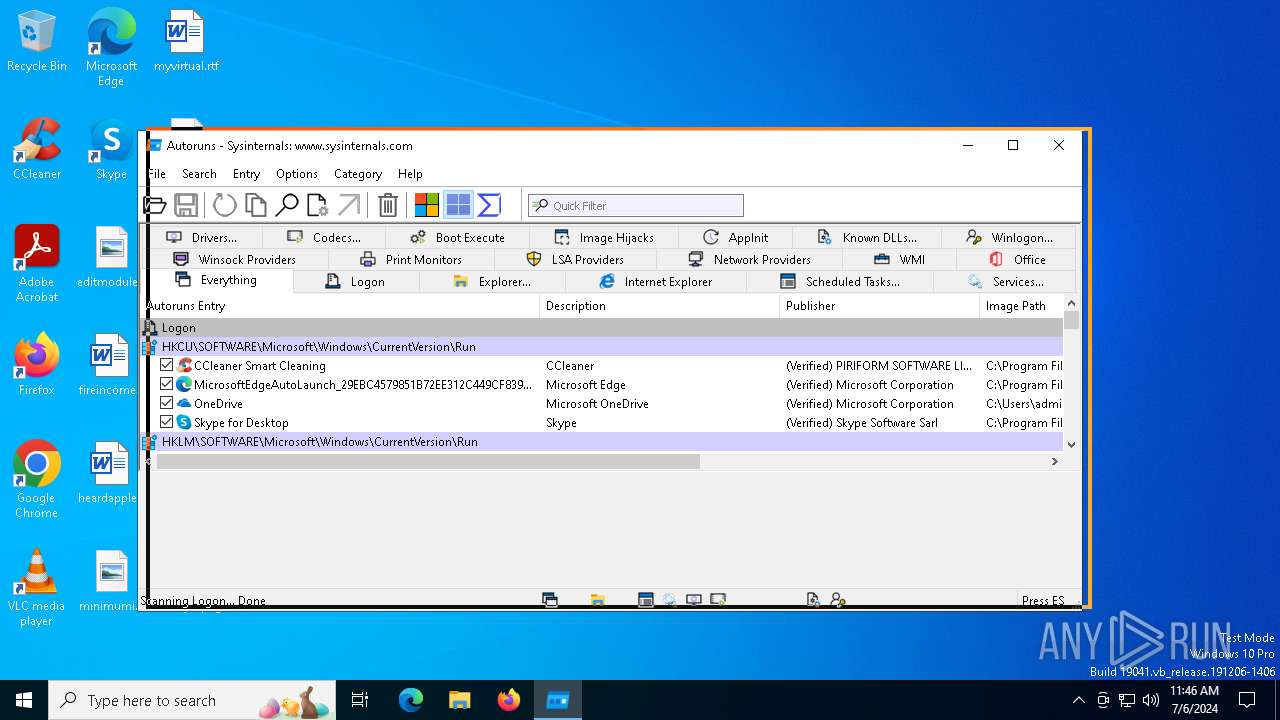
| File name: | Autoruns64.exe |
| Full analysis: | https://app.any.run/tasks/0ec400a7-d7dc-4b63-99fd-51059cc160cd |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2024, 11:45:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 6AE8E963B33EE52DF761412B451B2962 |
| SHA1: | F7AB1987848A91AF2C77A72583211DCADEED420A |
| SHA256: | F59056339DE56820E57C961D6DDD9032BD78AF9F2333797944F4EE57B77EE2CA |
| SSDEEP: | 24576:qU8EqexVDmS0d1ARkxDRlzmYj0tYC/5JReKq1QMcXEkb9fzTXJe:qHEqexVDmSOxxDI5JRhMIFT4 |
MALICIOUS
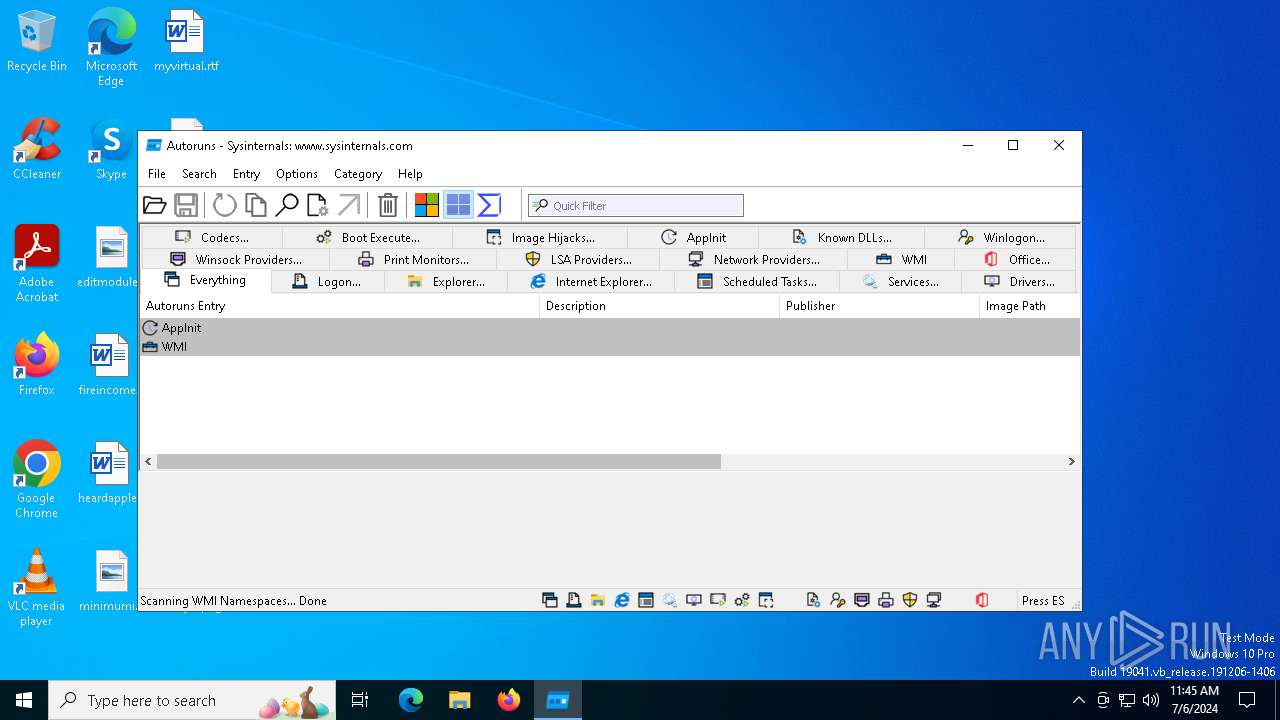
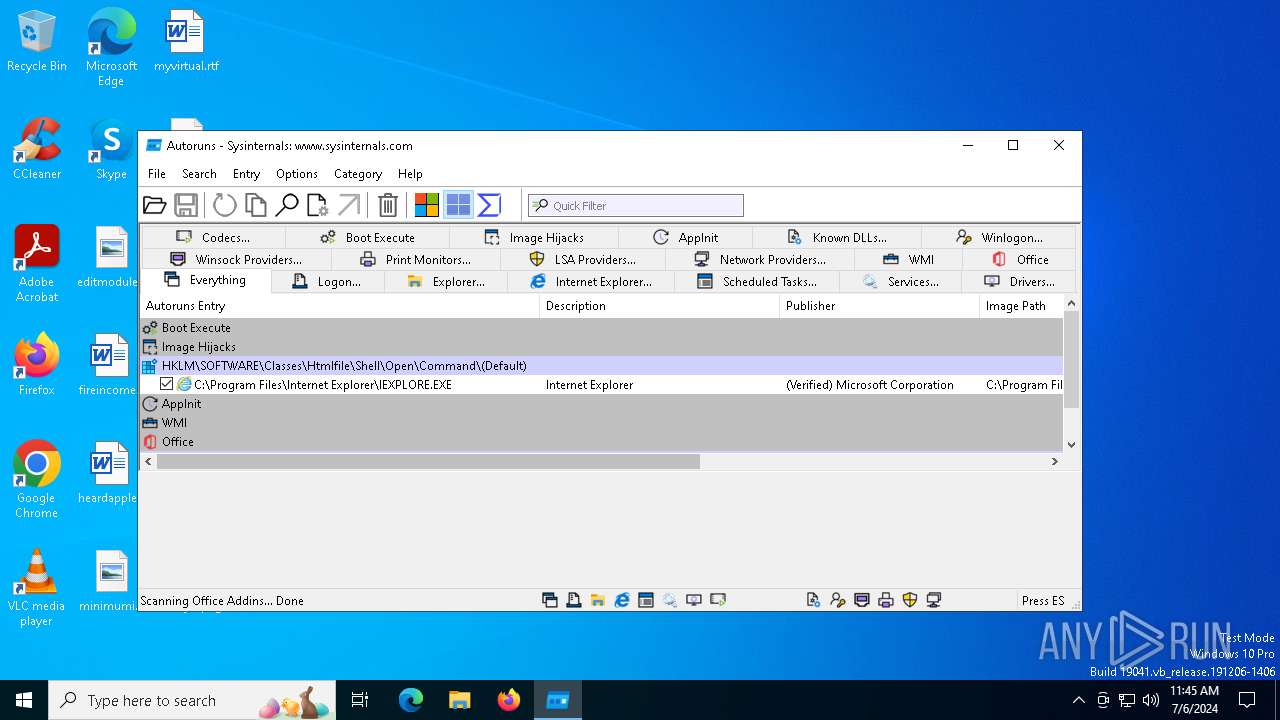
Drops the executable file immediately after the start
- Autoruns64.exe (PID: 3972)
SUSPICIOUS
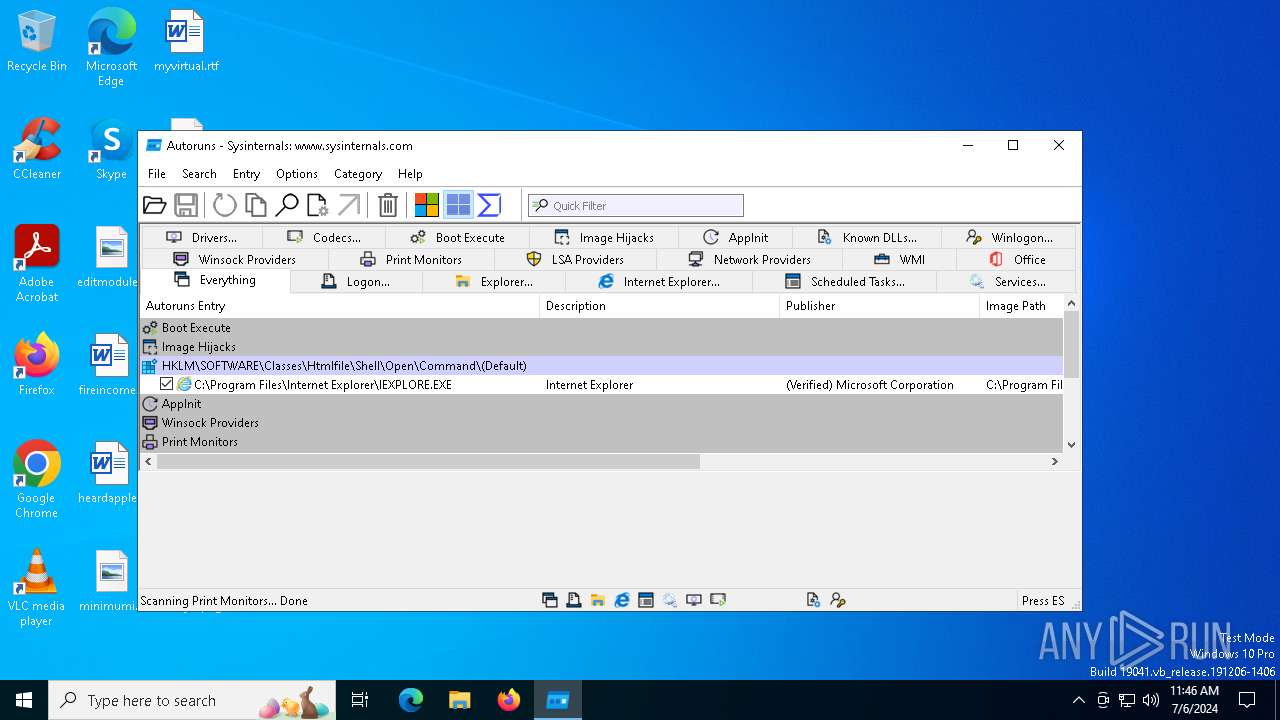
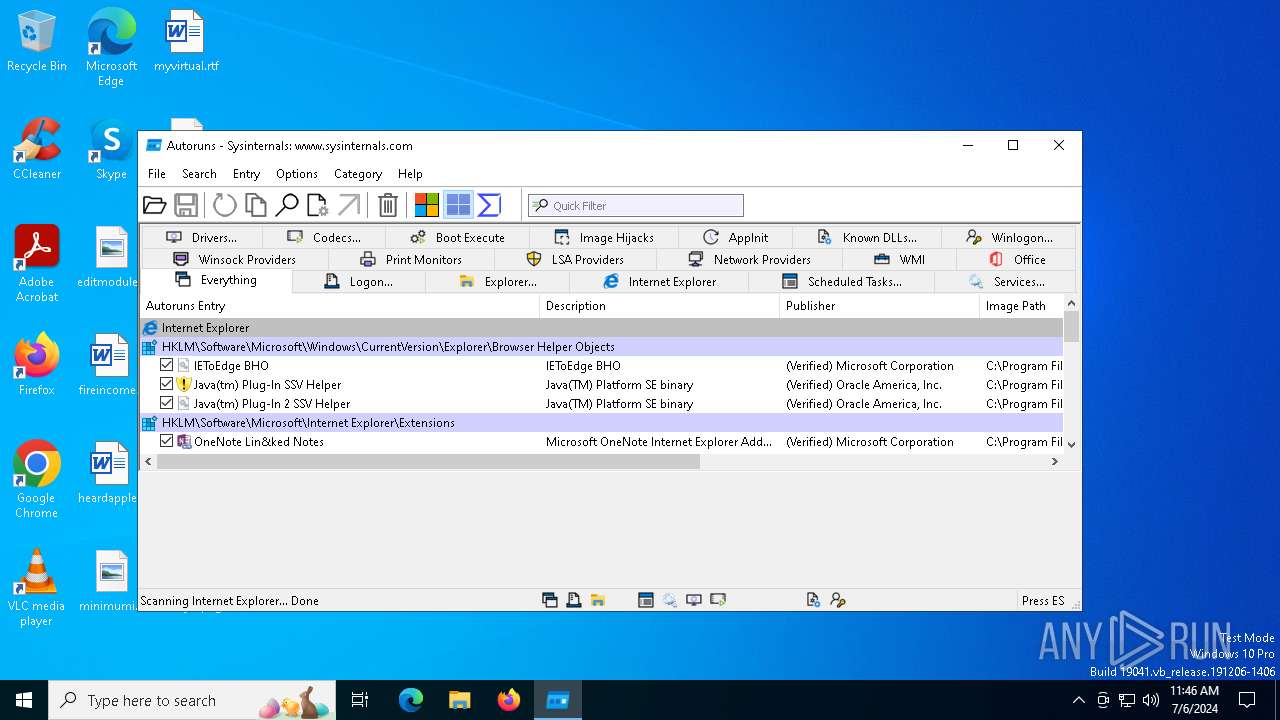
Reads security settings of Internet Explorer
- Autoruns64.exe (PID: 3972)
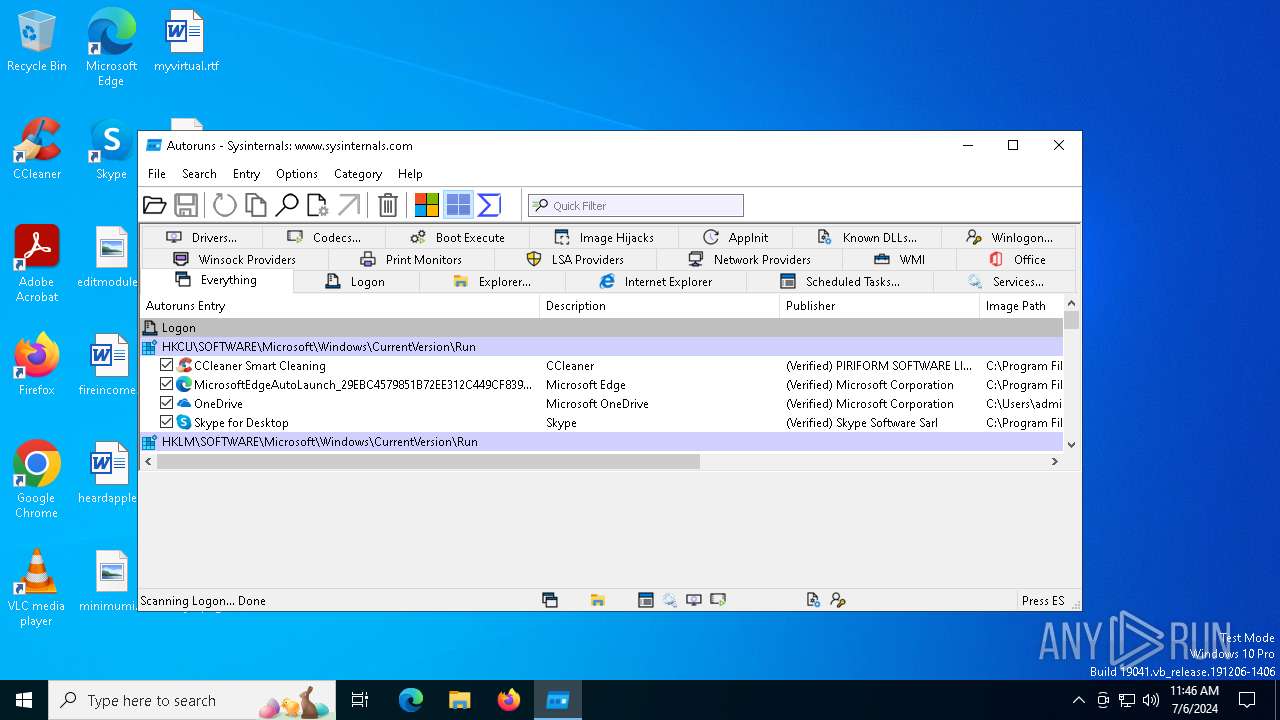
Read startup parameters
- Autoruns64.exe (PID: 3972)
Checks Windows Trust Settings
- Autoruns64.exe (PID: 3972)
INFO
Checks supported languages
- Autoruns64.exe (PID: 3972)
Reads product name
- Autoruns64.exe (PID: 3972)
Reads Environment values
- Autoruns64.exe (PID: 3972)
Reads the machine GUID from the registry
- Autoruns64.exe (PID: 3972)
Checks proxy server information
- Autoruns64.exe (PID: 3972)
Reads the computer name
- Autoruns64.exe (PID: 3972)
Creates files or folders in the user directory
- Autoruns64.exe (PID: 3972)
Reads Microsoft Office registry keys
- Autoruns64.exe (PID: 3972)
Reads the software policy settings
- Autoruns64.exe (PID: 3972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:06:27 08:46:43+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.36 |
| CodeSize: | 865280 |
| InitializedDataSize: | 1178624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9cd64 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 14.10.0.0 |
| ProductVersionNumber: | 14.10.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Autostart program viewer |
| FileVersion: | 14.1 |
| InternalName: | Sysinternals Autoruns |
| LegalCopyright: | Copyright (C) 2002-2023 Mark Russinovich |
| OriginalFileName: | autoruns.exe |
| ProductName: | Sysinternals autoruns |
| ProductVersion: | 14.1 |
Total processes
141
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3972 | "C:\Users\admin\AppData\Local\Temp\Autoruns64.exe" | C:\Users\admin\AppData\Local\Temp\Autoruns64.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Version: 14.10 Modules
| |||||||||||||||
| 6724 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6756 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
42 688
Read events
42 634
Write events
54
Delete events
0
Modification events
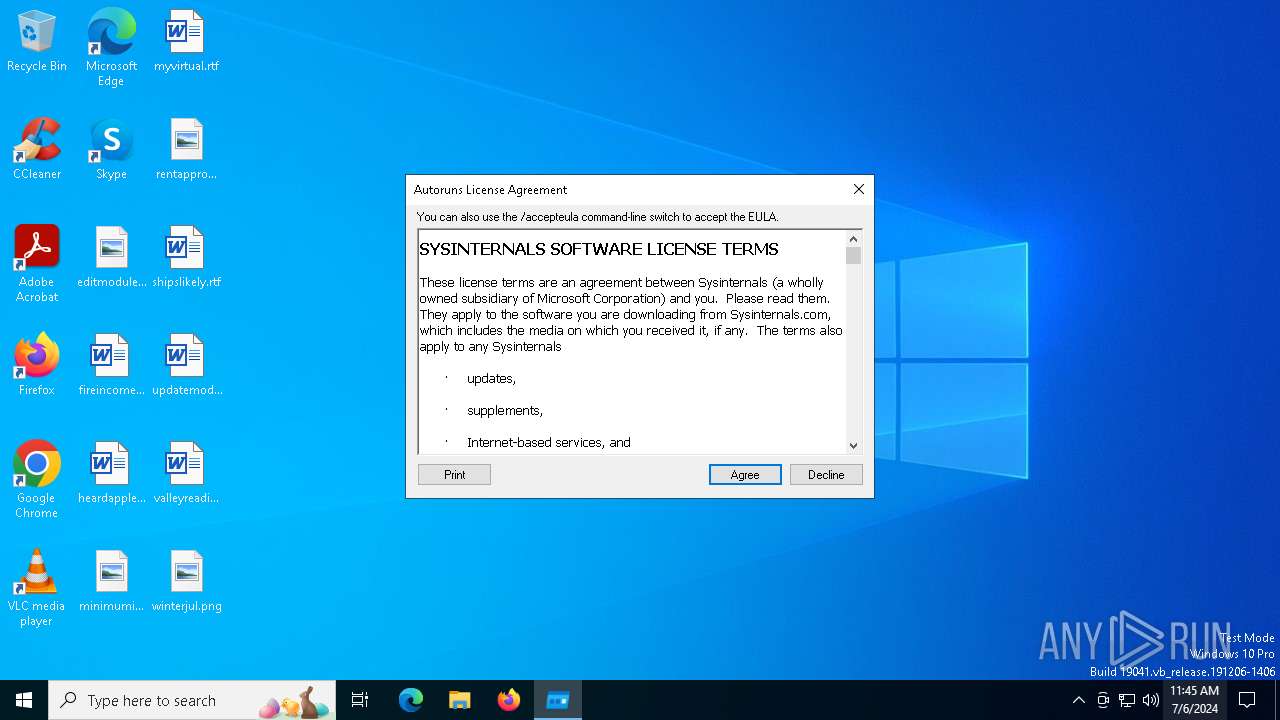
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Autoruns |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60100 |
Value: MSAFD Tcpip [TCP/IP] | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60101 |
Value: MSAFD Tcpip [UDP/IP] | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60102 |
Value: MSAFD Tcpip [RAW/IP] | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60200 |
Value: MSAFD Tcpip [TCP/IPv6] | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60201 |
Value: MSAFD Tcpip [UDP/IPv6] | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60202 |
Value: MSAFD Tcpip [RAW/IPv6] | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshqos.dll,-100 |
Value: RSVP TCPv6 Service Provider | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshqos.dll,-101 |
Value: RSVP TCP Service Provider | |||
| (PID) Process: | (3972) Autoruns64.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshqos.dll,-102 |
Value: RSVP UDPv6 Service Provider | |||
Executable files
0
Suspicious files
52
Text files
0
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | der | |
MD5:A20961D8BD1A5A7D241026D0011751FB | SHA256:4D6AE5BBEF0EACFDC09D5ADE4D145E883CF41B131E4C6988738769F1D32E12F3 | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\45AE547469FB7137480E06153457A2DD | binary | |
MD5:7A2FBA626E15C82E7839DCD0B943B2C5 | SHA256:DBC7B9DE360F49125435F73DBBECDC9950D810CC7F640605F86920119C8D77D5 | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4C7F163ED126D5C3CB9457F68EC64E9E | der | |
MD5:92EAB03C771E2873C170D7835E98FC93 | SHA256:B13036F0FEC353CDBF9B73F2B7C28B1AFD3331DF5D5E12A4A9EA592B3B4353C6 | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:9387B60E18F20471336B2D1D428365C7 | SHA256:F819A04690ADC1755A41DF4A55426ACE62FA174D64500F65A6F7A633A05A6ACB | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | der | |
MD5:3582D5284FE8B34513E337C07AE9B8F8 | SHA256:686C5D8F56C9BC20D444B6F3A32D78C249B94F10080F1B595CC8F856A62B65A6 | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\45AE547469FB7137480E06153457A2DD | der | |
MD5:6B769DB3020C81D2E526159023B9859E | SHA256:1E929D06F06A034171AB4F6C015C97C8927E5FB43C6DA2FDE645AD16CAE7CDEF | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:89632B0F5491F2A32BC05F3A26F8AAE1 | SHA256:3471C469B7C580E96A3C11AB2FE36B2E1D512BB87CC2407C7D99B45E4FD44DEB | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C0018BB1B5834735BFA60CD063B31956 | der | |
MD5:FC1193C6345AC35188AA3DE0F824CEB7 | SHA256:BDFB8FAFF4C0C0A15C642890A5544BD32F930F55CA199470DBD4736A32D6E200 | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0B8A20E1F3F4D73D52A19929F922C892 | der | |
MD5:09E5AA2B1903859E6FA248FC0EE3B3B4 | SHA256:A963DA4FCDC475B2B367819A3F54002864E22BEF83C1D5BCEACB2A9B66B69F65 | |||
| 3972 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:CBA2426F2AAFE31899569ACE05E89796 | SHA256:A465FEBE8A024E3CDB548A3731B2EA60C7B2919E941A24B9A42890B2B039B85A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
75
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3972 | Autoruns64.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2140 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1828 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3944 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3944 | svchost.exe | 192.229.221.95:80 | crl.verisign.com | EDGECAST | US | whitelisted |
1928 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 52.111.243.30:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3972 | Autoruns64.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.verisign.com |
| whitelisted |
ocsp.verisign.com |
| whitelisted |
csc3-2004-crl.verisign.com |
| unknown |