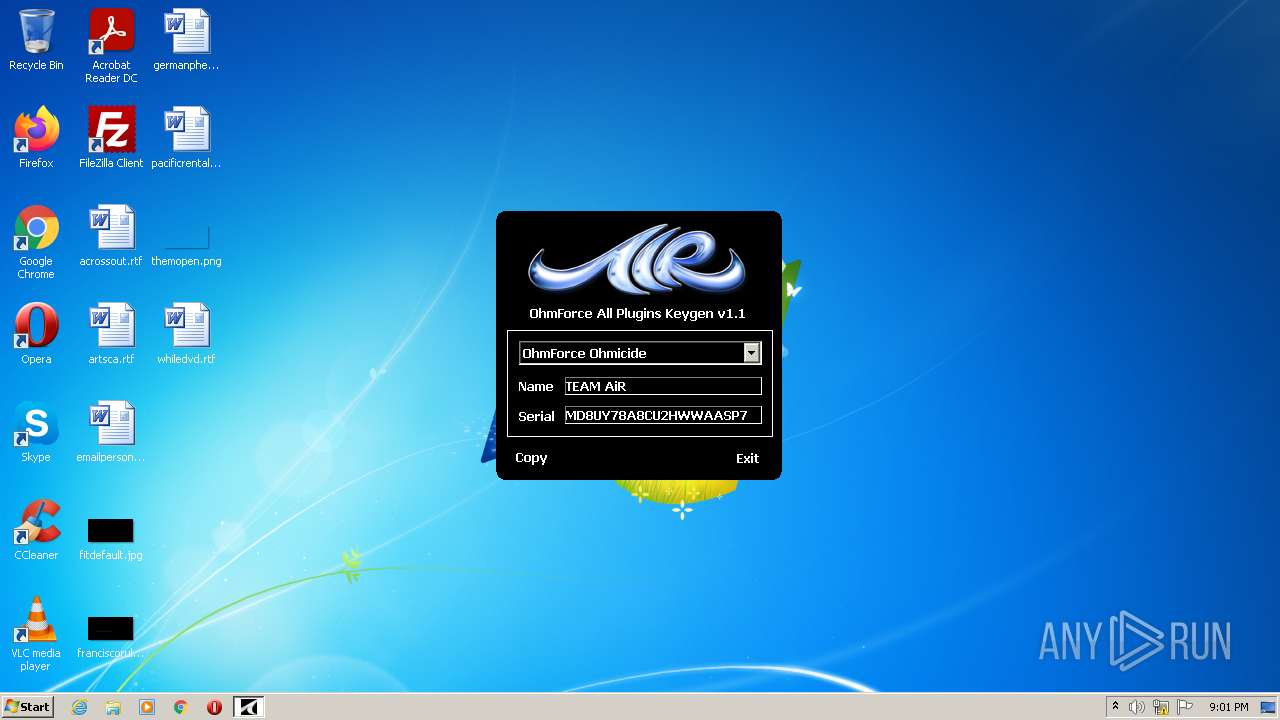
| File name: | keygen.exe |
| Full analysis: | https://app.any.run/tasks/ed66a4f4-d705-446b-aee6-8fd387442d6b |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2022, 20:01:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D3BE4AC211276300742F856CD4547777 |
| SHA1: | 4BFC58F268151009FDE73156D95D0CFC37C1A4E4 |
| SHA256: | F551FAB1E40BE1354AB11655225AB89B656E7D9E5858AA747D708384684B5376 |
| SSDEEP: | 768:27kMDRtNQabdyYdMEfwmf4/4YDEFKymegI+6aWBvAoSf15kyx2CGTh9euIOwN:2HD/Cabr+EfZCNyMjZaAirt/Q |
MALICIOUS
Loads dropped or rewritten executable
- keygen.exe (PID: 2948)
Drops executable file immediately after starts
- keygen.exe (PID: 2948)
SUSPICIOUS
Checks supported languages
- keygen.exe (PID: 2948)
Reads the computer name
- keygen.exe (PID: 2948)
Executable content was dropped or overwritten
- keygen.exe (PID: 2948)
Drops a file with a compile date too recent
- keygen.exe (PID: 2948)
INFO
Checks supported languages
- notepad.exe (PID: 2424)
Manual execution by user
- notepad.exe (PID: 2424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE Yoda's Crypter (60.7) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15) |
| .exe | | | Win32 Executable (generic) (10.3) |
| .exe | | | Win16/32 Executable Delphi generic (4.7) |
| .exe | | | Generic Win/DOS Executable (4.5) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2047-Jul-10 21:36:22 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 3 |
| TimeDateStamp: | 2047-Jul-10 21:36:22 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
TEAM AiR | 4096 | 86016 | 0 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
TEAM AiR (#2) | 90112 | 49152 | 46080 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.84317 |
.rsrc | 139264 | 4096 | 2048 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.08109 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.74097 | 744 | UNKNOWN | UNKNOWN | RT_ICON |
101 | 7.37252 | 396 | UNKNOWN | UNKNOWN | RT_DIALOG |
1003 | 2.16096 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
1015 | 7.7467 | 3384 | UNKNOWN | UNKNOWN | RT_BITMAP |
1016 | 7.75673 | 3384 | UNKNOWN | UNKNOWN | RT_BITMAP |
1017 | 7.77083 | 3384 | UNKNOWN | UNKNOWN | RT_BITMAP |
1018 | 7.79443 | 3384 | UNKNOWN | UNKNOWN | RT_BITMAP |
1019 | 7.81816 | 3384 | UNKNOWN | UNKNOWN | RT_BITMAP |
1020 | 7.82793 | 3384 | UNKNOWN | UNKNOWN | RT_BITMAP |
Imports
GDI32.dll |
KERNEL32.DLL |
USER32.dll |
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2424 | "C:\Windows\system32\notepad.exe" | C:\Windows\system32\notepad.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2948 | "C:\Users\admin\AppData\Local\Temp\keygen.exe" | C:\Users\admin\AppData\Local\Temp\keygen.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
141
Read events
141
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | keygen.exe | C:\Users\admin\AppData\Local\Temp\PlaySound.dll | executable | |
MD5:E77293F6DA4FF1A2605DBD311F3B395F | SHA256:0FE373EE439003D0FB80AE3EA5BBCF4AA8CACF2E9B208365349A80E81EA76064 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report