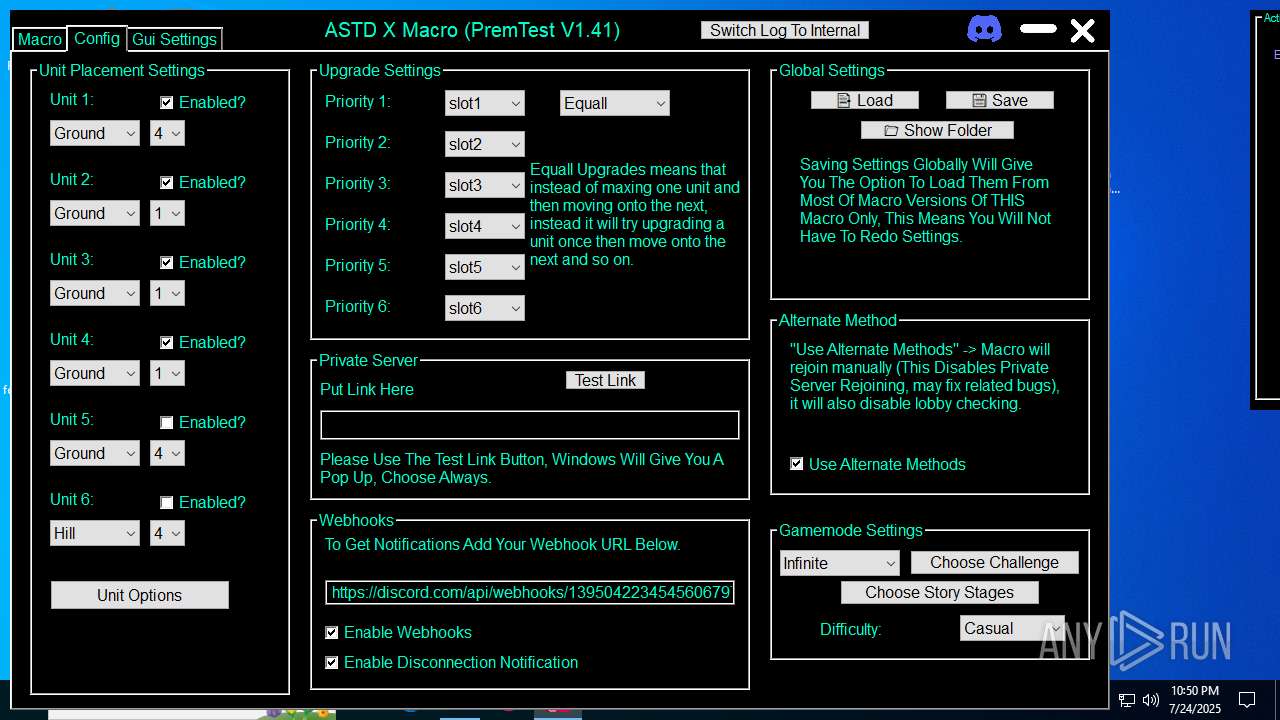
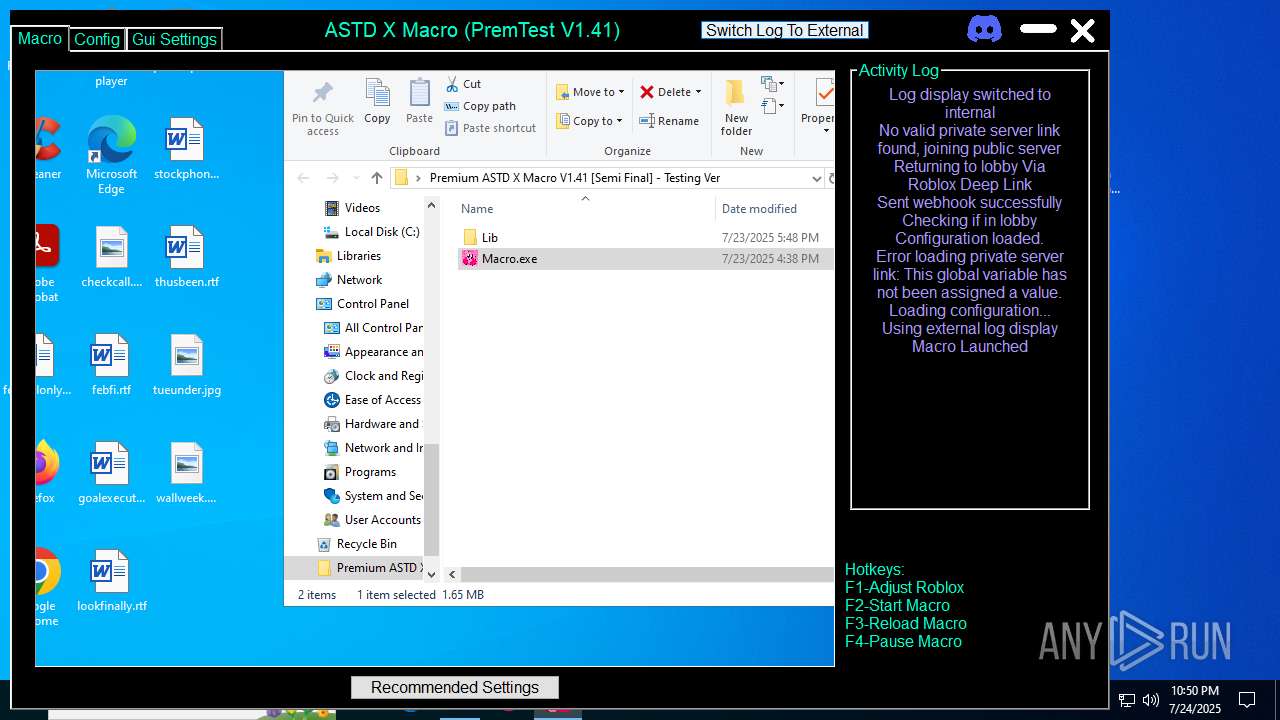
| File name: | Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver.rar |
| Full analysis: | https://app.any.run/tasks/d2641c86-9bcb-4069-96bb-b4d202262607 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2025, 22:49:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A9F153246F1549ED7225F340C615ADCE |
| SHA1: | C698B667DC74A06A6B57573702C4BB6C272E242E |
| SHA256: | F59557BC9E9E85E28DEA49B7985C97FCB689BA2B021489B89BDD8F04727955EF |
| SSDEEP: | 49152:VUitPmpeGKoDvNWz6YlGgwqWhgGteN3h4Suk4JeQSjzc8xh1Z9upRJGk8mhr/WDq:VD9m7566ZNRm40zjzc8xbPupfGk8or8q |
MALICIOUS
No malicious indicators.SUSPICIOUS
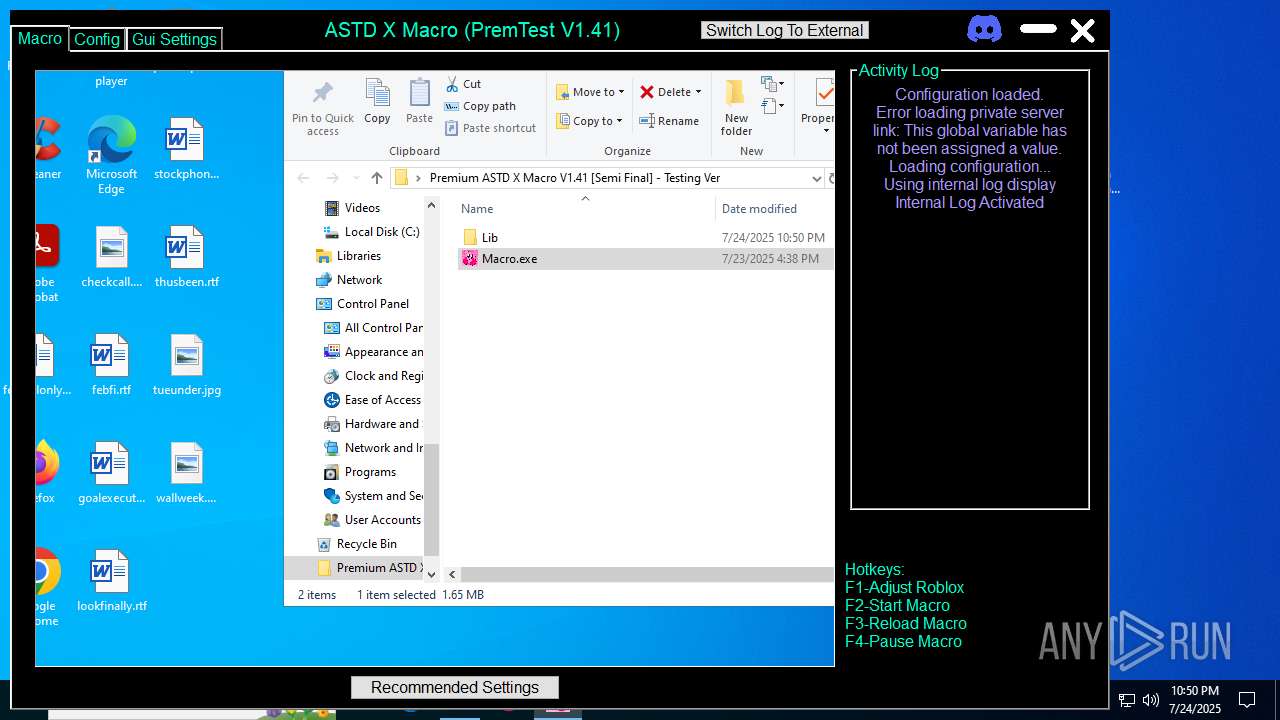
Reads security settings of Internet Explorer
- Macro.exe (PID: 4884)
Application launched itself
- Macro.exe (PID: 4884)
Possible usage of Discord/Telegram API has been detected (YARA)
- Macro.exe (PID: 2168)
There is functionality for taking screenshot (YARA)
- Macro.exe (PID: 2168)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 2804)
Checks supported languages
- Macro.exe (PID: 4884)
- Macro.exe (PID: 2168)
Manual execution by a user
- Macro.exe (PID: 4884)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2804)
Reads the computer name
- Macro.exe (PID: 4884)
- Macro.exe (PID: 2168)
Reads the software policy settings
- Macro.exe (PID: 4884)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 4024)
Detects AutoHotkey samples (YARA)
- Macro.exe (PID: 2168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(2168) Macro.exe
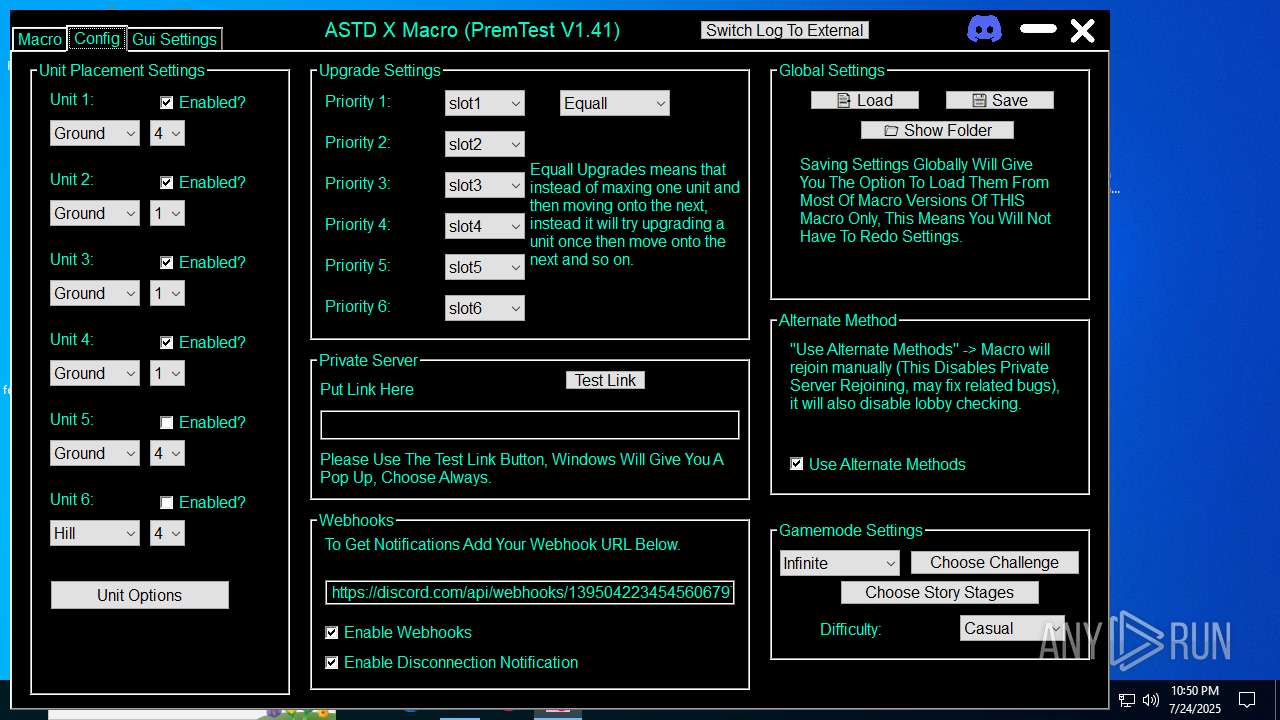
Discord-Webhook-Tokens (1)1395042234545606797/QKds1NckA9fbn1lq6Ul2ns6Y7AXuNwX930WY3_Pny9OmaJ0EyNyGNQmTES9LbabJNV5I
Discord-Info-Links
1395042234545606797/QKds1NckA9fbn1lq6Ul2ns6Y7AXuNwX930WY3_Pny9OmaJ0EyNyGNQmTES9LbabJNV5I
Get Webhook Infohttps://discord.com/api/webhooks/1395042234545606797/QKds1NckA9fbn1lq6Ul2ns6Y7AXuNwX930WY3_Pny9OmaJ0EyNyGNQmTES9LbabJNV5I
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 522 |
| UncompressedSize: | 983 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver/Lib/AHKv2-Gdip-master/CHANGE.log |
Total processes
139
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\Desktop\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Macro.exe" /restart /script "*#1" | C:\Users\admin\Desktop\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Macro.exe | Macro.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 2.0.18 Modules
ims-api(PID) Process(2168) Macro.exe Discord-Webhook-Tokens (1)1395042234545606797/QKds1NckA9fbn1lq6Ul2ns6Y7AXuNwX930WY3_Pny9OmaJ0EyNyGNQmTES9LbabJNV5I Discord-Info-Links 1395042234545606797/QKds1NckA9fbn1lq6Ul2ns6Y7AXuNwX930WY3_Pny9OmaJ0EyNyGNQmTES9LbabJNV5I Get Webhook Infohttps://discord.com/api/webhooks/1395042234545606797/QKds1NckA9fbn1lq6Ul2ns6Y7AXuNwX930WY3_Pny9OmaJ0EyNyGNQmTES9LbabJNV5I | |||||||||||||||
| 2804 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3756 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4884 | "C:\Users\admin\Desktop\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Macro.exe" | C:\Users\admin\Desktop\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Macro.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 2.0.18 Modules
| |||||||||||||||
Total events
6 619
Read events
6 592
Write events
27
Delete events
0
Modification events
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver.rar | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
0
Text files
45
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\gui.ahk | text | |
MD5:6336E874B1ADCD243F6A910A4A0A73D3 | SHA256:74F2DC7AF9CA2936E467625DEF6D884CBE4086D889E365265E37CF9C00EBE072 | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\Discord-Webhook-master\WEBHOOK.ahk | text | |
MD5:8B31209C7619C3E51B8036FADBDF0EA4 | SHA256:776577142ED76382B0C6D34727110E82A7A0EB7938742D70B3FE84CBC6E2235A | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\AHKv2-Gdip-master\CHANGE.log | text | |
MD5:F680FD332B2CE2006072CAE1B5ADE25F | SHA256:551EAAE393B4E31DFAC9BE546BE9BD169CBCA61F77BCB8FF47E65808CBFBD118 | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\AHKv2-Gdip-master\Gdip_Toolbox-usage_example.ahk | text | |
MD5:BEC0EAEF8BCC7D200CB5E6697BAD5E8E | SHA256:875961D6EE081855B941D66077EBD4B90343FA88589DCEDA57854BFFDCDA3E01 | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\AHKv2-Gdip-master\Gdip_All.ahk | text | |
MD5:1FC1EFABFA357888B63471FE11B4E6F1 | SHA256:184F9A5BF73E7BADD2519D1AAACA63A74436607BF48EFB2B098A5B21E5C87BDD | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\Discord-Webhook-master\resources\EmbedBuilder.ahk | text | |
MD5:B61FEF0304C96F04E0168001342AF528 | SHA256:154507EEADF7AE44C6CF36034FBDF4609A08728D37A9754F9336988C0360E46B | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\GlobalConfig.ahk | text | |
MD5:5288E40C302DF9D3D471B3B3B98ADFC2 | SHA256:FF3198BB17878E611FE691CC41B3534EC1972130FDE92F782EAE4EA3BE30C7CE | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\Discord-Webhook-master\resources\AttachmentBuilder.ahk | text | |
MD5:AA3351D73F5E748F391C5D366D6DAFF3 | SHA256:2292E1D3CA917F2E3F822CD22737501502F7821BF274BCA7985B6ADC140FCDA8 | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\Discord-Webhook-master\resources\JSON.ahk | text | |
MD5:3D5E99D8DE13C26FBC9F32AA5587A4FF | SHA256:A854BC0A22DA1008790E564EFB20EA34C07C2D6FB03BFE342A662B23A11AE4E3 | |||
| 2804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2804.20220\Premium ASTD X Macro V1.41 [Semi Final] - Testing Ver\Lib\Discord-Webhook-master\resources\FormData.ahk | text | |
MD5:079B14E54BA21A8772969EC124A844BE | SHA256:59FAE0A3F10E0CFBFA3F56105C67E92D0CB70279691F28D4F45F2D2810899386 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
17
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
504 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5992 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5992 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
472 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
504 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
discord.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2200 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
4884 | Macro.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
4884 | Macro.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
2200 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
— | — | Misc activity | ET HUNTING Discord WebHook Activity M2 (Contains Key, embeds) |
— | — | Misc activity | ET USER_AGENTS Discord Bot User-Agent Observed (DiscordBot) |