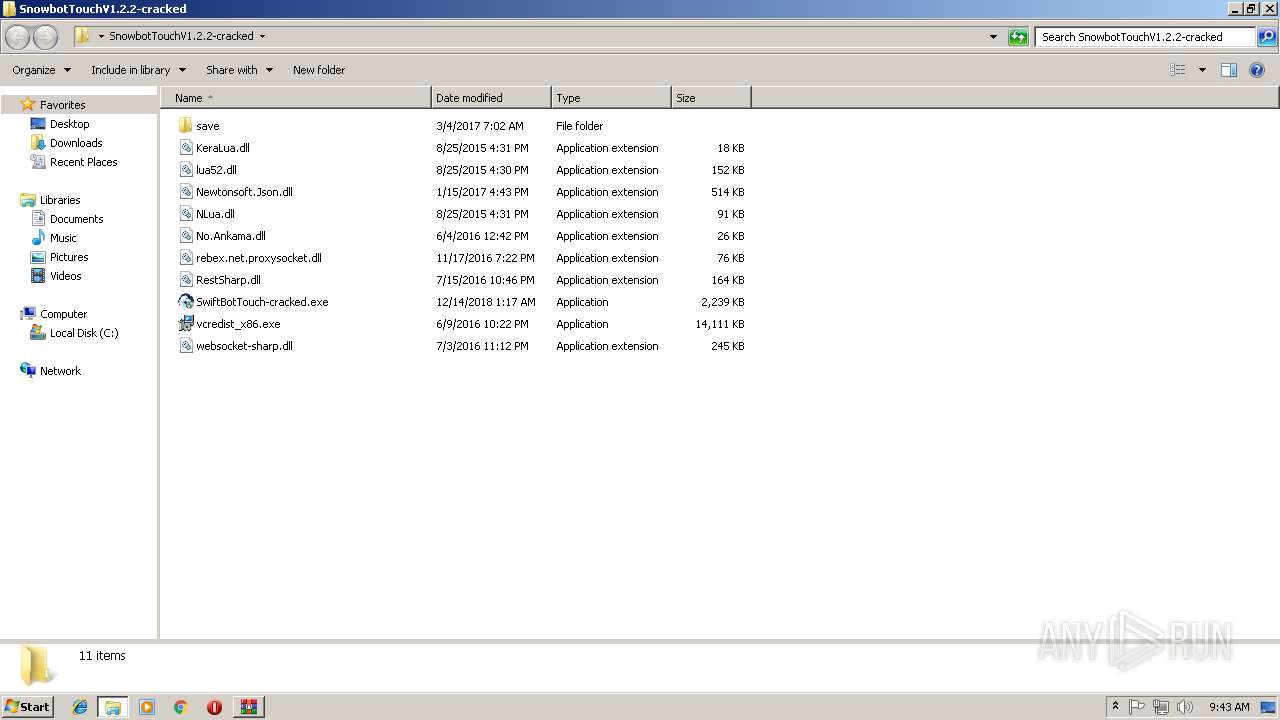
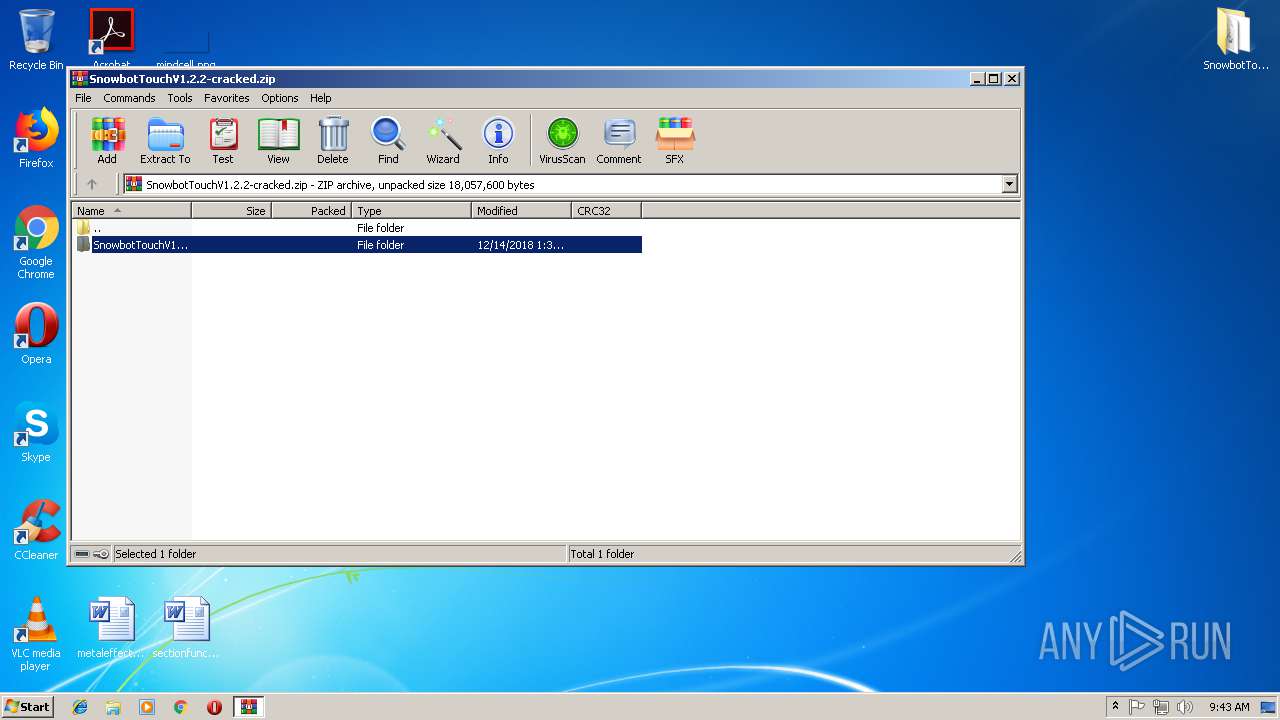
| File name: | SnowbotTouchV1.2.2-cracked.zip |
| Full analysis: | https://app.any.run/tasks/63eb191e-39c6-4520-bdfc-488593554866 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2018, 09:41:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 40C475732AF2239D2D37F7B14CFA67B3 |
| SHA1: | 54420133C6D01445D8C114459C339DE8C65EBBC0 |
| SHA256: | F544A6ECF45BA3BA7FBF48F38C0C3610ACF70D3854B532A417A1E8855BA21DDD |
| SSDEEP: | 393216:LvfNMlpgv89WAjWIV2PZwND2OlLiTF9r+5cu:LnepghwWIV2PZm2OkB+5cu |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1732)
Application was dropped or rewritten from another process
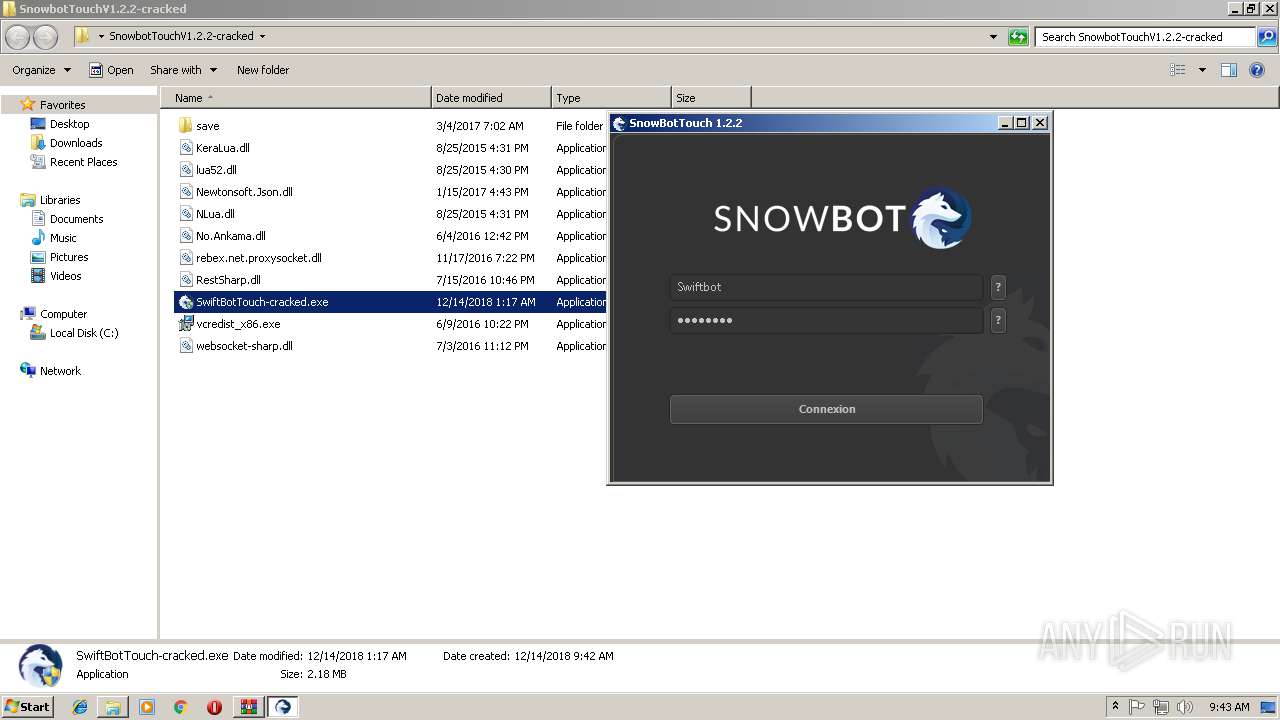
- SwiftBotTouch-cracked.exe (PID: 2240)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3336)
Connects to unusual port
- SwiftBotTouch-cracked.exe (PID: 2240)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:12:14 02:37:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | SnowbotTouchV1.2.2-cracked/ |
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1732 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
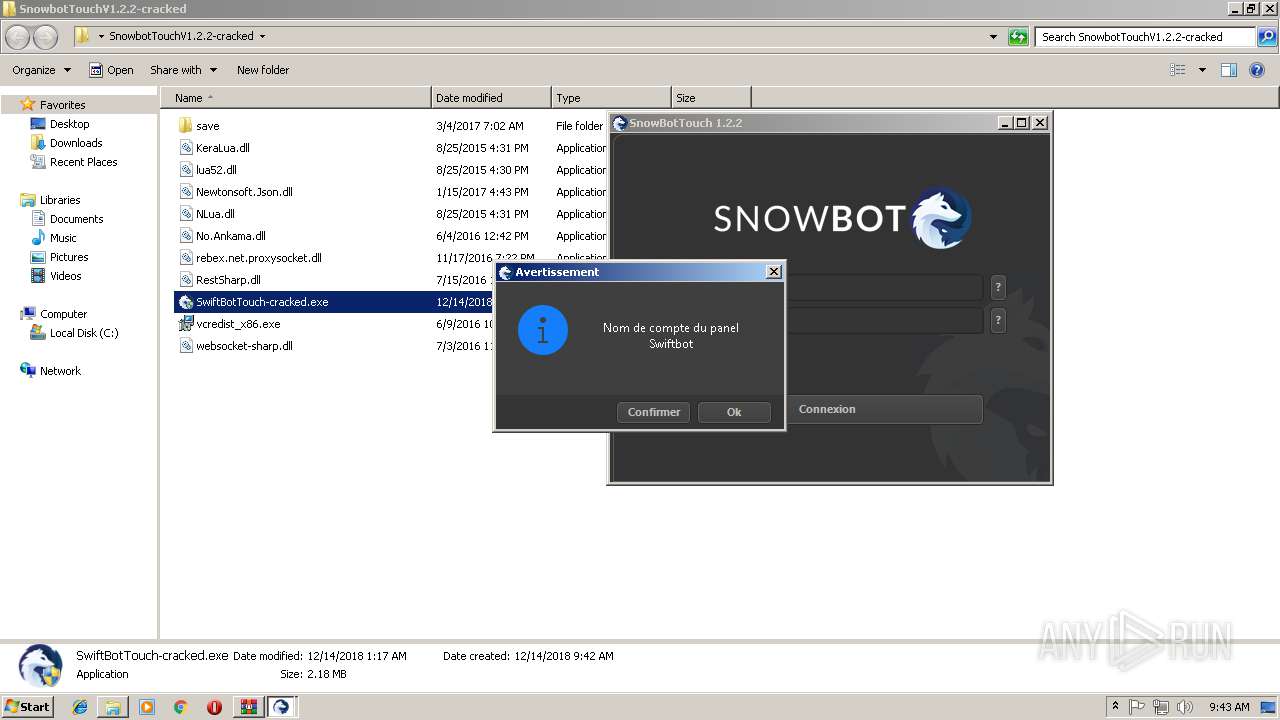
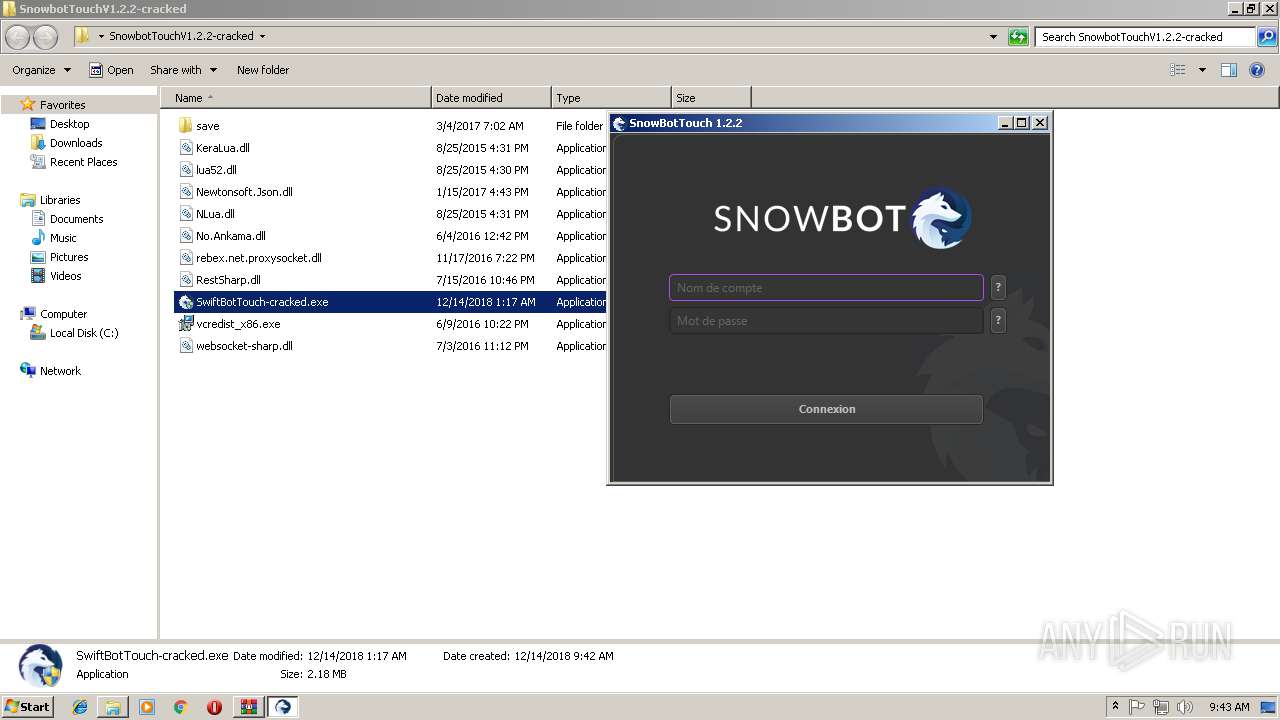
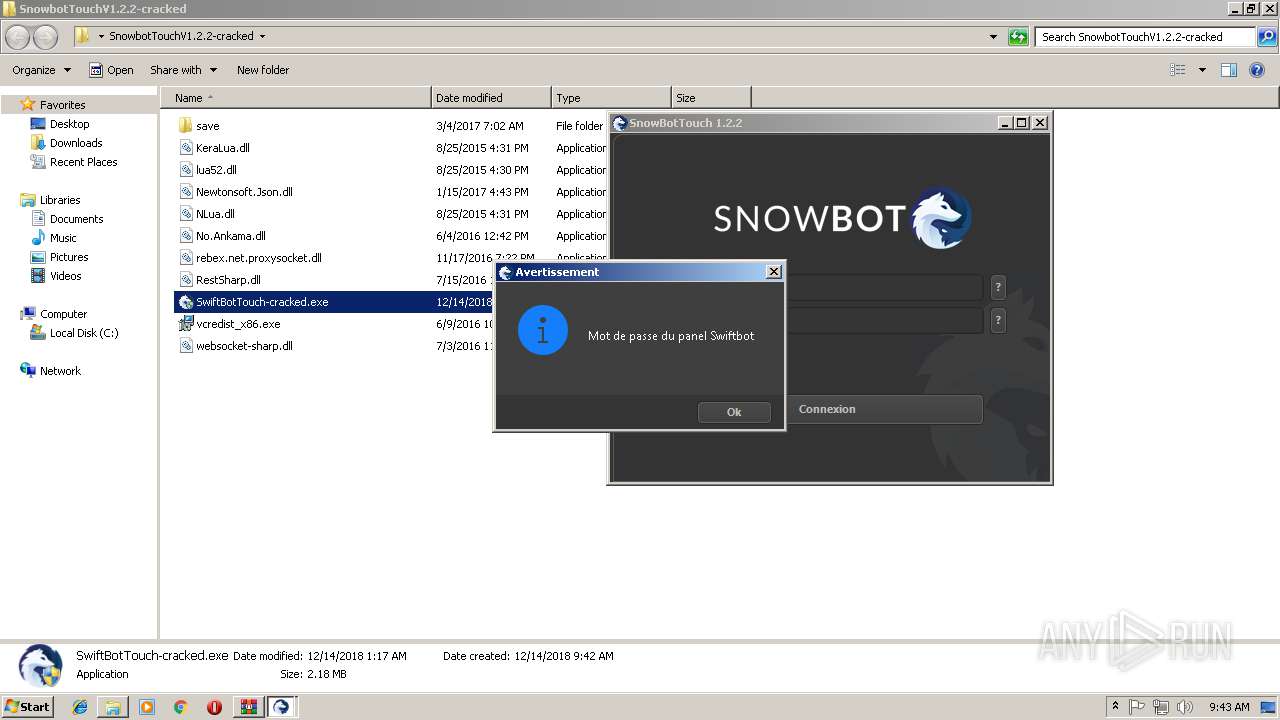
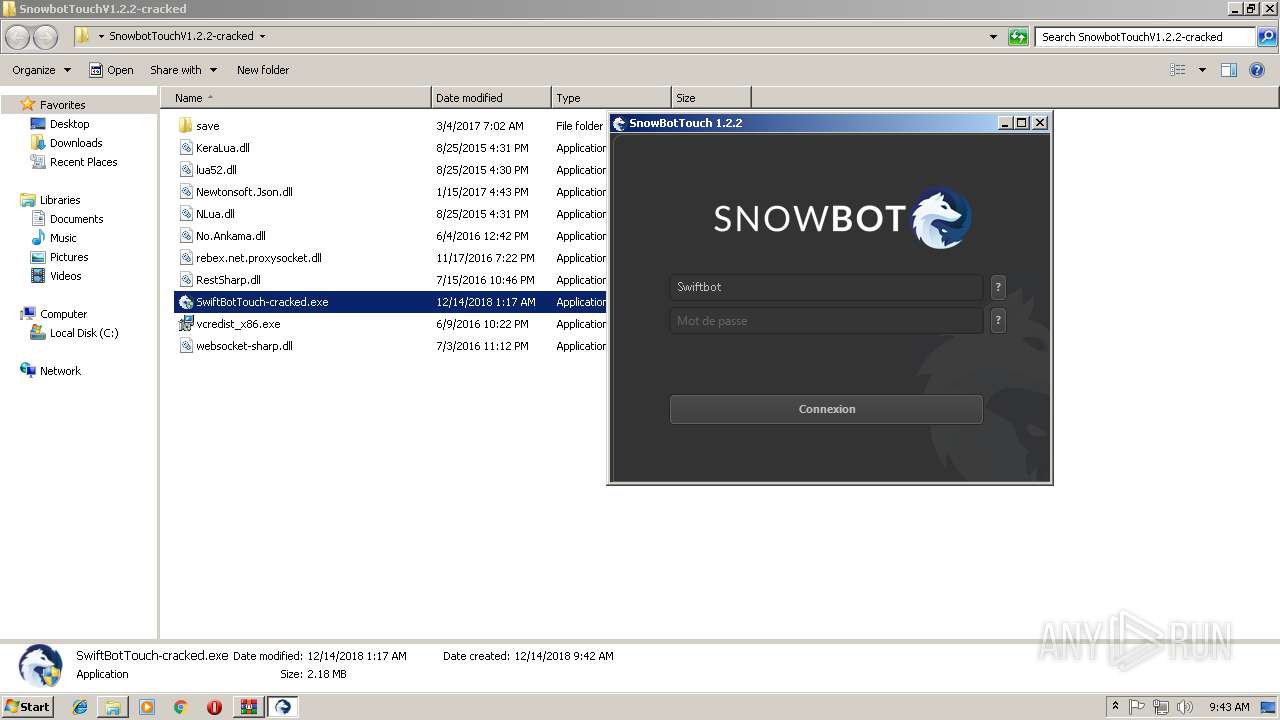
| 2240 | "C:\Users\admin\Desktop\SnowbotTouchV1.2.2-cracked\SwiftBotTouch-cracked.exe" | C:\Users\admin\Desktop\SnowbotTouchV1.2.2-cracked\SwiftBotTouch-cracked.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: SwiftBot Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3336 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SnowbotTouchV1.2.2-cracked.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
777
Read events
765
Write events
12
Delete events
0
Modification events
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SnowbotTouchV1.2.2-cracked.zip | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2240) SwiftBotTouch-cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2240) SwiftBotTouch-cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
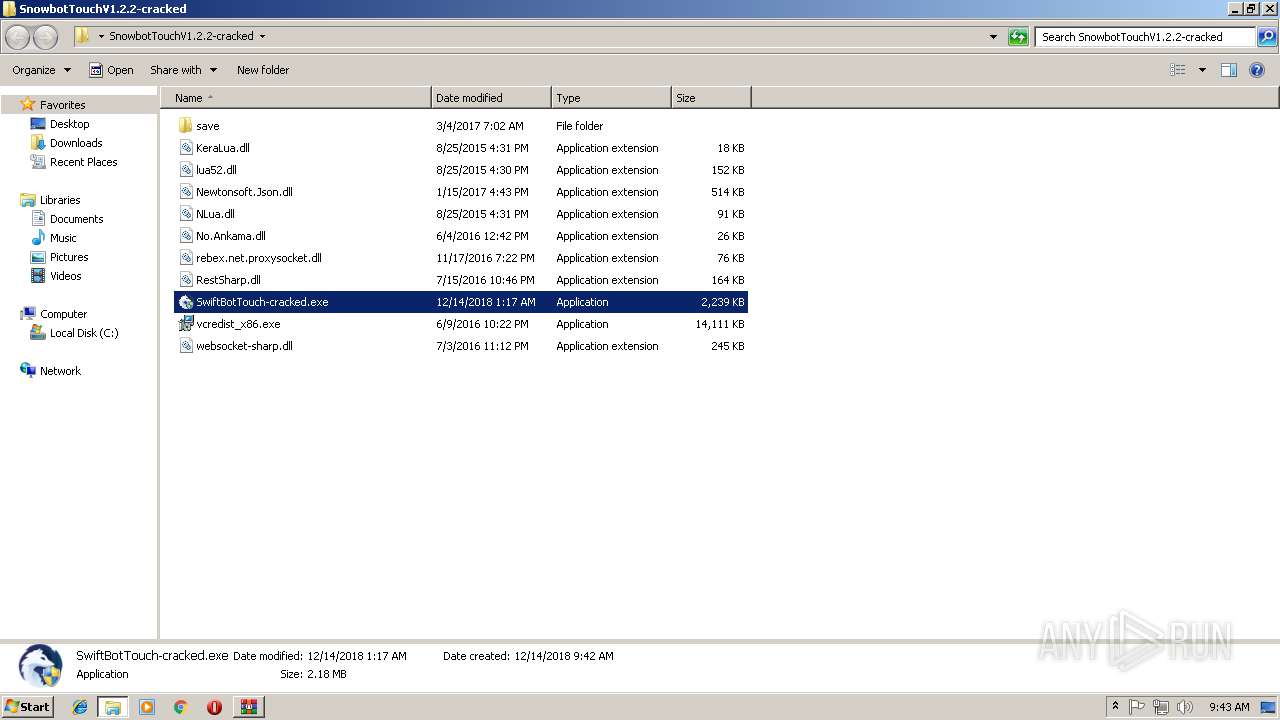
Executable files
8
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\vcredist_x86.exe | — | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\websocket-sharp.dll | — | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\No.Ankama.dll | executable | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\NLua.dll | executable | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\lua52.dll | executable | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\SwiftBotTouch-cracked.exe | executable | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\KeraLua.dll | executable | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\rebex.net.proxysocket.dll | executable | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\Newtonsoft.Json.dll | executable | |
MD5:C53737821B861D454D5248034C3C097C | SHA256:575E30F98E4EA42C9E516EDC8BBB29AD8B50B173A3E6B36B5BA39E133CCE9406 | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.7380\SnowbotTouchV1.2.2-cracked\RestSharp.dll | executable | |
MD5:545F418225B4BF04D7DBFE1B7FEF55D9 | SHA256:93BC87FE592ED8EC971018CB2D78F9AEF0BC049AB5A1DAA947D07C6F292B101E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2240 | SwiftBotTouch-cracked.exe | 93.115.96.98:1111 | — | Techcrea Solutions SARL | FR | unknown |