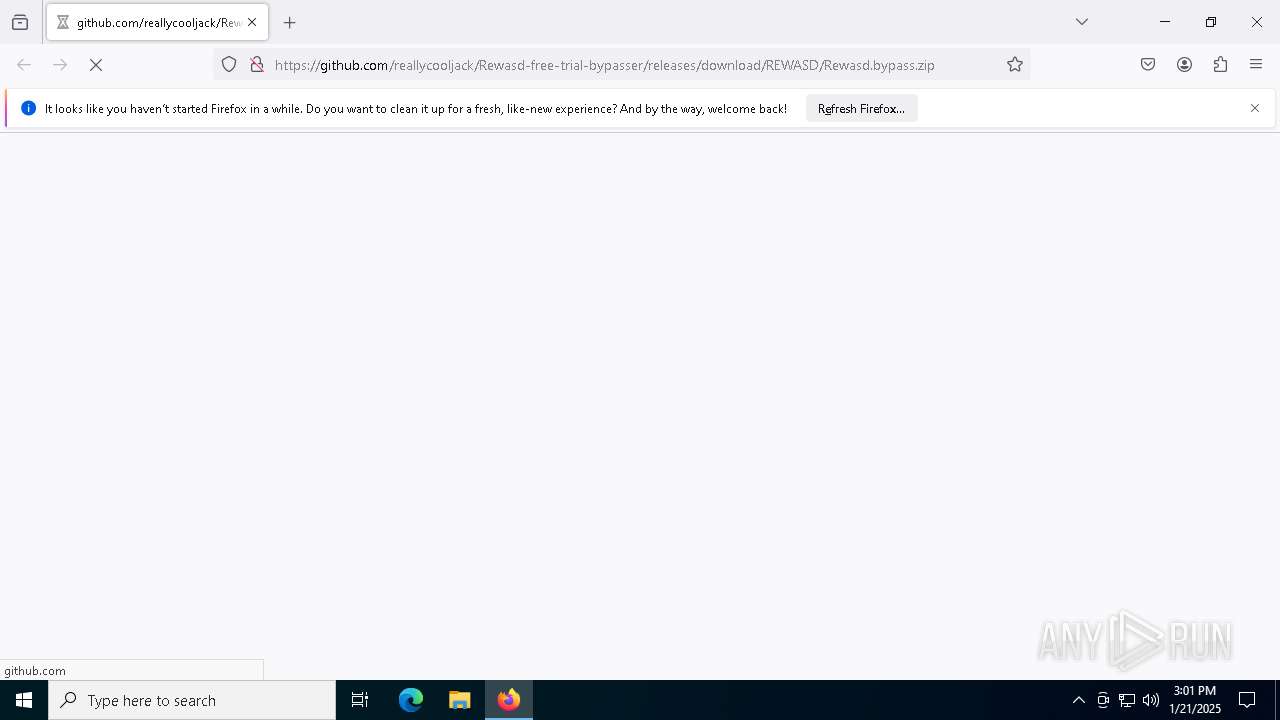
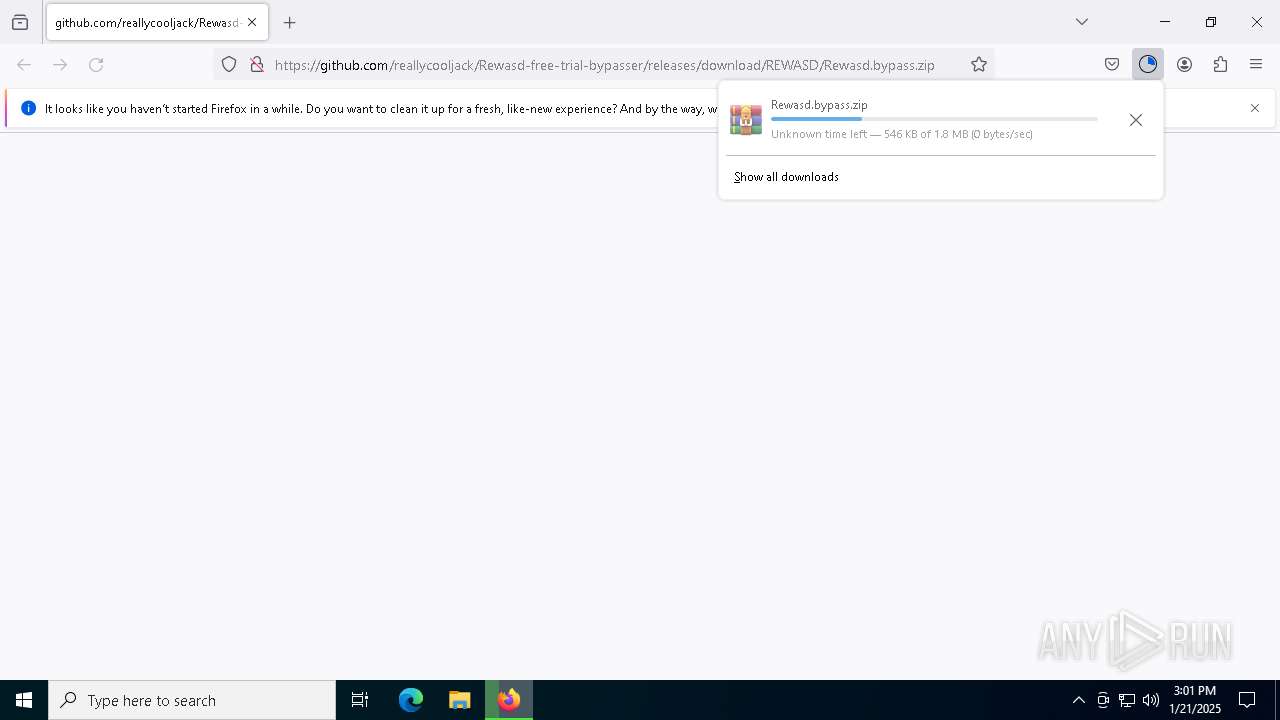
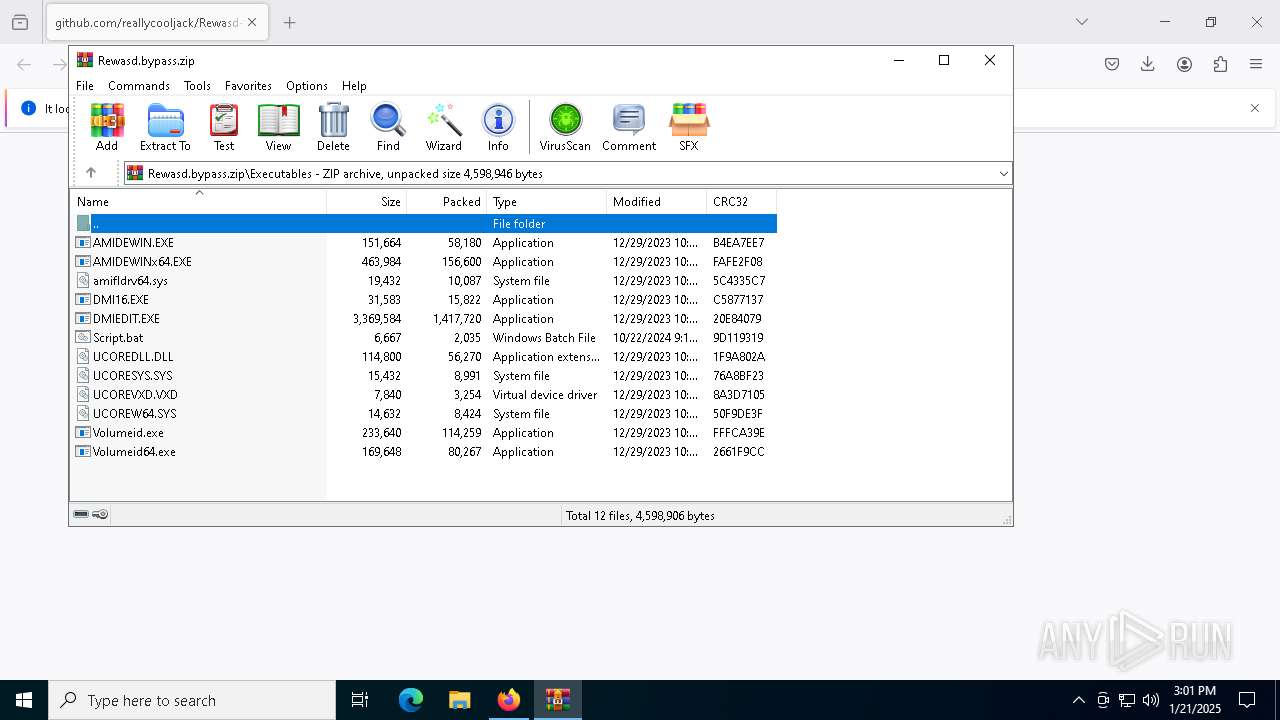
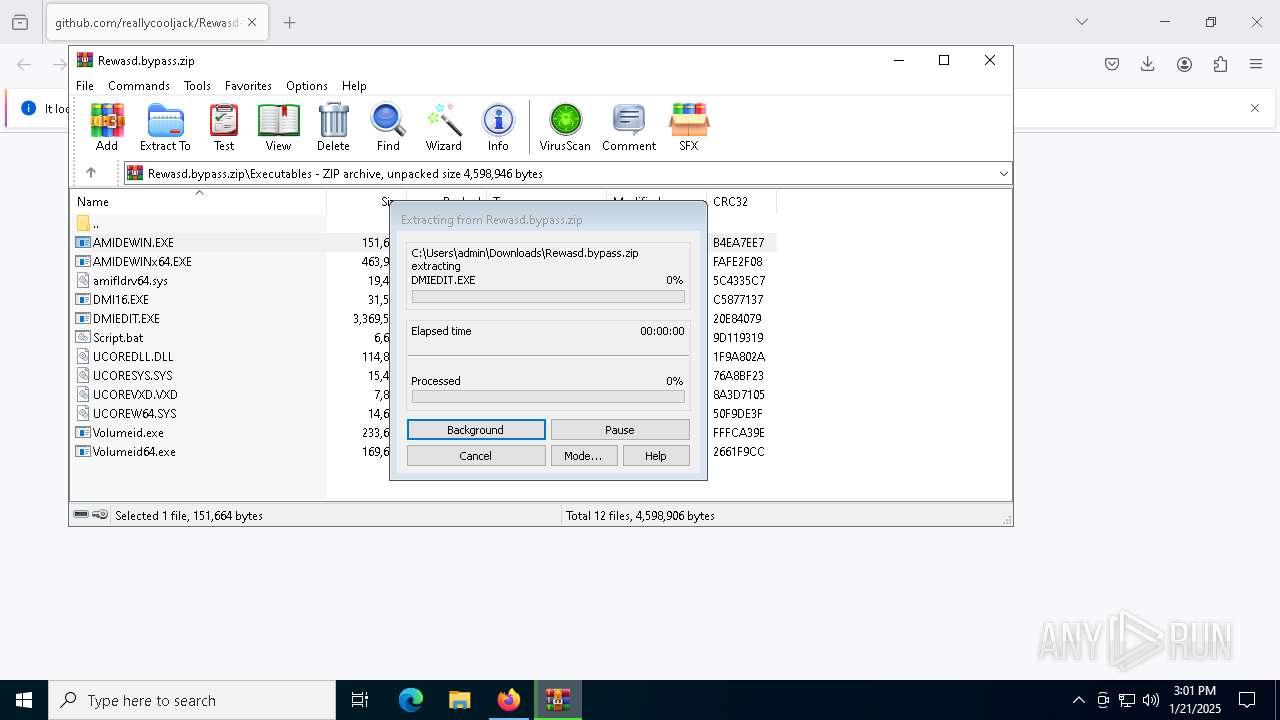
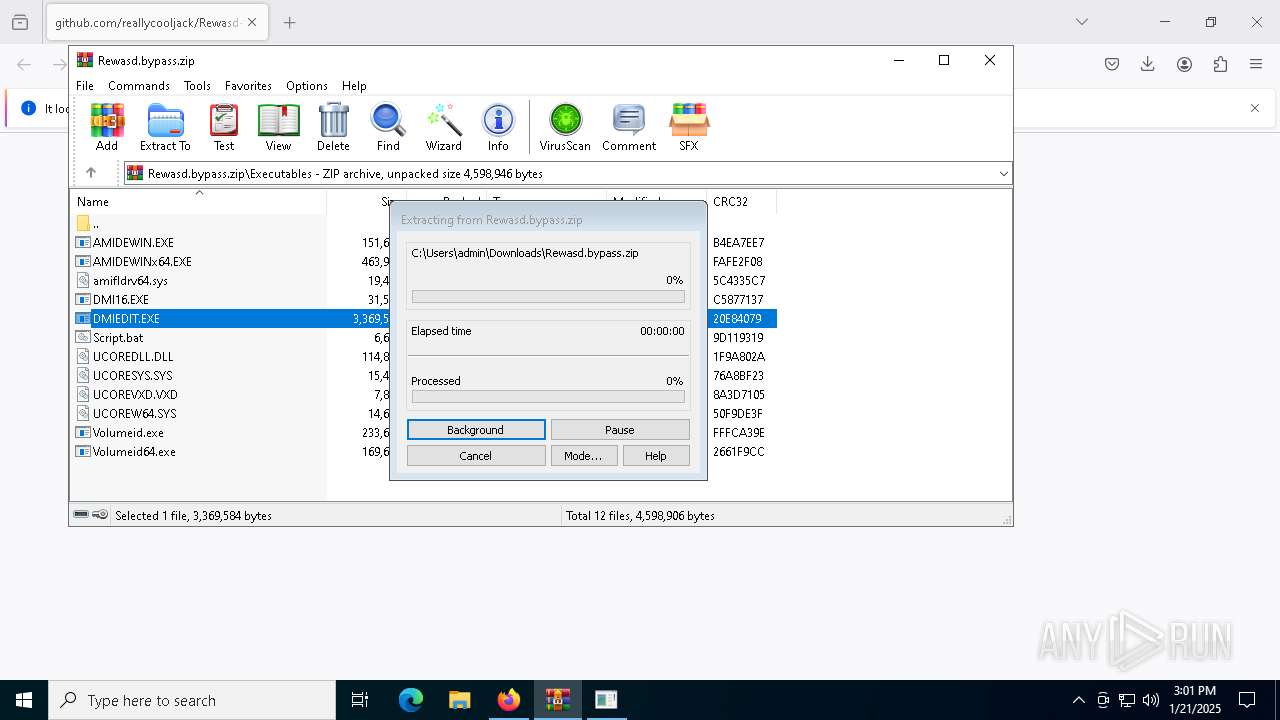
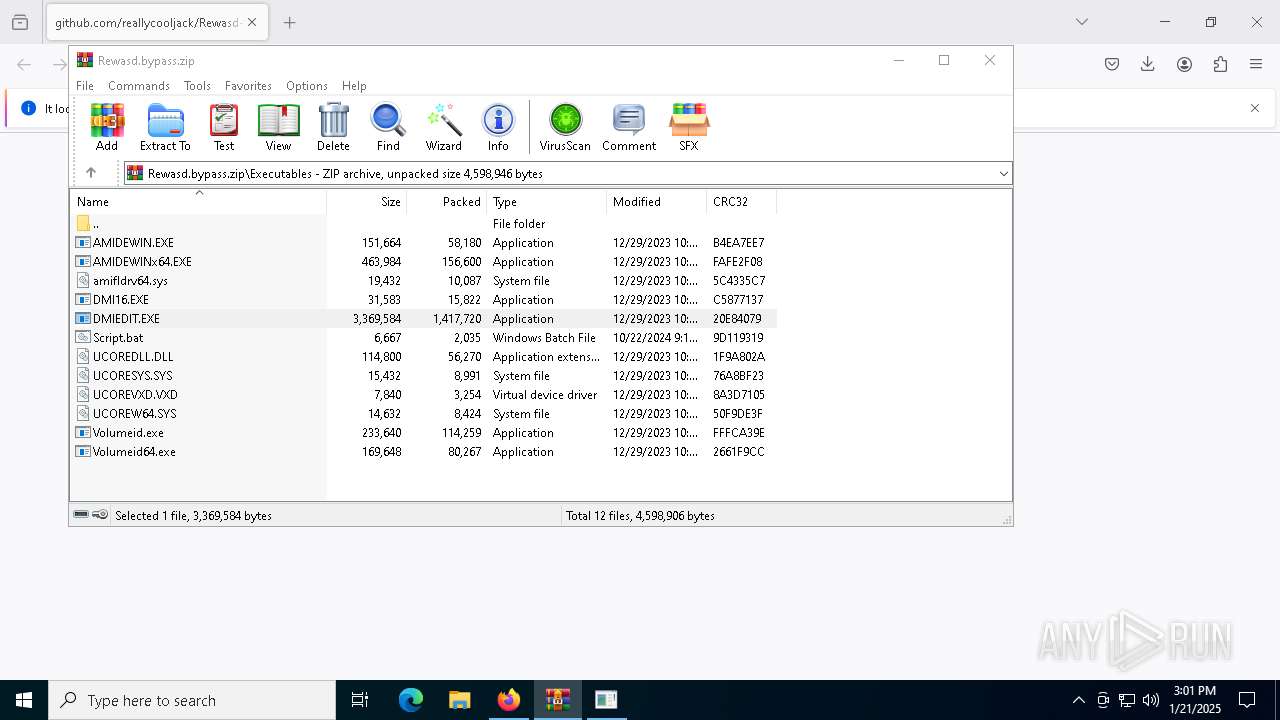
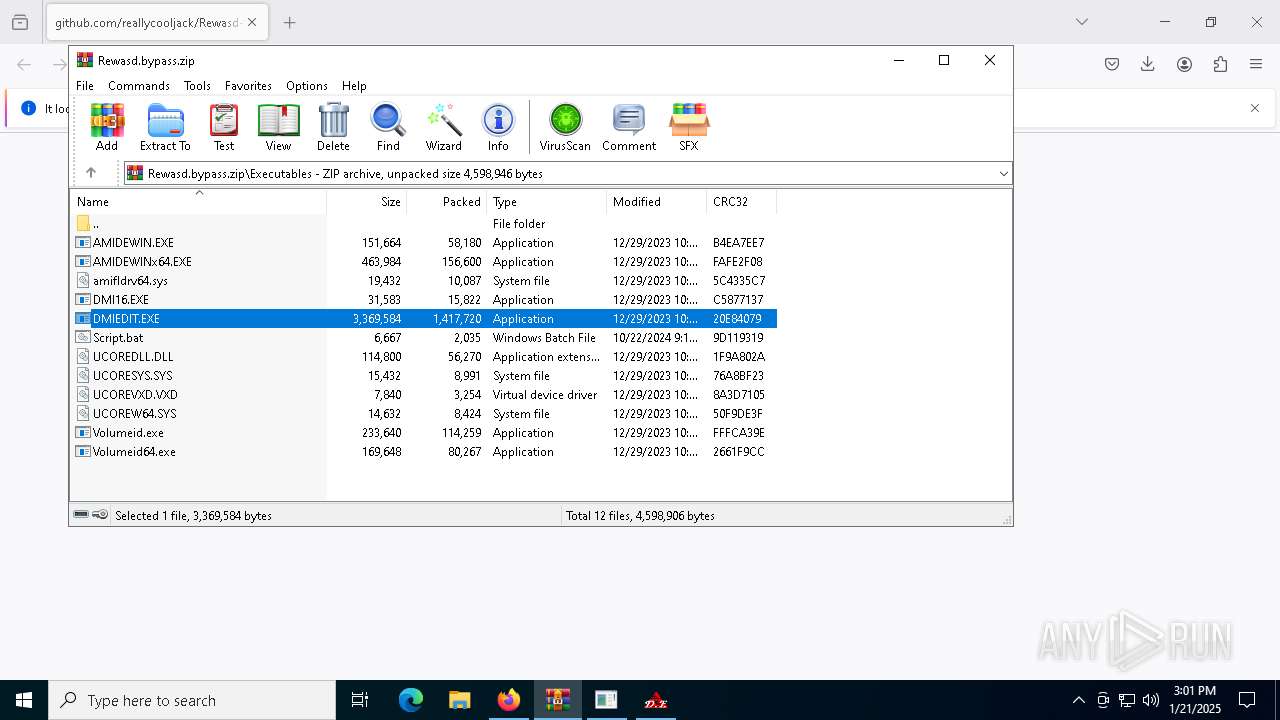
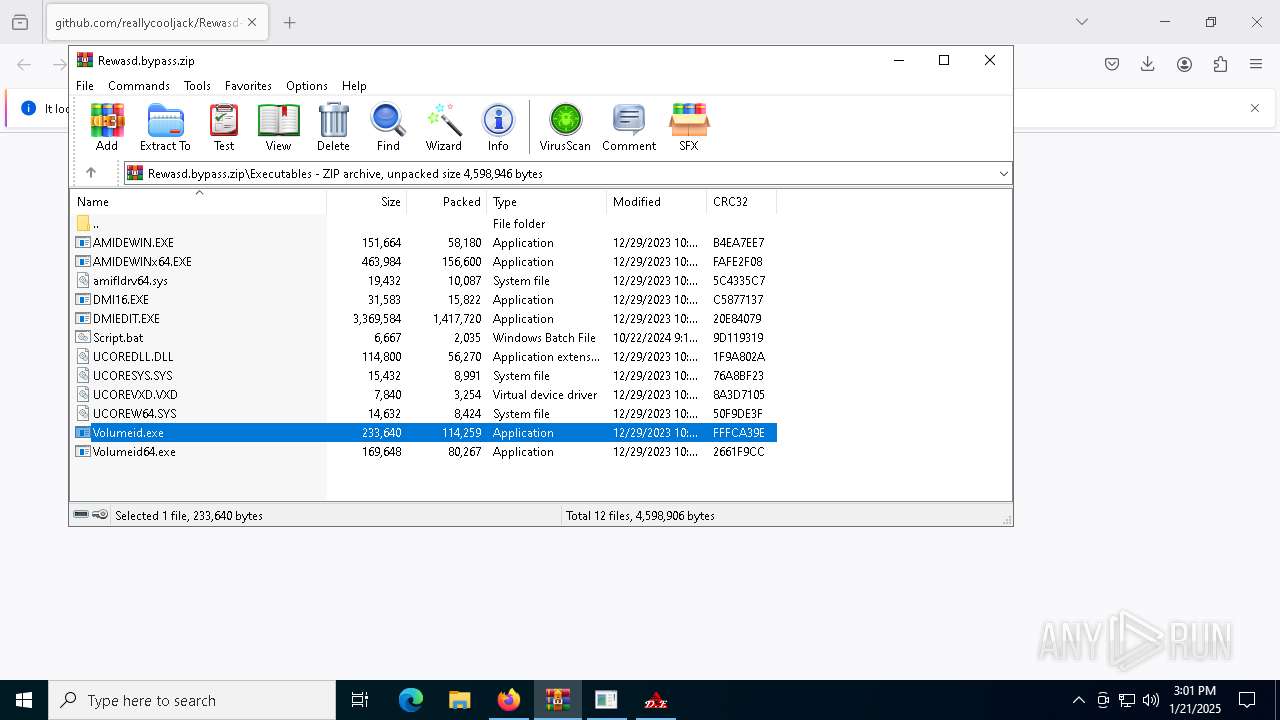
| URL: | https://github.com/reallycooljack/Rewasd-free-trial-bypasser/releases/download/REWASD/Rewasd.bypass.zip |
| Full analysis: | https://app.any.run/tasks/56b86414-b9c1-46e9-866c-6b83574d57e7 |
| Verdict: | Malicious activity |
| Analysis date: | January 21, 2025, 15:01:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1BC0F2B86E44210E1C80F656AA084940 |
| SHA1: | BEFBFB3C5BA228B58711886646A2E560DF393514 |
| SHA256: | F54559470213819B51B2C560F90B66F67C1E8C9AEBD48E3DD37CBA948E4CE466 |
| SSDEEP: | 3:N8tEdnfqGBEfDycVcV/vAE2kCkFkWLcn:2ugGyfDly3ArKeMc |
MALICIOUS
No malicious indicators.SUSPICIOUS
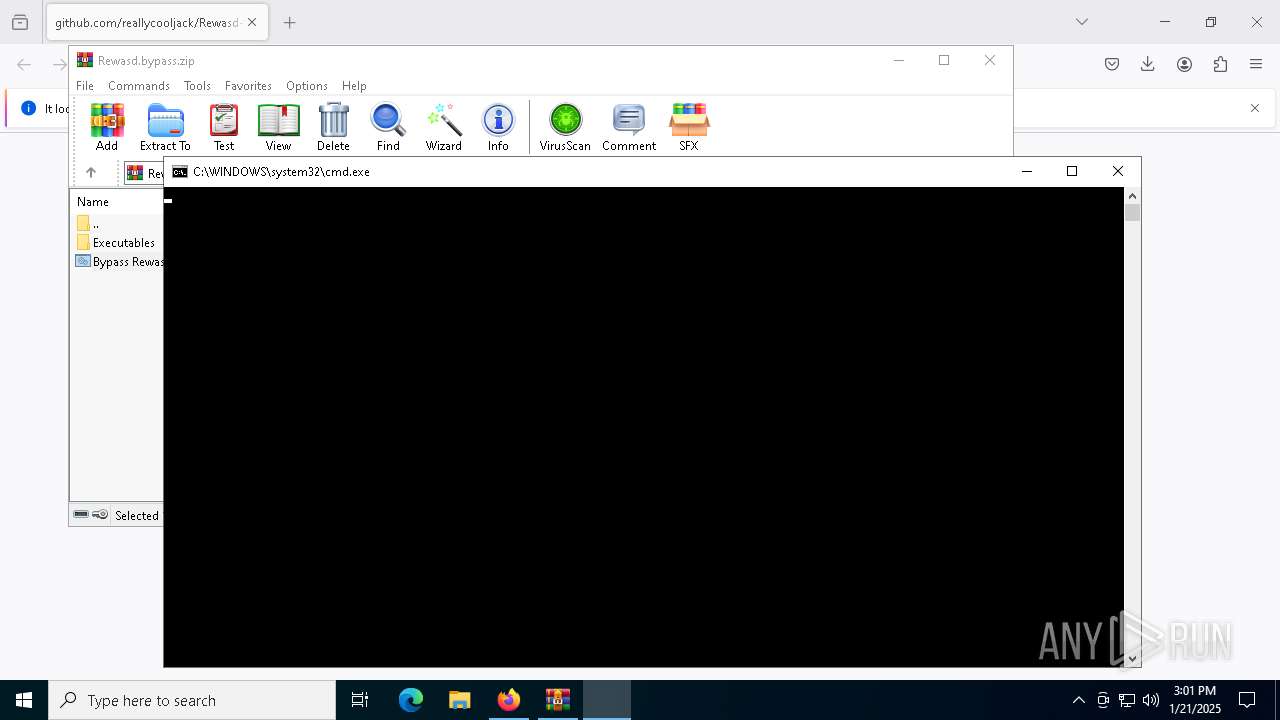
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 8056)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 8056)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8056)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 8056)
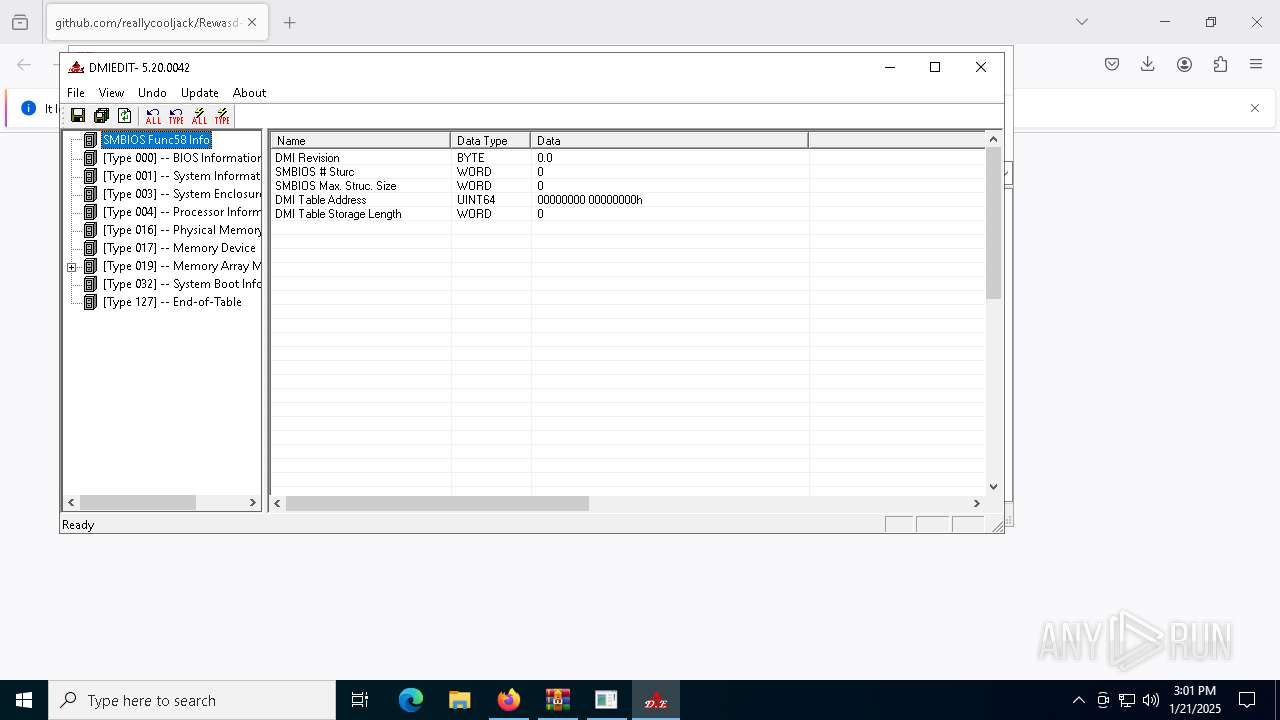
There is functionality for taking screenshot (YARA)
- DMIEDIT.EXE (PID: 5740)
INFO
Application launched itself
- firefox.exe (PID: 6552)
- firefox.exe (PID: 6612)
Manual execution by a user
- WinRAR.exe (PID: 8056)
The sample compiled with english language support
- firefox.exe (PID: 6612)
- WinRAR.exe (PID: 8056)
The process uses the downloaded file
- firefox.exe (PID: 6612)
- WinRAR.exe (PID: 8056)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8056)
- firefox.exe (PID: 6612)
Checks supported languages
- AMIDEWIN.EXE (PID: 3812)
- DMIEDIT.EXE (PID: 5740)
- Volumeid.exe (PID: 3952)
Reads the computer name
- DMIEDIT.EXE (PID: 5740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
149
Monitored processes
20
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3208 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.276\Executables\DMIEDIT.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.276\Executables\DMIEDIT.EXE | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DMI EDITOR/Windows MFC Application Exit code: 3221226540 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
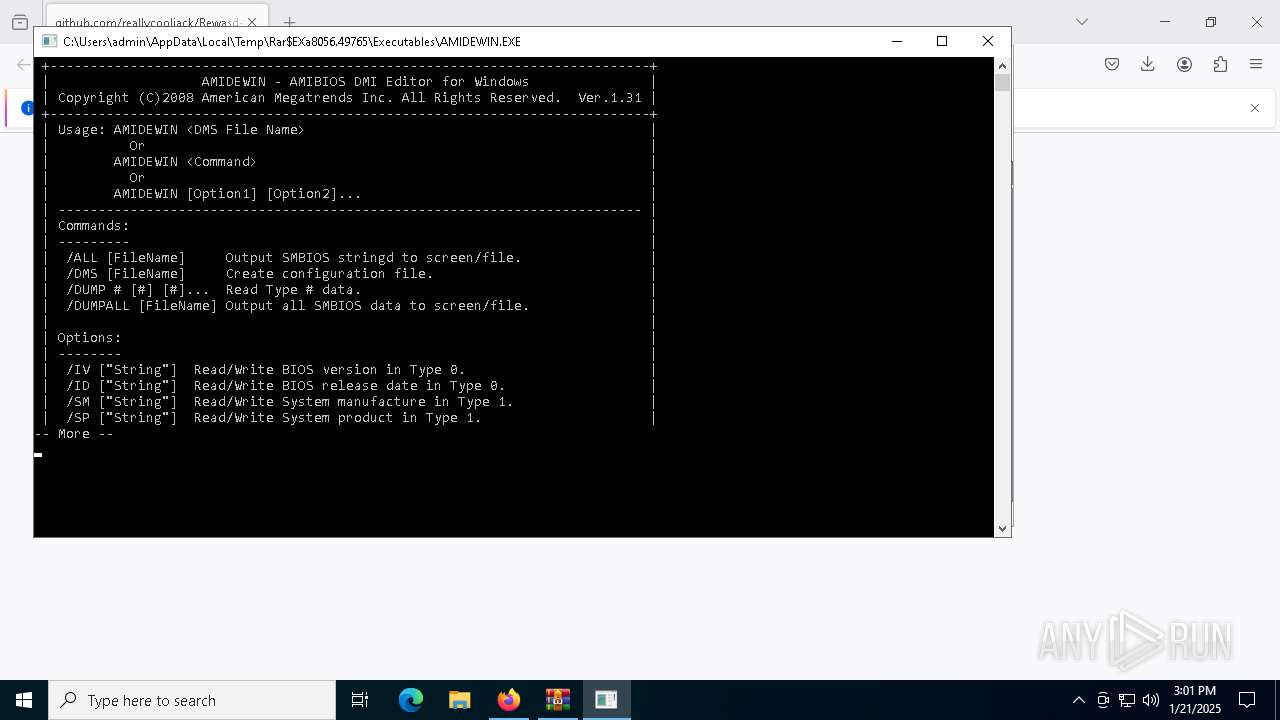
| 3812 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.49765\Executables\AMIDEWIN.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.49765\Executables\AMIDEWIN.EXE | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AMIDEWIN.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
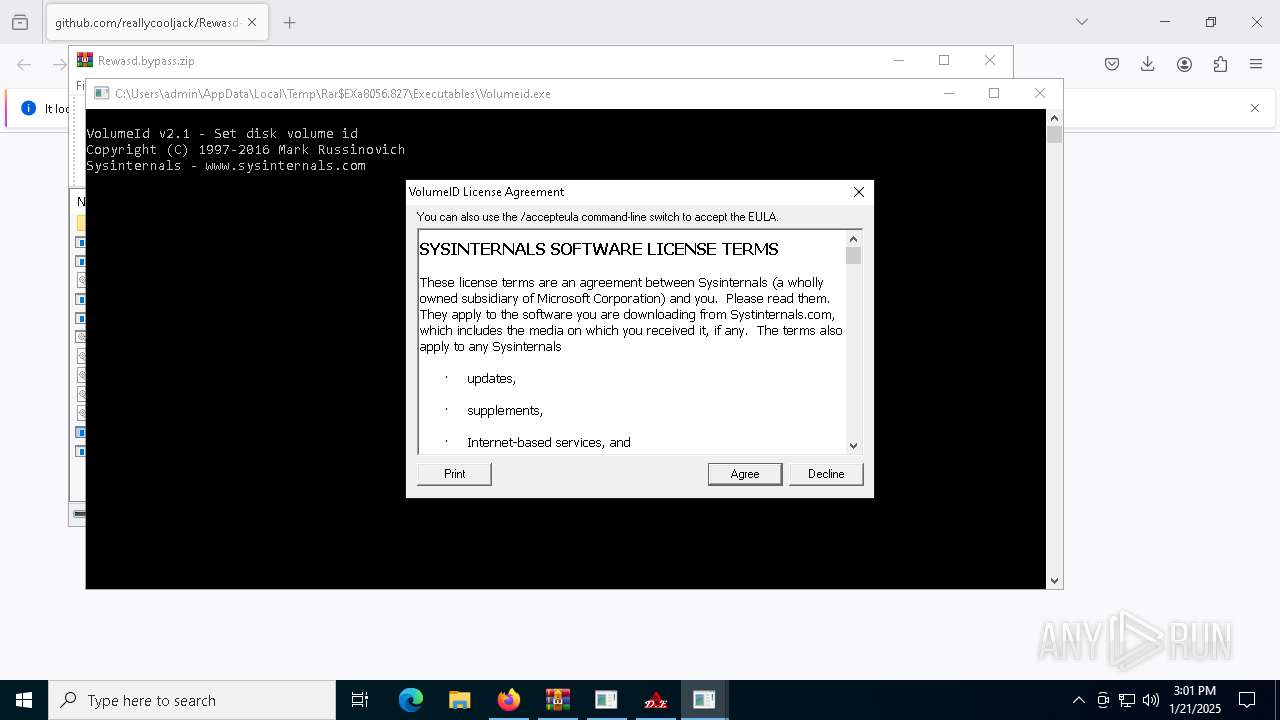
| 3952 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.827\Executables\Volumeid.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.827\Executables\Volumeid.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Set disk volume id Exit code: 1 Version: 2.1 Modules
| |||||||||||||||
| 5740 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.276\Executables\DMIEDIT.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.276\Executables\DMIEDIT.EXE | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: DMI EDITOR/Windows MFC Application Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 5920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Volumeid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6224 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4148 -childID 2 -isForBrowser -prefsHandle 4140 -prefMapHandle 4136 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1132 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {cd238cac-6897-4716-a7f8-ceaca08f574d} 6612 "\\.\pipe\gecko-crash-server-pipe.6612" 2756a3d8690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6552 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://github.com/reallycooljack/Rewasd-free-trial-bypasser/releases/download/REWASD/Rewasd.bypass.zip" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 6612 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://github.com/reallycooljack/Rewasd-free-trial-bypasser/releases/download/REWASD/Rewasd.bypass.zip | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6772 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1740 -parentBuildID 20240213221259 -prefsHandle 1732 -prefMapHandle 1404 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {ceae1ed8-ae66-43a3-9daf-a75ea5b4543b} 6612 "\\.\pipe\gecko-crash-server-pipe.6612" 27563fe8810 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
15 417
Read events
15 407
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6612) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Rewasd.bypass.zip | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3952) Volumeid.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\VolumeID |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
Executable files
35
Suspicious files
166
Text files
48
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6612 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6612 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 6612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 6612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 6612 | firefox.exe | C:\Users\admin\Downloads\Rewasd.rGJUgLwn.bypass.zip.part | — | |
MD5:— | SHA256:— | |||
| 6612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
79
DNS requests
127
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6612 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6612 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
6612 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6612 | firefox.exe | POST | 200 | 172.217.23.99:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
6612 | firefox.exe | POST | 200 | 184.24.77.69:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6612 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6612 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6612 | firefox.exe | POST | 200 | 184.24.77.69:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6612 | firefox.exe | POST | 200 | 172.217.23.99:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.146:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6612 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | whitelisted |
6612 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
6612 | firefox.exe | 142.250.186.74:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
ipv4only.arpa |
| whitelisted |
example.org |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |