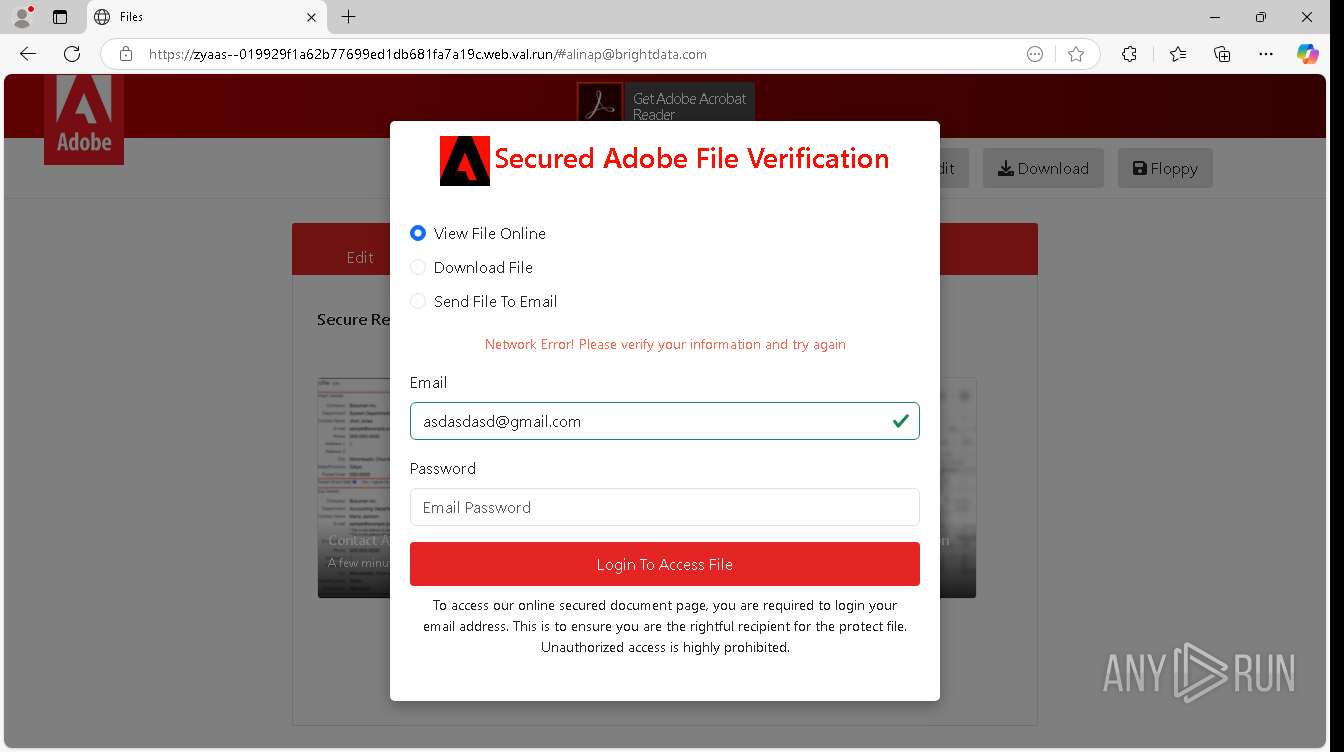
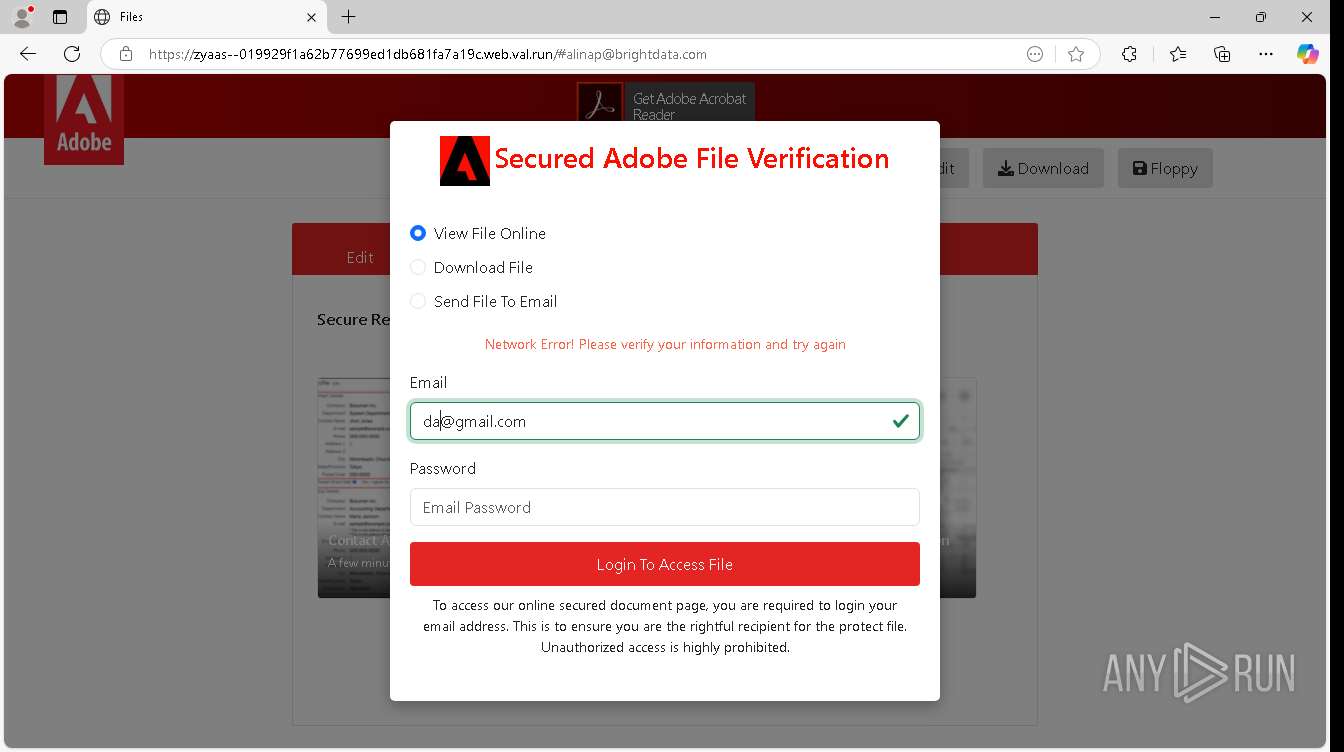
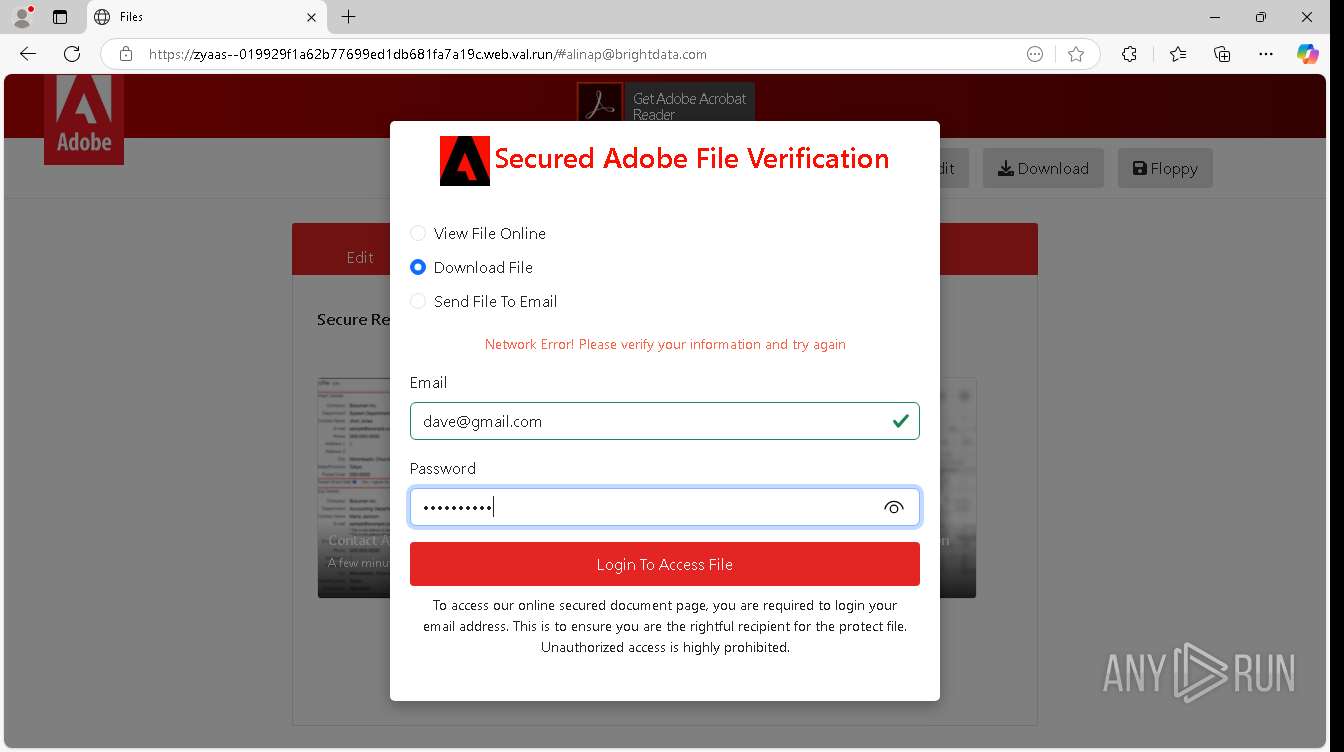
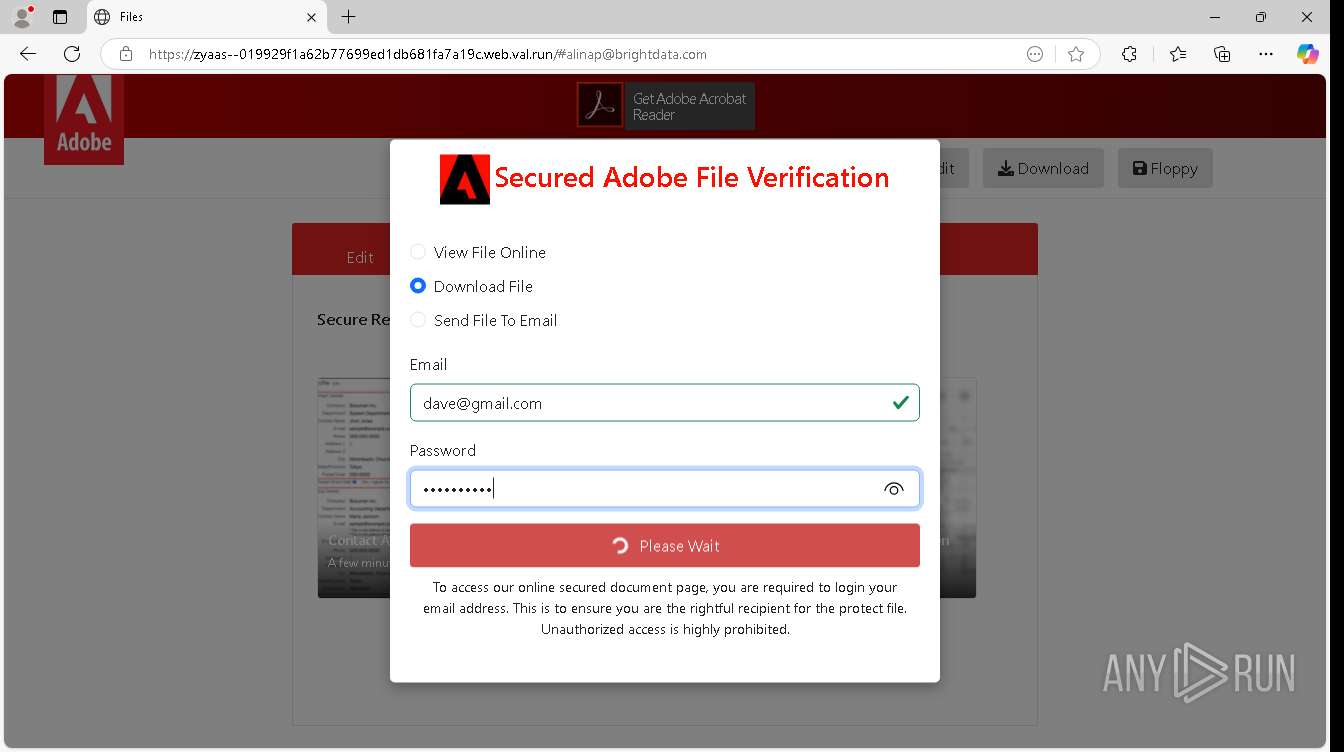
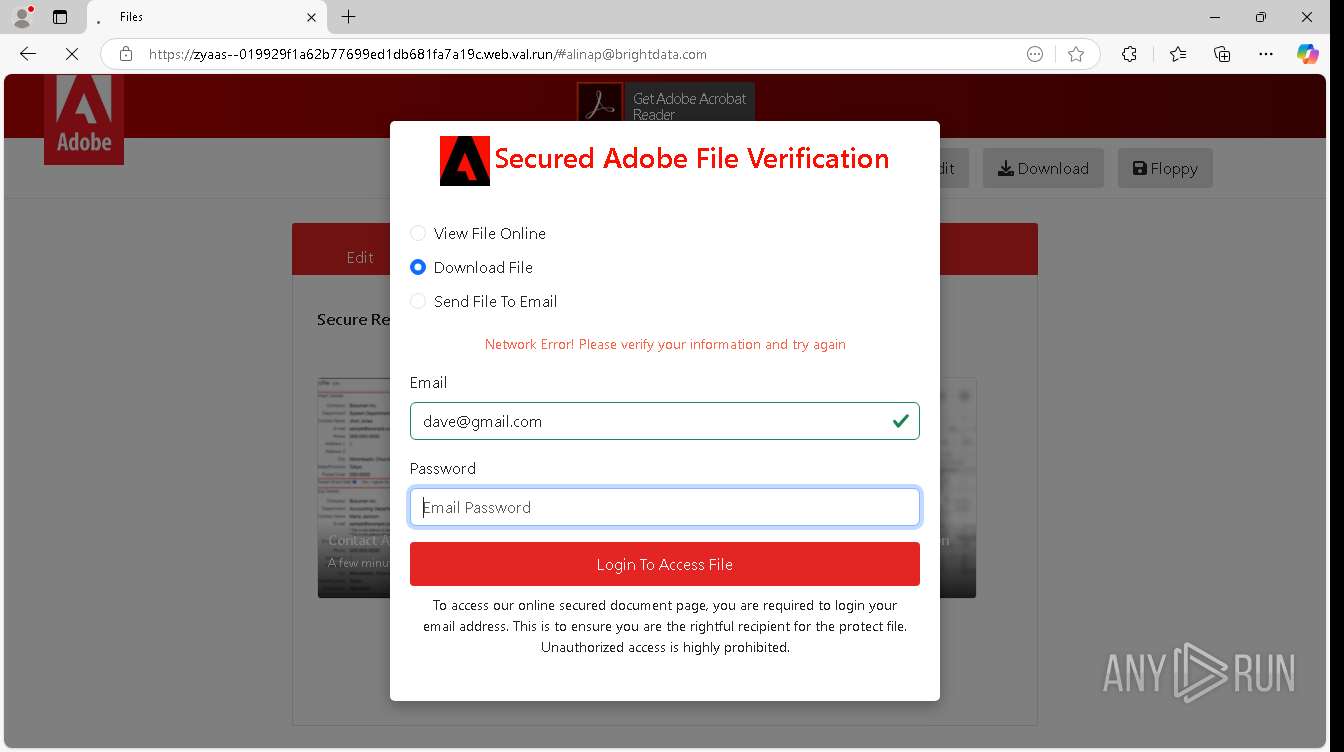
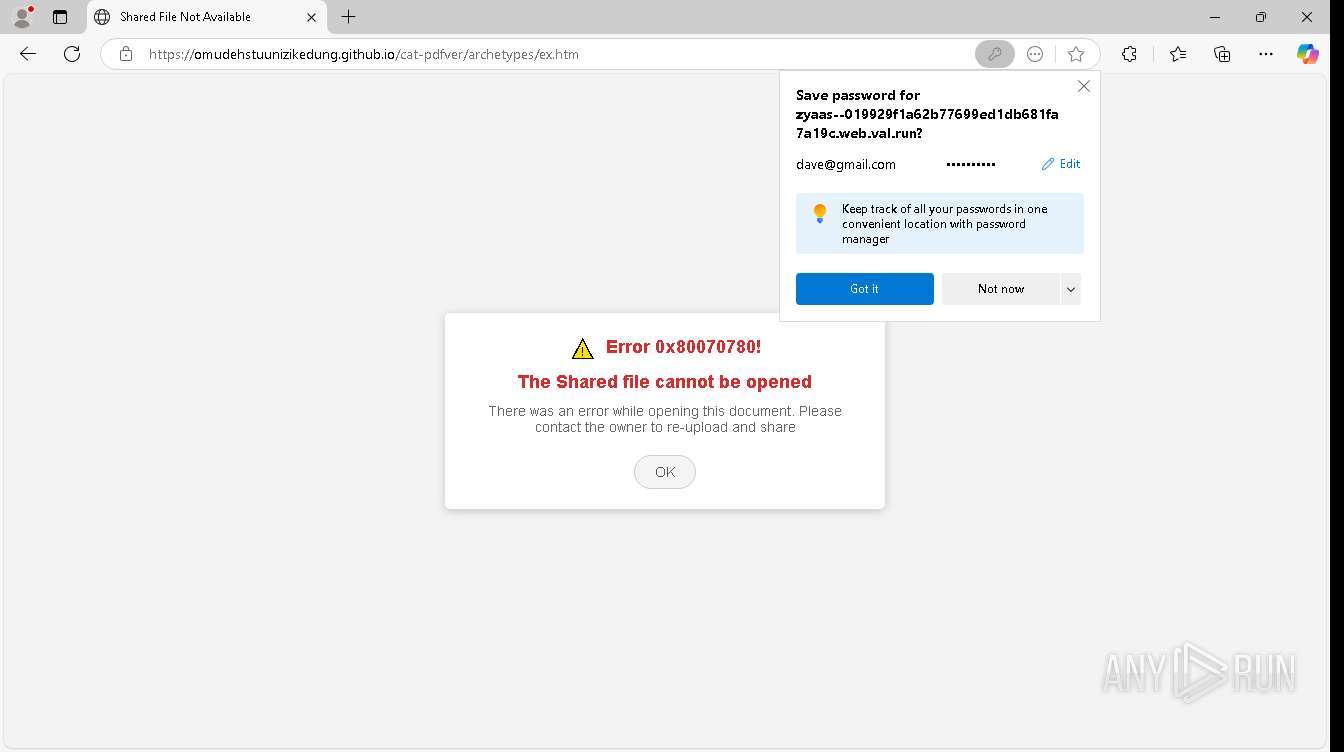
| URL: | https://zyaas--019929f1a62b77699ed1db681fa7a19c.web.val.run/#[email protected] |
| Full analysis: | https://app.any.run/tasks/486888b5-33bf-47c0-83ca-e5cc7f7b08fd |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2025, 11:33:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MD5: | E95ECC0A0AE64FD77395A21AA6E60D4B |
| SHA1: | 404DDBEF7E3D3A900791EBA1DCC0C559A7C2D5C8 |
| SHA256: | F5A98B9D80B10590EF80A42CDDB6CAF22D92ABDFBE49B929E099B2044A90869B |
| SSDEEP: | 3:N8/UGDRb3daES53Ys+kEGT:2/UURb0ES2svT |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
143
Monitored processes
0
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
113
TCP/UDP connections
107
DNS requests
74
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | — | 23.57.4.240:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | — | — | — |
— | — | POST | — | 23.57.4.240:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | — | — | — |
— | — | POST | — | 23.57.4.240:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | — | — | — |
6456 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6888 | msedge.exe | GET | 403 | 2.16.56.71:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1753186353&P2=404&P3=2&P4=JctxgV%2fBzu58lG09sot5gGnCe%2fY1hwdAjsjhuzjzxTQ2YzQOHr%2fJXcKzV3SdbfHgQEdRSVQGHksTHkDx0nQLkQ%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 3.136.67.80:443 | https://zyaas--019929f1a62b77699ed1db681fa7a19c.web.val.run/ | unknown | binary | 33.3 Kb | — |
— | — | HEAD | 200 | 23.199.214.10:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
— | — | POST | 200 | 150.171.27.11:443 | https://edge.microsoft.com/componentupdater/api/v1/update | unknown | text | 1.46 Kb | — |
4704 | RUXIMICS.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5336 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6456 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4704 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6888 | msedge.exe | 2.16.56.71:80 | msedge.b.tlu.dl.delivery.mp.microsoft.com | AKAMAI-AS | GB | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 23.57.6.7:443 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
5008 | svchost.exe | 104.102.63.189:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
6888 | msedge.exe | 3.136.67.80:443 | zyaas--019929f1a62b77699ed1db681fa7a19c.web.val.run | AMAZON-02 | US | unknown |
6456 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | unknown |
4704 | RUXIMICS.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
msedge.b.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
zyaas--019929f1a62b77699ed1db681fa7a19c.web.val.run |
| unknown |
crl.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious sending of an email address as an unencrypted POST request |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |