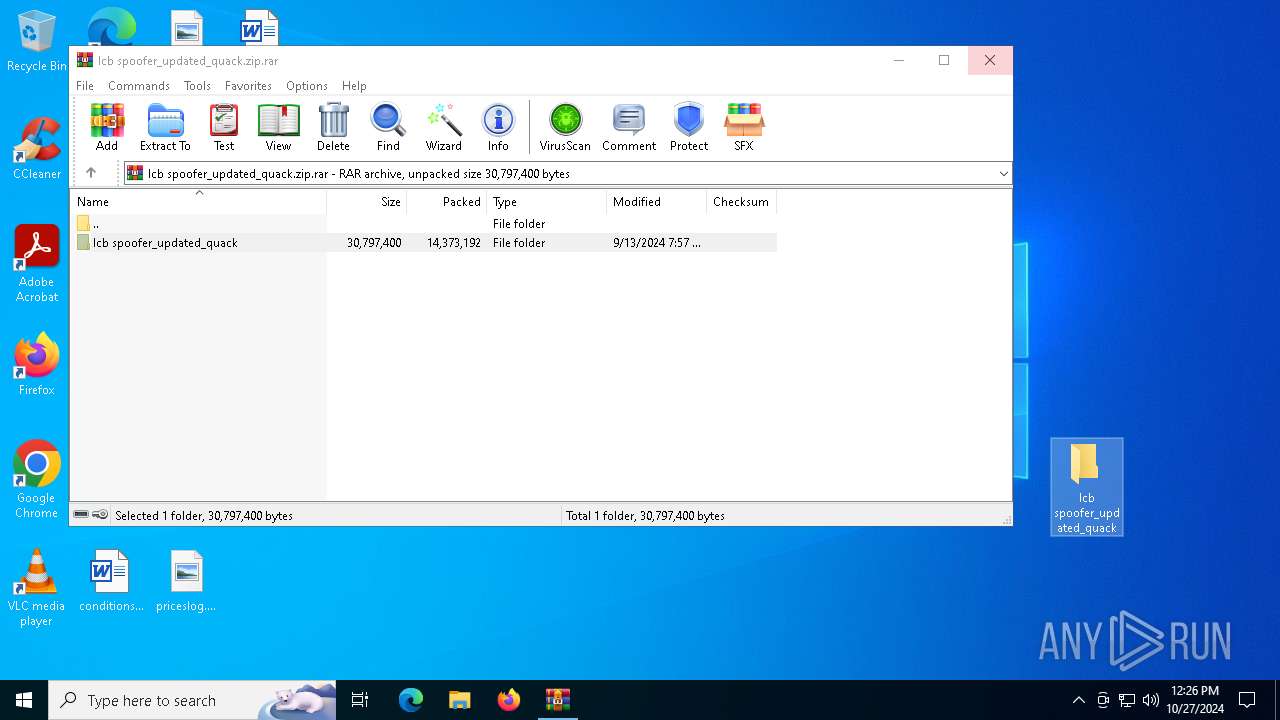
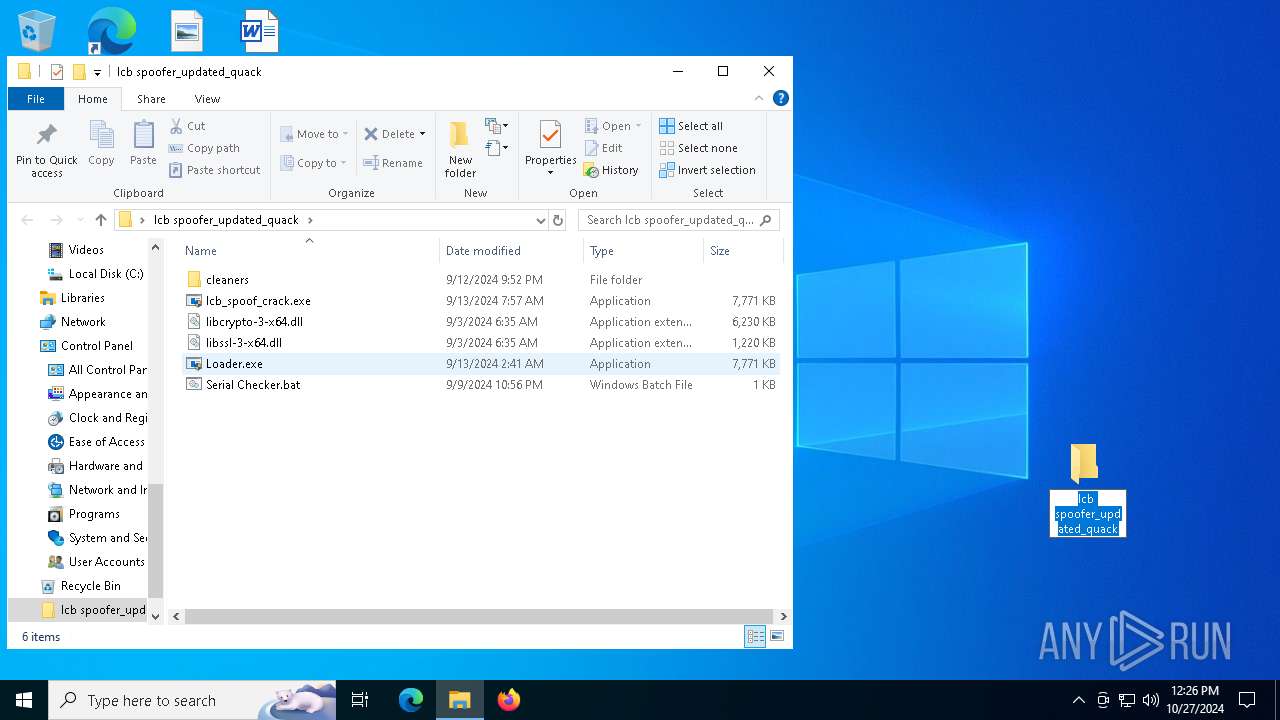
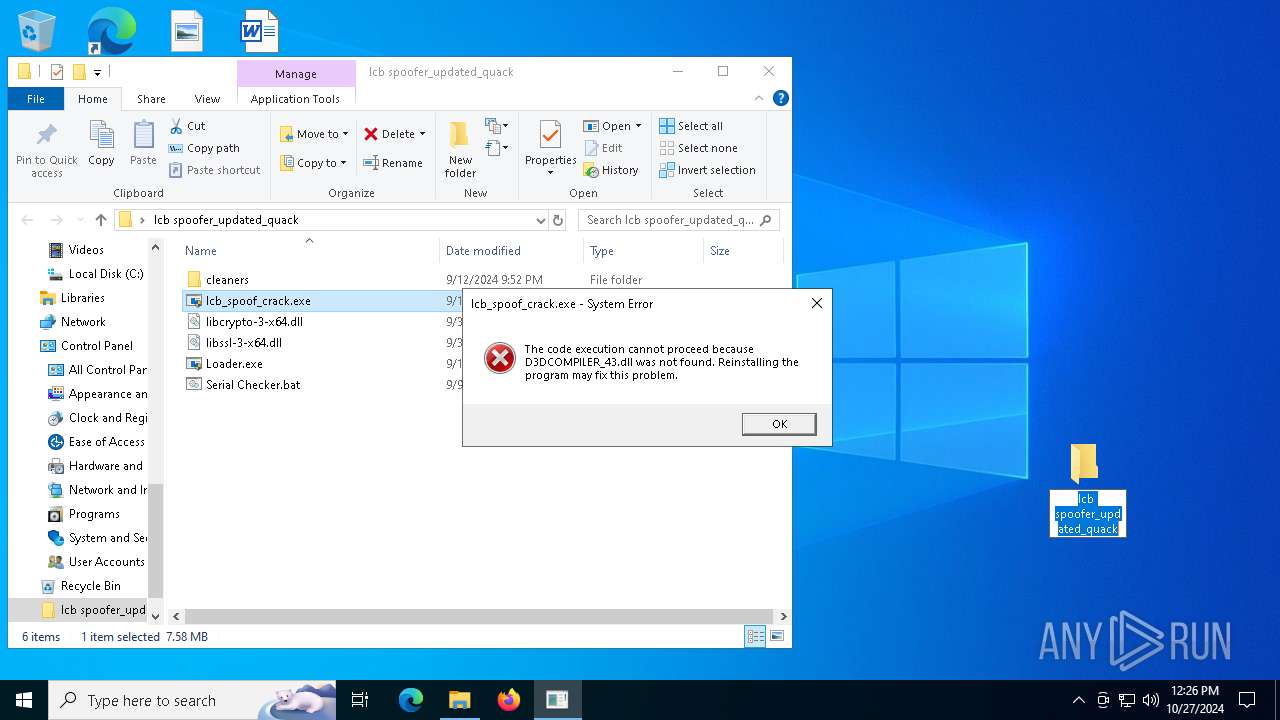
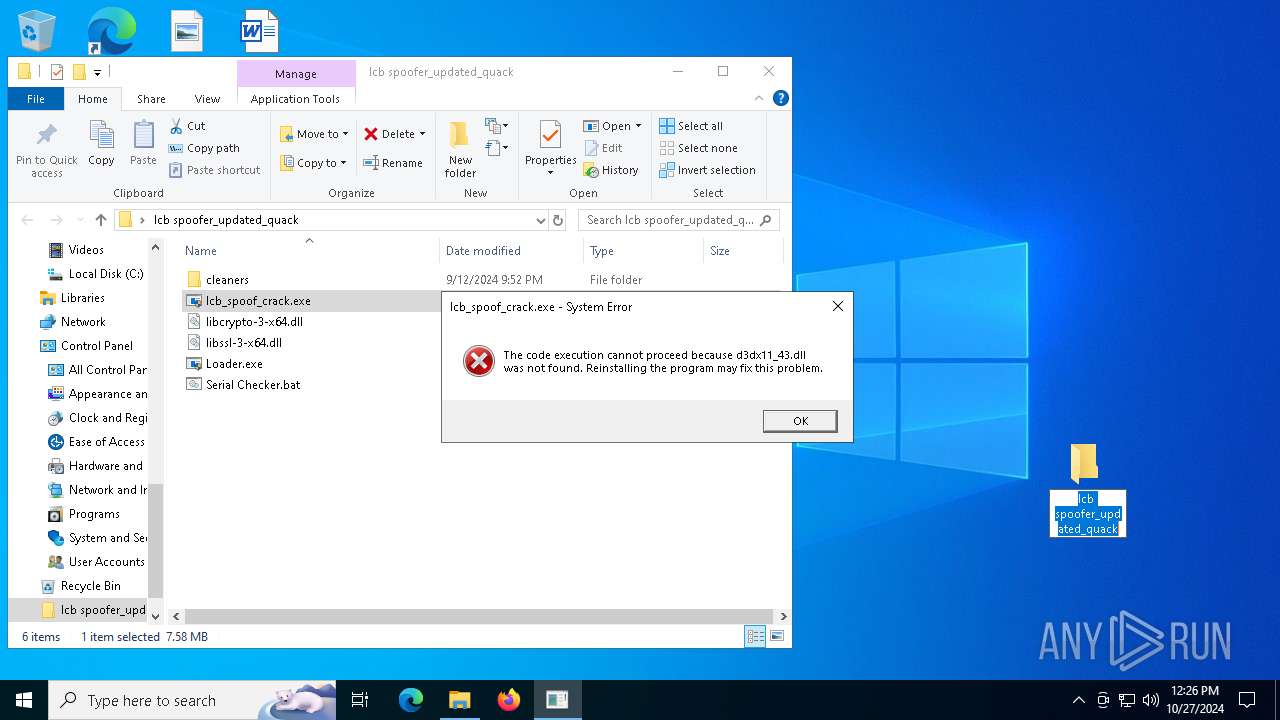
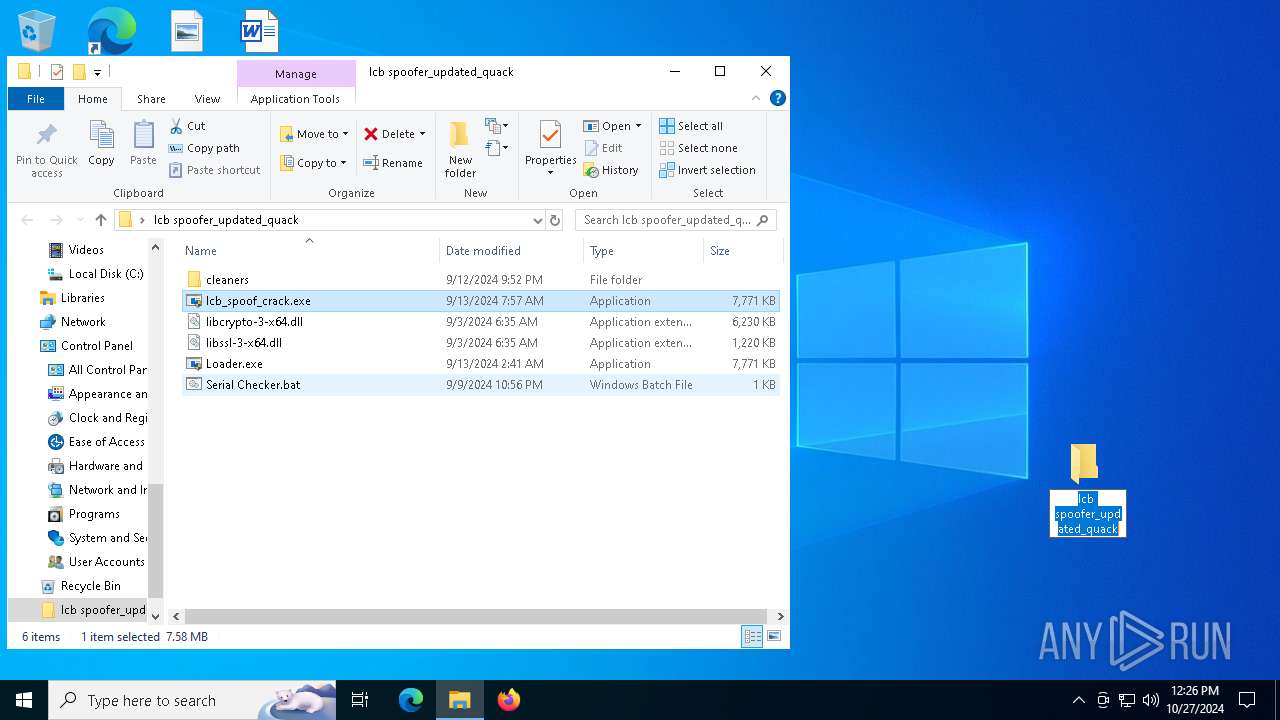
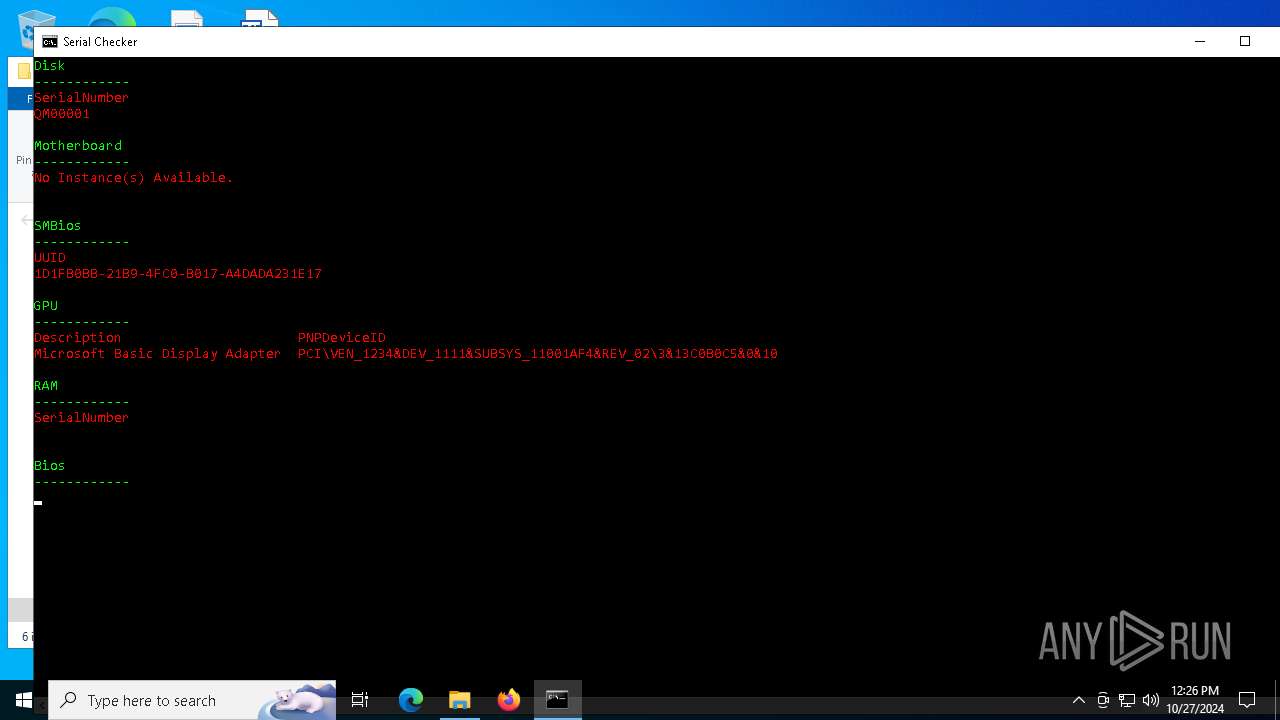
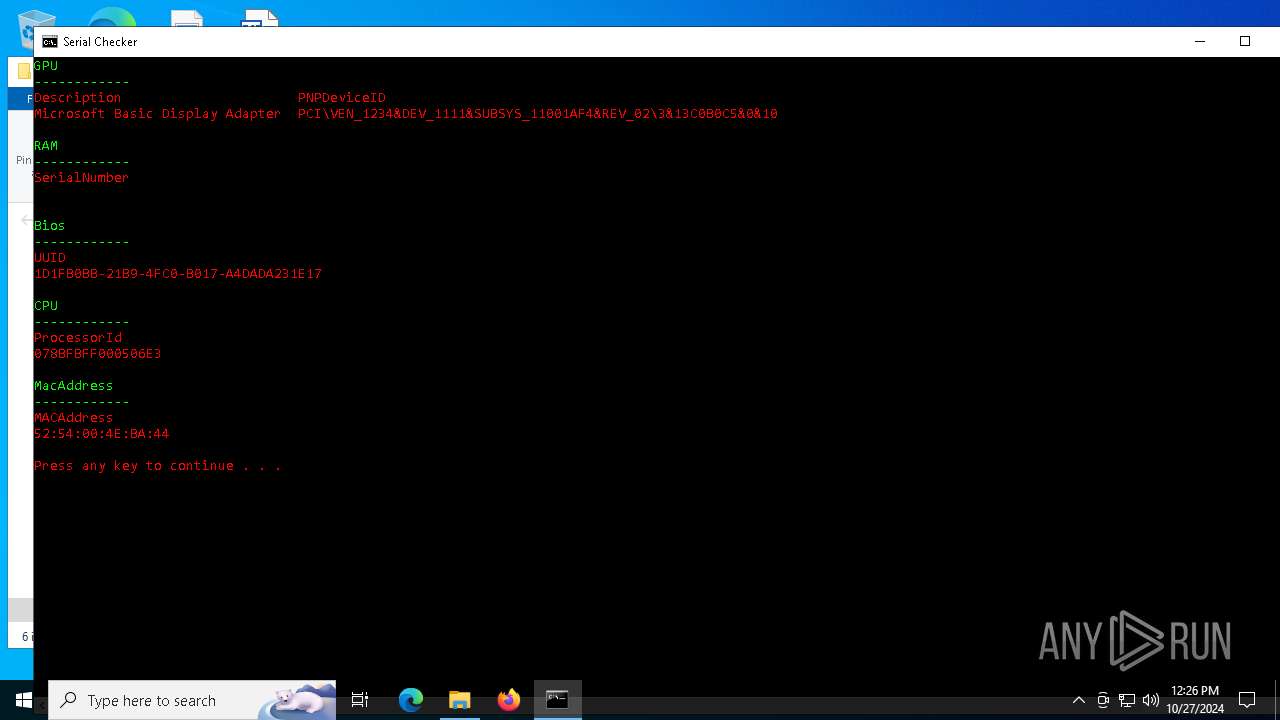
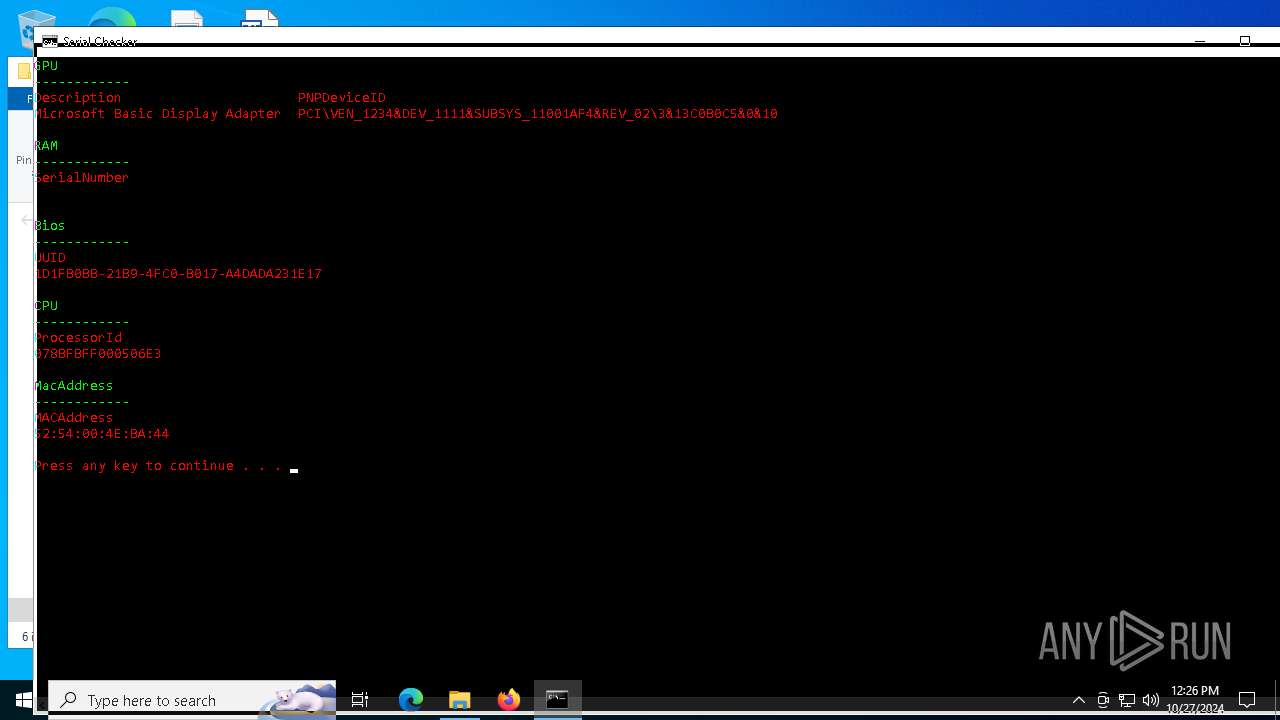
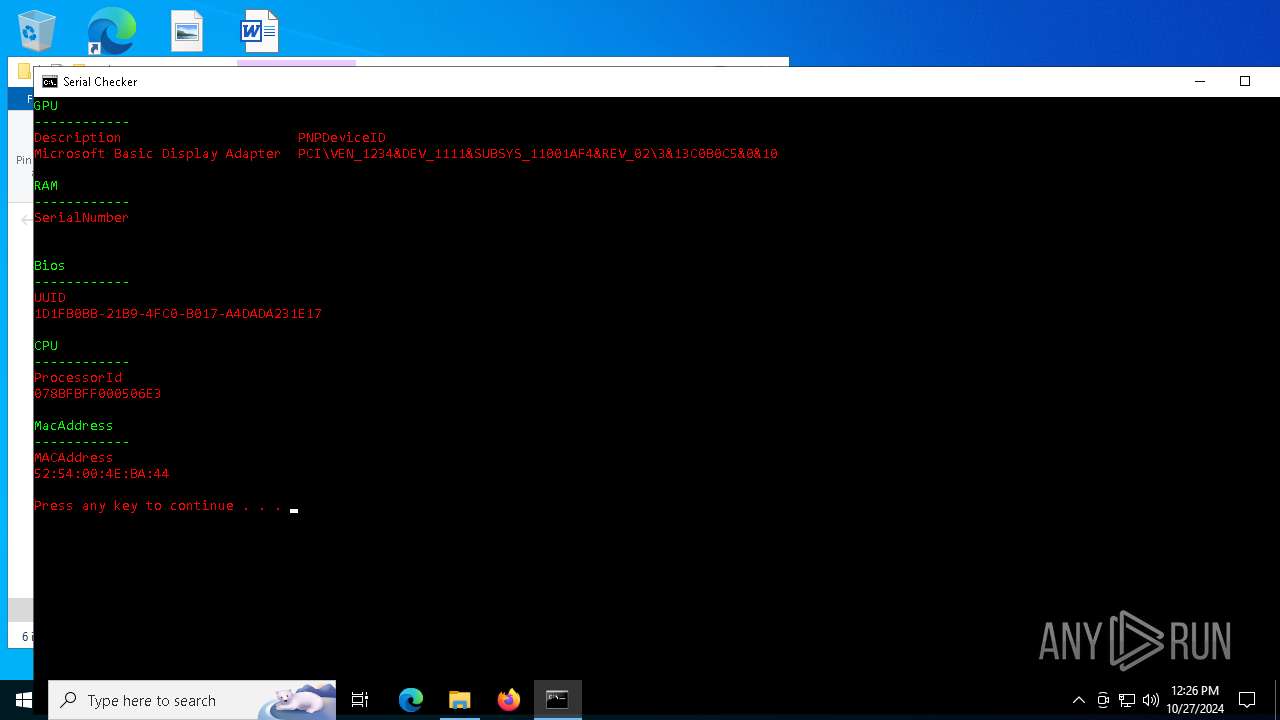
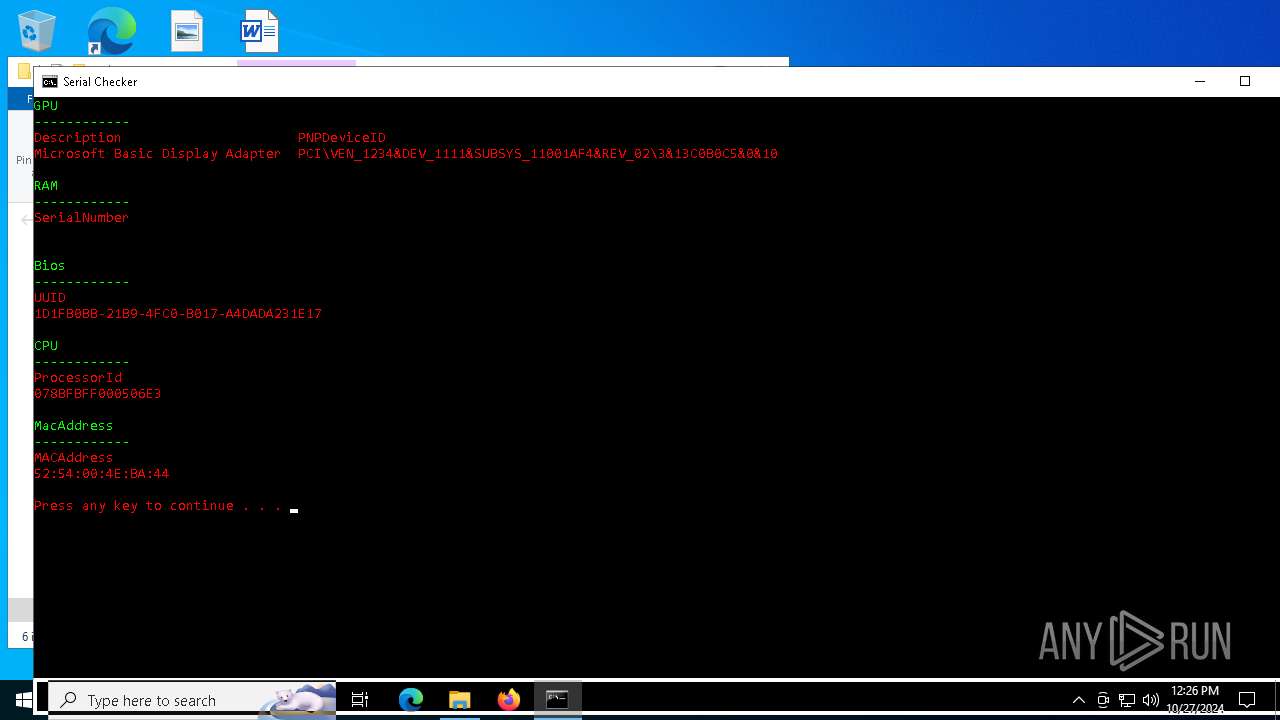
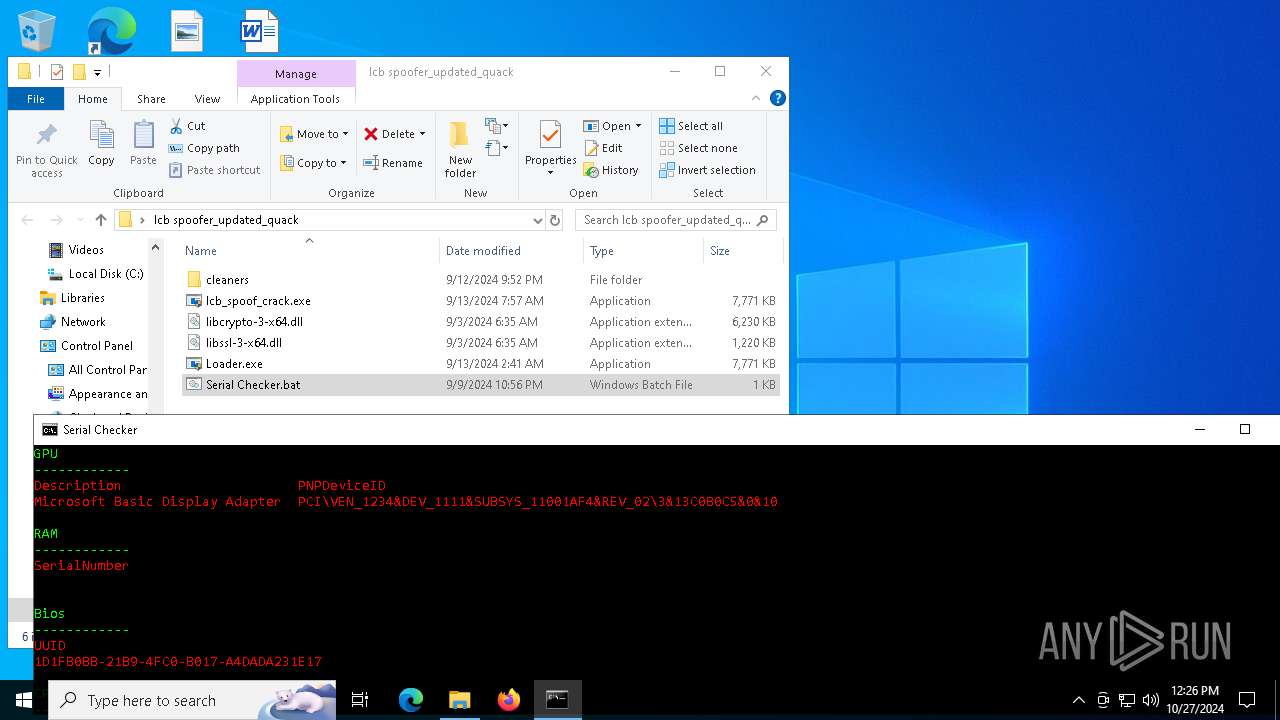
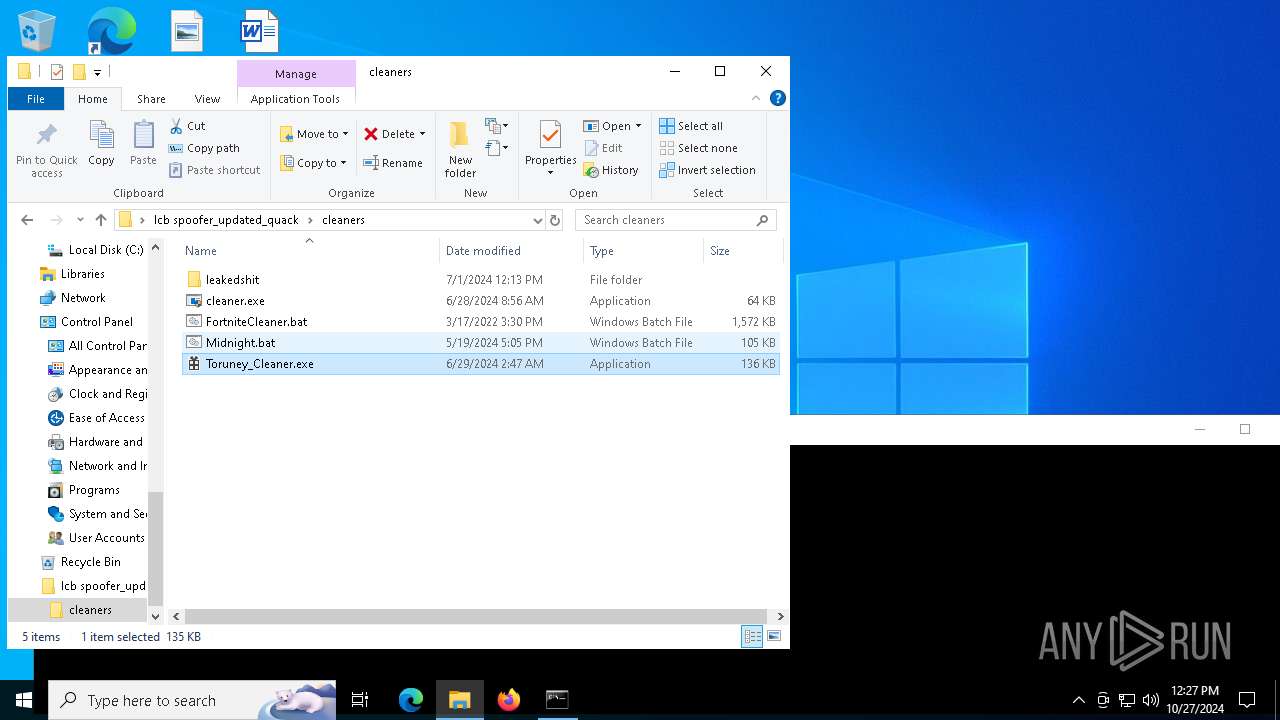
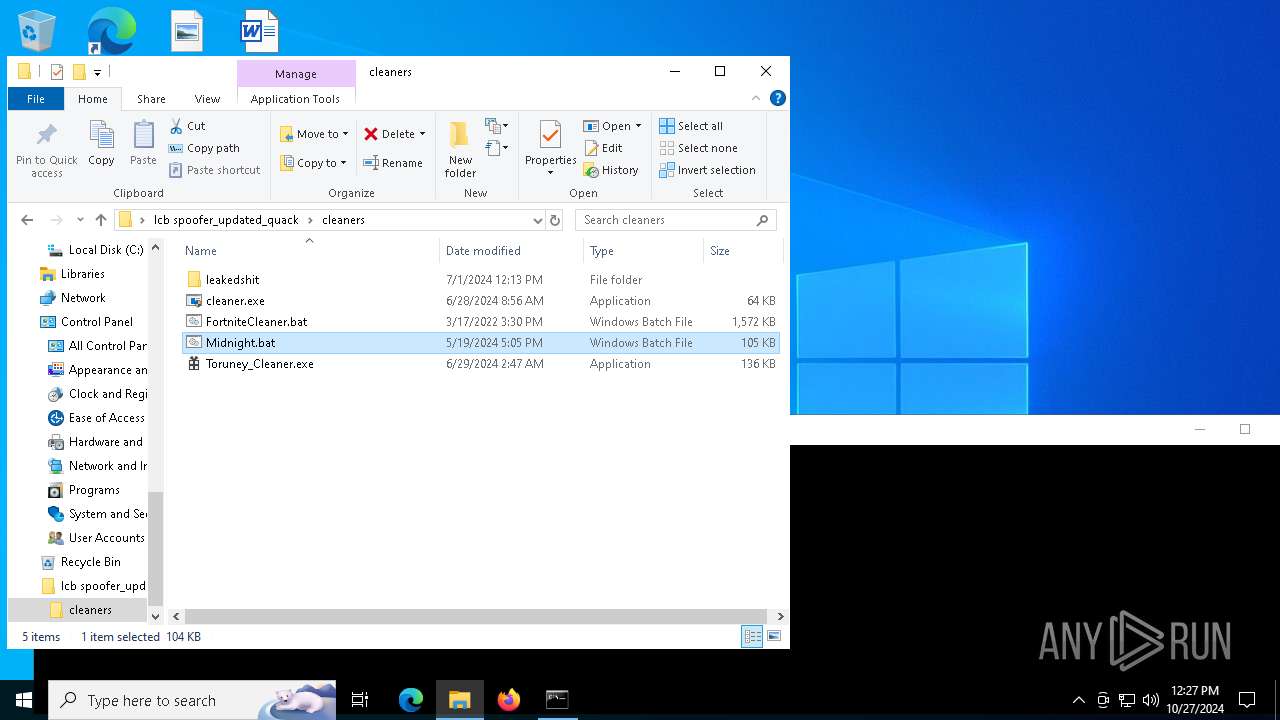
| File name: | lcb spoofer_updated_quack.zip |
| Full analysis: | https://app.any.run/tasks/e4266eec-9173-4be2-ba51-f29be3ee3f89 |
| Verdict: | Malicious activity |
| Analysis date: | October 27, 2024, 12:26:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F43A112608B3F0973436B37D87B0A52B |
| SHA1: | 560E06B4B1158691DB16AFC64100CD9BC6D4B616 |
| SHA256: | F578D77E5264494FD9CF4B740953B12B348745C43CC256CC5339C6A91413F909 |
| SSDEEP: | 196608:NsbpXnsQ7d8kYFwvapdAi3h3HXIkWFwvapdAi3Y:KbpXsQmkYFwyXAiRH4kWFwyXAiY |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5852)
SUSPICIOUS
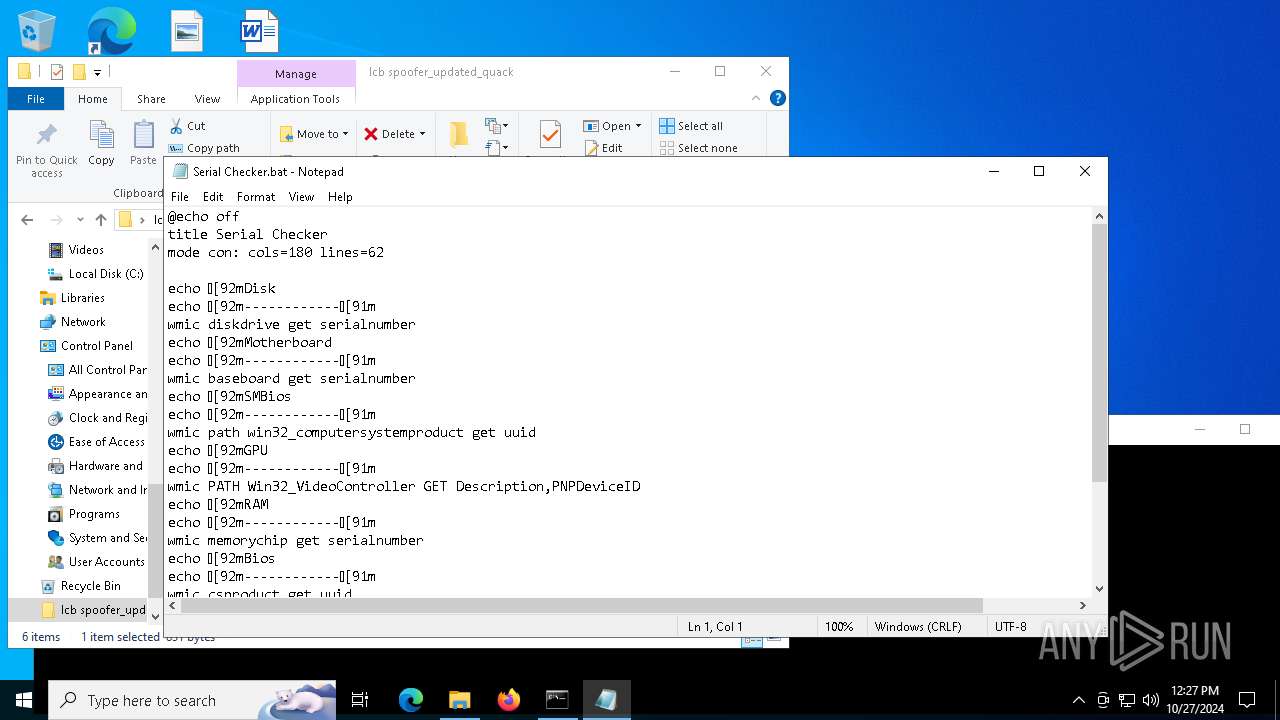
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 4224)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4224)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 5948)
- WMIC.exe (PID: 1196)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 4224)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 4224)
Accesses computer name via WMI (SCRIPT)
- WMIC.exe (PID: 7164)
Uses WMIC.EXE to obtain network information
- cmd.exe (PID: 4224)
Uses WMIC.EXE to obtain memory chip information
- cmd.exe (PID: 4224)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 4224)
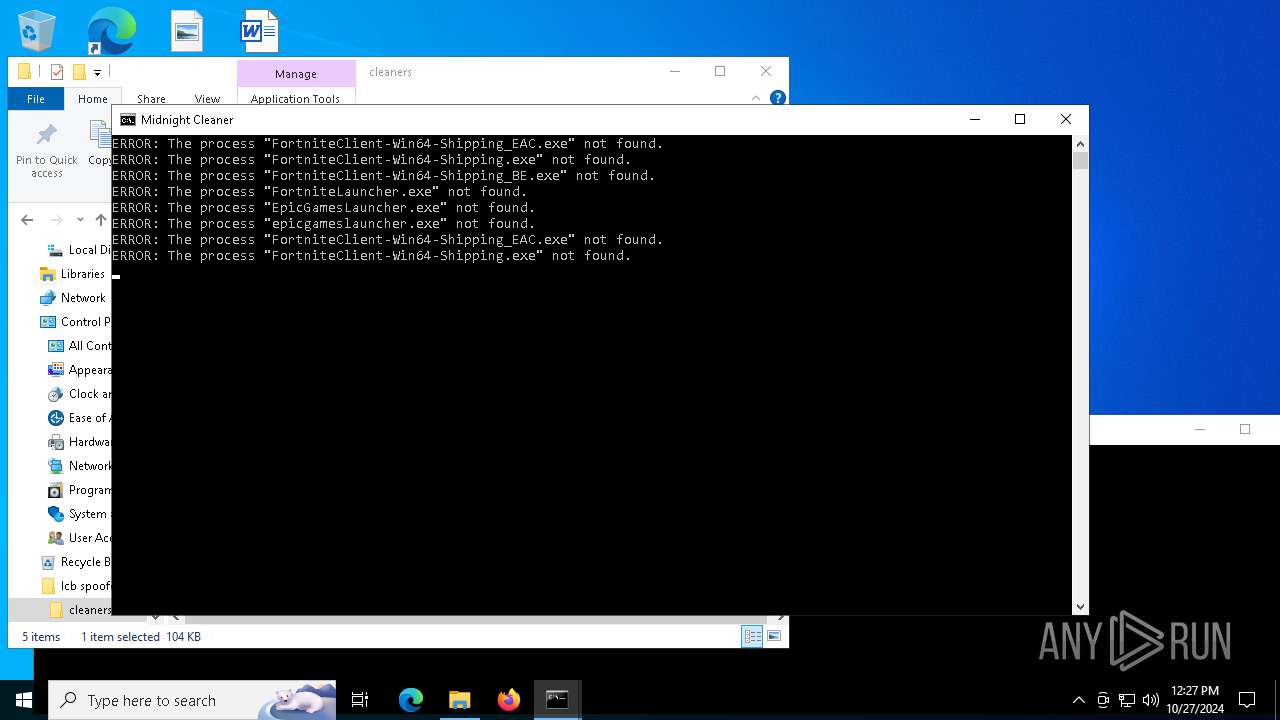
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3772)
- cmd.exe (PID: 4340)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 6428)
- cmd.exe (PID: 1280)
- cmd.exe (PID: 5600)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 7164)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4128)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 6756)
- cmd.exe (PID: 944)
- cmd.exe (PID: 692)
- cmd.exe (PID: 5652)
- cmd.exe (PID: 4464)
- cmd.exe (PID: 5444)
- cmd.exe (PID: 7080)
- cmd.exe (PID: 4340)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 1184)
- cmd.exe (PID: 6200)
- cmd.exe (PID: 2184)
- cmd.exe (PID: 5892)
- cmd.exe (PID: 2888)
- cmd.exe (PID: 7036)
- cmd.exe (PID: 5332)
- cmd.exe (PID: 4584)
- cmd.exe (PID: 4996)
- cmd.exe (PID: 6200)
Starts SC.EXE for service management
- cmd.exe (PID: 5600)
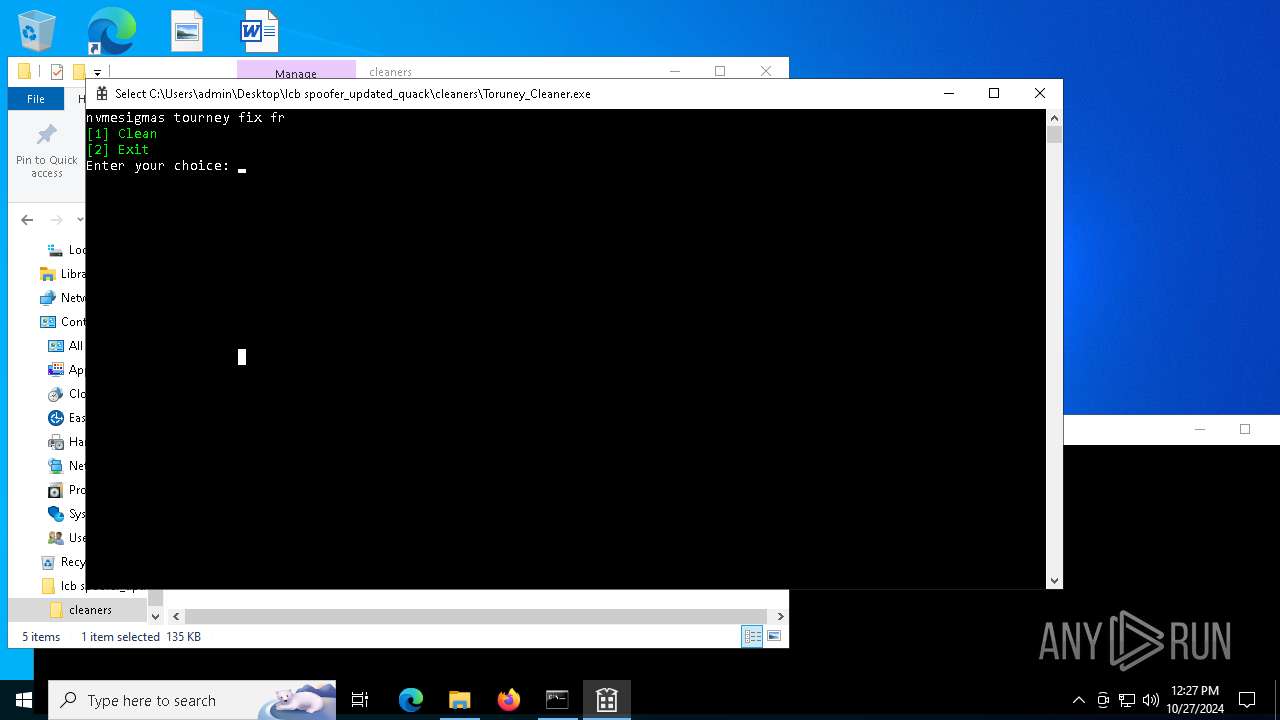
Starts CMD.EXE for commands execution
- Toruney_Cleaner.exe (PID: 6288)
INFO
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5948)
- WMIC.exe (PID: 7048)
- WMIC.exe (PID: 6740)
- WMIC.exe (PID: 7164)
- WMIC.exe (PID: 1952)
- WMIC.exe (PID: 1196)
- WMIC.exe (PID: 3608)
- WMIC.exe (PID: 2428)
Starts MODE.COM to configure console settings
- mode.com (PID: 6820)
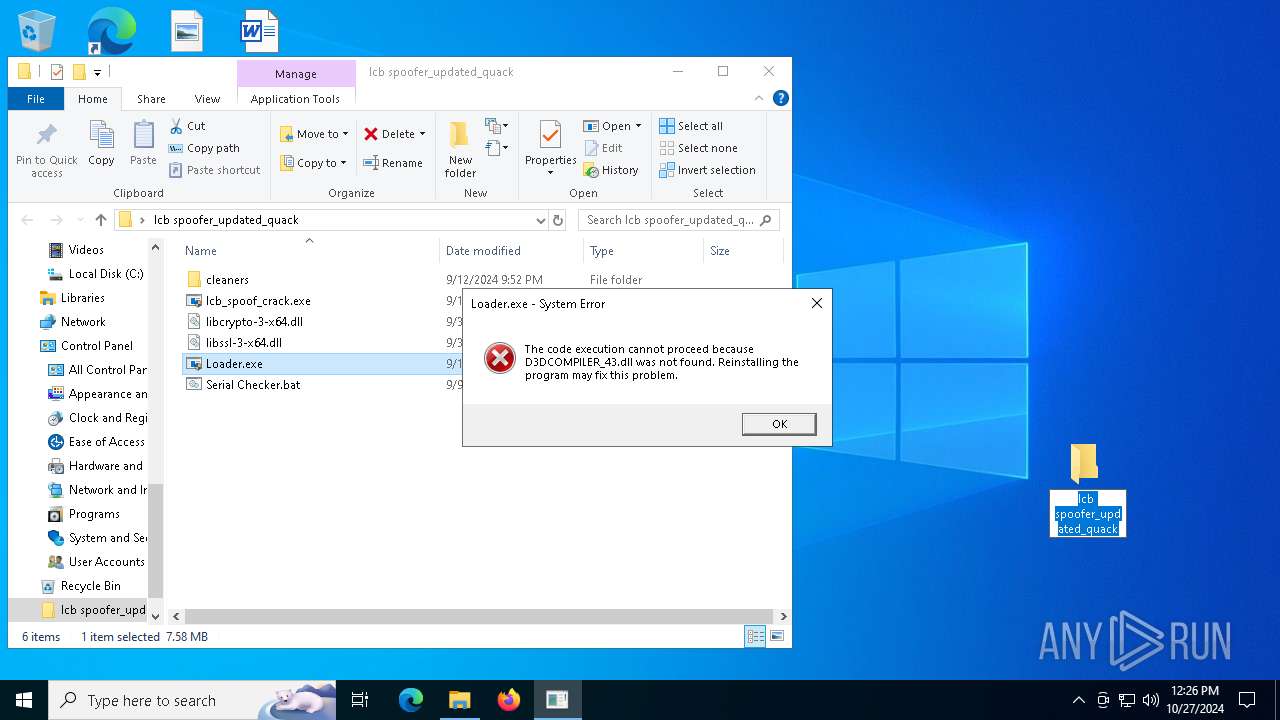
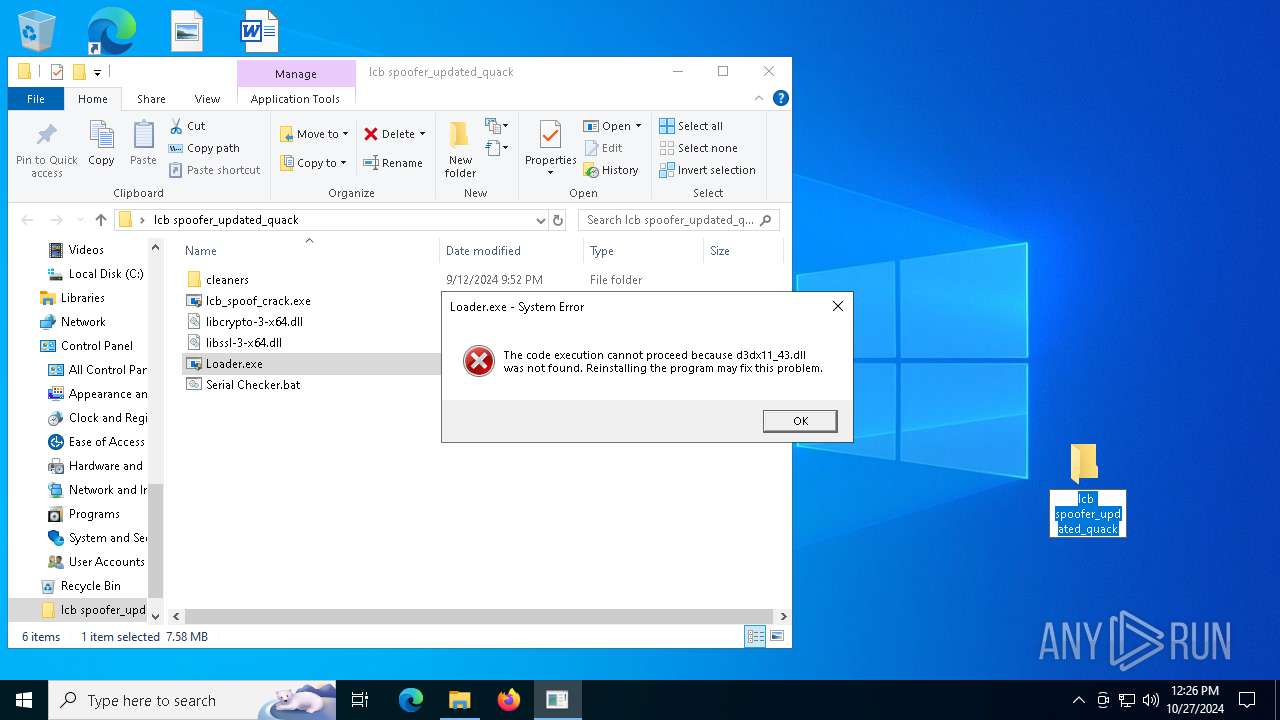
Manual execution by a user
- Loader.exe (PID: 6808)
- cmd.exe (PID: 4224)
- lcb_spoof_crack.exe (PID: 5236)
- Loader.exe (PID: 6176)
- lcb_spoof_crack.exe (PID: 1952)
- Toruney_Cleaner.exe (PID: 6288)
- cleaner.exe (PID: 6176)
- cleaner.exe (PID: 7156)
- cmd.exe (PID: 5600)
- notepad.exe (PID: 6952)
Checks supported languages
- mode.com (PID: 6820)
The process uses the downloaded file
- WinRAR.exe (PID: 5852)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 12347 |
| UncompressedSize: | 65024 |
| OperatingSystem: | Win32 |
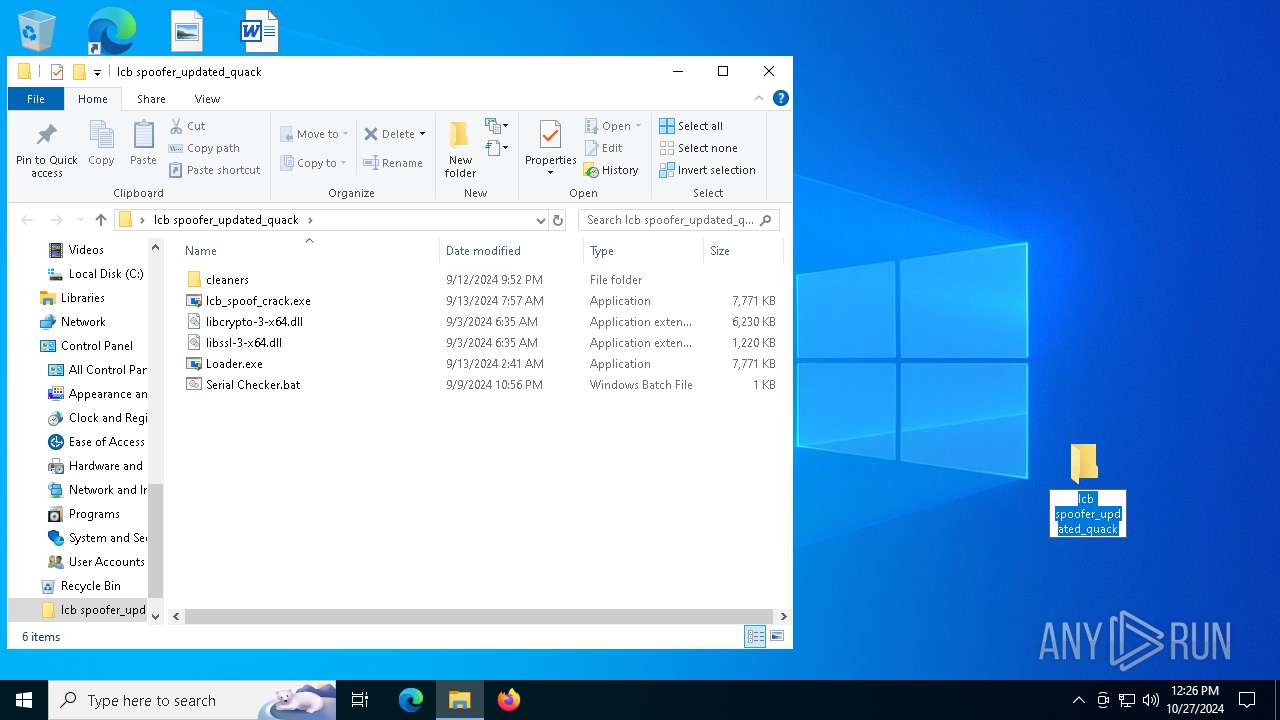
| ArchivedFileName: | lcb spoofer_updated_quack/cleaners/cleaner.exe |
Total processes
226
Monitored processes
100
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | reg delete "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control" /v SystemStartOptions /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 692 | C:\WINDOWS\system32\cmd.exe /c REG ADD HKLM\SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName /v ComputerName /t REG_SZ /d Norc%random% /f | C:\Windows\System32\cmd.exe | — | Toruney_Cleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 944 | C:\WINDOWS\system32\cmd.exe /c reg delete "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control" /v SystemStartOptions /f | C:\Windows\System32\cmd.exe | — | Toruney_Cleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | C:\WINDOWS\system32\cmd.exe /c reg delete "HKEY_LOCAL_MACHINE\Hardware\Description\System\BIOS" /v BIOSReleaseDate /f | C:\Windows\System32\cmd.exe | — | Toruney_Cleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | C:\WINDOWS\system32\cmd.exe /c taskkill /f /im EpicGamesLauncher.exe | C:\Windows\System32\cmd.exe | — | Toruney_Cleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1584 | taskkill /f /im EasyAntiCheat.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | reg delete "HKEY_CURRENT_USER\Software\Epic Games" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1784 | taskkill /f /im FortniteClient-Win64-Shipping_BE.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1788 | taskkill /f /im smartscreen.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 167
Read events
6 151
Write events
16
Delete events
0
Modification events
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\lcb spoofer_updated_quack.zip.rar | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
8
Suspicious files
0
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
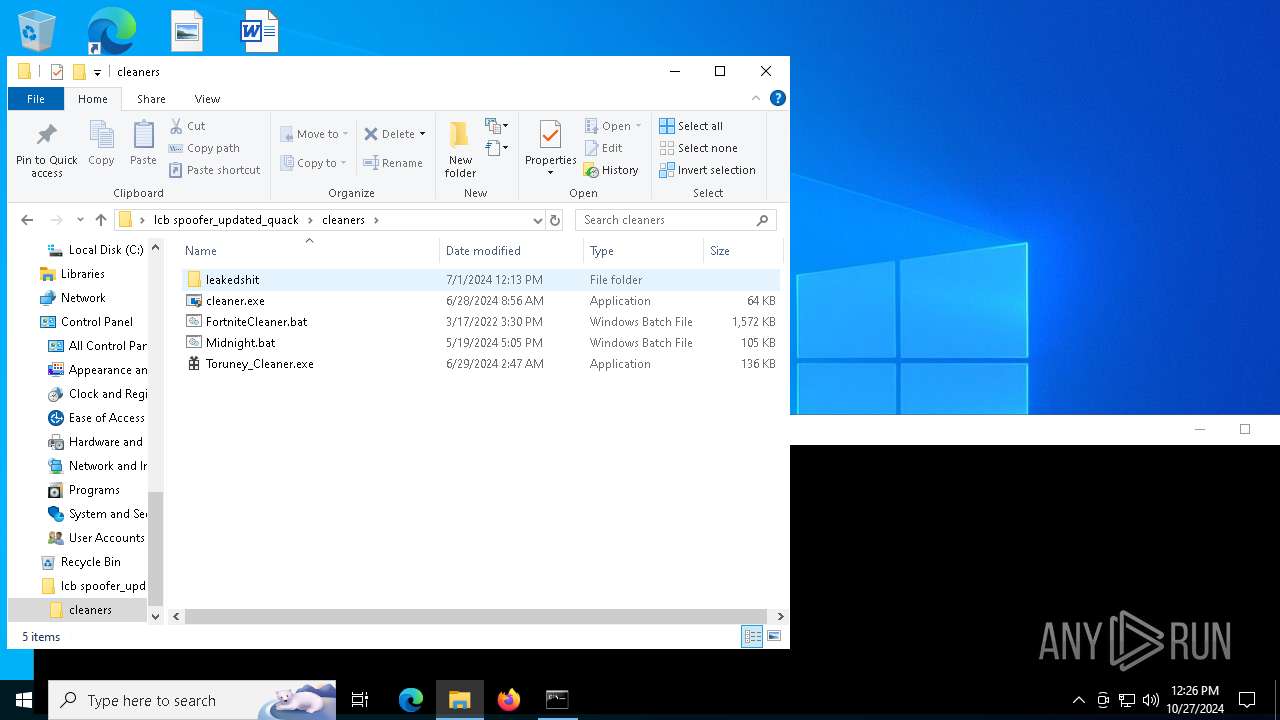
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\cleaners\leakedshit\read me.txt | text | |
MD5:59DFA2CBE2F497AC864C8EE4443D30B4 | SHA256:D7E6C82A988598566A0EE892B036BB4F4B1E8D13C4D7914F1EC11EFD9D933662 | |||
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\cleaners\leakedshit\eac install\EasyAntiCheat_EOS_Setup.exe | executable | |
MD5:B2CF34920A4010EF3799921D8E0D18D7 | SHA256:6108A4F378AE293A5EA2BA74058BEAE388D85FC199EDDE903BA81375D8744396 | |||
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\cleaners\leakedshit\clean2.bat | text | |
MD5:049FCE145ABFED6AFA90599762B08C6B | SHA256:97377C7AE3FF41E72DAC718A4DD82CDD079FF50E026CE159D3435E6EDB8BC543 | |||
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\cleaners\leakedshit\eac install\EAC.bat | text | |
MD5:8E25B700F094C22CF9545B24DF4B3B98 | SHA256:5A98534F6DE39AF620B6520D25AC388D1EE46F10D10C7A05F34F6593098C99D7 | |||
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\cleaners\leakedshit\clean1.bat | text | |
MD5:4BF8DD140901A615B1A5FA5136728521 | SHA256:E2B6CE87A5FA871709665B0306E15D45CD7B5550A4DE6701A8CE31E811A646ED | |||
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\cleaners\leakedshit\clean3.bat | text | |
MD5:FBD3EBE26A823F86AE2DEED72DF613B9 | SHA256:8E43A6E232E9842777D3FCE8C552BF942359757E6AF092595C98AE101EE0E94D | |||
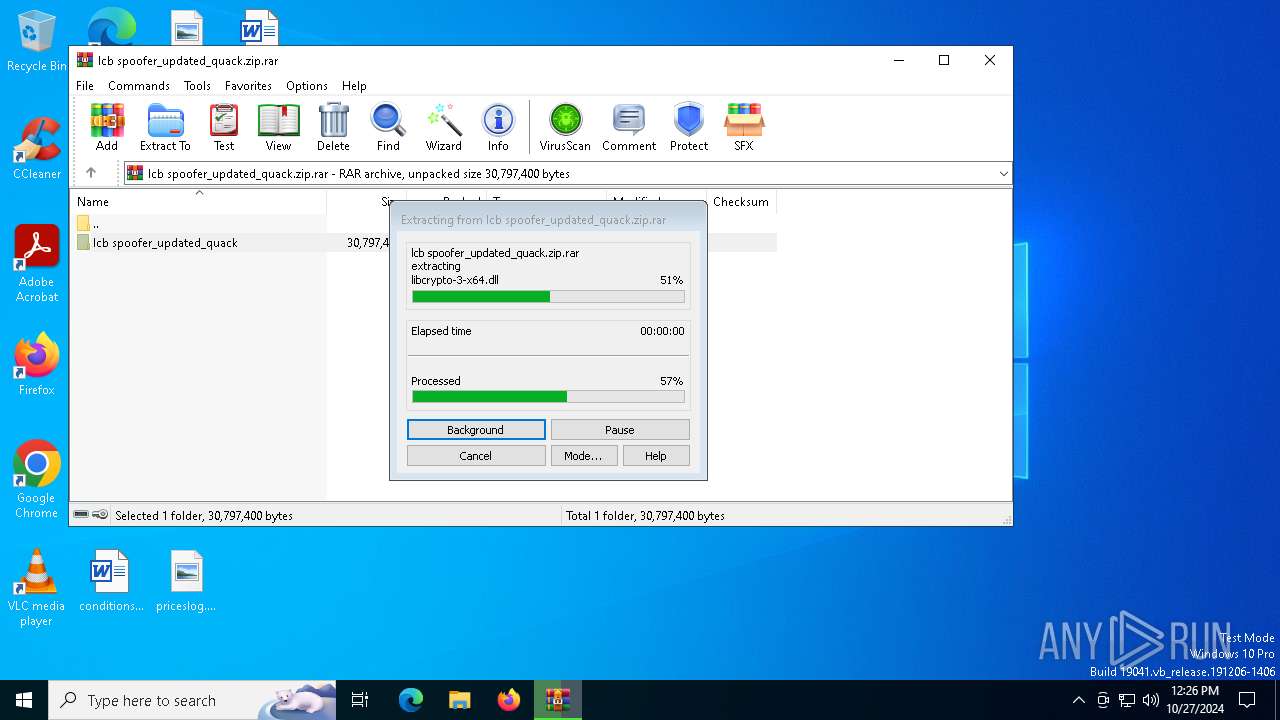
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\libcrypto-3-x64.dll | executable | |
MD5:E7463D58D7AFF43C7D71A3847BA8201E | SHA256:2249476A14DEA73AE271D661483BDC6C15E45B931F8DBFD0BD1B84193CF420EA | |||
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\cleaners\leakedshit\New Cleaner.bat | text | |
MD5:18C77961F8086F26C028643BA76E9B46 | SHA256:B1ED8EF4D46BFB260356E37B884AD4A86BEE9F0415BC6A73EF3ACEDC0DD8F1F4 | |||
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\Loader.exe | executable | |
MD5:E4076E54CCCEE49CEE936AD763A0E46A | SHA256:7F0109B00A1E644A7AF8C517FA8749D764D952434F3E192990E97A64B54AD4BB | |||
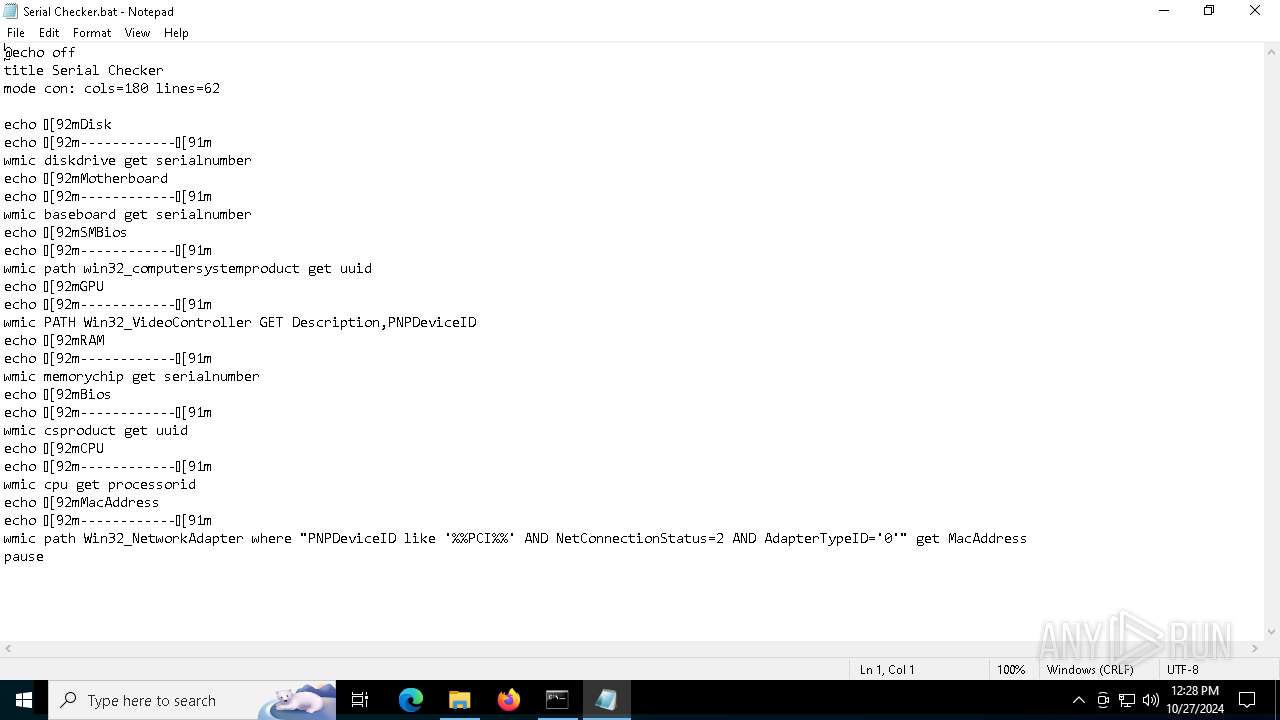
| 5852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5852.28844\lcb spoofer_updated_quack\Serial Checker.bat | text | |
MD5:119A816FB17E3C634DEDA5FA650BBB50 | SHA256:8E04607E18F90A99E360F4BFFE37102B20006143859C87AE845694512B41094F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
44
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5232 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2312 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2312 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6572 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1752 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 2.16.110.193:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |