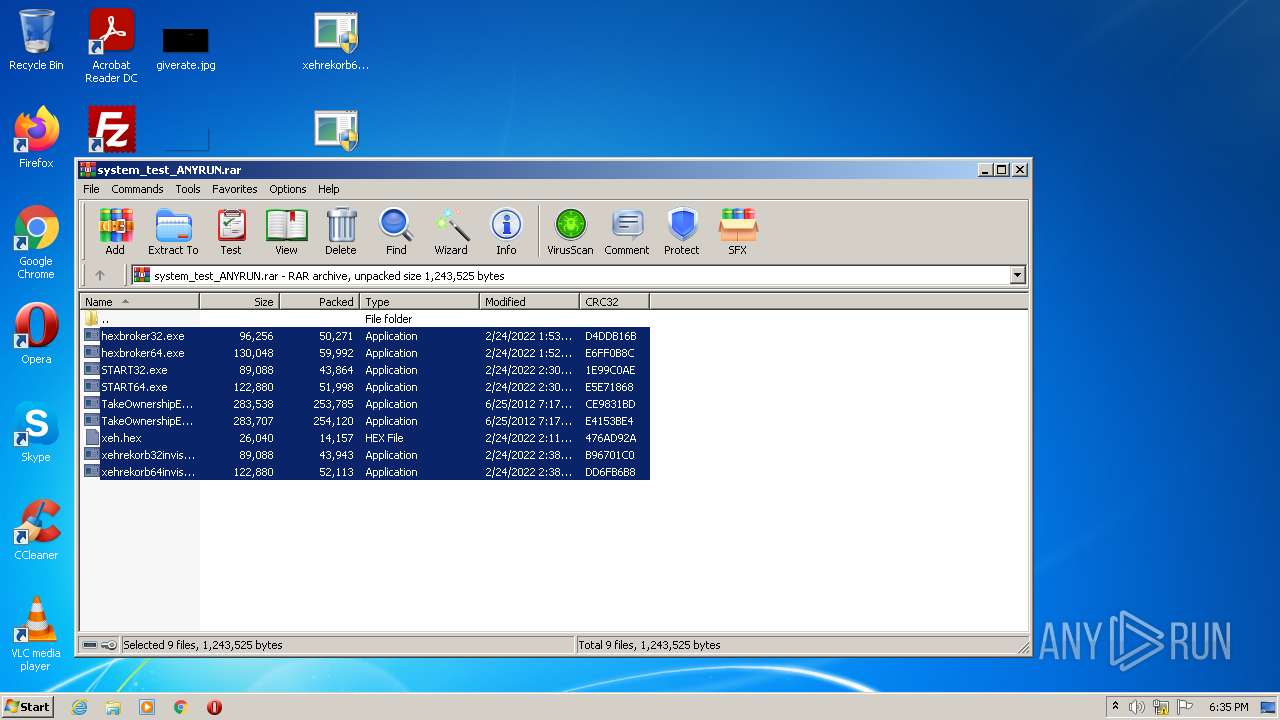
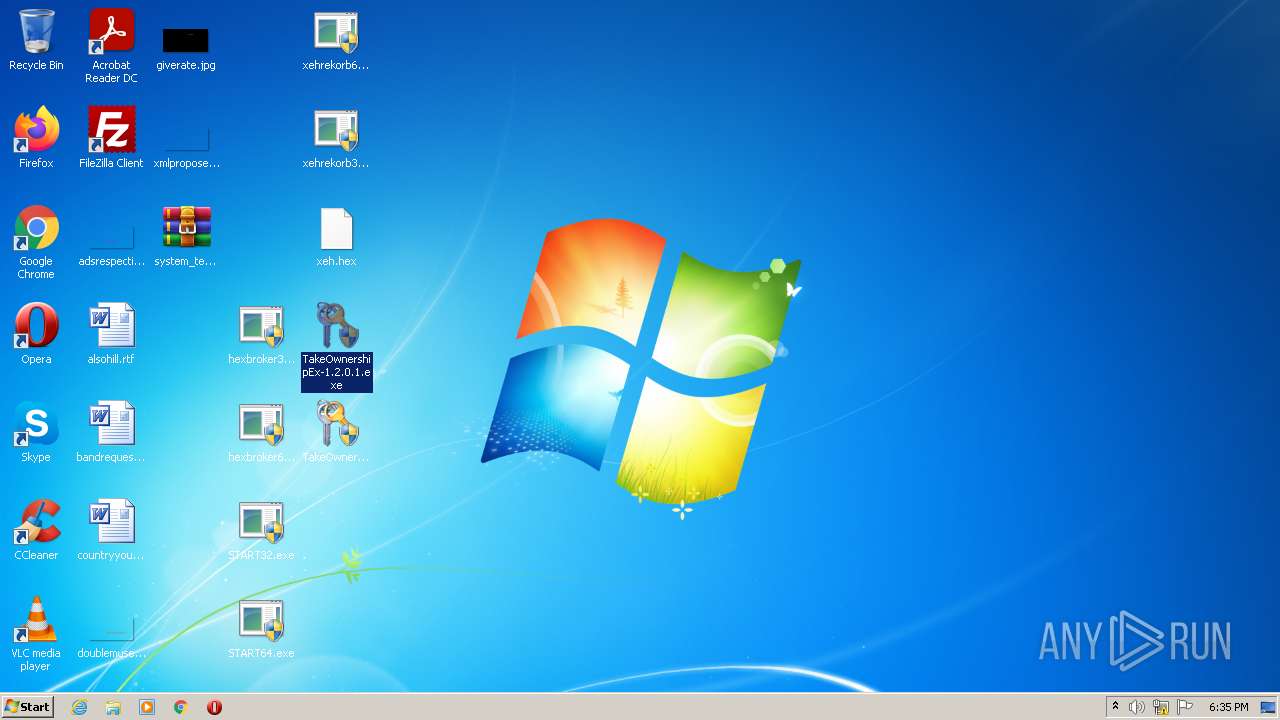
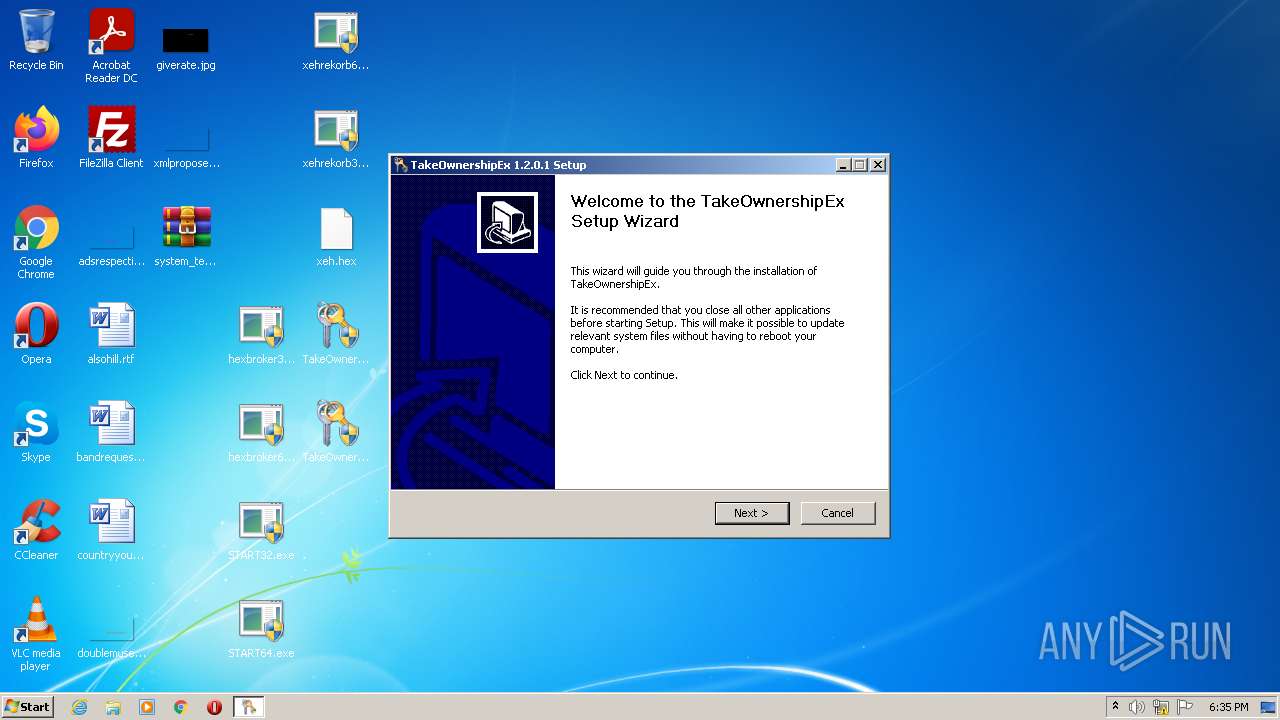
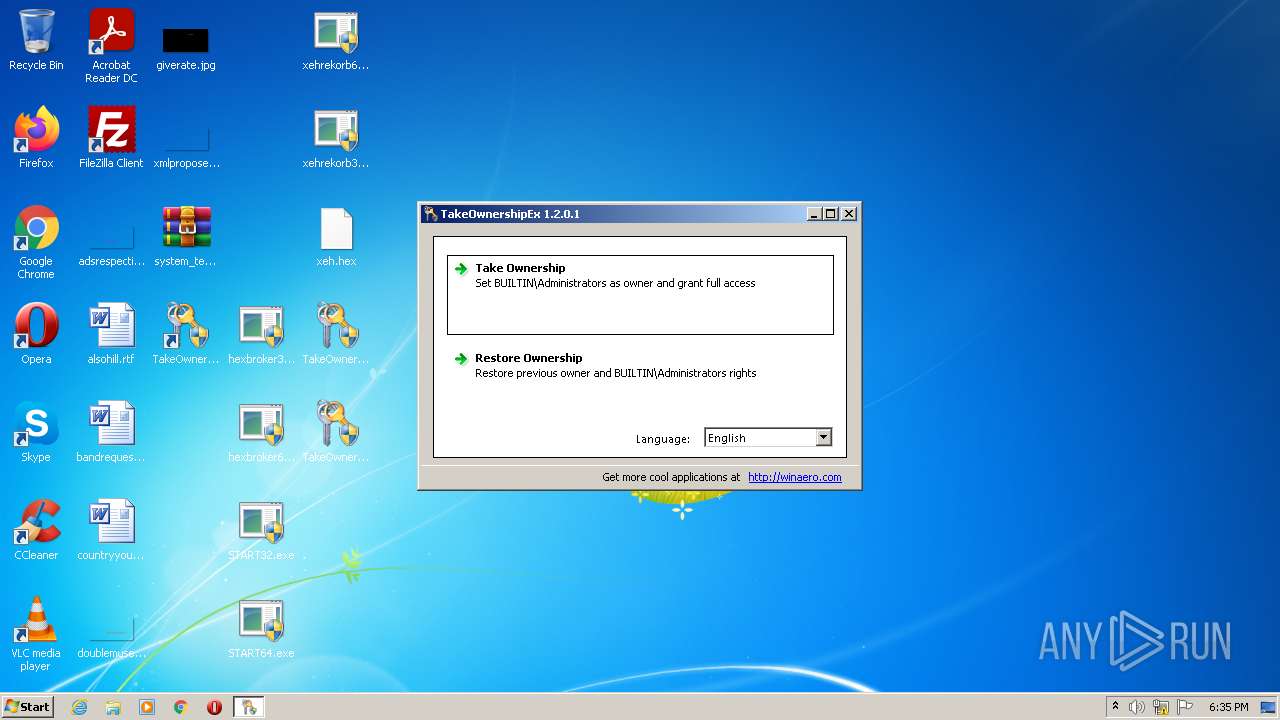
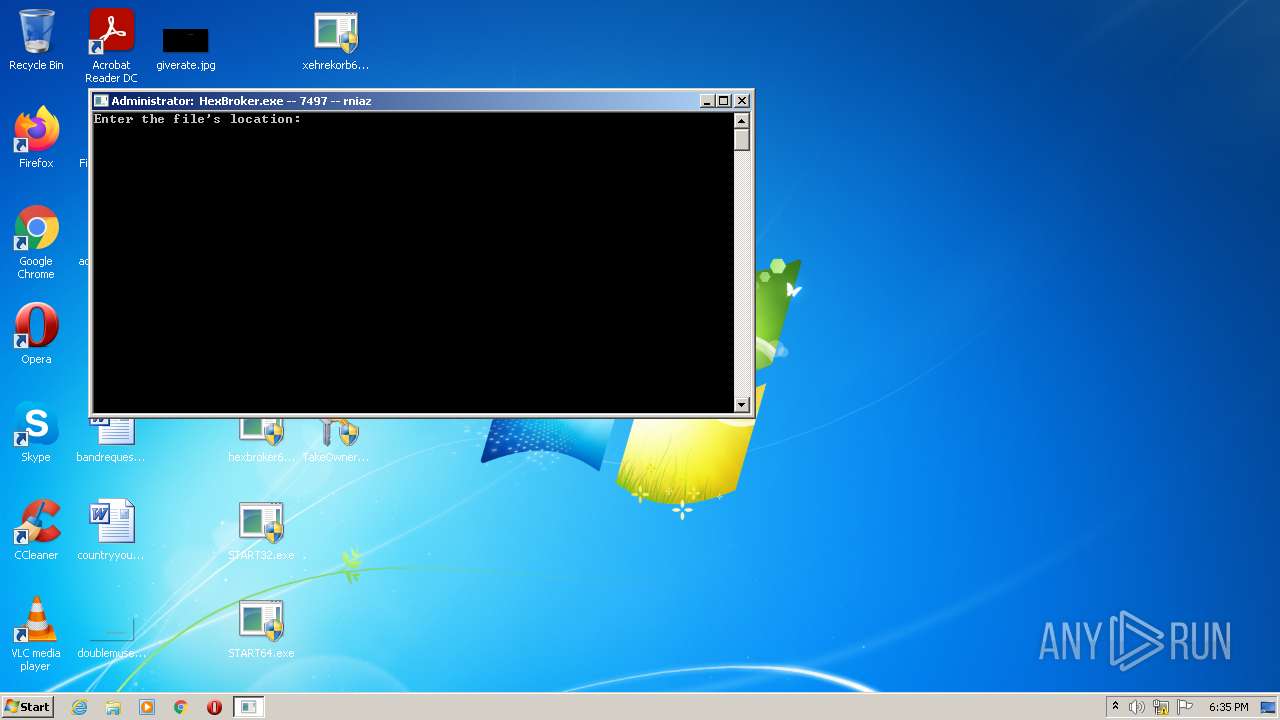
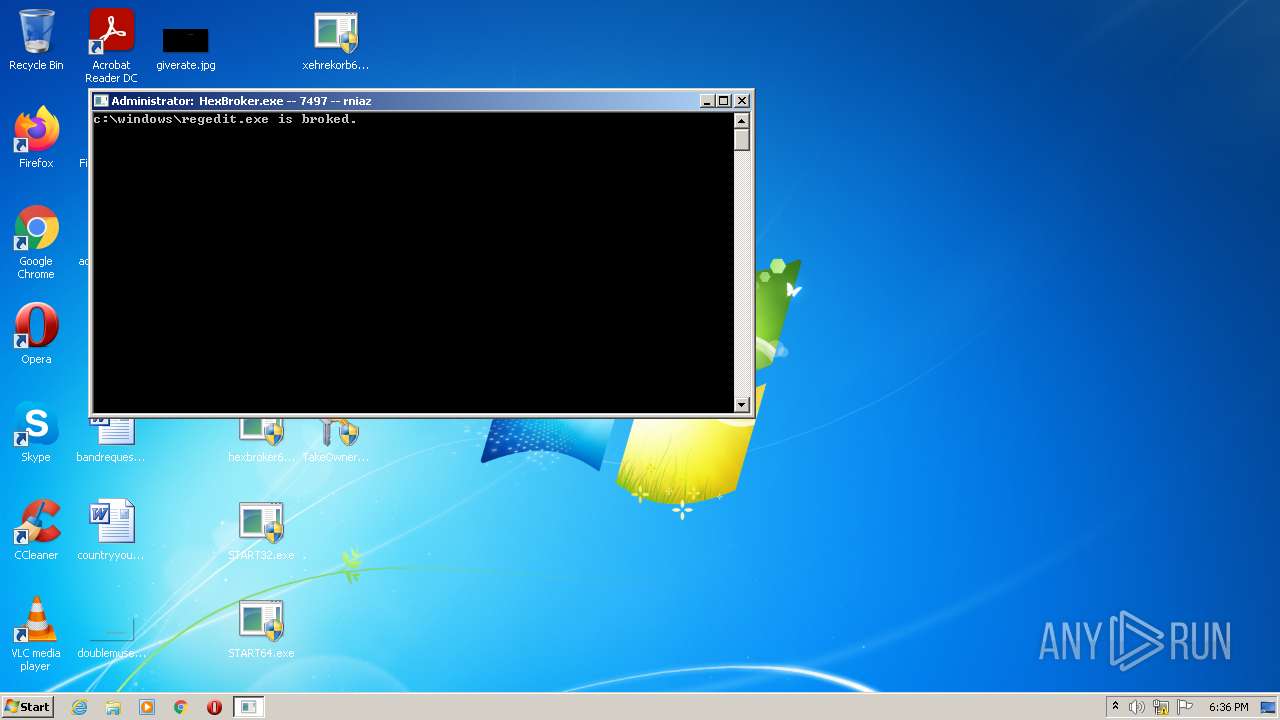
| File name: | system_test_ANYRUN.rar |
| Full analysis: | https://app.any.run/tasks/33801e10-9680-464c-8bdd-b98e5729cbdf |
| Verdict: | Malicious activity |
| Analysis date: | February 24, 2022, 18:35:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 90C0ACE31904EBF75FFB3E16CD3F05AF |
| SHA1: | 20D618DC915A4DA64E48A8A15B6D404487886ADB |
| SHA256: | F56193163AA618781BC08C0CE651BFE1CDF94210370031E08D993ED02DE517A0 |
| SSDEEP: | 24576:mhlyP0KGHpHzRo7i3NjeTSF2jInFHzRUWb2OhE:IllKGHplo7ip44FlU0rE |
MALICIOUS
Application was dropped or rewritten from another process
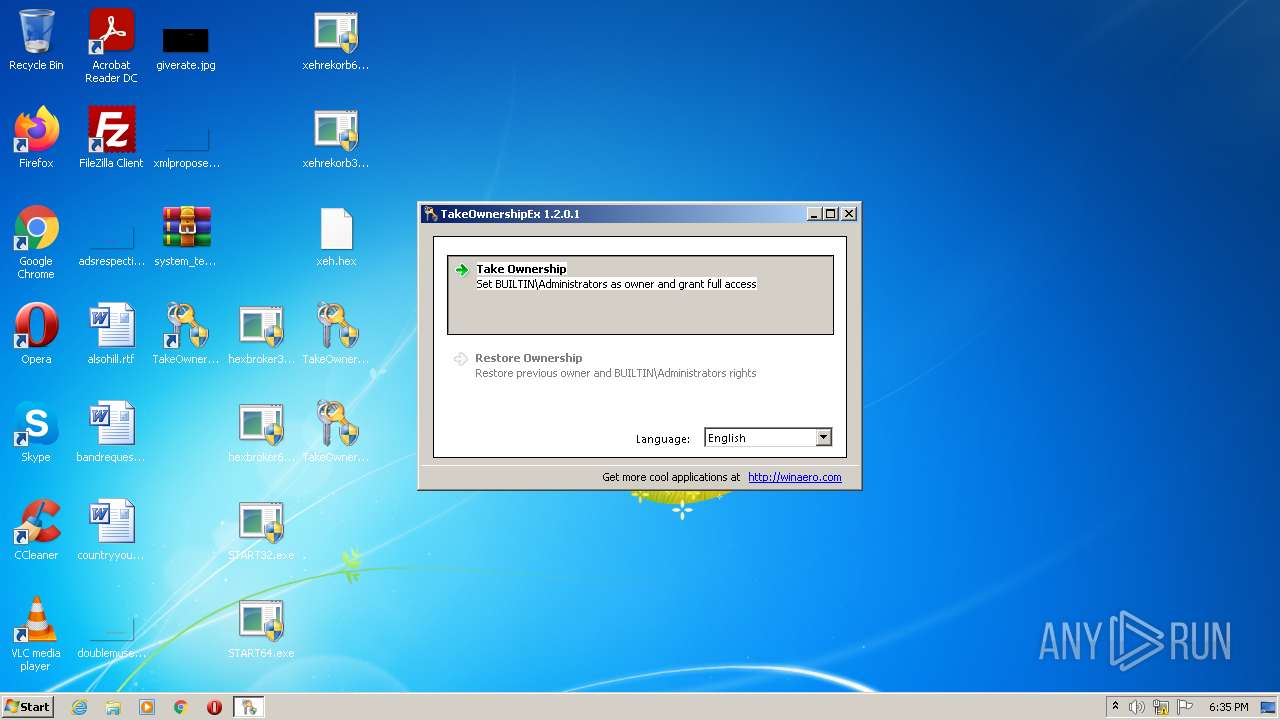
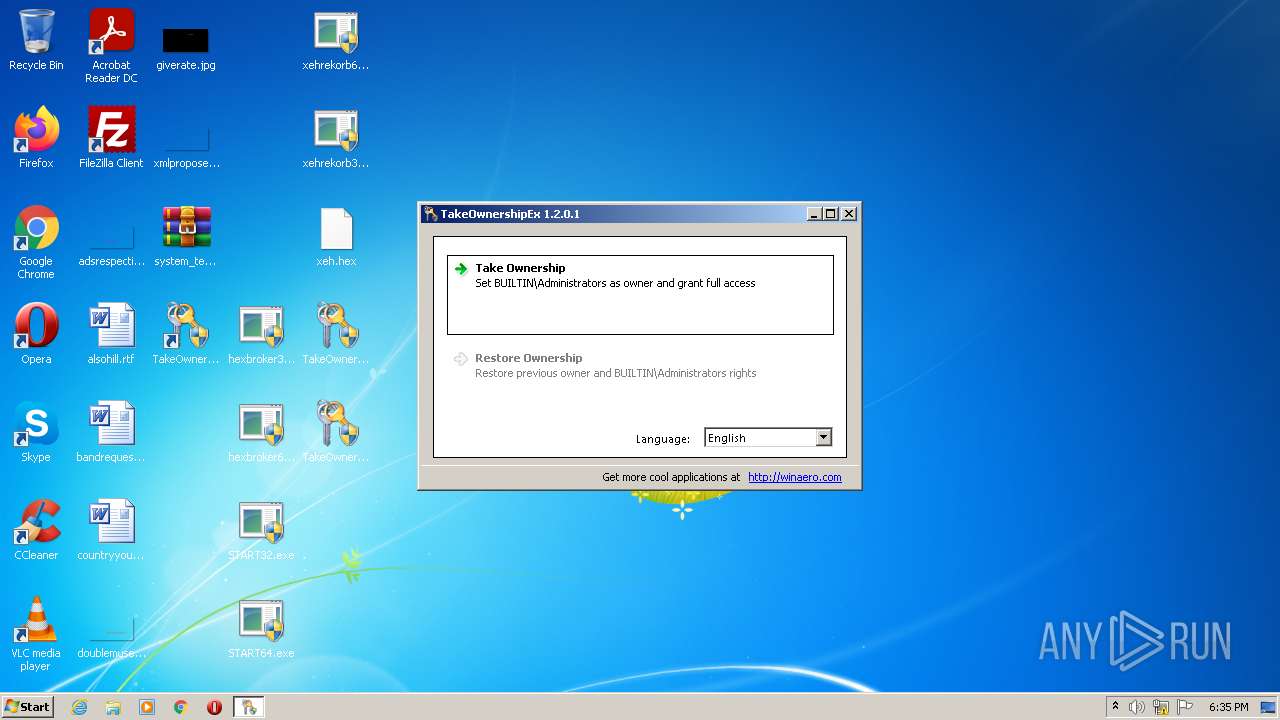
- TakeOwnershipEx-1.2.0.1.exe (PID: 1728)
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
- TakeOwnershipEx.exe (PID: 2744)
- TakeOwnershipEx.exe (PID: 3300)
- hexbroker32.exe (PID: 804)
- hexbroker32.exe (PID: 3768)
Loads dropped or rewritten executable
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
Drops executable file immediately after starts
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 1324)
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
- TakeOwnershipEx.exe (PID: 3300)
Checks supported languages
- WinRAR.exe (PID: 1324)
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
- TakeOwnershipEx.exe (PID: 3300)
- cmd.exe (PID: 3060)
- hexbroker32.exe (PID: 3768)
Drops a file with too old compile date
- WinRAR.exe (PID: 1324)
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1324)
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
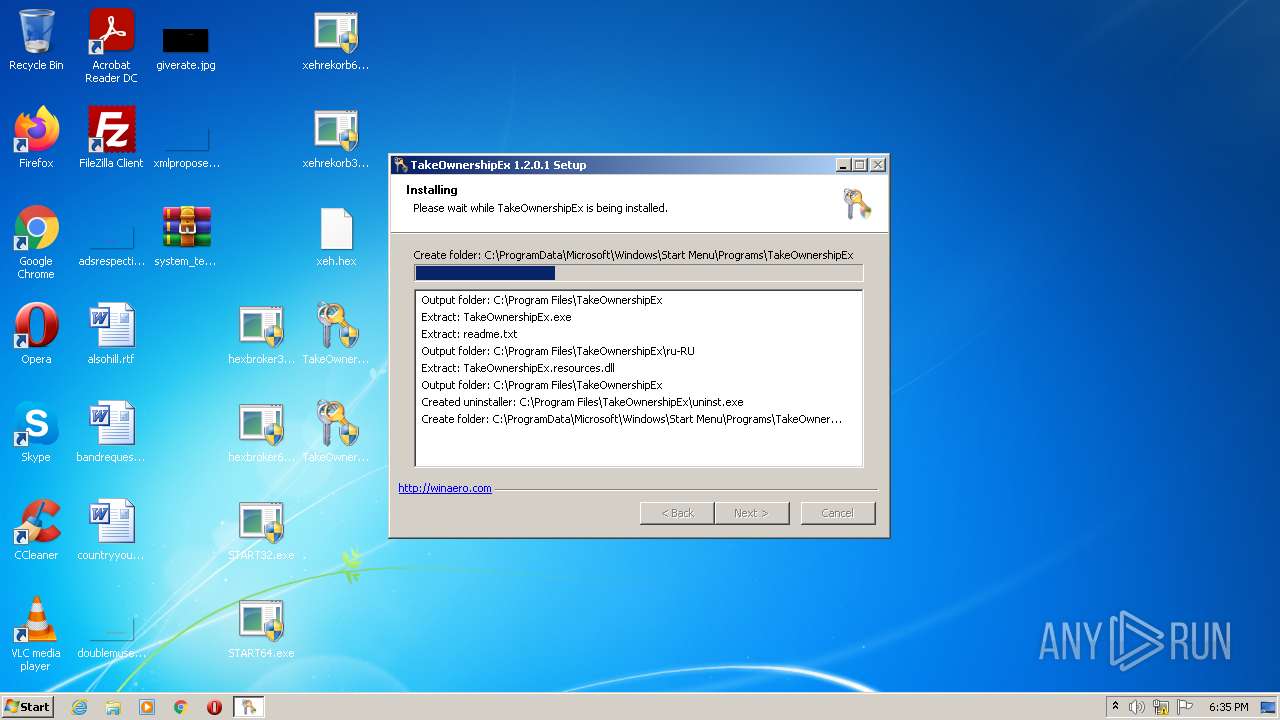
Creates a directory in Program Files
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
Creates a software uninstall entry
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
Changes default file association
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
Drops a file that was compiled in debug mode
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
Creates files in the program directory
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
Reads internet explorer settings
- TakeOwnershipEx.exe (PID: 3300)
Creates files in the user directory
- TakeOwnershipEx.exe (PID: 3300)
Reads Environment values
- TakeOwnershipEx.exe (PID: 3300)
Reads default file associations for system extensions
- TakeOwnershipEx.exe (PID: 3300)
Starts CMD.EXE for commands execution
- hexbroker32.exe (PID: 3768)
INFO
Manual execution by user
- TakeOwnershipEx-1.2.0.1.exe (PID: 1728)
- TakeOwnershipEx-1.2.0.1.exe (PID: 1404)
- TakeOwnershipEx.exe (PID: 2744)
- TakeOwnershipEx.exe (PID: 3300)
- hexbroker32.exe (PID: 3768)
- hexbroker32.exe (PID: 804)
- explorer.exe (PID: 3220)
Checks supported languages
- explorer.exe (PID: 3220)
Reads the computer name
- explorer.exe (PID: 3220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
55
Monitored processes
9
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 804 | "C:\Users\admin\Desktop\hexbroker32.exe" | C:\Users\admin\Desktop\hexbroker32.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1324 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\system_test_ANYRUN.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
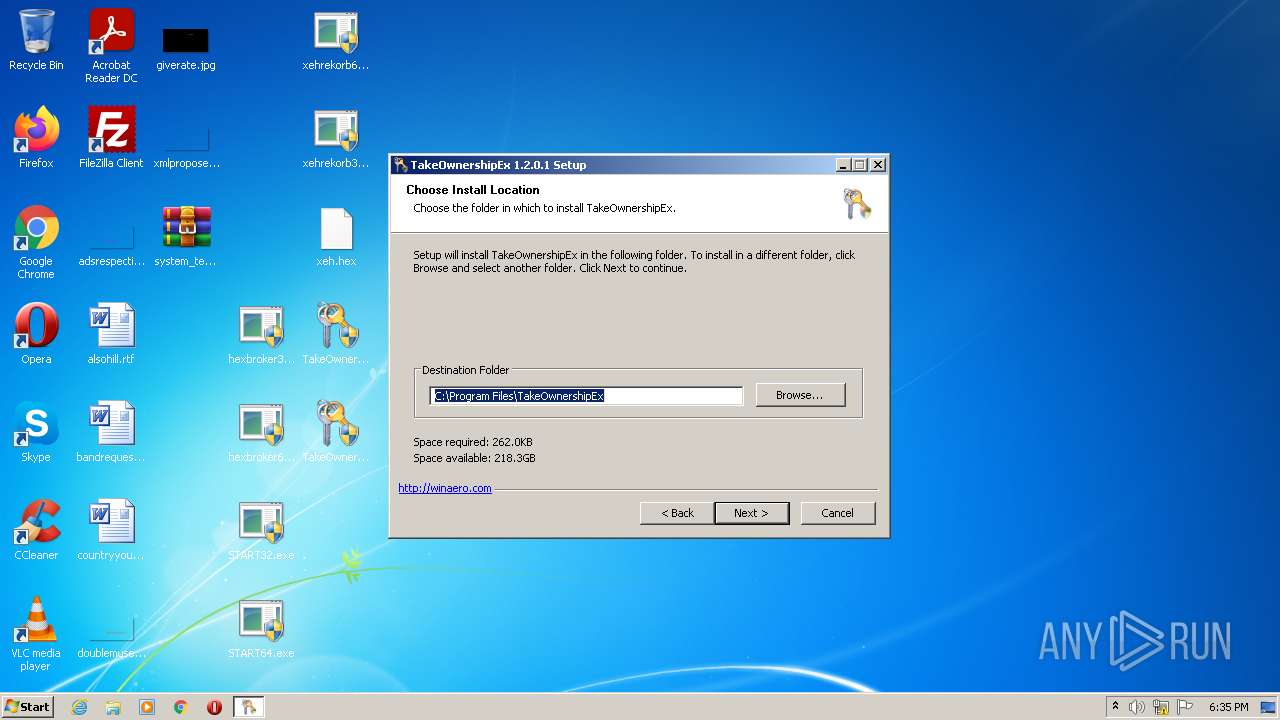
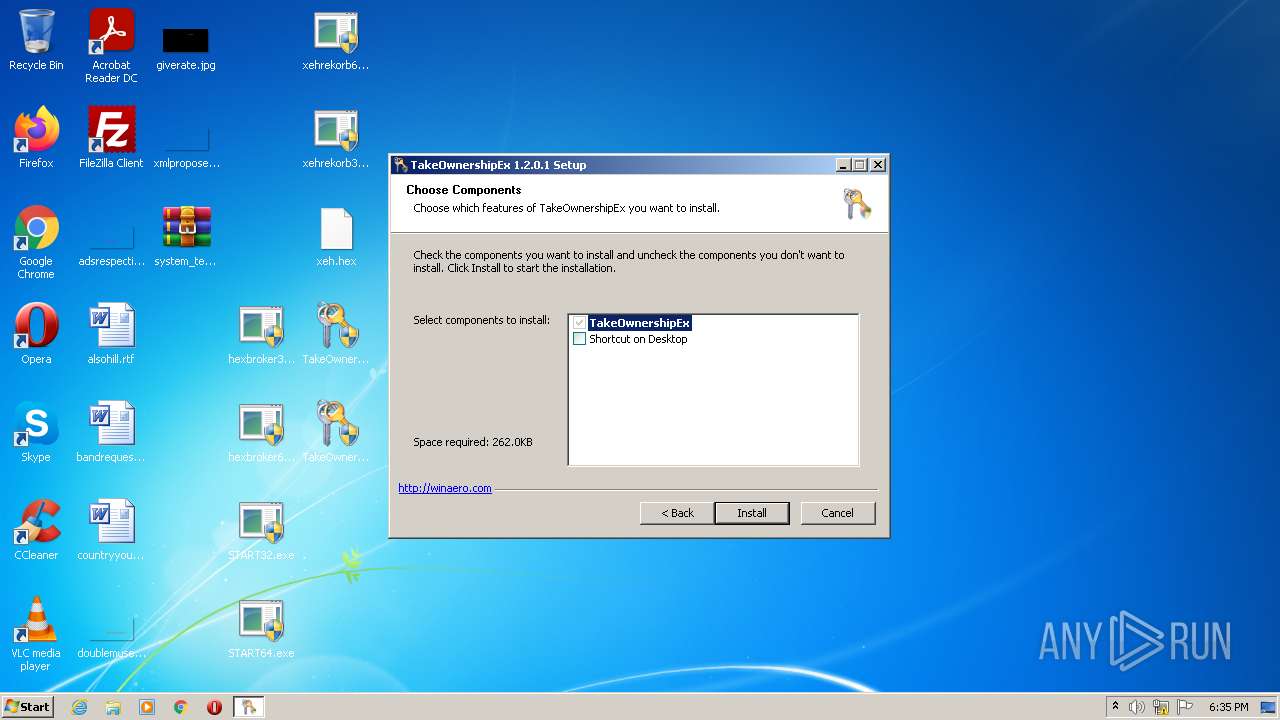
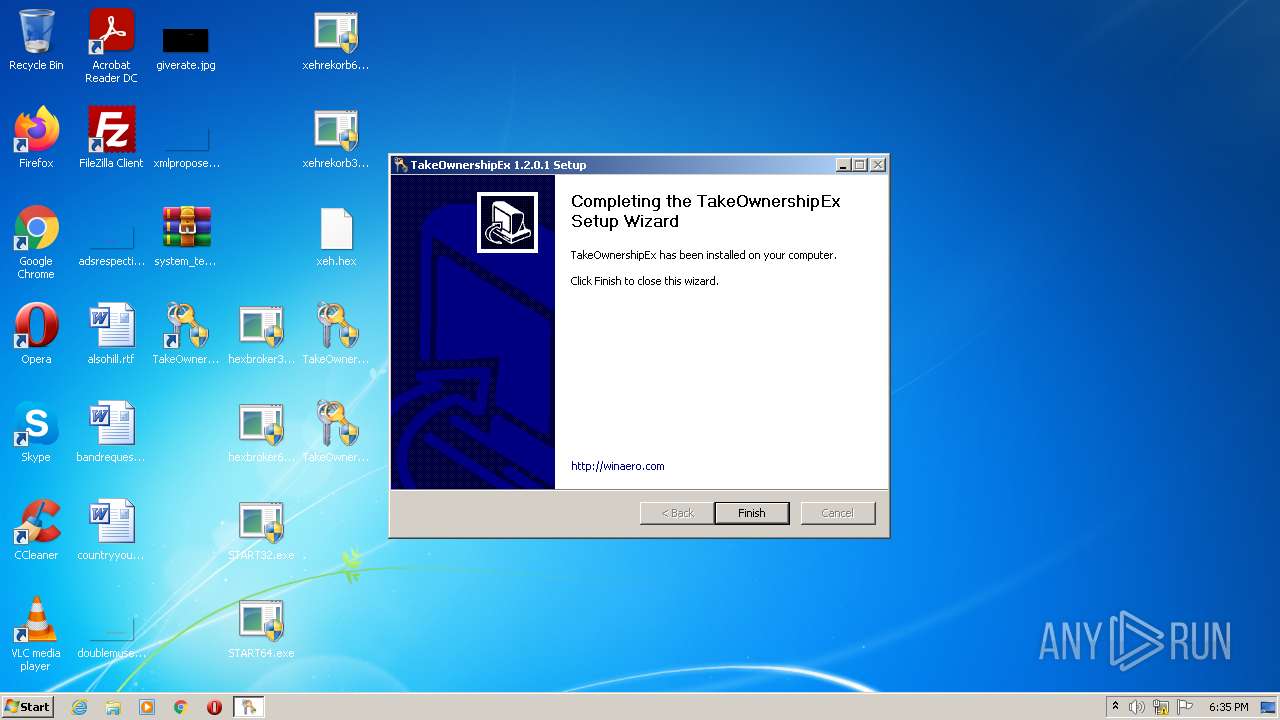
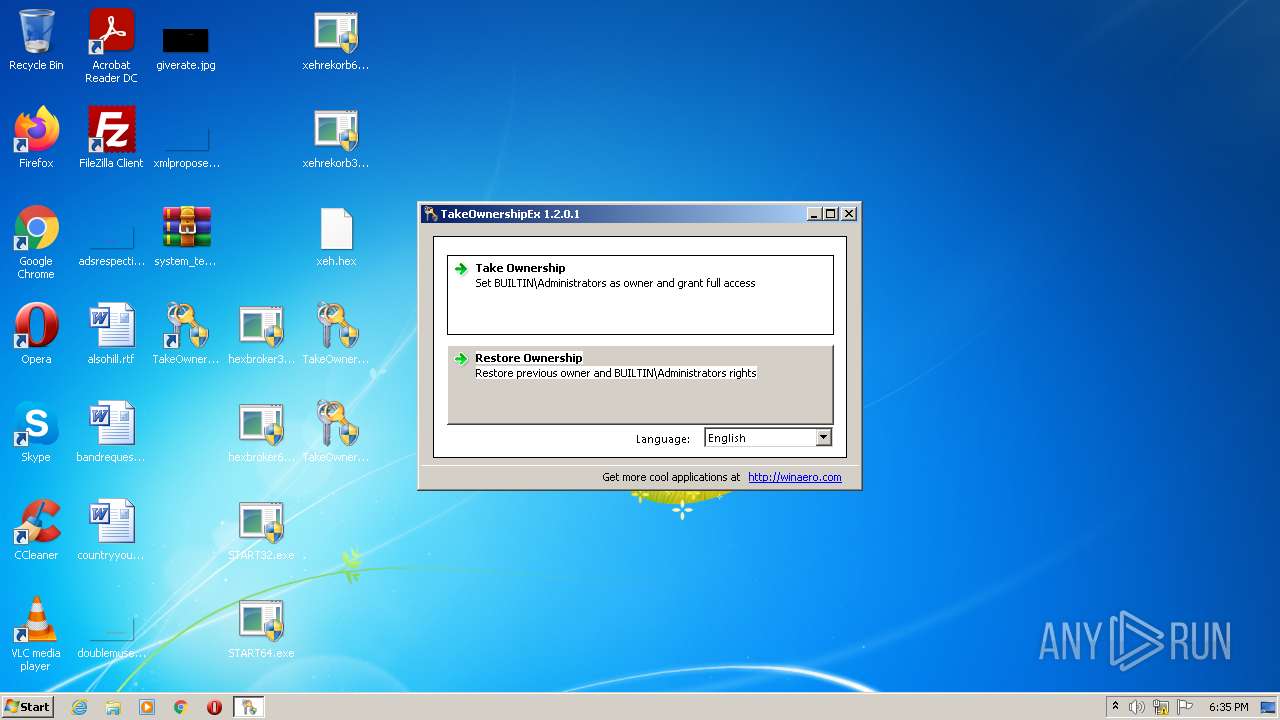
| 1404 | "C:\Users\admin\Desktop\TakeOwnershipEx-1.2.0.1.exe" | C:\Users\admin\Desktop\TakeOwnershipEx-1.2.0.1.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1728 | "C:\Users\admin\Desktop\TakeOwnershipEx-1.2.0.1.exe" | C:\Users\admin\Desktop\TakeOwnershipEx-1.2.0.1.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2744 | "C:\Program Files\TakeOwnershipEx\TakeOwnershipEx.exe" | C:\Program Files\TakeOwnershipEx\TakeOwnershipEx.exe | — | Explorer.EXE | |||||||||||
User: admin Company: http://winaero.com Integrity Level: MEDIUM Description: TakeOwnershipEx Exit code: 3221226540 Version: 1.2.0.1 Modules
| |||||||||||||||
| 3060 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\826D.tmp\826E.tmp\826F.bat C:\Users\admin\Desktop\hexbroker32.exe" | C:\Windows\system32\cmd.exe | — | hexbroker32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3220 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3300 | "C:\Program Files\TakeOwnershipEx\TakeOwnershipEx.exe" | C:\Program Files\TakeOwnershipEx\TakeOwnershipEx.exe | Explorer.EXE | ||||||||||||
User: admin Company: http://winaero.com Integrity Level: HIGH Description: TakeOwnershipEx Exit code: 0 Version: 1.2.0.1 Modules
| |||||||||||||||
| 3768 | "C:\Users\admin\Desktop\hexbroker32.exe" | C:\Users\admin\Desktop\hexbroker32.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 884
Read events
2 831
Write events
53
Delete events
0
Modification events
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\system_test_ANYRUN.rar | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
15
Suspicious files
1
Text files
5
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\xehrekorb64invis.exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\START64.exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\xehrekorb32invis.exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\hexbroker64.exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\TakeOwnershipEx-1.2.0.1-Win8.exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\TakeOwnershipEx-1.2.0.1.exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\hexbroker32.exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\START32.exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1324.37785\xeh.hex | text | |
MD5:— | SHA256:— | |||
| 1404 | TakeOwnershipEx-1.2.0.1.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\TakeOwnershipEx\TakeOwnershipEx.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
1
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3300 | TakeOwnershipEx.exe | GET | 301 | 68.183.112.81:80 | http://winaero.com/updates/takeownershipex.txt | US | html | 162 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3300 | TakeOwnershipEx.exe | 68.183.112.81:80 | winaero.com | DSL Extreme | US | suspicious |
3300 | TakeOwnershipEx.exe | 68.183.112.81:443 | winaero.com | DSL Extreme | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
winaero.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3300 | TakeOwnershipEx.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1 ETPRO signatures available at the full report