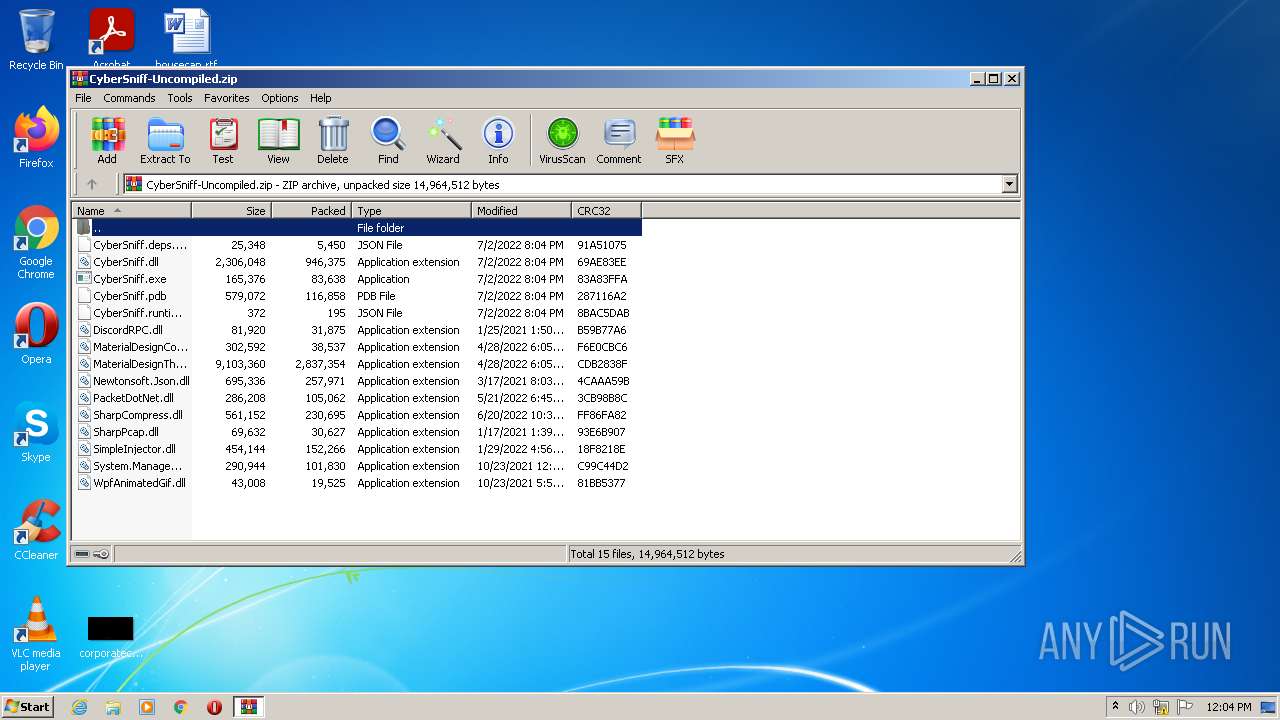
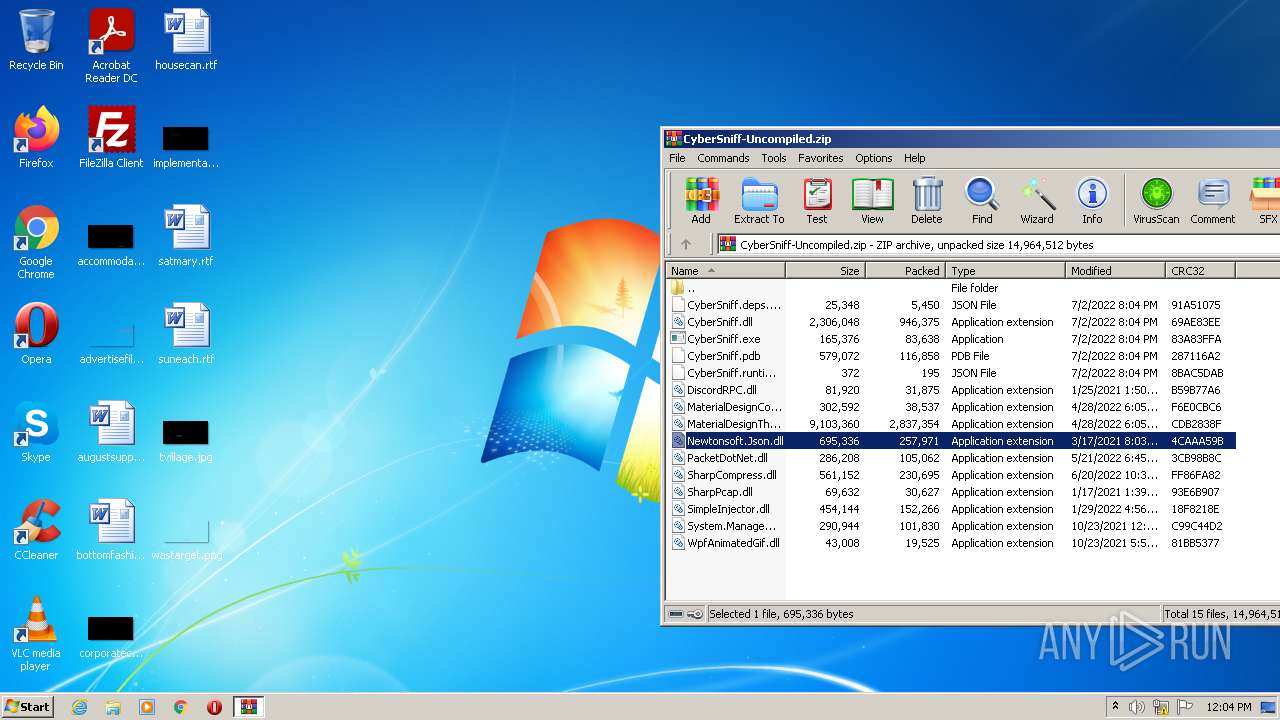
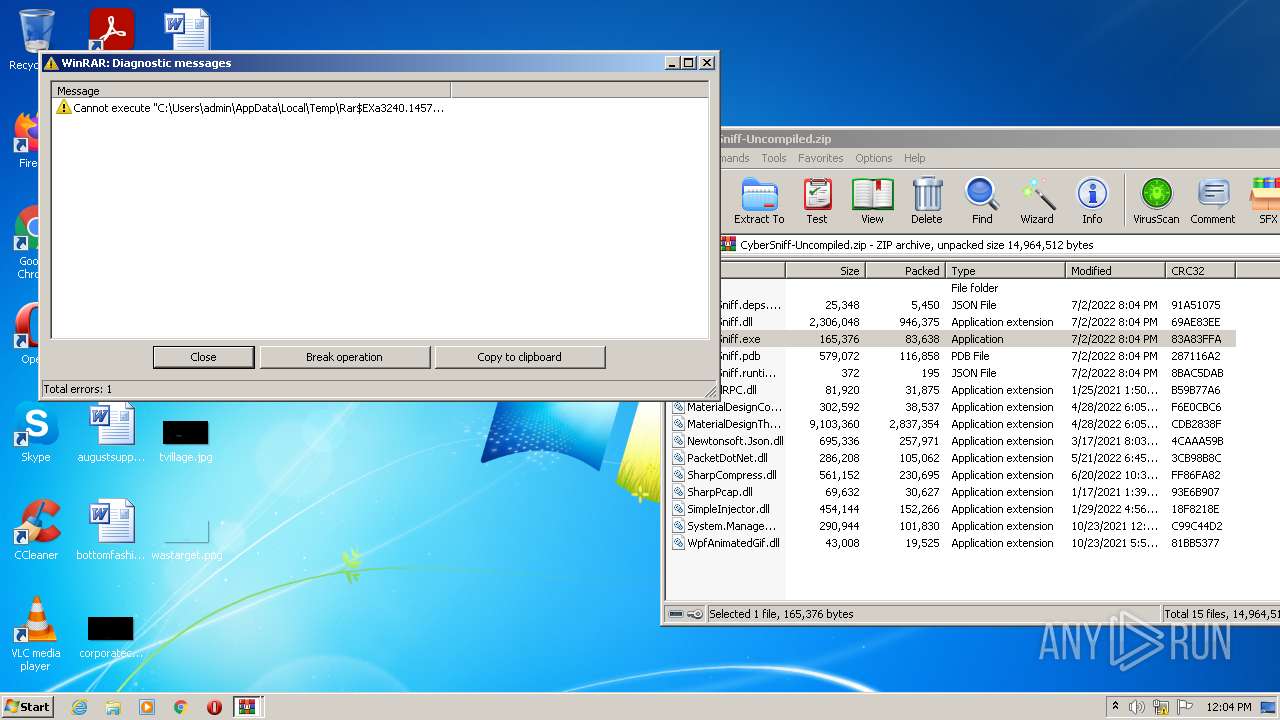
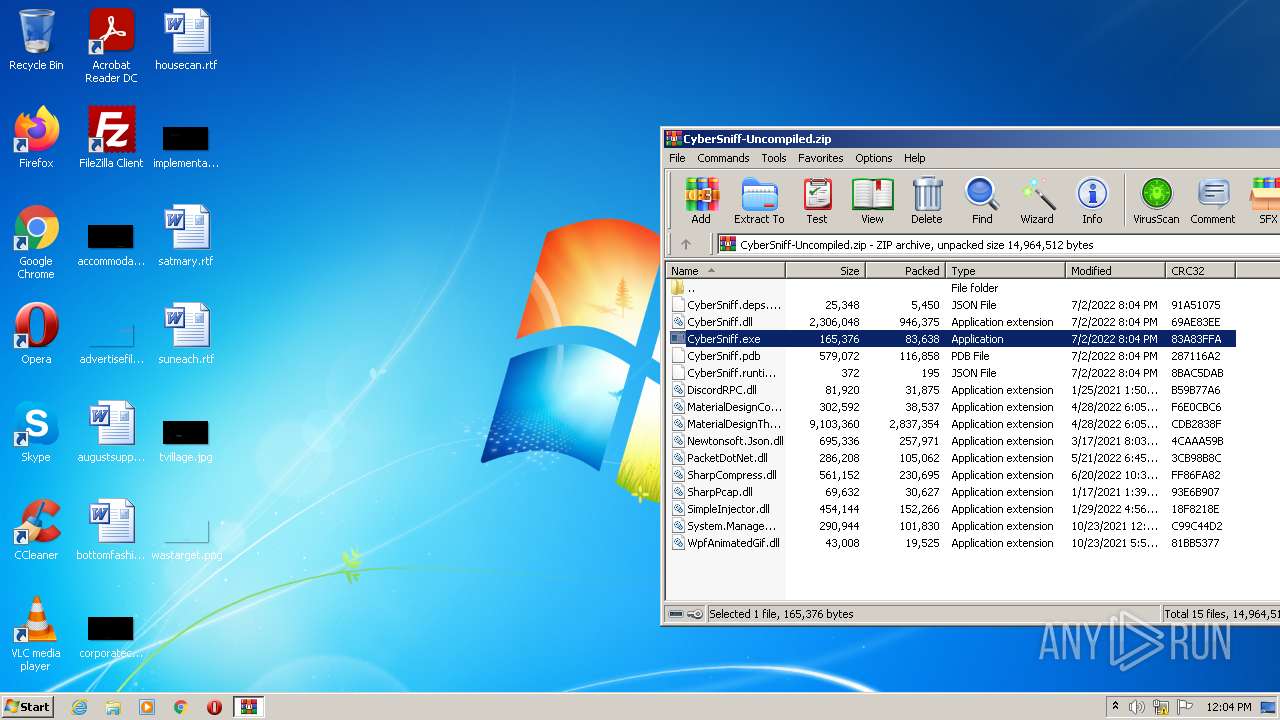
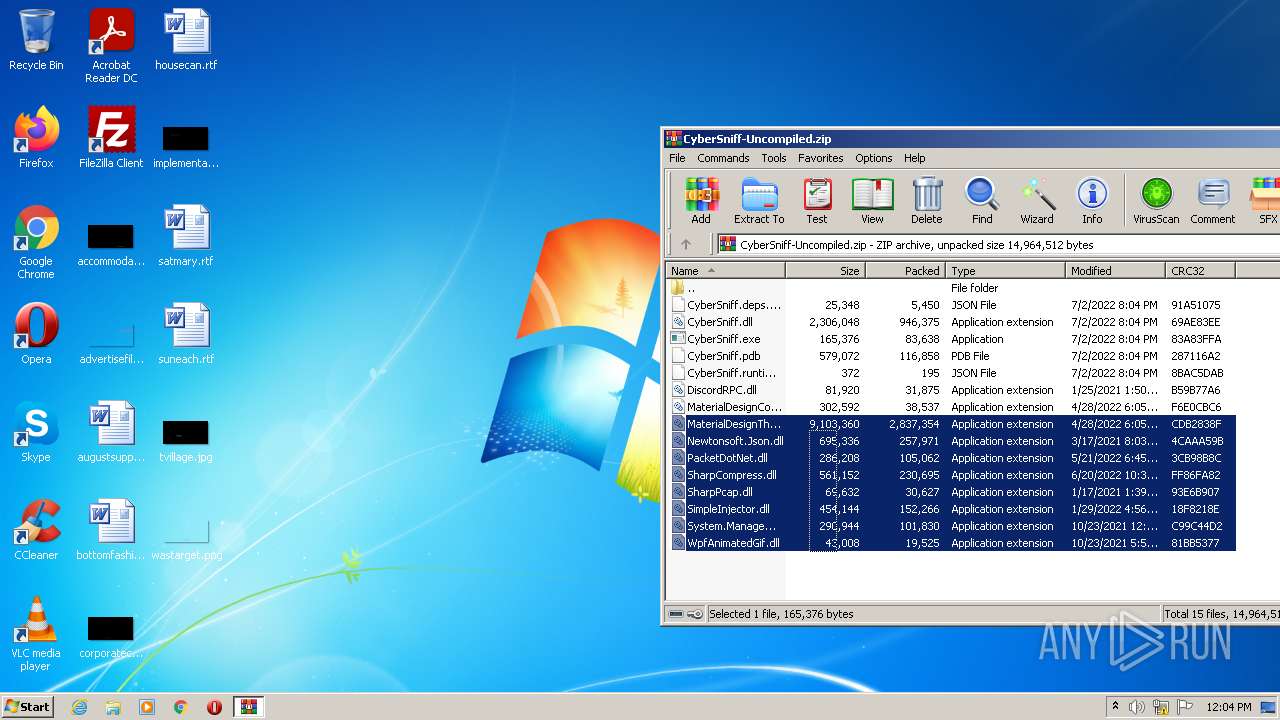
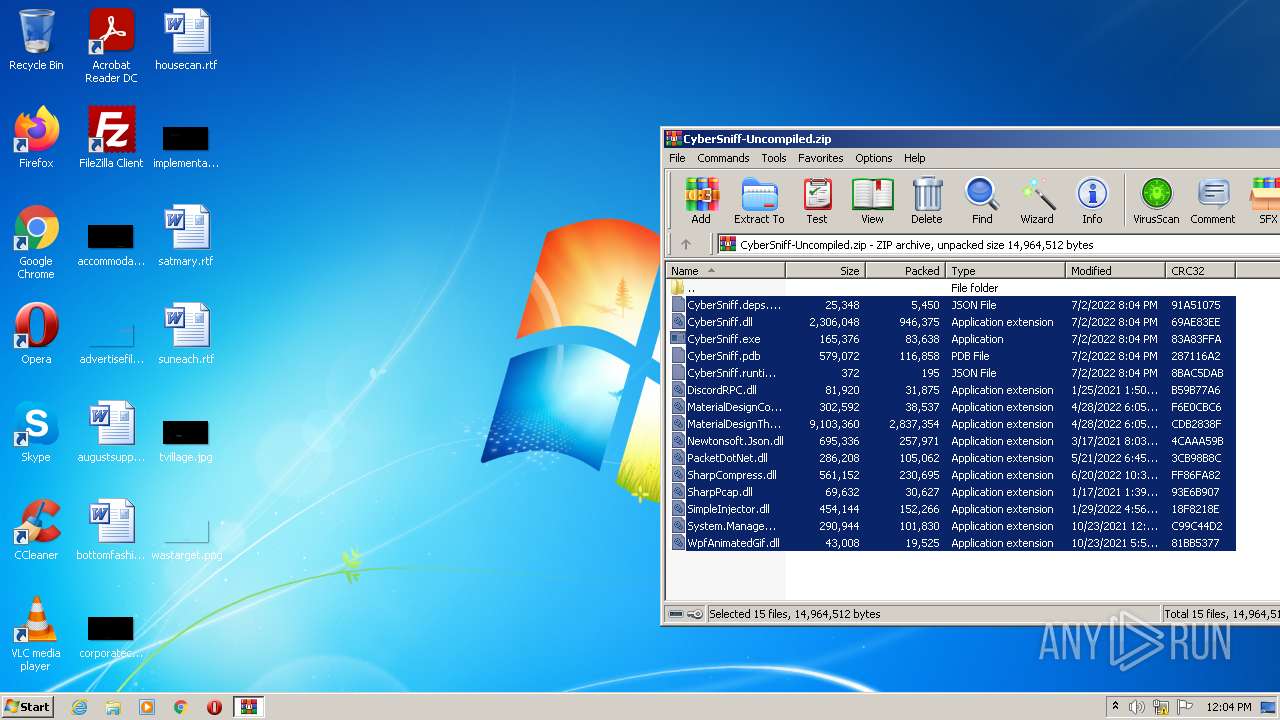
| File name: | CyberSniff-Uncompiled.zip |
| Full analysis: | https://app.any.run/tasks/1436a364-ae57-4dd6-8c6b-105db70e4f70 |
| Verdict: | Malicious activity |
| Analysis date: | July 16, 2022, 11:04:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 28F1F3A370AE99D78785221F508DDEDC |
| SHA1: | 867E8B1E1EEC2B592DF9690E9C4E18BB4E993BC1 |
| SHA256: | F53B181FCBB4C31E0EBD9C144632CFA6528B6CB986DE295DFE871088551A4F7E |
| SSDEEP: | 98304:PBQI6lCTbecSQgXva+i3dlbhU9aWsKRJhQVkyaJeUiOSp6bNypRsCWXdTQFvAxzw:PB56IPlS7C+UjFkTZRzpEFgUwXd2QU |
MALICIOUS
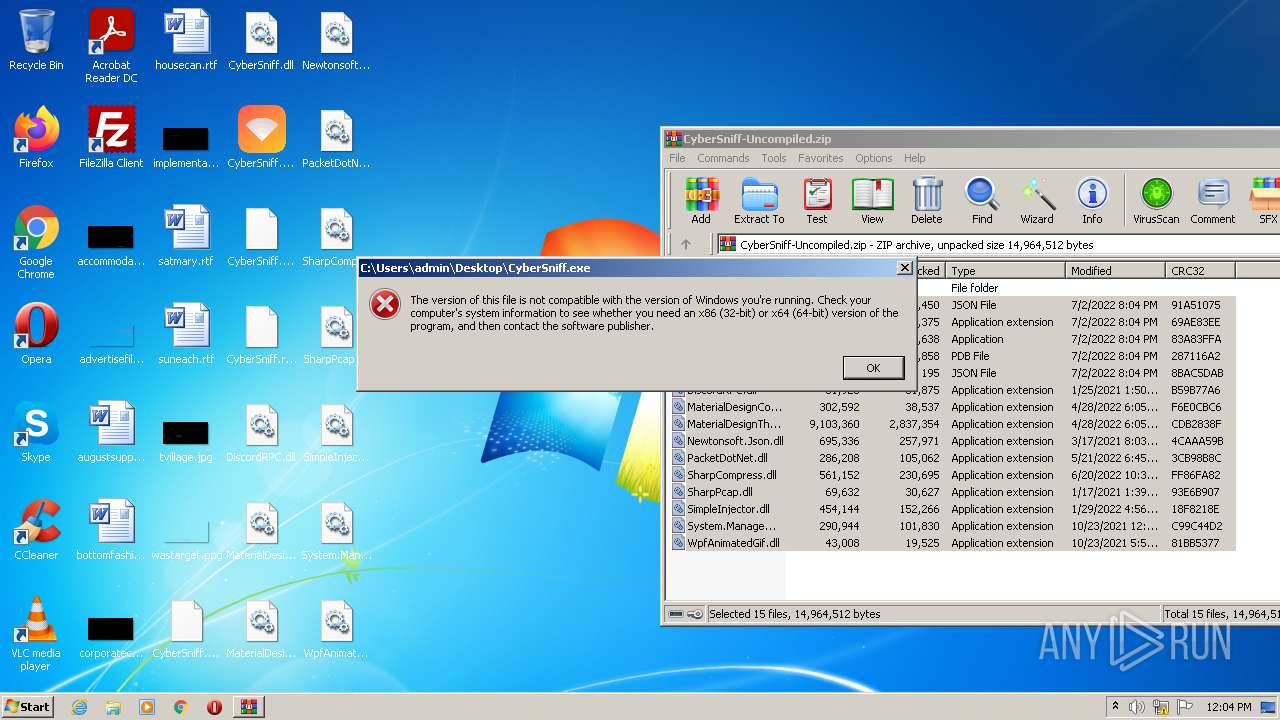
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1448)
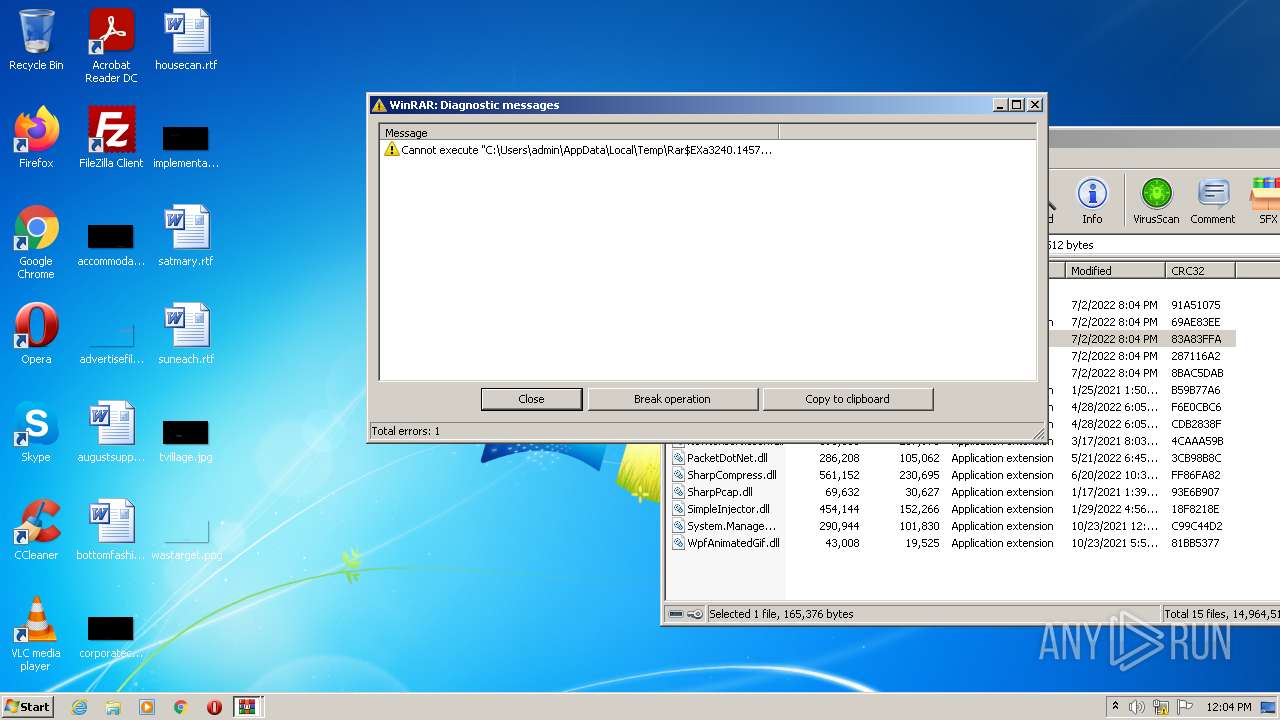
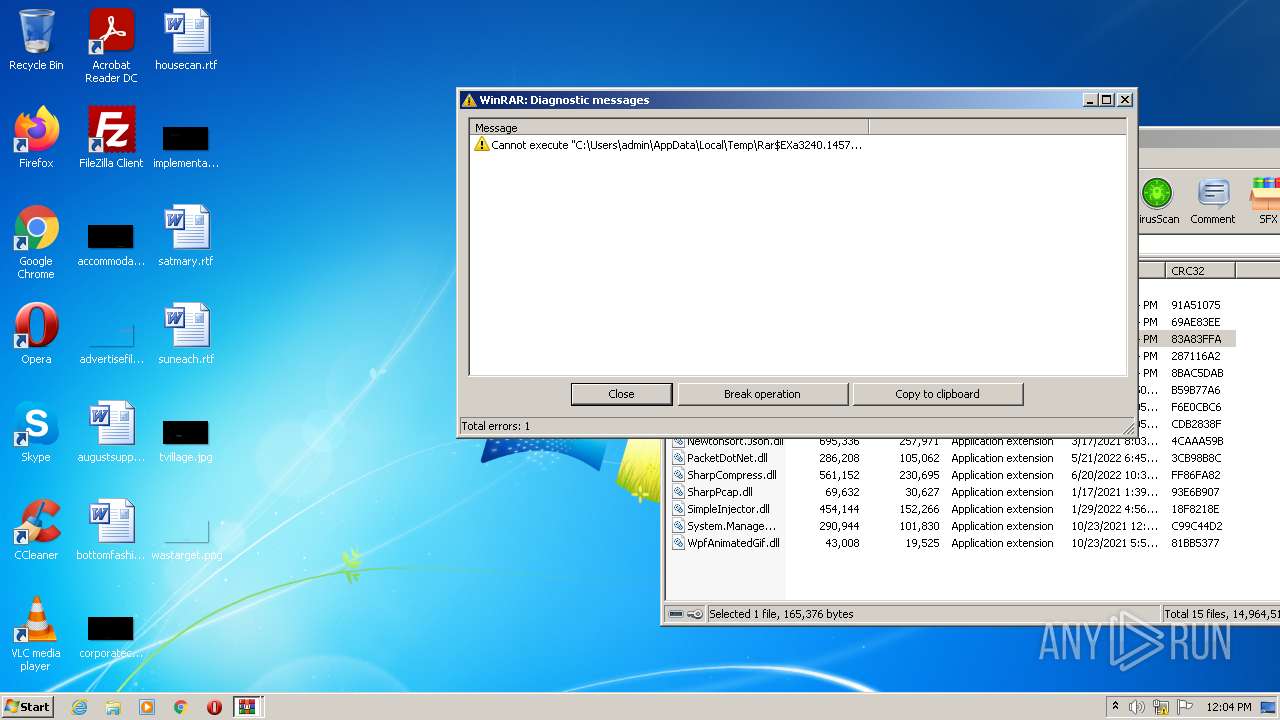
Drops executable file immediately after starts
- WinRAR.exe (PID: 3240)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3240)
Reads the computer name
- WinRAR.exe (PID: 3240)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3240)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3240)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3240)
INFO
Checks supported languages
- rundll32.exe (PID: 2208)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | CyberSniff.runtimeconfig.json |
|---|---|
| ZipUncompressedSize: | 372 |
| ZipCompressedSize: | 195 |
| ZipCRC: | 0x8bac5dab |
| ZipModifyDate: | 2022:07:02 20:04:05 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1448 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2208 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa3240.15955\CyberSniff.runtimeconfig.json | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CyberSniff-Uncompiled.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 100
Read events
1 082
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CyberSniff-Uncompiled.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
22
Suspicious files
3
Text files
2
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\System.Management.dll | executable | |
MD5:83CDA4CC597E6A0B2EBBD1B8F41E94D3 | SHA256:AA474C96B9FD17CB3580D89BB8EB716CB1407C89026B5E8180402666EEEB766A | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\SimpleInjector.dll | executable | |
MD5:F41812A9DD2000C8ED266B0FDDE6448F | SHA256:B8DA962F4852AFEE72C179695D7BB0DE950E6FB55634A38B36433EFC19C6B784 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\DiscordRPC.dll | executable | |
MD5:9ED0CC60FAA1CA995F75DC8B4BF407C4 | SHA256:ACFDE5B1463C95832DD7757A0407D7B81584D1F2AA5175095CA88A47535B2557 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\WpfAnimatedGif.dll | executable | |
MD5:BD86598613F23B58A5E11CE0023FB14A | SHA256:091C944F2DB95521F9190319173F17848D515DA8F5A2374A0AB680406BA65914 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\MaterialDesignThemes.Wpf.dll | executable | |
MD5:B6B346F60F7943EA6B0D2CD3E37CDEA4 | SHA256:8C32F2872FB86C65C01DFEA688AFC48C22013672976219BC1AE2D2D16D285D8D | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\SharpCompress.dll | executable | |
MD5:76CB31819DAD5B386CF995B9CA13A76C | SHA256:963E2620197E09A3E246CE1E751B042C849F78F84B5E472517510D113B9965BC | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\PacketDotNet.dll | executable | |
MD5:A6A8334DE471F57CEA7DFD133B435A59 | SHA256:4CFF6D1ABAFBB93B79632B2A2F4990B93BDBDF1C2BB6965629BB9E085EC3E8E3 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\Newtonsoft.Json.dll | executable | |
MD5:916D32B899F1BC23B209648D007B99FD | SHA256:72CF291D4BAB0EDD08A9B07C6173E1E7AD1ABB7AB727FD7044BF6305D7515661 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\MaterialDesignColors.dll | executable | |
MD5:914C26874567D180A2DD407AA3FB12F6 | SHA256:AED3EFC36186C40C758DF954B76F5BE4A02EEC64486C32AA65A2CA877EA5F21F | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.14572\SharpPcap.dll | executable | |
MD5:0BA9A0E2F4C6122CBD221F9487E6EDD0 | SHA256:9653C299268B81788EC3D9D30CE75E92F8D14846E8428254D80702C46A857938 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report