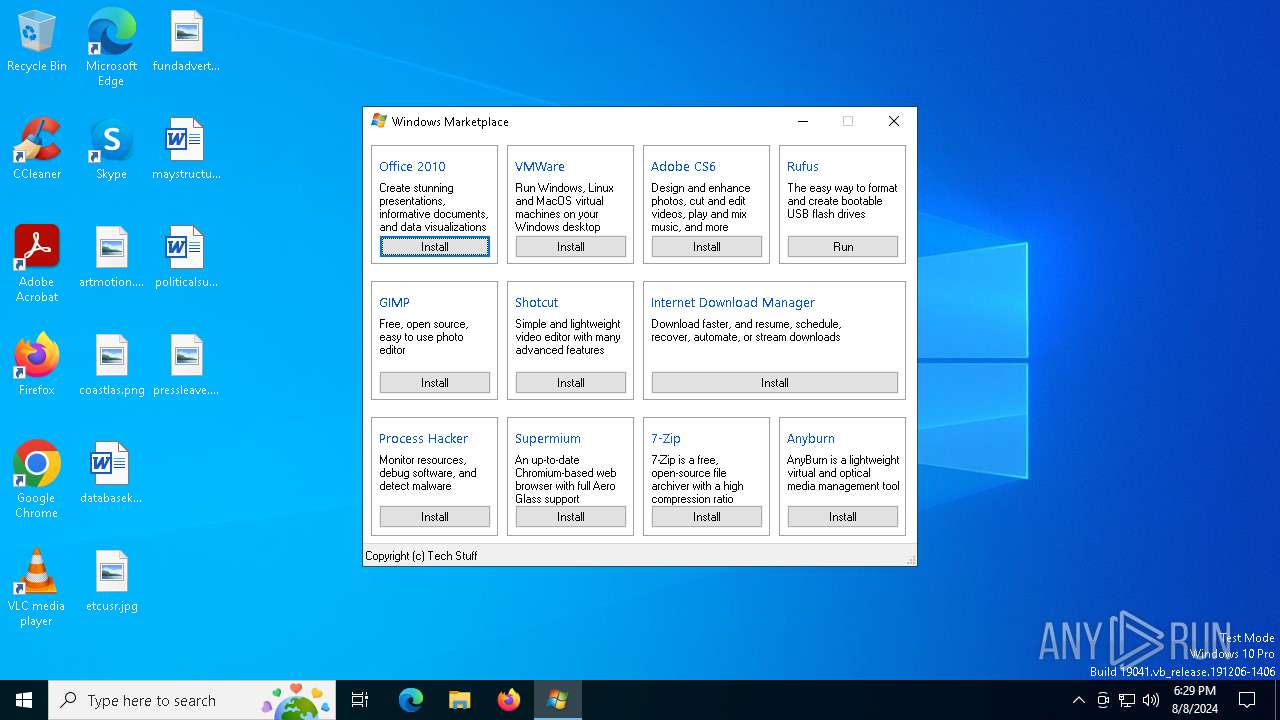
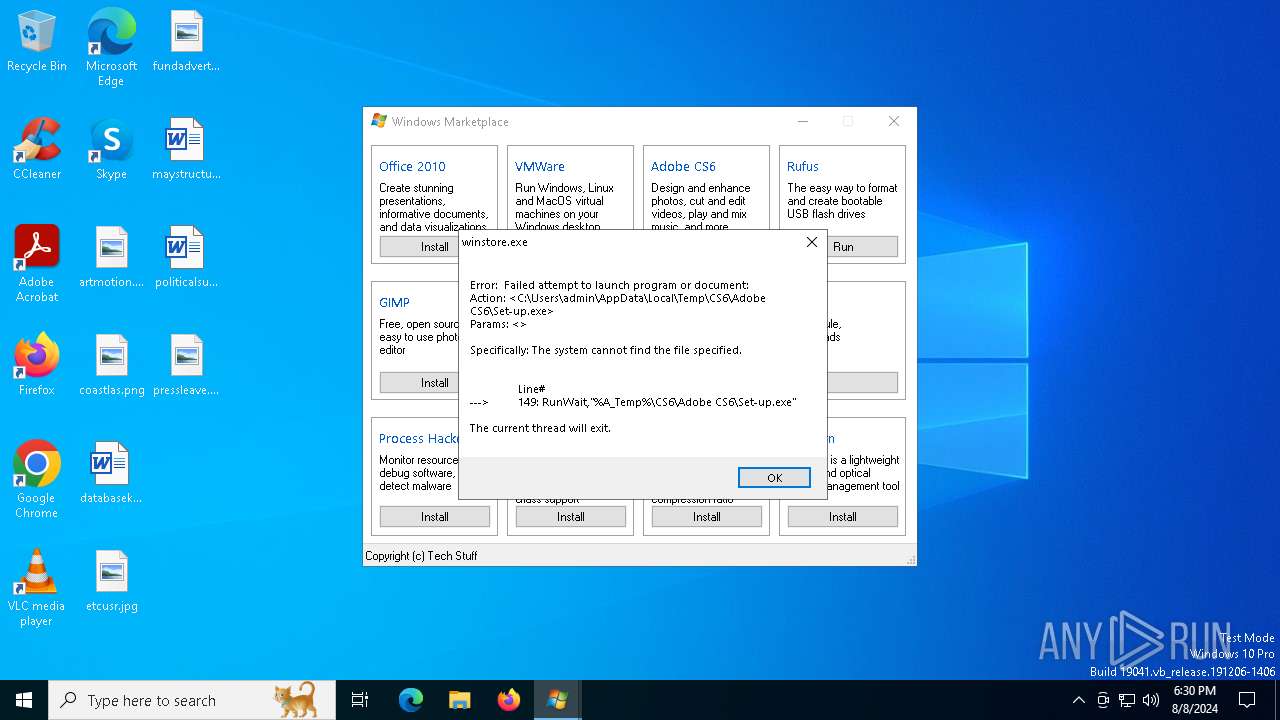
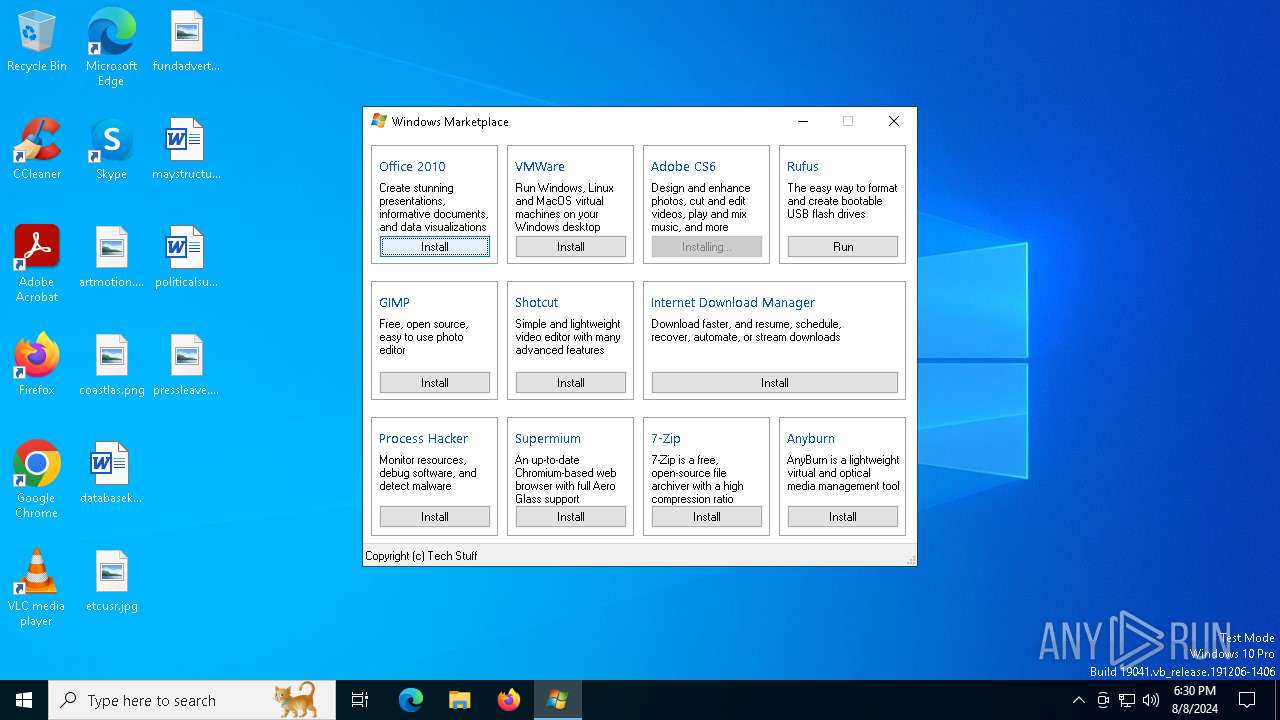
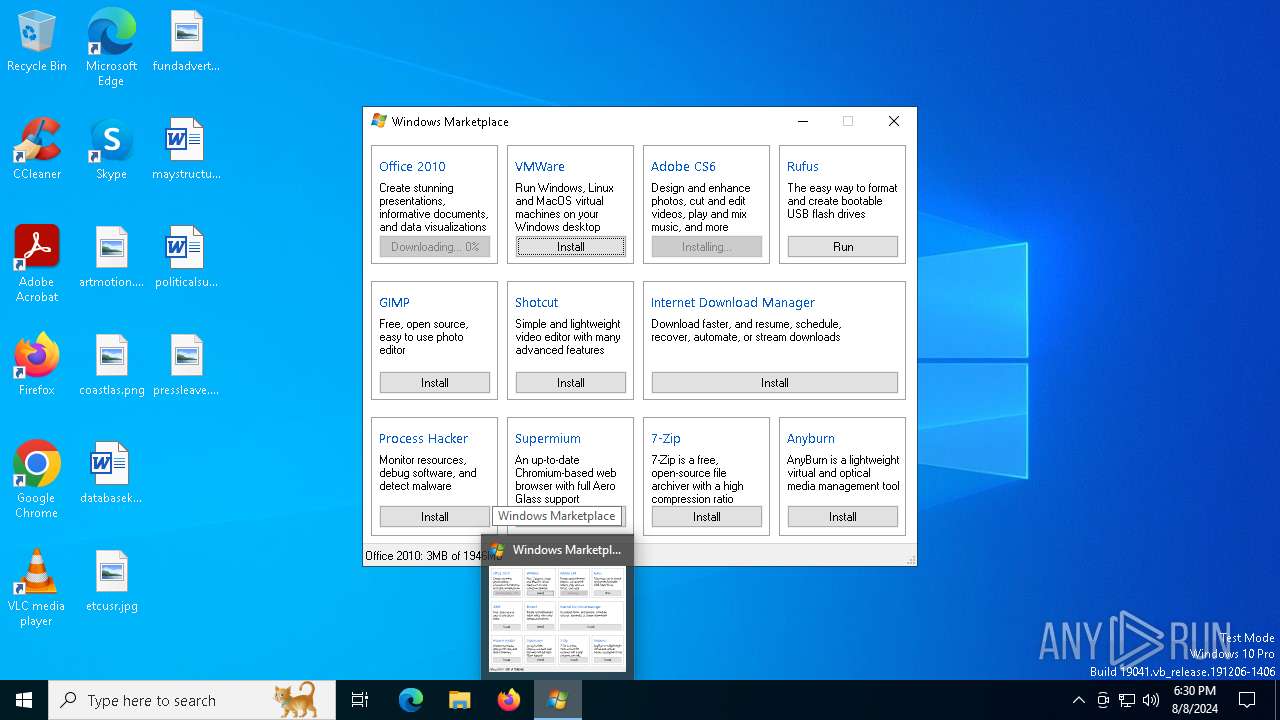
| File name: | winstore.exe |
| Full analysis: | https://app.any.run/tasks/f9fcc954-b1b9-4138-b5d9-49a33ac3317c |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2024, 18:29:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 53084E425064922E956509941D42D252 |
| SHA1: | 2D6F1006788488B9183A2CAA73BD1D19C2B5EA94 |
| SHA256: | F59D154D2A70B1498E0FAE7F510ADD8469AD1A128CEBE544BF0D97A2C734FB26 |
| SSDEEP: | 98304:fRM0t6TFK6D0us/1X47c4DbjU5UBlq8xjv6JgOTPw0/erO7DSWPiYm2533q1O/l+:71YUPG8LujfCBil |
MALICIOUS
Adds path to the Windows Defender exclusion list
- winstore.exe (PID: 6468)
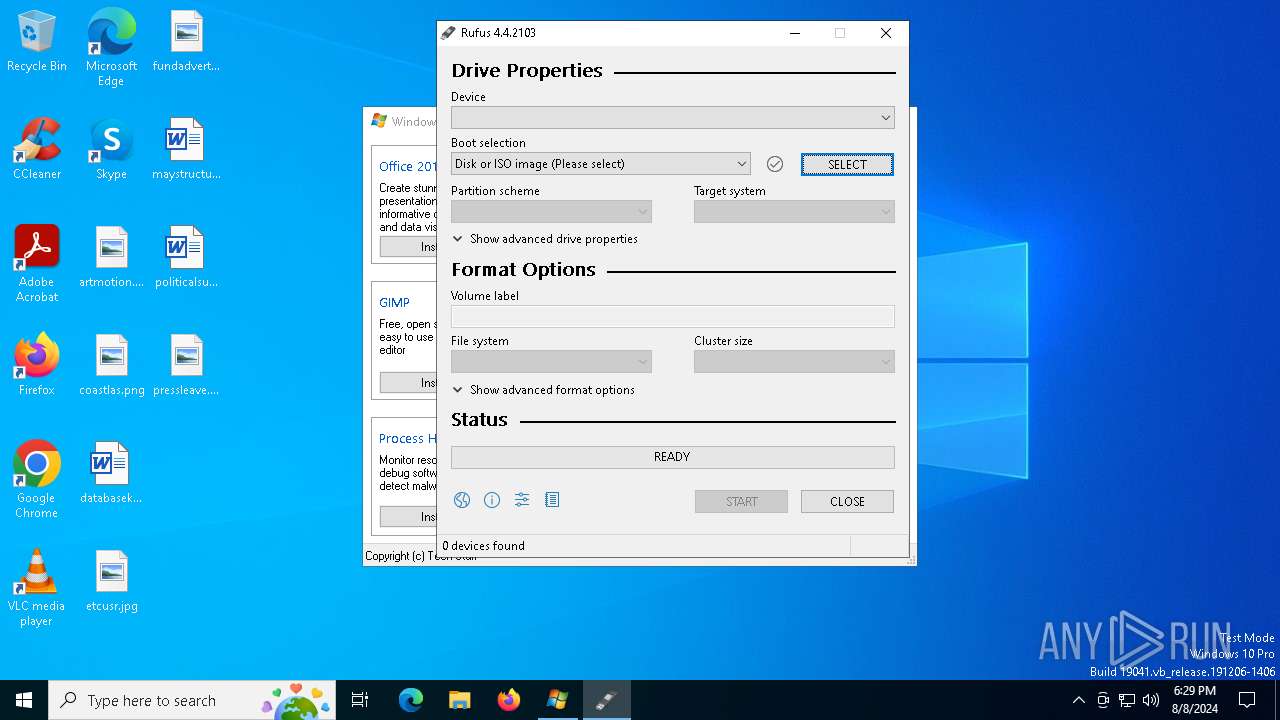
Changes the Windows auto-update feature
- rufus.exe (PID: 7048)
SUSPICIOUS
Drops the executable file immediately after the start
- winstore.exe (PID: 6468)
Script adds exclusion path to Windows Defender
- winstore.exe (PID: 6468)
Starts CMD.EXE for commands execution
- winstore.exe (PID: 6468)
Application launched itself
- winstore.exe (PID: 6468)
Starts POWERSHELL.EXE for commands execution
- winstore.exe (PID: 6468)
Reads security settings of Internet Explorer
- winstore.exe (PID: 6968)
- winstore.exe (PID: 3700)
- winstore.exe (PID: 2456)
Checks Windows Trust Settings
- winstore.exe (PID: 6968)
- winstore.exe (PID: 3700)
- winstore.exe (PID: 2456)
Executable content was dropped or overwritten
- winstore.exe (PID: 6468)
Executes as Windows Service
- vds.exe (PID: 7120)
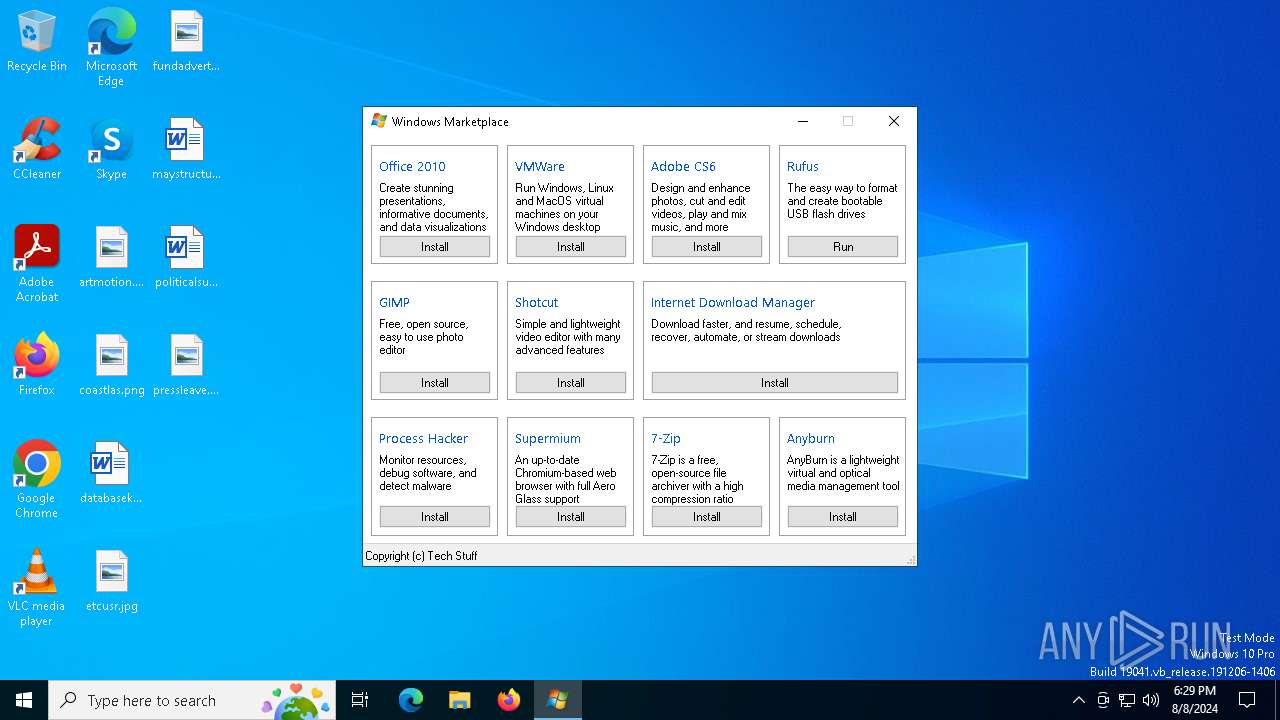
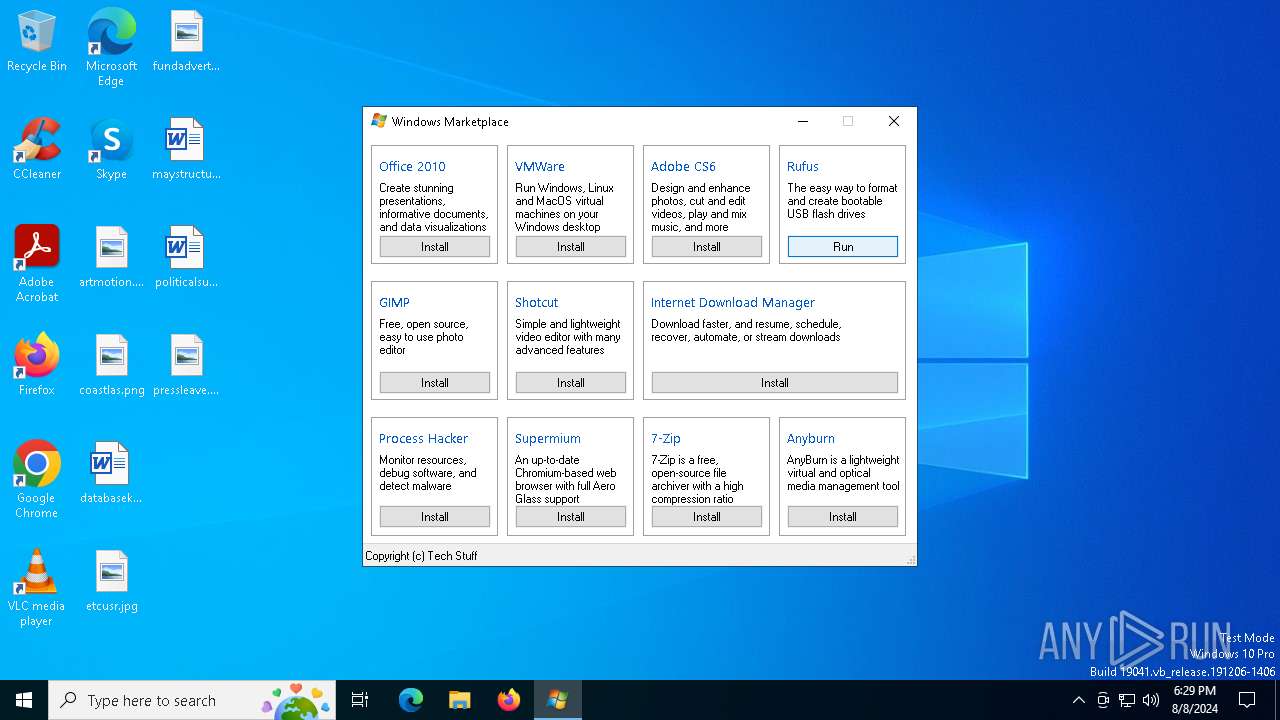
Drops 7-zip archiver for unpacking
- winstore.exe (PID: 6468)
Creates files in the driver directory
- winstore.exe (PID: 6468)
INFO
Checks supported languages
- winstore.exe (PID: 6468)
- winstore.exe (PID: 6968)
- rufus.exe (PID: 7048)
- winstore.exe (PID: 3700)
- 7za.exe (PID: 5924)
- winstore.exe (PID: 2456)
Reads the computer name
- winstore.exe (PID: 6468)
- winstore.exe (PID: 6968)
- rufus.exe (PID: 7048)
- 7za.exe (PID: 5924)
- winstore.exe (PID: 3700)
- winstore.exe (PID: 2456)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6788)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 188)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6788)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 188)
Checks proxy server information
- winstore.exe (PID: 6968)
- winstore.exe (PID: 3700)
- winstore.exe (PID: 2456)
Reads the machine GUID from the registry
- winstore.exe (PID: 6968)
- rufus.exe (PID: 7048)
- winstore.exe (PID: 3700)
- winstore.exe (PID: 2456)
Reads the software policy settings
- winstore.exe (PID: 6968)
- winstore.exe (PID: 3700)
- winstore.exe (PID: 2456)
- winstore.exe (PID: 6468)
Creates files or folders in the user directory
- winstore.exe (PID: 6968)
- rufus.exe (PID: 7048)
- winstore.exe (PID: 3700)
- winstore.exe (PID: 2456)
Create files in a temporary directory
- winstore.exe (PID: 6968)
- rufus.exe (PID: 7048)
- winstore.exe (PID: 6468)
- winstore.exe (PID: 3700)
- winstore.exe (PID: 2456)
Process checks whether UAC notifications are on
- rufus.exe (PID: 7048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (46.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (41) |
| .exe | | | Win32 Executable (generic) (6.6) |
| .exe | | | Generic Win/DOS Executable (2.9) |
| .exe | | | DOS Executable Generic (2.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:07:08 05:25:42+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 10 |
| CodeSize: | 970752 |
| InitializedDataSize: | 9867264 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xda894 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.37.1 |
| ProductVersionNumber: | 1.1.37.1 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileVersion: | 1.1.37.01 |
| ProductVersion: | 1.1.37.01 |
Total processes
151
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | powershell Add-MpPreference -ExclusionPath ((gp 'HKCU:\Volatile Environment').WINSTORECMD) -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | winstore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Users\admin\AppData\Local\Temp\winstore.exe" /script * | C:\Users\admin\AppData\Local\Temp\winstore.exe | winstore.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.1.37.01 Modules
| |||||||||||||||
| 3700 | "C:\Users\admin\AppData\Local\Temp\winstore.exe" /script * | C:\Users\admin\AppData\Local\Temp\winstore.exe | winstore.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.1.37.01 Modules
| |||||||||||||||
| 5924 | "C:\Users\admin\AppData\Local\Temp\7za.exe" x "C:\Users\admin\AppData\Local\Temp\CS6.7z" "-oC:\Users\admin\AppData\Local\Temp\CS6" -y | C:\Users\admin\AppData\Local\Temp\7za.exe | — | winstore.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 2 Version: 24.01 Modules
| |||||||||||||||
| 6168 | powershell Add-MpPreference -ExclusionPath ((gp 'HKCU:\Volatile Environment').WINSTORECMD) -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | winstore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6420 | "C:\Users\admin\AppData\Local\Temp\winstore.exe" | C:\Users\admin\AppData\Local\Temp\winstore.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.1.37.01 Modules
| |||||||||||||||
| 6468 | "C:\Users\admin\AppData\Local\Temp\winstore.exe" | C:\Users\admin\AppData\Local\Temp\winstore.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.1.37.01 Modules
| |||||||||||||||
| 6496 | cmd | C:\Windows\System32\cmd.exe | — | winstore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | powershell Add-MpPreference -ExclusionPath ((gp 'HKCU:\Volatile Environment').WINSTORECMD) -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | winstore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 787
Read events
21 640
Write events
82
Delete events
65
Modification events
| (PID) Process: | (6468) winstore.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | WINSTORECMD |
Value: C:\Users\admin\AppData\Local\Temp\rufus.exe | |||
| (PID) Process: | (6968) winstore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6968) winstore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6968) winstore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6968) winstore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7048) rufus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{355C36EA-BA9D-47D0-BE81-C0A693DA151D}Machine\Software\Policies\Microsoft\AppHVSI |
| Operation: | write | Name: | AllowAppHVSI_ProviderSet |
Value: 0 | |||
| (PID) Process: | (7048) rufus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{355C36EA-BA9D-47D0-BE81-C0A693DA151D}Machine\Software\Policies\Microsoft\EdgeUpdate |
| Operation: | write | Name: | UpdateDefault |
Value: 0 | |||
| (PID) Process: | (7048) rufus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{355C36EA-BA9D-47D0-BE81-C0A693DA151D}Machine\Software\Policies\Microsoft\Windows\Network Connections |
| Operation: | write | Name: | NC_DoNotShowLocalOnlyIcon |
Value: 1 | |||
| (PID) Process: | (7048) rufus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{355C36EA-BA9D-47D0-BE81-C0A693DA151D}Machine\Software\Policies\Microsoft\Windows\Windows Feeds |
| Operation: | write | Name: | EnableFeeds |
Value: 0 | |||
| (PID) Process: | (7048) rufus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{355C36EA-BA9D-47D0-BE81-C0A693DA151D}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUServer |
Value: http://neverupdatewindows10.com | |||
Executable files
2
Suspicious files
12
Text files
12
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6788 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wi0gdonr.1fm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6968 | winstore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:FBA967F47E5D66E41664A7F37B892C27 | SHA256:82DF5555E9B9AA4C10DC72EBE71B48AC1BBF28BD913099993C6BF45BB1041B8A | |||
| 6788 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3r5qbkct.ntj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6968 | winstore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | der | |
MD5:777F2D601E4FA71219A4B30539032C8F | SHA256:7B4DE06CC253C21609D76B5077628ADD27BC0C6FAF45180A380F61204A5B88CF | |||
| 3700 | winstore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:84C077E8F652B2AC4FDE251F740F850F | SHA256:D1239B61C2C1B4B966604504AC78D6E1AF0D4A943212BBB277339E0F69ABFED7 | |||
| 6968 | winstore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:70D11C3DDE35A9B48B4B4ACA05552F85 | SHA256:1A1697A5AD6D7B8FC9E839F7290D5FBD8A40632DA5FF9F1C28FBABDDDB2BD011 | |||
| 6968 | winstore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A66A8DB907BADC9D16AD67B2FBFFDD5C | binary | |
MD5:BB3D5E0CAEED1BFE218C60CDF8A19B7B | SHA256:918F31BF7849DC5A3C31AFF72F10047BAFF3C2ECD84094EAFEC9460D43B1C91E | |||
| 6968 | winstore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | der | |
MD5:979E41B6E144BDB24D4A4B0EFD2A23F9 | SHA256:ABEAD8E00E65D83F7C5055F34EC15C29A478648975E416536446447E46DA01B5 | |||
| 6968 | winstore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:EF27E11995C0AE9D67BBCB82582B23A5 | SHA256:D33B2483D6121B812955AF02C75B7D39E8C6595B237C32B1427C3D5CAA847A01 | |||
| 6468 | winstore.exe | C:\Users\admin\AppData\Local\Temp\rufus.exe | executable | |
MD5:F426E7265FC92E91F77C0E0106262DA0 | SHA256:2100534F2014275090C3133EB648DCDBE878C5A05FC1377F0483755119E7BB33 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
53
DNS requests
27
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6968 | winstore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
6968 | winstore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
6968 | winstore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
6968 | winstore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEE4o94a2bBo7lCzSxA63QqU%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6940 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6820 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3700 | winstore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4936 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4936 | svchost.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
6468 | winstore.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
6468 | winstore.exe | 185.199.111.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
6968 | winstore.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
objects.githubusercontent.com |
| shared |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6468 | winstore.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
2456 | winstore.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
Process | Message |
|---|---|
rufus.exe | *** Rufus init ***
|
rufus.exe | Cur dir: 'C:\Users\admin\AppData\Local\Temp\'
|
rufus.exe | App dir: 'C:\Users\admin\AppData\Local\Temp\'
|
rufus.exe | Sys dir: 'C:\WINDOWS\system32'
|
rufus.exe | Usr dir: 'C:\Users\admin'
|
rufus.exe | Dat dir: 'C:\Users\admin\AppData\Local'
|
rufus.exe | Tmp dir: 'C:\Users\admin\AppData\Local\Temp\'
|
rufus.exe | Binary executable is signed by 'Akeo Consulting'
|
rufus.exe | Will use settings from registry
|
rufus.exe | loc file not found in current directory - embedded one will be used
|